A Hybrid Privacy-Preserving Deep Learning Approach for Object Classification in Very High-Resolution Satellite Images
Abstract
:1. Introduction
- A novel hybrid PPDL approach combining Paillier homomorphic encryption and somewhat homomorphic encryption for satellite image classification is proposed. This combination will improve the security of encrypted images. Using only PHE, such as the work proposed in Alkhelaiwi et al. [19], can lead to some security issues [20]. Indeed, the capacity of the PHE schema used in [19] is constrained to addition or multiplication, but it cannot use the two operations simultaneously. As a result, this technique cannot secure data confidentiality when using it in the cloud [21]. However, integrating SHE with the encryption scheme will ensure more robustness to encrypted images while maintaining an excellent computational complexity and excellent runtime thanks to the shorter bit-length of SHE.
- To evaluate its efficiency, the proposed hybrid PPDL approach was applied to several DL-based CNN models, namely ResNet50, InceptionV3, DenseNet169, and MobileNetV2.
- Several experiments on real-world satellite image datasets were carried out to assess the overall performance of the proposed approach in terms of accuracy and security.
2. Background and Related Works
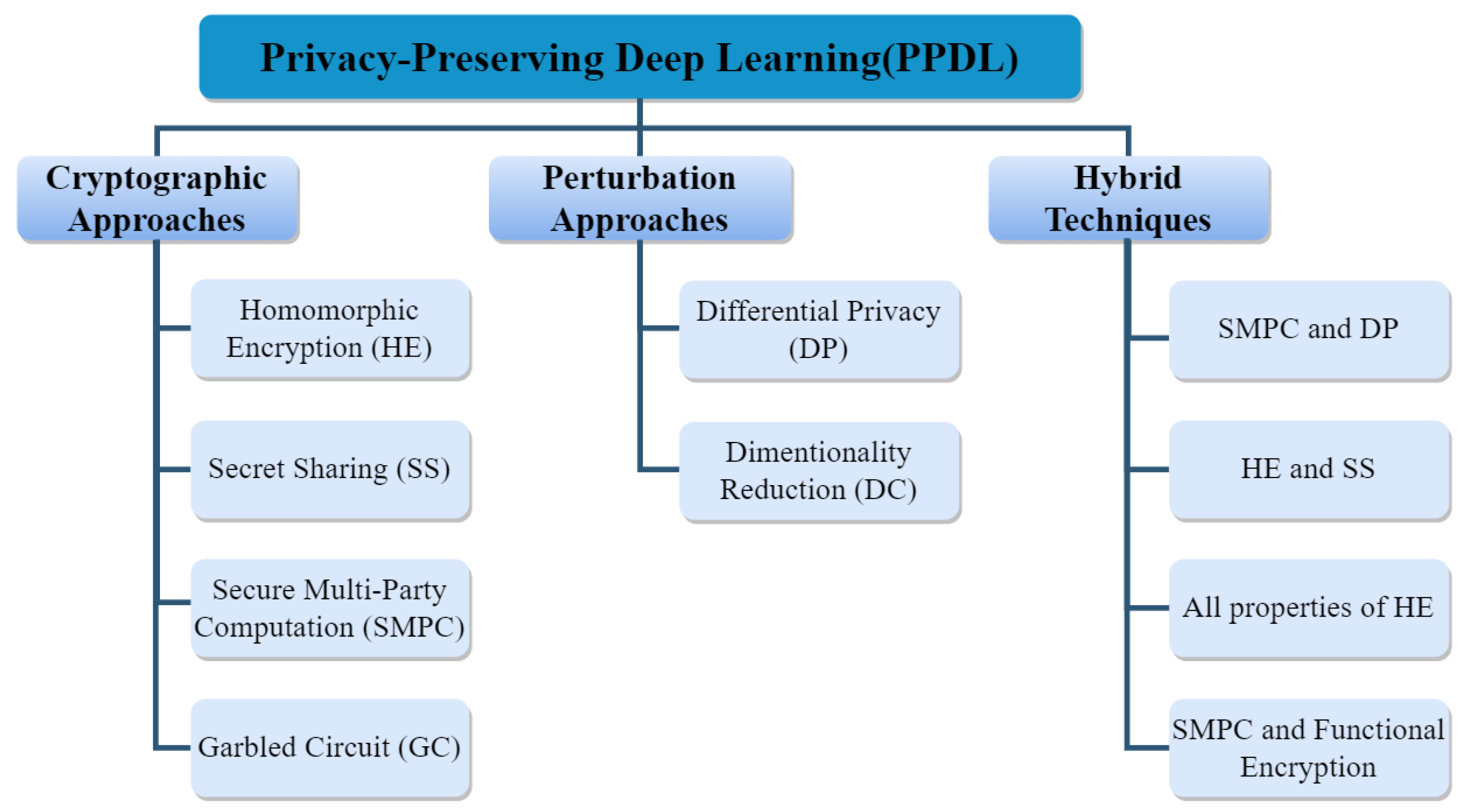
2.1. Privacy-Preserving Deep Learning
2.2. PPDL Methods
2.2.1. Comparison between PPDL Techniques
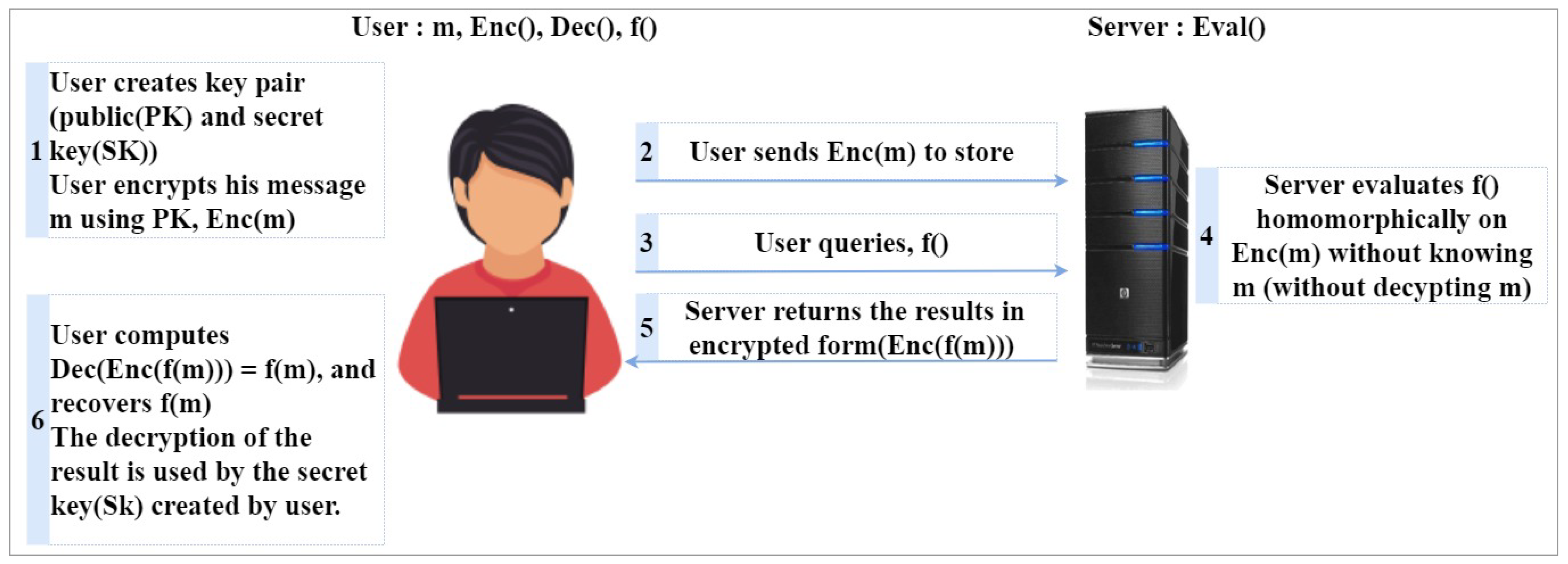
2.2.2. Homomorphic Encryption
- Key generation: The customer will produce the public parameter and the public and secret key (PK, SK).
