1. Introduction
Nowadays, marine transportation plays an important role in international trade. In marine transportation, many ships are equipped with Automatic Identification System (AIS), which can continuously send the dynamic and static information of the ships. This information mainly includes Maritime Mobile Service Identity (MMSI) number, type, position, speed over ground, and course over ground of the ship [
1]. Through the AIS data, the maritime authorities can obtain the navigation status of ships in certain sea areas, thus facilitating the management of maritime traffic.
During navigation, in addition to normal activities, some ships may participate in illegal activities, such as smuggling, pollution, piracy, and unauthorized fishing in protected areas [
2]. These ships may pose a threat to maritime traffic safety and national sovereignty. Therefore, timely detection of dangerous ships with illegal behaviors is an important task in maritime management. In the current researches, the dangerous ships are identified mainly by detecting the abnormal trajectories of ships. The main basis of these researches is that the trajectories of dangerous ships are often out of the ordinary. The authors of [
3] studied the abnormal fishing vessel behavior based on vessel trajectories. The authors of [
4] trained a behavior/interaction model based on trajectory data of ships, and identified abnormal and possibly dangerous situations through the model. The authors of [
5] considered that the vessel trajectory points that did not follow the traffic pattern are anomalous vessel behaviors, and detected anomalous vessel behavior by creating a vessel trajectory predictor. The authors of [
6] proposed a framework named MT-MAD for maritime trajectory modeling and anomaly detection. The authors of [
7] judged whether the ship’s trajectory was abnormal based on type of ship, traffic direction, speed, course, number of stop points, and number of phase changes. The authors of [
8] used trajectory kernels with one-class SVMs to find outlying trajectories. The authors of [
9] proposed a multi-class hierarchy framework to detect anomalous trajectories. However, in these researches, the abnormal trajectories are often defined subjectively, or the detected distinctive trajectories are regarded as abnormal trajectories. There is no uniform standard for the definition of the abnormal trajectory, which also limits the scope of application of related researches.
AIS is a self-reporting system; any self-reporting system is prone to “spoofing” or the intentional reporting of incorrect information [
10]. Therefore, in illegal activities, on the one hand, AIS data transmitted by the ship can be spoofed, on the other hand, the AIS transponder in the ship can be turned off [
11]. Therefore, from another perspective, the correct detection of AIS closing and spoofing can help maritime authorities to detect illegal activities of ships in time, so that the safety of the relevant sea areas can be guaranteed. The authors of [
12] demonstrated the feasibility of radiolocation of AIS emissions, which is the basis for future anti-spoofing and AIS verification applications. The AIS data spoofing mainly includes ship identity (MMSI) spoofing and position spoofing. At this stage, there are some researches on the detection of position spoofing, the authors of [
10] studied this problem with the help of radar measurements and information from the tracking system, but the research was mainly aimed at the single-target case. The authors of [
13] mainly solved the problem of position spoofing by comparing the estimated AIS emitter position and position reported in AIS data, but it required related domain knowledge. The authors of [
14] calculated the speed based on the distance and duration between two AIS points, and determined whether a spoofing event occurred based on the speed, this method was suitable for resolving spoofing events with large changes in position. However, there is less research on MMSI spoofing and AIS closing detection, and it is easier for ships to perform these two behaviors in illegal activities. The authors of [
15] provided an idea for MMSI spoofing and AIS switch-off detection, but no further research has been done. The authors of [
11] determined whether a shortage of AIS messages represented an alerting situation by exploiting the received signal strength information; however, this method relied on ship-related features, like the height of the transmitting antenna, and when the number of ships in a certain sea area is large, it is difficult to obtain the height of the transmitting antenna of each ship. This paper mainly studies the AIS closing and MMSI spoofing problems in multi-ship scenario. In this research, the spatiotemporal data provided by AIS and radar are used without the need for ship-related features, radar is an alternative sensor for maritime surveillance near the ports [
16]. The work of this paper is mainly carried out by finding the association between AIS data and radar data, and analyzing the characteristics of AIS closing behavior and MMSI spoofing behavior. The authors of [
17,
18,
19] studied the association between spatiotemporal data of ships provided by different sensors, which provided the basis for our work. The main contributions of this paper are as follows.
