Secure One-Way Hash Function Using Cellular Automata for IoT
Abstract
:1. Introduction
- A CA-based hash function that inheres the simplicity and high speed computation of CA, and is suitable for a resource-constrained IoT environment is proposed.
- The utilization of sliding-window can promote the chaos of the scheme under relatively simple CA operations, and it promotes the chaos of the proposed scheme.
- Multilayer cellular automata operations further avalanche the effect of the hash function.
- The outperforming results are compared with other related works.
2. Preliminaries
2.1. Operation of Cellular Automata
2.2. Related Work
- Variable input size: Hash function H can be applied to a block of data of any size.
- Fixed output size: Hash function H produces a fixed-length output.
- Efficiency: Hash function H is relatively easy to compute for any given message x.
- Preimage resistant (one-way property): For any given h = H(x), it is infeasible to find y such that H(y) = h.
- Second preimage resistant (weak collision resistant): For any given block x, it is infeasible to find y ≠ x with H(y) = H(x).
- Collision resistant (strong collision resistance): It is infeasible to find any pair (x, y) such that H(y) = H(x).
- Pseudorandomness: Output of H meets standard tests for pseudorandomness.
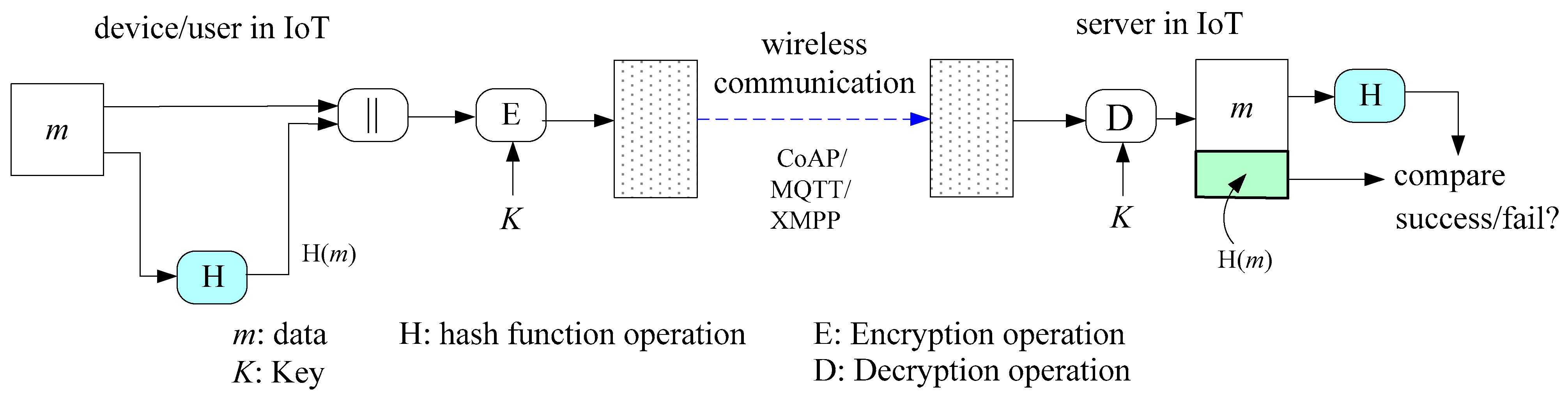
3. The Proposed SWCA-Based One-Way Hash Function
3.1. The Combination of Multiple CA Rules
3.2. Sliding-Window
3.3. Multi-Layer Cellular Automata
3.4. The Output of One-Way Hash Value
| Algorithm 1: Algorithm of SWCA based one-way hash function |
