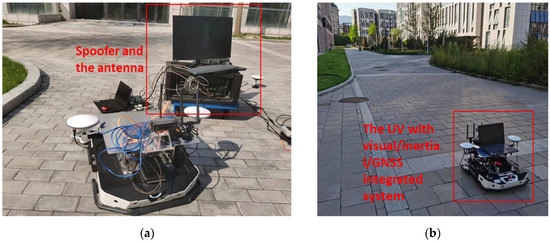
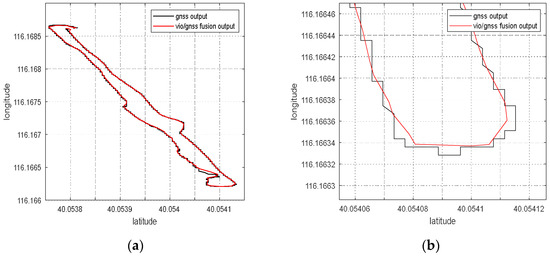
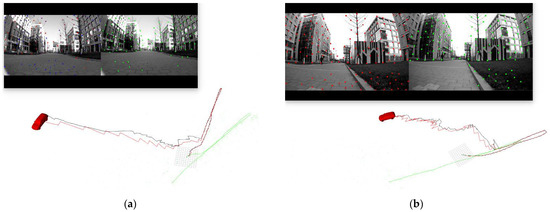
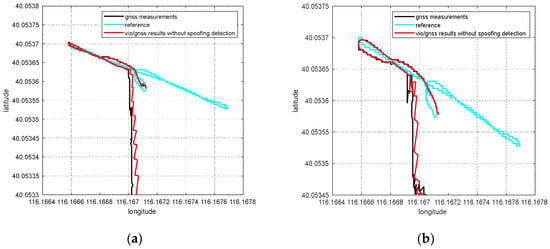
Abstract
Visual/Inertial/GNSS (VIG) integrated navigation and positioning systems are widely used in unmanned vehicles and other systems. This VIG system is vulnerable to of GNSS spoofing attacks. Relevant research on the harm that spoofing causes to the system and performance analyses of VIG systems under GNSS spoofing are not sufficient. In this paper, an open-source VIG algorithm, VINS-Fusion, based on nonlinear optimization, is used to analyze the performance of the VIG system under a GNSS spoofing attack. The influence of the visual inertial odometer (VIO) scale estimation error and the transformation matrix deviation in the transition period of spoofing detection is analyzed. Deviation correction methods based on the GNSS-assisted scale compensation coefficient estimation method and optimal pose transformation matrix selection are proposed for VIG-integrated system in spoofing areas. For an area that the integrated system can revisit many times, a global pose map-matching method is proposed. An outfield experiment with a GNSS spoofing attack is carried out in this paper. The experiment result shows that, even if the GNSS measurements are seriously affected by the spoofing, the integrated system still can run independently, following the preset waypoint. The scale compensation coefficient estimation method, the optimal pose transformation matrix selection method and the global pose map-matching method can depress the estimation error under the circumstances of a spoofing attack.
1. Introduction
Positioning and navigation are basic problems in the autonomous operation of unmanned ground vehicles (UGVs), unmanned aerial vehicles (UAVs) and other intelligent systems. Positioning and navigation technology is an ancient and modern technology. With the development of sensor technology, a variety of navigation sensors with different physical principles have been utilized. One of the most important reasons that there are so many kinds of navigation sensors is that each kind of navigation sensor has particular technical advantages and disadvantages, so it is often necessary to combine different kinds of sensors to achieve complementary advantages. With the gradual maturity of each kind of navigation sensor technology and the reduction in costs, intelligent systems such as UVs and UAVs are often equipped with various navigation sensors to form integrated navigation and positioning systems. The most commonly used positioning and navigation technologies mainly include the Global Navigation Satellite System (GNSS), Inertial Navigation System (INS) [1], etc. With the development of computer vision, visual Simultaneous Localization Additionally, Mapping (SLAM) technology has gradually become an important positioning and navigation technology for intelligent systems [2].
GNSS is still the most important absolute positioning technology. The main advantage of GNSS systems is that they provide all-weather, high-precision, high-stability positioning results in outdoor environments in most parts of the world and most situations [3]. GNSS has stable long-term positioning accuracy, high technology maturity, low-volume power consumption and an extremely low cost for the navigation receiver of the client, and has a wide range of applications. However, most GNSS receivers are vulnerable to spoofing attacks [4]. The deviation errors of the localization results caused by spoofing will lead the system to a pre-set wrong location [5]. The positioning signal of the GNSS system is easy to imitate, so its security is worth attention. Shepard et al. [6] successfully demonstrated the spoofing of drones. Noh et al. [7] proposed a method of hijacking drones using GPS spoofing. GNSS spoofing could also influence the integrated positioning system of GNSS combined with other sensors, such as INS [8]. As the influence of GNSS spoofing on VIG systems has not been discussed in depth, this paper focuses on the performance of VIG-integrated systems under GNSS spoofing.
Inertial sensor is another important kind of sensors in the VIG system. Inertial measurement does not depend on external information, nor does it radiate energy to the outside [9]. It has high security, high short-term accuracy, and a high data update rate, and can be applied to some special environments, such as underground and underwater. The disadvantage of INS is that, because the navigation information is generated through integration, it can only provide relative positioning information, not absolute information. Moreover, the integration process will inevitably lead to the accumulation of positioning errors over time, resulting in poor long-term accuracy and high costs for high-precision inertial sensors. Visual SLAM also has the problem of accumulating positioning errors, but it does not have the problem of zero bias, and the errors are mostly accumulated due to motion. Therefore, the long-term accuracy of integrated systems can be significantly improved by combining an inertial sensor with a SLAM sensor. The combined use of visual/inertial odometry (VIO) can achieve the accuracy level of high-cost inertial sensors at a low cost [10].
The VIG system can combine the advantages of the three kinds of sensors, and these can complement each other to achieve absolute positioning with high accuracy, a high update rate and no cumulative error. Studies that combine visual SLAM technology with inertial and GNSS technology include VINS-Fusion [11] and GVINS [12]. Although many kinds of integrated algorithms have been discussed, the performance of these algorithms in some critical circumstances, such as GNSS spoofing, need further research. Spoofing has gradually become a research hotspot for satellite navigation interference technology [13].
GNSS spoofing signals are designed to mislead GNSS receivers [14]. References [15,16] utilized INS information to monitor GPS spoofing for aircraft. Reference [17] used tightly coupled INS/GNSS algorithms to counter GNSS spoofing. Reference [18] used the information of GNSS/IMU/odometry systems to detect GNSS spoofing. These pieces of research did not involve visual measurements and were not designed for nonlinear VIG systems. Reference [19] proposed a GPS spoofing detection method based on cameras, but this was also not designed for nonlinear VIG systems and did not discuss the positioning performance after GNSS spoofing identification.
In the previous study [20], the problem of the VINS-Fusion algorithm being induced by spoofing signals is discussed for the first time, and the vulnerability of the VIG-integrated algorithm without a specific anti-spoofing design is proven. Reference [21] also studied the characteristics of a visual SLAM/GNSS system under spoofing attack and proposed a Time-Localization Verification and Smoothing Localization Method (PTC-SLM) method to identify the spoofing and smooth the positioning solution. The PTC-SLM method analyzed the joint error offset from the GNSS from the dimensions of time and localization using visual SLAM estimations to identify GNSS spoofing, and selected the corresponding back-end optimization strategy to obtain a smoothing localization result. Dataset experiments were carried out with the KITTI dataset [22] in that study. Compared with the study in [21], the previous study [20] not only carried out KITTI dataset experiments, but also carried out a spoofing detection experiment in a real spoofing environment. Compared with the study in this paper, Reference [21] did not evaluate the SLAM/GNSS system in a real spoofing environment after GNSS spoofing detection.
Some methods related to this study have been discussed. Reference [23] discussed the robust initialization and online scale estimation of the visual/inertial odometry, but did not have GNSS measurements to correct the scale. Reference [24] proposed a method that used a map with weak GPS priors to correct the localization results of a repetitive UAV flight. Reference [25] treated the localization problem as a rigid base-frame alignment problem between a local map and a reference map. However, none of this research referred to the influence of spoofing.
The main purpose of study [20] is to verify the effectiveness of a GNSS spoofing detection algorithm assisted by visual/inertial information. The research on the characteristics and problems of VIG-integrated systems under spoofing is not sufficient. Experiment with VIG-integrated system in the spoofing environment are also not sufficient. The study in this paper will use the GNSS spoofing detection method proposed in a previous study [20], and discuss the performance and key problems of the VIG system based on the identification of GNSS spoofing.
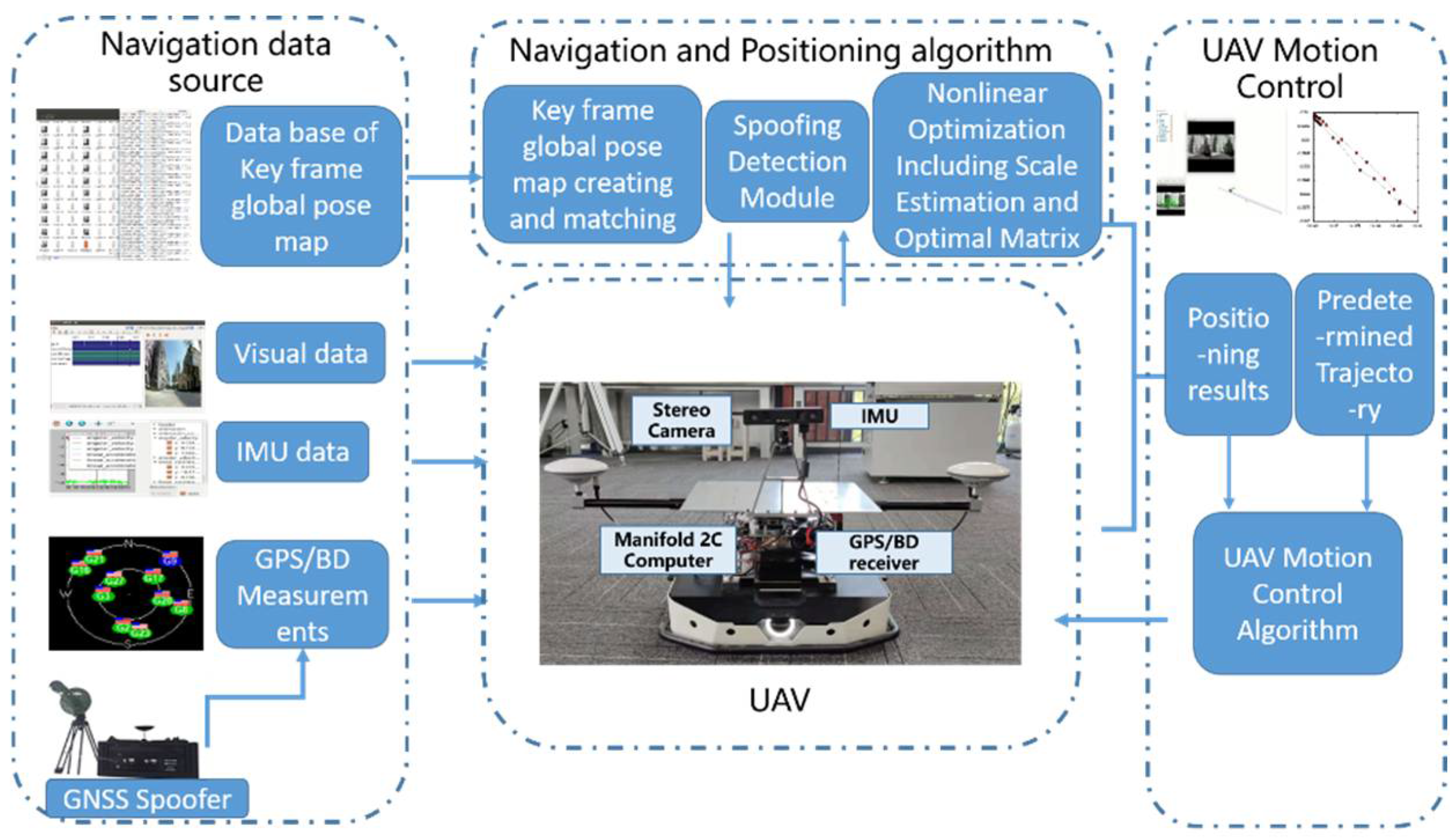
The VIG system proposed in this study combines sensor hardware and a positioning algorithm. The positioning algorithm used in this study has three modules. One is a nonlinear optimization and positioning module, including the scale estimation methods and optimal transformation matrix selection method proposed in this paper. The second is the key frame global pose map-creating and matching module, also proposed in this paper. The final module is the spoofing detection module introduced in study [20]. The input of the system is visual/IMU/GNSS data and key frame data from the database. The framework structure of the VIG system in this paper is illustrated in Figure 1.