- Encryption: The customer will generate the ciphertext (C) using M and PK, and C will be stored in the cloud.
- Evaluation: The server evaluates C, then the customer receives the encrypted result sent by the server.
- Decryption: The customer will obtain the original text (M) by decrypting the evaluation received from the server using SK.
- The encryption and storage of the user data are carried out within the cloud.
- The consumer sends information about the training task to the cloud server.
- The data encrypted by homomorphic encryption is fed to the model in the cloud server, which transfers back the encrypted result to the consumer. Through the secret key, the user can decrypt the result. Thus, the data’s safety and privacy are preserved.
2.3. Related Works
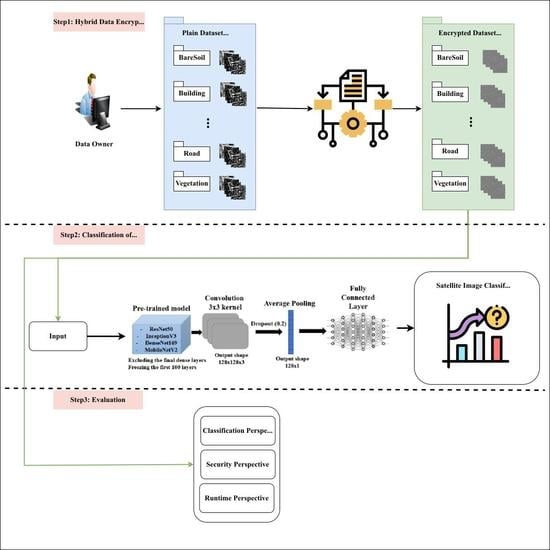
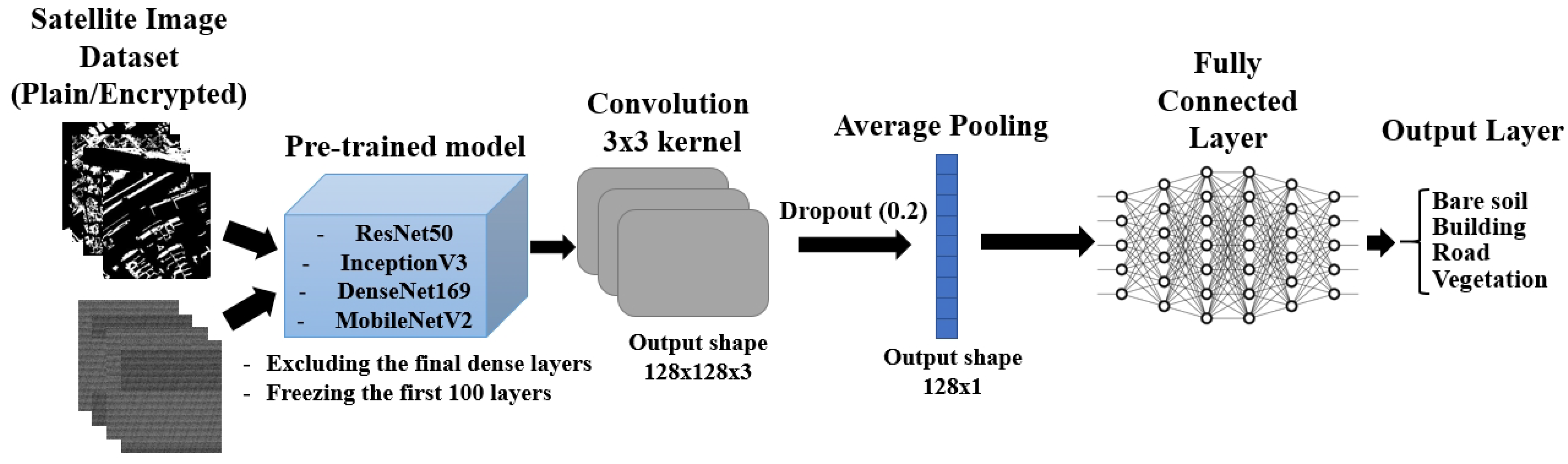
3. Materials and Methods
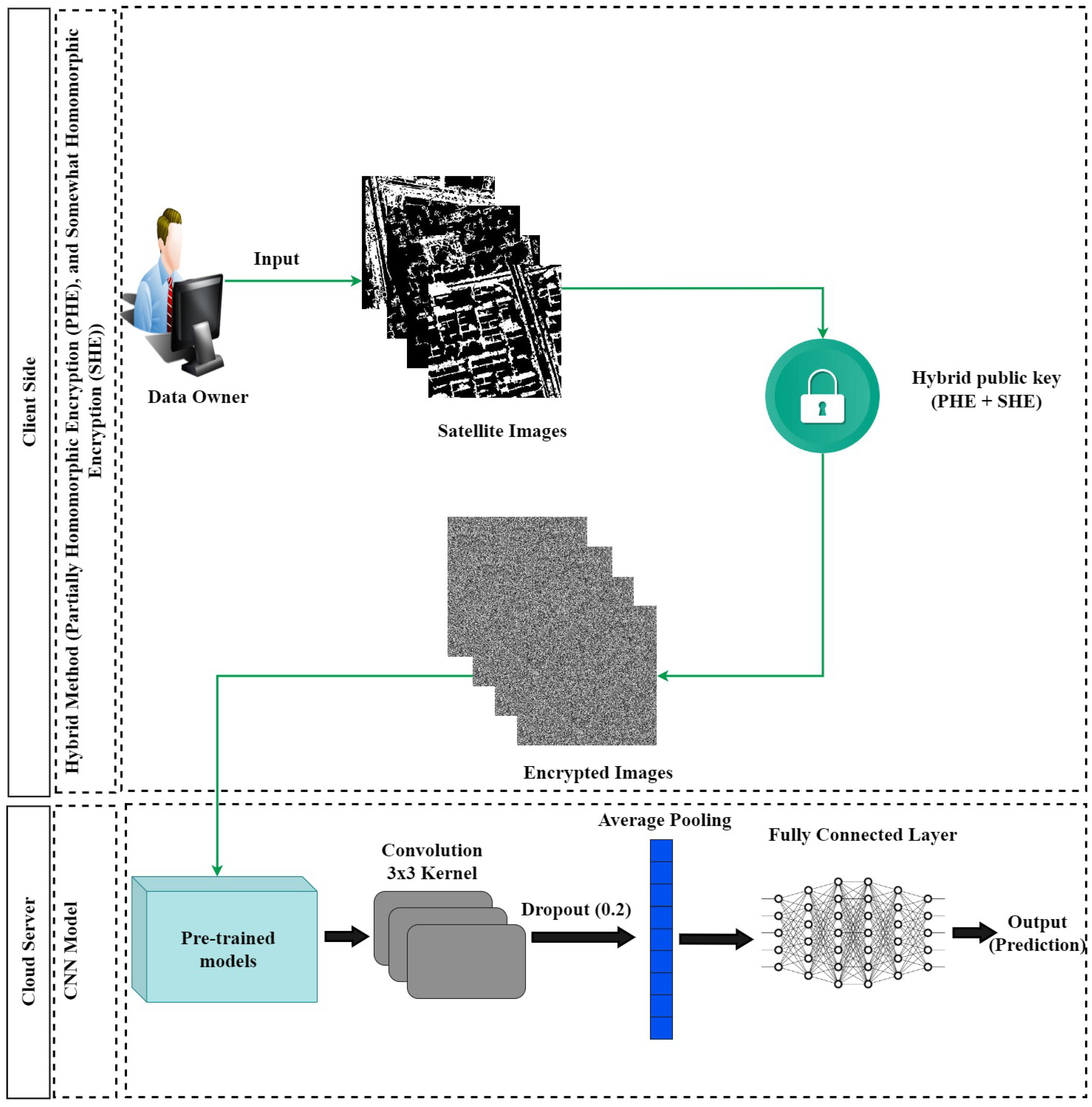
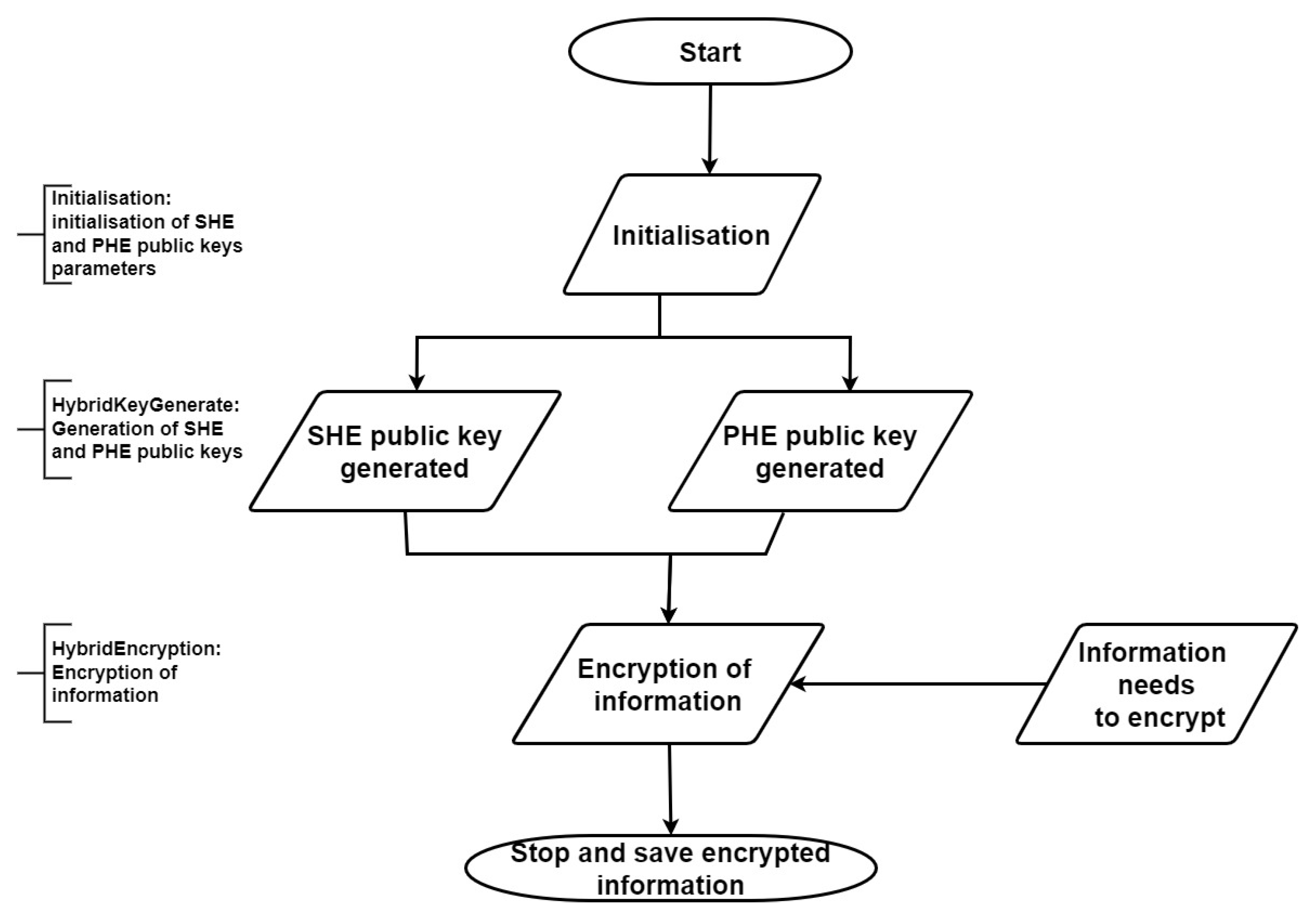
Hybrid Encryption Approach for Satellite Images Privacy
| Algorithm 1: Key generation (p, q). |
Input: Select two great prime numbers p, randomly and independently of each other Output: two different keys are: the encryption key that is the public key and the decryption key that is the secret key (,) 1: if length (p) = length(q) 1.1: Calculate and 1.2: Compute = where is the Euler totient function and 1.3: Let be mod n |
| Algorithm 2: Encryption (M, ). |
Input: M is a plaintext that is less than n, where M ∈ Output: c is a ciphertext where c ∈ 1: Take r ≺ n, where (r,n) equals 1 and r is a random value 2: c = mod |
| Algorithm 3: Decryption (c, ). |
