User Privacy Awareness, Incentive and Data Supply Chain Pricing Strategy
Abstract
:1. Introduction
2. Theoretical Background
2.1. Data Supply Chain
2.2. Data Privacy, Privacy Awareness and Data Protection
2.3. Data Awareness and Data Incentive
2.4. Pricing Model
3. Model
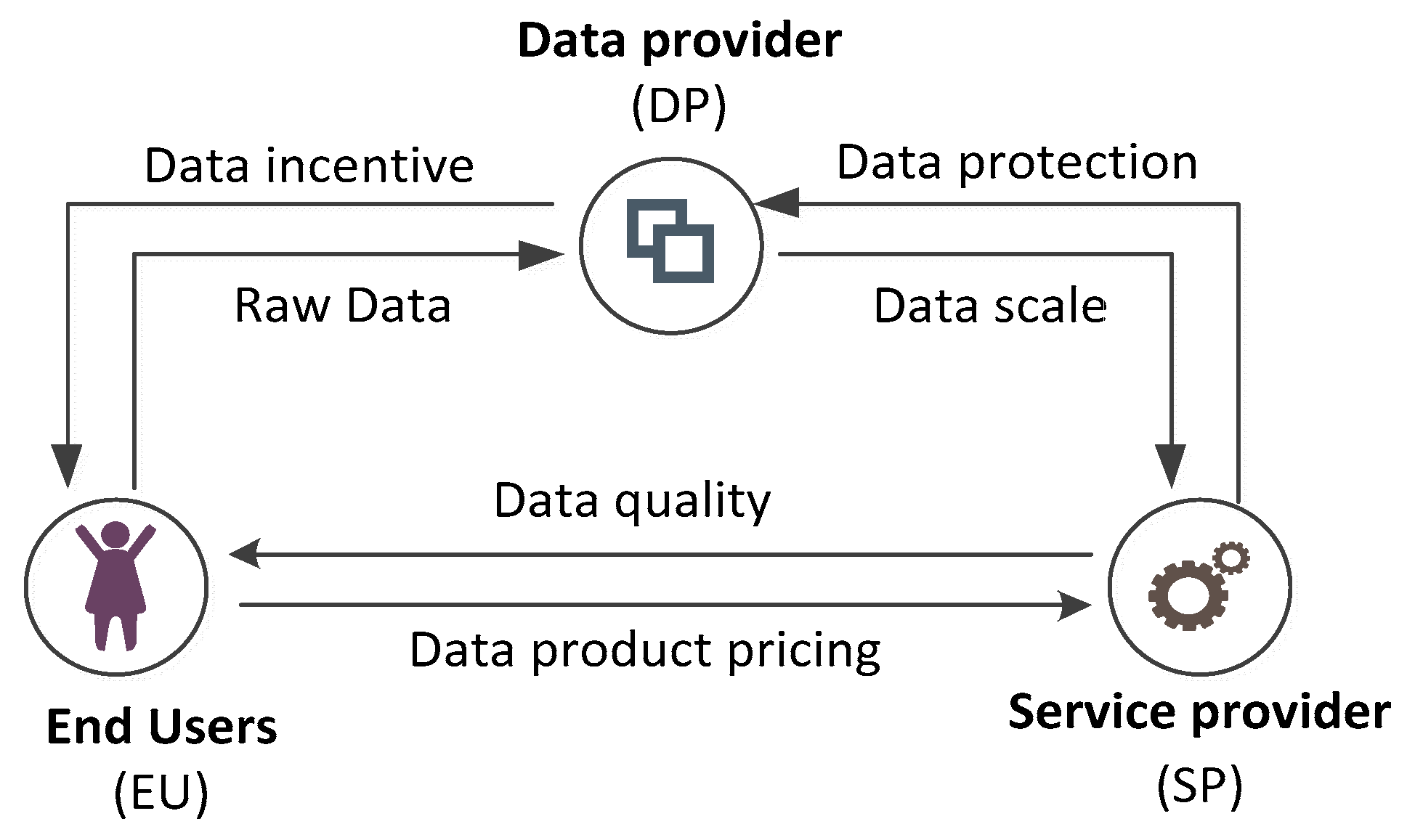
3.1. Problem Description
3.2. Transaction Process of Data Supply Chain