| Input: M (Message) , L bits (Message size) Output: h = 256 bits (Hash value) Begin //padding message p= ( L ) mod 256 if p ≠ 0 { PM = M || 1 || 0*(p−1) } // message division j = 1 i = 0 While (i < = size (PM)){ mj = PM[i : i+255] i += 256 j ++ } return mn = mj //main hash founction for( i = 1 ; i < n ; i ++){ Row_sliding = Sliding_512(mi ,mi+1) Row_CA = 5_layer_CA(Row_sliding) Mixed_row = mi ⊕ mi+1 ⊕ Row_CA mi = Mixed_row } return mi // 256 bits (Hash value) End |
4. Security Analysis and Experimental Results
4.1. Collision Analysis
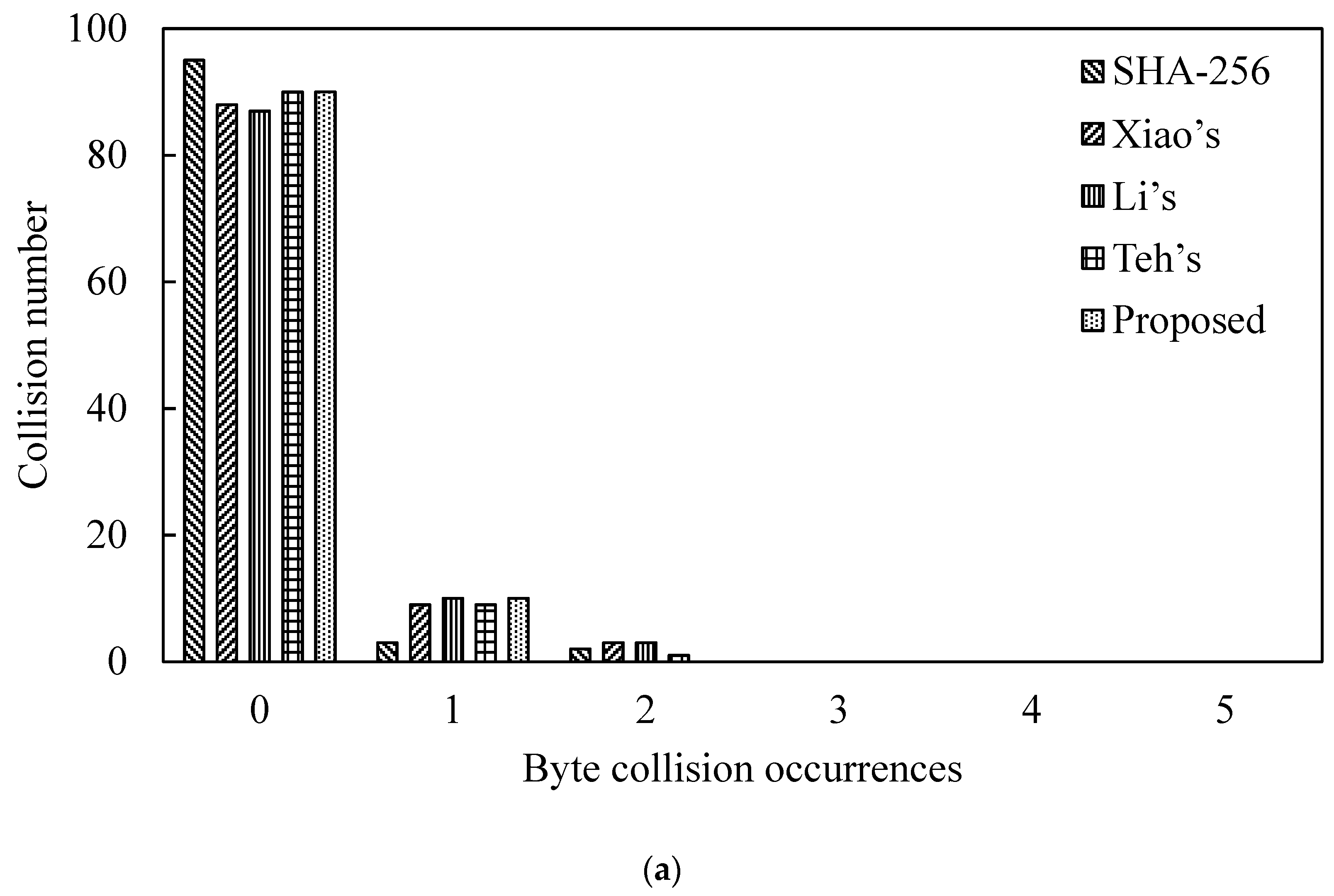
4.2. Analysis of Byte Collision Occurrences for Message Pair
4.3. Probabilistic Analysis of Byte Collision Occurrences
4.4. Statistical Analysis
4.5. Differential Attack
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Cao, B.; Sun, Z.; Zhang, J.; Gu, Y. Resource Allocation in 5G IoV Architecture Based on SDN and Fog-Cloud Computing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3832–3840. [Google Scholar] [CrossRef]
- Lv, Z.; Song, H. Mobile Internet of Things under Data Physical Fusion Technology. IEEE Internet Things J. 2020, 7, 4616–4624. [Google Scholar] [CrossRef]
- Lv, Z.; Chen, D.; Lou, R.; Song, H. Industrial Security Solution for Virtual Reality. IEEE Internet Things J. 2021, 8, 6273–6281. [Google Scholar] [CrossRef]
- Lv, Z.; Qiao, L.; Hossain, M.S.; Choi, B.J. Analysis of Using Blockchain to Protect the Privacy of Drone Big Data. IEEE Netw. 2021, 35, 44–49. [Google Scholar] [CrossRef]
- Akanksha, E.; Javali, A.; Jyoti. A review on Security in Internet of Things. In Proceedings of the 2022 IEEE World Conference on Applied Intelligence and Computing (AIC), Sonbhadra, India, 17–19 June 2022; pp. 883–887. [Google Scholar]
- Roy, S.; Bhatia, N.; Rawat, U.S. A Novel Cryptosystem Using Cellular Automata. In Proceedings of the 2017 International Conference on Communication and Signal Processing, Chennai, India, 6–8 April 2017; pp. 1781–1785. [Google Scholar]
