Abstract
In the era of the Internet of Things (IoT), security is a very important issue. Recently, some security studies have been proposed based on the applications of Cellular Automata (CA). These works have the simplicity and high speed computation of CA, and are suitable for the resource-constrained IoT. In this paper, we make use of CA and propose a sliding-window CA (SWCA)-based one-way hash function. The sliding-window captures input data randomly for operation and promotes the chaos of the hash function. The proposed one-way hash function possesses high sensitivity to the input data and the one-way feature. Its performance exhibits good collision resistance along with well cryptographic characteristics. For statistical analysis, the mean changed probability is close to 50%. It can resist differential attack under the NPCR and UACI values, which are at least 99% and 33%, respectively.
1. Introduction
The Internet of Things (IoT) has been proceeded rapidly in recent years with advancements in technologies and module devices. This progress has led applications in the industrial, civil, military, marine fields. The IoT has been identified as an important power that deserves attention in the new technological revolution because it primarily changes people’s lives. The seamless integration of the digital and physical worlds through networked actuators, sensors, embedded hardware, and software is believed to transform various industrial frameworks that allow the provision of multiple products and services in very diverse domain forms. The sustainable industrial development is also accelerating due to the development of the IoT [1,2,3,4].
For the consideration of security and risk control in sustainable industrial development, the current cryptosystem generally requires quite complex operations. However, under the resource-constrained Internet of Things (IoT), a complex system will lead to a reduction in communications efficiency [5,6,7]. In terms of efficiency, Cellular Automata (CA) is a very suitable method. At present, CA have been used in the field of cryptography. Many encryption systems based on CA have been proposed [8,9,10,11,12,13,14]. Based on the simple logic operations of CA, multiple CA rules are combined to further the security of information [1,13,15,16].
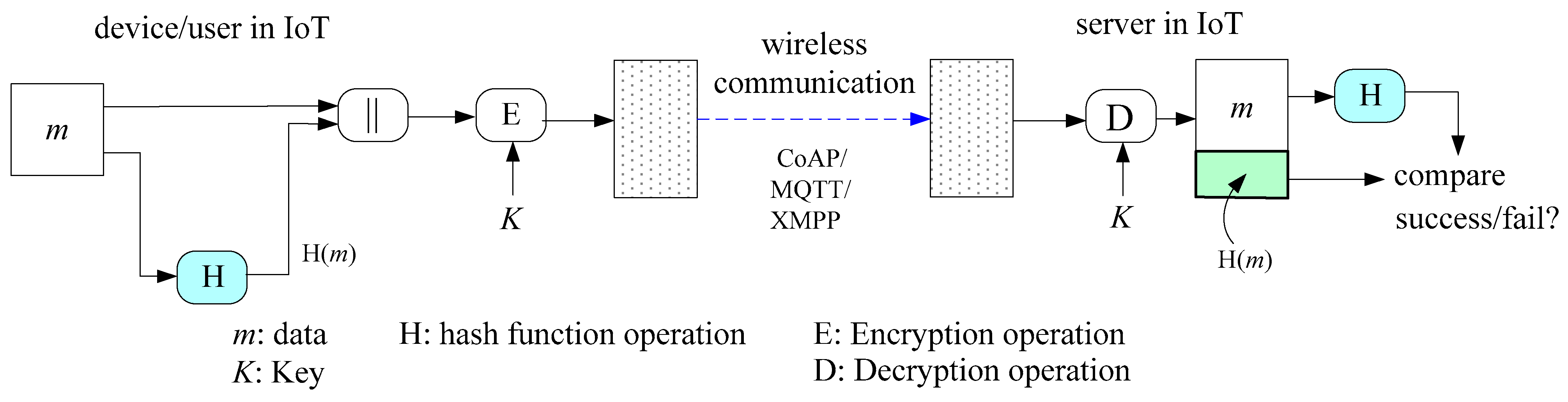
In the applications of security, the main purpose of the one-way hash function is to process the input data to obtain its hash value of the data. It is the digest of the information [14]. Many communications and the authentication of protocols require hash values to verify the integrity of messages [17,18,19,20,21]. Figure 1 shows the application of hash for the integrity of transmitting data and that it can be further utilized in message authentication. Authentication is an important issue for authentication in IoT, and both user authentication and device authentication require the hash function. It is the basic equipment for secure communications in the IoT.
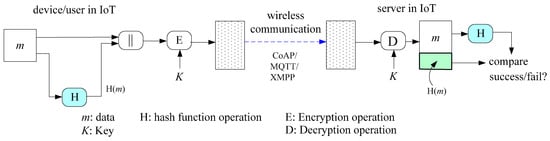
Figure 1.
Application of hash function in the IoT.
Cellular automata inhere excellent simplicity, high speed computation and nonlinear properties, and are, therefore, a good choice to be applied to the hash function [22,23,24,25,26]. Exercising the concept of sliding-window, it is used to capture input data randomly for iteration and also gains the chaos of the proposed CA-based scheme. In this paper, based on sliding-window CA (SWCA) and multi-layer cellular automata operation, we propose a one-way keyless hash function for the secure applications of the IoT. The sliding-window provides the variability of the input data, and multilayer cellular automata operations give good avalanche effects; this provides the improvement in the properties of the one-way hash function in data sensitivity. The experimental result shows that the proposed one-way hash function has good collision resistance. For statistical analysis, the mean changed probability of the proposed scheme is close to 50%. It can resist differential attacks under the NPCR and UACI values, which are at least 99% and 33%, respectively. The contributions of this study can be briefly stated as follows:
- A CA-based hash function that inheres the simplicity and high speed computation of CA, and is suitable for a resource-constrained IoT environment is proposed.
- The utilization of sliding-window can promote the chaos of the scheme under relatively simple CA operations, and it promotes the chaos of the proposed scheme.
- Multilayer cellular automata operations further avalanche the effect of the hash function.
- The outperforming results are compared with other related works.
The rest of the paper is organized as follows: Section 2 introduces the CA and the related works. Section 3 depicts our proposed SWCA-based hash function. Section 4 gives the result analysis to test the functionality of our proposed scheme and its experimental results. Finally, the conclusion is provided in Section 5.
2. Preliminaries
2.1. Operation of Cellular Automata
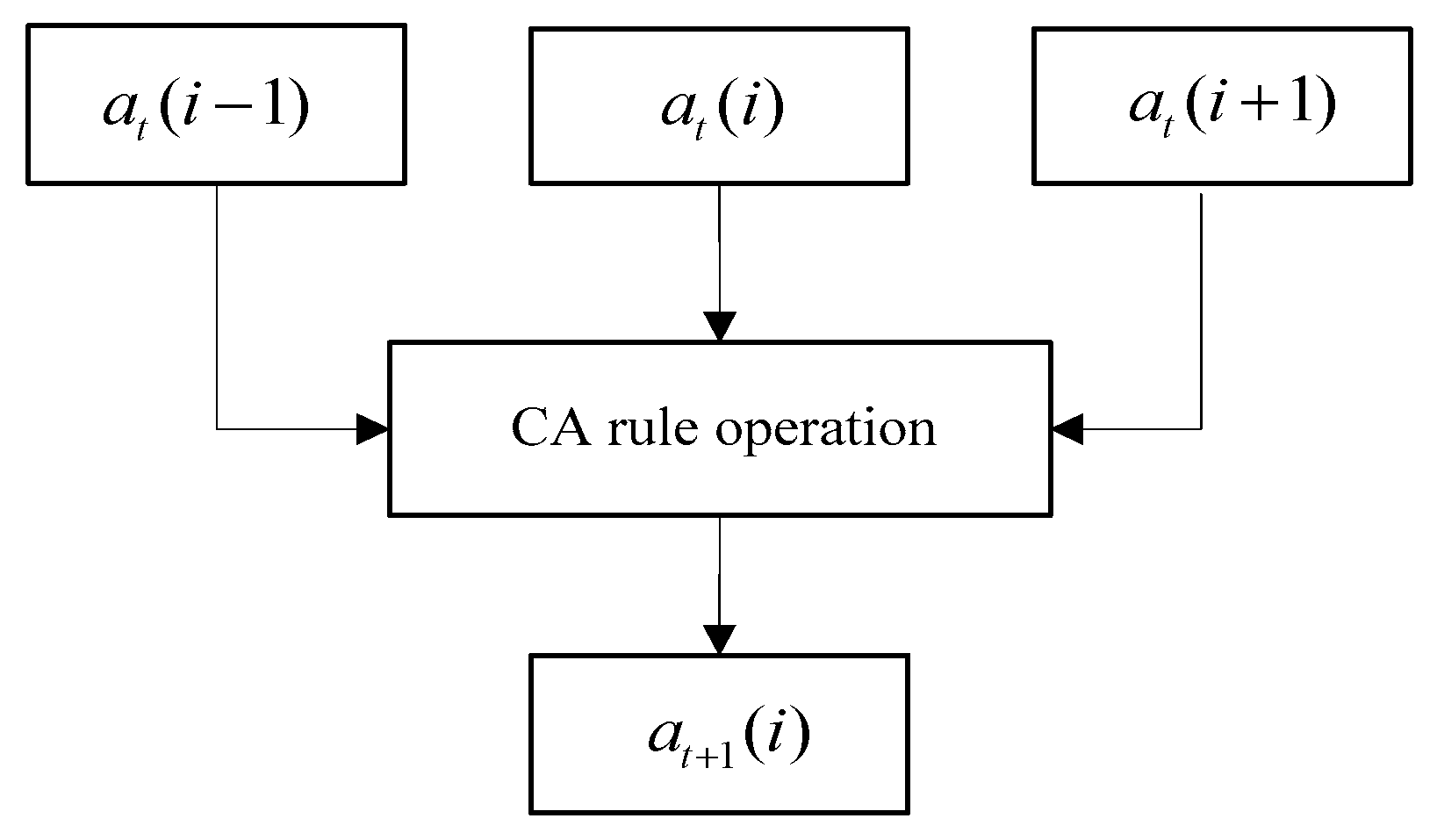
The CA is a discrete model that is applied in mathematics, physics, and computer science. In addition, CA play an important role in information security [27]. Neumann proposed the concept of CA based on simple logic operation, which has the characteristics of simplicity and nonlinearity [10]. According to its own state, the state of its neighbors and different rules of CA, various results are generated. For the CA in a one-dimensional space, an iterative output consists of a logical value of 0 or 1. Mathematically, it can be defined as Equation (1) [10].
where at(i) represents the current state of a bit, i is the position of the bit in the sequence, t is the current state of the sequence, and at+1(i) is the next state of the bit. When the operation of one bit is iterated to the next bit, the logic operation will be performed according to the cell itself and the states of the neighborhoods. As shown in Figure 2, the bits on the left and the right generate the bit state of the next iteration according to different CA rules. CA have different rule numbers according to different logical operations.
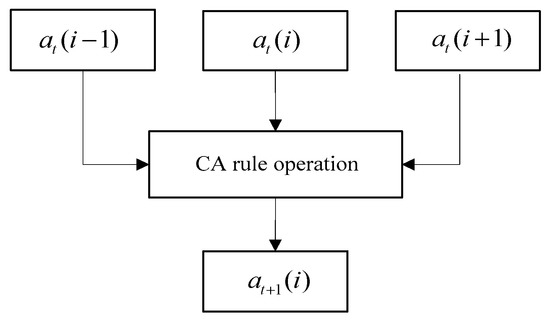
Figure 2.
Cellular automata.
