Abstract
Cloud enterprise resource planning (Cloud ERP) provides an efficient big data management solution for lithium-ion battery (LiB) enterprises. However, in the open ecological environment, Cloud ERP makes the LiB supply chain face multi-user and multi-subject interactions, which can generate sensitive data and privacy data security issues (such as user override access behavior). In this study, we take the value and information interaction into account to examine the user behaviors of the diverse stakeholders in the LiB supply chain. Therefore, a user behavior monitoring algorithm (UBMA), different from the mainstream supervised algorithms and unsupervised learning algorithms, is proposed to monitor the unsafe behaviors that may threaten data privacy in Cloud ERP. The results show that the UBMA can accurately search out the user behavior sequence where the unsafe behavior is located from a large amount of user behavior information, which reduces the complexity of directly identifying the unsafe behavior. In addition, compared with the recursive unsupervised binary classification method, the UBMA model has a lower resource consumption and higher efficiency. In addition, the UBMA has great flexibility. The UBMA can be further updated and extended by re-establishing the statistical characteristics of the standard user behavior fields to quickly adapt to user changes and function upgrades in the LiB supply chain.
1. Introduction
There is great interest in researching clean energy storage systems to make a fossil-fuel-free world, as climate change intensifies. In this regard, the lithium-ion battery (LiB) is considered as a preferred power source due to its high energy density and long lifespan [1]. The LiB has been widely used in electric vehicles, portable electronics, and aviation [2,3]. The growing market for electric vehicles has boosted the demand for LiBs, which further exacerbates the information management dilemmas in the LiB supply chain [4]. Blomgren emphasized the rapid growth in sales and the benefits of lithium-ion batteries during the past 25 years [5]. Compared with traditional data management software, pieces of cloud-based enterprise software such as Cloud ERP have lower operating costs, a more reliable big data processing capability, and a higher flexibility of access. Furthermore, previous research indicated that a cloud-based service is useful to enhance the safety, reliability, and performance of battery supply systems [6] Bosch, a practitioner of battery management, developed a cloud-based service to optimize battery lifetime and performance (https://www.bosch-mobility-solutions.com/en/solutions/software-and-services/battery-in-the-cloud/battery-in-the-cloud/, accessed on 1 January 2023). However, the open and ecological service environment makes battery enterprises using Cloud ERP face unforeseen risks. Data security in the LiB supply chain deserves further exploration.
The literature on the LiB supply chain can be summarized into two major parts. The first part focuses on identifying the critical risks of the LiB supply chain. Some scholars focused more on the safety and reliability of the LiB, while Zhang et al. proposed a new adaptive method to predict the remaining service life of the LiB to improve reliability [7,8]. However, the LiB itself requires the support of a supply chain, in addition to the complex supply chain environment needed for elements such as battery raw materials and battery handling; thus, the LiB faces new safety and reliability problems [9,10,11]. Olivetti et al. [12] indicated that the low concentration of transition metal (i.e., Cobalt and Nickel) natural resources can potentially limit the technology development and mass production of LiBs. Several published results explored the material supply risks of LiBs in three major stages, mining, refining, and manufacturing, in addition to emphasizing that the supply uncertainties of Cobalt, Nickel, and Manganese are the most critical risks in the entire LiB supply chain [9,10,11]. Several studies investigated the safety risk of the LiB, and some safety risk assessment methods were developed such as the data driven safety risk prediction method and the assessment of NMC cathode technology [13,14]. The second part investigated the recycling and re-manufacturing contributions to a sustainable LiB supply chain design. Li et al. [15] proposed a closed loop supply chain network model to maximize the profit in LiBs’ re-manufacture. The model took diverse quality levels of spent battery returns into consideration and provided a theoretical reference for LiBs’ re-manufacture development. Several researchers analyzed the possible profit of a multi-echelon closed-loop battery supply chain with multi-components and multi-products in a multi-period, based on fully fuzzy programming, which provided a possible configuring solution for the closed-loop battery supply chain from an economic aspect [16,17]. Gu et al. [18] investigated the scheme to incentive electric vehicle battery reuse from the perspective of the government.
The existing studies figured out the critical material supply risks in the LiB supply chain and conducted relevant intelligent algorithm to optimize LiBs’ recycling process among different parties [19]. In reality, numerous stakeholders (material providers, manufacturers, sellers, users, etc.) are involved in the LiB supply chain through various transactions. The huge number of transactions and amount of logistics-related information among stakeholders requires efficient data management. Cloud ERP is a mainstream enterprise information software owing to its real-time data analysis and low operating costs. However, privacy security is the largest concerns of LiB enterprises because of the open and ecological characteristics of the cloud service environment. Significant gaps in the literature exist regarding the crucial role of database and information technology in the LiB supply chain’s sustainability and coordination enhancement [20,21,22]. First, few studies have examined the operating risks of the LiB supply chain from the perspective of information and value flow. Second, the operating data in the LiB supply chain is multi-dimensional, highly interactive, and large-scale. Thus, there is an urgent demand for an efficient data management solution. However, few studies concentrated on the information management of the LiB supply chain. Third, Cloud ERP has received attention from LiB enterprises. However, due to the open and ecological characteristics of the Cloud ERP service environment, ERP clouding makes all parties involved in the LiB supply chain face the more serious security issues of sensitive data and private data. The research on privacy protection in the LiB supply chain is insufficient.
Based on the LiB supply chain research review, this study fills in the aforementioned research gaps through the following points. First, the study explains the connotation of the LiB supply chain from the perspective of information and value flow to explore privacy security in an LiB supply chain adopting Cloud ERP. This study considers the LiB supply chain as a network of organizations that are connected through diverse activities to deliver value to the market in the form of products and services delivered to market. The LiB supply chain consists of multiple stakeholders including upstream (i.e., material suppliers and LiB assemblers) and downstream (i.e., transportation companies and battery retailer merchants). Information related to production, logistics, and finance is generated in large quantities in diverse activities among these upstream and downstream stakeholders. Second, data security is the most critical concern for LiB enterprises regarding information sharing [20,23]. Cloud enterprise resource planning (Cloud ERP) is a cloud-based data management software that can help companies record, store, and manage the data generated during the whole process [21,22,24] Cloud ERP is a potential solution to solve the LiBs’ database construction and management dilemmas. However, the privacy concern for Cloud ERP is high-profile because the cloud service is open. Data security concerns are prevalent when enterprises move their ERP system to a cloud-based service [25,26]. This study proposes a user behavior monitoring algorithm to provide data security support for the LiBs’ supply chain that is adopting Cloud ERP, which contributes to the standardized data management of the LiBs’ supply chain transactions.
This study contributes to the current literature by (1) proposing a less resource-consuming and more efficient UBMA model that can be further updated and extended by re-establishing the statistical characteristics of standard user behavior fields to quickly adapt to user changes and functional upgrades in the supply chain and (2) incorporating user behavior factors into the model to address new security issues arising from multi-user information interactions after ERP clouding and make up for the lack of consideration of user behavior factors in existing algorithms. The remainder of this study is structured as follows. The next section describes the user behavior monitoring algorithm based on machine learning. Section 3 takes ultra vires behavior as an example to further explain the UBMA model. Section 4 provides the conclusions and future research directions.