3.2.1. Data Privacy, Privacy Awareness, and Data Collection
3.2.2. Data Transaction Process
3.2.3. Data Product Supply Process
4. Pricing Mechanism of Data Supply Chain
4.1. Analysis of Centralized Pricing Model
4.1.1. Data Product Pricing in Centralized Pricing Model
4.1.2. Total Supply Chain Profit of Centralized Pricing Model
4.2. Analysis of Decentralized Pricing Model
4.2.1. Data Product Pricing in Decentralized Pricing Model
4.2.2. Analysis of DP, SP Profit of Decentralized Pricing Model
4.2.3. Consumer Surplus in Decentralized Pricing Model
4.3. Analysis of Revenue Sharing Pricing Model
4.3.1. Data Product Pricing in the Revenue Sharing Model
4.3.2. Profit Analysis of DP and SP in the Revenue-Sharing Model
5. Numerical Experiments
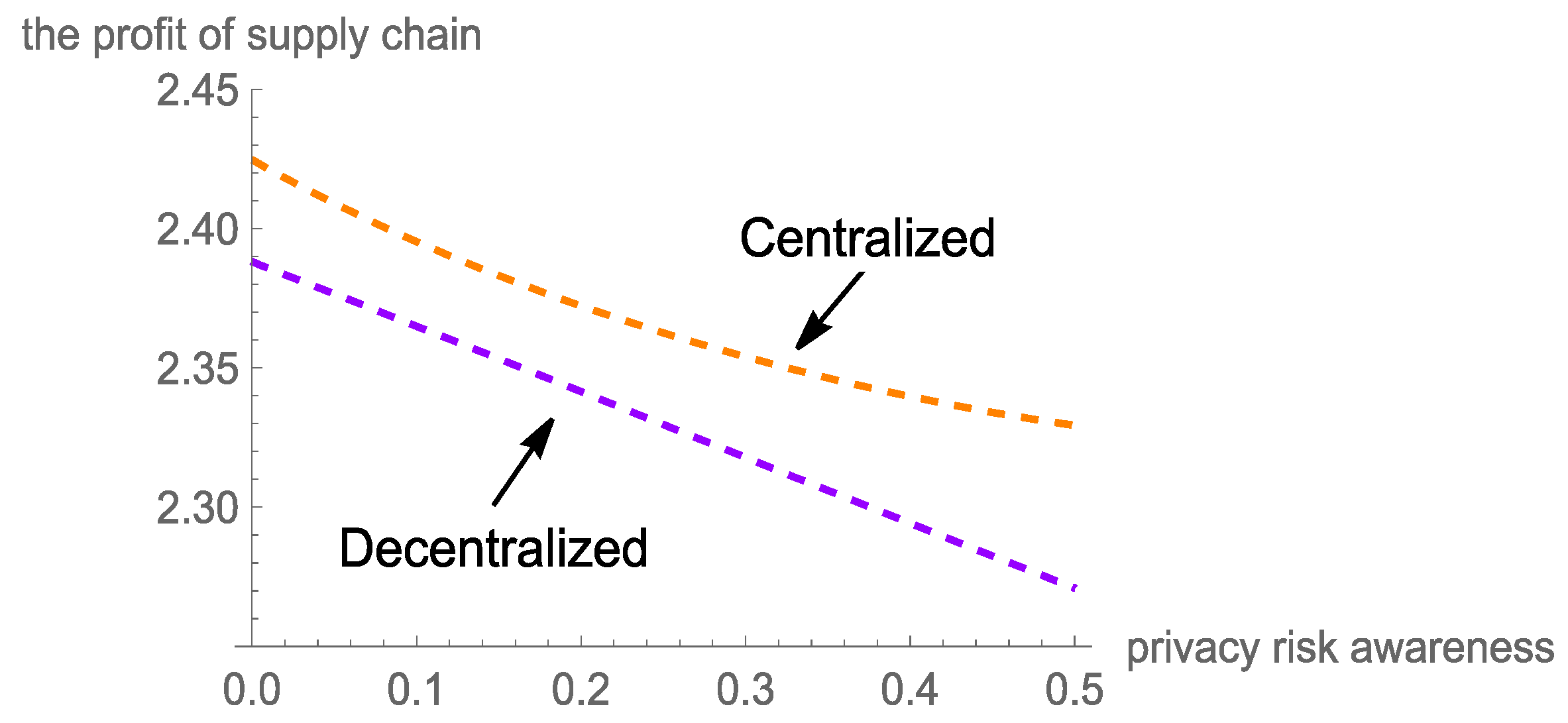
5.1. Analysis of Total Profit of Data Supply Chain
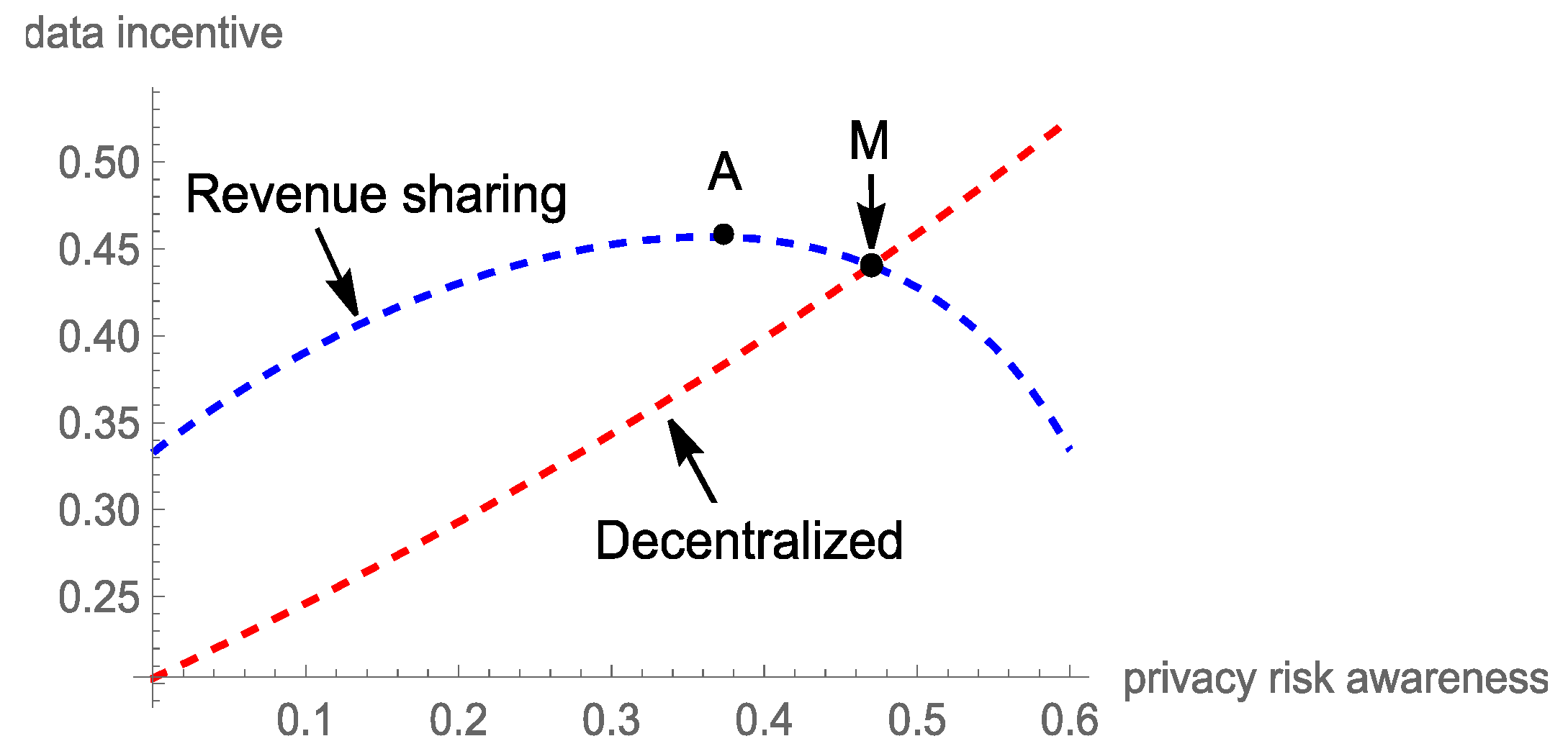
5.2. Analysis of Data Incentive
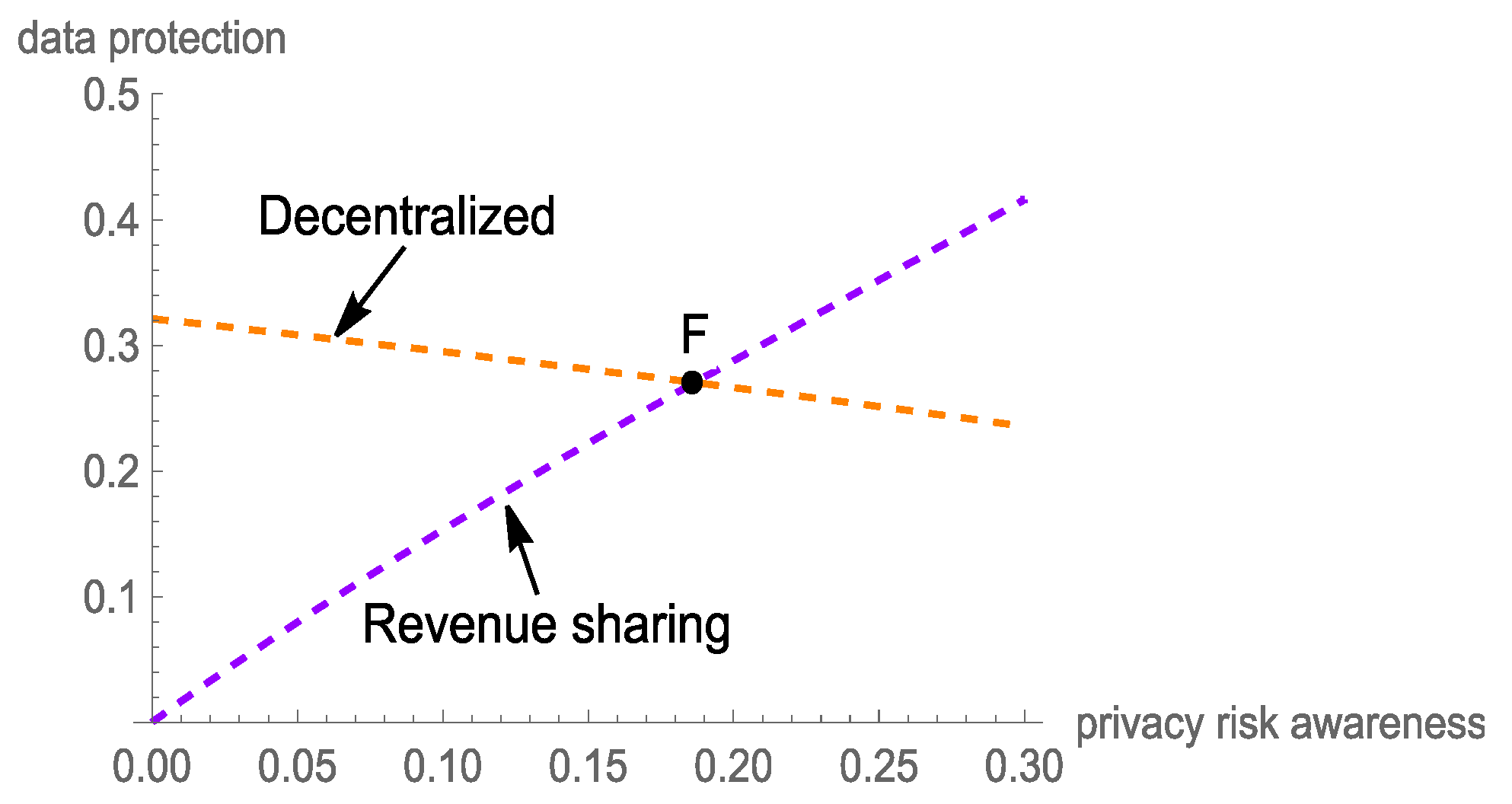
5.3. Analysis of Data Protection
5.4. Analysis of Data Product Price
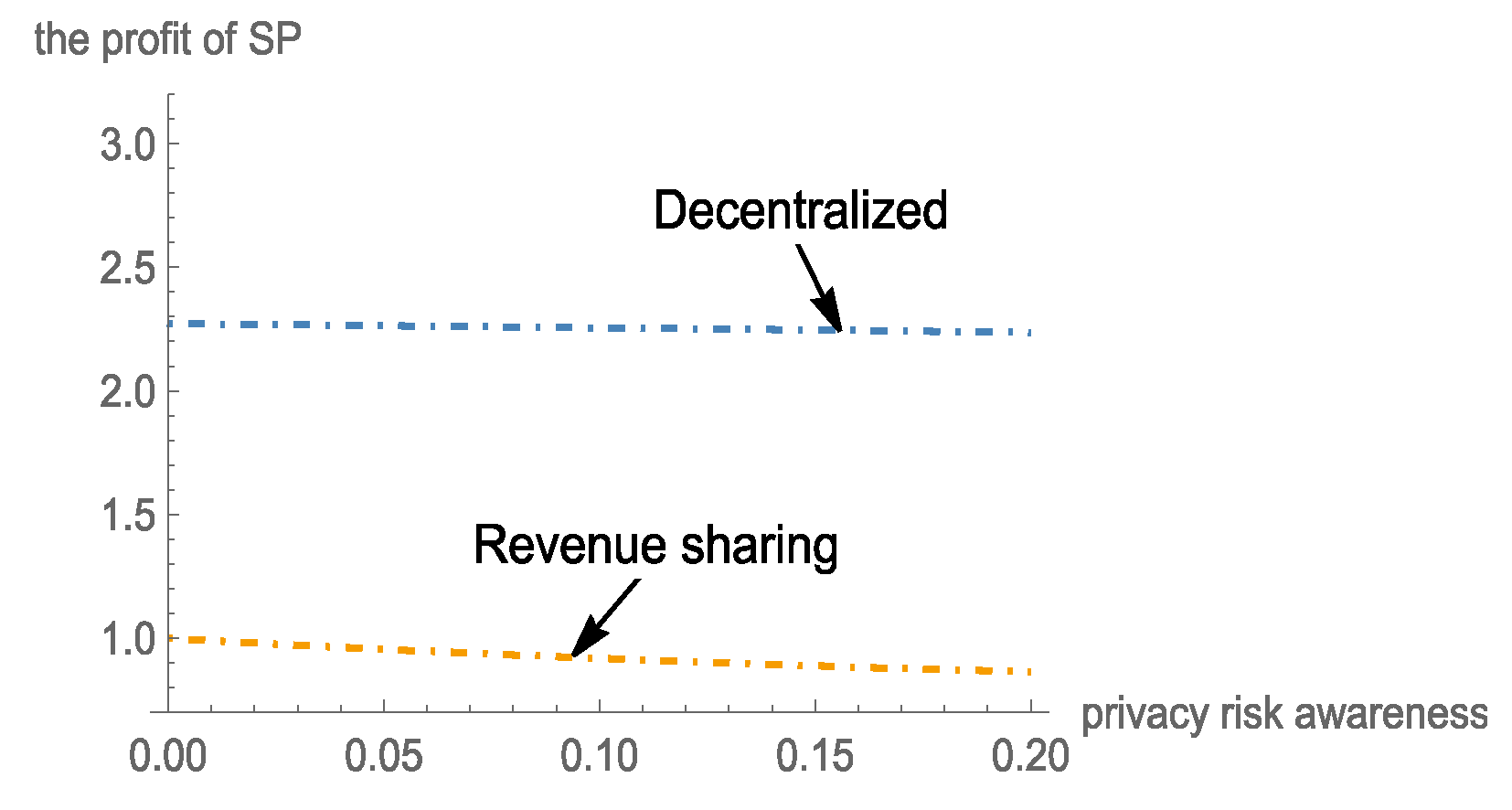
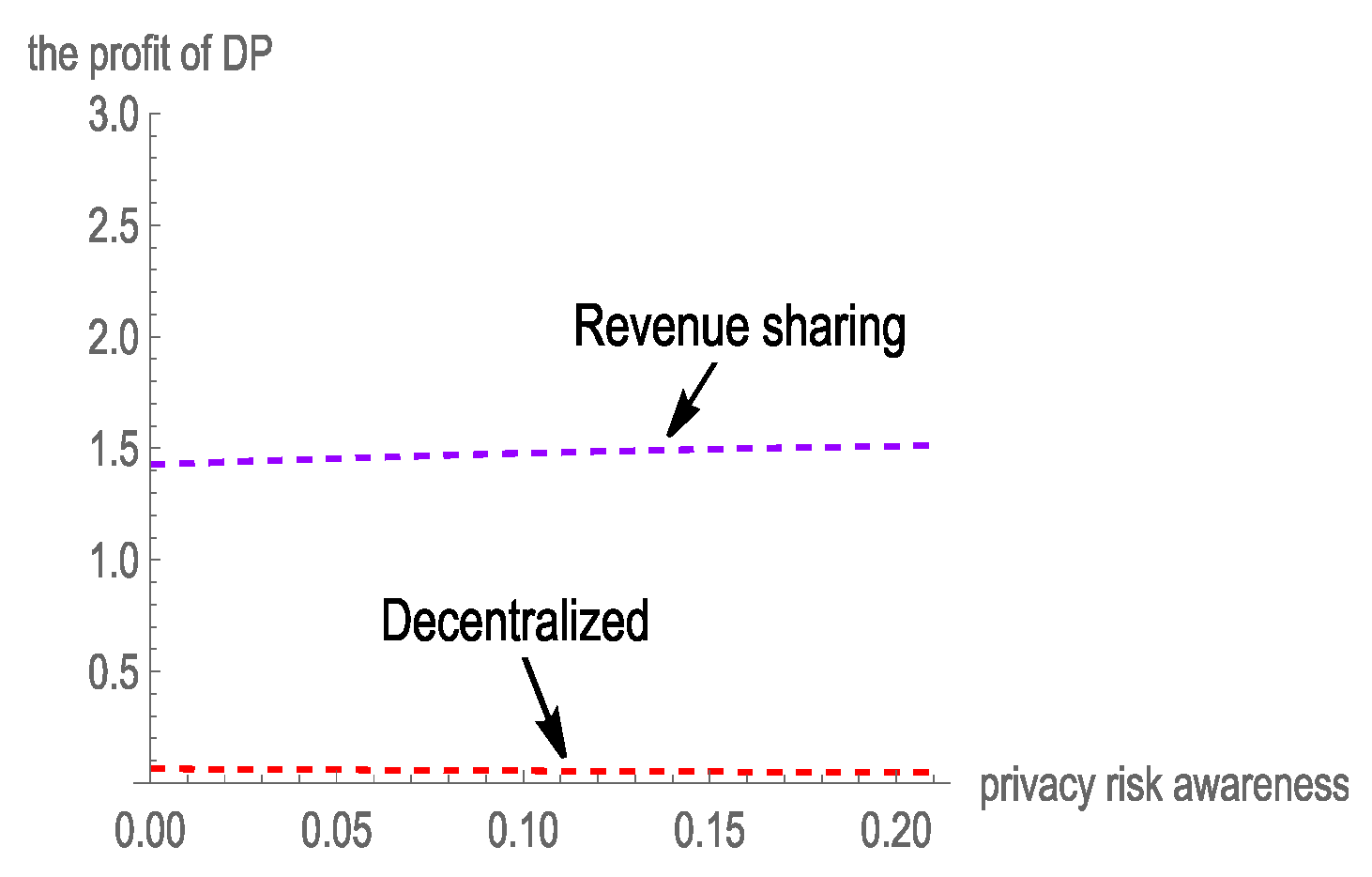
5.5. Analysis of the Profit of SP and DP
