Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia
Abstract
1. Introduction
- What are the information security practices employed by the business employees in Saudi Arabia?
- Which security factors are considered relevant/irrelevant by employees working in different business domains in Saudi Arabia?
- How can the security behavior of business employees in Saudi Arabia be improved by adopting more secure practices?
2. Theoretical Basis and Hypothesis
2.1. Digital Transformation and Cybersecurity
2.2. Password Management
2.3. Infrastructure Security
2.4. Email Security Management
2.5. Security Education and Training
2.6. Security in Social Networks
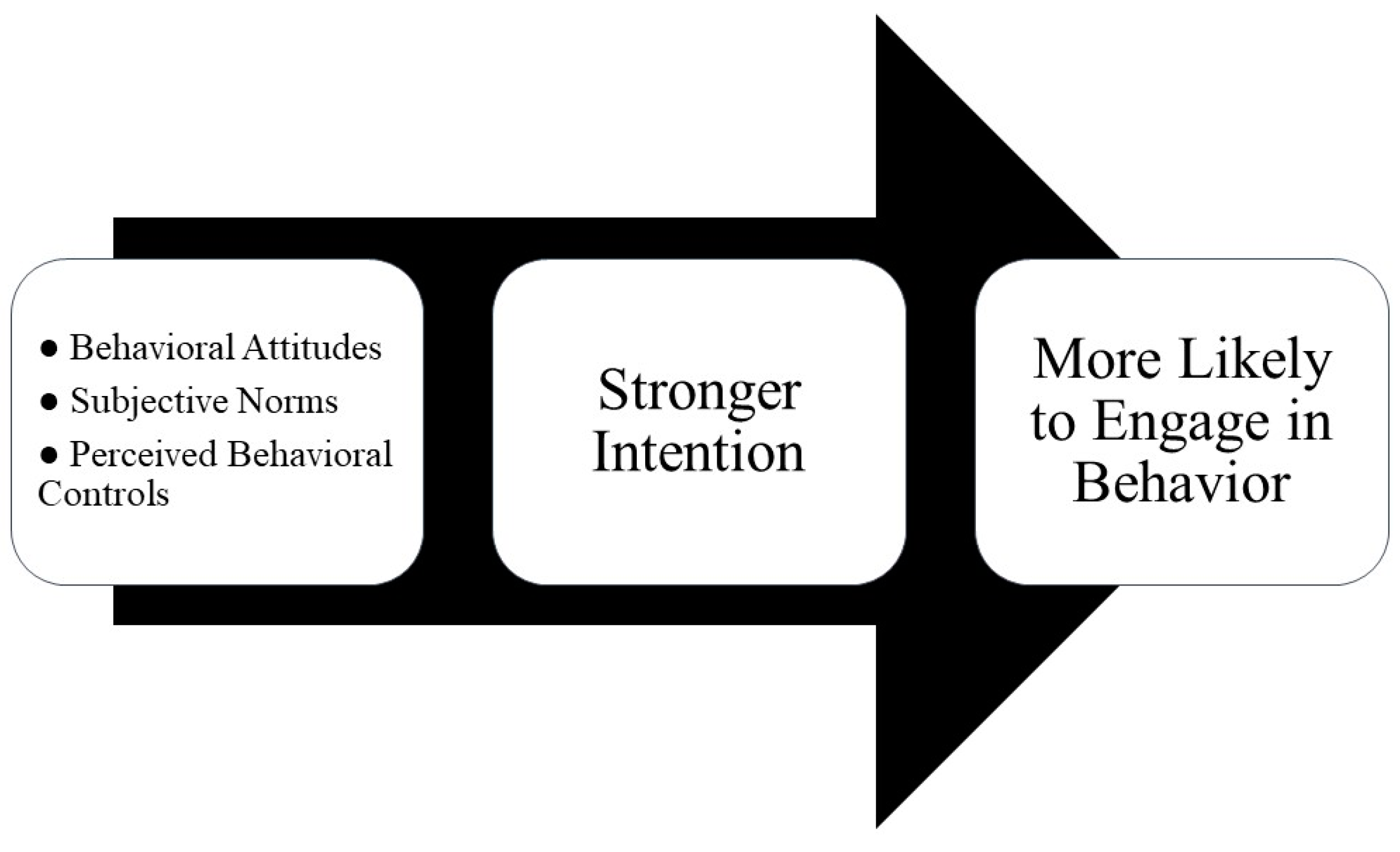
2.7. Theory of Planned Behavior in Security Research
2.8. Information Security Research in Saudi Arabia
2.9. Hypotheses Formulation for Our Study
3. Materials and Methods
4. Results
Discriminant Validity
5. Discussion
5.1. Theoretical Implications
5.2. Managerial Implications
5.3. Limitations and Future Directions
6. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
References
- ACM Cybersecurity Curricula 2017. Available online: https://dl.acm.org/doi/book/10.1145/3184594 (accessed on 10 November 2022).