2. Method
Cloud ERP system is deployed on the cloud server. Traditional network protection methods, such as deploying firewalls in the enterprise’s internal LAN [27,28,29], cannot effectively manage user behavior and resist external intrusions. In addition, in the Cloud ERP system, users conduct business cooperation through the Internet, and then information interaction and resource sharing become frequent. The close connection among users makes the Cloud ERP system face serious information security threats, which are never faced by traditional ERP systems. This study proposes a user behavior monitoring algorithm to monitor unsafe user behavior in Cloud ERP system. UBMA constructs statistical features of normal user behavior by analyzing a large number of normal user behaviors stored in logs. Then, the unsafe user behavior can be identified by comparing the statistical characteristics of the behavior to be detected to the normal behavior.
2.1. Related Definition on Use Behavior Monitoring Model
The user behavior and user behavior sequence are defined as follows.
Definition 1.
User behavior: In Cloud ERP, instructions from users are completed by sending and responding to requests. From the perspective of cyber security, user behavior is defined as a request consisting of six basic fields that can be recognized by computers: timestamp, user identification (ID), target Uniform Resource Locator (URL), command/request name, parameters, and values. This definition clearly delineates the requester, request time, and request content, which can be retrieved in the log of Cloud ERP. User behavior can be described as.
Definition 2.
User behavior sequence: User behavior sequence is a collection of user behaviors. User behavior shows regularity affected by the environment, position, and personal preferences. User behavior sequence is used to analyze user’s behavior habits. User behavior sequence can be depicted as.
2.2. Unsafe User Behavior
External attacks and internal attacks are two main cyberattacks [30,31,32]. This study selects three typical unsafe user behaviors as detection examples, involving acts of ultra vires, information disclosure, and cross-site hacking, as shown in Table 1. This is supplemented by the user behavior monitoring algorithm proposed in this study, which has strong flexibility and allows custom behaviors to be detected.

Table 1.
Three typical unsafe user behaviors.
These three unsafe user behaviors are defined as follows.
Definition 3.
Cross-site hacking: Cross-site scripting attack is currently the most mainstream method used by hackers to attack cloud-server-based applications. Cross-site scripting attack specifically refers to hacktivism where the hacker substitutes a pre-designed fraudulent script for a legal parameter when they access the regular public network service URL of Cloud ERP system and induce the system to run their code [32,33]. Thereby, the Cloud ERP system is hacked, and private information is leaked.
The two feature fields describing cross-site hacking behaviors are values and timestamp. They are selected for the following reasons: (1) Cross-site scripting attacks replace values in request with code, and then the length of the values changes. Therefore, it is possible to determine whether there is a cross-site scripting attack by monitoring the variation of values. (2) Hackers have little information about the client logic of the Cloud ERP system, so they often use one-by-one tests to find fields that can induce suspicious system operating requests. So the timestamp becomes dense and is chosen as another representative field.
Definition 4.
Acts of ultra vires: Ultra vires refer to actions beyond the user’s authority [34,35]. The four feature fields describing ultra vires behaviors are User ID, command/request name, values, and timestamp.
Take checking salary as an example to explain ultra vires behavior. Generally, the human resources (HR) department has the authority to check the salary of employees. A request to view salary from someone other than HR will be considered ultra vires. In the historical log, user ID, network command/request name, values, and timestamp of salary viewing request from HR have certain regularity. In this case, the four most important fields of ultra vires exhibit the following anomalies: (1) The user ID who made the view salary request does not match the user ID in the history log. (2) Although the command/request name is the same as in the historical log, the value does not match the historical value. (3) The time density of requests varies significantly compared to historical data.
Definition 5.
Information disclosure: Information disclosure is manifested as requests for sensitive information that are sent to unusual addresses through the Cloud ERP system [36,37]. The three feature fields describing information disclosure behaviors are target URL, values, and timestamp. The three representative fields of requests for information disclosure behaviors have the following characteristic: (1) The target URL is unusual. (2) There are different types and large quantities of values. (3) Numerous requests are issued in a short period of time.
2.3. User Behavior Monitoring Algorithm Design Based on Dynamic Programming Sequence Comparison
The model proposed in this study identifies unsafe user behaviors in the feature fields by comparing the statistical characteristics of the user behavior sequence with statistical characteristics of the standard behavior sequence.
2.3.1. Statistical Characteristics of Standard User Behavior Sequence
In Cloud ERP system, user demand is completed through the issuance and response of requests, and then, in this study, the requests are used to characterize user behavior. If the total number of requests received and issued by user A within T days is in the normal range, the user behavior is regarded as a safe behavior. Such security behavior in the log is served as the training set of user behavior monitoring algorithm (UBMA). The normal range is based on the historical statistics of a set of users in a given service. Within the range of historical statistics, it is called the normal range.
The request set of all users within T days is where , and is a user request that is characterized by six basic fields defined in Section 2.1. is the request set of all users on a given day t; with m user requests, is identified as being divided into n data subset, and each subset has a of length b based on timestamp order; and b is workload that can be handled by the predefined filter. The collection of user behavior sequences on a given day is , where . and contains b user requests, which is used to represent the behavior sequence.
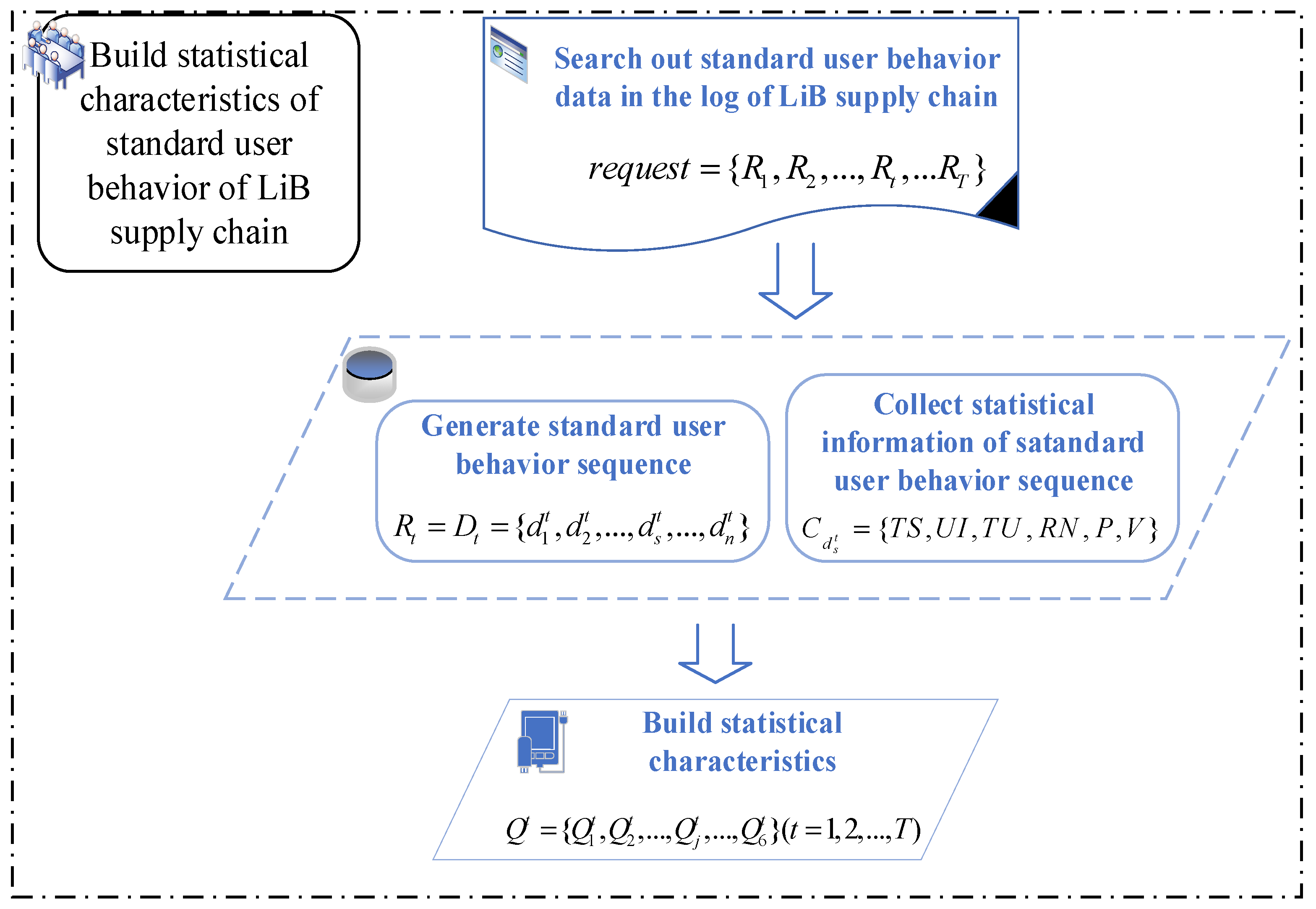
The method of building statistical characteristics of standard user behavior sequence is shown in Figure 1.
