The Integration of WoT and Edge Computing: Issues and Challenges
Abstract
1. Introduction
2. Review of WoT and Edge Computing
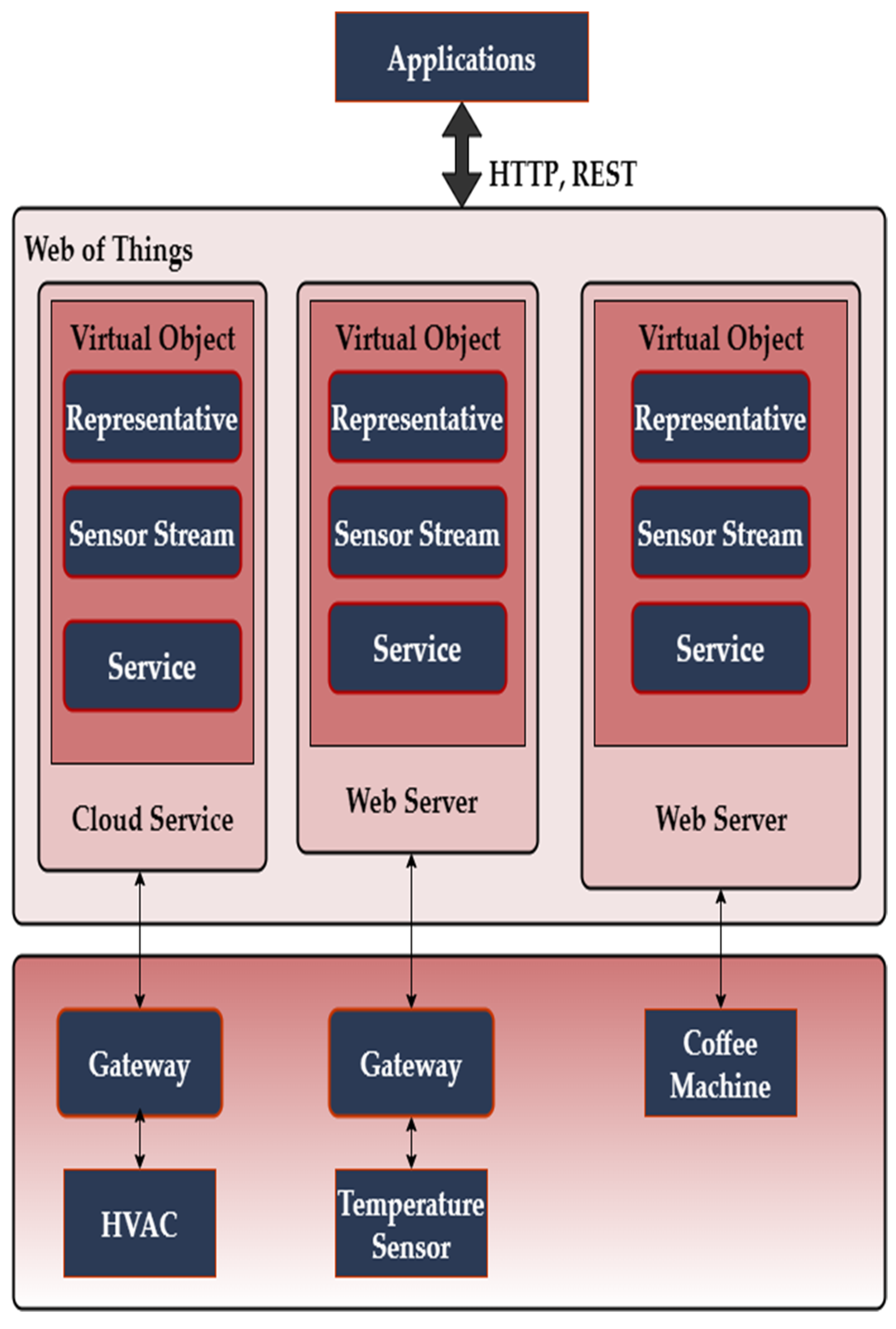
2.1. Web of Things
| Author Name | Working of Authors | Citations of Paper |
|---|---|---|
| (Baraković, S., et al., 2020) | Examine the connections and interactions between quality of life (QoL), quality of experience (QoE), perceptions of safety, and the variables affecting those perceptions. | [20] |
| (Niwarlangga, A.C. and M.Z.C. Candra. 2020) | It focuses on creating a framework for Semantic Web of Things applications that maximizes productivity while creating Semantic Web of Things applications. | [21] |
| (Datta, S.K. and C. Bonnet. 2018) | A list of WoT components that provide communication between two IoT systems. | [22] |
| (Kamilaris, A., et al., 2017) | Create an ecosystem for urban computing that blends the network of things idea with big data analytics and event processing in order to realize the goal of creating smarter cities that provide their citizens with real-time information about the city. | [23] |
| (Younan, M., S. Khattab, and R. Bahgat, 2021) | Provide an overview of wireless sensor networks (WSNs), the Internet of Things, and its future paradigm (WoT) with a discussion of key elements, major layers, major challenges, and annotation formats | [24] |
| (Cimmino, A., M. Poveda-Villalón, and R. García-Castro, 2020) | It provides a mechanism based on SPARQL queries to transparently discover and access IoT devices that publish heterogeneous data. | [25] |
| (Premkumar, M., et al., 2022) | To identify malicious behaviors in WoT, such as normal, botnet, brute force, DoS/DDoS, infiltration, port scans, and web assaults, an intrusion detection system based on deep belief networks is used. | [26] |
| (Parwej, F., N. Akhtar, and Y. Perwej, 2019) | Provide a thorough overview of the Web of Things, including its architecture, open platform, devices that make it possible, security measures it takes, and use cases. | [27] |
| (Sciullo, L., et al., 2019) | Authors proposed a WoT Store, a novel platform for managing and easing the deployment of Things and applications on the W3C WoT. | [28] |
| (Vanden Hautte, S., et al., 2020) | Demonstrate a dynamic dashboard that fixes these problems. As long as a RESTful Web of Things compatible gateway is available, sensors, visualizations, and aggregations may be automatically found. | [29] |
2.2. Integration Pattern for Connecting Things to Web
2.2.1. Direct Integration
2.2.2. Gateway Integration
2.2.3. Cloud Integration
2.3. Edge Computing
2.3.1. Edge Computing Architecture
2.3.2. Cloud
2.3.3. Edge Device
2.3.4. Edge Node
2.3.5. Edge Cluster/Server
2.3.6. Edge Gateway
2.3.7. Edge Computing Implementation
- Hierarchical Model: The edge structure is divided into categories, defining resources and functions based on distance, considering that edge/cloudlet servers might be utilized by end users in various locations. As a result, the hierarchical model must specify the edge computing network’s topology. Numerous studies on the hierarchical model have been conducted. In [48] for instance, a phased paradigm using Mobile edge computing (MEC) servers and cloud infrastructure was developed. Because the MEC enables them to meet their computational and storage demands, mobile users in this model may access the services they have requested. Tong, L., Y. Li, and W. Gao in [49] has proposed a cloud-based methodology that may be utilized to deliver the required loads for mobile users. In this concept, the terminal servers are utilized in conjunction with a regional edge cloud that is constructed as a tree configuration and used cloudlet servers at the network edge. The computing capabilities of peripheral servers may be reconstructed to handle heavy loads by adopting this design procedure [50].