Input: c is a ciphertext Output: M is a plaintext 1: M = mod ).( mod n), where c≺ |
| Algorithm 4: SH.keyGenerate (). |
Input: is the secret parameter Output: public key : and private key : : 1: Choose randomly the private key p that is an odd number, where and 2: Generate an array of integers, where , , , and 3: Choose randomly and , where and with 4: Define the function : 5: is the largest pk value and must be odd. Then, the remainder of must be even |
| Algorithm 5: SH.Encryption (M, ). |
Input: M is the message to encode Output: c is the encrypted message 1: Take a random subset 2: Generate a random integer 3: mod |
| Algorithm 6: SH.Decryption (c, ). |
Input: c is the encrypted message Output: M is the original message 1: Calculate (c mod ) mod 2 |
| Algorithm 7: HybridKeyGenerate (, p, q). |
Input: is the secret parameter, and p and q are two huge primes having the same length in binary representation. Output: two different public keys: One is generated by the PHE scheme, and the other is developed by the SHE scheme in Algorithms 1 and 4, respectively. 1: = keyGeneration (p,q) 2: = SH.keyGenerate () |
| Algorithm 8: HybridEncryption (, , M, ). |
Input: Let M be the plain message to encrypt Output: Let c be the encrypted message to decode, and 1: Take r less than n, where gcd(r,n) equals 1 and r is a random value ∈ 2: Generate a random subset 3: Compute : mod |
- A rotation range that equals 90 degrees.
- A zoom and a shear range equal to 20%.
- A brightness scale between [0.2,…, 1.0].
- A shift range that equals 20% in height and width.
- A horizontal flip and a vertical flip.
