Beyond Data Protection: Exploring the Convergence between Cybersecurity and Sustainable Development in Business
Abstract
1. Introduction
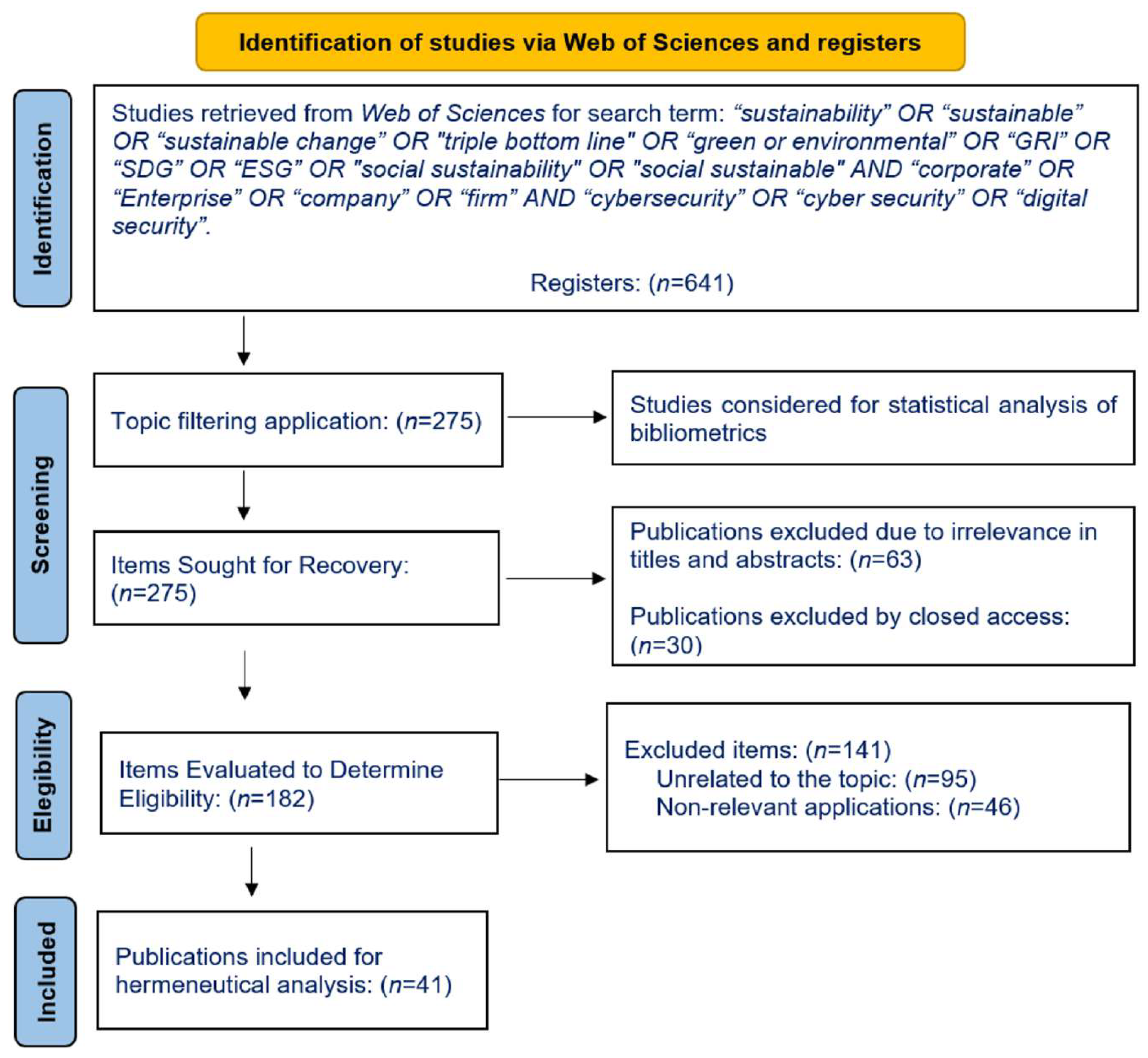
2. Method
Systematic Review and Selection Criteria
3. Results
3.1. Quality of Journals and Areas of Knowledge
3.2. Temporal Distribution of Publications
3.3. Frequency by Funding Institution
3.4. Frequency by Most Cited
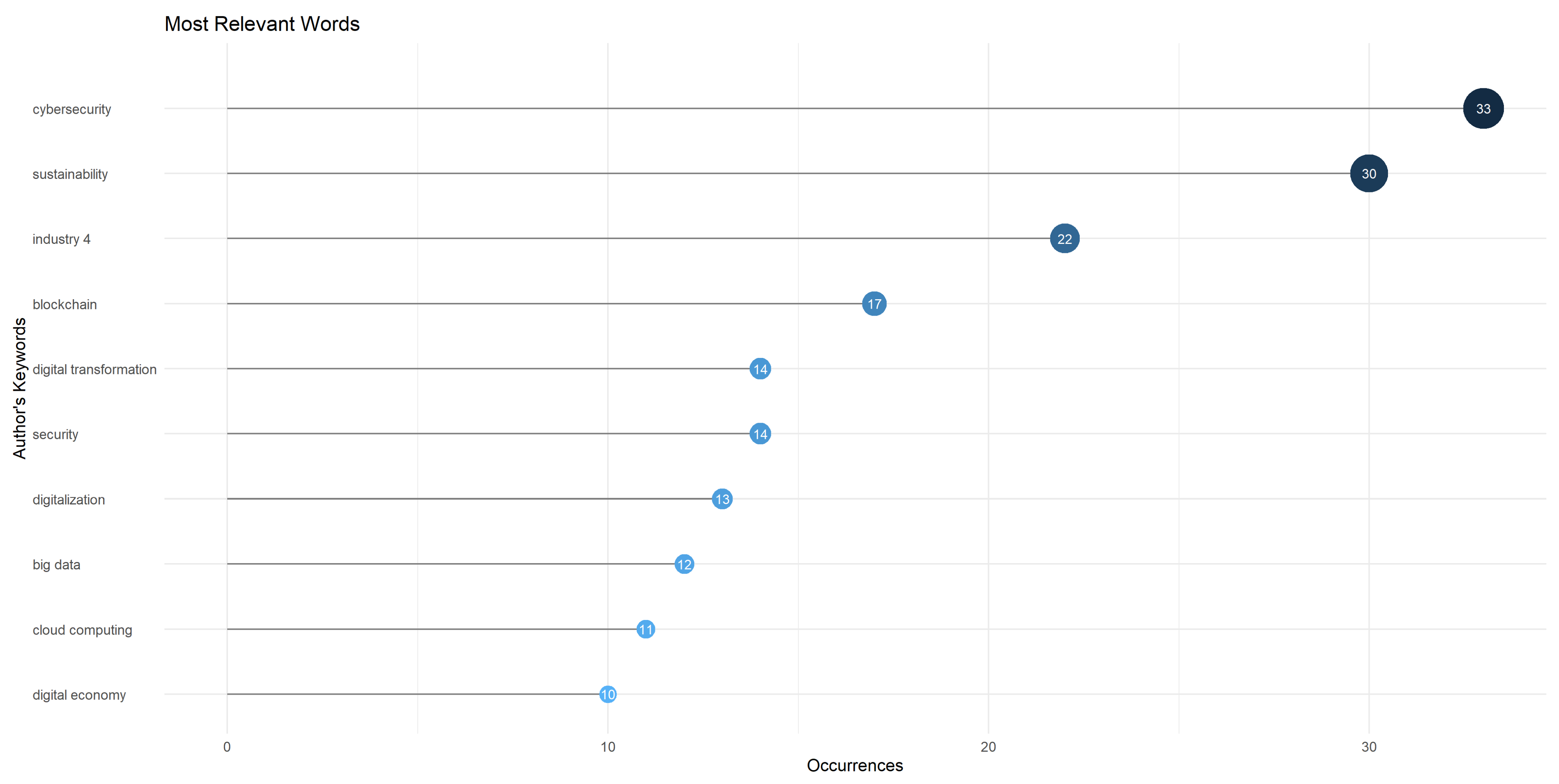
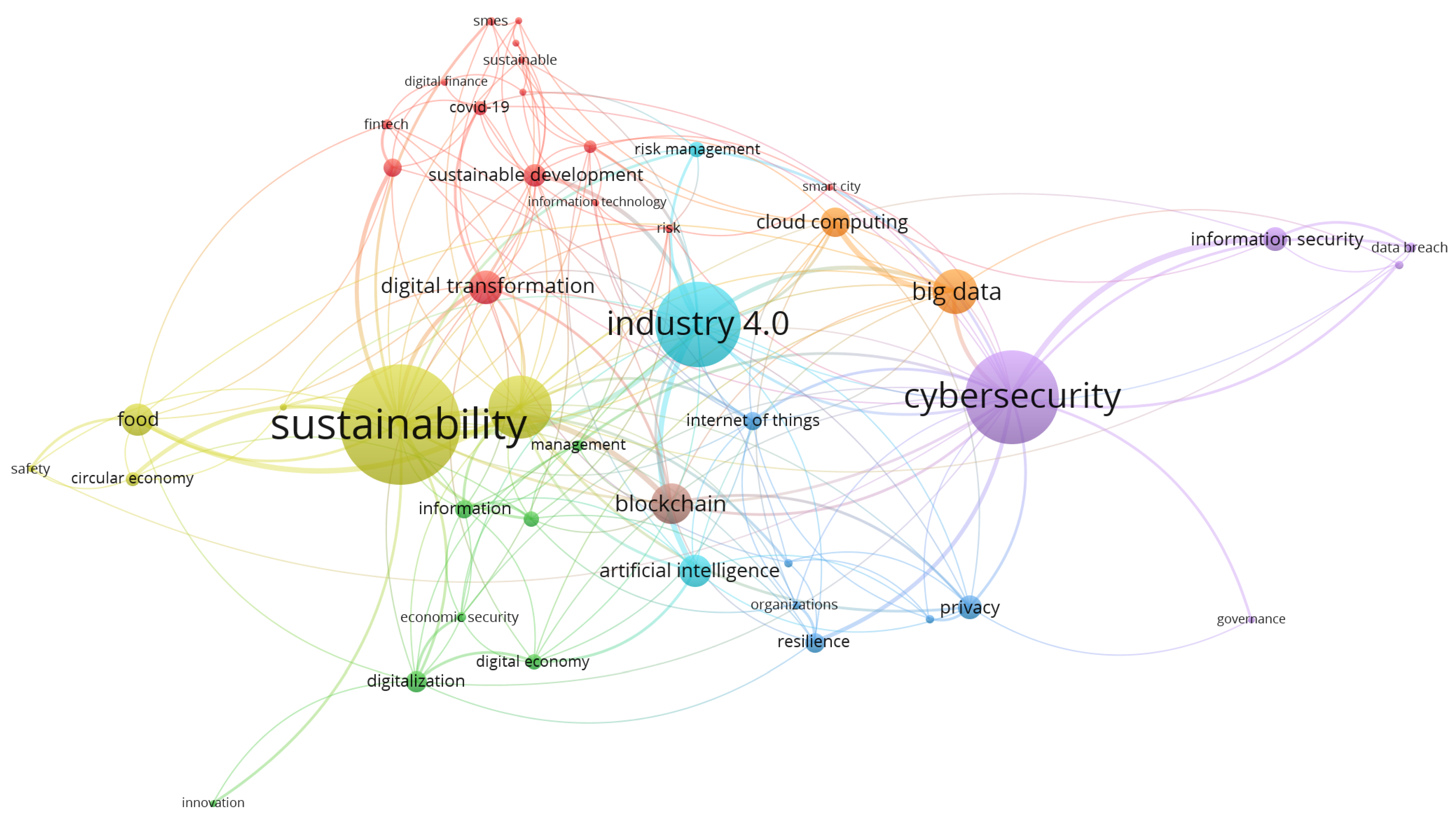
3.5. Frequency and Network of Key Concepts
3.6. Analysis of the Use of Definitions
3.7. Aspects of Sustainable Development
3.8. Cybersecurity and Sustainability Dimensions and Indicators
3.9. Links between Cybersecurity and Sustainable Development
3.10. Aspects of Methodology and Technique
4. Discussion
5. Conclusions
6. Gaps in the Literature and Future Lines of Research
7. Managerial Implications
Author Contributions
Funding
Conflicts of Interest
References
- Al-Sibai, H.; Alrubaie, T.; Elmedany, W. IoT cybersecurity threats mitigation via integrated technical and non-technical solutions. Int. J. Electron. Secur. Digit. Forensics 2021, 13, 298–333. [Google Scholar] [CrossRef]
- Darem, A. Anti-Phishing Awareness Delivery Methods. Eng. Technol. Appl. Sci. Res. 2021, 11, 7944–7949. [Google Scholar] [CrossRef]
- Taherdosst, H. Understanding Cybersecurity Frameworks and Information Security Standards—A Review and Comprehensive Overview. Electronics 2022, 11, 2181. [Google Scholar] [CrossRef]
- Arroyabe, I.; Arranz, C.; Arroyabe, M.; Arroyabe, J. Cybersecurity capabilities and cyber-attacks as drivers of investment in cybersecurity systems: A UK survey for 2018 and 2019. Comput. Secur. 2023, 124, 102954. [Google Scholar] [CrossRef]