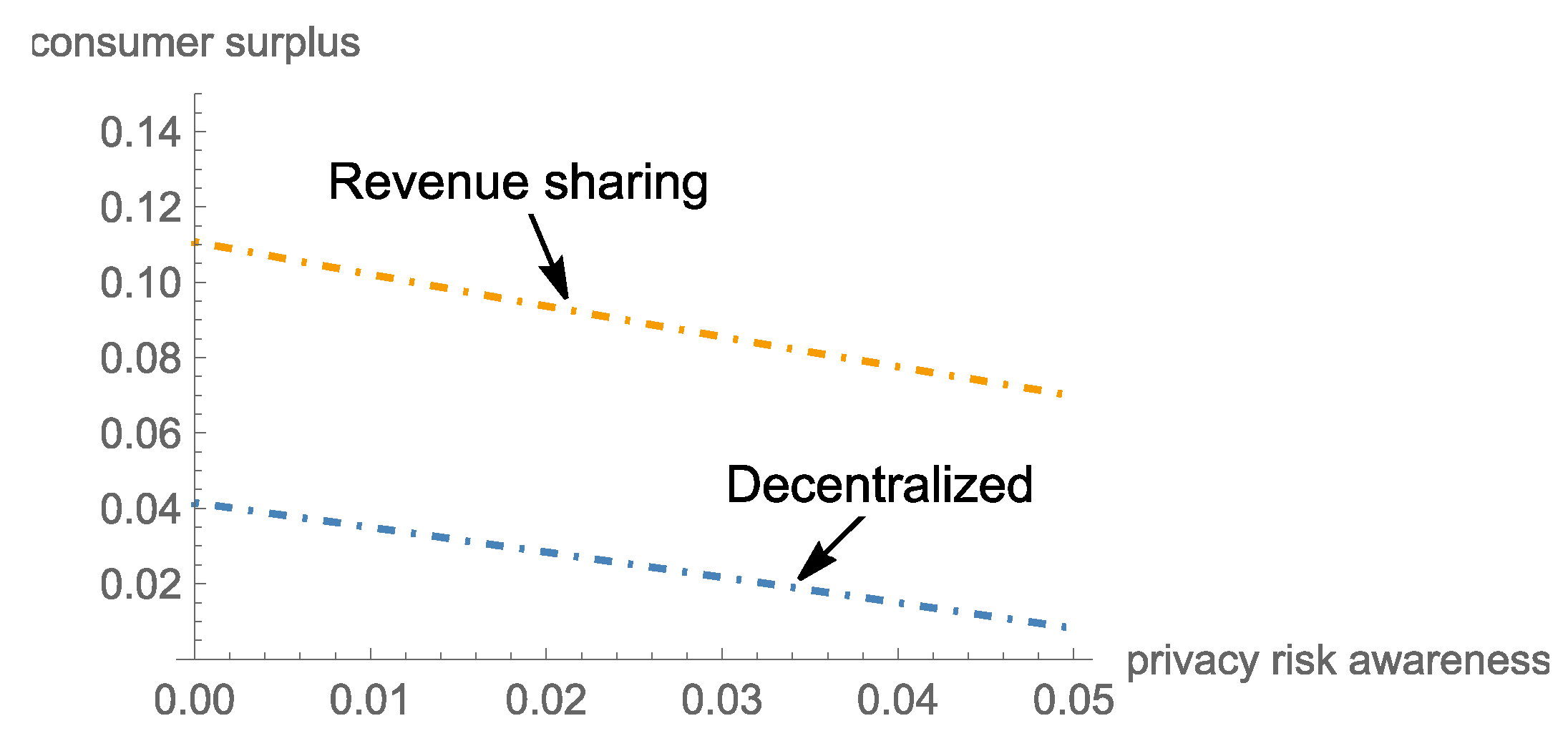
5.6. Analysis of Consumer Surplus
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
Appendix C
References
- Graef, I.; Krasteva, G.; Petročnik, T. Response to the European Commission’s Public Consultation ‘A European Strategy for Data’. 2020. Available online: https://ssrn.com/abstract=3635368 (accessed on 17 July 2020).