- Gull, H.; Alabbad, D.A.; Saqib, M.; Iqbal, S.Z.; Nasir, T.; Saeed, S.; Almuhaideb, A.M. E-Commerce and Cybersecurity Challenges: Recent Advances and Future Trends. In Handbook of Research on Cybersecurity Issues and Challenges for Business and FinTech Applications; IGI Global: Hershey, PA, USA, 2023; pp. 91–111. [Google Scholar]
- Saeed, S. A Customer-Centric View of E-Commerce Security and Privacy. Appl. Sci. 2023, 13, 1020. [Google Scholar] [CrossRef]
- Saeed, S.; Bolívar MP, R.; Thurasamy, R. Pandemic, Lockdown, and Digital Transformation; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Artamonov, V.A.; Artamonova, E.V. The Cybersecurity in Conditions of the Digital Transformation. Digit. Transform. 2022. Available online: https://ideas.repec.org/a/abx/journl/y2022id642.html (accessed on 10 November 2022).
- Medoh, C.; Telukdarie, A. The Future of Cybersecurity: A System Dynamics Approach. Procedia Comput. Sci. 2022, 200, 318–326. [Google Scholar] [CrossRef]
- Mishra, A.; Alzoubi, Y.I.; Gill, A.Q.; Anwar, M.J. Cybersecurity Enterprises Policies: A Comparative Study. Sensors 2022, 22, 538. [Google Scholar] [CrossRef]
- Díaz, A.; Guerra, L.; Díaz, E. Digital Transformation Impact in Security and Privacy. In Developments and Advances in Defense and Security; Springer: Singapore, 2022; pp. 61–70. [Google Scholar]
- Lee, W.J.; Hwang, I. Sustainable Information Security Behavior Management: An Empirical Approach for the Causes of Employees’ Voice Behavior. Sustainability 2021, 13, 6077. [Google Scholar] [CrossRef]
- Nemec Zlatolas, L.; Feher, N.; Hölbl, M. Security perception of IoT devices in smart homes. J. Cybersecur. Priv. 2022, 2, 65–73. [Google Scholar] [CrossRef]
- Mehrnezhad, M.; Toreini, E. What is this sensor and does this app need access to it? Informatics 2019, 6, 7. [Google Scholar] [CrossRef]
- Goh, C.H.; Teoh, A.P. Determining Bring Your Own Device (Byod) Security Policy Compliance among Malaysian Teleworkers: Perceived Cybersecurity Governance as Moderator. In Proceedings of the 2021 IEEE 5th International Conference on Information Technology, Information Systems and Electrical Engineering (ICITISEE), Purwokerto, Indonesia, 24–25 November 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 305–310. [Google Scholar]
- Jarlhem, J.; Stigsson, J. Digital Vulnerability Awareness: In a “Working from Home” Environment during COVID-19. Bachelor Thesis. Available online: https://www.diva-portal.org/smash/record.jsf?pid=diva2%3A1576133&dswid=3885 (accessed on 10 November 2022).
- Dangheralou, A.; Jahankhani, H. The Impact of GDPR Regulations on Cyber Security Effectiveness Whilst Working Remotely. In Artificial Intelligence in Cyber Security: Impact and Implications; Springer: Cham, Switzerland, 2021; pp. 253–279. [Google Scholar]
- Arogbodo, M. Impacts of the COVID-19 Pandemic on Online Security Behavior within the UK Educational Industry. Available online: https://doi.org/10.31234/osf.io/h5qgk (accessed on 10 November 2022).