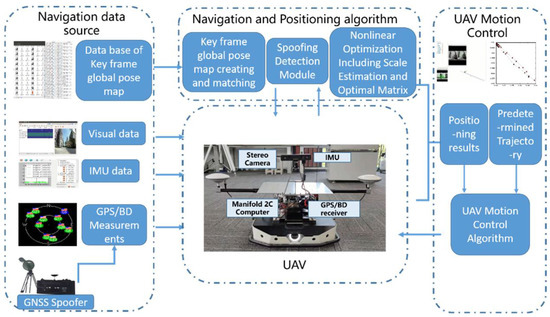
Figure 1.
An illustration of the proposed algorithm and the visual/inertial/GNSS integrated navigation system.
The main contributions of this paper can be summarized as follows:
- (1)
- To solve the problem of inaccurate scale estimation of the VIO under spoofing attack, a real-time scale compensation coefficient estimation method in a nonlinear optimization framework is proposed for the first time. GNSS measurements are used to estimate the scale compensation coefficient, helping to solve the problem of inaccurate pose estimation caused by inaccurate scale estimation when VIO is applied in a large-scale outdoor scenario.
- (2)
- For a revisit area, a VIG-integrated positioning algorithm, based on global pose map-matching, is proposed to accurately determine the pose of the system in a spoofing environment.
- (3)
- The experiment compares the difference in positioning accuracy between the two conditions without and with scale real-time estimation, and the two conditions without and with spoofing attack. It is proved that the real-time and high-precision estimation of the scale is the basis of the optimization-based VIG system operating in the spoofing environment.
- (4)
- Experiments under spoofing conditions show that the VIG navigation algorithm based on global pose map-matching has autonomous navigation and positioning abilities.
The rest of the paper is organized as follows. In Section 2, the scale compensation coefficient estimation method in the optimization-based VIG algorithm is introduced. Then, the key frame global pose map-matching method of the integrated navigation system in the revisit area under GNSS spoofing attack is introduced in Section 3. In Section 4, the optimal pose transformation matrix under the influence of spoofing is introduced. In Section 5, the algorithm proposed in this paper is tested and evaluated. Section 6 and Section 7 discuss and conclude this paper.
2. Scale Estimation of Visual/Inertial/GNSS-Integrated Algorithm
Scale factor refers to the scaling relationship between the VIO body coordinate system and the ENU world coordinate system. Under the ideal initialization conditions, the scale factor could be accurately recovered from the initialization process of the VIO [26], and directly used to obtain the transformation matrix from any frame to the world system in the subsequent estimation and localization. Therefore, the issue of scale was not taken into consideration when VIO and GNSS were fused in the VINS-Fusion algorithm [11] and other fusion algorithms. The problems in the theory analysis and experiment show that the precision of the VIO scale estimation will seriously affect the integrated positioning result under spoofing circumstances. In this section, the influence of VIO scale estimation errors on positioning accuracy is discussed, and a real-time estimation method is proposed for the nonlinear optimization of scale compensation coefficients in the fusion of VIO and GNSS.
2.1. The Influence of VIO Scale Estimation Errors on the Positioning Accuracy
In the optimization-based integrated algorithm such as VINS-MONO [26] and ORB-SLAM3 [27], the estimation of the scale factor is obtained by optimizing the cost function of the VIO. However, the scale of monocular VO could not accurately be determined, such as ORB-SLAM [28] and ORB-SLAM2 [29]. When the initialization of VINS-MONO is completed, the scale factor is also determined, so the estimation accuracy of the scale factor depends on the initialization conditions. When binocular image and IMU data are used for initialization, if the initial motion excitation of the system is sufficient, the situation is similar to that of a monocular image and IMU data. However, when the initial motion excitation of the system is insufficient, or even in a completely static state at the initial stage, the initialization of VIO degenerates so that the binocular image is only used to initialize scale. According to the discussion on binocular image scale estimation in the literature [28], the initialization condition is related to the baseline, which represents