4. Experiments and Results
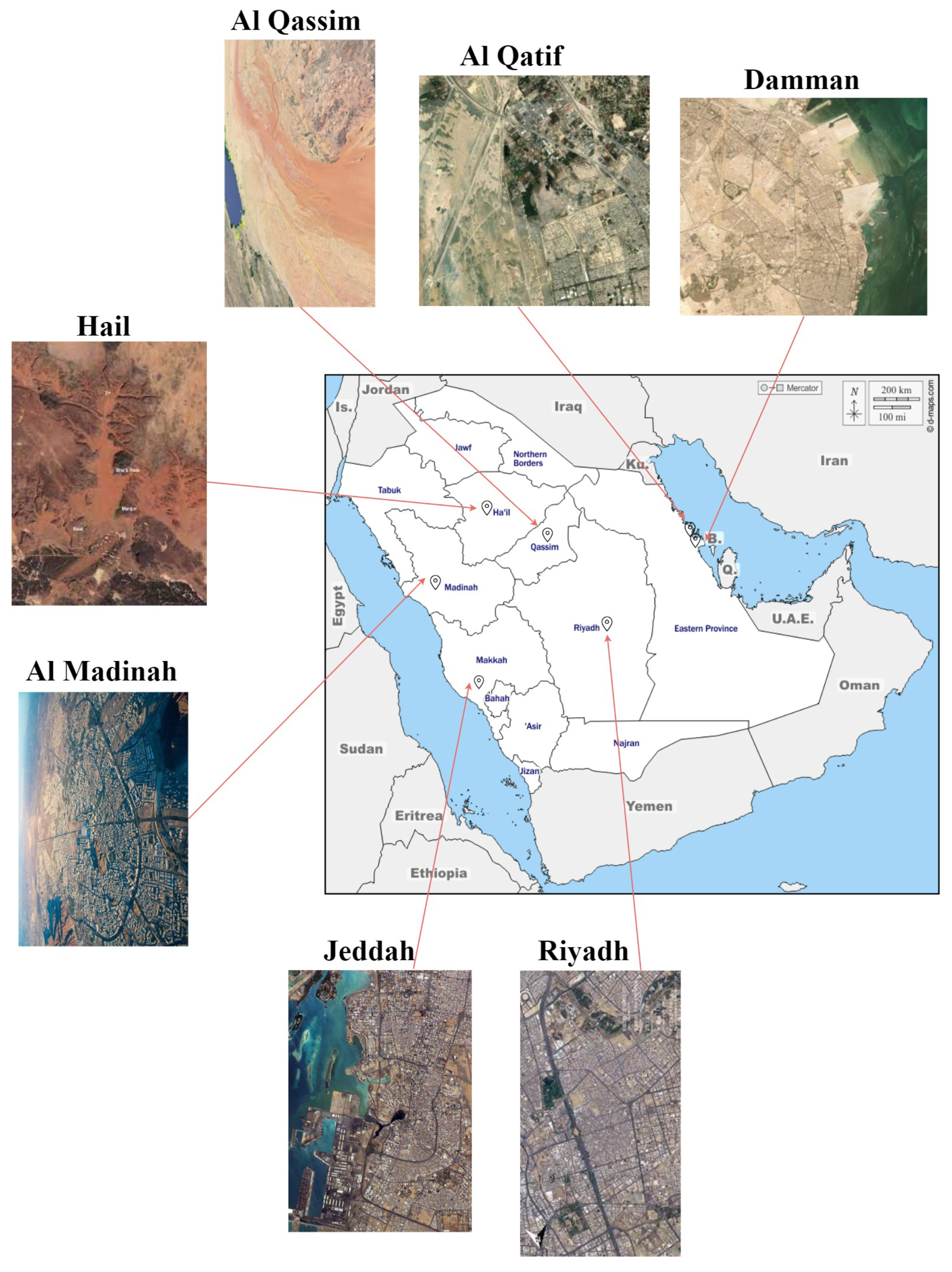
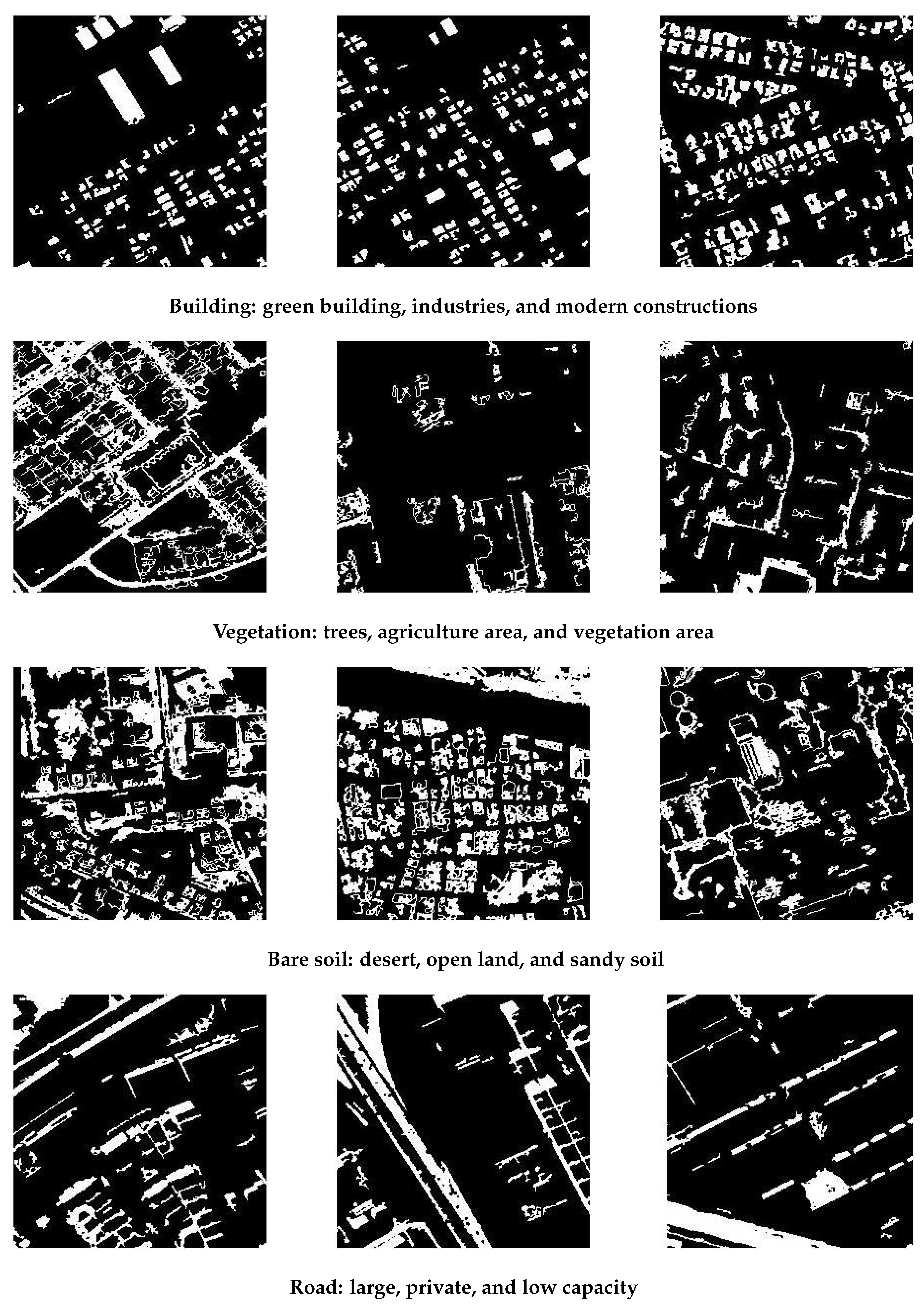
4.1. Study Regions and Dataset
4.2. Experimental Setup
4.3. Metrics
- True positives (TPs): the number of images correctly predicted as belonging to class C.
- True negatives (TNs): the number of images of other classes correctly predicted as not belonging to class C.
- False positives (FPs): the number of images wrongly predicted as belonging to class C.
- False negatives (FNs): the number of images of class C wrongly predicted as belonging to other classes.