- Abidi, N.; El Herradi, M.; Sakha, S. Digitalization and resilience during the COVID-19 pandemic? Telecommun. Policy 2023, 47, 102522. [Google Scholar] [CrossRef] [PubMed]
- Sendur, Y. The Covid-19 Pandemic and Digitalization in Financial Markets. Istanb. J. Econ. 2022, 72, 1025–1038. [Google Scholar] [CrossRef]
- García-Perez, A.; Sallos, M.; Tiwasing, P. Dimensions of cybersecurity performance and crisis response in critical infrastructure organisations: An intellectual capital perspective. J. Intellect. Cap. 2023, 24, 465–486. [Google Scholar] [CrossRef]
- Bodin, L.; Gordon, L.; Loeb, M.; Wang, A. Cybersecurity insurance and risk-sharing. J. Account. Public Policy 2018, 37, 527–544. [Google Scholar] [CrossRef]
- Williams, C.; Chaturvedi, R.; Chakravarthy, K. Cybersecurity Risks in a Pandemic. J. Med. Internet Res. 2020, 22, e23692. [Google Scholar] [CrossRef]
- Al-Qahtani, A.; Cresci, S. The COVID-19 scamdemic: A survey of pishing attacks and their countermeasures during COVID-19. IET Inf. Secur. 2022, 16, 324–345. [Google Scholar] [CrossRef]
- Berlilana; Noparumpa, T.; Ruangkanjanases, A.; Hariguna, T.; Sarmini. Organization Benefit as an Outcome of Organizational Security Adoption: The Role of Cyber Security Readiness and Technology Readiness. Sustainability 2021, 13, 13761. [Google Scholar] [CrossRef]
- Silaule, C.; Makhubele, L.; Mamorobela, S. A model to reduce insider cybersecurity threats in a South African telecommunications company. S. Afr. J. Inf. Manag. 2022, 24, 1573. [Google Scholar] [CrossRef]
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mammela, A.; Ahmad, I. Machine Learning Threatens 5G Security. IEEE Access 2020, 8, 190822–190842. [Google Scholar] [CrossRef]
- World-Bank-Group. Internet Crime Complaint Center IC3. 2021. Available online: https://www.ic3.gov/ (accessed on 1 July 2024).