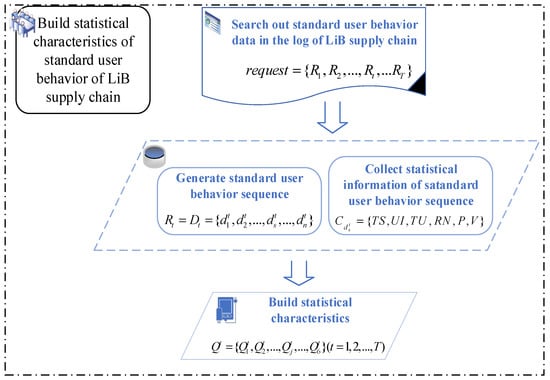
Figure 1.
The flowchart of method for statistical characteristics building.
The details of statistical characteristics building method are summarized as follows.
Step 1: Build a statistical database to record the statistical information in each basic field of a given user’s behavior. The user behavior in the log is divided into behavior sequences of length s according to the order of timestamps. indicates the collection of user behavior sequence. Each user behavior can be described using six basic fields. is used to record statistical information in six basic fields of user behavior , where indicates the timestamp of , indicates the user ID of , indicates the target URL of , indicates the command/request name of , indicates the parameters of , and indicates the average length of parameter value of . is the collection of statistical information in six basic fields of user behavior sequence , where is statistical information in six basic fields of the user behavior sequence, TS indicates occurrences of each timestamp of , UI indicates occurrences of each user ID of , TU indicates occurrences of each target URL of , RN indicates occurrences of each command/request name of , P indicates occurrences of each parameter of , and V indicates occurrences of each parameter value of .
Step 2: The statistical database obtained in step 1 is used as a training data set to complete the construction of statistical features of user behavior in each field. The uniqueness of each user behavior can be described by the statistical characteristics of its six basic fields. The following constructs the statistical characteristics of the six basic fields.
- The calculation of time gap between different requests.
- For the all the user behavior sequences, in T days, with the basic fields statistics being , and the statistical information of Median , standard deviation , and mean value are calculated in each basic field in R.
- Dispersion of a statistical parameter is widely used to measure the degree of data variability, but it cannot describe data concentration. Therefore, in this study, we define the dispersion difference to represent the statistical characteristics of user behavior sequence on day t. The definition is as follows: , where . The statistical characteristics of standard user behavior sequences are calculated through .
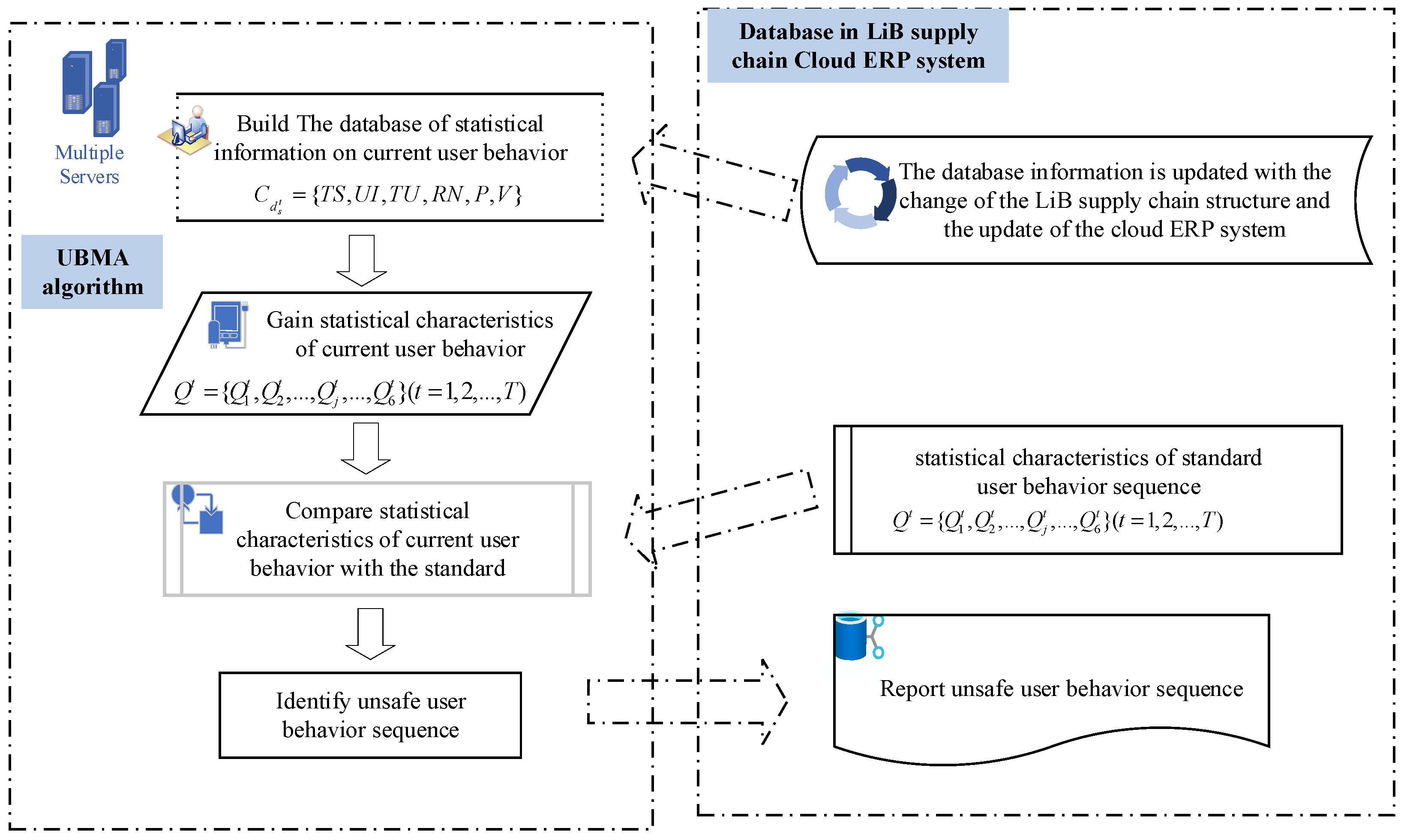
2.3.2. User Behavior Sequence Matching Method Design
UBMA compares the statistical characteristics of the basic fields between the to-be-detected user behavior sequence and the established standard user behavior sequence to check whether the current user behavior is normal. The logic of UBMA is shown in Figure 2.