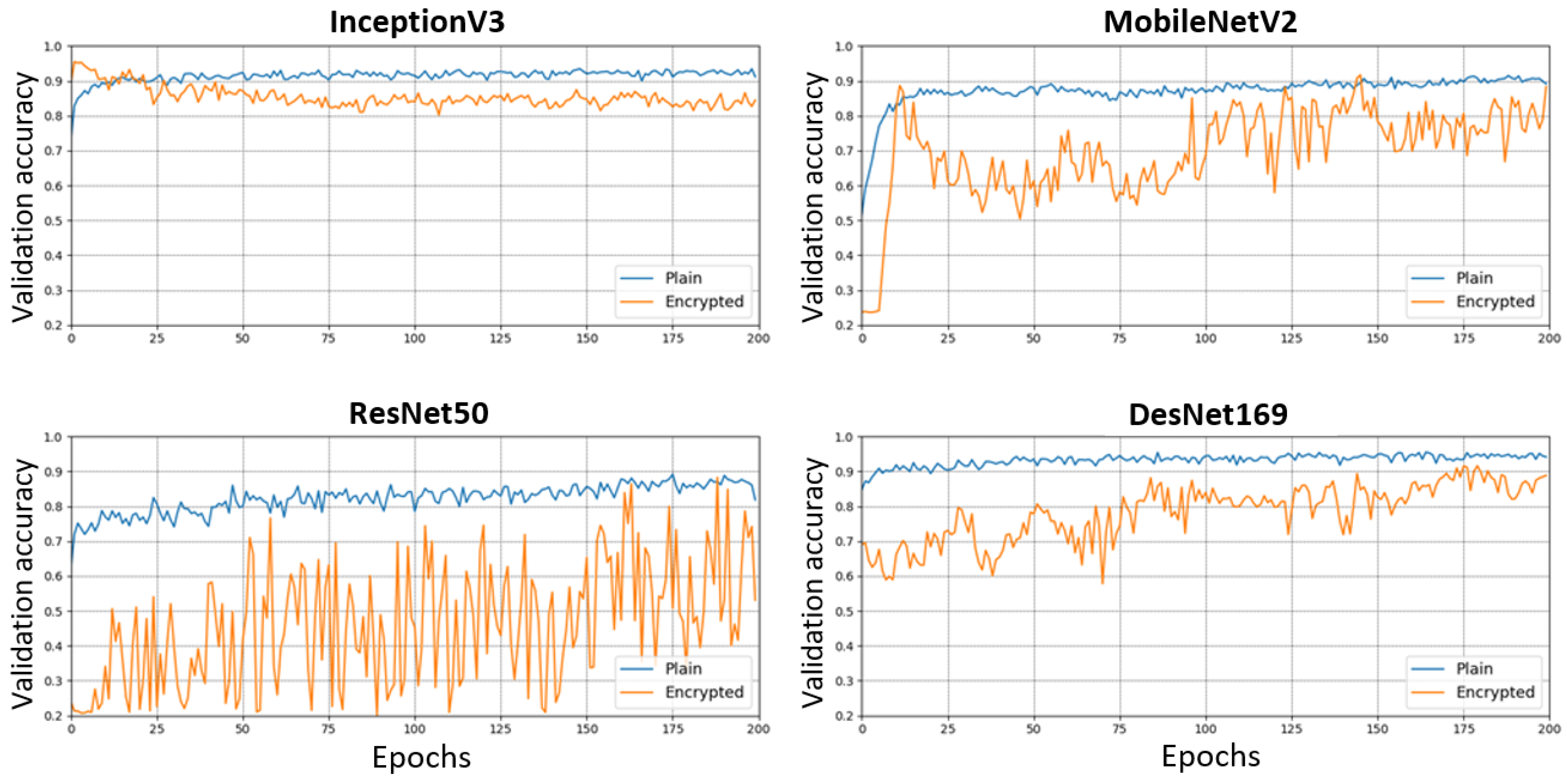
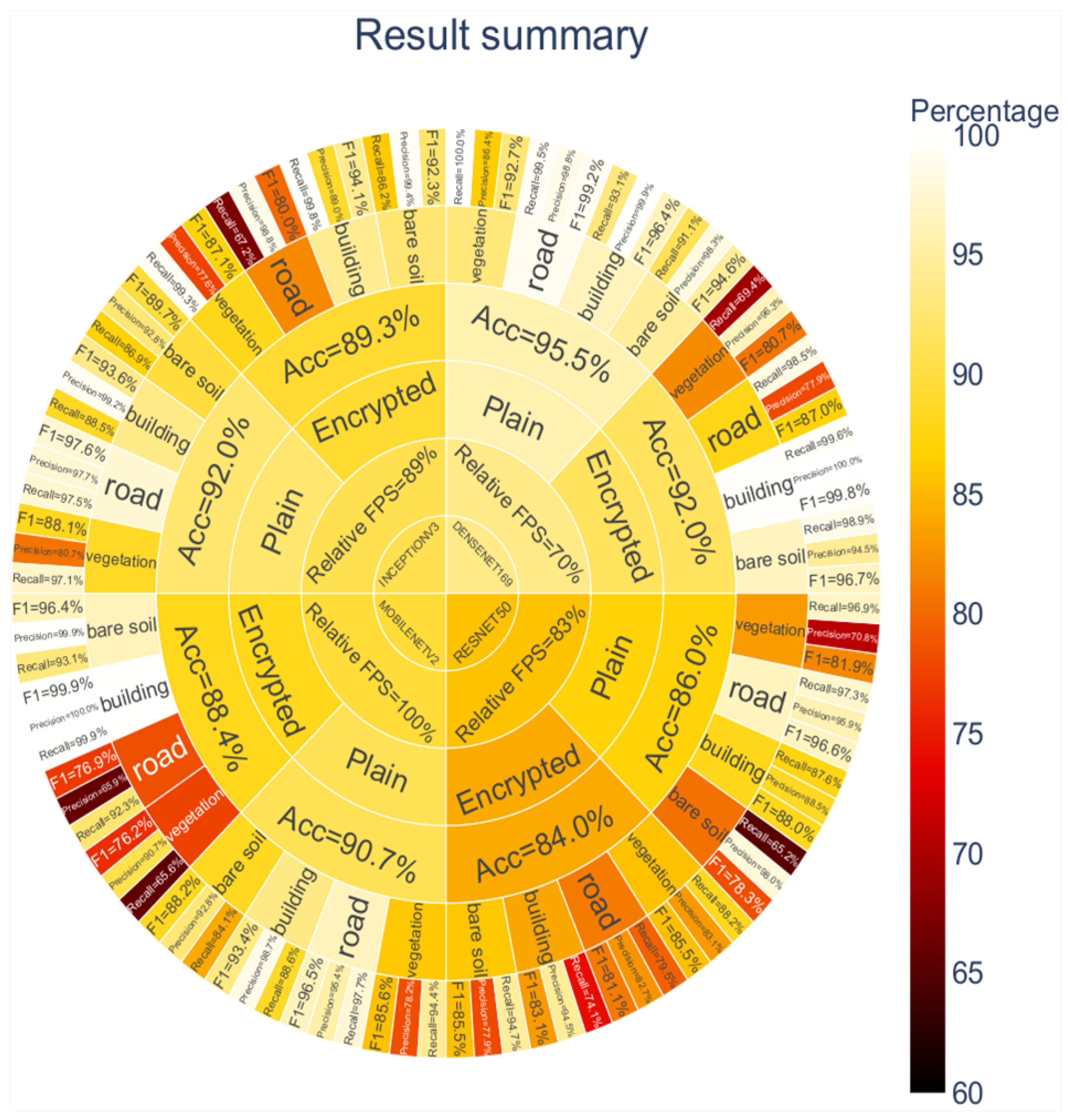
4.4. Results
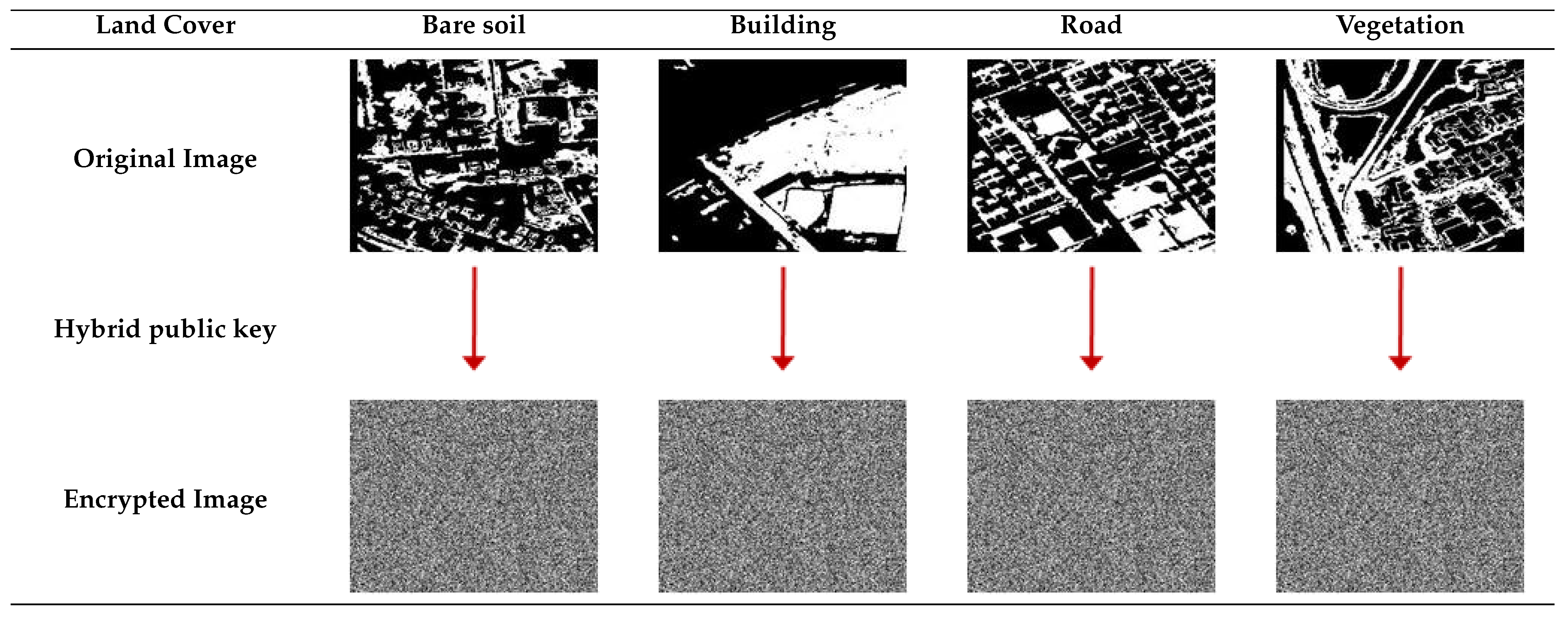
4.4.1. Image Encryption
4.4.2. Application of Transfer Learning Models
4.5. Evaluation
5. Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Ferchichi, A.; Boulila, W.; Farah, I.R. Propagating aleatory and epistemic uncertainty in land cover change prediction process. Ecol. Inform. 2017, 37, 24–37. [Google Scholar] [CrossRef]
- Bakaeva, N.; Le Minh, T. Determination of urban pollution islands by using remote sensing technology in Moscow, Russia. Ecol. Inform. 2022, 67, 101493. [Google Scholar] [CrossRef]
- Pan, X.; Jiang, J.; Xiao, Y. Identifying plants under natural gas micro-leakage stress using hyperspectral remote sensing. Ecol. Inform. 2022, 68, 101542. [Google Scholar] [CrossRef]
- Wadii, B.; Zouhayra, A.; Riadh, F.I. Sensitivity analysis approach to model epistemic and aleatory imperfection: Application to Land Cover Change prediction model. J. Comput. Sci. 2017, 23, 58–70. [Google Scholar]
- Mahdi, J. Intelligent algorithms and complex system for a smart parking for vaccine delivery center of COVID-19. Complex Intell. Syst. 2022, 8, 597–609. [Google Scholar]
- Xiao, Y.; Lim, S.; Tan, T.; Tay, S. Feature extraction using very high resolution satellite imagery. In Proceedings of the IGARSS 2004, 2004 IEEE International Geoscience and Remote Sensing Symposium, Anchorage, AK, USA, 20–24 September 2004; Volume 3. [Google Scholar]
- Dhingra, S.; Kumar, D. A review of remotely sensed satellite image classification. Int. J. Electr. Comput. Eng. 2004, 9, 1720. [Google Scholar] [CrossRef]
- Boulila, W.; Farah, I.R.; Ettabaa, K.S.; Solaiman, B.; Ghézala, H.B. Spatio-Temporal Modeling for Knowledge Discovery in Satellite Image Databases. In CORIA; ARIA: Narbonne, France, 2010; pp. 35–49. [Google Scholar]
- Chabot, D.; Stapleton, S.; Francis, C.M. Using Web images to train a deep neural network to detect sparsely distributed wildlife in large volumes of remotely sensed imagery: A case study of polar bears on sea ice. Ecol. Inform. 2022, 68, 101547. [Google Scholar] [CrossRef]
- Ståhl, N.; Weimann, L. Identifying wetland areas in historical maps using deep convolutional neural networks. Ecol. Inform. 2022, 68, 101557. [Google Scholar] [CrossRef]