- Wolfram, S. Cryptography with Cellular Automata. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1985. [Google Scholar]
- Chen, Q.; Dai, Y.; Niu, Z. An Image Encryption Algorithm Based on Combination of Chaos and DNA Encoding. In Proceedings of the 2020 International Conference on Computer Vision, Image and Deep Learning (CVIDL), Chongqing, China, 10–12 July 2020; pp. 182–185. [Google Scholar]
- Gonzalez, R.C.; Woods, R.E. Digital Image Processing, 3rd ed.; Prentice Hall: Hoboken, NJ, USA, 2008. [Google Scholar]
- Kumar, J. Novel and Efficient Cellular Automata Based Symmetric Key Encryption Algorithm for Wireless Sensor Networks. Int. J. Comput. Appl. 2010, 13, 1767–2424. [Google Scholar]
- Kumaravel, A.; Meetei, O.N. An application of non-uniform cellular automata for efficient cryptography. In Proceedings of the 2013 IEEE Conference on Information & Communication Technologies, Thuckalay, India, 11–12 April 2013; pp. 1200–1205. [Google Scholar] [CrossRef]
- Kerckhoffs, A. La Cryptographie Militaire. J. Des Sci. Mil. 1883, 9, 5–38. [Google Scholar]
- Stallings, W. Cryptography and Network Security: Principles and Practice, 6th ed.; Pearson: London, UK, 2014. [Google Scholar]
- Wolfram, S. A New Kind of Science; Wolfram-Research Inc: Champaign, IL, USA, 2002. [Google Scholar]
- Nandi, S.; Kar, B.K.; Chaudhuri, P.P. Theory and applications of cellular automata in cryptography. IEEE Trans. Comput. 1994, 43, 1346–1357. [Google Scholar] [CrossRef] [Green Version]
- Roy, S.; Rawat, U.; Karjee, J. A Lightweight Cellular Automata Based Encryption Technique for IoT Applications. IEEE Access 2019, 7, 39782–39793. [Google Scholar] [CrossRef]
- Rivest, R.L. RFC 1321: The MD5 Message-Digest Algorithm. MIT Laboratory for Computer Science and RSA Data Security, Inc. 1992. Available online: https://www.ietf.org/rfc/rfc1321.txt (accessed on 9 December 2022).