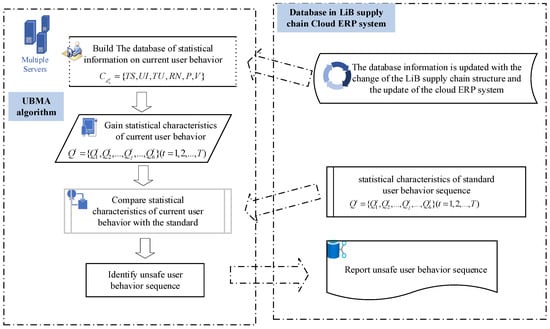
Figure 2.
UBMA algorithm.
The following steps demonstrate the method.
Step 1: Obtain the statistical characteristics of the basic field of the user behavior sequence that is to be detected. For a given behavior sequence , with its statistical information , the user’s statistical characteristics are , where . User behavior is represented by basic fields. Therefore, , where is the statistical characteristics of the jth basic field.
Step 2: Security judgment of to-be-detected user behavior sequence is obtained by comparing the statistical characteristics of each basic field between to-be-detected user behavior sequence and the standard user behavior sequence in the same field (). If , the jth basic field meets the matching conditions; when each basic field in meets the matching condition, it means the action of is safe; when the behavior data (the number of the data is b) in meet the matching condition, it means that matches with the basic field. To make it clear, the pseudo-code in this study is as follows (Algorithm 1).
| Algorithm 1 Pseudo-code of user behavior monitoring algorithm(UBMA) |
| public class ModelVersion1 { |
| public static void main (String [] args) { |
| //User Behavior Type 1: |
| /* |
| * Standard User Behavior Sequence: ABCDEFGGCAD |
| * Current User Behavior Sequence: AKCDOFGGCAD |
| */ |
| float matchScore = 1; |
| float mismatchScore = −1; |
| float indelScore = −1; |
| String sequence1 = “ABCDEFGGCAD”; |
| String sequence2 = “AKCDOFGGCAD”; |
| float [][] computedMatrix = computeMatrix(sequence1, sequence2, matchScore, mismatchScore, indelScore); |
| System.out.println(“User Behavior Type 1\n”); |
| System.out.println(obtainOptimalAlignmentByDownmostOrder (computedMatrix, sequence1, sequence2, matchScore, mismatchScore, indelScore)); |
2.4. UBMA Evaluation
The Cloud ERP system is deployed on the cloud server and provides ERP application services to users via the Internet. Cloud ERP users can access the solution from any Internet-connected device in any location. In addition, the Cloud ERP system provides a new open and ecological enterprise-level service mode for enterprise customer based on the Internet: each enterprise customer uses the Cloud ERP platform to exchange information, share resources, and jointly create value. In this new service model, the information security risk brought by the improper operation of a single user spreads along with the interaction between enterprises. Therefore, frequent interaction among enterprise users not only provides enterprises with new ways to create value but also makes Cloud ERP systems face unprecedented information security issues. UBMA investigates the impact of user behavior on system security in the Cloud ERP system, establishes normal user behavior characteristics by analyzing user behavior data in system logs, and monitors unsafe behavior in the system based on behavior characteristic comparison algorithms.
UBMA uses discriminating and classification algorithms to identify unsafe user behavior. Currently, popular classification algorithms include supervised learning classification algorithms and unsupervised learning classification algorithms. Supervised learning classification algorithm uses a large amount of historical data as training data and establishes a discriminant model by analyzing the characteristics of historical data to predict unknown samples [38,39]. Zhang et al. proposed a novel variational auto-encoder long–short-term memory network–local weighted deep sub-domain adaptation network to analyze the aircraft turbofan engine data set [40]. Unsupervised learning is a machine learning algorithm that automatically classifies input information. Unsupervised learning does not require prior labeling of training data sets [41,42]. Unsupervised learning method is widely adopted in fault diagnosis. Zhang et al. proposed a bearing fault detection approach by adopting unsupervised learning method based on modified denoising autoencoder with self-attention mechanism [43].
Compared with supervised learning and unsupervised learning, the UBMA proposed in this study has the following advantages in solving the problem of identifying unsafe user behavior in the Cloud ERP system: (1) Compared with supervised learning and unsupervised learning, the UBMA model has advantages in feasibility and algorithm accuracy. Supervised learning requires a large amount of safe and unsafe behaviors in the Cloud ERP system as training data to complete the learning process of the classification algorithm. The amount of unsafe user behavior data recorded in the Cloud ERP system log is small, so the accuracy of the trained supervised learning classification algorithm is low. The UBMA model uses a large number of security behaviors in the logs as a training data set and establishes the statistical characteristics of the characteristic fields of standard behaviors as the standard for judging whether user behaviors are abnormal in the UBMA model. The UBMA model does not require abnormal behavior in the system as training data, so, in the actual application process, the UBMA model is more feasible than the supervised learning algorithm. The Cloud ERP system provides a variety of enterprise-level information services to various enterprises, so the requests stored in the Cloud ERP system are quite different.