- Yuan, Q.; Shen, H.; Li, T.; Li, Z.; Li, S.; Jiang, Y.; Xu, H.; Tan, W.; Yang, Q.; Wang, J.; et al. Deep learning in environmental remote sensing: Achievements and challenges. Remote Sens. Environ. 2020, 241, 111716. [Google Scholar] [CrossRef]
- Boulemtafes, A.; Derhab, A.; Challal, Y. A review of privacy-preserving techniques for deep learning. Neurocomputing 2020, 384, 21–45. [Google Scholar] [CrossRef]
- Tanuwidjaja, H.C.; Choi, R.; Kim, K. A survey on deep learning techniques for privacy-preserving. In International Conference on Machine Learning for Cyber Security; Springer: Cham, Switzerland, 2019; pp. 29–46. [Google Scholar]
- Boulila, W.; Farah, I.R.; Ettabaa, K.S.; Solaiman, B.; Ghézala, H.B. Improving spatiotemporal change detection: A high level fusion approach for discovering uncertain knowledge from satellite image databases. In ICDM; World Academy of Science, Engineering and Technology: Paris, France, 2009; Volueme 9, pp. 222–227. [Google Scholar]
- Mahdi, J.; Hani, A. Equity data distribution algorithms on identical routers. In International Conference on Machine Learning for Cyber Security; Springer: Cham, Switzerland, 2020; pp. 297–305. [Google Scholar]
- Tanuwidjaja, H.C.; Choi, R.; Baek, S.; Kim, K. Privacy-preserving deep learning on machine learning as a service—a comprehensive survey. IEEE Access 2020, 8, 167425–167447. [Google Scholar] [CrossRef]
- Domingo-F, J.; Farras, O.; Ribes-González, J.; Sánchez, D. Privacy-preserving cloud computing on sensitive data: A survey of methods, products and challenges. Comput. Commun. 2019, 140, 38–60. [Google Scholar] [CrossRef]
- Shrestha, R.; Kim, S. Integration of IoT with blockchain and homomorphic encryption: Challenging issues and opportunities. Adv. Comput. 2019, 115, 293–331. [Google Scholar]
- Alkhelaiwi, M.; Boulila, W.; Ahmad, J.; Koubaa, A.; Driss, M. An efficient approach based on privacy-preserving deep learning for satellite image classification. Remote Sens. 2021, 13, 2221. [Google Scholar] [CrossRef]
- Morris, L. Analysis of partially and fully homomorphic encryption. Rochester Inst. Technol. 2013, 1–5. Available online: https://www.semanticscholar.org/paper/Analysis-of-Partially-and-Fully-Homomorphic-Morris/03036b989a3f838a9e130563357492fcc4d76402 (accessed on 12 September 2022).