Table 1 shows the logical operations of different CA rules, which iterate different output sequences according to different rules and input data [10]. The sequence is needed as the keystream in the stream cipher. The keystream generated by CA has the characteristics of simplification, regularization and modularization [13,28], and it is easy to implement on various platforms [16,25]. Therefore, CA is an efficient method to generate keystreams, which satisfies the characteristics of keystream generators in today’s communications. For example, the operation of CA rule 45 has the logic operation listed in Equation (2) [10].

Table 1.
The rules of cellular automata and their logical operation.
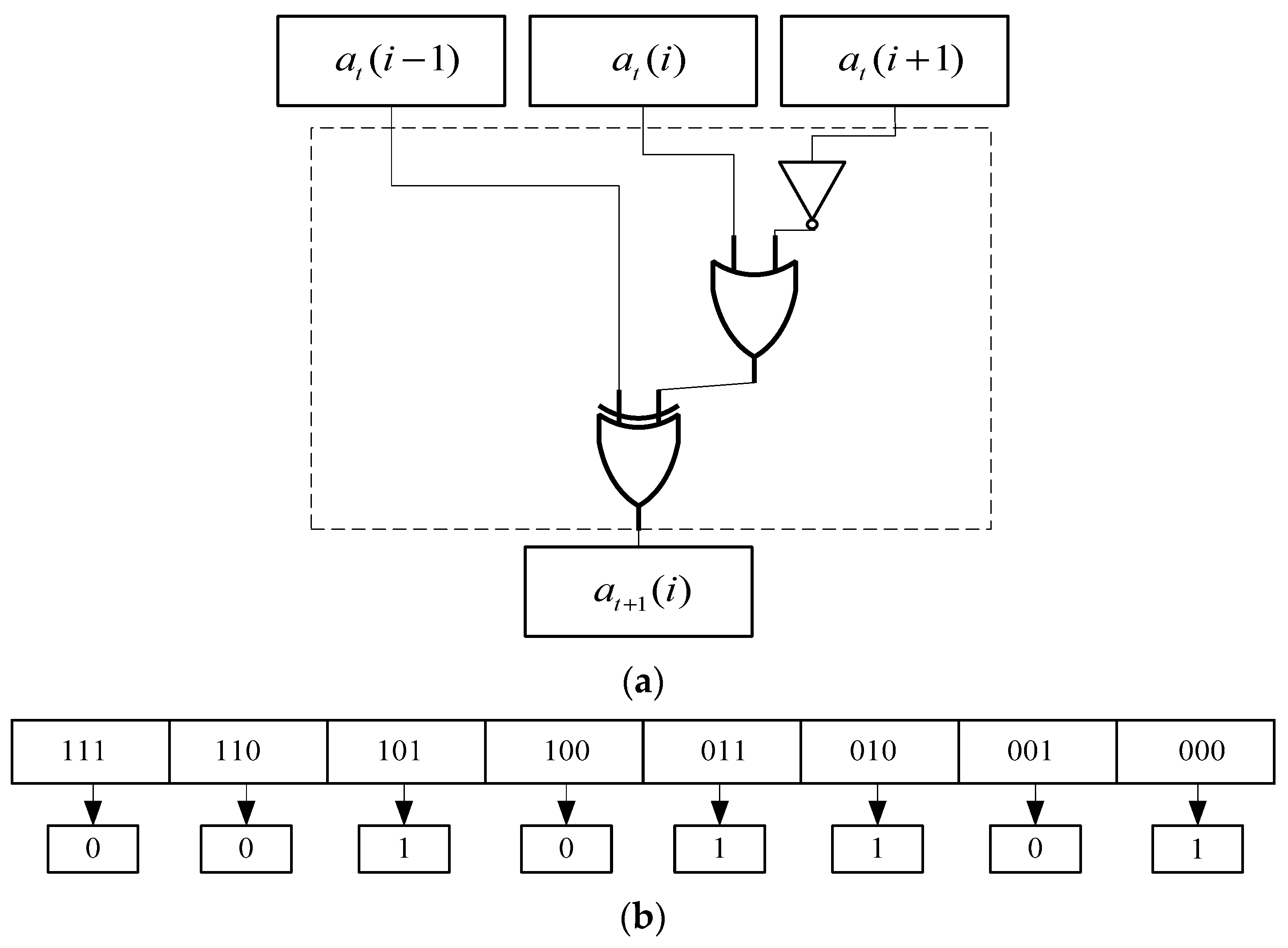
Figure 3 represents the input and output results of the cellular automaton rule 45 operation. According to various logical operations, different CA rules are formulated. Stephen Wolfram researched the CA in one-dimensional space and put forward 256 kinds of CA rules [7].
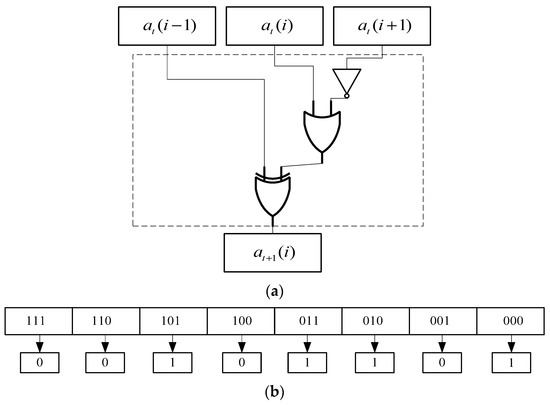
Figure 3.
Input and output of CA rule 45. (a) Logic circuit of CA rule 45. (b) Truth table of CA rule 45.
2.2. Related Work
Cryptographic hash functions are an important part of modern cryptography. The MD5 hash function took an important role in the authentication of data integrity [17]. Officially, SHA-1 is the basis of the advanced SHA algorithm. SHA-2 and SHA-3 are more secure for applications of network communications and other information applications. A hash function must satisfy the following requirements [13]:
- Variable input size: Hash function H can be applied to a block of data of any size.
- Fixed output size: Hash function H produces a fixed-length output.
- Efficiency: Hash function H is relatively easy to compute for any given message x.
- Preimage resistant (one-way property): For any given h = H(x), it is infeasible to find y such that H(y) = h.
- Second preimage resistant (weak collision resistant): For any given block x, it is infeasible to find y ≠ x with H(y) = H(x).
- Collision resistant (strong collision resistance): It is infeasible to find any pair (x, y) such that H(y) = H(x).
- Pseudorandomness: Output of H meets standard tests for pseudorandomness.
In the literature, many hash functions are proposed based on chaos theory [29,30,31,32,33,34,35]. In the resource-constrained IoT environment, CA has the advantage of simplicity and high speed computation. Therefore, cryptographic schemes based on CA have flourished widely [10,11,16,19,20]. In 2017, [22] presented a hashing algorithm using CA, Rule 30 and Rule 134, along with a custom Omega-Flip Network. The use of hybrid Cellular Automata rules along with Omega-Flip networks achieves the strong avalanche effect of the hash function. Parashar et al. addressed a CA-based hash algorithm that serially worked on blocks of bits along with bit rotation to build up a strong hash [23]. Rajeshwaran et al. proposed a CA-Based Hashing Algorithm (CABHA) by using CA rules and a custom transformation function to create a strong hash from an input message [27]. It can verify the integrity and authenticity of the message. CA provide a good nonlinear transformation, and the transformation function offers better diffusion and confusion. It makes the one-way hash function have a good avalanche effect.
In this paper, the proposed algorithm uses the concepts of cellular automata along with sliding-window and multiple CA logical operations to form an extremely random hash. The sliding-window captures input data randomly for operation and promotes the chaos of the hash function. The fusion of multiple CA gains the randomness of the output hash values, and promotes the security of the hash function. The proposed hash function would make it computationally infeasible to get back to the original input, as well as the byte collision resistance for the highly secure hashing algorithm.
3. The Proposed SWCA-Based One-Way Hash Function
3.1. The Combination of Multiple CA Rules
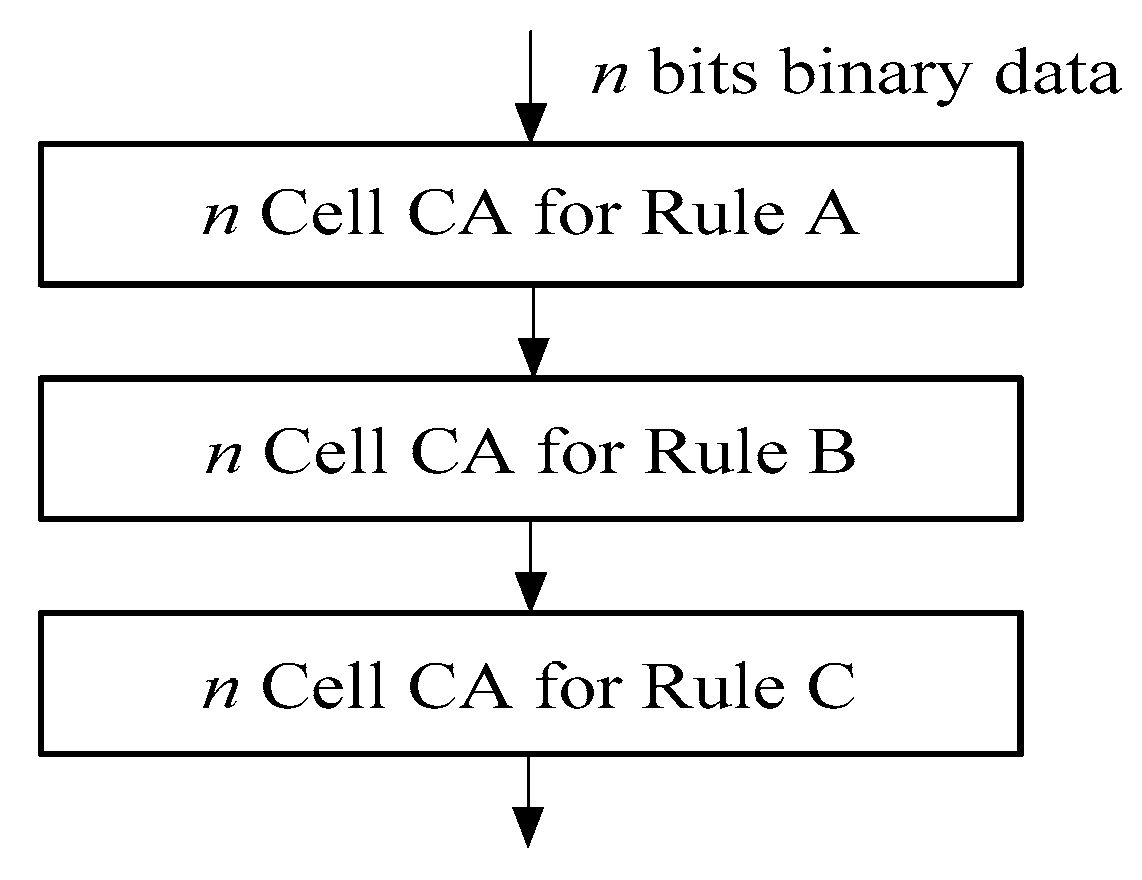
The security is lower if the hash function iterated with a single CA rule is to be used. In order to increase the chaos of the output value of the hash function and improve the randomness, we process the iteration by different CA rules. Figure 4 shows the composite use of multiple CA rules [29], which increases the properties of chaos. We further combine one dimensional CA along with the sliding-window to propose a SWCA-based one-way hash function.