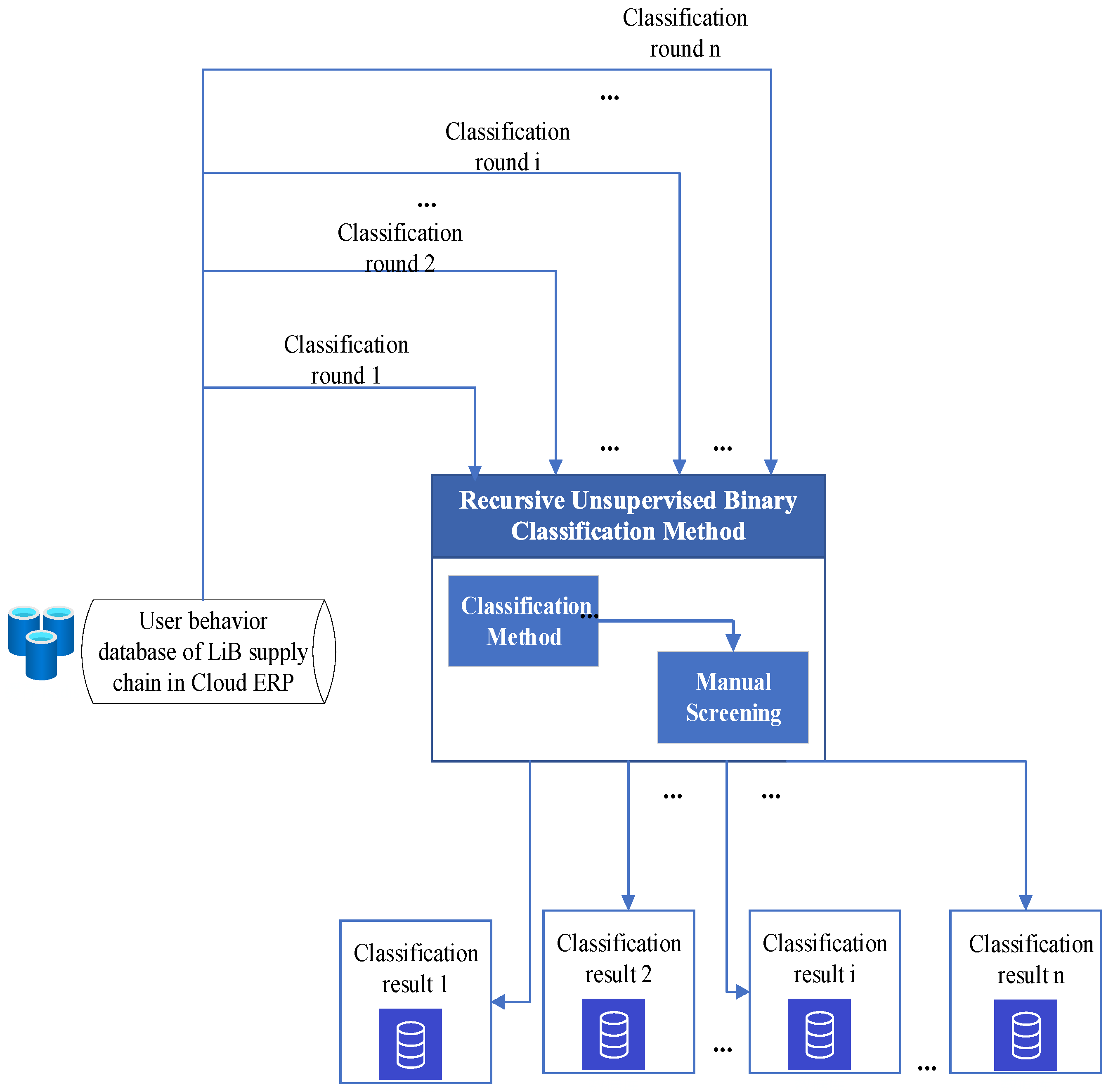
Unsupervised learning algorithms classify requests as binary by computing the difference between requests. Since the difference between requests is not singly reflected in safety, the two behavior categories obtained by the unsupervised learning algorithm include both safe behavior and unsafe behavior. Therefore, compared with unsupervised learning, the recognition accuracy of UBMA model is higher. (2) Compared with the recursive unsupervised binary classification method, the algorithm complexity of the UBMA model is low, and the cost is controllable. The recursive unsupervised binary classification method [44] can identify unsafe user behaviors with the help of manual screening, as shown in Figure 3. In the recursive unsupervised binary classification algorithm, the results need to be scanned or manually screened after each classification that requires a lot of human resources and computing resources, which is not cost effective. In addition, the computational complexity of the UBMA model is low. The UBMA model only needs one comparison to determine where the unsafe behavior occurs. Its computational complexity is . Assuming that the time complexity of manual screening is N, even if the basic K-means classification algorithm is used, the time complexity of the recursive unsupervised binary classification algorithm is , which is far more complicated than in the UBMA model.
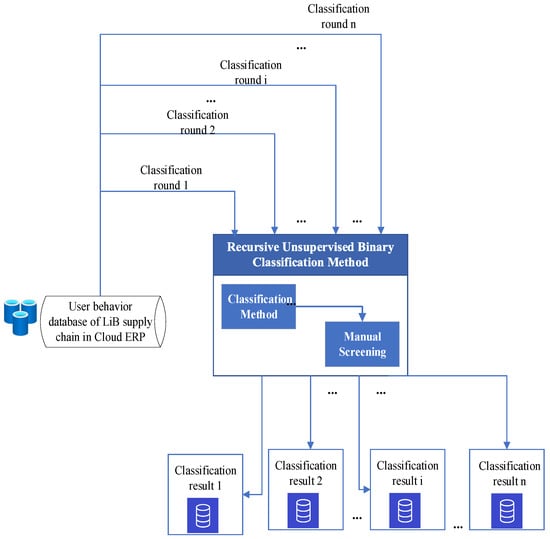
Figure 3.
Process of recursive unsupervised binary classification method.
3. Result and Discussion
3.1. Case Study
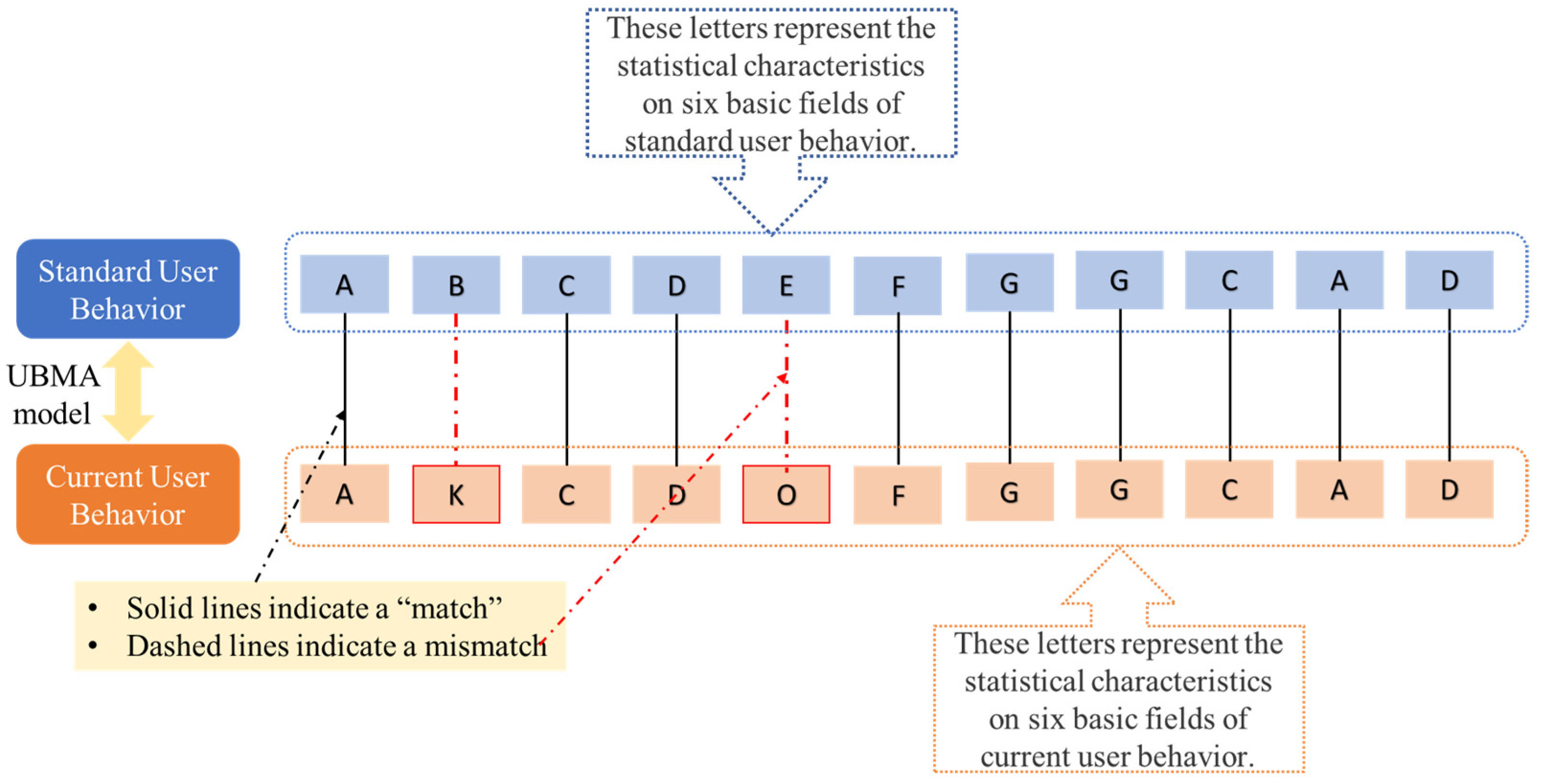
This study takes ultra vires behavior as an example to further explain the UBMA model. The Cloud ERP system often sets up an access to sensitive databases during its service. The case study shows that Li is an important raw material in the production process of the lithium-ion battery, and there are frequent transactions between Li suppliers and manufacturers. The “invoice service system” in the Cloud ERP system provides Li suppliers with transaction record services. Transaction information is a business secret of Li suppliers, and usually only designated staff have the right to view it. When a hacker attacks and successfully accesses the sensitive database by imitating the access frequency of normal users, the ultra vires occurs. The statistical characteristics of the standard user behavior sequence given normal access to the “Invoice Service System” for “Invoicing” operation are expressed as “ABCDEFGGCAD”. By calculating the statistical characteristics of the current user behavior sequence as “AKCDOFGGCAD” and applying the UBMA algorithm, the following results can be obtained. Figure 4 shows the unmatched fields of ultra vires behavior found using UBMA algorithm.
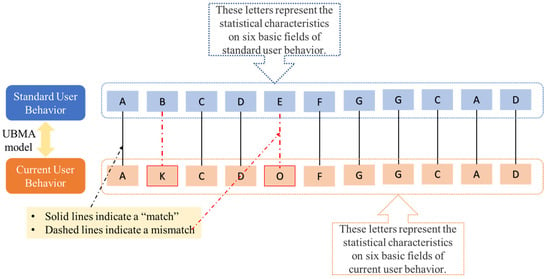
Figure 4.
Case study of ultra vires act. The predefined screening method is a classic data screening method for identifying abnormal data. Since the amount of data that can be processed by the predefined screening method is limited, it cannot be directly used for cloud ERP user behavior monitoring. UBMA is able to identify the sequence of user behaviors including unsafe user behaviors , while b is workload that can be handled by the predefined screening method. Then, predefined screening method can be used to identify the specific unsafe user behavior. Taking the above case study as an example, the UBMA identifies two mismatched user behavior sequences K and O. The user behavior sequences K and O contain the following user behaviors.
The predefined screening method locates unsafe behaviors by filtering the abnormal data in the six basic fields (including timestamp, user ID, target URL, command/request, parameters, and values) in turn. Table 2 shows the transactions between the Li suppliers and lithium-ion battery manufactures recorded in the invoice system. The third timestamp and user ID in sequence K and the fifth timestamp and user ID in sequence O can be determined by using predefined screening. These two unsafe user behaviors (shown in bold in Table 2) can be identified as two unsafe behaviors because a strange user ID visited the “invoice service system” at irregular times. It is reasonable to suspect that hackers have invaded the invoicing system and attempted to steal the transaction data in the “invoice service system”.