- Yang, J.; Linkeschová, L. Remote Working and Cybersecurity in the Pandemic: Research on the Employee Perceptions of Remote Work and Cybersecurity in an International Organisation during COVID-19. Ph.D. Thesis, University of Geneva, Geneva, Switzerland, 2021. [Google Scholar]
- Carlsten, F.; Hultman, E.; Nilsson, D.E. Work from Home-Information Security Threats and Best Practices. Master’s Thesis, Lund University, Lund, Sweden, 2021. [Google Scholar]
- Borkovich, D.J.; Skovira, R.J. Working from home: Cybersecurity in the age of COVID-19. Issues Inf. Syst. 2020, 21, 234–246. [Google Scholar]
- Powell, C.R. The Impact of Telework on Organizational Cybersecurity during the COVID-19 Pandemic. Ph.D. Thesis, Utica College, Utica, NY, USA, 2021. [Google Scholar]
- Tam, L.; Glassman, M.; Vandenwauver, M. The psychology of password management: A tradeoff between security and convenience. Behav. Inf. Technol. 2010, 29, 233–244. [Google Scholar] [CrossRef]
- Tarwireyi, P.; Flowerday, S.; Bayaga, A. Information security competence test with regards to password management. In Proceedings of the 2011 Information Security for South Africa, Johannesburg, South Africa, 15–17 August 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 1–7. [Google Scholar]
- Zezschwitz, E.V.; Luca, A.D.; Hussmann, H. Survival of the shortest: A retrospective analysis of influencing factors on password composition. In IFIP Conference on Human-Computer Interaction, Cape Town, South Africa, 2–6 September 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 460–467. [Google Scholar]
- Habib, H.; Naeini, P.E.; Devlin, S.; Oates, M.; Swoopes, C.; Bauer, L.; Christin, N.; Cranor, L.F. User behaviors and attitudes under password expiration policies. In Proceedings of the Fourteenth Symposium on Usable Privacy and Security (SOUPS 2018), Baltimore, MD, USA, 12–14 August 2018; pp. 13–30. [Google Scholar]
- Sanok, D.J., Jr. An analysis of how antivirus methodologies are utilized in protecting computers from malicious code. In Proceedings of the 2nd Annual Conference on Information Security Curriculum Development, Kennesaw, GA, USA, 23–24 September 2005; pp. 142–144. [Google Scholar]
- Al-Saleh, M.I.; Espinoza, A.M.; Crandall, J.R. Antivirus performance characterisation: System-wide view. IET Inf. Secur. 2013, 7, 126–133. [Google Scholar] [CrossRef]
- Tiwari, R.K.; Karlapalem, K. Cost Tradeoffs for Information Security Assurance. In Proceedings of the Workshop on the Economics of Information Security, Cambridge, MA, USA, 1–3 June 2005. [Google Scholar]
- Hayajneh, T.; Mohd, B.J.; Itradat, A.; Quttoum, A.N. Performance and information security evaluation with firewalls. Int. J. Secur. Its Appl. 2013, 7, 355–372. [Google Scholar] [CrossRef]
- Lee, Y.; Kozar, K.A. An empirical investigation of anti-spyware software adoption: A multitheoretical perspective. Inf. Manag. 2008, 45, 109–119. [Google Scholar] [CrossRef]
- Gurung, A.; Luo, X.; Liao, Q. Consumer motivations in taking action against spyware: An empirical investigation. Inf. Manag. Comput. Secur. 2009, 17, 276–289. [Google Scholar] [CrossRef]
- Albrechtsen, E.; Hovden, J. Improving information security awareness and behaviour through dialogue, participation and collective reflection. An intervention study. Comput. Secur. 2010, 29, 432–445. [Google Scholar] [CrossRef]
- Almeida, F. Web 2.0 technologies and social networking security fears in enterprises. arXiv 2012, arXiv:1204.1824. [Google Scholar] [CrossRef]
- Koushik, P.; Chandrashekhar, A.M.; Takkalakaki, J. Information security threats, awareness and cognizance. Int. J. Tech. Res. Eng. 2015, 2, 19–28. [Google Scholar]
- Rao, G.R.K.; Prasad, D.R.S. Combating Cross-Site Scripting Assaults without Proprietary Software. Int. J. Appl. Eng. 2017, 12, 6788–6796. [Google Scholar]
- Kruger, H.; Drevin, L.; Steyn, T. Email security awareness—A practical assessment of employee behaviour. In Proceedings of the Fifth World Conference on Information Security Education, West Point, NY, USA, 19–21 June 2007; Springer: New York, NY, USA, 2007; pp. 33–40. [Google Scholar]