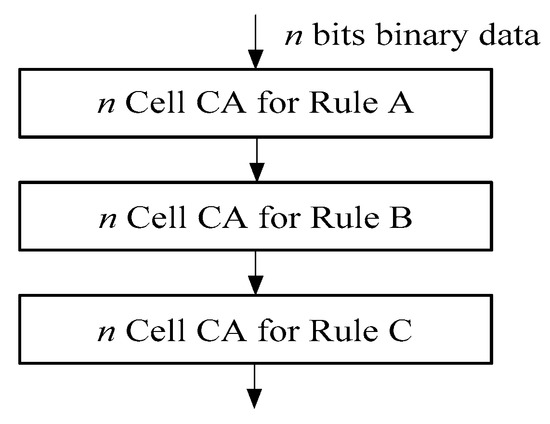
Figure 4.
The combination of multiple CA rules for hash function.
3.2. Sliding-Window
In this subsection, we propose a one-way hash function using sliding-windows CA (SWCA). One-way hash functions are an important part of modern cryptography. The function of the one-way hash function is to convert a message of variable length into fixed-length data after operation. The basic characteristics of the one-way hash function are as follows: fixed-length hash value, anti-collision, one-way and fast speed. One of the most important characteristics is that it is one-way, which means that the attacker cannot deduce the original message from the output hash value.
Nowadays, cellular automata have many applications in one-way hash functions. K. Rajeshwaran proposed a one-way hash function that combines cellular automata and transfer function [27]. The utilization of sliding-window can promote the chaos of the scheme under relatively simple CA operations. Through the proposed sliding-window algorithm, the range in the previous output data captured is variable; the input data of the iteration is not fixed. This can increase the variability in the input data of this iteration, and make the output more chaotic.
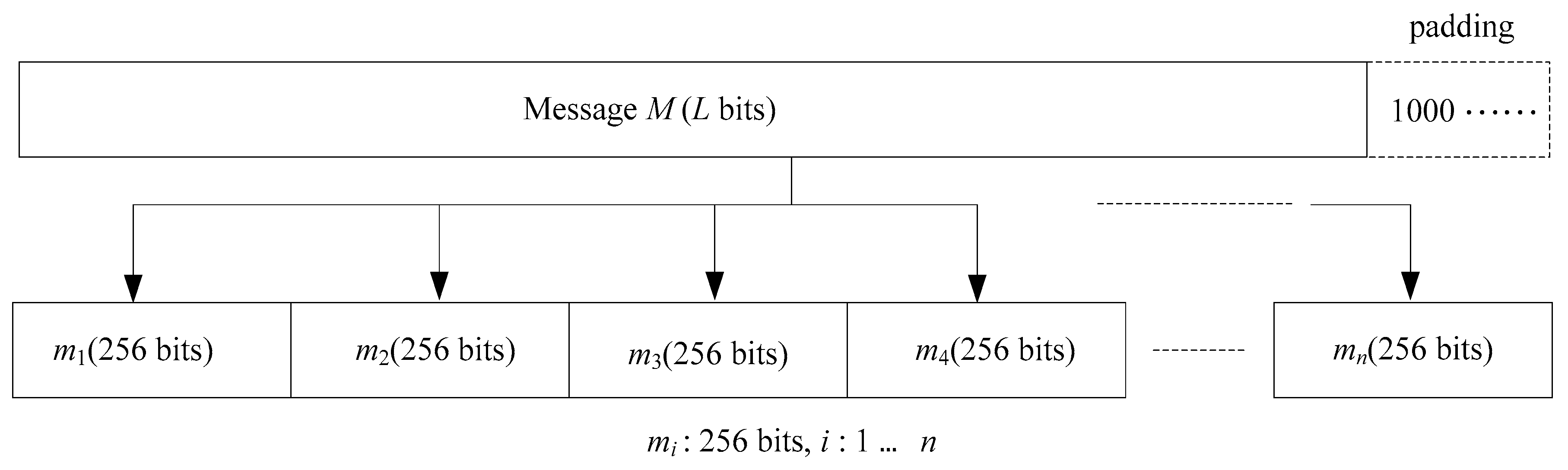
The proposed SWCA-based one-way hash function of the cellular automata based on the sliding-window we propose belongs to the unkeyed-hash function. Its purpose is to provide the integrity of the data. First, the input data is padded and divided into several data blocks. Each data block is 256 bits, as shown in Figure 5. The padding is filled with a 1 of 1 bit followed by a 0 until the data block of 256 bits can be divided equally. In this figure, M represents the plaintext, L represents the size of the plaintext, and mi represents the divided data block.
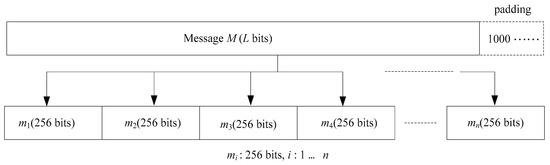
Figure 5.
Data padding and fragmentation.
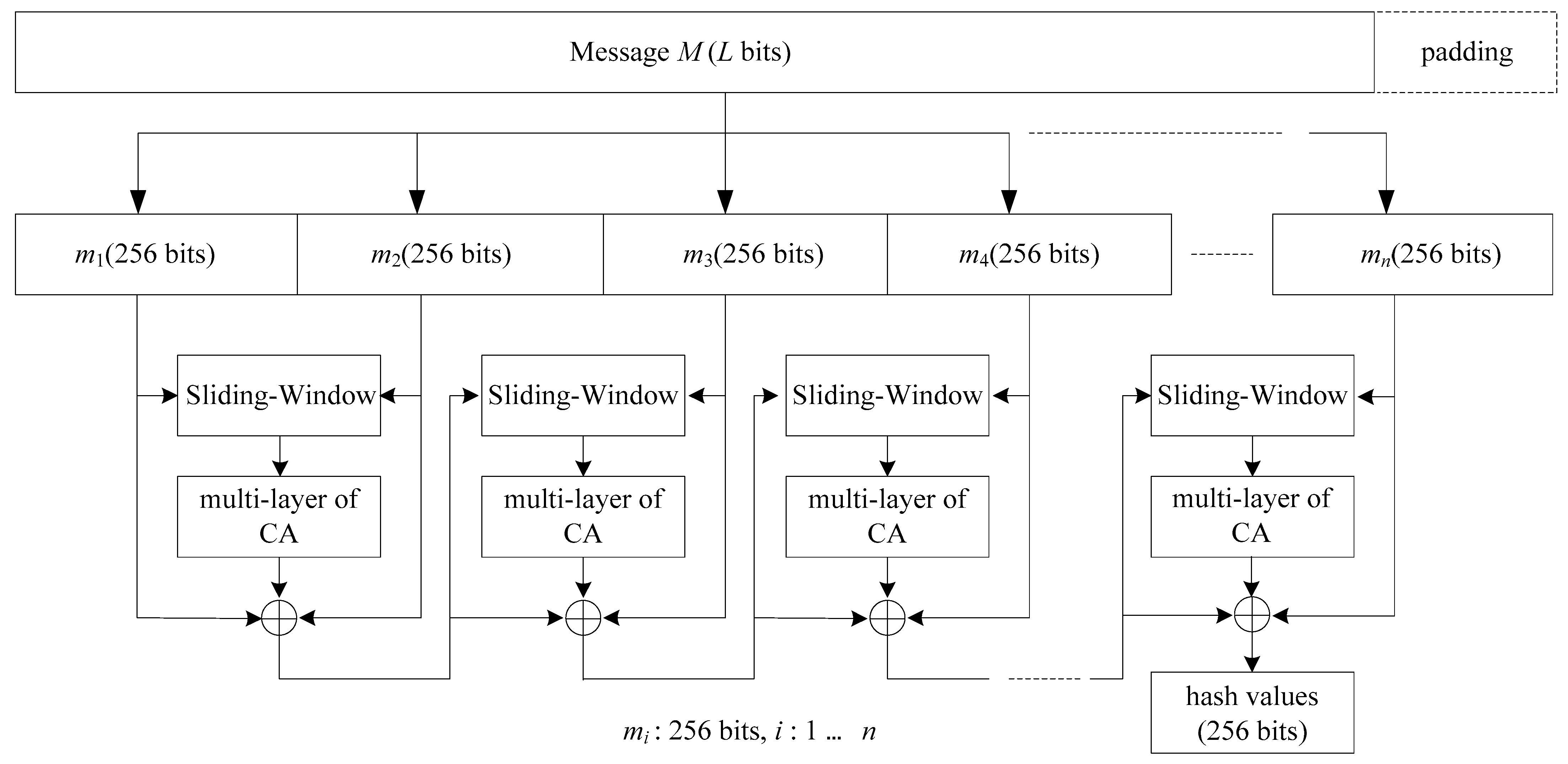
Then, each data block goes through the following three steps: (1) 256-bit sliding window (Sliding window), (2) multi-layer of 256-cell cellular automata, and (3) mutual exclusion OR operation (XOR). Figure 6 shows the block diagram of the SWCA-based one-way hash function, and finally a 256-bit one-way hash function is obtained. In this paper, we introduce the internal operations of padding and fragmentation, the 256-bit sliding window, blending stage, and multi-layer cellular automata. The output with a 256-bit length satisfies the requirement of the one-way hash function.
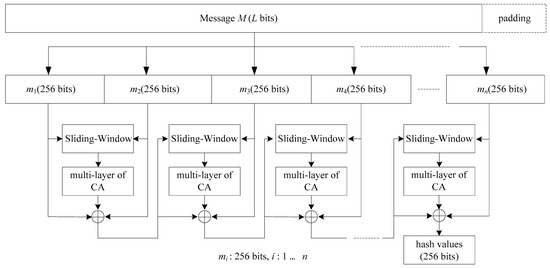
Figure 6.
The block diagram of SWCA-based one-way hash function.