- Software Defined Model: Additionally, maintaining IoT and edge computing will be quite challenging given that hundreds of apps with millions of users and end devices have been involved. IT management complexity may be successfully addressed by Software Defined Networking (SDN) [51,52,53,54]. The SDN model has been the subject of several research projects. For example, in [53], the capabilities of MEC systems with software-defined systems provide a suitable software model. Costs related to management and administration might be decreased in this way as mentioned by Du, P. and A. Nakao in [54]. In order to merge the capabilities of MEC systems with software-defined systems, a special software model should be proposed. Management and administrative costs might be decreased in this way. Authors in [55] presented a cutting-edge operating system that strengthens network and service platforms by utilizing freely accessible open-source technologies. Salman, O., et al. in [56] planned to combine three novel ideas: Network Functions Virtualization, Software Defined Networking (SDN), and MEC. The system may then be scaled up to support IoT deployments anywhere while achieving the highest MEC performance on the mobile network. Lin, T., et al. in [57] offer the creation of intelligent applications within the Software Defined Virtual infrastructure of the smart edge frameworks, which may be utilized to facilitate the creation of a broad variety of distributed network resources and applications.
3. Integration of Wot and Edge Computing
3.1. Overview
3.2. WoT Performance Demands
3.2.1. Transmission
3.2.2. Storage
3.2.3. Computation
- Use software emulation to provide support for earlier descriptions of objects on modern devices.
- Offer innovative, potent multipurpose gadgets that can handle a variety of Things’ Descriptions.
- Let older and newer versions of devices coexist in a device.
- Protect current software from modifications.
4. Challenges and Advantages of Edge Computing and WoT
4.1. Challenges of Web of Things
4.1.1. Search and Discovery of Smart Things
4.1.2. Data Inconsistency
4.1.3. Security
4.1.4. IoT Protocol
4.1.5. Identity Verification
4.1.6. Resilience
4.1.7. Things and Avatars
4.1.8. Smart Searches
4.1.9. Legal Implications
4.2. Advantages of Web of Things
4.2.1. Current Open Ecosystem
4.2.2. Home Hubs
- Configuration by the user of the device before starting to use the service
- ○
- The user of the device logs in to the server of the “Household Management Service Provider” with which the user has a contract.
- ○
- The user specifies the lighting, air conditioning, and security sensor operating modes for when the user is away from home, when the user returns home, and when the specified time has elapsed after the user returned home.
- When the device user leaves home
- ○
- The user of the device accesses the server of the “Home Management Service Provider” using a smartphone and informs the server that the user is about to leave the home.
- ○
- The server updates the operating modes of the lighting, air conditioning, and security sensor according to the configuration entered by the user during the time when the user is away from home.
- ○
- The server reads the operating modes of the lighting, air conditioning, and security sensor and informs the user’s smartphone about these operating modes.
4.2.3. Cloud Platforms
4.2.4. Standard Vocabularies and Repository
4.2.5. Monetizing
4.2.6. Cyber Physical Systems
4.3. Challenges of Edge Computing
4.3.1. Bandwidth
4.3.2. Latency
4.3.3. Energy
4.3.4. Cost
4.4. Advantages of Edge Computing
4.4.1. Distributed Computing
4.4.2. Security and Accessibility
4.4.3. Backup
4.4.4. Data Accumulation
4.4.5. Control and Management
4.4.6. Scale
5. Future Challenges
- Data Management: Handling the massive amounts of data generated by IoT devices and ensuring their timely and efficient processing at the edge is a major challenge [86].
- Security: Ensuring the security of IoT devices and the data they generate is a critical challenge, as these devices are often vulnerable to hacking and cyber-attacks [87,88,89]. Another problem is that the integration of smart things into the standard Internet introduces additional security challenges because the majority of Internet technologies and communication protocols were not designed to support Internet of Things [90].
- Interoperability: Ensuring interoperability between different IoT devices and edge computing systems is a challenge, as it requires standardization and common protocols [91].
- Scalability: Scaling edge computing systems to meet the demands of growing IoT networks is a challenge, as it requires efficient resource utilization and effective management [92].