- Lee, I. Cybersecurity: Risk management framework and investment cost analysis. Bus. Horiz. 2021, 64, 659–671. [Google Scholar] [CrossRef]
- Buil-Gil, D.; Lord, N.; Barret, E. The Dynamics of Business, Cybersecurity and Cyber-Victimization: Foregrounding the Internal Guardian in Prevention. Vict. Offenders 2021, 16, 286–315. [Google Scholar] [CrossRef]
- Nugraha, Y.; Martin, A. Cybersecurity service level agreements: Understanding government data confidentiality requirements. J. Cybersecur. 2022, 8, tyac004. [Google Scholar] [CrossRef]
- Morales-Sáenz, F.; Medina-Quintero, J.; Ortíz-Rodríguez, F. Bibliometrics Study of Organizational Cybersecurity. In Emerging Technologies and Digital Transformation in the Manufacturing Industry; IGI Global: Hershey, PA, USA, 2023; pp. 115–139. [Google Scholar]
- Sabillon, R. A Practical Model to Perform Comprehensive Cybersecurity Audits. Enfoque UTE 2018, 9, 127–137. [Google Scholar] [CrossRef]
- Rodger, J.A.; George, J.A. Triple bottom line accounting for optimizing natural gas sustainability: A statistical linear programming fuzzy ILOWA optimized sustainment model approach to reducing supply chain global cybersecurity vulnerability through information and communications technology. J. Clean. Prod. 2017, 142, 1931–1949. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T. A Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry. IEEE Access 2019, 7, 17578–17598. [Google Scholar] [CrossRef]
- Arcuri, M.C.; Gai, L.; Ielasi, F.; Ventisette, E. Cyber attacks on hospitality sector: Stock market reaction. J. Hosp. Tour. Technol. 2020, 11, 277–290. [Google Scholar] [CrossRef]
- Ghobakhloo, M.; Fathi, M. Corporate survival in Industry 4.0 era: The enabling role of lean-digitized manufacturing. J. Manuf. Technol. Manag. 2019, 31, 1–30. [Google Scholar] [CrossRef]
- Ram, J.; Zhang, Z. Belt and road initiative (BRI) supply chain risks: Propositions and model development. Int. J. Logist. Manag. 2020, 31, 777–799. [Google Scholar] [CrossRef]
- Bondarenko, L.; Moroz, N.; Zhelizniak, R.; Bonetskyy, O. Fintech market development in the world and in Ukraine. Financ. Credit Act. Probl. Theory Pract. 2022, 6, 121–127. [Google Scholar] [CrossRef]
- Naffa, H.; Fain, M. Performance measurement of ESG-themed megatrend investments in global equity markets using pure factor portfolios methodology. PLoS ONE 2020, 15, e0244225. [Google Scholar] [CrossRef]
- Shaikh, F.A.; Siponen, M. Organizational Learning from Cybersecurity Performance: Effects on Cybersecurity Investment Decisions. Inf. Syst. Front. 2024, 26, 1109–1120. [Google Scholar] [CrossRef]
- Radu, C.; Smaili, N. Board Gender Diversity and Corporate Response to Cyber Risk: Evidence from Cybersecurity Related Disclosure. J. Bus. Ethics 2022, 177, 351–374. [Google Scholar] [CrossRef]
- Okpa, J.T.; Ajah, B.O.; Nzeakor, O.F.; Eshiotse, E.; Abang, T.A. Business e-mail compromise scam, cyber victimization, and economic sustainability of corporate organizations in Nigeria. Secur. J. 2023, 36, 350–372. [Google Scholar] [CrossRef]
- Skerhakova, V.; Taha, V.A.; Tirpák, D.; Kraľ, S. Perception of Corporate Reputation in the Era of Digitization: Case Study of Online Shopping Behavior on Young Consumers. Sustainability 2022, 14, 14302. [Google Scholar] [CrossRef]
- Wang, G.; Tse, D.; Cui, Y.; Jiang, H. An Exploratory Study on Sustaining Cyber Security Protection through SETA Implementation. Sustainability 2022, 14, 8319. [Google Scholar] [CrossRef]
- Litvinenko, V. Digital Economy as a Factor in the Technological Development of the Mineral Sector. Nat. Resour. Res. 2020, 29, 1521–1541. [Google Scholar] [CrossRef]
- Laskuraín-Iturbe, I.; Arana-Landín, G.; Landeta-Manzano, B.; Uriarte-Gallastegi, N. Exploring the influence of industry 4.0 technologies on the circular economy. J. Clean. Prod. 2021, 321, 128944. [Google Scholar] [CrossRef]
- Chun, S.H. E-Commerce Liability and Security Breaches in Mobile Payment for e-Business Sustainability. Sustainability 2019, 11, 715. [Google Scholar] [CrossRef]
- Shackelford, S.; Fort, T.; Charoen, D. Sustainable cybersecurity: Applying lessons from the green movement to managing Cyber Attacks. U. Ill. L. Rev. 2016, 1995. [Google Scholar] [CrossRef]
- Malatji, M.; Marnewick, A.; von Solms, S. Validation of a socio-technical management process for optimising cybersecurity practices. Comput. Secur. 2020, 95, 101846. [Google Scholar] [CrossRef]
- Burgess, K.; Singh, P.; Koroglu, R. Supply chain management: A structured literature review and implications for future research. Int. J. Oper. Prod. Manag. 2006, 26, 703–729. [Google Scholar] [CrossRef]
- Wacker, J.G. A definition of theory: Research guidelines for different theory-building research methods in operations management. J. Oper. Manag. 1998, 16, 361–385. [Google Scholar] [CrossRef]
- Goyanes, M.; Demeter, M. How the geographic diversity of editorial boards affects what is published in JCR-Ranked communication journals. Journal. Mass Commun. Q. 2020, 97, 1123–1148. [Google Scholar] [CrossRef]
- Kipper, L.; Furstenau, L.; Hoppe, D.; Frozza, R.; Lespen, S. Scopus scientific mapping production in industry 4.0 (2011–2018): A bibliometric analysis. Int. J. Prod. Res. 2019, 58, 1605–1627. [Google Scholar] [CrossRef]
- Snyder, H. Literature review as a research methodology: An overview and guidelines. J. Bus. Res. 2019, 104, 333–339. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Vaccaro, G.; Sánchez-Núñez, P.; Witt-Rodríguez, P. Bibliometrics Evaluation of Scientific Journals and Country Research Output of Dental Research in Latin America Using. Scimago J. Ctry. Rank Publ. 2022, 10, 26. [Google Scholar] [CrossRef]
- Gupta, S.; Meissonier, R.; Drave, V.; Roubaud, D. Examining the impact of Cloud ERP on sustainable performance: A dynamic capability view. Int. J. Inf. Manag. 2020, 51, 102028. [Google Scholar] [CrossRef]
- Murch, R.; So, W.; Buchholz, W.; Raman, S.; Peccoud, J. Cyberbiosecurity: An emerging new discipline to help safeguard the bioeconomy. Front. Bioeng. Biotechnol. 2018, 6, 39. [Google Scholar] [CrossRef] [PubMed]
- Henrandez-de Mendenez, M.; Escobar, C.; Morales-Menendez, R. Engineering education for smart 4.0 technology: A review. Int. J. Interact. Des. Manuf. 2020, 14, 789–803. [Google Scholar] [CrossRef]
- Adbul-Hamid, A.; Ali, M.; Osman, L.; Tseng, M. The drivers of industry 4.0 in a circular economy: The palm oil industry in Malaysia. J. Clean. Prod. 2021, 324, 129216. [Google Scholar] [CrossRef]
- Najaf, K.; Mostafiz, M.; Najaf, R. Fintech firms and banks sustainability: Why cybersecurity risk matters? Int. J. Financ. Eng. 2021, 8, 2150019. [Google Scholar] [CrossRef]
- Calabrese, A.; Costa, R.; Tiburzi, L.; Brem, A. Merging two revolutions: A human-artificial intelligence method to study how sustainability and Industry 4.0 are intertwined. Technol. Forecast. Soc. Chang. 2023, 188, 122265. [Google Scholar] [CrossRef]
- Sulich, A.; Rutkowska, M.; Krawczyk-Jezierska, A.; Jezierski, J.; Zema, T. Cybersecurity and Sustainable Development. Procedia Comput. Sci. 2021, 192, 20–28. [Google Scholar] [CrossRef]
- Muhammad, Z.; Anwar, Z.; Saleem, B.; Shahid, J. Emerging Cybersecurity and Privacy Threats to Electric Vehicles and Their Impact on Human and Environmental Sustainability. Energies 2023, 16, 1113. [Google Scholar] [CrossRef]
- Lim, H.; Taeihagh, A. Autonomous Vehicles for Smart and Sustainable Cities: An In-Depth Exploration of Privacy and Cybersecurity Implications. Energies 2018, 11, 1062. [Google Scholar] [CrossRef]
- Ramírez, M.; Ariza, L.R.; Miranda, M.E.G.; Vartika. The Disclosures of Information on Cybersecurity in Listed Companies in Latin America—Proposal for a Cybersecurity Disclosure Index. Sustainability 2022, 14, 1390. [Google Scholar] [CrossRef]
- Ponce, H.G.; González, J.C.; Al-Mohareb, M. Sustainable finance in cybersecurity investment for future profitability under uncertainty. J. Sustain. Financ. Invest. 2023, 13, 614–633. [Google Scholar] [CrossRef]
- Fernandez, C.M.; Alves, J.; Gaspar, P.D.; Lima, T.M. Fostering Awareness on Environmentally Sustainable Technological Solutions for the Post-Harvest Food Supply Chain. Processes 2021, 9, 1611. [Google Scholar] [CrossRef]
- Annarelli, A.; Palombi, G. Digitalization Capabilities for Sustainable Cyber Resilience: A Conceptual Framework. Sustainability 2021, 13, 13065. [Google Scholar] [CrossRef]
- Abbas, H.S.M.; Qaisar, Z.H.; Ali, G.; Alturise, F.; Alkhalifah, T. Impact of cybersecurity measures on improving institutional governance and digitalization for sustainable healthcare. PLoS ONE 2022, 17, e0274550. [Google Scholar] [CrossRef]
- Blažič, B.J.; Blažič, A.J. Cybersecurity Skills among European High-School Students: A New Approach in the Design of Sustainable Educational Development in Cybersecurity. Sustainability 2022, 14, 4763. [Google Scholar] [CrossRef]