- Oladunni, T.; Sharma, S. Homomorphic Encryption and Data Security in the Cloud. In Proceedings of 28th International Conference, Washington, DC, USA, 16–17 February 2019; Volume 64, pp. 129–138. [Google Scholar]
- Al-Rubaie, M.; Chang, J.M. Privacy-preserving machine learning: Threats and solutions. IEEE Secur. Priv. 2019, 17, 49–58. [Google Scholar] [CrossRef]
- Dhanalakshmi, M.; Sankari, E.S. Privacy preserving data mining techniques-survey. In Proceedings of the International Conference on Information Communication and Embedded Systems, (ICICES2014), Chennai, India, 27–28 February 2014; pp. 1–6. [Google Scholar]
- Zapechnikov, S. Privacy-preserving machine learning as a tool for secure personalized information services. Procedia Comput. Sci. 2020, 169, 393–399. [Google Scholar] [CrossRef]
- Lopardo, A.; Farrand, T. What is Homomorphic Ecryption? Available online: https://blog.openmined.org/what-is-homomorphic-encryption/ (accessed on 28 February 2021).
- Harold, B. The Advantages and Disadvantages of Homomorphic Encryption. 2019. Available online: https://blog.openmined.org/what-is-homomorphic-encryption/https://baffle.io/blog/the-advantages-and-disadvantages-of-homomorphic-encryption/ (accessed on 28 February 2021).
- Medhi, B. Privacy-Preserving Computation Techniques & FHE from Ziros Labs. 2019. Available online: https://medium.com/@bhaskarmedhi/privacy-preserving-computation-techniques-fhe-from-ziroh-labs-8814e88044a (accessed on 28 February 2021).
- Lapardo, A.; Benaissa, A. What is Secure Multi-party Computation? 2020. Available online: https://medium.com/pytorch/what-is-secure-multi-party-computation-8c875fb36ca5 (accessed on 3 March 2021).
- Singh, P. Dimensionality Reduction Approches. 2020. Available online: https://towardsdatascience.com/dimensionality-reduction-approaches-8547c4c44334 (accessed on 3 March 2021).
- What is Dimensionality Reduction—Techniques, Methods, Components. Available online: https://data-flair.training/blogs/dimensionality-reduction-tutorial/ (accessed on 3 March 2021).
- Kasar, N. Image secret sharing using Shamir’s Algorithm. 2016. Available online: https://fr.slideshare.net/NikitaKasar/image-secret-sharing-using-shamirs-algorithm-59670385 (accessed on 15 March 2021).
- Wood, A.; Najarian, K.; Kahrobaei, D. Homomorphic encryption for machine learning in medicine and bioinformatics. ACM Comput. Surv. CSUR 2020, 53, 1–35. [Google Scholar] [CrossRef]
- Parmar, P.V.; Padhar, S.B.; Patel, S.N.; Bhatt, N.I.; Jhaveri, R.H. Survey of various homomorphic encryption algorithms and schemes. Int. J. Comput. Appl. 2014, 91, 26–32. [Google Scholar]
- Kaaniche, N.; Laurent, M.; Belguith, S. Privacy enhancing technologies for solving the privacy-personalization paradox: Taxonomy and survey. J. Netw. Comput. Appl. 2020, 171, 102807. [Google Scholar] [CrossRef]
- Truex, S.; Baracaldo, N.; Anwar, A.; Steinke, T.; Ludwig, H.; Zhang, R.; Zhou, Y. A hybrid approach to privacy-preserving federated learning. In Proceedings of the 12th ACM Workshop on Artificial Intelligence and Security, London, UK, 15 November 2019; pp. 1–11. [Google Scholar]
- Chase, M.; Gilad-Bachrach, R.; Laine, K.; Lauter, K.; Rindal, P. Private collaborative neural network learning. Cryptol. ePrint Arch. 2017; preprint. Available online: https://eprint.iacr.org/2017/762(accessed on 12 September 2022).
- Chen, C.; Zhou, J.; Wang, L.; Wu, X.; Fang, W.; Tan, J.; Wang, L.; Liu, A.X.; Wang, H.; Hong, C. When homomorphic encryption marries secret sharing: Secure large-scale sparse logistic regression and applications in risk control. In Proceedings of the 27th ACM SIGKDD Conference on Knowledge Discovery & Data Mining, Singapore, 14–18 August 2021; pp. 2652–2662. [Google Scholar]
- El Makkaoui, K.; Beni-Hssane, A.; Ezzati, A. A Can hybrid Homomorphic Encryption schemes be practical? In Proceedings of the 2016 5th International Conference on Multimedia Computing and Systems (ICMCS), Marrakech, Morocco, 29 September–1 October 2016; pp. 294–298. [Google Scholar]
- Xu, R.; Baracaldo, N.; Zhou, Y.; Anwar, A.; Ludwig, H. Hybridalpha: An efficient approach for privacy-preserving federated learning. In Proceedings of the 12th ACM Workshop on Artificial Intelligence and Security, London, UK, 15 November 2019; pp. 13–23. [Google Scholar]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A survey on homomorphic encryption schemes: Theory and implementation. ACM Comput. Surv. CSUR 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Mattsson, U. Security and Performance of Homomorphic Encryption. 2021. Available online: https://www.globalsecuritymag.com/Security-and-Performance-of,20210601,112333.html (accessed on 26 August 2021).
- Xiong, L.; Dong, D.; Xia, Z.; Chen, X. High-capacity reversible data hiding for encrypted multimedia data with somewhat homomorphic encryption. IEEE Access 2018, 6, 60635–60644. [Google Scholar] [CrossRef]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. [Google Scholar]
- Muhammad, K.; Sugeng, K.A.; Murfi, H. Machine Learning with Partially Homomorphic Encrypted Data. J. Phys. Conf. Ser. 2018, 1, 012112. [Google Scholar] [CrossRef]
- Kulynych, B. Symmetric Somewhat Homomorphic Encryption over the Integers. Proc. Ukr. Sci. Conf. Young Sci. Math. Phys. 2015, 1–12. Available online: https://www.semanticscholar.org/paper/Symmetric-Somewhat-Homomorphic-Encryption-over-the-Kulynych/9e212b22769d4dbfac09f47542871194f69fafc6 (accessed on 12 September 2022).