- Latency: Reducing latency in IoT networks and edge computing systems is a challenge, as it requires efficient data processing and communication [93].
- Energy Efficiency: Ensuring energy efficiency in IoT devices and edge computing systems is a challenge, as it requires energy-saving algorithms and strategies [94].
- Cost Effectiveness: Ensuring cost-effectiveness in IoT and edge computing systems is a challenge, as it requires efficient resource utilization and effective cost management [97].
- Searching resources in WoT is also a big challenge, especially dynamic searching and intent based searching [63]. Many physical objects (Things) are connected to the internet and are accessible through a web interface, and efficient searching of Things is required as there is a significant increase in IoT devices [98]. Searching of suitable Things from billions of device is also difficult because of multiple Things performing the same functionality, but some devices are near to the user or free at some time which can respond more accurately and efficiently which depends upon the selection of the right Thing [99].
6. Conclusions and Future Remarks
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Corcoran, P.; Datta, S.K. Mobile-edge computing and the internet of things for consumers: Extending cloud computing and services to the edge of the network. IEEE Consum. Electron. Mag. 2016, 5, 73–74. [Google Scholar] [CrossRef]
- Vallati, C.; Virdis, A.; Mingozzi, E.; Stea, G. Mobile-edge computing come home connecting things in future smart homes using LTE device-to-device communications. IEEE Consum. Electron. Mag. 2016, 5, 77–83. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Buyya, R. Fog computing: Helping the Internet of Things realize its potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Georgakopoulos, D.; Jayaraman, P.P.; Fazia, M.; Villari, M.; Ranjan, R. Internet of Things and edge cloud computing roadmap for manufacturing. IEEE Cloud Comput. 2016, 3, 66–73. [Google Scholar] [CrossRef]
- Jutila, M. An adaptive edge router enabling internet of things. IEEE Internet Things J. 2016, 3, 1061–1069. [Google Scholar] [CrossRef]
- Sabella, D.; Vaillant, A.; Kuure, P.; Rauschenbach, U.; Giust, F. Mobile-edge computing architecture: The role of MEC in the Internet of Things. IEEE Consum. Electron. Mag. 2016, 5, 84–91. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Frankston, B. Mobile-Edge Computing versus The Internet?: Looking beyond the literal meaning of MEC. IEEE Consum. Electron. Mag. 2016, 5, 75–76. [Google Scholar] [CrossRef]
- Garcia Lopez, P.; Montresor, A.; Epema, D.; Datta, A.; Higashino, T.; Iamnitchi, A.; Barcellos, M.; Felber, P.; Riviere, E. Edge-Centric Computing: Vision and Challenges. ACM SIGCOMM Comput. Commun. Rev. 2015, 45, 37–42. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A Survey on the Edge Computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar]
- Li, H.; Shou, G.; Hu, Y.; Guo, Z. Mobile edge computing: Progress and challenges. In Proceedings of the 2016 4th IEEE International Conference on Mobile Cloud Computing, Services and Engineering (MobileCloud), Oxford, UK, 29 March–1 April 2016. [Google Scholar]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutor. 2017, 19, 1628–1656. [Google Scholar] [CrossRef]
- Hatcher, W.G.; Booz, J.; McGiff, J.; Lu, C.; Yu, W. Edge Computing Based Machine Learning Mobile Malware Detection. 2017. Available online: https://www.google.com.hk/search?q=Edge+computing+based+machine+learning+mobile+malware+detection&ei=hNIXZJnlE7S6seMPys-EgAU&ved=0ahUKEwiZt-7_x-n9AhU0XWwGHconAVAQ4dUDCA4&uact=5&oq=Edge+computing+based+machine+learning+mobile+malware+detection&gs_lcp=Cgxnd3Mtd2l6LXNlcnAQA0oECEEYAFAAWABg_AVoAHABeACAAW6IAW6SAQMwLjGYAQCgAQKgAQHAAQE&sclient=gws-wiz-serp (accessed on 27 February 2023).