- HEM Infosec, Ltd. OWASP Top 10. 2021. Available online: https://www.heminfosec.com/eDM/2021-10-OWASPtop10-2021-WAPPLES-OSCAN.html (accessed on 9 December 2022).
- Hanin, C.; Echandouri, B.; Omary, F.; El Bernoussi, S. L-CAHASH: A novel lightweight hash function based on cellular automata for RFID. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Tripathy, S.; Nandi, S. LCASE: Lightweight cellular automata-based symmetric-key encryption. Int. J. Netw. Secur. 2009, 8, 243–252. [Google Scholar]
- Machicao, J.; Bruno, O.M. A cryptographic hash function based on chaotic network automata. J. Phys. Conf. Ser. 2017, 936, 012058. [Google Scholar] [CrossRef]
- Hammad, B.T.; Jamil, N.; Rusli, M.E.; Z‘aba, M.R. A survey of Lightweight Cryptographic Hash Function. Int. J. Sci. Eng. Res. 2017. [Google Scholar]
- Parashar, D.; Roy, S.; Dey, N.; Jain, V.; Rawat, U.S. Symmetric key encryption technique: A cellular automata based approach. In Advances in Intelligent Systems and Computing; Elsevier: Amsterdam, The Netherlands, 2018; Available online: https://cyberleninka.org/article/n/622459 (accessed on 9 December 2022).
- Nguyen, L.H.; Roscoe, A.W. Short-output universal hash functions and their use in fast and secure data authentication. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2012. [Google Scholar]
- Zhang, X.; Xu, Q.; Li, X.; Wang, C. A Lightweight Hash Function Based on Cellular Automata for Mobile Network. In Proceedings of the 2019 15th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), Shenzhen, China, 11–13 December 2019; pp. 247–252. [Google Scholar] [CrossRef]
- El Rakaiby, M.M. Cryptographic Hash Function using Cellular Automata. Int. J. Comput. Appl. Technol. Res. 2016, 5, 238–240. [Google Scholar]
- Rajeshwaran, K.; Kumar, K.A. Cellular Automata Based Hashing Algorithm (CABHA) for Strong Crypto-graphic Hash Function. In Proceedings of the 2019 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, 20–22 February 2019; pp. 1–6. [Google Scholar]
- Goncu, E.; Kocdogan, A.; Yalcin, M.E. A High Speed True Random Number Generator with Cellular Automata with Random Memory. In Proceedings of the 2018 IEEE International Symposium on Circuits and Systems (ISCAS), Florence, Italy, 27–30 May 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Dogaru, R.; Dogaru, I. Efficient and cryptographically secure pseudorandom number generators based on chains of hybrid cellular automata maps. In Proceedings of the 2014 10th International Conference on Communications (COMM), Bucharest, Romania, 29–31 May 2014; pp. 1–4. [Google Scholar] [CrossRef]
- NIST. The Keyed-Hash Message Authentication Code; Federal Information Processing Standard Publication: Gaithersburg, MD, USA, 2008.