- Fan, Y.; Li, J.; Zhang, D.; Pi, J.; Song, J.; Zhao, G. Supporting Sustainable Maintenance of Substations under Cyber-Threats: An Evaluation Method of Cybersecurity Risk for Power CPS. Sustainability 2019, 11, 982. [Google Scholar] [CrossRef]
- D’Adamo, I.; González-Sánchez, R.; Medina-Salgado, M.S.; Settembre-Blundo, D. Methodological Perspective for Assessing European Consumers´ Awareness of Cybersecurity and Sustainability in E-Commerce. Sustainability 2021, 13, 11343. [Google Scholar] [CrossRef]
- Hu, J.L.; Chen, Y.C.; Yang, Y.P. The Development and Issues of Energy-ICT: A Review of Literature with Economic and Managerial Viewpoints. Energies 2022, 15, 594. [Google Scholar] [CrossRef]
- Shackelford, S. Exploring the Shared Responsibilityy of Cyber Peace: Should Cybersecurity Be a Human Right? SSRN Electron. J. 2017. [Google Scholar] [CrossRef]
- Sadik, S.; Ahmed, M.; Sikos, L.F.; Islam, A.K.M.N. Toward a Sustainable Cybersecurity Ecosystem. Computers 2020, 9, 74. [Google Scholar] [CrossRef]
- Cassotta, S.; Sidortsov, R. Sustainable cybersecurity? Rethinking approaches to protecting energy infrastructure in the European High North. Energy Res. Soc. Sci. 2019, 51, 129–133. [Google Scholar] [CrossRef]
- Soltovski, R.; de Resende, L.M.M.; Pontes, J.; Yoshino, R.T.; da Silva, L.B.P. Um estudo quantitativo sobre os riscos da indústria 4.0 no contexto industrial: Uma revisão sistemática da literatura. Rev. Gestão Desenvolv. 2020, 17, 165. [Google Scholar] [CrossRef]
- D’Arcy, J.; Basoglu, A. The Influences of Public and Institutional Pressure on Firms’ Cybersecurity Disclosures. J. Assoc. Inf. Syst. 2022, 23, 779–805. [Google Scholar] [CrossRef]
- Sidibé, A.; Olabisi, L.S.; Doumbia, H.; Touré, K.; Niamba, C.A. Barriers and enablers of the use of digital technologies for sustainable agricultural development and food security. Elem. Sci. Anthr. 2021, 9, 00106. [Google Scholar] [CrossRef]
- Polverini, D.; Ardente, F.; Sanchez, I.; Mathieux, F.; Tecchio, P.; Beslay, L. Resource efficiency, privacy and security by design: A first experience on enterprise servers and data storage products triggered by a policy process. Comput. Secur. 2018, 76, 295–310. [Google Scholar] [CrossRef]
- Shackelford, S. Shoul cybersecurity be a human right? Exploring the Shared responsibillity of cyberpeace. In Music, Business and Peacebuilding; Routledge: London, UK, 2021; pp. 174–197. [Google Scholar]
- Cui, Y.; Kara, S.; Chan, K. Manufacturing big data ecosystem: A systematic literature review. Robot. Comput.-Integr. Manuf. 2020, 62, 101861. [Google Scholar] [CrossRef]
- Ganji, K.; Afshan, N. A bibliometric review of Internet of Things (IoT) on cybersecurity issues. J. Sci. Technol. Policy Manag. 2024; ahead-of-print. [Google Scholar] [CrossRef]

| Category | Covered Content | Foundation |
|---|---|---|
| I. Descriptive characteristics of the literature | 1. Quality of journals and areas of knowledge 2. Temporal distribution of publications 3. Funding institutions 4. Frequency by most citations | Describe the characteristics of the sample analyzed |
| II. Conceptual and definitional issues | 5. Frequency and network of key terms 6. Analysis of the use of definitions | To explore the consistency or variation in the researchers’ definitions of the variables. Define the territory that researchers claim lies within sustainable cybersecurity |
| III. Meetings between cybersecurity and sustainable development | 7. Aspects of sustainable development 8. Cybersecurity and sustainability dimensions and indicators 9. Links between cybersecurity and sustainable development | Analyzing and synthesizing the links between cybersecurity and sustainability |
| IV. Questions about method and technique | 10. Types of research. | Know the paths used to explore the variables studied |
| No | Journal | Area | Records | Ranking |
|---|---|---|---|---|
| 1 | Sustainability | Environmental Science | 36 | Q2 |
| 2 | Journal of Cleaner Production | Engineering | 7 | Q1 |
| 3 | IEEE Access | Business Economics | 5 | Q2 |
| 4 | Computer Security | Computer Science | 4 | Q2 |
| 5 | Baltic Journal of Economic Studies | Business Economics | 4 | Q2 |
| 6 | Information | Computer Science | 4 | Q2 |
| 7 | Journal of the Knowledge Economy | Business Economics | 4 | Q2 |
| 8 | Technological Forecasting and Social Change | Business Economics | 4 | Q1 |
| 9 | International Journal for Quality Research | Engineering | 3 | Q2 |
| 10 | Sustainable Energy Technologies and Assessments | Energy | 3 | Q1 |
| Institution | N° of Publications | Country |
|---|---|---|
| Indiana University | 9 | USA |
| Bucharest University of Economic Studies | 7 | Romania |
| Lutsk National Technical University | 7 | Ukraine |
| National University of Life and Environmental Sciences | 7 | Ukraine |
| Royal Melbourne Institute of Technology | 7 | Australia |
| Dasia University | 6 | Taiwan |
| Seoul National University | 6 | South Korea |
| Shanghai Maritime University | 6 | China |
| University of Johannesburg | 6 | South Africa |
| Delhi Technological University | 5 | India |
| Research | Title | Magazine | Total Citations |
|---|---|---|---|
| Litvinenko [32] | Digital Economy as a Factor in the Technological Development of the Mineral Sector | Natural Resources Research | 229 |
| Ghobakhloo [23] | Corporate survival in Industry 4.0 era: the enabling role of lean-digitized manufacturing | Journal of Manufacturing Technology Management | 222 |
| Fraga-Lamas and Fernández-Caramés [21] | A Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry | IEEE Access | 152 |
| Laskuraín-Iturbe et al. [33] | Exploring the influence of Industry 4.0 technologies on the circular economy | Journal of Cleaner Production | 72 |
| Gupta et al. [44] | Examining the impact of Cloud ERP on sustainable performance: A dynamic capability view | International Journal of Information Management | 67 |
| Murch et al. [45] | Cyberbiosecurity: An Emerging New Discipline to Help Safeguard the Bioeconomy | Frontiers in Bioengineering and Biotechnology | 56 |
| Rodger and George [20] | Triple bottom line accounting for optimizing natural gas sustainability: A statistical linear programming fuzzy ILOWA optimized sustainment model approach to reducing supply chain global cybersecurity vulnerability through information and communications technology | Journal of Cleaner Production | 42 |
| Hernández et al. [46] | Engineering education for smart 4.0 technology: a review. | International Journal on Interactive Design and Manufacturing (IJIDeM) | 48 |
| Adbul-Hamid et al. [47] | The drivers of Industry 4.0 in a circular economy: The palm oil industry in Malaysia | Journal of Cleaner Production | 23 |
| Najaf et al. [48] | Fintech firms and banks sustainability: Why cybersecurity risk matters? | International Journal of Financial Engineering | 19 |
| Category | Research | Count * |
|---|---|---|
| (a) Cybersecurity Concepts | Abdul-Hamid et al. [47]; Calabrese et al. [49]; Litvinenko [32]; Sulich et al. [50]; Muhammad et al. [51]; Lim [52]; Radu and Samili [28]; Ram et al. [24]. | 8 |
| (b) Implicit Concept of Cybersecurity | Laskurain-Iturbe et al. [33]; Gupta et al. [44]; Morales-Menendez [18]; Malatji et al. [36]; Rodger and George [20]; Ramírez et al. [53]; Gutiérrez et al. [54]; Shackelford [35]; Fernández et al. [55]; Najaf and Mostafiz et al. [48]; Fraga-Lamas and Fernández Caramés et al. [21]; Chun [34]; Annarelly and Palombi [56]; Arcuri et al. [22]; Abbas et al. [57]; Jerman et al. [58]; Fan et al. [59]; D’Adamo et al. [60]; Hu et al. [61]; Shackelford [62]; Okpa [29] (2022); Wang et al. [31]; Škerháková et al. [30]; Shaikh and Siponen [27]; Ghobakhlo et al. [23]. | 25 |
| (c) Sustainable Cybersecurity Concept | Murch et al. [45]; Annarelly and Palombi [56]; Sadik et al. [63]; Cassota and Sidortov [64] | 4 |
| (d) No concept of cybersecurity | Soltovski et al. [65]; D’Arcy and Basoglu [66]; Sidibé et al. [67]; Polverini et al. [68] | 4 |
| Research | Type */Definition of Cybersecurity |
|---|---|
| Rodger and George [20] | [I-O]/Cybersecurity is addressed as a potential threat to the sustainability of the natural gas supply chain. It protects computer systems, networks, and data against unauthorized access, attacks, and damage. It involves implementing measures to prevent, detect, and respond to cyber-threats and ensure information confidentiality, integrity, and availability. |
| Lim [52] | [E-P]/Cybersecurity protects the integrity, confidentiality, and accessibility of information. |
| Chun [34] | [I-O]/In the context of e-commerce and online transactions, cybersecurity is crucial to ensure the privacy and security of customer information and to maintain customers’ confidence in conducting business online. |