- Christophe, B.; Boussard, M.; Lu, M.; Pastor, A.; Toubiana, V. The web of things vision: Things as a service and interaction patterns. Bell Labs Tech. J. 2011, 16, 55–61. [Google Scholar] [CrossRef]
- Duquennoy, S.; Grimaud, G.; Vandewalle, J.-J. The web of things: Interconnecting devices with high usability and performance. In Proceedings of the 2009 International Conference on Embedded Software and Systems, Hangzhou, China, 25–27 May 2009; IEEE: Piscataway, NJ, USA, 2009. [Google Scholar]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Stirbu, V. Towards a restful plug and play experience in the web of things. In Proceedings of the 2008 IEEE International Conference on Semantic Computing, Santa Monica, CA, USA, 4–7 August 2008; IEEE: Piscataway, NJ, USA, 2008. [Google Scholar]
- Baraković, S.; Baraković Husić, J.; Maraj, D.; Maraj, A.; Krejcar, O.; Maresova, P.; Melero, F.J. Quality of life, quality of experience, and security perception in web of things: An overview of research opportunities. Electronics 2020, 9, 700. [Google Scholar] [CrossRef]
- Niwarlangga, A.C.; Candra, M.Z.C. Application framework for semantic web of things. In Proceedings of the 2020 7th International Conference on Advance Informatics: Concepts, Theory and Applications (ICAICTA), Online, 8–9 September 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Datta, S.K.; Bonnet, C. Advances in web of things for IoT interoperability. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Taichung, Taiwan, 19–21 May 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar]
- Kamilaris, A.; Pitsillides, A.; Prenafeta-Bold, F.X.; Ali, M.I. A Web of Things based eco-system for urban computing-towards smarter cities. In Proceedings of the 2017 24th International Conference on Telecommunications (ICT), Limassol, Cyprus, 3–5 May 2017; IEEE: Piscataway, NJ, USA, 2017. [Google Scholar]
- Younan, M.; Khattab, S.; Bahgat, R. From the wireless sensor networks (WSNs) to the Web of Things (WoT): An overview. J. Intell. Syst. Internet Things 2021, 4, 56–68. [Google Scholar] [CrossRef]
- Cimmino, A.; Poveda-Villalón, M.; García-Castro, R. eWoT: A semantic interoperability approach for heterogeneous iot ecosystems based on the web of things. Sensors 2020, 20, 822. [Google Scholar] [CrossRef]
- Premkumar, M.; Ashokkumar, S.R.; Mohanbabu, G.; Jeevanantham, V.; Jayakumar, S. Security behavior analysis in web of things smart environments using deep belief networks. Int. J. Intell. Netw. 2022, 3, 181–187. [Google Scholar] [CrossRef]
- Parwej, F.; Akhtar, N.; Perwej, Y. An empirical analysis of web of things (WOT). Int. J. Adv. Res. Comput. Sci. 2019, 10, 32–40. [Google Scholar] [CrossRef]
- Sciullo, L.; Gigli, L.; Trotta, A.; Di Felice, M. WoT Store: Managing resources and applications on the web of things. Internet Things 2020, 9, 100164. [Google Scholar] [CrossRef]
- Vanden Hautte, S.; Moens, P.; Van Herwegen, J.; De Paepe, D.; Steenwinckel, B.; Verstichel, S.; Ongenae, F.; Van Hoecke, S. A dynamic dashboarding application for fleet monitoring using semantic web of things technologies. Sensors 2020, 20, 1152. [Google Scholar] [CrossRef] [PubMed]
- Pastor-Vargas, R.; Tobarra, L.; Robles-Gómez, A.; Martin, S.; Hernández, R.; Cano, J. A wot platform for supporting full-cycle iot solutions from edge to cloud infrastructures: A practical case. Sensors 2020, 20, 3770. [Google Scholar] [CrossRef]
- Marsh-Hunn, D.; Trilles, S.; González-Pérez, A.; Torres-Sospedra, J.; Ramos, F. A Comparative Study in the Standardization of IoT Devices Using Geospatial Web Standards. IEEE Sensors J. 2020, 21, 5512–5528. [Google Scholar] [CrossRef]
- Vresk, T.; Čavrak, I. Architecture of an interoperable IoT platform based on microservices. In Proceedings of the 2016 39th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 30 May–3 June 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Trilles, S.; Calia, A.; Belmonte, Ó.; Torres-Sospedra, J.; Montoliu, R.; Huerta, J. Deployment of an open sensorized platform in a smart city context. Futur. Gener. Comput. Syst. 2017, 76, 221–233. [Google Scholar] [CrossRef]
- Huang, C.Y.; Wu, C.H. Design and implement an interoperable Internet of Things application based on an extended OGC sensorthings API Standard. In Proceedings of the The International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Prague, Czech Republic, 12–19 July 2016. [Google Scholar]
- Trilles, S.; Torres-Sospedra, J.; Belmonte, Ó.; Zarazaga-Soria, F.J.; González-Pérez, A.; Huerta, J. Development of an open sensorized platform in a smart agriculture context: A vineyard support system for monitoring mildew disease. Sustain. Comput. Inform. Syst. 2020, 28, 100309. [Google Scholar] [CrossRef]
- Kotsev, A.; Schleidt, K.; Liang, S.; Van der Schaaf, H.; Khalafbeigi, T.; Grellet, S.; Lutz, M.; Jirka, S. Extending INSPIRE to the Internet of Things through SensorThings API. Geosciences 2018, 8, 221. [Google Scholar] [CrossRef]
- Kotsev, A.; Minghini, M.; Tomas, R.; Cetl, V.; Lutz, M. From spatial data infrastructures to data spaces—A technological perspective on the evolution of European SDIs. ISPRS Int. J. Geo-Inf. 2020, 9, 176. [Google Scholar] [CrossRef]
- Granell, C.; Kamilaris, A.; Kotsev, A.; Ostermann, F.O.; Trilles, S. Internet of things. In Manual of Digital Earth; Springer Singapore: Singapore, 2020; pp. 387–423. [Google Scholar]
- Trilles, S.; Luján, A.; Belmonte, Ó.; Montoliu, R.; Torres-Sospedra, J.; Huerta, J. SEnviro: A sensorized platform proposal using open hardware and open standards. Sensors 2015, 15, 5555–5582. [Google Scholar] [CrossRef]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An overview on edge computing research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Porambage, P.; Okwuibe, J.; Liyanage, M.; Ylianttila, M.; Taleb, T. Survey on multi-access edge computing for internet of things realization. IEEE Commun. Surv. Tutor. 2018, 20, 2961–2991. [Google Scholar] [CrossRef]
- Sha, K.; Yang, T.A.; Wei, W.; Davari, S. A survey of edge computing-based designs for IoT security. Digit. Commun. Netw. 2020, 6, 195–202. [Google Scholar] [CrossRef]