Table 2.
User behaviors in user behavior sequences K and O.
Combining the UBMA and predefined screening method can efficiently identify the unsafe user behavior, which reduces the complexity of precisely positioning the unsafe behavior, and provides a reference for the data security operation and maintenance of the Cloud ERP system under the background of big data.
3.2. UBMA Extension
The LiB supply chain is developed dynamically. The supply chain’s members, structure, and demand for information management are changing. The flexibility of the Cloud ERP system is strong, and it supports the replacement and addition of users and functionalities. Cloud ERP can adapt well to the changing demand of the LiB supply chain. The UBMA model proposed in this study compares user behavior sequences based on the Needleman–Wunsch algorithm and accurately locates the difference. The algorithm has strong extensibility and a strong configuration and can adapt well to the changes in users/functionalities, the increase in users/functionalities, and the system structure updates in the ERP system. The corresponding algorithm is extended as follows.
- Algorithm expansion to deal with user/functionality changes: When a service user changes or the functionality of the same category changes (such as a personnel change in the financial department or a version upgrade of the performance evaluation service), the new user/functionality behavior logs are used to replace the old user/functionality behavior logs and re-establish the statistical characteristics of the standard user behavior fields.
- Algorithm expansion to deal with a user/functionality increase: To avoid the impact of the change of dispersion caused by the addition of user/functionality on the judgment results, collect the behavior logs of the user/functionality increase over a period, construct the statistical features of the new standard user behavior sequences, and update the Needleman–Wunsch algorithm. For example, the financial department of the Li supplier adds a new employee H. At this time, the user behavior of H needs to be added to the training set data, and the statistical characteristics of the basic fields of the user behavior need to be relearned, by adding the code to the current Needleman–Wunsch algorithm (Algorithm 2) to exclude the change in the degree of dispersion brought by the new employee H.
- Algorithm expansion for Cloud ERP system update: When the Cloud ERP undergoes structural changes (such as secondary development or a system update), re-record the user behavior of the updated Cloud ERP system and construct the statistical characteristics of the field of the new standard behavior sequence to update the UBMA. During the UBMA update period, the Needleman–Wunsch algorithm is updated to avoid the impact of the dispersion degree changes caused by the addition of users/a functionality increase on the judgment results (similar to the case of a user/functionality increase).
| Algorithm 2 Extended code of Needleman–Wunsch algorithm |
| If the current behavior is the new employee H’s behavior {ignore differences} Else {report detected discrepancies} |
4. Conclusions
Given the ever-growing demand for the LiB, the supply chain of the LiB is expanding, resulting in a repaid flow of materials, products, information, and funds among stakeholders. This leads to the increased complexity of information management in the LiB supply chain. Cloud ERP is an enterprise-level information management software, which has the potential to help enterprises in the LiB supply chain improve their information storage and management. Under the wave of digital transformation, the LiB supply chain needs to improve its operational efficiency, by seeking to promote the Cloud ERP system. However, in the open ecological environment, the frequent multi-user interaction characteristics of Cloud ERP bring sensitive data and private data security issues. This study proposes a UBMA model to monitor Cloud ERP user behavior to protect user privacy in the Cloud ERP system, which is beneficial to the application of Cloud ERP systems in LiB supply chains, and to provide a reference on data security for the adoption of Cloud ERP in LiB supply chain enterprises.