- Hariss, K.; Chamoun, M.; Samhat, A.E. On DGHV and BGV fully homomorphic encryption schemes. In Proceedings of the 2017 1st Cyber Security in Networking Conference (CT), Virtual, 18–20 October 2017; pp. 1–9. [Google Scholar]
- Pisa, P.S.; Abdalla, M.; Duarte, O.C.M.B. Somewhat homomorphic encryption scheme for arithmetic operations on large integers. In Proceedings of the 2012 Global Information Infrastructure and Networking Symposium (GIIS), Choroni, Venezuela, 17–19 December 2012; pp. 1–8. [Google Scholar]
- Van Dijk, M.; Gentry, C.; Halevi, S.; Vaikuntanathan, V. Fully homomorphic encryption over the integers. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2010; pp. 24–43. [Google Scholar]
- Coron, J.; Naccache, D.; Tibouchi, M. Public key compression and modulus switching for fully homomorphic encryption over the integers. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2012; pp. 446–464. [Google Scholar]
- Yi, X.; Paulet, R.; Bertino, E. Homomorphic encryption. In Homomorphic Encryption and Applications; Springer: Cham, Switzerland, 2014; pp. 27–46. [Google Scholar]
- Shorten, C.; Khoshgoftaar, T.M. A survey on image data augmentation for deep learning. J. Big Data 2019, 6, 1–48. [Google Scholar] [CrossRef]
- Hernández-García, A.; König, P. Data augmentation instead of explicit regularization. arXiv 2018, arXiv:1806.03852. [Google Scholar]
- Kassani, S.H.; Kassani, P.H. A comparative study of deep learning architectures on melanoma detection. Tissue Cell 2019, 58, 76–83. [Google Scholar] [CrossRef]
- Ghandorh, H.; Boulila, W.; Masood, S.; Koubaa, A.; Ahmed, F.; Ahmad, J. Semantic Segmentation and Edge Detection—Approach to Road Detection in Very High Resolution Satellite Images. Remote Sens. 2022, 14, 613. [Google Scholar] [CrossRef]
- Huang, G.; Liu, Z.; Van Der Maaten, L.; Weinberger, K.Q. Densely connected convolutional networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Honolulu, HI, USA, 21–26 July 2017; pp. 4700–4708. [Google Scholar]
- Sandler, M.; Howard, A.; Zhu, M.; Zhmoginov, A.; Chen, L. Mobilenetv2: Inverted residuals and linear bottlenecks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Salt Lake City, UT, USA, 18–23 June 2018; pp. 4510–4520. [Google Scholar]
- Szegedy, C.; Vanhoucke, V.; Ioffe, S.; Shlens, J.; Wojna, Z. Rethinking the inception architecture for computer vision. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 2818–2826. [Google Scholar]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Deng, J.; Dong, W.; Socher, R.; Li, L.; Li, K.; Li, F. Imagenet: A large-scale hierarchical image database. In Proceedings of the 2009 IEEE Conference on Computer Vision and Pattern Recognition, Miami, FL, USA, 20–25 June 2009; pp. 248–255. [Google Scholar]
- Ganti, A. Imagenet: Correlation coefficient. Corp. Financ. Acc. 2020, 9, 145–152. [Google Scholar]
- Lu, Q.; Yu, L.; Zhu, C. Symmetric Image Encryption Algorithm Based on a New Product Trigonometric Chaotic Map. Symmetry 2022, 14, 373. [Google Scholar] [CrossRef]
- Huang, X.; Dong, Y.; Zhu, H.; Ye, G. Visually asymmetric image encryption algorithm based on SHA-3 and compressive sensing by embedding encrypted image. Alex. Eng. J. 2022, 61, 7637–7647. [Google Scholar] [CrossRef]
- Anees, A.; Siddiqui, A.M.; Ahmed, F. Chaotic substitution for highly autocorrelated data in encryption algorithm. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 3106–3118. [Google Scholar] [CrossRef]
- Dosselmann, R.; Yang, X.D. A comprehensive assessment of the structural similarity index. Signal Image Video Process. 2011, 5, 81–91. [Google Scholar] [CrossRef]
- Alquhayz, H.; Jemmali, M. Fixed Urgent Window Pass for a Wireless Network with User Preferences. Wirel. Pers. Commun. 2021, 120, 1565–1591. [Google Scholar] [CrossRef]

| Methodologies | Advantages | Drawbacks | References |
|---|---|---|---|
| Homomorphic encryption (HE) |
|
| [25,26,27] |
| Secure multi-party computation (SMPC) |
|
| [27,28] |
| Differential privacy (DP) |
| When datasets are bulky, noise and loss of information may occur. | [27] |
| Dimensionality reduction (DR) |
|
| [29,30] |
| Secret sharing (SS) |
| Computationally complex. | [22,31] |
| REF | [35] | [39] | [37] | [38] | [36] | [19] | The Proposed Research | |
|---|---|---|---|---|---|---|---|---|
| Domain of application | Nursery application Classification of handwritten digits | Classification of handwritten digits | Risk control | Attack distinguishing | Classification of handwritten digits | Satellite image classification | Satellite image classification | |
| PPDL methods | HE | √ | √ | √ | √ | √ | ||
| SS | √ | |||||||
| SMPC | √ | √ | √ | |||||
| GC | ||||||||
| DP | √ | √ | ||||||
| DR | ||||||||
| ML models | Decision Trees (DT) Convolutional neural networks (CNNs) Linear support vector machines (SVMs) | CNN | Logistic regression | Small NN (3-layer) NN (4-layer) | CNN | CNN | ||
| Dataset | Nursery dataset MNIST dataset Gisette dataset | MNIST dataset | Real-world dataset | - | MNIST dataset | Satellite dataset | Satellite dataset | |
| Goal | Combining SMPC with differential privacy to decrease the expansion of noise injection as the number of clients increases. | Use of an SMPC protocol based on a functional multi-entry encryption system. | Development of a hybrid encryption approach based on HE and SS to construct a secure large-scale sparse logistic regression model that fulfills the requirements of both effectiveness and safeness. | A hybrid HE system was created based on two different systems that back up the additive and multiplicative properties. | Development of a collaborative protocol based on an NN and the gradient descent method to add random noise to guarantee that the information will not be divulged. | Training DL models based on encrypted data with PHE to preserve the confidentiality of information. | Encryption of data using a hybrid method to enhance data encryption while ensuring good runtime and classification accuracy. |
| Land Cover Type | No. of Training Samples | No. of Validation Samples |
|---|---|---|
| BareSoil | 6784 | 754 |
| Building | 7541 | 838 |
| Road | 5411 | 601 |
| Vegetation | 6162 | 685 |
| Weighted Average on the 4 Classes | No. of Param. | No. of Operations (FLOPS) | Inference Time per Image (ms) | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| CNN Models | Precision | Recall | F1-Score | |||||||||
| Plain | Enc | Loss | Plain | Enc | Loss | Plain | Enc | Loss | ||||
| ResNet50 | 88.3% | 84.5% | 3.8% | 86.0% | 84.0% | 2.0% | 85.8% | 83.9% | 1.9% | 25.9 M | 51.8 M | 1.9 |
| InceptionV3 | 92.8% | 91.1% | 1.7% | 92.0% | 89.3% | 2.7% | 92.1% | 89.0% | 3.1% | 24.1 M | 48.3 M | 1.8 |
| DenseNet169 | 96.0% | 93.1% | 2.9% | 95.5% | 92.0% | 3.5% | 95.6% | 91.8% | 3.8% | 14.6 M | 29.1 M | 2.3 |
| MobileNetV2 | 94.1% | 90.6% | 3.5% | 93.6% | 88.4% | 5.2% | 93.7% | 88.5% | 5.2% | 3.7 M | 7.4 M | 1.6 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boulila, W.; Khlifi, M.K.; Ammar, A.; Koubaa, A.; Benjdira, B.; Farah, I.R. A Hybrid Privacy-Preserving Deep Learning Approach for Object Classification in Very High-Resolution Satellite Images. Remote Sens. 2022, 14, 4631. https://doi.org/10.3390/rs14184631
Boulila W, Khlifi MK, Ammar A, Koubaa A, Benjdira B, Farah IR. A Hybrid Privacy-Preserving Deep Learning Approach for Object Classification in Very High-Resolution Satellite Images. Remote Sensing. 2022; 14(18):4631. https://doi.org/10.3390/rs14184631
Chicago/Turabian StyleBoulila, Wadii, Manel Khazri Khlifi, Adel Ammar, Anis Koubaa, Bilel Benjdira, and Imed Riadh Farah. 2022. "A Hybrid Privacy-Preserving Deep Learning Approach for Object Classification in Very High-Resolution Satellite Images" Remote Sensing 14, no. 18: 4631. https://doi.org/10.3390/rs14184631
APA StyleBoulila, W., Khlifi, M. K., Ammar, A., Koubaa, A., Benjdira, B., & Farah, I. R. (2022). A Hybrid Privacy-Preserving Deep Learning Approach for Object Classification in Very High-Resolution Satellite Images. Remote Sensing, 14(18), 4631. https://doi.org/10.3390/rs14184631