- Ahmed, E.; Rehmani, M.H. Mobile Edge Computing: Opportunities, Solutions, and Challenges; Elsevier: Amsterdam, The Netherlands, 2017; pp. 59–63. [Google Scholar]
- Pan, J.; McElhannon, J. Future edge cloud and edge computing for internet of things applications. IEEE Internet Things J. 2017, 5, 439–449. [Google Scholar] [CrossRef]
- Premsankar, G.; Di Francesco, M.; Taleb, T. Edge computing for the Internet of Things: A case study. IEEE Internet Things J. 2018, 5, 1275–1284. [Google Scholar] [CrossRef]
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward edge intelligence: Multiaccess edge computing for 5G and Internet of Things. IEEE Internet Things J. 2020, 7, 6722–6747. [Google Scholar] [CrossRef]
- Hamdan, S.; Ayyash, M.; Almajali, S. Edge-computing architectures for internet of things applications: A survey. Sensors 2020, 20, 6441. [Google Scholar] [CrossRef]
- Jararweh, Y.; Doulat, A.; AlQudah, O.; Ahmed, E.; Al-Ayyoub, M.; Benkhelifa, E. The future of mobile cloud computing: Integrating cloudlets and mobile edge computing. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Tong, L.; Li, Y.; Gao, W. A hierarchical edge cloud architecture for mobile computing. In Proceedings of the IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Ahmed, E.; Akhunzada, A.; Whaiduzzaman, M.; Gani, A.; Ab Hamid, S.H.; Buyya, R. Network-Centric Performance Analysis of Runtime Application Migration in Mobile Cloud Computing. Simul. Model. Pract. Theory 2015, 50, 42–56. [Google Scholar] [CrossRef]
- Wang, G.; Zhao, Y.; Huang, J.; Wang, W. The controller placement problem in software defined networking: A survey. IEEE Netw. 2017, 31, 21–27. [Google Scholar] [CrossRef]
- Zhu, D.; Yang, X.; Zhao, P.; Yu, W. Towards effective intra-flow network coding in software defined wireless mesh networks. In Proceedings of the 2015 24th International Conference on Computer Communication and Networks (ICCCN), Las Vegas, NV, USA, 3–6 August 2015; IEEE: Piscataway, NJ, USA, 2015. [Google Scholar]
- Jararweh, Y.; Doulat, A.; Darabseh, A.; Alsmirat, M.; Al-Ayyoub, M.; Benkhelifa, E. SDMEC: Software defined system for mobile edge computing. In Proceedings of the 2016 IEEE international conference on cloud engineering workshop (IC2EW), Berlin, Germany, 4–8 April 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Du, P.; Nakao, A. Application specific mobile edge computing through network softwarization. In Proceedings of the 2016 5th IEEE International Conference on Cloud Networking (Cloudnet), Pisa, Italy, 3–5 October 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Manzalini, A.; Crespi, N. An edge operating system enabling anything-as-a-service. IEEE Commun. Mag. 2016, 54, 62–67. [Google Scholar] [CrossRef]
- Salman, O.; Elhajj, I.; Kayssi, A.; Chehab, A. Edge computing enabling the Internet of Things. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 603–608. [Google Scholar]
- Lin, T.; Park, B.; Bannazadeh, H.; Leon-Garcia, A. Demo abstract: End-to-end orchestration across SDI smart edges. In Proceedings of the 2016 IEEE/ACM Symposium on edge computing (SEC), Washington, DC, USA, 27–28 October 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog computing: A platform for internet of things and analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Springer: Berlin/Heidelberg, Germany, 2014; pp. 169–186. [Google Scholar]
- Jiang, H.; Shen, F.; Chen, S.; Li, K.-C.; Jeong, Y.-S. A secure and scalable storage system for aggregate data in IoT. Futur. Gener. Comput. Syst. 2015, 49, 133–141. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an analysis of security issues, challenges, and open problems in the internet of things. In Proceedings of the 2015 IEEE world congress on services, New York, NY, USA, 27 June–2 July 2015; IEEE: Piscataway, NJ, USA, 2015. [Google Scholar]
- Yang, X.; Wang, T.; Ren, X.; Yu, W. Survey on improving data utility in differentially private sequential data publishing. IEEE Trans. Big Data 2017, 7, 729–749. [Google Scholar] [CrossRef]
- Guinard, D.; Trifa, V.; Wilde, E. A resource oriented architecture for the web of things. In Proceedings of the 2010 Internet of Things (IOT), Tokyo, Japan, 29 November–1 December 2010; IEEE: Piscataway, NJ, USA, 2010. [Google Scholar]
- Faheem, M.R.; Anees, T.; Hussain, M. The Web of Things: Findability Taxonomy and Challenges. IEEE Access 2019, 7, 185028–185041. Available online: https://ieeexplore.ieee.org/abstract/document/8935107 (accessed on 27 February 2023). [CrossRef]
- Sardar, R.; Anees, T. Web of Things: Security Challenges and Mechanisms. IEEE Access 2021, 9, 31695–31711. [Google Scholar] [CrossRef]
- Ostermaier, B.; Römer, K.; Mattern, F.; Fahrmair, M.; Kellerer, W. A real-time search engine for the web of things. In Proceedings of the 2010 Internet of Things (IOT), Tokyo, Japan, 29 November–1 December 2010; IEEE: Piscataway, NJ, USA, 2010. [Google Scholar]
- Wang, H.; Tan, C.C.; Li, Q. Snoogle: A search engine for pervasive environments. IEEE Trans. Parallel Distrib. Syst. 2009, 21, 1188–1202. [Google Scholar] [CrossRef]
- Tan, C.C.; Sheng, B.; Wang, H.; Li, Q. Microsearch: When search engines meet small devices. In Proceedings of the Pervasive Computing: 6th International Conference, Pervasive 2008, Sydney, Australia, 19–22 May 2008; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Yap, K.-K.; Srinivasan, V.; Motani, M. Max: Human-centric search of the physical world. In Proceedings of the 3rd international conference on Embedded networked sensor systems, San Diego, CA, USA, 2–4 November 2005; pp. 166–179. [Google Scholar]
- Blanco, J.M.; Ge, M.; Pitner, T. Modeling Inconsistent Data for Reasoners in Web of Things. Procedia Comput. Sci. 2021, 192, 1265–1273. [Google Scholar] [CrossRef]
- Schneier, B. The internet of things is wildly insecure-and often unpatchable. Schneier Secur. 2014, 6. Available online: https://www.wired.com/2014/01/theres-no-good-way-to-patch-the-internet-of-things-and-thats-a-huge-problem/ (accessed on 27 February 2023).