- Rudd, E.M.; Harang, R.; Saxe, J. Meade: Towards a malicious email attachment detection engine. In Proceedings of the 2018 IEEE International Symposium on Technologies for Homeland Security (HST), Woburn, MA, USA, 23–24 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar]
- Wei, W.; Ding, X.; Chen, K. Multiplex encryption: A practical approach to encrypting multi-recipient emails. In Proceedings of the International Conference on Information and Communications Security, Beijing, China, 10–13 December 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 269–279. [Google Scholar]
- Wei, J.; Chen, X.; Wang, J.; Hu, X.; Ma, J. Forward-secure puncturable identity-based encryption for securing cloud emails. In Proceedings of the European Symposium on Research in Computer Security, Luxembourg, 23–27 September 2019; Springer: Cham, Switzerland, 2019; pp. 134–150. [Google Scholar]
- Roth, S.; Calzavara, S.; Wilhelm, M.; Rabitti, A.; Stock, B. The Security Lottery: Measuring Client-Side Web Security Inconsistencies. In Proceedings of the 31st USENIX Security Symposium, Boston, MA, USA, 10–12 August 2022. [Google Scholar]
- Villamarín-Salomón, R.; Brustoloni, J.; DeSantis, M.; Brooks, A. Improving User Decisions About Opening Potentially Dangerous Attachments in E-Mail Clients. In Proceedings of the Poster, Symposium on Usable Privacy and Security, CMU, Pittsburgh, PA, USA, 12–14 July 2006. [Google Scholar]
- Bilal, K.; Khaled, S.A.; Syed, I.N.; Muhammad, K.K. Effectiveness of information security awareness methods based on psychological theories. Afr. J. Bus. Manag. 2011, 5, 10862–10868. [Google Scholar] [CrossRef]
- Stafford, T.; Deitz, G.; Li, Y. The role of internal audit and user training in information security policy compliance. Manag. Audit. J. 2018, 33, 410–424. [Google Scholar] [CrossRef]
- Safa, N.S.; Von Solms, R.; Furnell, S. Information security policy compliance model in organizations. Comput. Secur. 2016, 56, 70–82. [Google Scholar] [CrossRef]
- Herath, T.; Rao, H.R. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 2009, 47, 154–165. [Google Scholar] [CrossRef]
- Knapp, K.J.; Morris Jr, R.F.; Marshall, T.E.; Byrd, T.A. Information security policy: An organizational-level process model. Comput. Secur. 2009, 28, 493–508. [Google Scholar] [CrossRef]
- Hagen, J.M.; Albrechtsen, E.; Hovden, J. Implementation and effectiveness of organizational information security measures. Inf. Manag. Comput. Secur. 2008, 16, 377–397. [Google Scholar] [CrossRef]
- Huang, D.L.; Rau PL, P.; Salvendy, G. Perception of information security. Behav. Inf. Technol. 2010, 29, 221–232. [Google Scholar] [CrossRef]
- Al-Molhem, N.R.; Rahal, Y.; Dakkak, M. Social network analysis in Telecom data. J. Big Data 2019, 6, 99. [Google Scholar] [CrossRef]
- Li, K.; Cheng, L.; Teng, C.I. Voluntary sharing and mandatory provision: Private information disclosure on social networking sites. Inf. Process. Manag. 2020, 57, 102128. [Google Scholar] [CrossRef]
- Cerruto, F.; Cirillo, S.; Desiato, D.; Gambardella, S.M.; Polese, G. Social network data analysis to highlight privacy threats in sharing data. J. Big Data 2022, 9, 19. [Google Scholar] [CrossRef]
- Kim, J.; Mou, J. Meta-analysis of Information Security Policy Compliance Based on Theory of Planned Behavior. J. Digit. Converg. 2020, 18, 169–176. [Google Scholar]
- Sommestad, T.; Karlzén, H.; Hallberg, J. The sufficiency of the theory of planned behavior for explaining information security policy compliance. Inf. Comput. Secur. 2015, 23, 200–217. [Google Scholar] [CrossRef]
- Grassegger, T.; Nedbal, D. The role of employees’ information security awareness on the intention to resist social engineering. Procedia Comput. Sci. 2021, 181, 59–66. [Google Scholar] [CrossRef]
- AlMindeel, R.; Martins, J.T. Information security awareness in a developing country context: Insights from the government sector in Saudi Arabia. Inf. Technol. People 2020, 34, 770–788. [Google Scholar] [CrossRef]