| Fan et al. [59] | [I-O]/Threats to the cybersecurity of electrical systems were summarized into four types: unauthorized access to information, unauthorized modification or theft of information, denial of service, and repudiation/lack of accountability. |
| Fraga-Lamas and Fernández-Caramés [21] | [I-O]/Cybersecurity is an important concept in the context of blockchain technology and its application in the automotive industry. Blockchain can improve data security, privacy, and integrity, providing a higher level of cybersecurity to the industry. |
| Arcuri et al. [22] | [I-O]/In particular, to reduce cyber incidents that can adversely affect the activity of organizations, as well as trust in electronic transactions and customer interactions, companies should invest in cybersecurity infrastructures to protect system networks against unauthorized access and data alteration. |
| Gupta et al. [44] | [I-O]/Organizations should consider cybersecurity when adopting cloud-based operations and services like Cloud ERP. |
| Litvinenko [32] | [E-P]/Cybersecurity is the steady state of protection of information, its carriers, and infrastructure, which ensures the integrity and stability of information-related processes against natural, artificial, intentional, or unintentional impacts. Impacts are information security threats that can harm the subjects of information relationships. |
| Malatji et al. [36] | [I-O]/The authors argue that cybersecurity is not only about implementing technical measures; it is also important to consider the social and organizational aspects of information security. Therefore, the socio-technical approach focuses on the interaction between the technical and non-technical aspects of information security and seeks to optimize both to improve the overall security of business systems. |
| Morales-Menendez [18] | [I-O]/Cybersecurity is essential to ensuring the integrity, confidentiality, and availability of data and systems and to mitigate the risks associated with interconnected industrial networks. |
| Shackelford [69] | [I-O]/Cybersecurity refers to the protection of computer systems and networks against unauthorized access, data theft, service interruption, and other types of cyber-attacks. The paper explores how cybersecurity relates to human rights and cyber peace and how it can be improved domestically and internationally. |
| Abdul-Hamid et al. [47] | [E-P]/Services and technologies designed to protect industrial users, systems, equipment, networks, and data from illicit intrusion. |
| D’Adamo et al. [60] | [I-O]/Cybersecurity is important to ensure the privacy and security of users’ personal and financial information and to protect the integrity of critical systems and infrastructure. In the context of e-commerce, cybersecurity is essential to ensure consumer confidence in online transactions and to protect them from potential fraud. |
| Férnandez et al. [55] | [I-O]/To formulate appropriate risk mitigation strategies, it is essential to understand the cybersecurity risk and threat landscape to classify, detect, analyze, protect, and protect privacy. |
| Gutierrez et al. [54] | [I-O]/It involves developing and implementing technologies and strategies to prevent and mitigate cyber-attacks, hacking, and cybersecurity breaches. |
| Laskurain-Iturbide et al. [33] | [I-O]/Cybersecurity protects computer systems, networks, and data from unauthorized access, attacks, and damage. It involves implementing measures to prevent, detect, and respond to threats and vulnerabilities in digital environments. Cybersecurity is crucial to ensure the confidentiality, integrity, and availability of information and systems and to safeguard against cybercrime and data breaches. It encompasses various technologies, processes, and practices to secure digital assets and mitigate the risks associated with cyber-threats. |
| Najaf et al. [48] | [I-O]/Cybersecurity refers to the measures and practices used to protect computer systems, networks, and data from unauthorized access, attacks, and damage. It protects information and technology assets against cyber-threats such as hacking, data breaches, malware, and phishing attacks. |
| Sulich et al. [50] | [E-P]/The concept of cybersecurity is related, among other things, to protecting the information processing space and the interactions in information technology networks. |
| Hu et al. [61] | [I-O]/Cybersecurity refers to the measures and practices to protect computer systems, networks, and data from unauthorized access, attacks, and damage. It involves using technologies, processes, and policies to prevent, detect, and respond to cyber-threats and ensure information and systems’ confidentiality, integrity, and availability. |
| Jerman et al. [58] | [I-O]/Effective cybersecurity education and awareness are crucial for individuals and organizations to understand the risks and adopt best practices to mitigate them. |
| Abbas et al. [57] | [I-O]/In healthcare, cybersecurity measures are crucial to ensure the security and privacy of sensitive patient data and the smooth functioning of digital health systems. |
| Ramírez et al. [53] | [I-O]/For the corporate realm, cybersecurity becomes an inescapable business responsibility, and accountability becomes a way to provide trust and ensure resilience in the face of high-impact cyber risks and threats. |
| Calabrese et al. [49] | [E-P]/A set of technologies that enable data security, storage, and transfer. |
| Muhammad et al. [51] | [E-P]/Cybersecurity is the practice of protecting networks, systems, and programs from cyber-attacks. |
| Ghobakhlo et al. [23] | [I]/Cybersecurity ensures the safety, reliability, and security of communications between interconnected devices within the Industry 4.0 environment. |
| Ram et al. [24] | [P]/Defending against cyber-threats is crucial as it prevents unauthorized use, denial of service, modification, disclosure, loss of revenue, or even the destruction of critical systems or information assets, which can have severe consequences for your organization. |
| Radu and Smaili [28] | [P]/It is the activity, process, ability, or state by which information and communications systems and the information contained are protected and defended against damage, unauthorized use or modification, or exploitation. |
| Naffa and Fain [26] | [I]/Cybersecurity is considered an essential topic in corporate governance, and its relevance to the responsibility of boards of directors to protect companies in cyberspace and manage associated cyber risks is highlighted. |
| Bondarenk et al. [25] | [I]/They note that increased digitization and the development of financial technology have led to an increased focus on cybersecurity to protect systems and data in the financial sector. |
| Okpa et al. [29] | [I]/The authors strongly advocate for the need to take proactive measures and stay ahead of the latest trends and threats in cybersecurity. This approach empowers your organization to protect both itself and its individuals from potential cyber-attacks, giving you a sense of control in an ever-evolving digital landscape. |
| Wang et al. [31] | [I]/Cybersecurity is not just a protective measure, it is a vital element that ensures the smooth operation of business activities in a highly competitive and Internet-dependent environment, giving your organization a sense of security and confidence. |
| Škerháková et al. [30] | [I]/The company’s management team stresses that cybersecurity is a significant part of sustainable corporate reputation and that proper online reputation management is essential for companies in a constantly evolving digital environment. |
| Shaikh and Siponen [27] | [I]/Refers to the measures, practices, and strategies organizations implement to protect their information systems, networks, and data against cyber-threats, such as attacks, intrusions, and security breaches. |
| Research | Social Aspects | Environmental Aspects | Economic Aspects | Dimensions of Sustainability |
|---|---|---|---|---|
| Shackelford [62] | 🗸 | 🗸 | Polycentric governance: Cybersecurity best practices in the public and private sectors would help reduce threats of conflict, crime, and cyber espionage comparable to national and enterprise security risks. | |
| Rodger and George [20] | 🗸 | 🗸 | 🗸 | Economic: Economic gains, transparency, social responsibility. Social: Employee well-being, community involvement, work practices. Environmental: environmental impact, carbon emissions, energy conservation. |
| Polverini et al. [68] | 🗸 | Resource Efficiency and Reduction of Environmental Impacts. | ||