- Kim, H. Protection against packet fragmentation attacks at 6LoWPAN adaptation layer. In Proceedings of the 2008 International conference on convergence and hybrid information technology, Daejeon, Republic of Korea, 28–30 August 2008; IEEE: Piscataway, NJ, USA, 2008. [Google Scholar]
- Chen, G.; Yau, N.; Hansen, M.; Estrin, D. Sharing Sensor Network Data; UCLA: Center for Embedded Network Sensing: Los Angeles, CA, USA, 2007. [Google Scholar]
- Guinard, D.; Trifa, V. Towards the web of things: Web mashups for embedded devices. In Proceedings of the Workshop on Mashups, Enterprise Mashups and Lightweight Composition on the Web (MEM 2009), Madrid, Spain, 20 April 2009. [Google Scholar]
- Lin, X.; Andrews, J.G.; Ghosh, A.; Ratasuk, A. An overview of 3GPP device-to-device proximity services. IEEE Commun. Mag. 2014, 52, 40–48. [Google Scholar] [CrossRef]
- Greenberg, A.; Hamilton, J.; Maltz, D.A.; Patel, P. The Cost of a Cloud: Research Problems in Data Center Networks; ACM: New York, NY, USA, 2008; pp. 68–73. [Google Scholar]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I. A view of cloud computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef]
- Alam, Q.; Malik, S.U.; Akhunzada, A.; Choo, K.-K.R.; Tabbasum, S.; Alam, M. A Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification. IEEE Trans. Inf. Forensics Secur. 2016, 12, 1259–1268. [Google Scholar] [CrossRef]
- Jackson, K.R.; Ramakrishnan, L.; Muriki, K.; Canon, S.; Cholia, S.; Shalf, J.; Wasserman, H.J.; Wright, N.J. Performance analysis of high performance computing applications on the amazon web services cloud. In Proceedings of the 2010 IEEE Second International Conference on Cloud Computing Technology and Science, Indianapolis, IN, USA, 30 November–3 December 2010; IEEE: Piscataway, NJ, USA, 2010. [Google Scholar]
- Li, A.; Yang, X.; Kandula, S.; Zhang, M. CloudCmp: Comparing public cloud providers. In Proceedings of the 10th ACM SIGCOMM conference on Internet measurement, Melbourne, Australia, 1–30 November 2010. [Google Scholar]
- Wadhwa, H.; Aron, R. TRAM: Technique for Resource Allocation and Management in Fog Computing Environment. J. Supercomput. 2022, 78, 667–690. [Google Scholar] [CrossRef]
- Hussain, S.M.; Wahid, A.; Shah, M.A.; Akhunzada, A.; Khan, F.; ul Amin, N.; Arshad, S.; Ali, I. Seven Pillars to Achieve Energy Efficiency in High-Performance Computing Data Centers. In Recent Trends and Advances in Wireless and IoT-Enabled Networks; Springer International Publishing: Cham, Switzerland, 2019. [Google Scholar]
- Satyanarayanan, M. Mobile computing: The next decade. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2011, 15, 2–10. [Google Scholar] [CrossRef]
- Miettinen, A.P.; Nurminen, J.K. Energy efficiency of mobile clients in cloud computing. In Proceedings of the 2nd USENIX Workshop on Hot Topics in Cloud Computing (HotCloud 10), Boston, MA, USA, 22–25 June 2010. [Google Scholar]
- Chun, B.-G.; Ihm, S.; Maniatis, P.; Naik, M.; Patti, A. Clonecloud: Elastic execution between mobile device and cloud. In Proceedings of the Sixth Conference on Computer Systems, Alzburg, Austria, 10–13 April 2011. [Google Scholar]
- Ding, N.; Wagner, D.; Chen, X.; Pathak, A.; Hu, Y.C.; Rice, A. Characterizing and modeling the impact of wireless signal strength on smartphone battery drain. ACM SIGMETRICS Perform. Eval. Rev. 2013, 41, 29–40. [Google Scholar] [CrossRef]
- Ma, M.; Wang, P.; Chu, C.-H. Data management for internet of things: Challenges, approaches and opportunities. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- Toor, A.; ul Islam, S.; Sohail, N.; Akhunzada, A.; Boudjadar, J.; Khattak, H.A.; Din, I.U.; Rodrigues, J.J. Energy and Performance Aware Fog Computing: A Case of DVFS and Green Renewable Energy. Future Gener. Comput. Syst. 2019, 101, 1112–1121. [Google Scholar] [CrossRef]
- Khan, M.T.; Akhunzada, A.; Zeadally, S. Proactive Defense for Fog-to-Things Critical Infrastructure. IEEE Commun. Mag. 2022, 60, 44–49. [Google Scholar] [CrossRef]
- Khan, W.Z.; Rafique, W.; Haider, N.; Hakak, S.; Imran, M. Internet of Everything: Enabling Technologies, Applications, Security and Challenges. 2022. Available online: https://www.techrxiv.org/articles/preprint/Internet_of_Everything_Enabling_Technologies_Applications_Security_and_Challenges/21341796 (accessed on 27 February 2023).