(1) We define the D-TRAP, with the help of D-TRAP, the accuracy of the association between trajectory points can be improved, so as to solve the problem that the associated relationship between AIS data and radar data in the multi-ship scenario is difficult to determine.
(2) We design the AIS closing detection algorithm and MMSI spoofing detection algorithm by establishing the associated AIS trajectory map of radar trajectory. The construction of the associated AIS trajectory map can break the limitation of one-to-one association of trajectories, which can expand the scope of application based on trajectory association, and also increase the robustness of the trajectory association algorithm.
(3) We simulate the AIS closing behavior and MMSI spoofing behavior using real data and simulation data, and verify the effectiveness of the proposed algorithms accordingly.
3. AIS Closing Detection Algorithm
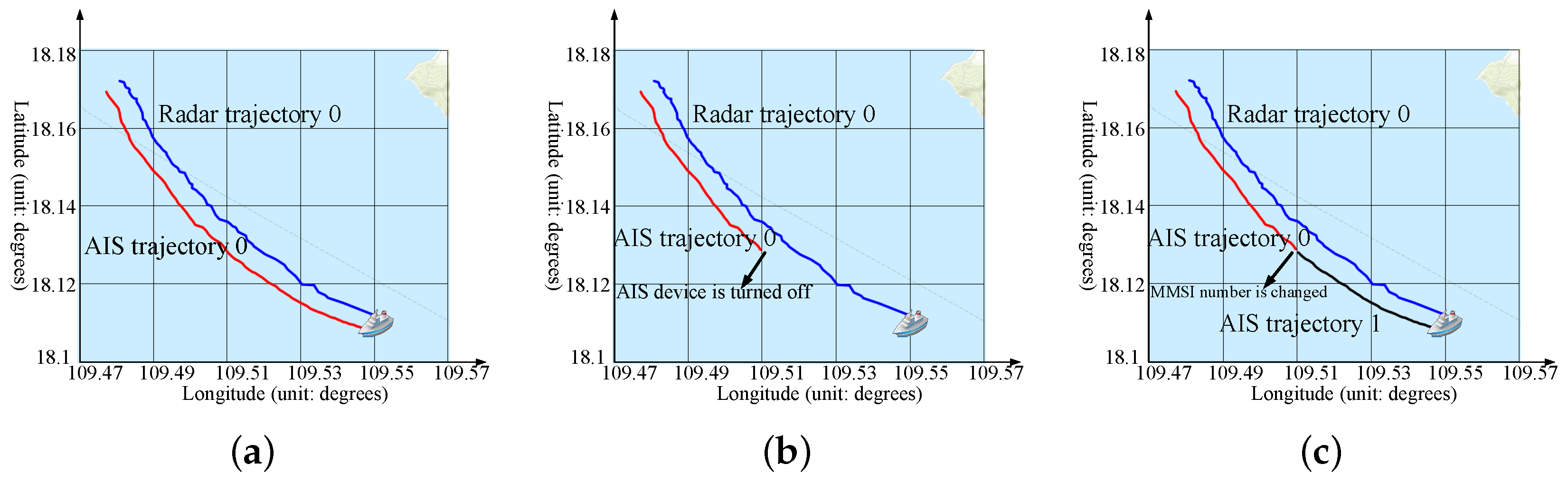
When a ship closes its AIS device, its AIS trajectory will be interrupted, and the range of the AIS trajectory will be smaller than the range of the ship’s real trajectory. Therefore, the AIS closing behavior can be detected by comparing the AIS trajectory range with the ship’s real trajectory range. The formula of trajectory range is as follows.
In the formula, the longitude and latitude of are the maximum longitude and maximum latitude in the trajectory, and the longitude and latitude of are the minimum longitude and minimum latitude in the trajectory. refers to the distance between two points expressed in latitude and longitude.