| Murch et al. [45] | 🗸 | 🗸 | 🗸 | Environmental sustainability, social equity, inclusivity, economic viability, governance, and institutions. |
| Lim [52] | 🗸 | 🗸 | 🗸 | Transport Infrastructure. |
| Casotta and Sidortov [64] | 🗸 | 🗸 | 🗸 | Critical Infrastructure, Energy Sector, Governance. |
| Fan et al. [59] | 🗸 | Energy. | ||
| Fraga-Lamas and Fernández-Caramés [21] | 🗸 | Supplies, gas reduction, sustainable management, resilience to environmental and social impacts. | ||
| Gupta et al. [44] | 🗸 | 🗸 | 🗸 | Economic performance, environmental performance, and social performance. |
| Litvinenko [32] | 🗸 | Sustainable planning, distribution of energy resources and materials, infrastructure development, clean energy, renewable energies, energy efficiency of investment, and mining industry training that addresses technical, economic, environmental, governance, and social aspects. | ||
| Morales-Menendez [18] | 🗸 | 🗸 | 🗸 | It addresses sustainability-related challenges such as reducing energy consumption and reducing greenhouse gases. |
| Malatji et al. [36] | 🗸 | Cybersecurity is an element for awareness campaigns and consideration of protecting privacy and user rights, which contributes to social sustainability. | ||
| Sadik et al. [63] | 🗸 | 🗸 | 🗸 | Sustainable security, sustainable cybersecurity. |
| Abdul-Hamid et al. [47] | 🗸 | 🗸 | 🗸 | Sustainability awareness, stakeholders, supply chain collaboration, waste management, emission reduction, and natural resource conservation, Blockchain can contribute to and benefit the circular economy, economic recovery, and social and environmental sustainability. |
| Fernández et al. [55] | 🗸 | 🗸 | Circular economy, food supply chain. | |
| Laskurain et al. [33] | 🗸 | 🗸 | The circular economy involves reducing input consumption, reuse, recycling, reducing waste and emissions, preventing money laundering (Blockchain), and protecting privacy and data. | |
| Shackelford [69] | 🗸 | 🗸 | 🗸 | They argue that organizations should treat cybersecurity as a matter of corporate social responsibility (CSR) and make an integrated assessment of public policies, environmental sustainability, intergenerational equity, political participation, and intergenerational responsibility. |
| Sidibé and Olabisi [67] | 🗸 | 🗸 | Digital technologies in sustainable agriculture and food security. | |
| Sulich et al. [50] | 🗸 | 🗸 | 🗸 | Environmental protection, social equity, economic viability. |
| Hu et al. [61] | 🗸 | 🗸 | 🗸 | Energy footprint, carbon, climate change, sustainable development goals. |
| Jerman et al. [58] | 🗸 | Education. | ||
| Abbas et al. [57] | 🗸 | 🗸 | Governance and institutional capacity, strengthening institutions, promoting transparency, accountability, and governance for sustainable development. | |
| Muhammad et al. [51] | 🗸 | 🗸 | 🗸 | Life and well-being, safe environment, innovation, and development. |
| Gutiérrez [54] | 🗸 | 🗸 | 🗸 | Ensuring resilient infrastructure, promoting inclusive and sustainable Industrialization. |
| Naffa and Fain [26] | 🗸 | 🗸 | 🗸 | Corporate governance; corporate governance. Energy efficiency, food security, water scarcity. |
| Bondarenko et al. [25] | 🗸 | 🗸 | Sustainable development of financial technologies, user confidence, and personal data protection. | |
| Okpa et al. [29] | 🗸 | 🗸 | Economic sustainability; business and financial sustainability. | |
| Wang et al. [31] | 🗸 | Corporate sustainability. | ||
| Škerháková et al. [30] | 🗸 | 🗸 | Social responsibility, sustainable corporate reputation. | |
| Shaikh and Siponen [27] | 🗸 | Organizational learning; business resilience. | ||
| Ghobakhlo et al. [23] | 🗸 | 🗸 | Business sustainability, productivity efficiency, and business competitiveness. | |
| Radu and Smaili [28] | 🗸 | 🗸 | Supply chain sustainability. |
| Research | Cybersecurity | Sustainability |
|---|---|---|
| Shackelford [62] | Technical vulnerability, hardware failures, configuration issues, laws and regulations, privacy, data protection, cybersecurity breaches, censorship, cyber peace. | Polycentric Governance |
| Rodger and George [20] | Economic: profits, transparency, social responsibility. Social: Employee well-being, community involvement, work practices. Environmental: Environmental impact, carbon emissions, energy conservation. | |
| Lim [52] | Privacy risks, security risks | transport infrastructure, greenhouse gas emissions. |
| Polverini et al. [68] | Privacy, data protection, digital infrastructure. | resource efficiency, reduction of environmental impact. |
| Murch et al. [45] | Biosecurity, supply chain security, data privacy and confidentiality, risk assessment and management, regulatory and legal considerations. | environmental sustainability, social equity and inclusivity, economic viability, governance and institutions. |
| Cassotta and Sidortov [64] | Sustainable/Sustainable Cybersecurity | Definition of cybersecurity |
| Fan et al. [59] | Confidentiality, integrity, information availability, risks, intrusion detection and prevention, user and device authentication and authorization, vulnerability management, user education and awareness. | Energy |
| Fraga-Lamas et al. [21] | Encryption, Authentication, Access Control, Network Security, Security Policies, Risk Management, Incident Response, Awareness and Training, Resilience, Legal and Regulatory Dimensions, User Behavior, Social Engineering, Cyber-Threat Psychology. Implementation costs, impact of cyber-attacks, ROI on cybersecurity solutions, critical infrastructure. | Supply chain management, gas reduction, sustainable management, resilience to environmental and social impacts. |
| Chun [34] | Personal and Financial Data Protection—Fraud and Cybercrime Prevention—Network Infrastructure and Computer Systems Security—Protection against Viruses, Malware and Other Cyber Risks—Password Management and User Authentication—Privacy Policies and Information Security—Online Safety User Training and Awareness—Compliance with Cyber Security Laws and Regulations—Incident Management Security | Emergency Response. |
| Gupta et al. [44] | Economic Performance, Environmental Performance, Social Performance. | |
| Morales-Menendez [18] | Attacks, decreased productivity, counterfeiting, theft. | It hints at some challenges related to sustainability, such as reducing energy consumption and greenhouse gases. |
| Malatji et al. [36] | Organizational: communication, cybersecurity governance, physical access controls, awareness campaigns, organizational structure. Technical: Antimalware, antivirus, user awareness policies. | |
| Litvinenko [32] | Reliability, Security, Storage and Use of Data in the Mineral Sector. | Sustainable planning, distribution of material and energy resources, development of infrastructure such as clean energy, renewable energies, energy efficiency, and investment. It mentions the need for high training in the mining industry that addresses technical, economic, environmental, governance and social factors. |
| Arcuri et al. [22] | Confidentiality, integrity, availability, risk management, incident response, infrastructure security. | |
| Laskurain et al. [33] | Security, Reliability, Protection, Trust: Confidentiality, Integrity, Availability, Authentication, Authorization, Resilience, Risk Management. | Circular Economy: Reduction of Input Consumption, Reuse, Recycling, Reduction of Waste and Emissions, Prevention of Money Laundering (Blockchain), Privacy and Data Protection. |
| Sadik et al. [63] | Assets, Threats, Vulnerabilities, Risk, Assessment, Mitigation, Resilience. | Sustainable Security, Sustainable Cybersecurity. |
| Abdul et al. [47] | Protection of the user, systems, equipment, networks, data. | Stakeholders, sustainability awareness, supply chain collaboration, waste management, emissions reduction, and natural resource conservation. |
| D’Adamo et al. [60] | Data Protection, Attack Prevention, Transaction Security, Trust. | |
| Fernández et al. [55] | Industry Digitalization, Associated Logistics, Strategies, Risk Mitigation, and Asset Protection | Circular Economy, Food Supply Chain. |
| Gutiérrez et al. [54] | I+D in cybersecurity | |
| Najaf et al. [48] | Encryption systems, data integrity, cloud computing. | |
| Shackelford [69] | Confidentiality, integrity, availability, consistency, control, and auditing to build trust. | Integrated evaluation of public policies, environmental sustainability, intergenerational equity, political participation, intergenerational responsibility. |
| Sidibé and Olabisi [67] | Digital Capabilities and Skills, Device Security, Infrastructure and Support Services. | Digital Technologies in Sustainable Agriculture and Food Security. |
| Sulich et al. [50] | Technical, legal, organizational, and cultural. Green Cybersecurity. | Environmental protection, social equity, economic viability. |