- Mosenia, A.; Jha, N.K. A comprehensive study of security of internet-of-things. IEEE Trans. Emerg. Top. Comput. 2016, 5, 586–602. [Google Scholar] [CrossRef]
- Noura, M.; Atiquzzaman, M.; Gaedke, M. Interoperability in internet of things: Taxonomies and open challenges. Mob. Netw. Appl. 2019, 24, 796–809. [Google Scholar] [CrossRef]
- Gupta, A.; Christie, R.; Manjula, R. Scalability in internet of things: Features, techniques and research challenges. Int. J. Comput. Intell. Res. 2017, 13, 1617–1627. [Google Scholar]
- Shukla, S.; Hassan, M.F.; Tran, D.C.; Akbar, R.; Paputungan, I.V.; Khan, M.K. Improving latency in Internet-of-Things and cloud computing for real-time data transmission: A systematic literature review (SLR). Clust. Comput. 2021, 1–24. [Google Scholar] [CrossRef]
- Liu, C.H.; Fan, J.; Branch, J.W.; Leung, K.K. Toward QoI and energy-efficiency in Internet-of-Things sensory environments. IEEE Trans. Emerg. Top. Comput. 2014, 2, 473–487. [Google Scholar] [CrossRef]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of cloud computing and internet of things: A survey. Futur. Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Haghi Kashani, M.; Rahmani, A.M.; Jafari Navimipour, N. Quality of Service-Aware Approaches in Fog Computing. Int. J. Commun. Syst. 2020, 33, e4340. [Google Scholar] [CrossRef]
- Febrer, N.; Folkvord, F.; Lupiañez-Villanueva, F. Cost-effectiveness assessment of internet of things in smart cities. Front. Digit. Health 2021, 3, 662874. [Google Scholar] [CrossRef] [PubMed]
- Faheem, M.R.; Anees, T.; Hussain, M. Development of a Novel Ranking Mechanism and Search Engine in Web of Things; OSF: Galesburg, IL, USA, 2022. [Google Scholar]
- Faheem, M.R.; Anees, T.; Hussain, M. Keywords and Spatial Based Indexing for Searching the Things on Web. KSII Trans. Internet Inf. Syst. 2022, 16, 1489–1515. [Google Scholar]
- Ahmed, E.; Gani, A.; Sookhak, M.; Ab Hamid, S.H.; Xia, F. Application optimization in mobile cloud computing: Motivation, taxonomies, and open challenges. J. Netw. Comput. Appl. 2015, 52, 52–68. [Google Scholar] [CrossRef]
- Yang, R.; Yu, F.R.; Si, P.; Yang, Z.; Zhang, Y. Integrated blockchain and edge computing systems: A survey, some research issues and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 1508–1532. [Google Scholar] [CrossRef]
- Khan, W.Z.; Aalsalem, M.Y.; Khan, M.K.; Arshad, Q. Data and privacy: Getting consumers to trust products enabled by the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 8, 35–38. [Google Scholar] [CrossRef]
- Hussein, N.; Nhlabatsi, A. Living in the Dark: MQTT-Based Exploitation of IoT Security Vulnerabilities in ZigBee Networks for Smart Lighting Control. IoT 2022, 3, 450–472. [Google Scholar] [CrossRef]
- Al-Roomi, M.; Al-Ebrahim, S.; Buqrais, S.; Ahmad, I. Cloud computing pricing models: A survey. Int. J. Grid Distrib. Comput. 2013, 6, 93–106. [Google Scholar] [CrossRef]
- Bertolli, C.; Buono, D.; Mencagli, G.; Torquati, M.; Vanneschi, M.; Mordacchini, M.; Nardini, F.M. Resource discovery support for time-critical adaptive applications. In Proceedings of the 6th International Wireless Communications and Mobile Computing Conference, Caen, France, 28 June–2 July 2010. [Google Scholar]
- Kientopf, K.; Raza, S.; Lansing, S.; Güneş, M. Service Management Platform to Support Service Migrations for IoT Smart City Applications. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Kirci, P. Ubiquitous and Cloud computing: Ubiquitous computing. In Resource Management and Efficiency in Cloud Computing Environments; IGI Global: Hershey, PA, USA, 2017; pp. 1–32. [Google Scholar]
- Ahmed, E.; Gani, A.; Khan, M.K.; Buyya, R.; Khan, S.U. Seamless application execution in mobile cloud computing: Motivation, taxonomy, and open challenges. J. Netw. Comput. Appl. 2015, 52, 154–172. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J.J. Privacy preserving data aggregation scheme for mobile edge computing assisted IoT applications. IEEE Internet Things J. 2018, 6, 4755–4763. [Google Scholar] [CrossRef]








| Author Name | Work of Author | Citation of Paper |
|---|---|---|
| (Pastor-Vargas, R., et al., 2020) | Lab of Things at UNED (LoT@UNED), the proposed system, supports remote laboratories for the full development of IoT, including edge, fog, and cloud computing as well as communication protocols and cyber security. | [30] |
| (Marsh-Hunn, D., et al., 2020) | From a geospatial standpoint, it contrasts two open web standards (OGC Sensor Monitoring Service and SensorThings API). | [31] |
| (Vresk, T. and I. Čavrak 2016) | Outlines IoT-specific problems and suggests middleware architectures based on microservices for integrating a variety of IoT devices. | [32] |
| (Trilles, S., et al., 2017) | Gives a summary of the difficulties unique to the Internet of Things and suggests for a middleware architecture based on microservices that is intended to link a variety of IoT devices. | [33] |
| (Huang, C. and C. Wu 2016) | The goal of this project is to create a performance profile and include it into the SensorThings API, which was the industry standard. | [34] |
| (Trilles, S., et al., 2020) | Utilizing the IoT paradigm, edge computing, and the simplicity of end-to-end connectivity, SEnviro’s new platform version will be used to monitor the vineyard. | [35] |
| (Kotsev, A., et al., 2018) | Outlines our synthesis of the procedures that must be followed in order for the OGC SensorThings API standard to be regarded as a legal response to the responsibilities resulting from the INSPIRE Directive. | [36] |
| (Kotsev, A., et al., 2020) | Include developments relating to SDI in a wider discussion of the contemporary political and technical landscape. | [37] |