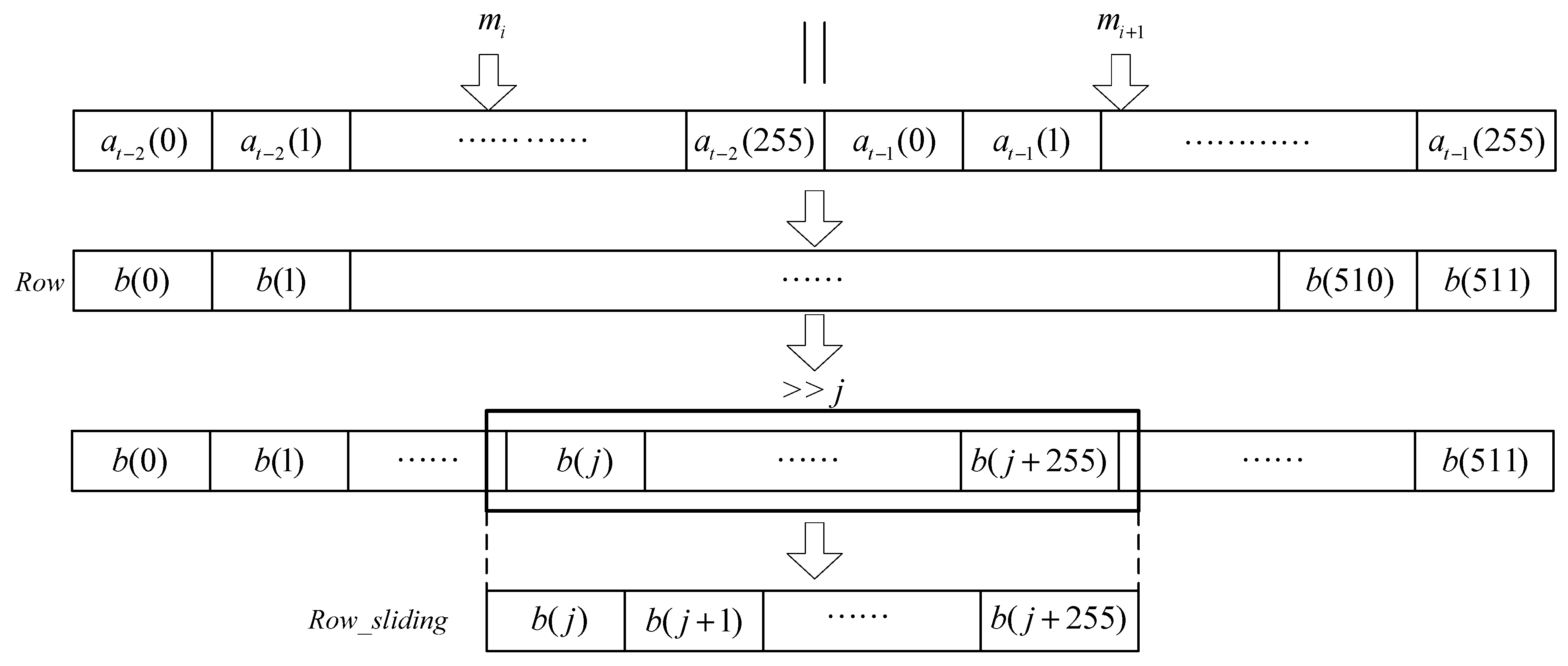
The displacement of sliding-window is determined by the parameters generated by each input data mi and mi+1. As shown in Figure 7, the total bit length of mi and mi+1 is 512 bits. The 2-data block {mi, mi+1} is equal to at−1, at−2, as shown in Equations (3) and (4):
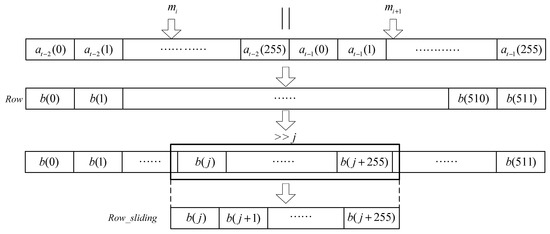
Figure 7.
The 256-bit sliding-window.
After at−1 and at−2 are concatenated, the displacement of the window is determined by the first 8 bits of the sequence {b(0), b(1), …b(7)}, such as Equation (5):
The captured data for further processing is determined by the sliding-window, and j represents the starting position of the window. According to the starting position j, the sequence with a total of 256 bits for operation is selected, as shown in Equation (6):
Row_sliding = {b(j), b(j+1), …b(j + 255)}
Finally, the sliding-window finally outputs 256-bit data, which are then fed into the multi-layer CA process.
3.3. Multi-Layer Cellular Automata
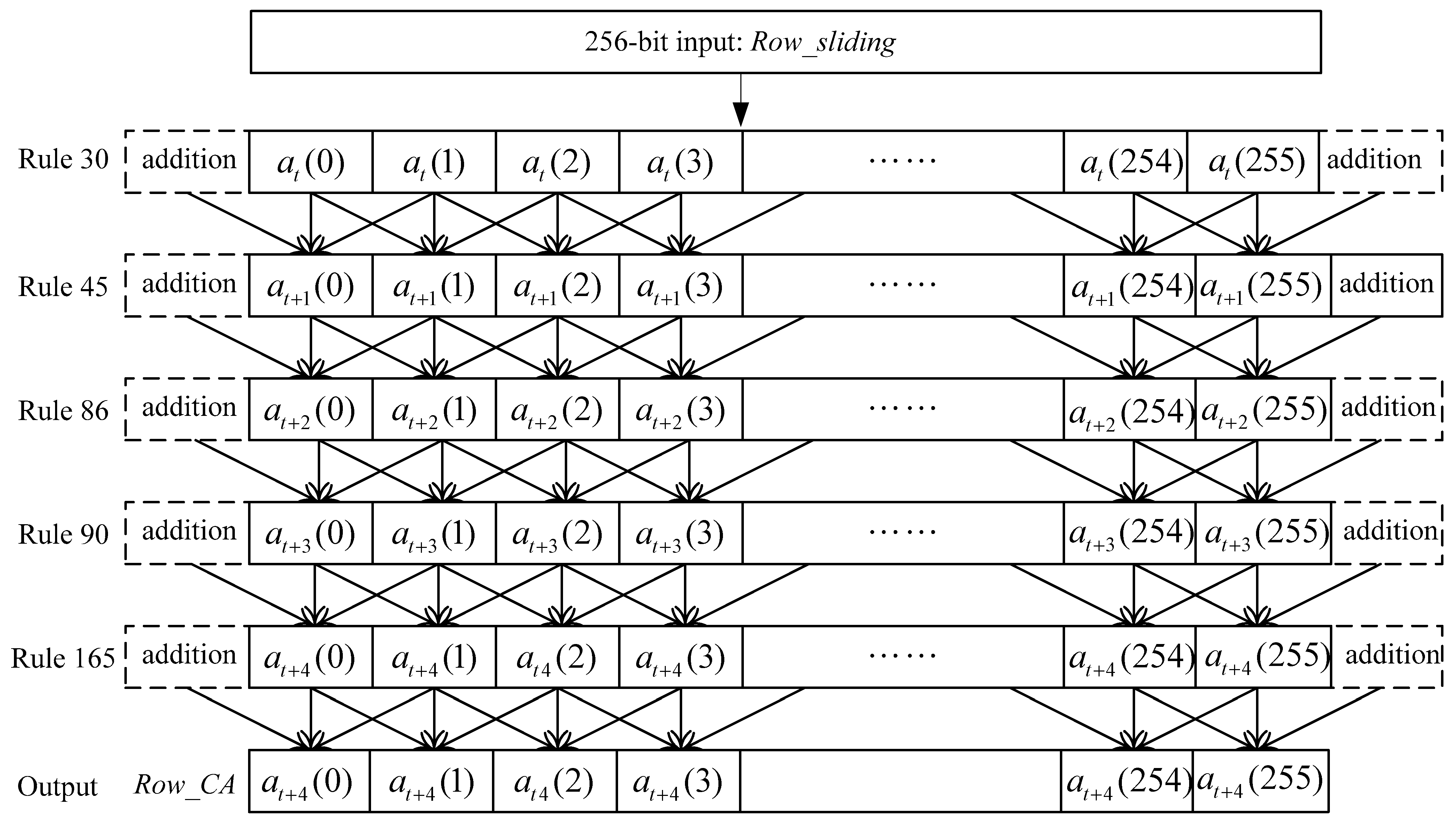
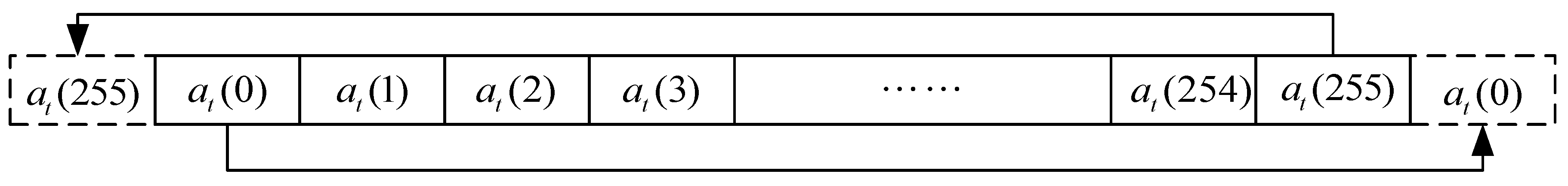
In order to promote the confusion of the one-way hash function, we use a multi-layer CA to process the 256-bit data block, as shown in Figure 8. The aim of the multi-layer cellular automaton is to provide the avalanche effect and the one-way property of the proposed hash function by means of the nonlinear transformation of the CA. The 256-bit input data is the output of the sliding-window procedure. In our scheme, there are five CA layers in the process and the CA rules are rule 30, 45, 86, 90 and 165, respectively. The reason for applying these is that the correlation of these CA rules are all 1/2. This provides good chaotic characteristics for cryptography. In addition, it satisfies the basic requirement for the cryptographic hash function. There are two additional bits that are added on the most left and the most right sides on the input 256-bit data: Row_sliding, respectively, as shown in Figure 9. That is, the first bit at(0) is filled to the end of the data, and the bit at(255) is filled to the front. Therefore, the data goes through multi-layer CA operations, and finally it receives 256-bit output data: Row_CA, in Figure 8.
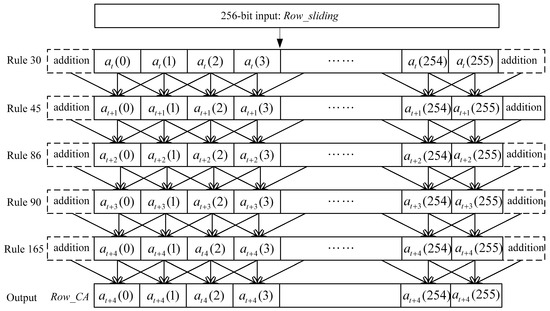
Figure 8.
Multi-layer CA process.

Figure 9.
Adding 2 bits for CA operation.
Sensitivity to input data is very important for one-way hash functions. Although the proposed sliding-window CA provides a good nonlinear calculation, Row_CA loses some of the message of the input data mi and mi+1. To overcome this weakness, a mixing operation further shuffles Row_CA with the input data, as shown in Equation (7):
The data mi and mi+1 perform a mutually exclusive OR (XOR) operation with Row_CA, which scrambles the data and improves the sensitivity of the input data. Finally, the data outputs to the next round.
3.4. The Output of One-Way Hash Value
The proposed one-way hash function merges sliding-windows and a multi-layer CA operation to generate hash values. We briefly describe the algorithm of the SWCA-based one-way hash function shown in Algorithm 1. First, the input data is message M and its data length is L in bits. If the length L is not a multiple of 256 bits, it fills 1 bit with 1 followed by 0 until the last data block is 256 bits. It obtains n 256-bit data blocks {mi} for i = 1, …, n. Then, the 2 input data blocks {mi, mi+1} for i = 1, …, n − 1, are sequentially put into the 256-bit sliding-window operation, Sliding_512. After the Sliding_512 operation and outputting the 256-bit Row_sliding, the data Row_sliding is put into the multi-layer CA operation to obtain Row_CA. The data Row_CA perform a mutually exclusive OR with mi and mi+1 until all data blocks have been processed. Finally it obtains the 256-bit hash value.
| Algorithm 1: Algorithm of SWCA based one-way hash function |
| Input: M (Message) , L bits (Message size) Output: h = 256 bits (Hash value) Begin //padding message p= ( L ) mod 256 if p ≠ 0 { PM = M || 1 || 0*(p−1) } // message division j = 1 i = 0 While (i < = size (PM)){ mj = PM[i : i+255] i += 256 j ++ } return mn = mj //main hash founction for( i = 1 ; i < n ; i ++){ Row_sliding = Sliding_512(mi ,mi+1) Row_CA = 5_layer_CA(Row_sliding) Mixed_row = mi ⊕ mi+1 ⊕ Row_CA mi = Mixed_row } return mi // 256 bits (Hash value) End |
4. Security Analysis and Experimental Results
In this section, we simulate the proposed sliding-window-based CA one-way hash function. We analyze the security of the simulated experimental results. The simulation system of this experiment is Python 3.9, on Windows 10, with Memory 16.0 GB.