| D’Arcy and Basoglu [66] | Breaches, viruses, information security, intrusion, cyber-attack, computer virus, data theft, risks, phishing, cyber-attack. | |
| Hu et al. [61] | Security, Data Privacy, Laws and Regulations, Confidentiality, Availability and Integrity, Privacy. | Energy footprint, carbon, climate change Sustainable development goals. Governance. |
| Jerman and Jerman [58] | Cybersecurity Awareness, Online Shopping Security, Cybersecurity Skills, Knowledge, Experience, Privacy, Data Protection. | Education |
| Abbas et al. [57] | Data Protection, Firewall, Threat Detection, Vulnerability Management | Governance and institutional capacity: strengthening institutions, promoting transparency, accountability, and good governance practices to support sustainable development efforts. |
| Ramírez et al. [53] | Risk, Incident and Breach Management. | |
| Calabrese et al. [49] | Security, attack, vulnerability, threat, privacy, phishing, defense, cyber-attack, intelligence, malicious, detection, sophisticated, hacking, software, secure, cloud, information, digital, tactical, crime, response, detection, analytics, regulation, networks, Internet, accessibility, applicability, digitalization. | Environmental footprint |
| Muhammad et al. [51] | Confidentiality, integrity, and availability of data and systems, security maturity, incident responsiveness, effectiveness of controls. Network Security, Software Security, and Data Security. | Innovation and Development. |
| Ghobakhlo et al. [23] | Cyber security. | Business sustainability, productivity efficiency, and business competitiveness. |
| Ram et al. [24] | Information security, information protection, data leakage, cyber-attacks. | Supply chain sustainability. Continuity and integrity of operations. |
| Naffa and Fain [26] | Cyber risks, disruptive technologies. | Corporate governance; corporate governance. Energy efficiency, food security, water scarcity. |
| Bondarenk et al. [25] | Fraud, cyber-attack, security of financial transactions, resilience of systems. | Sustainable development of financial technologies, user confidence, personal data protection. |
| Radu and Smaili [28] | Confidentiality, integrity, and availability of information. | Sustainability initiatives. |
| Okpa et al. [29] | Information protection, cybersecurity awareness, security software, and financial transaction security. | Economic, business and financial sustainability. |
| Wang et al. [31] | Cybersecurity awareness and training, prevention and management of vulnerabilities, protection of data and digital assets. | Corporate sustainability; sustainability of operations. |
| Škerháková et al. [30] | Digital security. | Social responsibility; sustainability promotion; sustainable corporate reputation. |
| Shaikh and Siponen [27] | Cybersecurity performance. | Organizational learning; organizational resilience. |
| Category | Research | Count |
|---|---|---|
| (a) Relationship between cybersecurity and sustainable development. | Laskurain-Iturbe et al. [33]; Malatji et al. [36]; Soltovski et al. [65]; Rodger and George [20]; Abdul-Hamid et al. [47]; Hu et al. [61]; Gutiérrez [54]; Shackelford [62]; Fernández et al. [55]; Najaf et al. [48]; Litvinenko [32]; Fraga-Lamas and Fernández-Caramés [21]; Chun [34]; Anarelly and Palombi [56]; Sulich et al. [50]; Murch et al. [45]; Arcuri et al. [22]; Abbas et al. [57]; Muhammad et al. [51]; Jerman et al. [58]; Sidibé and Olabisi [67]; Lim [52]; Sadik et al. [63]; Cassotta and Sidortov [64]; Fan et al. [59]; Ghobakhlo et al. [23]; Ram et al. [24]; Naffa and Fain [26]; Bondarenko et al. [25]; Radu and Smaili [28]; Okpa et al. [29]; Wang et al. [31]; Škerháková et al. [30]; Shaikh and Siponen [27]; D’Adamo et al. [60] | 35 |
| (b) No reference/relationship between cybersecurity and sustainable development. | Gupta et al. [44]; Morales-Menendez [18]; D’Arcy and Basoglu [66]; Ramirez et al. [53]; Polverini et al. [68]; Calabrese et al. [49] | 6 |
| TOTAL | 41 |
| Research | Reference to Cybersecurity and Sustainable Development |
|---|---|
| Rodger and George [20] | The paper links cybersecurity to sustainable development by addressing its importance in managing the global natural gas supply chain, reducing the risk of disruptions, and improving efficiency and transparency in supply chain management. |
| Lim [52] | Secure and affordable access to global networks is a crucial criterion for social and economic progress, ensuring cybersecurity and privacy while expanding Internet access and inculcating human rights is vital for sustainable development. |
| Chun [34] | It helps protect customers’ sensitive information, maintain privacy, and prevent identity theft, thus fostering a secure and trustworthy digital ecosystem. By addressing cybersecurity challenges and ensuring the resilience of digital systems, sustainable development goals related to innovation, economic growth, and social well-being can be achieved. |
| Fan et al. [59] | Cybersecurity is essential to ensuring the security and stability of critical infrastructure, protecting the environment, and improving energy efficiency, which contributes to sustainable development. However, cybersecurity measures also promote the resilience of energy systems, allowing them to resist and recover from cyber-attacks, minimizing their impact on sustainable development efforts. |
| Fraga-Lamas and Fernández-Caramés [21] | Cybersecurity is related to sustainable development, as it plays a crucial role in ensuring the long-term viability and resilience of digital systems and infrastructures. By improving data security, privacy, and integrity, blockchain technology can contribute to sustainable development by providing a secure foundation for various industries, including the automotive sector. Using blockchain in the automotive industry can improve data security, privacy, anonymity, traceability, and accountability, leading to higher cybersecurity. |
| Arcuri et al. [22] | The sources discussed the relationship between cybersecurity and sustainable development, highlighting the importance of cybersecurity in achieving the SDGs and the potential negative impact of cyber-attacks on the economic value and growth of the hotel sector. |
| Murch et al. [45] | Cyber biosecurity plays a crucial role in safeguarding the bio-economy and the sustainable development of sectors dependent on biological and biomedical systems. It ensures their safe use while minimizing risks and potential damage. |
| Litvinenko [32] | It delves into aspects such as the development of integrated and advanced mineral processing systems, the efficient use of energy and material resources, and the management of industrial and domestic waste, highlighting the role of digitalization and the integration of data, processes, and users in the mining industry to achieve scientific and technological advances. It also underlines how digital technology can drive sustainable development along the entire value chain, from exploration and production to sustainable resource planning and distribution. The study contributes significantly to cybersecurity and sustainable development in the mineral sector by providing a comprehensive view of how digital technology can improve efficiency, safety, and sustainability in using mineral resources. |
| Malatji et al. [36] | Although it is not explicitly mentioned, it refers to cybersecurity as an important element for the sustainable development of companies and business society. It highlights the importance of protecting users’ privacy and rights, which contributes to social sustainability. |
| Shackelford [69] | They argue that organizations should treat cybersecurity as a matter of corporate social responsibility (CSR) to safeguard their customers and the public, similar to companies’ role in fostering sustainability. |
| Abdul-Hamid et al. [47] | It is not explicitly mentioned, but it refers to the fact that digitalization, including blockchain technology, can contribute to the circular economy and, therefore, benefit economic recovery and social and environmental sustainability. |
| D’Adamo et al. [60] | In the context of e-commerce, cybersecurity is important to ensure consumer confidence in online transactions and to protect them from potential fraud and scams, which can, in turn, foster the sustainable growth of e-commerce. |
| Férnandez et al. [55] | Cybersecurity is crucial in achieving sustainable development, particularly in the logistics, supply chain, and agriculture. It ensures the protection of critical infrastructure, data, and systems, which are essential for these sectors’ efficient and secure operation and play a vital role in achieving the Sustainable Development Goals. |