the distance between two cameras of the binocular camera. When the distance between the feature points in the binocular image and camera is less than 40 times that of the camera baseline during initialization, relatively ideal initialization results can be obtained [27]. Therefore, using only binocular images to initialize VIO’s scale is affected by the baseline length of the binocular camera, and the actual distance between the extracted feature points and the binocular system. The main application scenario of visual SLAM and VIO is an indoor scenario, which can generally easily satisfy the relationship between image key points and binocular camera baseline. However, as the VIG system is generally used in outdoor scenarios, for small-size UV and UAV, the baseline of the binocular camera does not generally exceed the size of its body; therefore, the distance between the extracted feature points and the binocular system may generally be hundreds of times the baseline length. A small baseline size requires a uniform distribution and an abundant number of feature points within a few meters during initialization, which is a strict requirement for unmanned systems applied in outdoor open areas. Therefore, compared with indoor scenes, the initialization and scale estimation of outdoor scenes are worse, and the scale estimation accuracy is lower. In addition, the calibration accuracy of the external parameters of binocular camera will directly affect the determination of the baseline length, and seriously affect the estimation accuracy of scale factors.
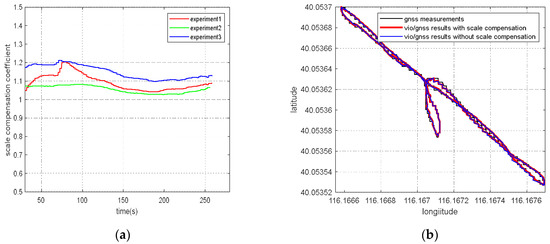
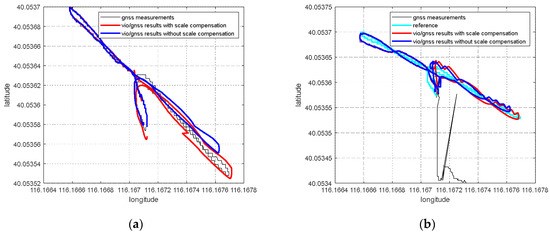
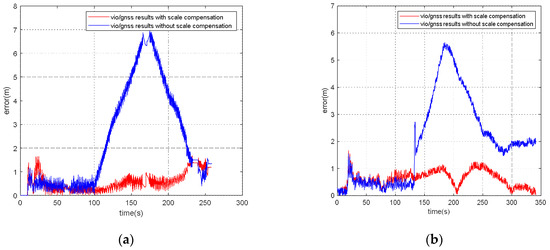
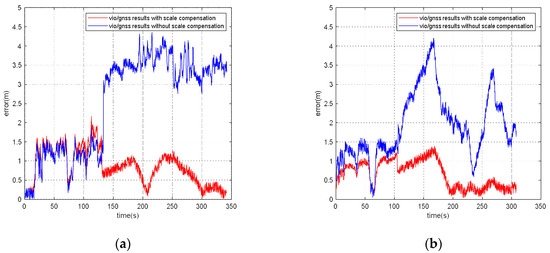
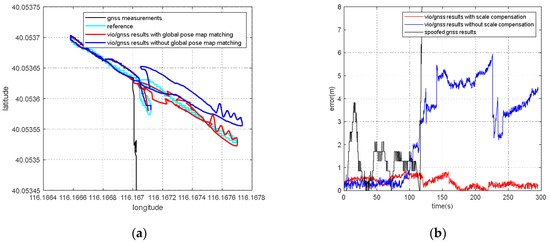
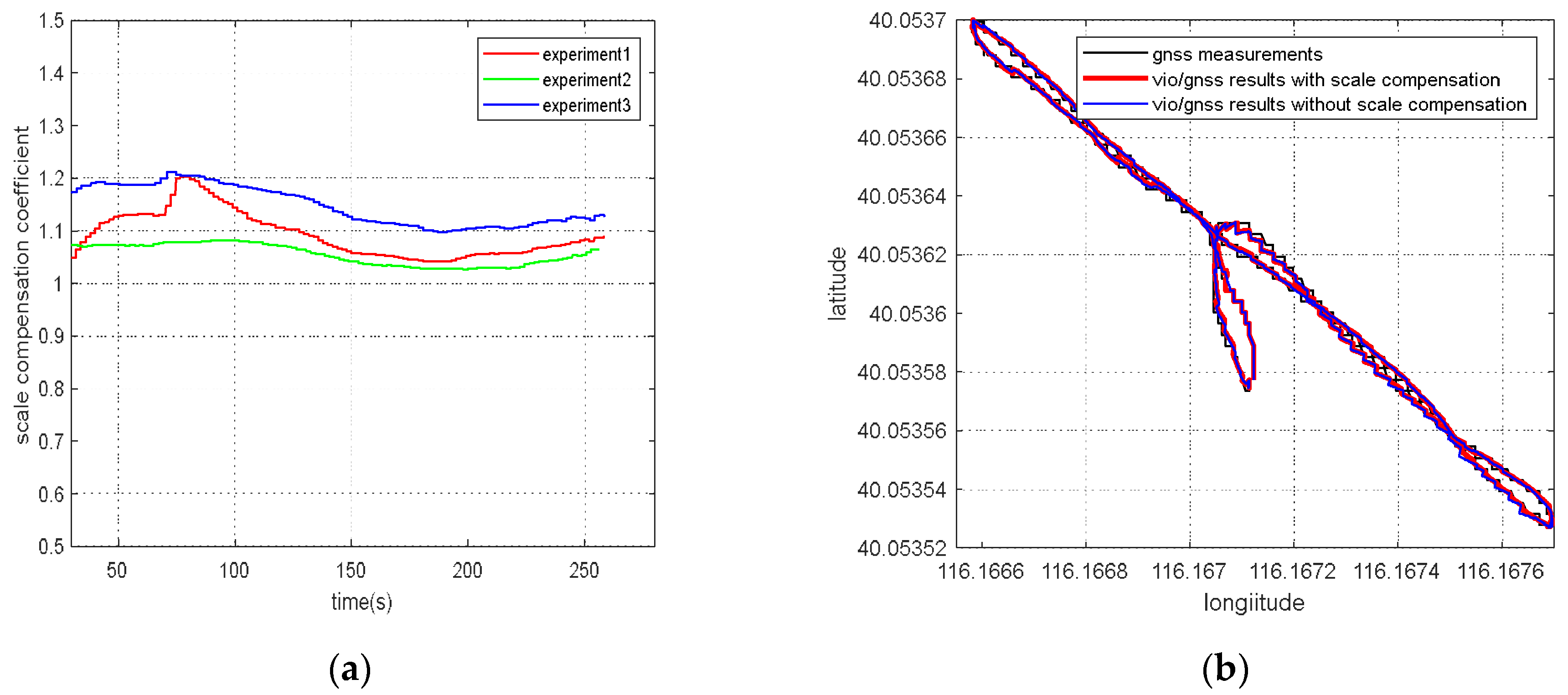
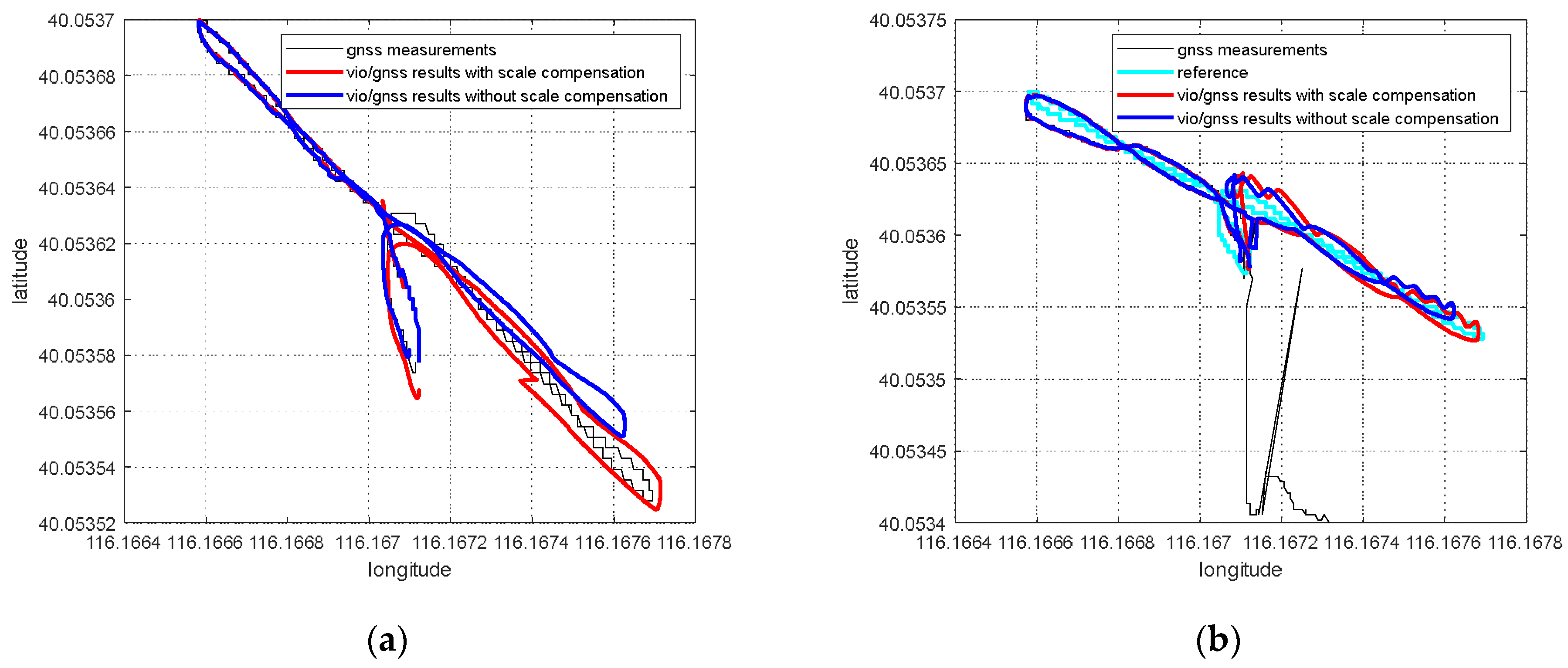
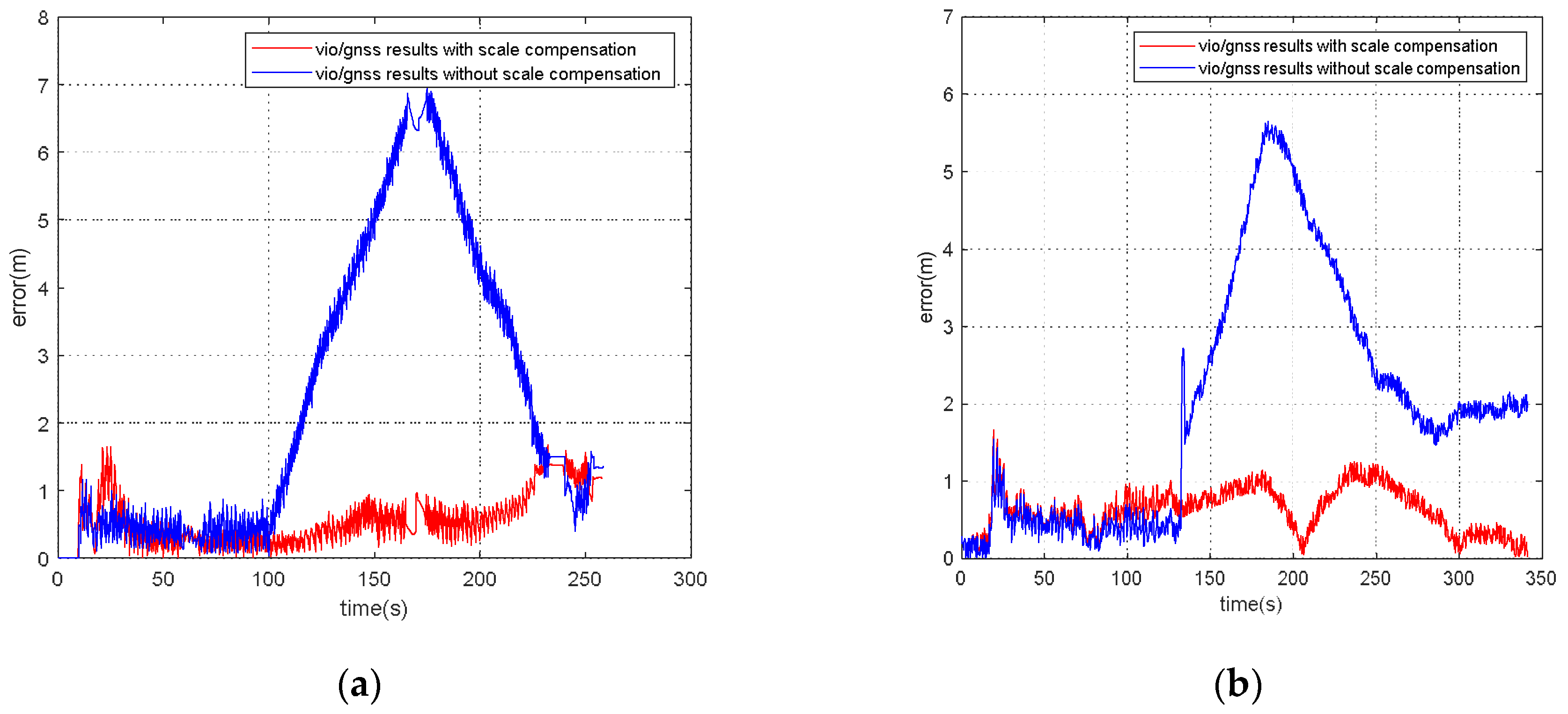
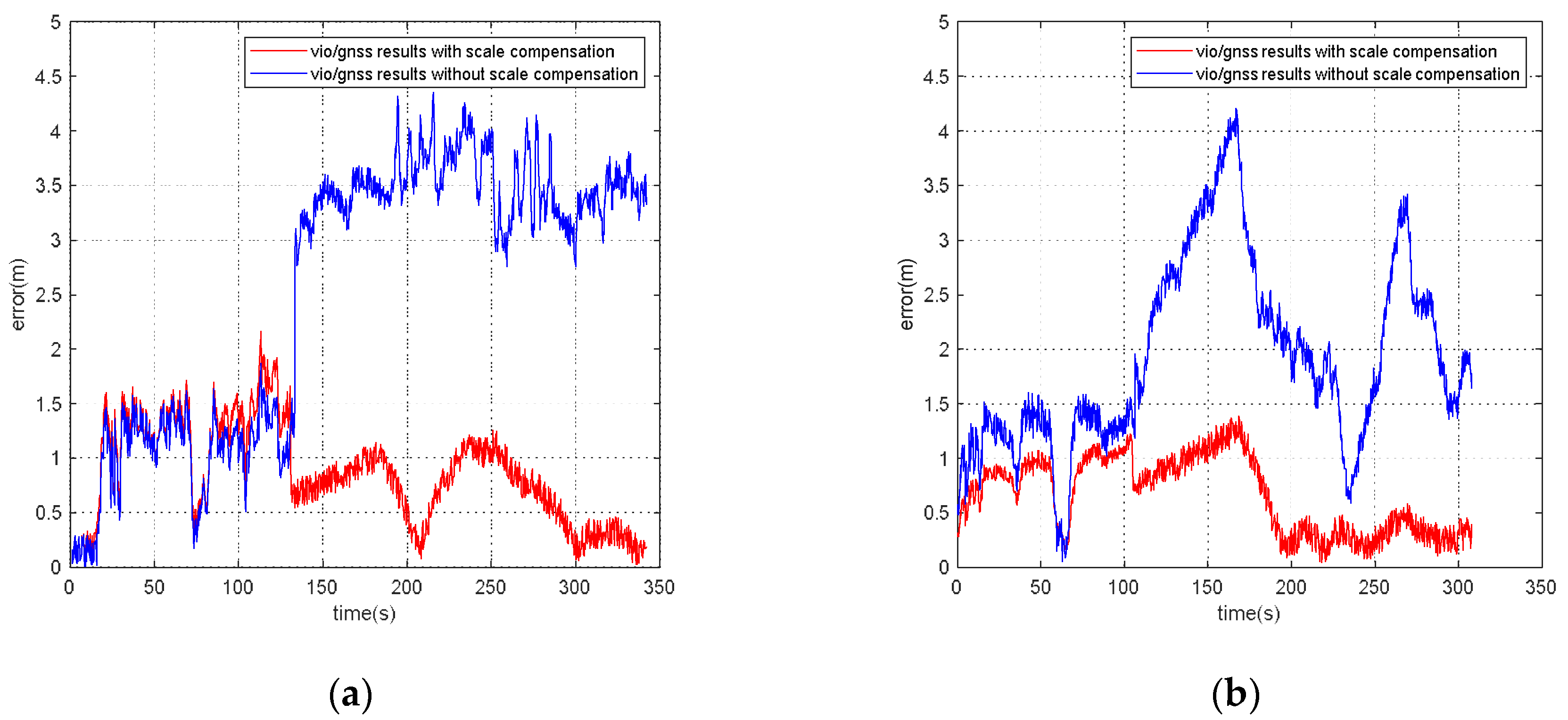
For the VIG-integrated algorithm based on nonlinear optimization adopted in this paper, the scale factor is fixed after VIO initialization. In this case, only translation and rotation exist between the VIO body coordinate system and ENU coordinate system during the nonlinear optimization of VIO and GNSS measurements. The transformation from VIO body coordinate system to an ENU coordinate system can be completely described by the pose transformation matrix, and there is no scale-scaling relationship between these two systems. When there is no spoofing, the integration of VIO and GNSS is essentially based on the characteristics of high short-term accuracy and a high update rate of VIO to correct GNSS measurements with a low update rate and positioning errors at the several meters level. Since the update rate of GNSS measurements is generally greater than 1 Hz, the higher the update rate, the lower the impact of VIO cumulative errors on the accuracy of the integrated results; therefore, the scale error has the greatest impact when the GNSS update rate is 1 Hz. In this case, the positioning error caused by the VIO scale factor mainly exists during the lag of two optimizations within 1 s. This error is related to the speed of the system, the accuracy of the initial estimation of the scale, and the time. Without loss of generality, the experiment results in Section 5.4 are used to clarify the influence of the scale estimation error. The scale compensation coefficient is about 1.1–12 in Section 5.4, which means that the relative error of the scale factor ranges from about 10% to 20%. That is, the error caused by the accumulated estimation deviation in the scale factor within 1 s is about from 10% to 20% of the system movement distance. For the unmanned system with a lower speed than 10 m/s, the error caused by the estimation deviation of scale factor ranges from about 1 m to 2 m in 1 s, which is still better than the accuracy of GNSS measurements. Therefore, for the outdoor environment with only real GNSS signals, due to the continuous correction effect of GNSS measurements, the impact of scale factor estimation deviation on the integrated results is within an acceptable range.