If the radar can detect the ship before and after the AIS device is closed, the radar trajectory can be considered to some extent as real trajectory. Therefore, it is feasible to detect the AIS closing behavior by comparing the AIS trajectory with the radar trajectory. Because there are many ships in a certain sea area, many radar trajectories and AIS trajectories will be generated. Therefore, the difficulty of the research is determining the radar trajectory and the AIS trajectory generated by the same ship at the same time period, that is, to determine the associated relationship between the radar trajectory and the AIS trajectory. When the ship has AIS closing behavior, the AIS trajectory is changed, and the radar trajectory is not affected. Therefore, the radar trajectory is used as a reference when determining the associated relationship. Algorithm 1 is the pseudocode of the AIS closing detection algorithm.
When looking for the associated trajectory of the radar trajectory, first, the radar trajectory is traversed to find the associated AIS point for each radar point. Due to the large number of AIS points, the search scope needs to be reduced, in this process, the start time and end time of the radar trajectory need to be acquired, which is represented by
and
, respectively, AIS points with timestamps between
and
are considered candidate AIS points,
is the set time interval (line 1, and line 2 in Algorithm 1). When judging whether two trajectory points are associated points, in addition to considering the distance between them, the directions of the two corresponding trajectories at the two points should also be considered. For example, as shown in
Figure 3, take
in the radar trajectory as an example, if only the distance between the trajectory points is considered,
in trajectory AIS0 should be the associated AIS point of
. However, the direction of trajectory AIS0 at
is significantly different from the direction of the radar trajectory at
, the two points are not generated by the same ship. Therefore, when looking for associated AIS point, the directions of trajectories at trajectory points should be considered.
To avoid the influence of detection error, the
Direction of a
TRajectory
At a certain
Point (D-TRAP) is defined as the direction of the vector from the first point successfully associated in the trajectory to the certain point. When determining whether the trajectory point
is the associated point of point
P in trajectory
, the D-TRAP of
at
P needs to be computed, and the formula can be expressed as
. In the paper, D-TRAP is computed when determining whether two trajectory points are associated, that is, D-TRAP occurs in pairs. To improve the accuracy, when computing the D-TRAP value of trajectory
at point
P, in addition to
and
P, the point
to be compared with
P also needs to be considered. According to
, the trajectory
to which it belongs can be obtained,
is the first point associated with
in
, the angle of clockwise rotation from the north direction to the vector
is the D-TRAP value of
at
P when compared with
. For example, in
Figure 3, the associated point of
is
, and the associated point of
is
. Next, the associated point of
needs to be found. When judging whether
is its associated point, first the direction of trajectory AIS0 at
needs to be computed, the first point associated with the radar trajectory in trajectory AIS0 is
, the direction of the vector from
to
is the direction of trajectory AIS0 at
, this direction is represented by the angle of clockwise rotation from the north direction to the vector, as indicated by angle
A in
Figure 3. Then, the direction of the radar trajectory at
at this time needs to be computed, as
to be judged belongs to trajectory AIS0, and the first point associated with trajectory AIS0 in the radar trajectory is
, the direction of the vector from
to
is the direction of the radar trajectory at
at this time, as indicated by angle
B in
Figure 3, angle
A and angle
B are significantly different, so
is not the associated point of
.
At this time, the next candidate point
is judged whether it is the associated point of
. Similarly, the direction of trajectory AIS1 at
needs to be computed, the first point associated with the radar trajectory in trajectory AIS1 is
, the direction of the vector from
to
is the desired direction, as indicated by angle
D in
Figure 3. Then, the direction of the radar trajectory at
at this time needs to be computed, as
to be judged belongs to trajectory AIS1, and the first point associated with trajectory AIS1 in the radar trajectory is
, the direction of the vector from
to
is the desired direction, as indicated by angle
C in
Figure 3, angle
C and angle
D are basically equal, and the distance between
and
is the smallest, therefore,
is the associated point of
.