| Gutierrez et al. [54] | By safeguarding data and systems, cybersecurity ensures the continuity of operations, avoiding disruptions that can have negative environmental, social, and economic impacts. In addition, it contributes to sustainable development goals such as ensuring resilient infrastructure and promoting inclusive and sustainable industrialization, which are supported by robust cybersecurity measures. |
| Laskurain-Iturbide et al. [33] | Cybersecurity is critical in the context of the circular economy, as it helps to ensure the traceability of products, prevent corporate circular laundering, and promote good practices that enhance circularity. It also addresses privacy and data protection concerns, which are crucial for building trust in digital technologies and promoting their adoption for sustainable development. |
| Najaf et al. [48] | Cybersecurity threats constantly put the assets and information of corporations, institutions, governments, and individuals, including financial institutions, at constant risk, which can have implications for sustainable development. |
| Sulich et al. [50] | It mentions that cybersecurity is essential to protect ICTs and the information they handle and that the lack of security can be a significant obstacle to sustainable development. In short, cybersecurity is an indispensable element for the success of the green technological revolution and for achieving sustainable development goals. Cybersecurity measures help counter attacks by criminal groups and prevent the penetration of hostile entities, thus safeguarding sustainable development efforts. |
| Hu et al. [61] | By protecting Energy-IT systems from cyber-threats, cybersecurity contributes to the stability and security of the energy sector, enabling the transition to a greener and more sustainable energy economy. |
| Jerman et al. [58] | The paper focuses on cybersecurity and its importance in education and sustainable development. |
| Abbas et al. [57] | Effective cybersecurity measures in healthcare improve data management systems, online services, and secure Internet services, leading to efficient and secure health services, which are essential for sustainable development. |
| Sadik et al. [63] | Integrating emerging technologies such as blockchain, artificial intelligence, and machine learning into cybersecurity improves the effectiveness and efficiency of security measures, supporting sustainable development efforts. |
| Muhammad et al. [51] | Electric vehicles serve multiple domains of sustainability, and on a broader level, sustainability can be divided into three main domains (also sometimes referred to as sustainability goals), such as (1) life and well-being, (2) safe environment, and (3) innovation and development. |
| Ghobakhlo et al. [23] | In the context of Industry 4.0, cybersecurity plays a pivotal role in ensuring security, reliability, and communication between interconnected devices. |
| Ram et al. [24] | The increasing reliance on information technology and real-time information sharing in supply chains makes cybersecurity a critical aspect of protecting information assets and technology infrastructure. |
| Naffa and Fain [48] | Cybersecurity is crucial to ensuring the long-term sustainability of organizations. Protecting digital assets and data privacy, preventing cyber-attacks, and effectively managing cyber risks are critical elements for business continuity and protecting stakeholders’ interests. |
| Bondarenko et al. [25] | It is highlighted that the sustainable development of FINTECHs focuses on issues of uncertainty and perceived quality, and cybersecurity plays a crucial role in ensuring the sustainability of financial operations in digital environments. |
| Radu and Smaili [28] | It is noted that the effects of cyber-attacks could materialize in financial costs, reputational costs, loss of confidential data, erosion of consumer trust in e-commerce, and violation of privacy, among others. In addition, it is mentioned that cybersecurity is critical not only for shareholders, managers, and employees but also for society as a whole, which highlights the importance of protecting information and systems against potential cyber-threats to ensure a safe and sustainable environment. |
| Okpa et al. [29] | An in-depth analysis reveals the profound impact of cybercrime on companies, affecting their reputation, financial resources, and economic stability. These implications can have far-reaching effects on the sustainable development of businesses. |
| Wang et al. [31] | In a highly competitive and Internet-dependent environment, the importance of cybersecurity for companies cannot be overstated. Proactively mitigating cyber risks is critical to ensuring the sustainability and continuity of business operations in an increasingly complex and challenging digital environment. |
| Škerháková et al. [30] | Cybersecurity is a crucial component in ensuring organizations’ economic sustainability and growth. It protects their assets, data, and business operations from potential cyber-threats that could jeopardize their financial stability and reputation. In this sense, investing in cybersecurity measures is presented as a key strategy to promote a safe and sustainable business environment in today’s digital economy. |
| Shaikh and Siponen [27] | It is pointed out that the relationship between cybersecurity and sustainable development is established through the impact that investments in cybersecurity have on business continuity and the protection of organizations’ digital assets. By ensuring the security of information and technology infrastructure, businesses can mitigate risks, protect data privacy, and maintain the trust of customers and business partners. This cyber protection contributes to the sustainability of business operations and the fulfillment of long-term organizational objectives. In addition, by strengthening cybersecurity, organizations can reduce the negative impact of potential cyber incidents on the environment, society, and economy, thus promoting sustainable development in the digital realm. |
| Research | Conceptual | Analytic Mathematician | Statistical | Experimental Design | Empirical Statistical Sampling | Case Study |
|---|---|---|---|---|---|---|
| Abdul-hamid et al. [47] | 🗸 | 🗸 | ||||
| Calabrese [49] | 🗸 | 🗸 | ||||
| Litvinenko et al. [32] | 🗸 | |||||
| Sulich et al. [50] | 🗸 | 🗸 | ||||
| Muhammad et al. [51] | 🗸 | |||||
| Rodger and George [20] | 🗸 | |||||
| Laskurain-Iturbe et al. [33] | 🗸 | |||||
| Gupta et al. [44] | 🗸 | |||||
| Malatji et al. [36] | 🗸 | |||||
| Gutierrez et al. [54] | 🗸 | |||||
| Polverini et al. [68] | 🗸 | |||||
| Fernández et al. [55] | 🗸 | |||||
| Najaf et al. [48] | ||||||
| Fraga-Lamas and Fernández-Caramés [21] | 🗸 | |||||
| Chun [34] | 🗸 | |||||
| Annarelly and Palombi [56] | 🗸 | |||||
| Arcuri et al. [22] | 🗸 | |||||
| Abbas et al. [57] | 🗸 | |||||
| Jerman et al. [58] | 🗸 | |||||
| Fan et al. [59] | 🗸 | |||||
| D’Adamo et al. [60] | 🗸 | 🗸 | ||||
| Hu et al. [61] | 🗸 | 🗸 | ||||
| Soltovsvki et al. [65] | 🗸 | |||||
| D’Arcy and Basoglu [66] | 🗸 | |||||
| Sidibé and Olabisi [67] | 🗸 | |||||
| Murch et al. [45] | 🗸 | |||||
| Sadik et al. [63] | 🗸 | |||||
| Cassota and Sidortov [64] | 🗸 | |||||
| Ghobakhlo et al. [23] | 🗸 | 🗸 | ||||
| Ram et al. [24] | 🗸 | |||||
| Naffa and Fain [26] | 🗸 | 🗸 | ||||
| Bondarenko et al. [25] | 🗸 | |||||
| Radu and Smaili [28] | 🗸 | 🗸 | ||||
| Okpa et al. [29] | 🗸 | 🗸 | ||||
| Wang et al. [31] | 🗸 | 🗸 | 🗸 | |||
| Škerháková et al. [30] | 🗸 | |||||
| Shaikh and Siponen [27] | 🗸 | 🗸 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Morales-Sáenz, F.I.; Medina-Quintero, J.M.; Reyna-Castillo, M. Beyond Data Protection: Exploring the Convergence between Cybersecurity and Sustainable Development in Business. Sustainability 2024, 16, 5884. https://doi.org/10.3390/su16145884
Morales-Sáenz FI, Medina-Quintero JM, Reyna-Castillo M. Beyond Data Protection: Exploring the Convergence between Cybersecurity and Sustainable Development in Business. Sustainability. 2024; 16(14):5884. https://doi.org/10.3390/su16145884
Chicago/Turabian StyleMorales-Sáenz, Francisco Isaí, José Melchor Medina-Quintero, and Miguel Reyna-Castillo. 2024. "Beyond Data Protection: Exploring the Convergence between Cybersecurity and Sustainable Development in Business" Sustainability 16, no. 14: 5884. https://doi.org/10.3390/su16145884
APA StyleMorales-Sáenz, F. I., Medina-Quintero, J. M., & Reyna-Castillo, M. (2024). Beyond Data Protection: Exploring the Convergence between Cybersecurity and Sustainable Development in Business. Sustainability, 16(14), 5884. https://doi.org/10.3390/su16145884