However, VIO cannot obtain an effective correction from GNSS measurements when GNSS spoofing occurs. At this time, the error caused by the scale estimation deviation will become the most important part of the VIO cumulative error, so the integrated results will continuously be affected by the scale factor error after spoofing is detected, and is also proportional to the system motion speed, motion time, etc. Additionally, a relative estimation accuracy of 10% is estimated; even if the unmanned system runs at a low speed of 1 m/s, it will accumulate more than 10 m cumulative errors within 2 min. Based on the above analysis, when GNSS spoofing exists, the estimation accuracy of the VIO scale factor will seriously affect the output accuracy of the integrated results after spoofing is detected. In addition to the scale factor estimation in the VIO initialization stage, it is necessary to further optimize the scale compensation coefficient by using GNSS measurements in the VIG nonlinear optimization [30].
2.2. Estimation of Scale Compensation Coefficient Based on Nonlinear Optimization
The estimation of scale factors in VIO initialization may have inherent errors due to poor initialization conditions and other factors. A real-time optimization estimation algorithm of the scale compensation coefficient was proposed for VIG-integrated positioning algorithm with GNSS measurement correction information.
The outputs of the VIG-integrated algorithm are the pose and position global estimations of the system. According to the previous study [20], the parameters that are to be estimated in the nonlinear optimization include a set of global estimations , in which represents the serial number of global estimations in the optimize window. is the global estimation of key frame number . is the positioning result in ENU system. is the attitude quaternion in ENU system. The cost function of the navigation algorithm can be described as follows:
in which . is the normalized residual of the VIO factor, which represents the residual between the VIO measurement and the global estimation of key frame . is the normalized residual of GNSS factor, which represents the residual between the GNSS measurement and the global estimation of key frame . is the error covariance matrix of the VIO factor, and is the error covariance matrix of the GNSS factor. is the GNSS confidence factor [20].
When ignoring the scale estimation error of the VIO, there is no scale-scaling relationship between the VIO body coordinate system and ENU co-ordinate system, and only translation and rotation exist between these two systems. The residual of VIO factor can be described as:
where is the positioning result of VIO in body system, is the attitude quaternion of VIO in the body system, and represents the quaternion subtraction that is used to calculate the residual.
Considering the scale estimation error, and are in two coordinate systems with different scales. It is not proper to directly calculate the residual. Therefore, the scale compensation coefficient is set to correct the scale estimation error of VIO, and the scale compensation coefficient is added to the parameters that are to be optimized for each node, in addition to the three-dimensional positioning information and attitude quaternion. The parameters to be optimized are modified to .
The residual of VIO factors is involved in quaternion multiplication and other operations. Adding the scale compensation coefficient into VIO factors will greatly increase the computation burden of nonlinear optimization. Therefore, an equivalent transformation is carried out, so that the residual of GNSS factor with a relatively simple structure is adjusted, instead of adjusting the structure of the residual of the VIO factor. A pseudo-world coordinate system is defined, whose origin and axes exactly coincide with the ENU coordinate system, but whose scale is the same as the VIO body system. This pseudo-world coordinate system and the real ENU system differ only in the scale-scaling caused by the scale estimation error. GNSS factor adjustment means that the optimization strategy of minimizing the cost function in the ENU coordinate system is adjusted to minimize the cost function in the pseudo-world system containing the scale factor error. Then, based on the optimized scale compensation coefficient, the optimized pose solution consistent with the scale of VIO system is transformed into the real ENU system.
In this case, the parameters to be optimized are , which contain the pose solution in pseudo-world system and the scale compensation coefficient from the pseudo-world system to the ENU system. The set of global pose estimations is . The residual of the GNSS factor in the pseudo-world system can be described as
in which is the GNSS measurement at the moment of key frame , which has been transformed from latitude and longitude coordinates to ENU coordinates. Superscript stands for pseudo-world system.
The residual of the VIO factor in the pseudo-world system can be described as
The residual of the GNSS factor and the residual of the VIO factor are both calculated in a pseudo-world system. The cost function of VIG integrated algorithm can be described as follows:
in which .
The solution of this cost function is a graph-based optimization problem. The iteration-based Google Ceres Solver [31], which uses Gaussian–Newton and Levenberg–Marquadt approaches, was used to solve this optimization problem in this study. The global pose estimation obtained from the optimization of the cost function is in the pseudo-world system. The positioning information and attitude quaternion of the global pose estimation in the real ENU system can be calculated by the scale compensation coefficient as:
In the nonlinear optimization, the global pose estimation and the scale compensation coefficient from the pseudo-world system to the ENU system are optimized and estimated at the same time. Finally, the global pose estimation in the ENU system is obtained through the scale compensation coefficient. In this way, even if the initialization conditions are not good and the VIO scale factors have errors, the errors in the scale factors can be compensated in the nonlinear optimization of GNSS fusion. The error from the VIO local system to the world system transformation matrix caused by the scale factor error is eliminated, guaranteeing high accuracy in the global pose obtained by VIO recursion during the two optimization intervals.
4. Optimal Pose Transformation Matrix under Spoofing Interference
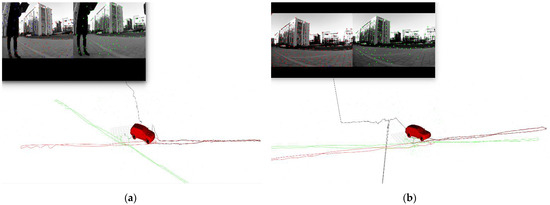
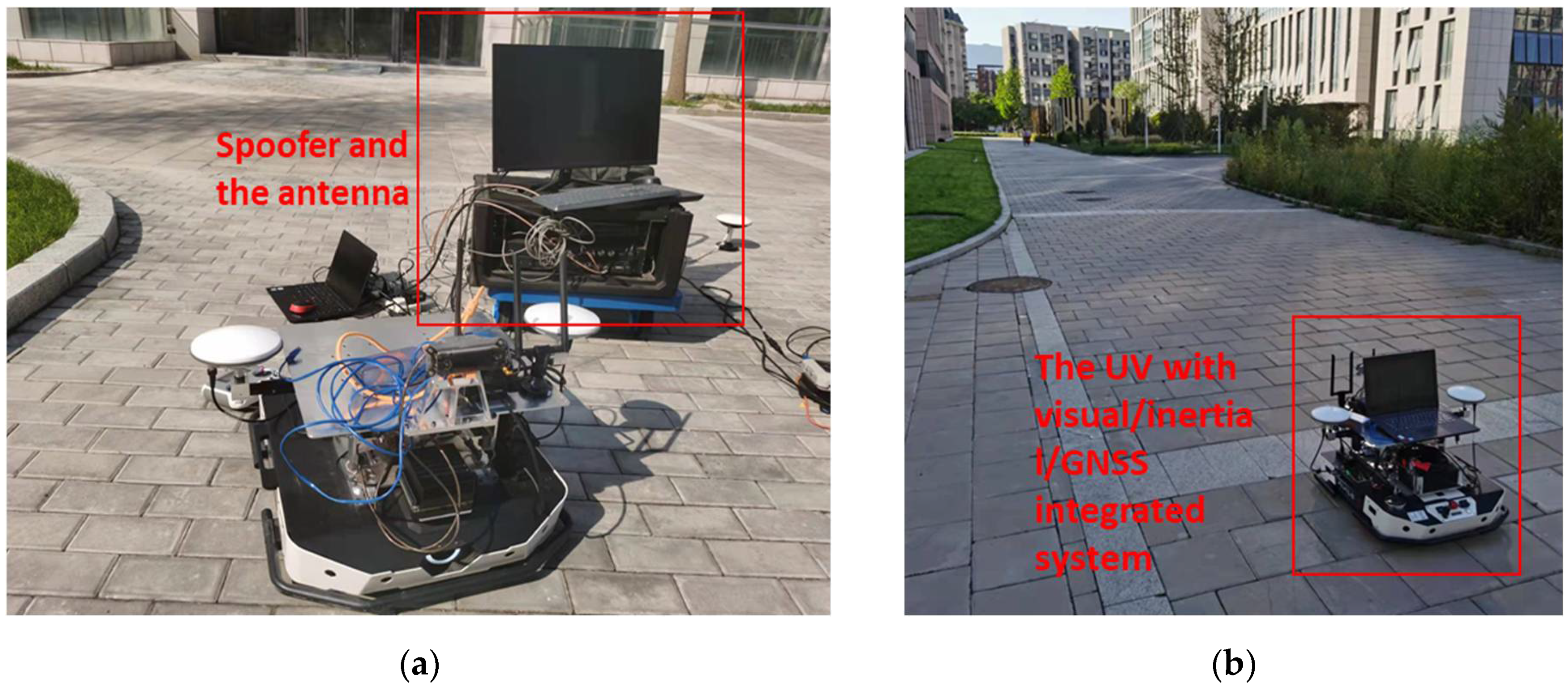
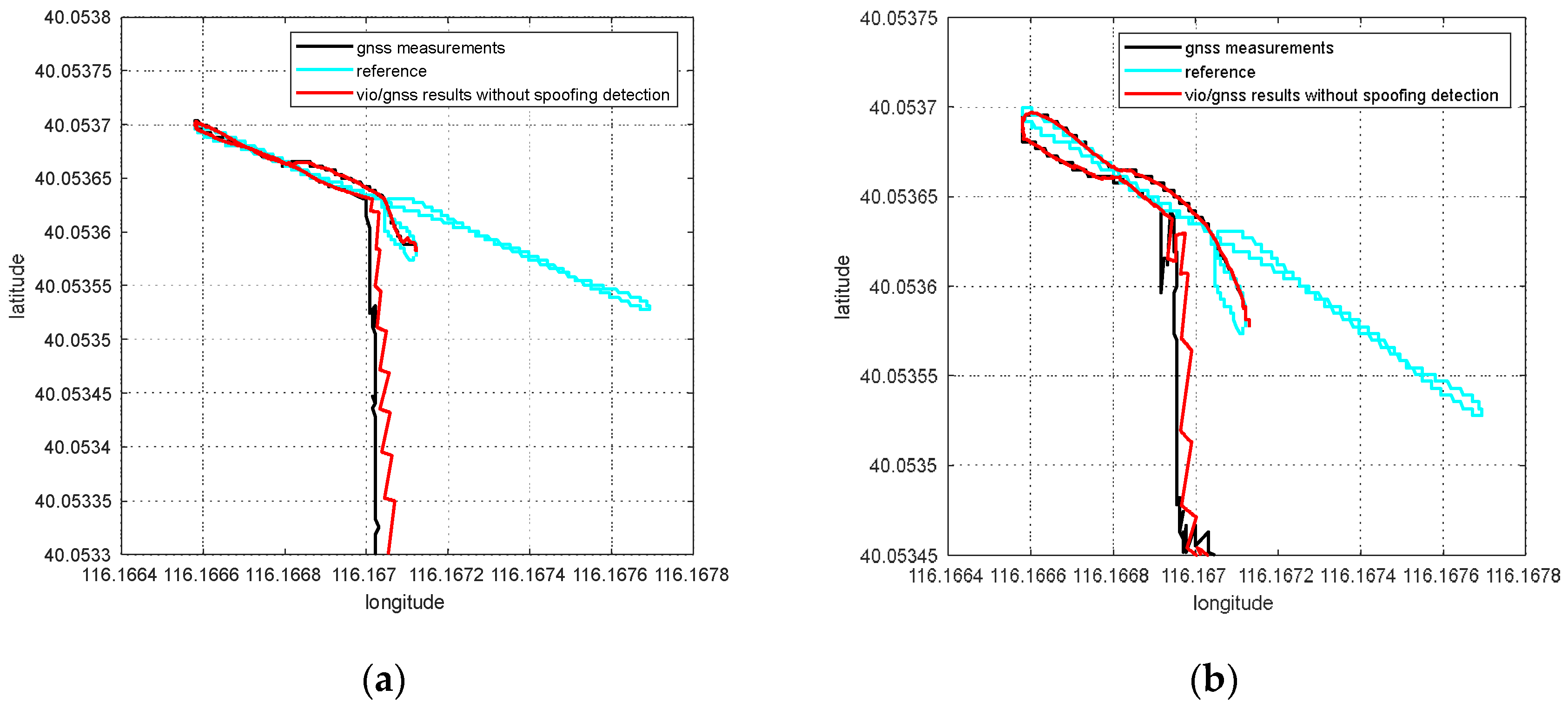
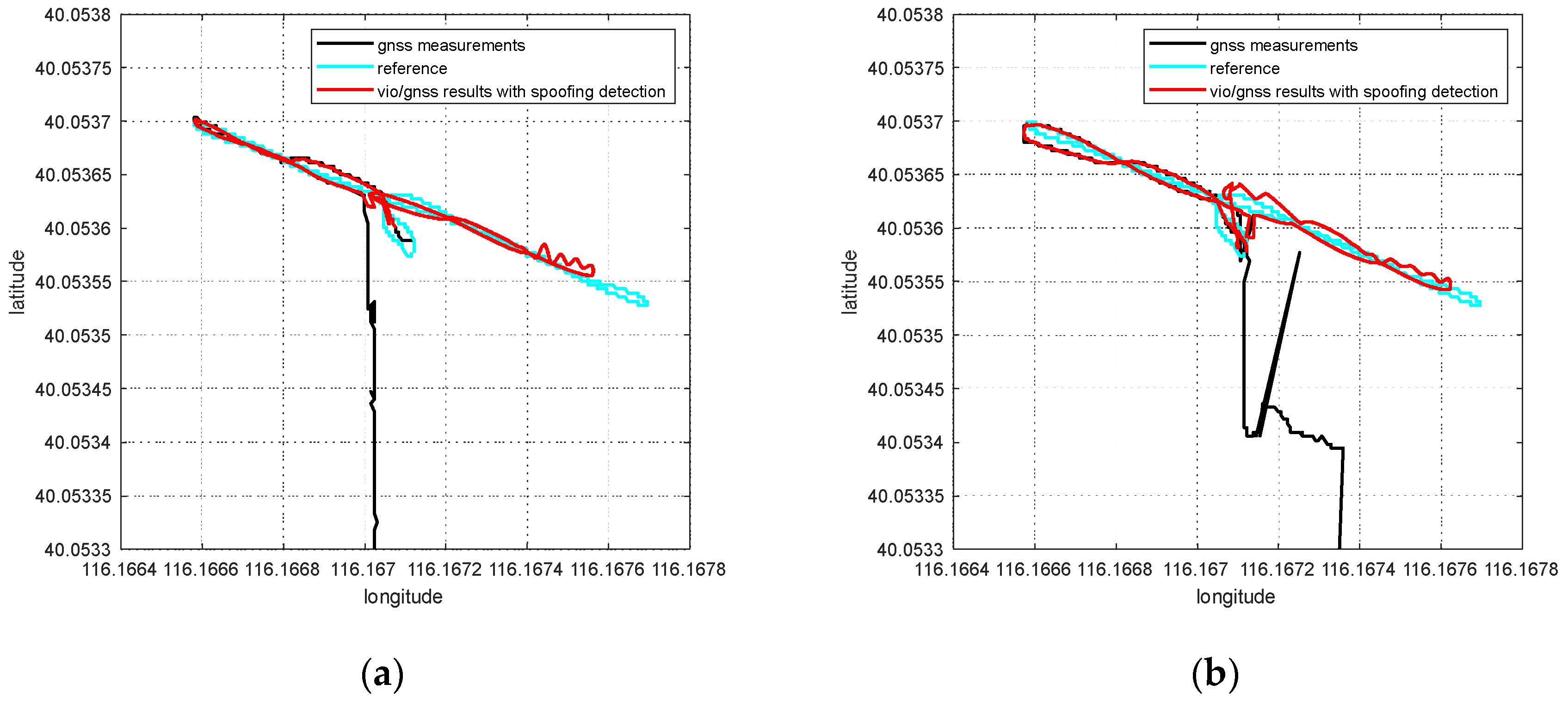
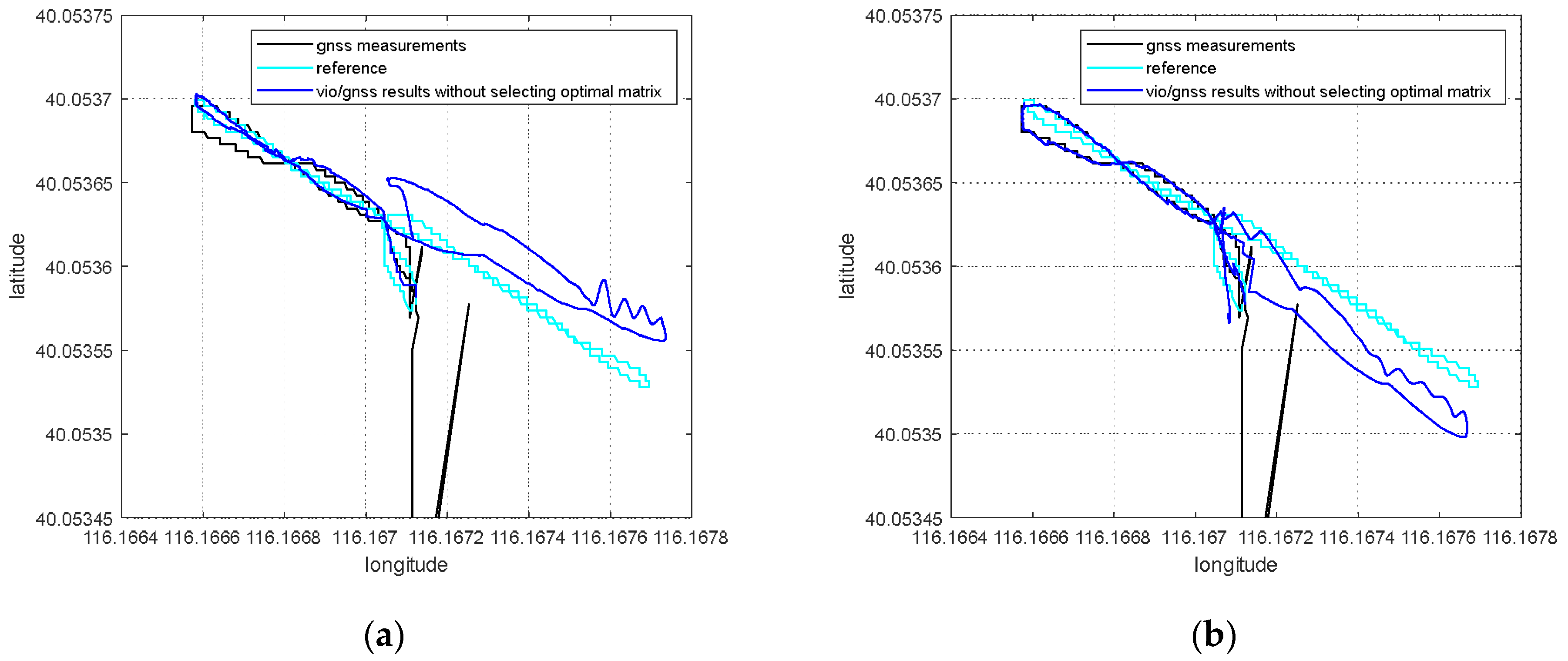
To slowly induce spoofing [4], spoofing deviation is gradually added into the GNSS measurements. For the Chi-square-based spoofing detection or nonlinear optimization residual-based spoofing detection [20,21], it is necessary to accumulate multiple sets of GNSS measurements to complete the spoofing detection. In fact, ithas a transitional process from the appearance of the spoofing signal to the identification of spoofing. That is, although the positioning deviation of the system from the real position is small during this period, the GNSS measurements in the transition period already contain spoofing deviations. This part of the GNSS measurements enters the global optimization and has an impact on the global pose solution and the pose transformation matrix. In this section, the influence of the spoofing transition is discussed. The spoofing deviation correction method based on an optimal pose transfer matrix is proposed to eliminate the influence of the spoofing transition period.
4.1. Effect of Spoofing Interference on Pose Solution before Spoofing Been Detected
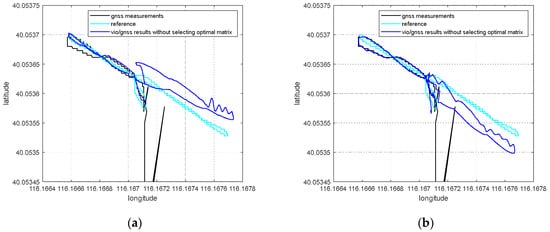
When the simulated position of the spoofing signal generally starts from the current real position of the integrated navigation system in inducing spoofing, and slowly pulls the output of the GNSS receiver in a certain direction. This is a continuous change from the real position to the spoofed one, not a sudden, sharp jump. As the receiver does not appear to lose lock or have a sharp jump in outputs, the inducing spoofing is more hidden and difficult to detect by the receiver or the whole system. It takes time to successfully detect spoofing. During the transition time of spoofing detection, the receiver is affected by spoofing signals, and the GNSS measurements contain some spoofing deviations.
There are two main effects on the global results that the GNSS measurements are affected by spoofing deviations in transition. On the one hand, it affects the estimation of the global pose through global optimization. On the other hand, it affects the pose transformation matrix from the VIO body system to the ENU system. When no GNSS measurement is updated, the integrated navigation system needs to transform the pose estimation by VIO into the ENU system through . The optimization and updating of the pose transformation matrix derive from the nonlinear optimization process of VIG pose estimation; therefore, the coordinate system transformation will also include errors when GNSS spoofing errors in the transition process enter the global optimization process.
If pose transformation matrix contains deviations, then the pose estimation of VIO cannot be accurately transformed into the ENU system. This will seriously affect the global estimation results in the spoofing environment.
4.2. Spoofing Deviation Correction Based on Optimal Pose Transformation Matrix Selection
When spoofing attacks exist, the GNSS confidence factor has been used, as in [20], to greatly reduce the weight of the spoofed GNSS measurements in nonlinear optimization, but the influence on the pose transformation matrix of the spoofed GNSS measurements in terms of transition time has not been taken into account. After each optimization, the pose transformation matrix will be updated according to the optimized global pose solution and VIO pose estimation. This optimization update is necessary under normal conditions. However, during the spoofing transition, the optimization and updating of will be affected by the spoofing deviation.