- Casadesus-Masanell, R.; Hervas-Drane, A. Competing with Privacy. Manag. Sci. 2015, 61, 229–246. [Google Scholar] [CrossRef]
- Malgieri, G.; Custers, B. Pricing privacy—The right to know the value of your personal data. Comput. Law Secur. Rev. 2018, 34, 289–303. [Google Scholar] [CrossRef]
- Ichihashi, S. Competing data intermediaries. RAND J. Econ. 2021, 52, 515–537. [Google Scholar] [CrossRef]
- Mišić, V.V.; Perakis, G. Data Analytics in Operations Management: A Review. Manuf. Serv. Oper. Manag. 2019, 22, 158–169. [Google Scholar] [CrossRef]
- Spiekermann, S.; Acquisti, A.; Böhme, R.; Hui, K.-L. The challenges of personal data markets and privacy. Electron Mark. 2015, 25, 161–167. [Google Scholar] [CrossRef]
- Spiekermann, M. Data Marketplaces: Trends and Monetisation of Data Goods. Intereconomics 2019, 54, 208–216. [Google Scholar] [CrossRef]
- Choi, J.P.; Jeon, D.-S.; Kim, B.-C. Privacy and personal data collection with information externalities. J. Public Econ. 2019, 173, 113–124. [Google Scholar] [CrossRef]
- Parra-Arnau, J. Optimized, direct sale of privacy in personal data marketplaces. Inf. Sci. 2018, 424, 354–384. [Google Scholar] [CrossRef]
- Shen, Y.; Guo, B.; Shen, Y.; Duan, X.; Dong, X.; Zhang, H. A Pricing Model for Big Personal Data. Tsinghua Sci. Technol. 2016, 21, 482–490. [Google Scholar] [CrossRef]
- Gkatzelis, V.; Aperjis, C.; Huberman, B.A. Pricing private data. Electron. Mark. 2015, 25, 109–123. [Google Scholar] [CrossRef]
- Li, X.-B.; Liu, X.; Motiwalla, L. Valuing Personal Data with Privacy Consideration. Decis. Sci. 2021, 52, 393–426. [Google Scholar] [CrossRef] [PubMed]
- Ghosh, A.; Roth, A. Selling privacy at auction. Games Econ. Behav. 2015, 91, 334–346. [Google Scholar] [CrossRef]
- Bergman, R.; Abbas, A.E.; Jung, S.; Werker, C.; de Reuver, M. Business model archetypes for data marketplaces in the automotive industry. Electron. Mark. 2022, 32, 747–765. [Google Scholar] [CrossRef]
- Zhang, Z.; Ren, D.; Lan, Y.; Yang, S. Price competition and blockchain adoption in retailing markets. Eur. J. Oper. Res. 2022, 300, 647–660. [Google Scholar] [CrossRef]
- Xu, Z.; Dukes, A. Personalization from Customer Data Aggregation Using List Price. Manag. Sci. 2021, 68, 960–980. [Google Scholar] [CrossRef]
- Hoffmann, F.; Inderst, R.; Ottaviani, M. Persuasion Through Selective Disclosure: Implications for Marketing, Campaigning, and Privacy Regulation. Manag. Sci. 2020, 66, 4958–4979. [Google Scholar] [CrossRef]
- Van Ooijen, I.; Vrabec, H.U. Does the GDPR Enhance Consumers’ Control over Personal Data? An Analysis from a Behavioural Perspective. J. Consum. Policy 2019, 42, 91–107. [Google Scholar] [CrossRef]
- Kumar, R.; Gopal, R.; Garfinkel, R. Freedom of Privacy: Anonymous Data Collection with Respondent-Defined Privacy Protection. Oper. Res. 2010, 22, 471–481. [Google Scholar] [CrossRef]
- Schomakers, E.-M.; Lidynia, C.; Ziefle, M. All of me? Users’ preferences for privacy-preserving data markets and the importance of anonymity. Electron. Mark. 2020, 30, 649–665. [Google Scholar] [CrossRef]
- Jia, J.; Jin, G.Z.; Wagman, L. The Short-Run Effects of the General Data Protection Regulation on Technology Venture Investment. Mark. Sci. 2021, 40, 661–684. [Google Scholar] [CrossRef]
- Xu, L.; Jiang, C.; Chen, Y.; Ren, Y.; Liu, K.J.R. Privacy or Utility in Data Collection? A Contract Theoretic Approach. IEEE J. Sel. Top. Signal Process. 2015, 9, 1256–1269. [Google Scholar] [CrossRef]
- Zhang, Z.; He, S.; Chen, J.; Zhang, J. REAP: An Efficient Incentive Mechanism for Reconciling Aggregation Accuracy and Individual Privacy in Crowdsensing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2995–3007. [Google Scholar] [CrossRef]
- Cong, Z.; Luo, X.; Pei, J.; Zhu, F.; Zhang, Y. Data pricing in machine learning pipelines. Knowl. Inf. Syst. 2022, 64, 1417–1455. [Google Scholar] [CrossRef]
- Kummer, M.; Schulte, P. When Private Information Settles the Bill: Money and Privacy in Google’s Market for Smartphone Applications. Manag. Sci. 2019, 65, 3470–3494. [Google Scholar] [CrossRef]