The UBMA model has several advantages for the privacy protection of an LiB supply chain adopting Cloud ERP, compared with mainstream behavior detecting methods involving supervised learning and unsupervised learning and the recursive unsupervised binary classification method. First, compared with the supervised learning method, the UBMA model is more applicable to the characteristics of the user behavior records in the LiB supply chain. Most of the user behavior records in the log are of security behavior. The UBMA method uses security behavior as a training set and constructs the characteristics of the normal user behavior used as the standard user behavior in the Needleman–Wunsch algorithm to detect insecure behaviors. However, supervised learning requires a large number of secure and insecure behaviors to train discriminators with high accuracy. Second, compared to the unsupervised learning method, the UBMA is more accurate in unsecured behavior detection. The use behaviors of LiB enterprises in Cloud ERP vary. Unsupervised learning algorithms classify data as binary by computing the difference between data sets. Since the difference between behaviors is not singly reflected in safety, the two behavior categories obtained by the unsupervised learning algorithm may include both safe behaviors and unsafe behaviors. Third, the UBMA has a lower complexity and lower resource consumption. The recursive unsupervised binary classification method can detect unsafe behaviors with the help of manual screening after each classification. However, the cyclic classification process increases the complexity of the algorithm, and manual screening makes the cost suddenly increase.
The UBMA model has great flexibility that can adapt to changes in the LiB supply chain and Cloud ERP, specifically involving the following situations. First, stakeholders and demands for service change along with business development in the LiB supply chain. To maintain the data security of a changed LiB supply chain, re-establish the statistical characteristics of the standard user behavior fields based on the new user behavior records after user or demand changes. Second, the extension that builds the new standard statistical characteristics of user behavior and updates the previous database of standard statistical characteristics can be used to adapt to the user and demand increases in the LiB supply chain. Third, when Cloud ERP undergoes structural changes (such as secondary development or a system update), re-record the user behavior of the updated Cloud ERP system and construct the statistical characteristics of the field of the new standard behavior sequence to update the UBMA.
This study also has certain limitations. The whole life cycle of data security includes data generation, data encryption, and data cross-domain processing. This study focuses on the security issues caused by user interaction behavior during data transmission after ERP clouding, which belongs to the category of data cross-domain processing. The security of user behavior during data encryption data is also crucial for Cloud ERP system security and deserves further in-depth study in the future.
Author Contributions
Z.W. and Q.S. designed the project. Z.W. performed all the coding and wrote the manuscript. J.W. and B.W. designed the model. Q.S. supervised the work. All authors contributed to the manuscript discussion. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Key Research and Development Program of China (No. 2019YFB1704100).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The availability of data and materials can be requested through Q.S. (qinsu@mail.xjtu.edu.cn).
Acknowledgments
The authors would like to thank the funding agency for the financial support.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kim, T.; Song, W.; Son, D.Y.; Ono, L.K.; Qi, Y. Lithium-ion batteries: Outlook on present, future, and hybridized technologies. J. Mater. Chem. A Mater. 2019, 7, 2942–2964. [Google Scholar]
- Alexander, G.V.; Indu, M.S.; Murugan, R. Review on the critical issues for the realization of all-solid-state lithium metal batteries with garnet electrolyte: Interfacial chemistry, dendrite growth, and critical current densities. Ionics 2021, 27, 4105–4126. [Google Scholar] [CrossRef]
- Shi, C.; Hamann, T.; Takeuchi, S.; Alexander, G.V.; Nolan, A.M.; Limpert, M.; Fu, Z.; O’Neill, J.; Godbey, G.; Dura, J.A.; et al. 3D Asymmetric Bilayer Garnet-Hybridized High-Energy-Density Lithium–Sulfur Batteries. ACS Appl. Mater. Interfaces 2023, 15, 751–760. [Google Scholar] [CrossRef]
- Ivanova, G.; Moreira, A.C. Antecedents of Electric Vehicle Purchase Intention from the Consumer’s Perspective: A Systematic Literature Review. Sustainability 2023, 15, 2878. [Google Scholar] [CrossRef]
- Blomgren, G.E. The Development and Future of Lithium Ion Batteries. J. Electrochem. Soc. 2017, 164, A5019–A5025. [Google Scholar] [CrossRef]
- Li, W.; Rentemeister, M.; Badeda, J.; Jöst, D.; Schulte, D.; Sauer, D.U. Digital twin for battery systems: Cloud battery management system with online state-of-charge and state-of-health estimation. J. Energy Storage 2020, 30, 101557. [Google Scholar] [CrossRef]
- Zhang, J.; Jiang, Y.; Li, X.; Luo, H.; Yin, S.; Kaynak, O. Remaining Useful Life Prediction of Lithium-Ion Battery with Adaptive Noise Estimation and Capacity Regeneration Detection. IEEE/ASME Trans. Mechatron. 2022, 1–12. [Google Scholar] [CrossRef]
- Zhang, J.; Jiang, Y.; Li, X.; Huo, M.; Luo, H.; Yin, S. An adaptive remaining useful life prediction approach for single battery with unlabeled small sample data and parameter uncertainty. Reliab. Eng. Syst. Saf. 2022, 222, 108357. [Google Scholar] [CrossRef]
- Sun, X.; Hao, H.; Hartmann, P.; Liu, Z.; Zhao, F. Supply risks of lithium-ion battery materials: An entire supply chain estimation. Mater. Today Energy 2019, 14, 100347. [Google Scholar] [CrossRef]
- Helbig, C.; Bradshaw, A.M.; Wietschel, L.; Thorenz, A.; Tuma, A. Supply risks associated with lithium-ion battery materials. J. Clean. Prod. 2018, 172, 274–286. [Google Scholar] [CrossRef]
- Christensen, P.A.; Anderson, P.A.; Harper, G.D.; Lambert, S.M.; Mrozik, W.; Rajaeifar, M.A.; Wise, M.S.; Heidrich, O. Risk management over the life cycle of lithium-ion batteries in electric vehicles. Renew. Sustain. Energy Rev. 2021, 148, 111240. [Google Scholar] [CrossRef]
- Olivetti, E.A.; Ceder, G.; Gaustad, G.G.; Fu, X. Lithium-Ion Battery Supply Chain Considerations: Analysis of Potential Bottlenecks in Critical Metals. Joule 2017, 1, 229–243. [Google Scholar]