- Wang, Y.; Wong, K.; Liao, X.; Xiang, T. A Chaos Based Image Encryption Algotithm with Variable Control Parameter. Appl. Soft Comput. 2009. [Google Scholar]
- Xiao, D.; Liao, X.; Deng, S. One-way Hash function construction based on the chaotic map with changeable-parameter. Chaos Solitons Fractals 2005, 24, 65–71. [Google Scholar] [CrossRef]
- Li, Y.; Ge, G.; Xia, D. Chaotic hash function based on the dynamic S-Box with variable parameters. Nonlinear Dyn. 2016, 84, 2387–2402. [Google Scholar] [CrossRef]
- Teh, J.S.; Alawida, M.; Ho, J.J. Unkeyed hash function based on chaotic sponge construction and fixed-point arithmetic. Nonlinear Dyn. 2020, 100, 713–729. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, L.; Wang, X.; Wu, G.; Yu, K.; Lu, T. The design of keyed hash function based on CNN-MD structure. Chaos Solitons Fractals 2021, 152, 111443. [Google Scholar] [CrossRef]














| CA Rule | Logical Operation |
|---|---|
| Rule 1 | |
| Rule 18 | |
| Rule 30 | |
| Rule 45 | |
| Rule 60 | |
| Rule 86 | |
| Rule 90 | |
| Rule 150 | |
| Rule 165 |
| (a) N = 100 | ||||||
| Byte Collision | ByteCollisionOccurrences | |||||
| 0 | 1 | 2 | 3 | 4 | 5 | |
| SHA-256 function | 95 | 3 | 2 | 0 | 0 | 0 |
| Xiao’s scheme [32] | 88 | 9 | 3 | 0 | 0 | 0 |
| Li’s scheme [33] | 87 | 10 | 3 | 0 | 0 | 0 |
| Je Sen Teh’s scheme [34] | 90 | 9 | 1 | 0 | 0 | 0 |
| Proposed hash function | 90 | 10 | 0 | 0 | 0 | 0 |
| (b) N = 1000 | ||||||
| SHA-256 function | 946 | 52 | 2 | 0 | 0 | 0 |
| Xiao’s scheme [32] | 935 | 60 | 5 | 0 | 0 | 0 |
| Li’s scheme [33] | 940 | 58 | 2 | 0 | 0 | 0 |
| Je Sen Teh’s scheme [34] | 941 | 58 | 1 | 0 | 0 | 0 |
| Proposed hash function | 946 | 53 | 1 | 0 | 0 | 0 |
| Probabilistic Analysis | Byte Collision Occurrences | |||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | 5 | |
| SHA-256 function | 94.7% | 4.5% | 0.8% | 0% | 0% | 0% |
| Xiao’s scheme [32] | 91.9% | 6.4% | 1.7% | 0% | 0% | 0% |
| Li’s scheme [33] | 91.9% | 7.1% | 1.0% | 0% | 0% | 0% |
| Je Sen Teh’s scheme [34] | 92.9% | 6.8% | 0.3% | 0% | 0% | 0% |
| Proposed hash function | 93.2% | 6.7% | 0.1% | 0% | 0% | 0% |
| N = 256 | N = 512 | N = 1024 | N = 2048 | Mean | |
|---|---|---|---|---|---|
| 128.26 | 128.42 | 128.16 | 128.08 | 128.23 | |
| P (%) | 50.08 | 49.93 | 49.91 | 50.11 | 50.01 |
| ΔB | 9.64 | 9.86 | 10.24 | 9.90 | 9.91 |
| ΔP (%) | 3.63 | 4.04 | 3.97 | 3.83 | 3.87 |
| Bmin | 99 | 100 | 102 | 102 | 100.8 |
| Bmax | 164 | 150 | 158 | 161 | 158.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, S.-T.; Chang, J.-R. Secure One-Way Hash Function Using Cellular Automata for IoT. Sustainability 2023, 15, 3552. https://doi.org/10.3390/su15043552
Wu S-T, Chang J-R. Secure One-Way Hash Function Using Cellular Automata for IoT. Sustainability. 2023; 15(4):3552. https://doi.org/10.3390/su15043552
Chicago/Turabian StyleWu, Shyi-Tsong, and Jieh-Ren Chang. 2023. "Secure One-Way Hash Function Using Cellular Automata for IoT" Sustainability 15, no. 4: 3552. https://doi.org/10.3390/su15043552