- Bataineh, A.S.; Mizouni, R.; Barachi, M.E.; Bentahar, J. Monetizing Personal Data: A Two-Sided Market Approach. Procedia Comput. Sci. 2016, 83, 472–479. [Google Scholar] [CrossRef]
- Niu, C.; Zheng, Z.; Wu, F.; Tang, S.; Chen, G. Online Pricing With Reserve Price Constraint for Personal Data Markets. IEEE Trans. Knowl. Data Eng. 2022, 34, 1928–1943. [Google Scholar] [CrossRef]
- Wu, D.; Baron, O.; Berman, O. Bargaining in competing supply chains with uncertainty. Eur. J. Oper. Res. 2009, 197, 548–556. [Google Scholar] [CrossRef]
- Wu, P.F.; Vitak, J.; Zimmer, M.T. A contextual approach to information privacy research. J. Assoc. Inf. Sci. Technol. 2020, 71, 485–490. [Google Scholar] [CrossRef]
- Martin, K. Privacy Notices as Tabula Rasa: An Empirical Investigation into How Complying with a Privacy Notice Is Related to Meeting Privacy Expectations Online. J. Public Policy Mark. 2015, 34, 210–227. [Google Scholar] [CrossRef]
- Inman, J.J.; Nikolova, H. Shopper-Facing Retail Technology: A Retailer Adoption Decision Framework Incorporating Shopper Attitudes and Privacy Concerns. J. Retail. 2017, 93, 7–28. [Google Scholar] [CrossRef]
- Wang, M.; Jiang, Z.; Zhang, Y.; Yang, H. T-Closeness Slicing: A New Privacy-Preserving Approach for Transactional Data Publishing. INFORMS J. Comput. 2018, 30, 438–453. [Google Scholar] [CrossRef]
- Cai, N.; Kou, S. Econometrics with Privacy Preservation. Oper. Res. 2019, 67, 905–926. [Google Scholar] [CrossRef]
- Cuzzocrea, A.; Leung, C.K.; Olawoyin, A.M.; Fadda, E. Supporting Privacy-Preserving Big Data Analytics on Temporal Open Big Data. Procedia Comput. Sci. 2022, 198, 112–121. [Google Scholar] [CrossRef]
- Guarino, A.; Lettieri, N.; Malandrino, D.; Zaccagnino, R. A machine learning-based approach to identify unlawful practices in online terms of service: Analysis, implementation and evaluation. Neural Comput. Appl. 2021, 33, 17569–17587. [Google Scholar] [CrossRef]
- Valletti, T.; Wu, J. Consumer Profiling with Data Requirements: Structure and Policy Implications. Prod. Oper. Manag. 2020, 29, 309–329. [Google Scholar] [CrossRef]
- Conitzer, V.; Taylor, C.R.; Wagman, L. Hide and Seek: Costly Consumer Privacy in a Market with Repeat Purchases. Mark. Sci. 2012, 31, 277–292. [Google Scholar] [CrossRef]
- Tsai, J.Y.; Egelman, S.; Cranor, L.; Acquisti, A. The Effect of Online Privacy Information on Purchasing Behavior: An Experimental Study. Inf. Syst. Res. 2010, 22, 254–268. [Google Scholar] [CrossRef]
- Koh, B.; Raghunathan, S.; Nault, B.R. Is Voluntary Profiling Welfare Enhancing? MIS Q. 2017, 41, 23–41. [Google Scholar] [CrossRef]
- Wang, D.; Wang, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Guarino, A.; Malandrino, D.; Zaccagnino, R. An automatic mechanism to provide privacy awareness and control over unwittingly dissemination of online private information. Comput. Netw. 2022, 202, 108614. [Google Scholar] [CrossRef]
- Li, X.-B.; Raghunathan, S. Pricing and disseminating customer data with privacy awareness. Decis. Support Syst. 2014, 59, 63–73. [Google Scholar] [CrossRef] [PubMed]
- Elvy, S.-A. Paying for privacy and the personal data economy. Columbia Law Rev. 2017, 117, 1369–1459. [Google Scholar]
- Johnson, G.A.; Shriver, S.K.; Du, S. Consumer Privacy Choice in Online Advertising: Who Opts Out and at What Cost to Industry? Mark. Sci. 2020, 39, 33–51. [Google Scholar] [CrossRef]
- Rafieian, O.; Yoganarasimhan, H. Targeting and Privacy in Mobile Advertising. Mark. Sci. 2020, 40, 193–218. [Google Scholar] [CrossRef]
- Zuiderveen Borgesius, F.; Poort, J. Online Price Discrimination and EU Data Privacy Law. J. Consum. Policy 2017, 40, 347–366. [Google Scholar] [CrossRef]
- Montes, R.; Sand-Zantman, W.; Valletti, T. The Value of Personal Information in Online Markets with Endogenous Privacy. Manag. Sci. 2018, 65, 1342–1362. [Google Scholar] [CrossRef]
- Guan, X.; Chen, Y.-J. The Interplay between Information Acquisition and Quality Disclosure. Prod. Oper. Manag. 2017, 26, 389–408. [Google Scholar] [CrossRef]