When is updated after optimization, the nonlinear optimization residual can be used as an indicator parameter to characterize whether the distribution of VIO pose estimation and GNSS measurements is reasonable in this nonlinear optimization. When the GNSS measurement contains spoofing bias, the deviation between the GNSS measurement and the ground truth will deviate from the reasonable range of normal distribution, so the nonlinear optimization residual will abnormally increases.
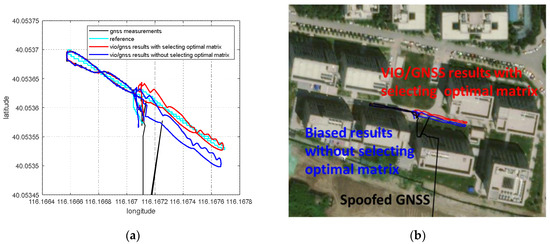
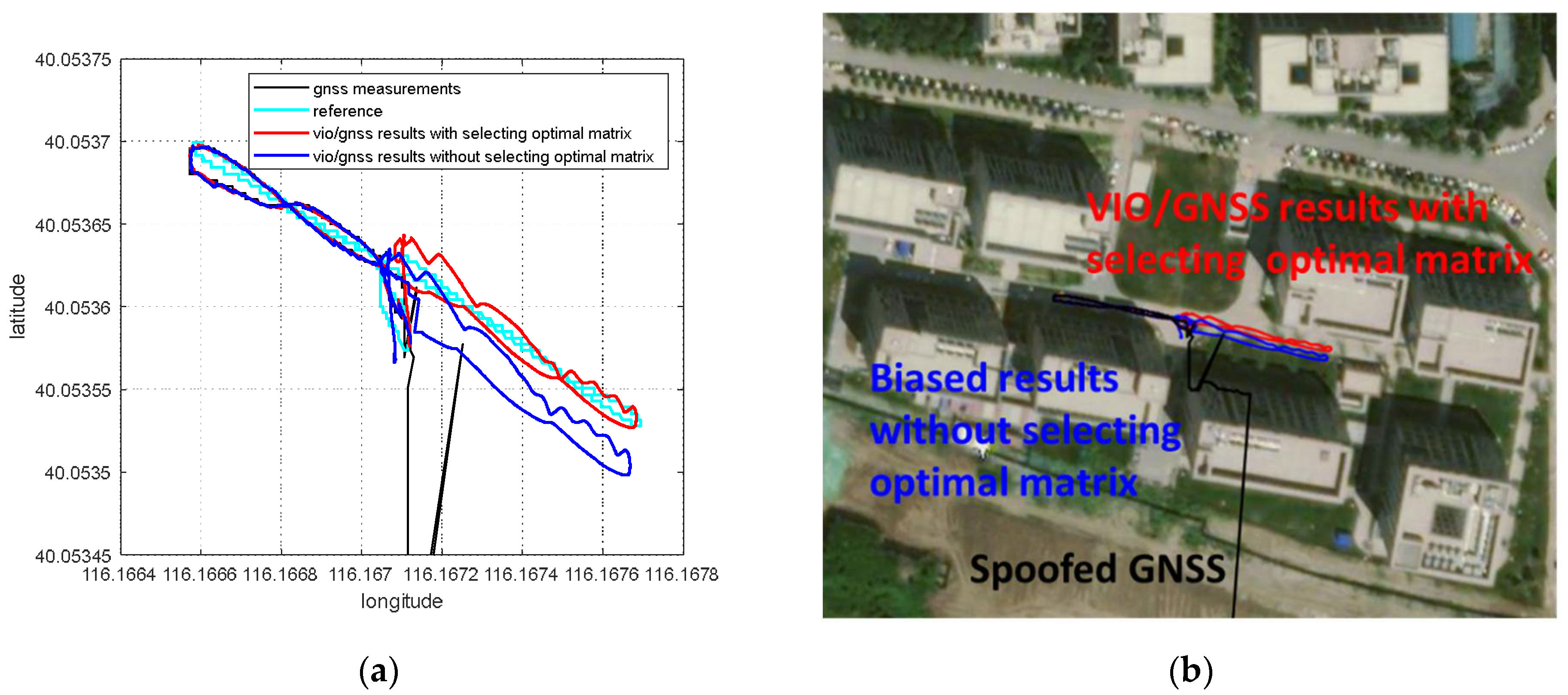
The optimal pose transformation matrix can be selected based on nonlinear optimization residual . When GNSS spoofing detection is finished, the pose transformation matrix is no longer updated according to the optimized global pose estimation and VIO pose estimation. Instead, the pose transformation matrix with the minimum nonlinear optimization residual is found to be the optimal pose transformation matrix . Optimization under this selection principle means that when the pose transformation matrix is , the deviation between the VIO pose estimation, the GNSS measurements and the global optimization pose estimation is at a minimum. The minimum nonlinear residual indicates that the pose transformation matrix obtained from VIO pose estimation and global optimization pose estimation is the most accurate. The optimal pose transformation matrix can be expressed as follows:
After GNSS spoofing interference is detected, the transformation of VIO pose estimation from a VIO body system to an ENU coordinate system can be completed through the optimal pose transformation matrix, as follows:
in which is the positioning estimation and the rotation matrix of VIO pose estimation in the ENU system. is the rotation matrix of optimal pose transformation matrix .
In the case of GNSS spoofing, the GNSS confidence factor approaches 0 in the nonlinear optimization of Equation (1), and the GNSS measurement is seduced by spoofing interference, so it is practically unavailable. The output of the VIG-integrated positioning system basically depends on the VIO pose estimation, which is transformed into the ENU coordinate system. Therefore, for the VIG system under spoofing interference conditions, the estimation accuracy of VIO itself and the pose transformation matrix between the VIO body system and the ENU system are the two most important aspects that affect the accuracy of global pose estimation. The pose estimation accuracy of VIO itself is guaranteed by the VIO algorithm, and the pose transformation matrix avoids the influence of spoofing deviation through the selection of the optimal pose transformation matrix.