- Almutairi, M.M.; Halikias, G.; Yamin, M. An overview of security management in Saudi Arabia. In Proceedings of the 2020 7th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 12–14 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 261–265. [Google Scholar]
- Alharbi, T. Developing Cost-effective Cybersecurity Management System for Academic Institutions in Saudi Arabia. J. Eng. Appl. Sci. 2022, 9, 57. [Google Scholar] [CrossRef]
- Alsulami, M. Social Media Security Awareness in Saudi Arabia. Tehnički Glasnik 2022, 16, 213–218. [Google Scholar] [CrossRef]
- Gull, H.; Saeed, S.; Iqbal, S.Z.; Bamarouf, Y.A.; Alqahtani, M.A.; Alabbad, D.A.; Saqib, M.; Al Qahtani, S.H.; Alamer, A. An empirical study of mobile commerce and customers security perception in Saudi Arabia. Electronics 2022, 11, 293. [Google Scholar] [CrossRef]
- Alzubaidi, A. Measuring the level of cyber-security awareness for cybercrime in Saudi Arabia. Heliyon 2021, 7, e06016. [Google Scholar] [CrossRef] [PubMed]
- Aljohni, W.; Elfadil, N.; Jarajreh, M.; Gasmelsied, M. Cybersecurity Awareness Level: The Case of Saudi Arabia University Students. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 276–281. [Google Scholar] [CrossRef]
- Shahid, J.; Ahmad, R.; Kiani, A.K.; Ahmad, T.; Saeed, S.; Almuhaideb, A.M. Data protection and privacy of the internet of healthcare things (IoHTs). Appl. Sci. 2022, 12, 1927. [Google Scholar] [CrossRef]
- Iqbal, Y.; Tahir, S.; Tahir, H.; Khan, F.; Saeed, S.; Almuhaideb, A.M.; Syed, A.M. A Novel Homomorphic Approach for Preserving Privacy of Patient Data in Telemedicine. Sensors 2022, 22, 4432. [Google Scholar] [CrossRef]
- Zulkifl, Z.; Khan, F.; Tahir, S.; Afzal, M.; Iqbal, W.; Rehman, A.; Saeed, S.; Almuhaideb, A.M. FBASHI: Fuzzy and Blockchain-Based Adaptive Security for Healthcare IoTs. IEEE Access 2022, 10, 15644–15656. [Google Scholar] [CrossRef]
- Faklaris, C.; Dabbish, L.A.; Hong, J.I. A {Self-Report} Measure of {End-User} Security Attitudes. In Proceedings of the Fifteenth Symposium on Usable Privacy and Security (SOUPS 2019), Santa Clara, CA, USA, 11–13 August 2019; pp. 61–77. [Google Scholar]
- Security Awareness Survey. Available online: https://www.securitymentor.com/resources/surveys/security-awareness-survey (accessed on 17 October 2022).
- Hammarstrand, J.; Fu, T. Information security awareness and behaviour: Of trained and untrained home users in Sweden. Bachelor’s Thesis, University of Borås, Borås, Sweden, 2015. [Google Scholar]
- Computer and Information Security End User Questionnaire. Available online: https://cqpi.wisc.edu/wp-content/uploads/sites/599/2016/07/Pilot_Study_Questionnaire.pdf (accessed on 17 October 2022).
- SANS Security Awareness, Human Risk Assessments and Surveys, SANS Institute. Available online: https://www.sans.org/blog/getting-support-for-your-human-risk-assessments-and-surveys/ (accessed on 17 October 2022).
- Parker, C.; Scott, S.; Geddes, A. Snowball Sampling; SAGE: New York, NY, USA, 2019. [Google Scholar]
- Zickar, M.J.; Keith, M.G. Innovations in Sampling: Improving the Appropriateness and Quality of Samples in Organizational Research. Annu. Rev. Organ. Psychol. Organ. Behav. 2023, 10, 315–337. [Google Scholar] [CrossRef]
- Vinzi, V.E.; Chin, W.W.; Henseler, J.; Wang, H. Handbook of Partial Least Squares: Concepts, Methods and Applications; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Hair, J.F.; Sarstedt, M.; Hopkins, L.; Kuppelwieser, V.G. Partial least squares structural equation modeling (PLS-SEM): An emerging tool in business research. Eur. Bus. Rev. 2014, 26, 106–121. [Google Scholar] [CrossRef]
- Discriminant Validity. Available online: https://www.analysisinn.com/post/discriminant-validity-through-fronell-larcker-criterion/#:~:text=The%20Fronell%2DLarcker%20criterion%20is,construct%20and%20any%20other%20construct (accessed on 17 October 2022).