For a safe one-way hash function, it requires strong collision resistance and an avalanche effect. The attacker cannot easily reverse the original data from the hash value output by the one-way hash function. It is so-called one-way property. In addition, the possibility of the collision of output hash values needs to be reduced. Our proposed SWCA-based one-way hash function can well satisfy the above properties. Next, in this subsection, we will analyze the security of our proposed one-way hash function.
4.1. Collision Analysis
In cryptography, the collision of hash values refers to the situation where the bytes in the hash values are the same after two messages are calculated by a one-way hash function. That is to say, attackers use this to disguise or find out the original message. However, it is possible for two hash values to collide with a byte. Therefore, we hope that the probability of a collision situation is as small as possible, which is also a guarantee of the security of the one-way hash function.
SHA-256 is a hash function developed by the National Security Agency (NSA) and published by the National Institute of Standards (NIST) [30]. It belongs to the second generation hash function algorithm in the SHA family after SHA-1, and is one of the most representative hash functions in the world. The output length of the proposed SWCA-based one-way hash function is 256 bits, which is the same as the output length of SHA-256. Next, we will compare the collision properties of the two.
4.2. Analysis of Byte Collision Occurrences for Message Pair
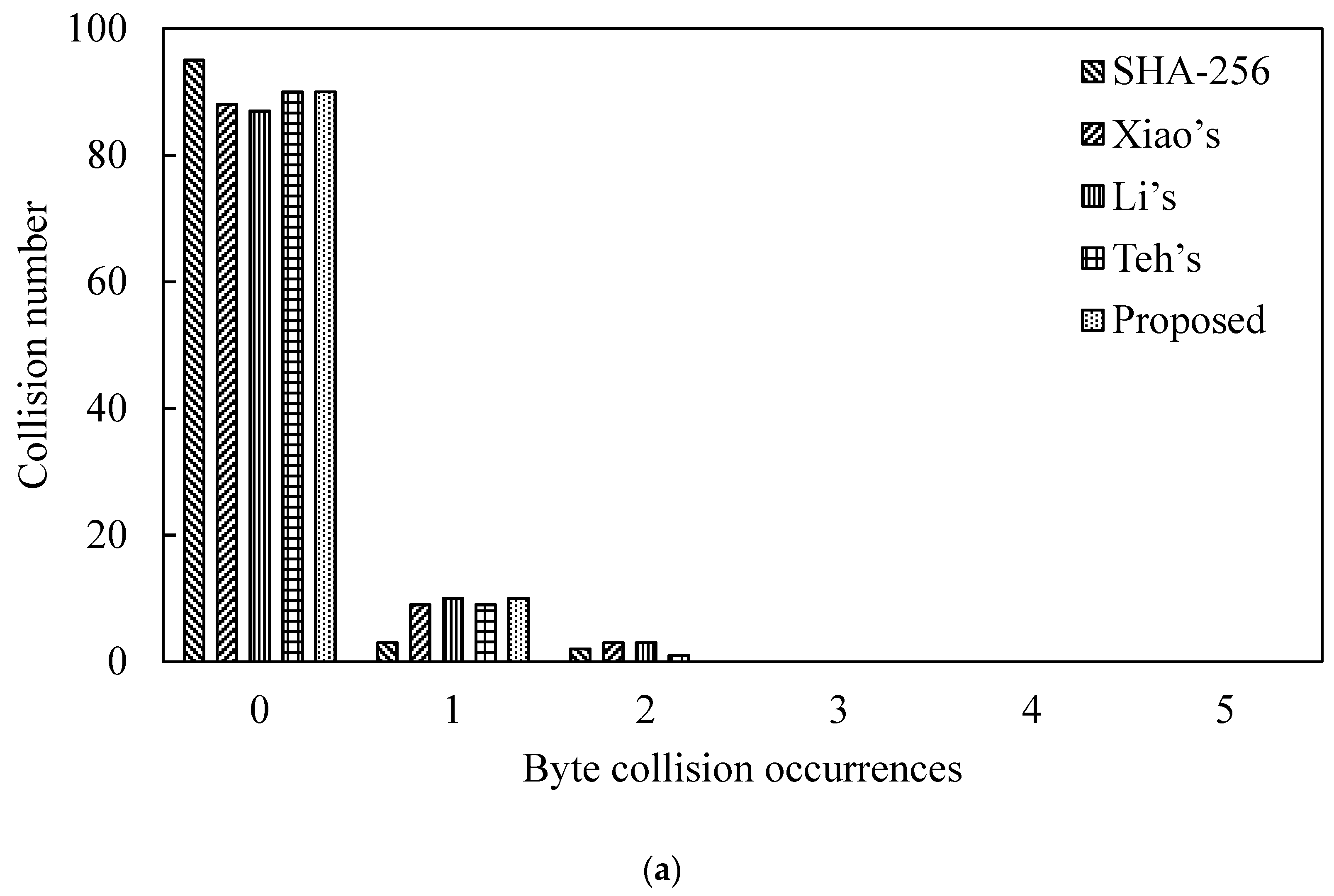
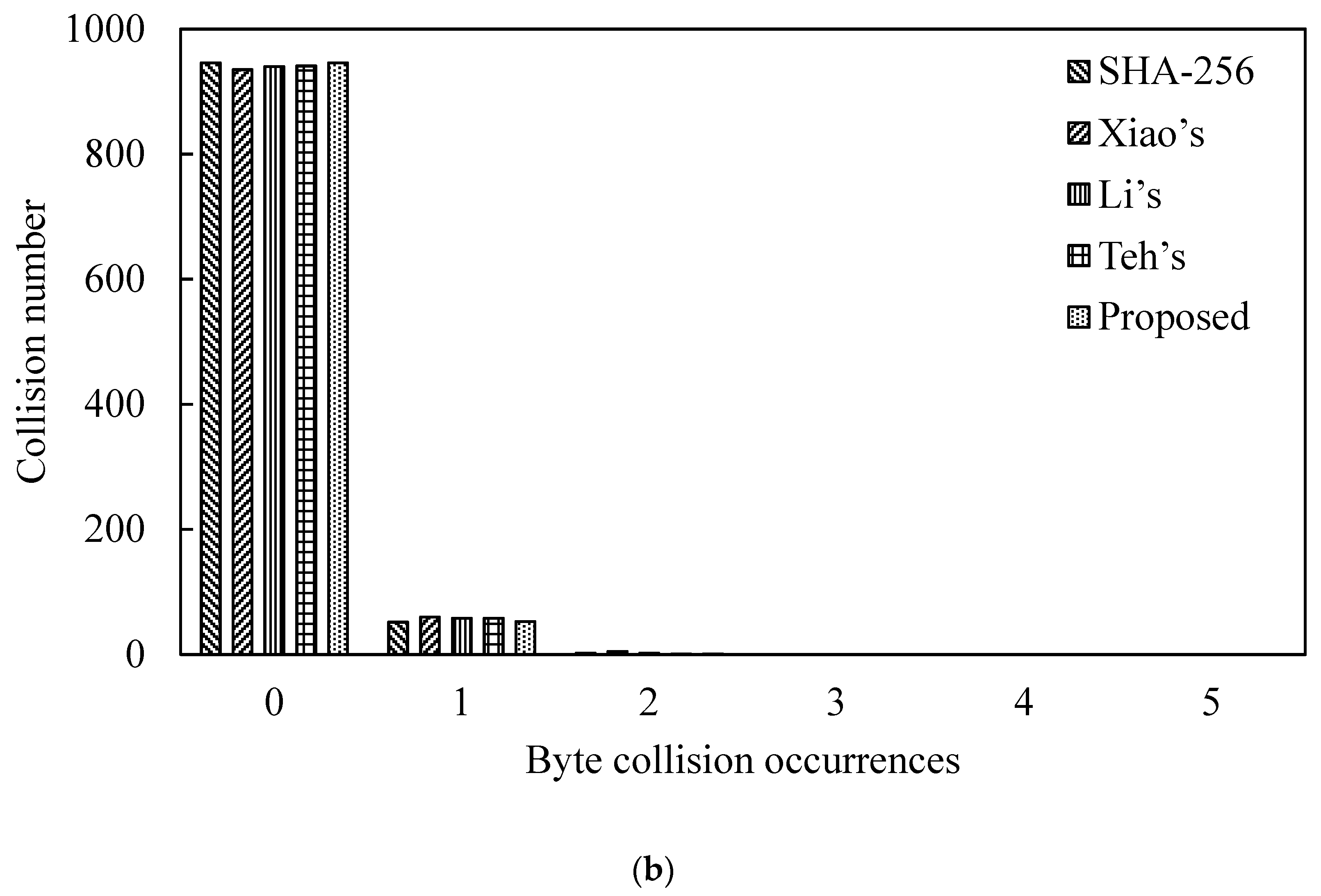
We performed the byte collisions test for the proposed SWCA-based one-way hash function algorithm and SHA-256. Firstly, 100 pairs of 106-bit random data were selected randomly, N = 100, and were input into our proposed one-way hash function. Then, the number of collisions in the hash value bytes was counted. That is, the hash value was compared with the data at the same position in the byte group. If the data are the same, a collision occurs. The related experimental results of the collision times are shown in Table 2a,b for N = 1000. The table shows the collision number under no collision, one collision and two collisions, respectively. Figure 10 is depicted corresponding to Table 2.

Table 2.
Collision number of hash values.
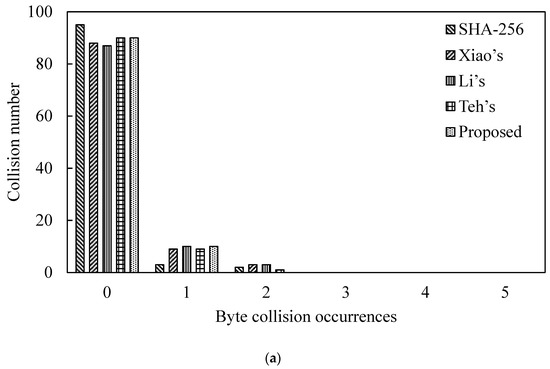
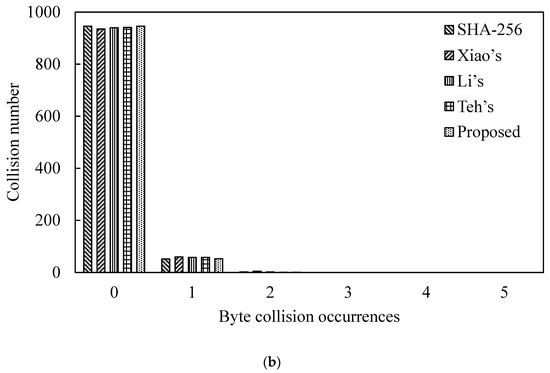
Figure 10.
Collision number Analysis of Hash Value. (a) N = 100. (b) N = 1000.
Table 2a and Figure 10a show that our proposed one-way hash function does not have more than 2 collisions. That is to say, the number of times that the hash values of the two random messages collide at the same position in the unit of bytes is less than 2 times. This result considers that the one-way hash function has good collision resistance [27]. For N = 1000, compared with the related works, the proposed scheme also exhibits excellent characteristics of collision resistance.