According to the above process, as the AIS points to be judged belong to different AIS trajectories, and the first radar point associated with the different AIS trajectories may not be the same, the direction of the radar trajectory at the same point may change with the different AIS points to be judged; this also applies to the direction of the AIS trajectory at the same point.
In line 3 with Algorithm 1, the primary key of is the AIS trajectory ID, and the value is the number of associated AIS points from the corresponding AIS trajectory. The primary key of is the AIS trajectory ID, the value is the sequence of radar points associated with the corresponding AIS trajectory, is mainly used to compute the direction of the radar trajectory at a certain radar point. The primary key of is the AIS trajectory ID, and the value is the sequence of AIS points associated with the radar trajectory in the corresponding AIS trajectory, is mainly used to compute the direction of the AIS trajectory at a certain AIS point.
After defining the D-TRAP, the associated AIS point of each point in the radar trajectory can be found in the candidate AIS points. For each radar point, when determining whether a candidate AIS point is its associated point, first, the AIS trajectory to which the candidate AIS point belongs is recorded, and this AIS trajectory is called belonging AIS trajectory. Then, the first point associated with the radar trajectory in the belonging AIS trajectory and the first point associated with the belonging AIS trajectory in the radar trajectory are obtained. Next, the direction of the belonging AIS trajectory at the candidate AIS point and the direction of the radar trajectory at the current radar point are computed, if the difference is small enough, that is, the two directions are basically the same, the distance between the candidate AIS point and the current radar point is computed. If the distance is the shortest distance and meets the set threshold, the candidate AIS point is regarded as the associated AIS point of the current radar point, and update associatedMap, associatedRadarMap, associatedAISMap (lines 4–12 in Algorithm 1).
When all associated AIS points of the radar trajectory have been found,
is sorted by value from big to small, and the AIS trajectory with the largest number of associated AIS points is used as the primary associated trajectory of the radar trajectory (line 13 and line 14 in Algorithm 1). At this time, the timestamp of the earliest AIS point associated with the radar trajectory in the primary associated trajectory is obtained, and the range of the primary associated trajectory after the timestamp is computed, and the result is used as the AIS trajectory range of the ship. Similarly, the timestamp of the earliest radar point associated with the primary associated AIS trajectory in the radar trajectory is obtained, the range of the radar trajectory after the timestamp is computed, and the result is used as the radar trajectory range of the ship (lines 15–18 in Algorithm 1). If the ratio of the AIS trajectory range to the radar trajectory range is less than
, it means that the AIS trajectory is interrupted and the corresponding ship has AIS closing behavior (lines 19–21 in Algorithm 1).
| Algorithm 1 AIS closing detection algorithm. |
| Input: Radar Trajectory, ; Parameter when searching for candidate AIS points, ; threshold to determine whether AIS closing behavior occurs, . |
| Output: AIS trajectory ID with AIS closing behavior. |
| 1: | |
| 2: | |
| 3: | Create associatedMap, associatedRadarMap, associatedAISMap. |
| 4: | for each radar point in do |
| 5: | |
| 6: | if is not null then |
| 7: | |
| 8: | Update |
| 9: | Update |
| 10: | Update |
| 11: | end if |
| 12: | end for |
| 13: | Sort by value from big to small. |
| 14: | |
| 15: | |
| 16: | |
| 17: | |
| 18: | |
| 19: | ifthen |
| 20: | Print out AIS trajectory ID with AIS closing behavior: . |
| 21: | end if |
6. Discussion
This research focuses on the detection of AIS closing and MMSI spoofing during ship navigation. Before designing the corresponding algorithms, the associated relationship between AIS data and radar data needs to be determined. In the multi-ship scenario, this problem is difficult to solve, and when the ship has AIS closing behavior and MMSI spoofing behavior, the corresponding AIS data volume will be reduced, which makes the problem more difficult. Therefore, we introduce the concept of the D-TRAP. According to the aforementioned, this will improve the association accuracy between points, and accordingly, the association accuracy between radar trajectories and their primary associated AIS trajectories will also increase.