- Jia, Y.; Li, J.; Yuan, C.; Gao, X.; Yao, W.; Lee, M.; Xu, J. Data-Driven Safety Risk Prediction of Lithium-Ion Battery. Adv. Energy Mater. 2021, 11, 2003868. [Google Scholar] [CrossRef]
- Greenwood, M.; Wentker, M.; Leker, J. A region-specific raw material and lithium-ion battery criticality methodology with an assessment of NMC cathode technology. Appl. Energy 2021, 302, 117512. [Google Scholar] [CrossRef]
- Li, L.; Dababneh, F.; Zhao, J. Cost-effective supply chain for electric vehicle battery remanufacturing. Appl. Energy 2018, 226, 277–286. [Google Scholar] [CrossRef]
- Tosarkani, B.M.; Amin, S.H. A possibilistic solution to configure a battery closed-loop supply chain: Multi-objective approach. Expert Syst. Appl. 2018, 92, 12–26. [Google Scholar] [CrossRef]
- Schultmann, F.; Engels, B.; Rentz, O. Closed-Loop Supply Chains for Spent Batteries. Interfaces 2003, 33, 57–71. [Google Scholar] [CrossRef]
- Gu, X.; Zhou, L.; Huang, H.; Shi, X.; Ieromonachou, P. Electric vehicle battery secondary use under government subsidy: A closed-loop supply chain perspective. Int. J. Prod. Econ. 2021, 234, 108035. [Google Scholar] [CrossRef]
- Kurz, L.; Forster, S.; Wörner, R.; Reichert, F. Environmental Impacts of Specific Recyclates in European Battery Regulatory-Compliant Lithium-Ion Cell Manufacturing. Sustainability 2023, 15, 103. [Google Scholar] [CrossRef]
- Lopez, A.B.; Vatanparvar, K.; Nath, A.P.D.; Yang, S.; Bhunia, S.; Al Faruque, M.A. A Security Perspective on Battery Systems of the Internet of Things. J. Hardw. Syst. Secur. 2017, 1, 188–199. [Google Scholar] [CrossRef]
- Wang, Z.-J.; Sun, Y.-Y.; Chen, Z.; Feng, G.; Su, Q. Optimal versioning strategy of enterprise software considering the customer cost-acceptance level. Kybernetes 2021. [Google Scholar] [CrossRef]
- Sun, Y.; Dang, C.; Feng, G. Optimal versioning strategies for software firms in the competitive environment. Int. J. Prod. Res. 2021, 59, 6881–6897. [Google Scholar] [CrossRef]
- Hosseini, P.; Sebastian, A.; Papandreou, N.; Wright, C.D.; Bhaskaran, H. Accumulation-based computing using phase-change memories with FET access devices. IEEE Electron. Device Lett. 2015, 36, 975–977. [Google Scholar] [CrossRef]
- Kiadehi, E.F.; Mohammadi, S. Cloud ERP: Implementation of Enterprise Resource Planning Using Cloud Computing Technology. J. Basic Appl. Sci. Res. 2012, 2, 11422–11427. [Google Scholar]
- Saa, P.; Moscoso-Zea, O.; Luján-Mora, S. Data Security Issues in Cloud-Based Software-as-a-Service ERP; Andrés Cueva Costales DGPCTI Public Company Yachay: Quito, Ecuador, 2017. [Google Scholar]
- Elmonem, M.A.A.; Nasr, E.S.; Geith, M.H. Benefits and challenges of cloud ERP systems—A systematic literature review. Future Comput. Inform. J. 2016, 1, 1–9. [Google Scholar] [CrossRef]
- von Solms, R.; van Niekerk, J. From information security to cyber security. Comput. Secur. 2013, 38, 97–102. [Google Scholar] [CrossRef]
- Ingham, K.; Forrest, S.; Fe, S. Network Firewalls. IEEE Commun. Mag. 1994, 32, 50–57. [Google Scholar]
- Thakur, K.; Qiu, M.; Gai, K.; Ali, M.L. An Investigation on Cyber Security Threats and Security Models. In Proceedings of the 2nd IEEE International Conference on Cyber Security and Cloud Computing, CSCloud 2015—IEEE International Symposium of Smart Cloud, IEEE SSC 2015, New York, NY, USA, 2–5 November 2015; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2016; pp. 307–311. [Google Scholar]
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-attack modeling analysis techniques: An overview. In Proceedings of the 2016 4th International Conference on Future Internet of Things and Cloud Workshops, W-FiCloud 2016, Vienna, Austria, 22–24 August 2016; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2016; pp. 69–76. [Google Scholar]
- Huang, K.; Siegel, M.; Madnick, S. Systematically understanding the cyber attack business: A survey. ACM Comput. Surv. 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Nithya, V.; Pandian, S.L.; Malarvizhi, C. A survey on detection and prevention of cross-site scripting attack. Int. J. Secur. Its Appl. 2015, 9, 139–152. [Google Scholar] [CrossRef]
- Shanmugam, J.; Ponnavaikko, M. Cross Site Scripting-Latest developments and solutions: A survey. Int. J. Open Problems Compt. Math. 2008, 1, 101–121. [Google Scholar]
- Bast, J. Special Issue The OMT Decision of the German Federal Constitutional Court Don’t Act Beyond Your Powers: The Perils and Pitfalls of the German Constitutional Court’s Ultra Vires Review. Ger. Law J. 2014, 15, 167–181. [Google Scholar]
- Osieke, E. The Legal Validity of Ultra Vires Decisions of International Organizations. Am. J. Int. Law 1983, 77, 239–256. [Google Scholar]
- Gao, L.; Calderon, T.G.; Tang, F. Public companies’ cybersecurity risk disclosures. Int. J. Account. Inf. Syst. 2020, 38, 100468. [Google Scholar] [CrossRef]
- Tang, M.; Alazab, M.; Luo, Y. Big data for cybersecurity: Vulnerability disclosure trends and dependencies. IEEE Trans. Big Data 2019, 5, 635–647. [Google Scholar] [CrossRef]
- Caruana, R. An Empirical Comparison of Supervised Learning Algorithms. In Proceedings of the 23rd International Conference on Machine Learning; Association for Computing Machinery: New York, NY, USA, 2006. [Google Scholar]
- Riedmiller, M. Advanced supervised learning in multi-layer perceptrons-from backpropagation to adaptive learning algorithms. Comput. Stand. Interfaces 1994, 16, 265–278. [Google Scholar]
- Zhang, J.; Li, X.; Tian, J.; Jiang, Y.; Luo, H.; Yin, S. A variational local weighted deep sub-domain adaptation network for remaining useful life prediction facing cross-domain condition. Reliab. Eng. Syst. Saf. 2023, 231, 108986. [Google Scholar] [CrossRef]
- Celebi, M.E.; Aydin, K. Unsupervised Learning Algorithms; Springer: Cham, Switzerland, 2016. [Google Scholar]
- Ghahramani, Z. Unsupervised learning. In Advanced Lectures on Machine Learning: ML Summer Schools 2003, Canberra, Australia, February 2–14, 2003, Tübingen, Germany, August 4–16, 2003, Revised Lectures; Springer: Berlin/Heidelberg, Germany, 2011; pp. 72–112. [Google Scholar]
- Zhang, J.; Zhang, K.; An, Y.; Luo, H.; Yin, S. An Integrated Multitasking Intelligent Bearing Fault Diagnosis Scheme Based on Representation Learning Under Imbalanced Sample Condition. IEEE Trans. Neural Netw. Learn Syst. 2023, 1–12. [Google Scholar] [CrossRef]
- Tarawneh, A.S.; Hassanat, A.B.; Elkhadiri, I.; Chetverikov, D.; Alrashidi, M. K-Means Tree for Fast Furthest Neighbor Approximation. In Proceedings of the 16th International Computer Engineering Conference, ICENCO 2020, Cairo, Egypt, 29–30 December 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020; pp. 77–82. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).