4.3. Probabilistic Analysis of Byte Collision Occurrences
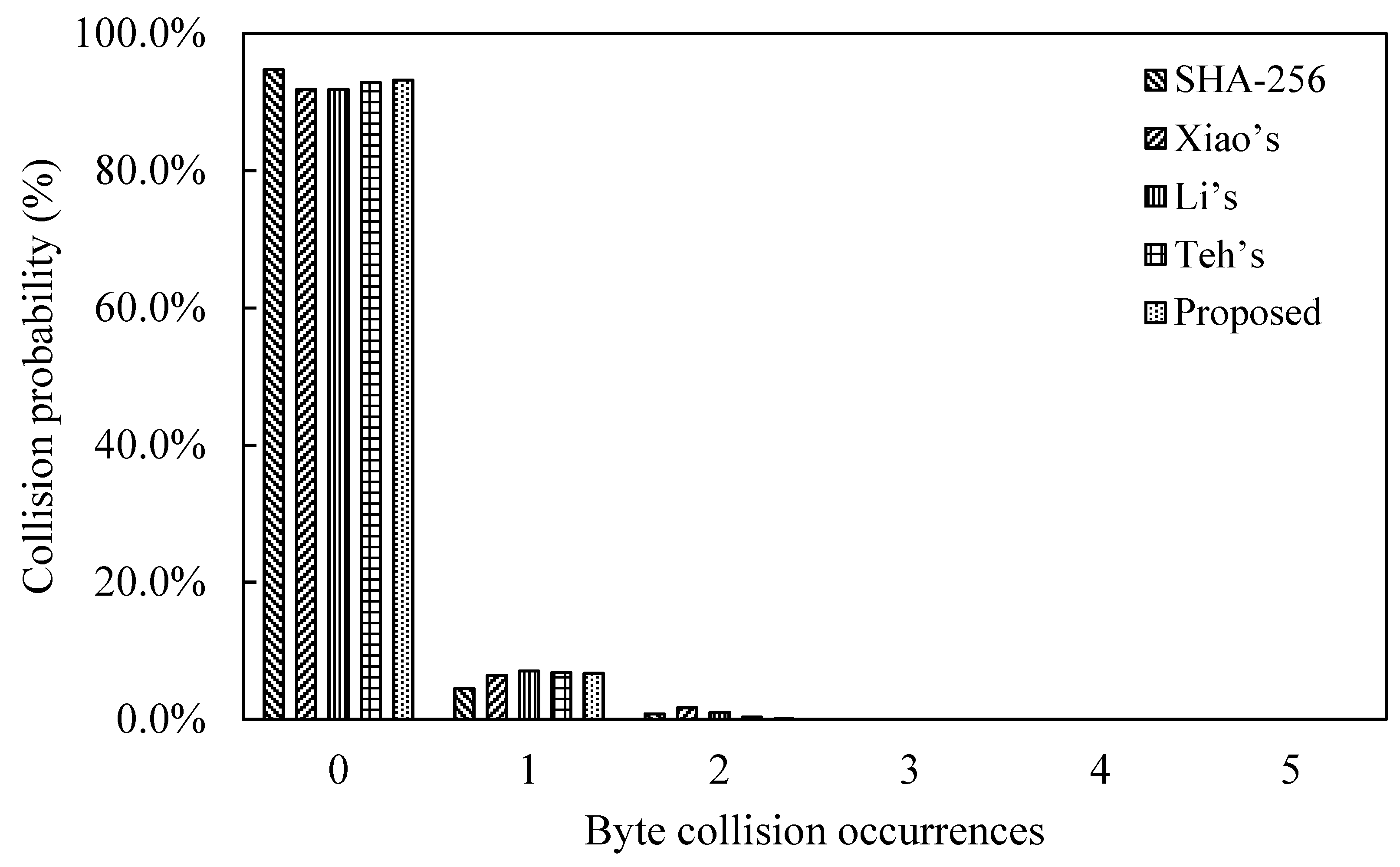
We performed a probabilistic analysis of byte collision occurrences on the sliding-window cellular automata one-way hash function algorithm proposed in this paper and other related works. A 106-bit message and other random 106-bit messages for N = 100, 500, and 1000 were chosen. After inputting the message into the hash function, the output hash value is compared with the probability of byte collision. The final results are shown in Table 3. Our proposed one-way hash function with the odds under zero collision, one collision and two collisions are 93.2%, 6.7%, and 0.1%, respectively.

Table 3.
Comparison of collision probability.
The data in Table 3 are charted into Figure 11. From this figure, it can be found that the probability of collision is almost indistinguishable from SHA-256 and other works. This means that our proposed SWCA-based one-way hash function has good collision resistance. It nearly has the same good collision resistance as SHA-256. However, the operation of SHA-256 is more complicated and has more round numbers. The one-way hash function of the SWCA proposed is composed of cellular automata, that is, only basic simple logical operations. Therefore, in terms of hardware design difficulty, the one-way hash function proposed has the merit of simplicity.
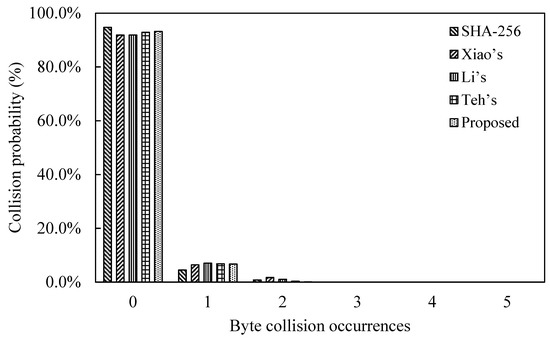
Figure 11.
Chart of comparison of collision probability.
4.4. Statistical Analysis
The distribution of the hash function has to be uniform, otherwise it will suffer brute force attack by means of the collision of the hash function. The statistical analysis performs the hash function operation by randomly selecting the input plaintext. The value of one bit of input is randomly changed, and the changed output hash function is found. In the experiment, the process is repeated 256, 512, 1024, and 2048 times. The following quantities, Equations (8)–(13) [35], are measured.
The mean changed bit number is as follows:
The mean changed probability is as follows:
The standard variance in the changed bit number is as follows:
Standard variance is as follows:
The minimum changed bit number is as follows:
Bmin = min(Bi).
The maximum changed bit number is as follows:
Bmax = max(Bi).
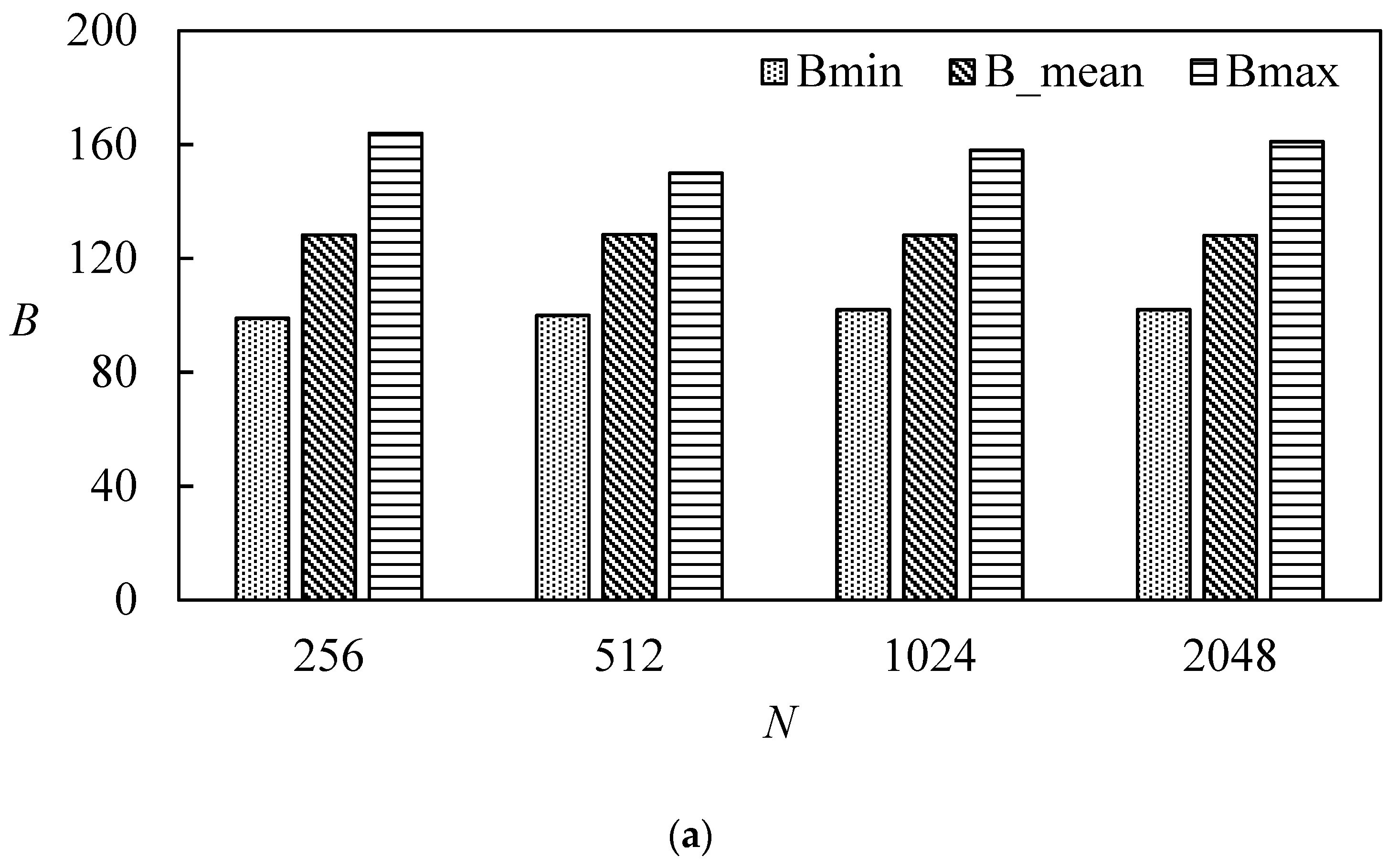
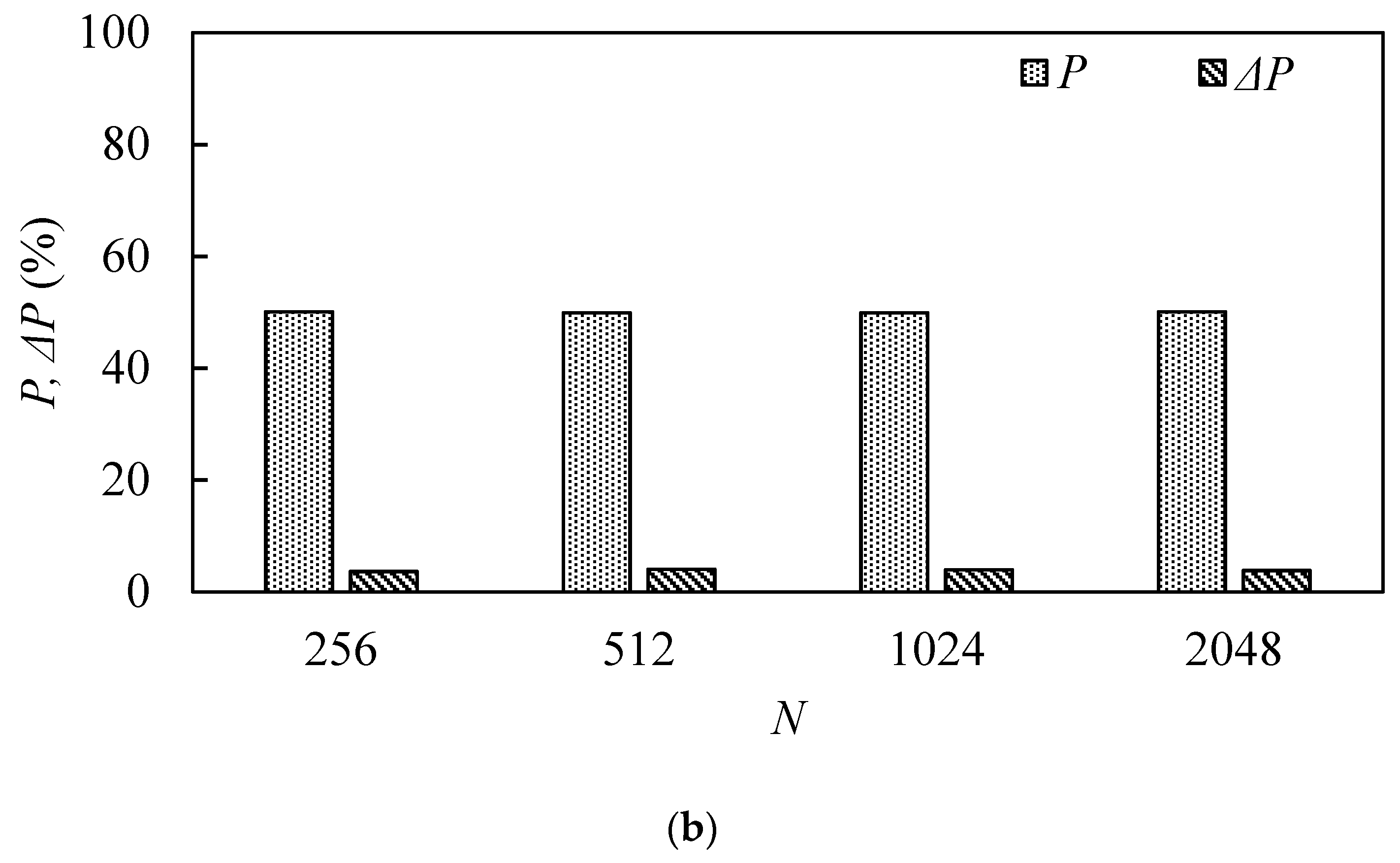
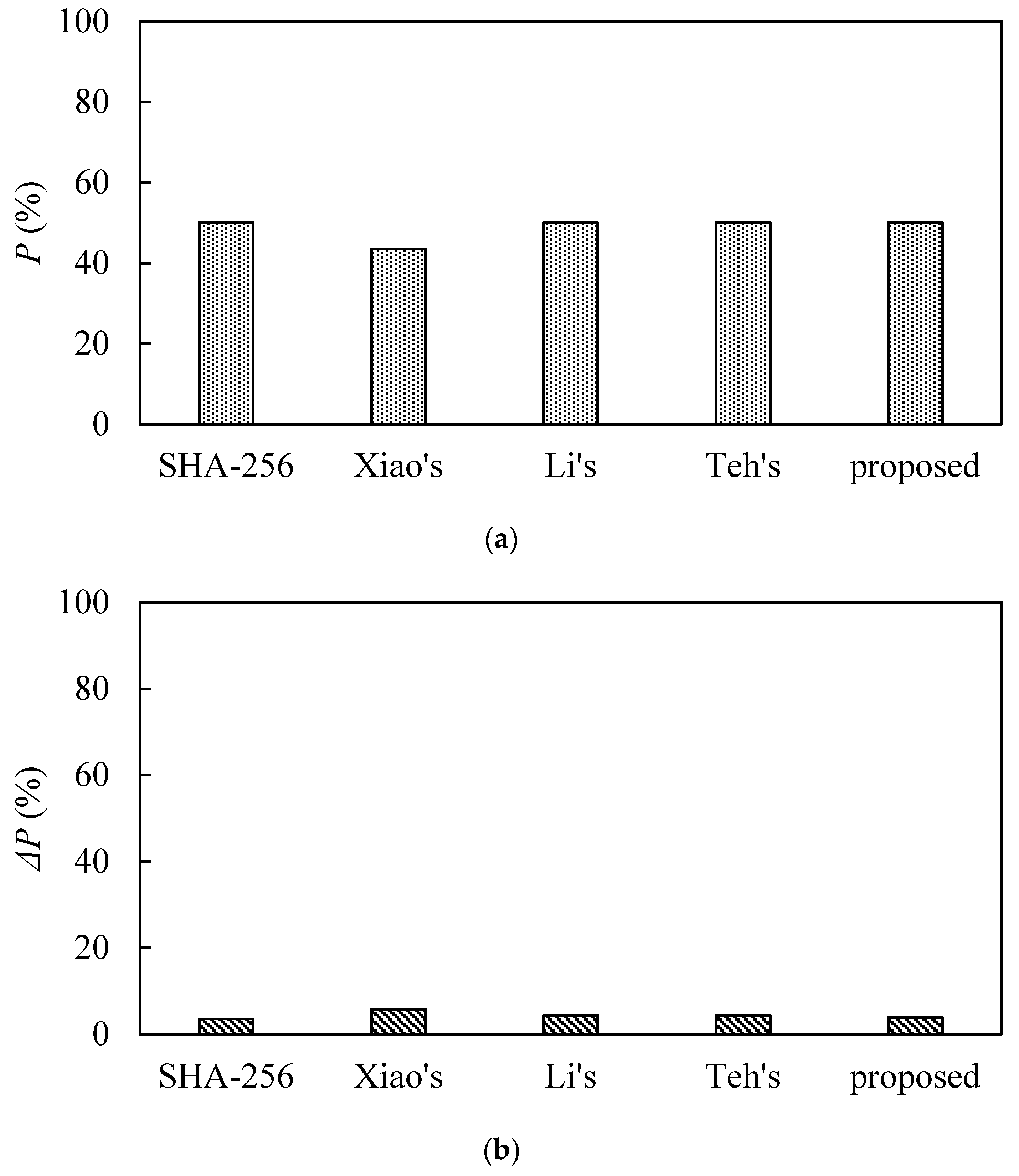
For the length of the hash output that is 256 bits, the ideal value of the average number of variation bits is 128, and the ideal average variation ratio P is 50%. ΔB and ΔP values of less than 5% are excellent values. Table 4 lists the algorithm’s performance metrics for N = 256, 512, 1024, and 2048. Figure 12 and Figure 13 are plotted from Table 4. From these table and figures, it can be seen that both and P are close to the ideal value. Statistical characteristics of the proposed function are serviceable. Table 5 is a comparison of the statistical analysis of our proposed scheme with other schemes. This table indicates that the hash value via our proposed scheme has excellent statistical characteristics.

Table 4.
Statistical analysis of the proposed scheme.
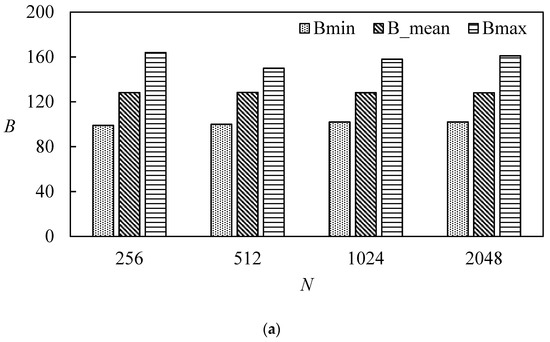
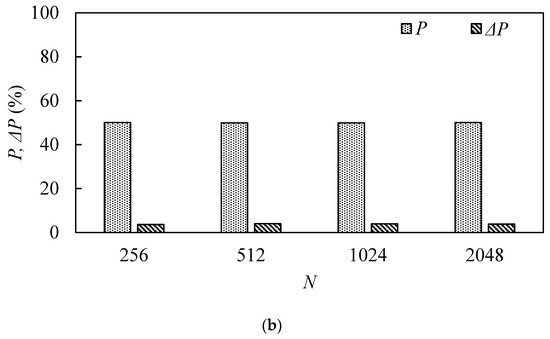
Figure 12.
Statistical analysis. (a) Bit changed analysis. (b) Bit changed probability analysis.
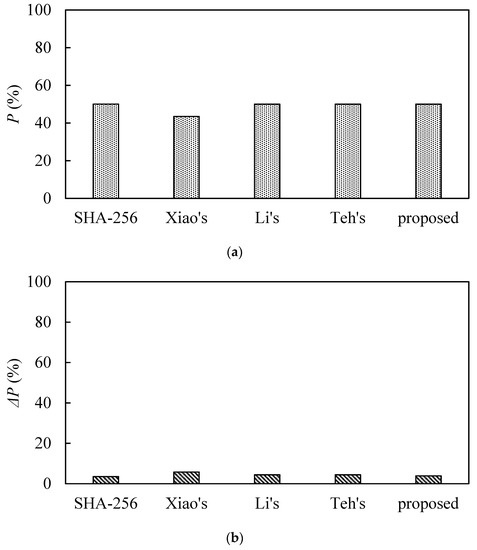
Figure 13.
Comparison of the statistical analysis. (a) Comparison of mean changed probability. (b) Comparison of standard variance in mean changed probability.

Table 5.
Comparison of the statistical analysis.
4.5. Differential Attack
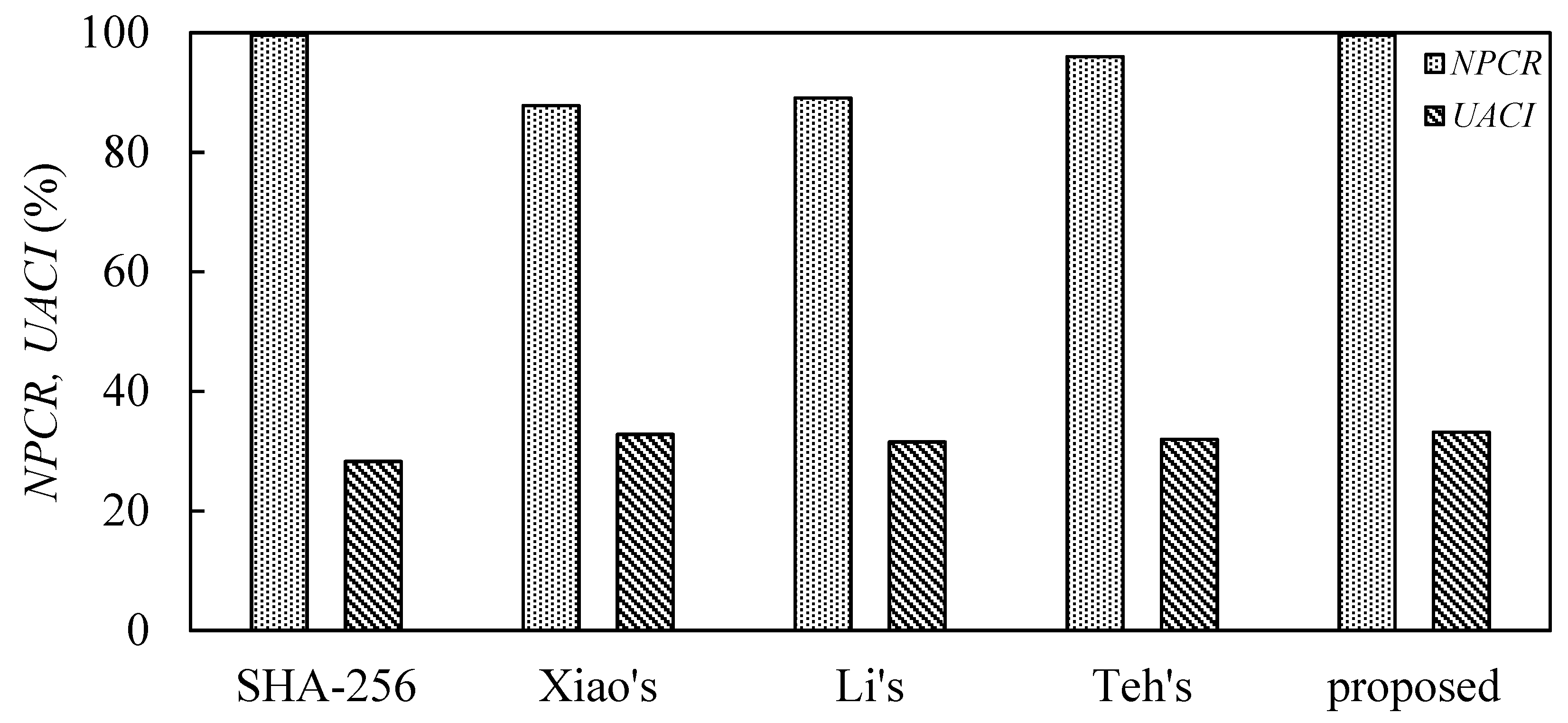
Differential attack is a method of analyzing the message input with a small difference, on the change in the hash function output. Therefore, a well hash function should be vastly different from a tiny input change in order to avoid differential attack. The strength of the resistance to differential attack can be evaluated by two parameters: Number of Changing Pixel Rate (NPCR) and Unified Averaged Changed Intensity (UACI). The ideal value of NPCR is above 99%, and the ideal value of UACI is above 33% [31]. The calculations of NPCR and UACI are shown in Equations (8) and (9) [31], respectively, where C1 and C2 are the two hash values and L is the hash value length.