| Theory of Planned Behavior Constructs | Construct of Study | Subfactors of Constructs | Relevant Literature Source | |
|---|---|---|---|---|
| Perceived Behavioral Controls | Password Management | PM1 | Single password reuse | [23,24] |
| PM2 | Password change only when mandatory due to organizational policy | [23,24] | ||
| PM3 | New password resembling old password | [23,24] | ||
| PM4 | Password storage on a paper or electronic file | [21] | ||
| PM5 | Password storage in a software | [21] | ||
| PM6 | Password sharing with colleagues | [22] | ||
| Perceived Behavioral Controls | Infrastructure Security Management | ISM1 | Antivirus presence | [25] |
| ISM2 | Antivirus update | [27] | ||
| ISM3 | Firewall usage | [28] | ||
| ISM4 | Anti-spyware usage | [29,30] | ||
| ISM5 | Allowing scripting | [34] | ||
| ISM6 | Locking computer while away | [31,33] | ||
| ISM7 | Password protected screensaver | [33] | ||
| ISM8 | Usage of social applications | [32] | ||
| Perceived Behavioral Controls | Email Management | EM1 | Opening unknown emails | [35] |
| EM2 | Opening attachments from unknown emails | [36] | ||
| EM3 | Usage of encryption in emails | [37,38] | ||
| EM4 | Analyzing security settings of web-based email clients | [40] | ||
| Subjective Norms | Organizational Security Policy | OSP1 | Attention to computer security | [47] |
| OSP2 | Presence of organizational security policy | [45] | ||
| OSP3 | Understandability of organizational security policy | [46] | ||
| OSP4 | Deviation from organizational security policy | [43] | ||
| OSP5 | Perception of coworkers’ deviation of organizational security policy | [43] | ||
| OSP 6 | Repercussions of security policy violations | [44] | ||
| Subjective Norms | Organizational Support and Training | OST1 | Availability of helpdesk | [41] |
| OST2 | Provision of training | [42] | ||
| OST3 | Enhanced understanding of security policy due to training | [42] | ||
| Behavioral Attitudes | Perception of Security | POS1 | Personal computer is safe | [47] |
| POS2 | I can protect my computer | [47] | ||
| POS3 | Computer security is worrying | [47] | ||
| POS4 | Special attention to security makes difference | [47] | ||
| POS5 | My information is not interesting for hackers | [47] | ||
| POS6 | Hacking is unavoidable | [47] | ||
| Hypothesis | Sample Mean | Standard Deviation | T Statistics | p Values | Result |
|---|---|---|---|---|---|
| Hypothesis 1 | 0.594 | 0.129 | 5.086 | 0.000 | Approved |
| Hypothesis 2 | 0.027 | 0.096 | 0.237 | 0.812 | Rejected |
| Hypothesis 3 | 0.434 | 0.096 | 4.910 | 0.000 | Approved |
| Hypothesis 4 | 0.075 | 0.041 | 2.149 | 0.032 | Approved |
| Hypothesis 5 | 0.150 | 0.162 | 0.493 | 0.622 | Rejected |
| Hypothesis 6 | 0.268 | 0.162 | 1.790 | 0.074 | Rejected |
| Fornell-Larcker Criterion | Email Management | Infrastructure Management | Organizational Security Policy | Organizational Support & Training | Password Management | Perception of Security |
|---|---|---|---|---|---|---|
| Email Management | 0.612 | |||||
| Infrastructure Management | 0.150 | 0.382 | ||||
| Organizational Security Policy | 0.095 | 0.104 | 0.443 | |||
| Organizational Support & Training | −0.015 | 0.020 | 0.002 | 0.586 | ||
| Password Management | 0.196 | 0.144 | 0.132 | 0.041 | 0.480 | |
| Perception of Security | 0.138 | 0.170 | 0.033 | 0.066 | 0.044 | 0.563 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saeed, S. Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia. Sustainability 2023, 15, 6019. https://doi.org/10.3390/su15076019
Saeed S. Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia. Sustainability. 2023; 15(7):6019. https://doi.org/10.3390/su15076019
Chicago/Turabian StyleSaeed, Saqib. 2023. "Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia" Sustainability 15, no. 7: 6019. https://doi.org/10.3390/su15076019
APA StyleSaeed, S. (2023). Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia. Sustainability, 15(7), 6019. https://doi.org/10.3390/su15076019