6. Discussion
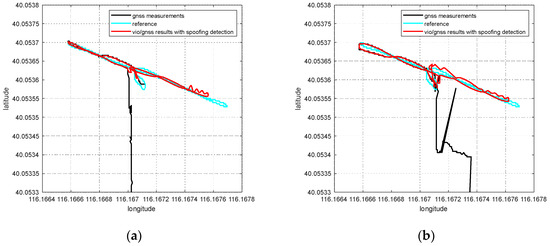
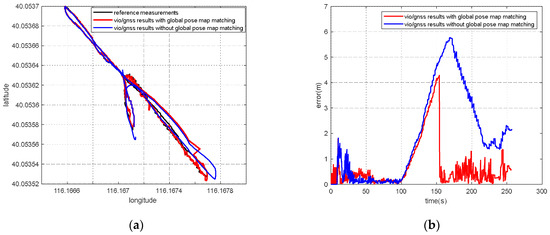
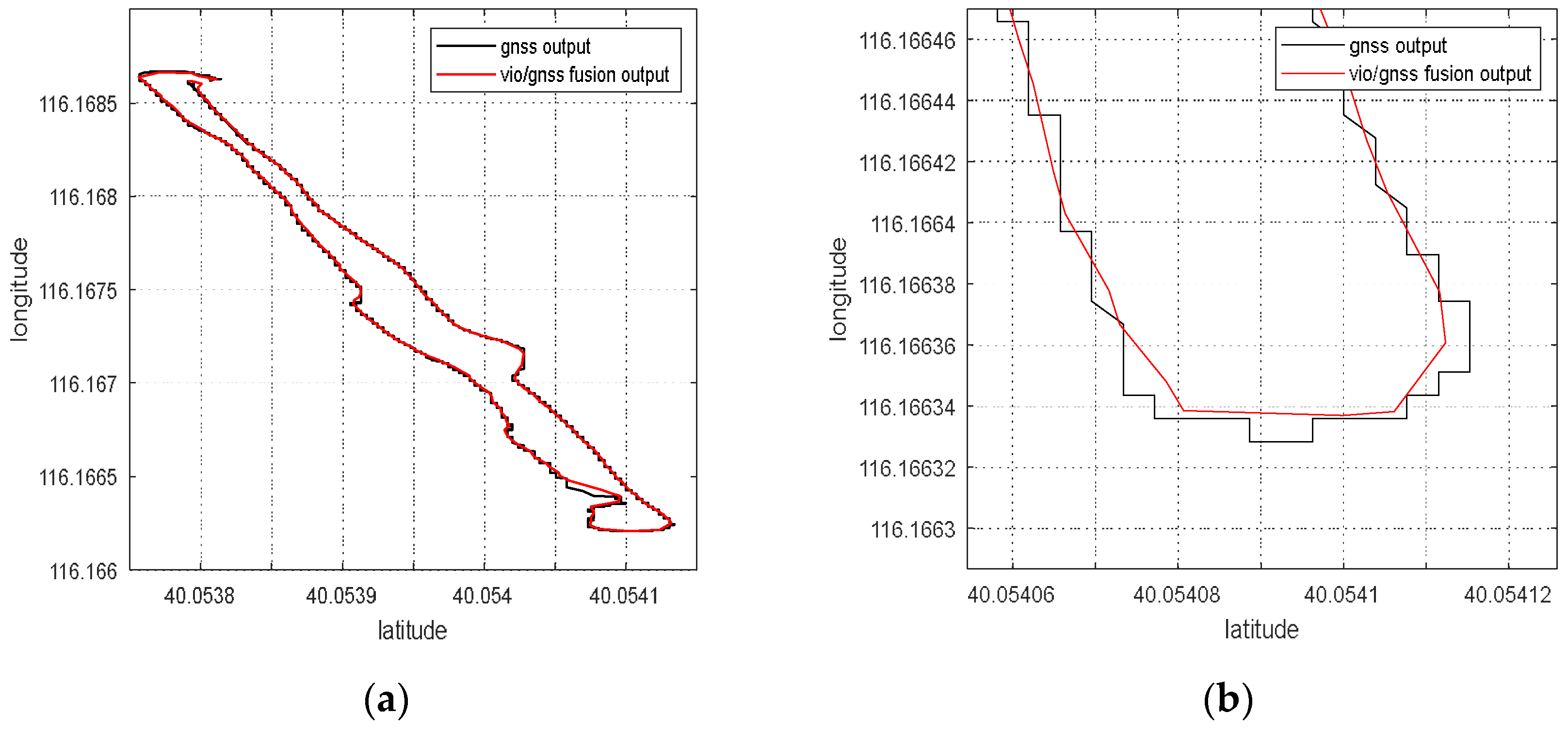
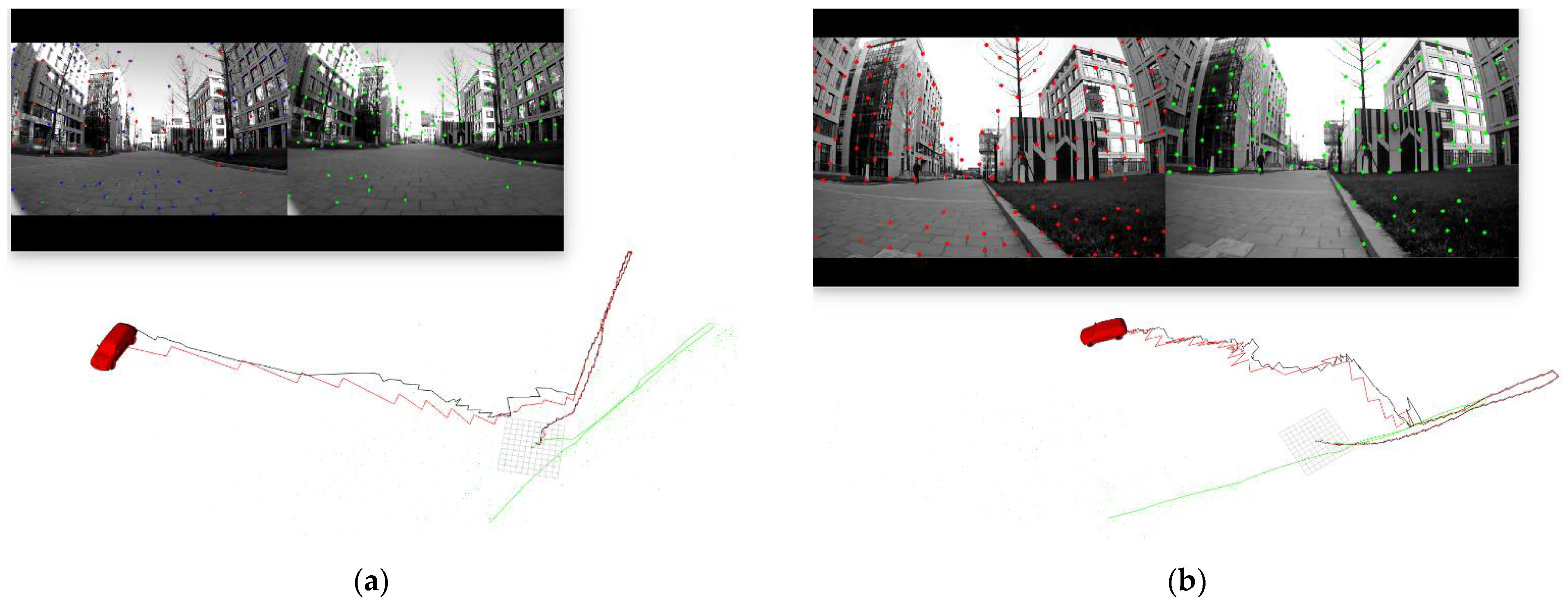
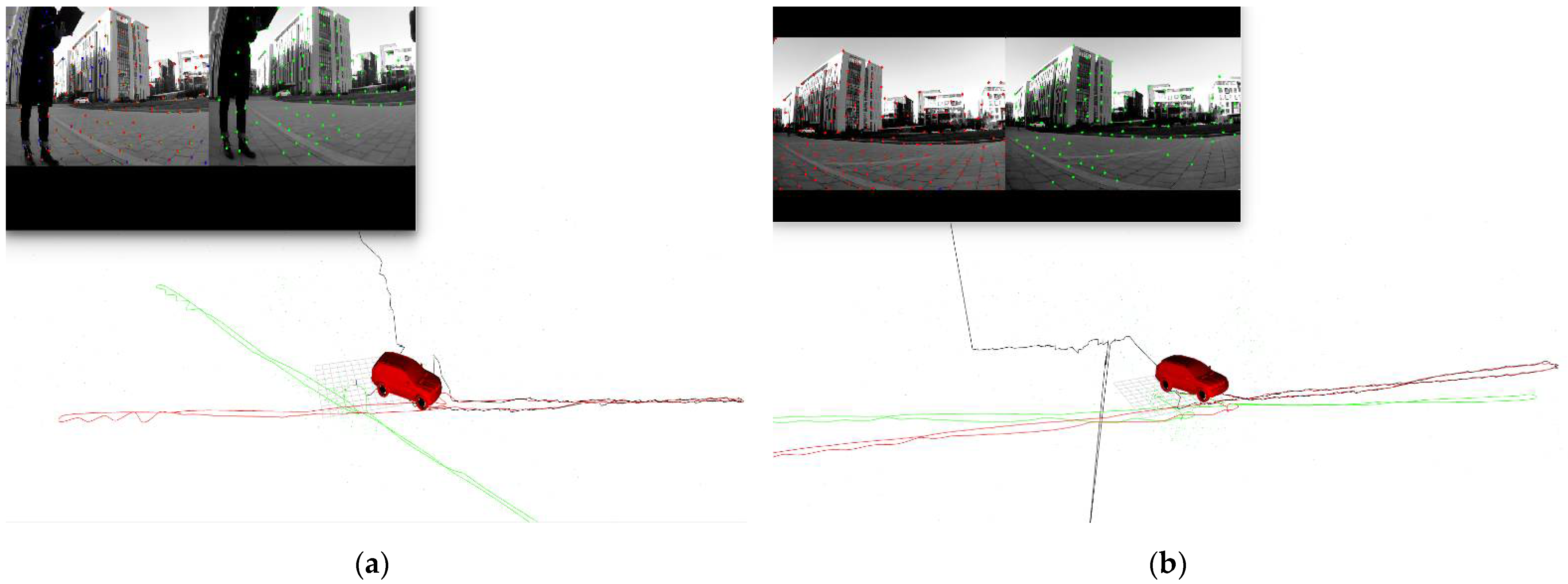
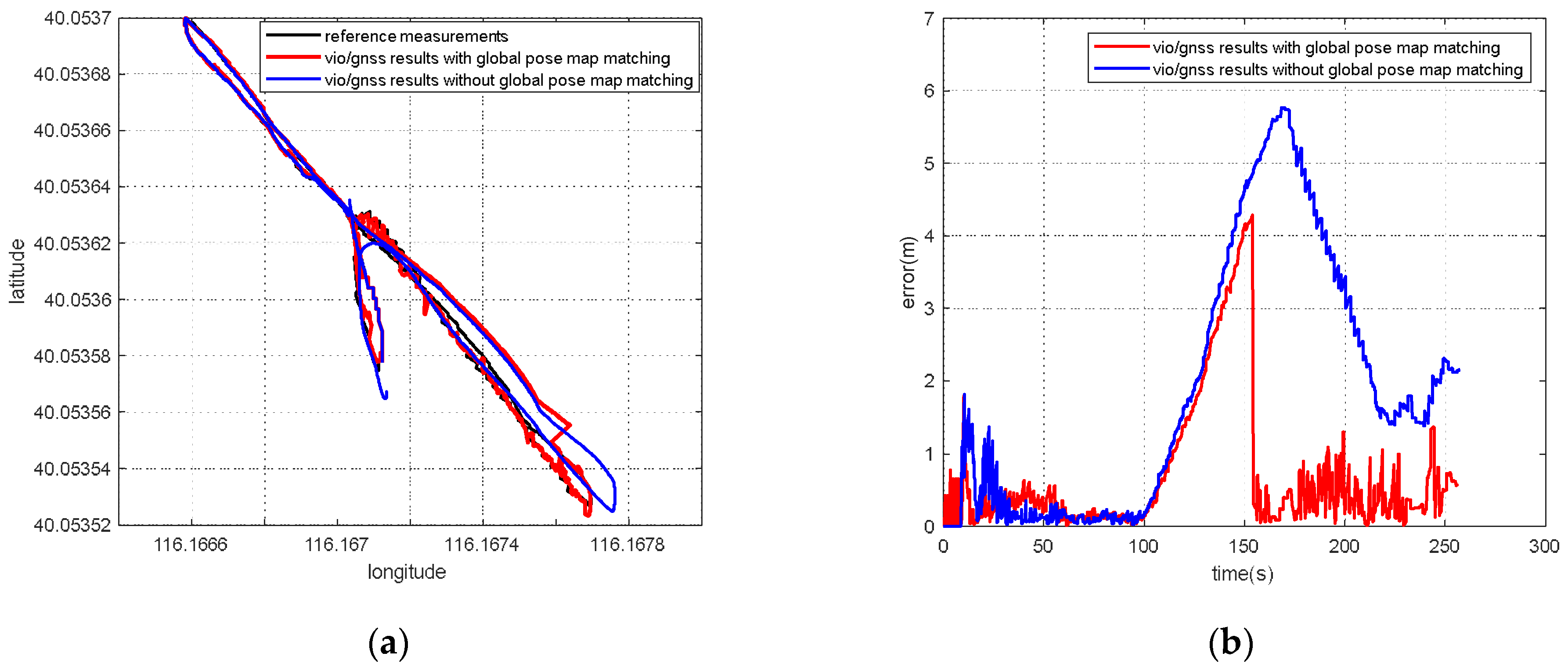
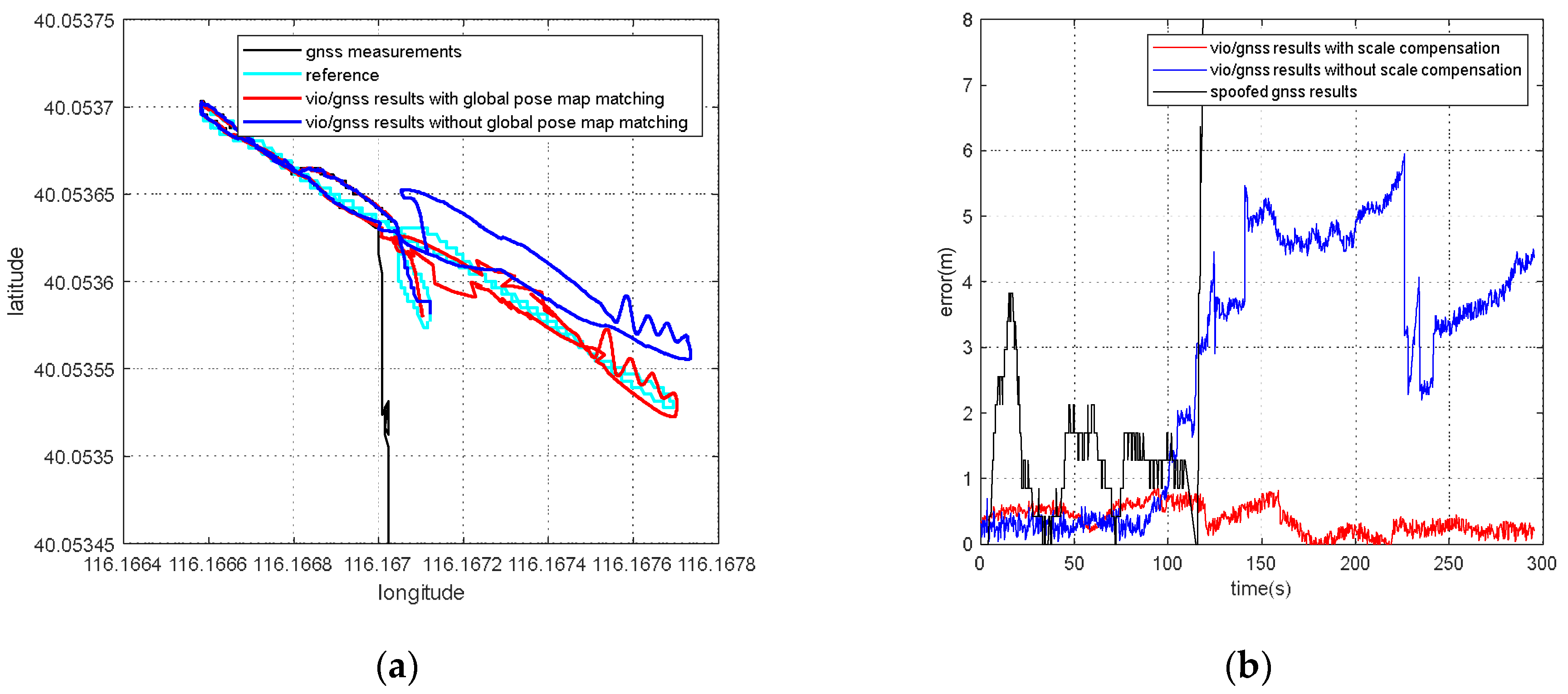
According to the experiment results, when the spoofing detection module proposed in [20] is not enabled, the positioning solutions output by the integrated system will be induced by spoofing signals. This means that the risk of VIG-integrated positioning system in GNSS spoofing scenarios actually exists and requires more attention. The VIO scale estimation error and the transformation matrix deviation in the transition period of spoofing detection proved to be harmful to the global pose estimation of integrated systems under GNSS spoofing. The experiment firstly verifies the effectiveness of the spoofing detection algorithm. Focusing on the problem of inaccurate scale estimation in VIO initialization, a real-time estimation method of scale compensation coefficients for nonlinear optimization framework is proposed in this paper. GNSS measurements are used to estimate the scale compensation coefficients from the VIO local system to the ENU coordinate system. The results of the scale compensation experiment under spoofing show that the relative positioning error of the integrated system can be reduced by an order of magnitude. To eliminate the influence that the spoofing GNSS measurements that enter nonlinear optimization during the spoofing transition process have on the subsequent integrated positioning results, a deviation correction method based on optimal pose transformation matrix selection is proposed in this paper. The experiment results show that the global deviation caused by the influence of the spoofing transition process can be corrected by selecting the optimal pose transformation matrix. For some special areas that the integrated system can revisit many times, a global pose map-matching method is proposed for VIG-integrated algorithms. The experimental results show the effectiveness of the proposed matching method. The relative positioning error of the integrated system and the accumulated error could be reduced by matching the key frames with global pose. The experiment area is limited because of the restrictions of the power of a GNSS spoofer so that it does not influence others. The performance of the integrated system in a large area under spoofing could be further studied.