- Smith, H.J.; Dinev, T.; Xu, H. Information Privacy Research: An Interdisciplinary Review. MIS Q. 2011, 35, 989–1015. [Google Scholar] [CrossRef]
- Li, C.; Li, D.Y.; Miklau, G.; Suciu, D. A Theory of Pricing Private Data. ACM Trans. Database Syst. 2014, 39, 1–28. [Google Scholar] [CrossRef]
- Fainmesser, I.P.; Galeotti, A.; Momot, R. Digital Privacy. Manag. Sci. 2022. [Google Scholar] [CrossRef]
- Karimi Adl, R.; Askari, M.; Barker, K.; Safavi-Naini, R. Privacy Consensus in Anonymization Systems via Game Theory. In Proceedings of the Data and Applications Security and Privacy XXVI: 26th Annual IFIP WG 11.3 Conference, Paris, France, 11–13 July 2012; pp. 74–89. [Google Scholar]
- Nget, R.; Cao, Y.; Yoshikawa, M. How to Balance Privacy and Money through Pricing Mechanism in Personal Data Market. arXiv 2017, arXiv:1705.02982. [Google Scholar]
- Rahmani, S.; Haeri, A.; Hosseini-Motlagh, S.-M. Proposing channel coordination and horizontal cooperation in two competitive three-echelon reverse supply chains. Int. Trans. Oper. Res. 2020, 27, 1447–1477. [Google Scholar] [CrossRef]
- Yang, J.; Xing, C. Personal Data Market Optimization Pricing Model Based on Privacy Level. Information 2019, 10, 123. [Google Scholar] [CrossRef]

| Theme | References | Similarities | Differences |
|---|---|---|---|
| Data privacy | Smith et al. [49] | Data pricing; Data value | Theoretical analysis We use a mathematical model. |
| Data compensation | Kummer et al. [25] | Data incentive; Data protection | Emphasis on platform use and data collection Similar to the first stage of our paper. |
| Montes et al. [47] | Personal information | Endogenous privacy and price discrimination We develop data product. | |
| Data collection | Johnson et al. [44] | Data value; privacy concerns | Targeted advertising We are dealing with the data. |
| Rafieian, O. and H. Yoganarasimhan [45] | Data value; Consumer privacy; Use of data | ||
| Zuiderveen Borgesius, F. and J. Poort [46] | Price discrimination We develop data product and then sale. | ||
| Privacy preferences | Guan et al. [48] | Data collection Data quality | Conjoint analysis Empirical research |
| Data incentive | Zhang et al. [23] | Data privacy Data incentive | Computer algorithm |
| Li et al. [50] | Data incentive and data scale | Data collection stage Our research covers the whole stage from data generation to transaction. |
| Symbol | Descriptions |
|---|---|
| User’s privacy risk awareness | |
| The price factor for SP to buy a unit of data from DP | |
| The cost coefficient of data protection | |
| The cost of data product development | |
| Wholesale price for SP to buy a unit of data from DP | |
| Scale of raw data obtained by DP from EU | |
| Quality of data product developed by SP | |
| Total end-market demand for data product | |
| Initial market potential for data product | |
| Quality of data products developed by SP | |
| Critical point of revenue-sharing rate | |
| Profit function of SP | |
| Profit function of DP | |
| Consumer Surplus | |
| The total profit of the data supply chain under centralized pricing model | |
| Decision variables | |
| Data incentive level | |
| Data protection level | |
| Data product pricing | |
| Proportion of revenue sharing between SP and DP |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, H.; Zheng, S.; Wu, H. User Privacy Awareness, Incentive and Data Supply Chain Pricing Strategy. Sustainability 2023, 15, 3362. https://doi.org/10.3390/su15043362
Yu H, Zheng S, Wu H. User Privacy Awareness, Incentive and Data Supply Chain Pricing Strategy. Sustainability. 2023; 15(4):3362. https://doi.org/10.3390/su15043362
Chicago/Turabian StyleYu, Haifei, Shanshan Zheng, and Hao Wu. 2023. "User Privacy Awareness, Incentive and Data Supply Chain Pricing Strategy" Sustainability 15, no. 4: 3362. https://doi.org/10.3390/su15043362
APA StyleYu, H., Zheng, S., & Wu, H. (2023). User Privacy Awareness, Incentive and Data Supply Chain Pricing Strategy. Sustainability, 15(4), 3362. https://doi.org/10.3390/su15043362