where
We perform NPCR and UACI calculations for the proposed hash function. The test results of NPCR and UACI are shown in Table 6 and depicted in Figure 14. For the proposed scheme, the NPCR value is 99.61% and the UACI value is 33.18%, which means that the proposed hash function can resist a differential attack.

Table 6.
Differential attack test results and comparisons.
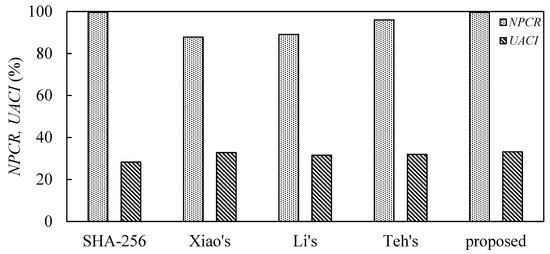
Figure 14.
Comparison of the statistical analysis.
5. Conclusions
In this paper, we propose a one-way hash function, based on CA and that combines sliding-windows, multi-layer cellular automata and mutually exclusive OR operations. The experimental results show that the one-way hash function of cellular automata based on sliding-window has good anti-collision characteristics. For the secure application of the IoT, CA have the advantages of simplicity and modularization. It has a low collision occurrence probability along with excellent statistical characteristics. For differential attack resistance, the proposed scheme can resist differential attacks with the NPCR and UACI values being at least 99% and 33%, respectively. In the embedded system with limited hardware performance or a Field Programmable Gate Array (FPGA) environment, the number of CA can be adjusted according to the performance of the device. In the future research, the number of CA can be designed according to the performance of the hardware equipment, in order to improve the efficiency of cellular automata in cryptographic applications. In addition, the output length of the hash function can be managed according to the requirements of cryptographic applications.
Author Contributions
Conceptualization, S.-T.W.; methodology and software, S.-T.W.; validation, S.-T.W. and J.-R.C.; investigation and data curation, S.-T.W.; writing—original draft preparation, S.-T.W. and J.-R.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Publicly available datasets were analyzed in this study.
Acknowledgments
The author wishes to thank Guo-Hua Wu for his important assistance and the anonymous referees for their valuable and useful comments that have enriched this paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Cao, B.; Sun, Z.; Zhang, J.; Gu, Y. Resource Allocation in 5G IoV Architecture Based on SDN and Fog-Cloud Computing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3832–3840. [Google Scholar] [CrossRef]
- Lv, Z.; Song, H. Mobile Internet of Things under Data Physical Fusion Technology. IEEE Internet Things J. 2020, 7, 4616–4624. [Google Scholar] [CrossRef]
- Lv, Z.; Chen, D.; Lou, R.; Song, H. Industrial Security Solution for Virtual Reality. IEEE Internet Things J. 2021, 8, 6273–6281. [Google Scholar] [CrossRef]
- Lv, Z.; Qiao, L.; Hossain, M.S.; Choi, B.J. Analysis of Using Blockchain to Protect the Privacy of Drone Big Data. IEEE Netw. 2021, 35, 44–49. [Google Scholar] [CrossRef]
- Akanksha, E.; Javali, A.; Jyoti. A review on Security in Internet of Things. In Proceedings of the 2022 IEEE World Conference on Applied Intelligence and Computing (AIC), Sonbhadra, India, 17–19 June 2022; pp. 883–887. [Google Scholar]
- Roy, S.; Bhatia, N.; Rawat, U.S. A Novel Cryptosystem Using Cellular Automata. In Proceedings of the 2017 International Conference on Communication and Signal Processing, Chennai, India, 6–8 April 2017; pp. 1781–1785. [Google Scholar]
- Wolfram, S. Cryptography with Cellular Automata. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1985. [Google Scholar]
- Chen, Q.; Dai, Y.; Niu, Z. An Image Encryption Algorithm Based on Combination of Chaos and DNA Encoding. In Proceedings of the 2020 International Conference on Computer Vision, Image and Deep Learning (CVIDL), Chongqing, China, 10–12 July 2020; pp. 182–185. [Google Scholar]
- Gonzalez, R.C.; Woods, R.E. Digital Image Processing, 3rd ed.; Prentice Hall: Hoboken, NJ, USA, 2008. [Google Scholar]
- Kumar, J. Novel and Efficient Cellular Automata Based Symmetric Key Encryption Algorithm for Wireless Sensor Networks. Int. J. Comput. Appl. 2010, 13, 1767–2424. [Google Scholar]
- Kumaravel, A.; Meetei, O.N. An application of non-uniform cellular automata for efficient cryptography. In Proceedings of the 2013 IEEE Conference on Information & Communication Technologies, Thuckalay, India, 11–12 April 2013; pp. 1200–1205. [Google Scholar] [CrossRef]
- Kerckhoffs, A. La Cryptographie Militaire. J. Des Sci. Mil. 1883, 9, 5–38. [Google Scholar]
- Stallings, W. Cryptography and Network Security: Principles and Practice, 6th ed.; Pearson: London, UK, 2014. [Google Scholar]
- Wolfram, S. A New Kind of Science; Wolfram-Research Inc: Champaign, IL, USA, 2002. [Google Scholar]
- Nandi, S.; Kar, B.K.; Chaudhuri, P.P. Theory and applications of cellular automata in cryptography. IEEE Trans. Comput. 1994, 43, 1346–1357. [Google Scholar] [CrossRef]
- Roy, S.; Rawat, U.; Karjee, J. A Lightweight Cellular Automata Based Encryption Technique for IoT Applications. IEEE Access 2019, 7, 39782–39793. [Google Scholar] [CrossRef]
- Rivest, R.L. RFC 1321: The MD5 Message-Digest Algorithm. MIT Laboratory for Computer Science and RSA Data Security, Inc. 1992. Available online: https://www.ietf.org/rfc/rfc1321.txt (accessed on 9 December 2022).
- HEM Infosec, Ltd. OWASP Top 10. 2021. Available online: https://www.heminfosec.com/eDM/2021-10-OWASPtop10-2021-WAPPLES-OSCAN.html (accessed on 9 December 2022).
- Hanin, C.; Echandouri, B.; Omary, F.; El Bernoussi, S. L-CAHASH: A novel lightweight hash function based on cellular automata for RFID. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Tripathy, S.; Nandi, S. LCASE: Lightweight cellular automata-based symmetric-key encryption. Int. J. Netw. Secur. 2009, 8, 243–252. [Google Scholar]
- Machicao, J.; Bruno, O.M. A cryptographic hash function based on chaotic network automata. J. Phys. Conf. Ser. 2017, 936, 012058. [Google Scholar] [CrossRef]
- Hammad, B.T.; Jamil, N.; Rusli, M.E.; Z‘aba, M.R. A survey of Lightweight Cryptographic Hash Function. Int. J. Sci. Eng. Res. 2017. [Google Scholar]
- Parashar, D.; Roy, S.; Dey, N.; Jain, V.; Rawat, U.S. Symmetric key encryption technique: A cellular automata based approach. In Advances in Intelligent Systems and Computing; Elsevier: Amsterdam, The Netherlands, 2018; Available online: https://cyberleninka.org/article/n/622459 (accessed on 9 December 2022).
- Nguyen, L.H.; Roscoe, A.W. Short-output universal hash functions and their use in fast and secure data authentication. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2012. [Google Scholar]
- Zhang, X.; Xu, Q.; Li, X.; Wang, C. A Lightweight Hash Function Based on Cellular Automata for Mobile Network. In Proceedings of the 2019 15th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), Shenzhen, China, 11–13 December 2019; pp. 247–252. [Google Scholar] [CrossRef]
- El Rakaiby, M.M. Cryptographic Hash Function using Cellular Automata. Int. J. Comput. Appl. Technol. Res. 2016, 5, 238–240. [Google Scholar]
- Rajeshwaran, K.; Kumar, K.A. Cellular Automata Based Hashing Algorithm (CABHA) for Strong Crypto-graphic Hash Function. In Proceedings of the 2019 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, 20–22 February 2019; pp. 1–6. [Google Scholar]
- Goncu, E.; Kocdogan, A.; Yalcin, M.E. A High Speed True Random Number Generator with Cellular Automata with Random Memory. In Proceedings of the 2018 IEEE International Symposium on Circuits and Systems (ISCAS), Florence, Italy, 27–30 May 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Dogaru, R.; Dogaru, I. Efficient and cryptographically secure pseudorandom number generators based on chains of hybrid cellular automata maps. In Proceedings of the 2014 10th International Conference on Communications (COMM), Bucharest, Romania, 29–31 May 2014; pp. 1–4. [Google Scholar] [CrossRef]
- NIST. The Keyed-Hash Message Authentication Code; Federal Information Processing Standard Publication: Gaithersburg, MD, USA, 2008.
- Wang, Y.; Wong, K.; Liao, X.; Xiang, T. A Chaos Based Image Encryption Algotithm with Variable Control Parameter. Appl. Soft Comput. 2009. [Google Scholar]
- Xiao, D.; Liao, X.; Deng, S. One-way Hash function construction based on the chaotic map with changeable-parameter. Chaos Solitons Fractals 2005, 24, 65–71. [Google Scholar] [CrossRef]
- Li, Y.; Ge, G.; Xia, D. Chaotic hash function based on the dynamic S-Box with variable parameters. Nonlinear Dyn. 2016, 84, 2387–2402. [Google Scholar] [CrossRef]
- Teh, J.S.; Alawida, M.; Ho, J.J. Unkeyed hash function based on chaotic sponge construction and fixed-point arithmetic. Nonlinear Dyn. 2020, 100, 713–729. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, L.; Wang, X.; Wu, G.; Yu, K.; Lu, T. The design of keyed hash function based on CNN-MD structure. Chaos Solitons Fractals 2021, 152, 111443. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).