7. Conclusions
In this paper, the performance of a visual/inertial/GNSS integrated system under GNSS spoofing attack is discussed. The spoofing detection method is based on previous studies [10] and is not the focal point of this study. The focal point is the key problems that mainly affect the positioning accuracy after GNSS spoofing detection. Two of these key problems are discussed: VIO scale estimation errors and errors in the transition period of spoofing detection. Three methods, scale compensation coefficient estimation, optimal pose transformation matrix selection and global pose map-matching, were proposed in this paper to depress the positioning errors due to GNSS spoofing attacks.
For the first time, the VIG-integrated system is evaluated in a real-world GNSS spoofing scenario. The three methods proposed in this paper are tested and compared in spoofing scenarios. All three methods proved that this could be used to improve the performance of the VIG-integrated system operating in a GNSS spoofing environments or under GNSS spoofing threats. Based on this work, the robustness and reliability of the integrated system under GNSS spoofing will be further discussed, and further research will be carried out concerning more complex spoofing scenarios such as intelligence-induced spoofing.
Author Contributions
Conceptualization, Z.Y. and F.X.; software, N.G.; validation, Z.Y., F.X. and N.G.; formal analysis, F.X.; investigation, N.G.; resources, Z.Y.; data curation, N.G.; writing—original draft preparation, N.G.; writing—review and editing, F.X.; visualization, N.G.; supervision, F.X.; project administration, Z.Y. All the authors have read and agreed to the published this version of the manuscript. All authors have read and agreed to the published version of the manuscript.
Funding
This research was carried out in the State Key Laboratory of Precision Measurement Technology and Instruments, Tsinghua University under the financial support by the NSFC project (No. 51827806) and the NSFC project (No. U21A6003).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Schreiber, M.; Königshof, H.; Hellmund, A.; Stiller, C. Vehicle localization with tightly coupled GNSS and visual odometry. In Proceedings of the 2016 IEEE Intelligent Vehicles Symposium (IV), Gothenburg, Sweden, 19–22 June 2016; pp. 858–863. [Google Scholar]
- Gong, Z.; Ying, R.; Wen, F.; Qian, J.; Liu, P. Tightly Coupled Integration of GNSS and Vision SLAM Using 10-DoF Optimization on Manifold. IEEE Sens. J. 2019, 19, 12105–12117. [Google Scholar] [CrossRef]
- Jafarnia-Jahromi, A.; Broumandan, A.; Nielsen, J.; Lachapelle, G. GPS Vulnerability to Spoofing Threats and a Review of Antispoofing Techniques. Int. J. Navig. Obs. 2012, 2012, 127072. [Google Scholar] [CrossRef]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber threats facing autonomous and connected vehicles: Future challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Shepard, D.; Bhatti, J.; Humphreys, T. Evaluation of smart grid and civilian UAV vulnerability to GPS spoofing attacks. In Proceedings of the ION GNSS Meeting, Nashville, TN, USA, 17–21 September 2012. [Google Scholar]
- Noh, J.; Kwon, Y.; Son, Y.; Shin, H.; Kim, D.; Choi, J.; Kim, Y. Tractor beam: Safe-hijacking of consumer drones with adaptive GPS spoofing. TOPS 2019, 22, 1–26. [Google Scholar] [CrossRef]
- Kerns, A.; Shepard, D.; Bhatti, J.; Humphreys, T. Unmanned Aircraft Capture and Control Via GPS Spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Groves, P. Principles of GNSS, Inertial, and Multi-Sensor Integrated Navigation Systems; Artech House: Norwood, MA, USA, 2007. [Google Scholar]
- Aumayer, B. Ultra-tightly Coupled Vision/GNSS for Automotive Applications. Ph.D. Thesis, University of Calgary, Calgary, Canada, 2016. [Google Scholar]
- Qin, T.; Pan, J.; Cao, S.; Shen, S. A General Optimization-based Framework for Local Odometry Estimation with Multiple Sensors. arXiv 2019, arXiv:1901.03638. [Google Scholar]
- Cao, S.; Lu, X.; Shen, S. GVINS: Tightly Coupled GNSS-Visual-Inertial Fusion for Smooth and Consistent State Estimation. arXiv 2021, arXiv:2103.07899. [Google Scholar] [CrossRef]
- Meng, L.; Yang, L.; Yang, W.; Zhang, L. A Survey of GNSS Spoofing and Anti-Spoofing Technology. Remote Sens. 2022, 14, 4826. [Google Scholar] [CrossRef]
- Humphreys, T.E.; Ledvina, B.M.; Psiaki, M.L.; O’Hanlon, B.W.; Kintner, P.M. Assessing the Spoofing Threat: Development of a Portable GPS Civilian Spoofer. In Proceedings of the International Technical Meeting of the Satellite Division of the Institute of Navigation, Savannah, GA, USA, 16–19 September 2008. [Google Scholar]
- Tanil, C.; Khanafseh, S.; Pervan, B. The impact of wind gust on detectability of GPS spoofing attack using RAIM with INS coupling. In Proceedings of the ION 2015 Pacific PNT Meeting, Honolulu, HI, USA, 20–23 April 2015; pp. 674–686. [Google Scholar]
- Tanil, C.; Khanafseh, S.; Pervan, B. Detecting global navigation satellite system spoofing using inertial sensing of aircraft disturbance. J. Guid. Control. Dyn. 2017, 40, 2006–2016. [Google Scholar] [CrossRef]
- Yimin, W.; Hong, L.; Mingquan, L. Spoofing profile estimation-based GNSS spoofing identification method for tightly coupled. MEMS INS/GNSS integrated navigation system. IET Radar Sonar Navig. 2019, 14, 216–225. [Google Scholar] [CrossRef]
- Broumandan, A.; Lachapelle, G. Spoofing Detection Using GNSS/INS/Odometer Coupling for Vehicular Navigation. Sensors 2018, 18, 1305. [Google Scholar] [CrossRef] [PubMed]
- Qiao, Y.R.; Zhang, Y.X.; Du, X. A Vision-Based GPS-Spoofing Detection Method for Small UAVs. In Proceedings of the 13th International Conference on Computational Intelligence and Security (CIS), Hong Kong, China, 15–17 December 2017; pp. 312–316. [Google Scholar]
- Gu, N.; Xing, F.; You, Z. GNSS Spoofing Detection Based on Coupled Visual/Inertial/GNSS Navigation System. Sensors 2021, 21, 6769. [Google Scholar] [CrossRef] [PubMed]
- Song, J.; Wu, H.; Guo, X.C.; Jiang, D.; Guo, X.Q.; Lv, T.; Luo, H. GNSS Spoofing Identification and Smoothing Localization Method for GNSS/Visual SLAM System. Appl. Sci. 2022, 12, 1386. [Google Scholar] [CrossRef]
- Geiger, A.; Lenz, P.; Urtasun, R. Are we ready for autonomous driving? The kitti vision benchmark suite. In Proceedings of the IEEE International Conference on Pattern Recognition, Tsukuba, Japan, 11–15 November 2012; pp. 3354–3361. [Google Scholar]
- Hong, E.; Lim, J. Visual-Inertial Odometry with Robust Initialization and Online Scale Estimation. Sensors 2018, 18, 4287. [Google Scholar] [CrossRef]
- Surber, J.; Teixeira, L.; Chli, M. Robust Visual-Inertial Localization with Weak GPS Priors for Repetitive UAV Flights. In Proceedings of the IEEE International Conference on Robotics and Automation (ICRA), Singapore, 29 May–3 June 2017; pp. 6300–6306. [Google Scholar]
- Oleynikova, H.; Burri, M.; Lynen, S.; Siegwart, R. Real-time visual-inertial localization for aerial and ground robots. In Proceedings of the IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Macau, China, 4–8 November 2015; pp. 3079–3085. [Google Scholar]
- Qin, T.; Li, P.; Shen, S. VINS-Mono: A Robust and Versatile Monocular Visual-Inertial State Estimator. IEEE Trans. Robot. 2018, 34, 1004–1020. [Google Scholar] [CrossRef]
- Campos, C.; Elvira, R.; Rodríguez, J.J.G.; Montiel, J.M.M.; Tardós, J.D. ORB-SLAM3: An Accurate Open-Source Library for Visual, Visual–Inertial, and Multimap SLAM. IEEE Trans. Robot. 2021, 37, 1874–1890. [Google Scholar] [CrossRef]
- Mur-Artal, R.; Montiel, J.M.M.; Tardós, J.D. ORB-SLAM: A Versatile and Accurate Monocular SLAM System. IEEE Trans. Robot. 2015, 31, 1147–1163. [Google Scholar] [CrossRef]
- Mur-Artal, R.; Tardós, J.D. Orb-slam2: An open-source slam system for monocular, stereo, and rgb-d cameras. IEEE Trans. Robot. 2017, 33, 1255–1262. [Google Scholar] [CrossRef]
- Dai, B.; He, Y.; Yang, L.; Su, Y.; Yue, Y.; Xu, W. SIMSF: A Scale Insensitive Multi-Sensor Fusion Framework for Unmanned Aerial Vehicles Based on Graph Optimization. IEEE Access 2020, 8, 118273–118284. [Google Scholar] [CrossRef]
- Agarwal, S.; Mierle, K.; The Ceres Solver Team. Ceres Solver. Available online: http://ceres-solver.org (accessed on 20 November 2022).
- Galvez-López, D.; Tardos, J.D. Bags of Binary Words for Fast Place Recognition in Image Sequences. IEEE Trans. Robot. 2012, 28, 1188–1197. [Google Scholar] [CrossRef]
- Rosten, E.; Drummond, T. Machine learning for high-speed corner detection. In Proceedings of the European Conference on Computer Vision, Graz, Austria, 7–13 May 2006; Volume 1, pp. 430–443. [Google Scholar]
- Calonder, M.; Lepetit, V.; Strecha, C.; Fua, P. BRIEF: Binary Robust Independent Elementary Features. In Proceedings of the European Conference on Computer Vision, Crete, Greece, 5–11 September 2010; Volume 6314, pp. 778–792. [Google Scholar]
- Arthur, D.; Vassilvitskii, S. K-means++: The advantages of careful seeding. In Proceedings of the ACM-SIAM Symposium on Discrete Algorithms, New Orleans, LA, USA, 7–9 January 2007; pp. 1027–1035. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).