Here, we prove it experimentally. The experiment use 175 radar trajectories generated from simulated radar points, and three methods are used to find their associated AIS trajectories. The first two methods are to achieve trajectory association by finding associated AIS points of radar trajectory points, among them, the first is the method proposed in the paper (distance +D-TRAP), and the second is the method based only on distance (only distance). The third is the traditional trajectory association method by computing the distance between trajectories (trajectory-to-trajectory). The simulated radar points are generated based on the AIS points, the associated relationship between them is determined, and therefore the associated results can be measured.
In the experiment, we first obtain AIS trajectories corresponding to these 175 radar trajectories, and then truncate these AIS trajectories according to different ratios, so as to test the associated results of the three methods under different AIS data volumes. When truncating AIS trajectories, we define the truncation ratio as
, where
is the range of the original AIS trajectory, and
is the AIS trajectory range after truncation. In the experiment, we set
to 100%, 80%, 60%, 40%, and 20%, respectively. In the experiment, F1 score is used to evaluate the three trajectory association algorithms, among them,
is the number of radar trajectories correctly associated,
is the number of radar trajectories with incorrect association, and
is the total number of radar trajectories minus
. The experimental results are shown in
Table 4.
According to
Table 4, the F1 scores of the method proposed in this paper are all greater than or equal to the F1 scores of the method based only on distance, which shows that with the help of D-TRAP, the accuracy of the association between trajectory points can be improved. When the amount of AIS data is reduced (
), the proposed method has better performance than traditional trajectory association method, which shows that the proposed method has stronger robustness for reduction of effective AIS data. When a ship has AIS closing behavior and MMSI spoofing behavior, the number of corresponding AIS points will decrease. Therefore, it is necessary to use the method proposed in the paper when determining the associated relationship between trajectories.
Based on real data and simulation data, this research simulates the AIS closing behavior and MMSI spoofing behavior of ships at different times, and tests these two algorithms. The test results show that the AIS closing detection algorithm has good performance when the ship does not close the AIS device prematurely; when the ship does not perform the MMSI spoofing behavior too early or too late, the MMSI spoofing detection algorithm has good performance. The test results are consistent with the actual situation. When the ship closes the AIS device prematurely, the amount of AIS data of the ship is small, which will result in the failure to form an AIS trajectory, or it is difficult to obtain the associated relationship between the AIS trajectory and the radar trajectory. At this time, only the radar trajectory can be observed, the ship to which the radar trajectory belongs cannot be determined, and the AIS closing behavior of the ship cannot be detected. When the ship performs MMSI spoofing behavior prematurely, the number of AIS points of the ship before the MMSI spoofing is small, which may also lead to the failure to form an AIS trajectory, or the associated relationship between the AIS trajectory before MMSI spoofing and the radar trajectory is difficult to obtain. At this time, only the AIS trajectory after the MMSI spoofing and the corresponding radar trajectory can be associated, and the MMSI spoofing behavior of the ship cannot be detected. Similarly, when the ship performs MMSI spoofing behavior too late, only the AIS trajectory before the MMSI spoofing and the corresponding radar trajectory can be associated, which will also cause the MMSI spoofing behavior of the ship to be undetectable. Therefore, in the following research, when looking for the associated AIS points of radar points, the accuracy of the association can be improved by comparing other attributes of trajectory points, such as speed in trajectory point, so that the application range of the AIS closing detection algorithm and the MMSI spoofing detection algorithm can be expanded.
The research in this paper can be applied to the ship data service system of the maritime authority. The maritime authority can establish radar, AIS receiver, and other data acquisition devices to obtain multisensor data of ships within its jurisdiction. At this stage, the multisensor data in most ship data service systems is often isolated, and the systems do not take full advantage of the multisensor data to achieve functions that cannot be achieved by using single-sensor data. This paper mainly uses the radar data and AIS data of ships to detect AIS closing behavior and MMSI spoofing behavior through D-TRAP and related algorithms, and these two types of illegal behaviors are difficult to detect through single-sensor data.