| (Granell, C., et al., 2020) | Explore synergies and trade-offs in building effective and sustainable collaboration between two-way infrastructures to automate multidisciplinary and increasingly complex problems, visualizations, and aggregates. | [38] |
| (Trilles, S., et al., 2015) | It offers a sensor platform based on the principles of the Internet of Things and the Web of Things. Wireless sensor nodes are built using open-source solutions, and communication relies on the HTTP/IP Internet protocol. | [39] |
| Reference | Year | Contribution |
|---|---|---|
| Cao, K., et al. [40] | 2020 | Summarizes the idea of edge computing, compares it to cloud computing, and discusses the architecture, technology, security, and privacy of edge computing. |
| Porambage, P., et al. [41] | 2018 | Gives some insight into various other integration technologies in this field and talks about the technical aspects of enabling Multi Access edge computing (MEC) in the IoT. |
| Sha, K., et al. [42] | 2020 | Explores in-depth edge-based IoT security research initiatives in the context of firewalls, intrusion detection systems, authentication and authorization protocols, and privacy protection measures. |
| Ahmed, E. and M.H. Rehmani [43] | 2017 | Discusses the advantages of MEC and some significant research difficulties in the MEC environment. |
| Pan, J. and J. McElhannon [44] | 2017 | Explores the main rationale, state-of-the-art efforts, key technologies and research topics, and typical IoT applications taking advantage of the cloud. |
| Premsankar, G., M. Di Francesco, and T. Taleb. [45] | 2018 | Talks about the capabilities of the most advanced computing platforms available today and how the adoption of new technologies will affect the development of IoT applications in the future. |
| Liu, Y., et al. [46] | 2020 | It gives a general overview of the function that MEC plays in 5G and IoT, details the various IoT and 5G applications that support MEC, and outlines some exciting new directions for integrating MEC with 5G and IoT in the future. |
| Hamdan, S., M. Ayyash, and S. Almajali [47] | 2020 | Classifies several categories of Deep Computing Architectures for IoT (ECAs-IoT) such as data distribution, orchestration services, security, and big data. The report also evaluates each interior architecture and contrasts them based on a number of factors and explains the edge computing applications for the Internet of Things. |
| Challenges | Causes | Guidelines |
|---|---|---|
| Heterogeneity | (a) Different operating systems and hardware architectures, (b) Can be heterogeneous with regard to data rate, transmission range, and bandwidth. | It should provide an edge node programming paradigm that is backed by task-level and data-level parallelism to make it easier to run workloads concurrently on various hardware levels. Using a language that enables hardware heterogeneity is a second thing to think about [100]. |
| Standard Protocols and Interfaces | (a) because of the rapid development of new devices. | Standard protocols and interfaces should be developed to enable communication between these heterogeneous devices [101]. |
| Trust | (a) Lack of security and privacy-preserving mechanisms | It is possible to overcome difficulties in fostering customer confidence in edge computing systems by implementing influential aspects of consumer trust, such as security and privacy [102,103] |
| Pricing Models | (a) High QoS requirements, (b) Inappropriate pricing models, (c) Service providers’ high cost. | Dynamic pricing models may be created by considering three crucial elements, including resource availability, customer resource use frequency, and consumer resource usage duration [104]. |
| Mobility | (a) Intermitted connectivity due to mobility [3], (b) No accessibility of local resources, (c) Immature security policies | Peer-to-peer networks’ service discovery and wireless networks’ mobility management can serve as models [105,106]. |
| Collaborations | (a) Heterogeneous architectures [3], (b) Interoperability problems, (c) Data privacy issues, (d) Deficiencies in terms of load balancing. | One can utilize ubiquitous systems’ interoperability and collaboration as a reference [107]. |
| Fault tolerant deployment models | (a) High availability, (b) Data integrity, (c) Fault torlerance [3], Disaster recovery. | Machine learning may help provide low-cost fault tolerance through anomaly detection and predictive maintenance [108]. |
| Security | (a) Involvement of distributed data processing, | Significant blockchain technology characteristics such as tamper-proof, redundant, and self-healing can reduce significant security risks. Quantum cryptography-based solutions may also be helpful [109]. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anees, T.; Habib, Q.; Al-Shamayleh, A.S.; Khalil, W.; Obaidat, M.A.; Akhunzada, A. The Integration of WoT and Edge Computing: Issues and Challenges. Sustainability 2023, 15, 5983. https://doi.org/10.3390/su15075983
Anees T, Habib Q, Al-Shamayleh AS, Khalil W, Obaidat MA, Akhunzada A. The Integration of WoT and Edge Computing: Issues and Challenges. Sustainability. 2023; 15(7):5983. https://doi.org/10.3390/su15075983
Chicago/Turabian StyleAnees, Tayyaba, Qaiser Habib, Ahmad Sami Al-Shamayleh, Wajeeha Khalil, Muath A. Obaidat, and Adnan Akhunzada. 2023. "The Integration of WoT and Edge Computing: Issues and Challenges" Sustainability 15, no. 7: 5983. https://doi.org/10.3390/su15075983
APA StyleAnees, T., Habib, Q., Al-Shamayleh, A. S., Khalil, W., Obaidat, M. A., & Akhunzada, A. (2023). The Integration of WoT and Edge Computing: Issues and Challenges. Sustainability, 15(7), 5983. https://doi.org/10.3390/su15075983











