CGAN BeiDou Satellite Short-Message-Encryption Scheme Using Ship PVT
Abstract
:1. Introduction
- To ensure the security of the BeiDou PVT (position, speed, and time) information used to generate the key, the user PVT information is analyzed under various BeiDou commands, and the BeiDou short-message communication channel for transmitting PVT information is encrypted and decrypted using a CGAN (conditional generative adversarial network).
- To improve the decryption success rate of the BeiDou PVT-key at the receiver, the dynamic region of ship PVT information is analyzed, the concept of a dynamic tolerance region is introduced into the encryption scheme; a complete BeiDou short-message encryption scheme is established.
- The security of PVT encryption based on the CGAN model and the influence of the dynamic tolerance region on the success rate of decryption are verified using simulation and experiments, and a host computer interface is designed to verify the engineering-application value of our scheme.
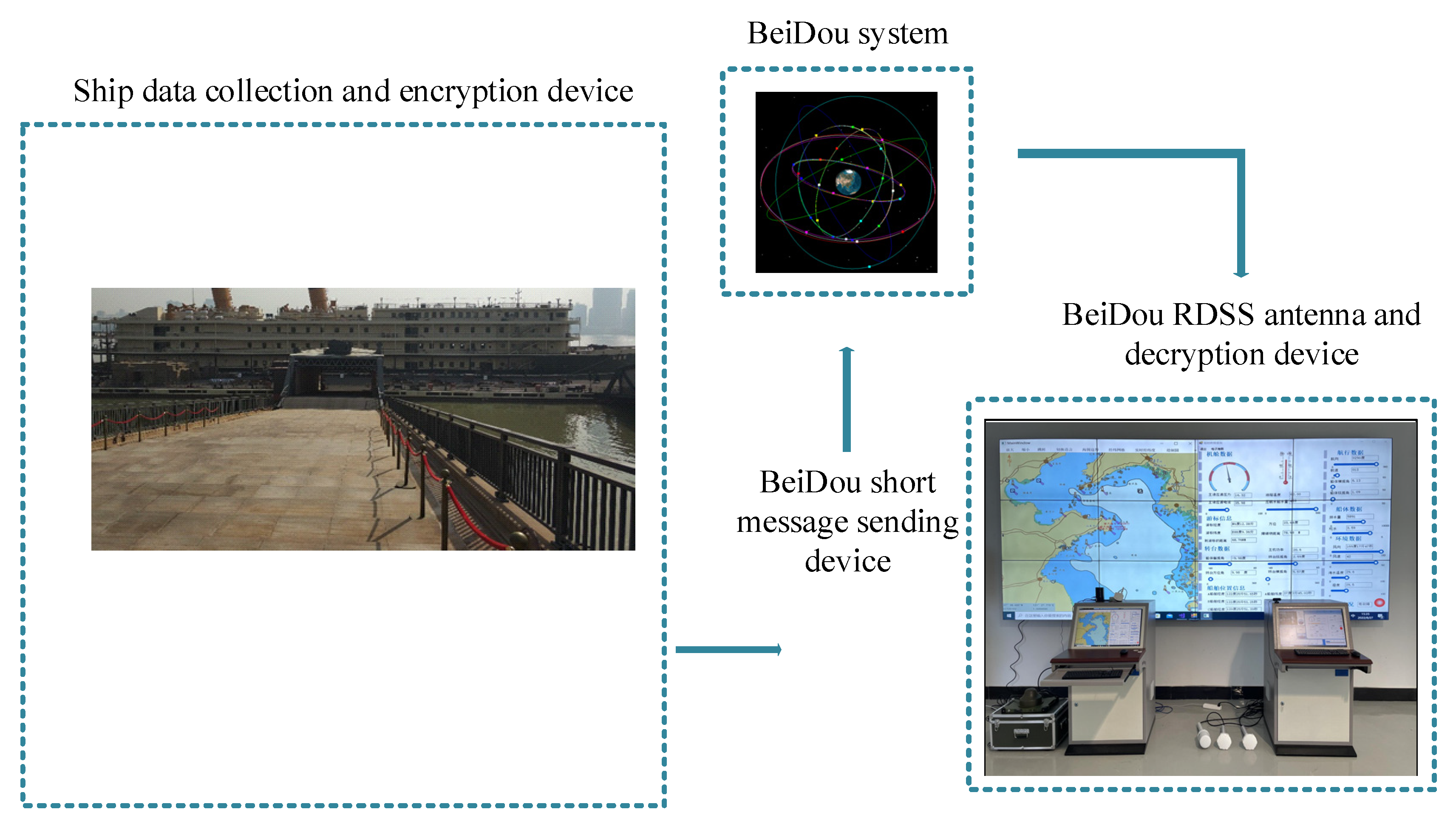
2. The Design of Our Proposed BeiDou Satellite Short-Message Encryption Scheme
2.1. Theoretical Principles
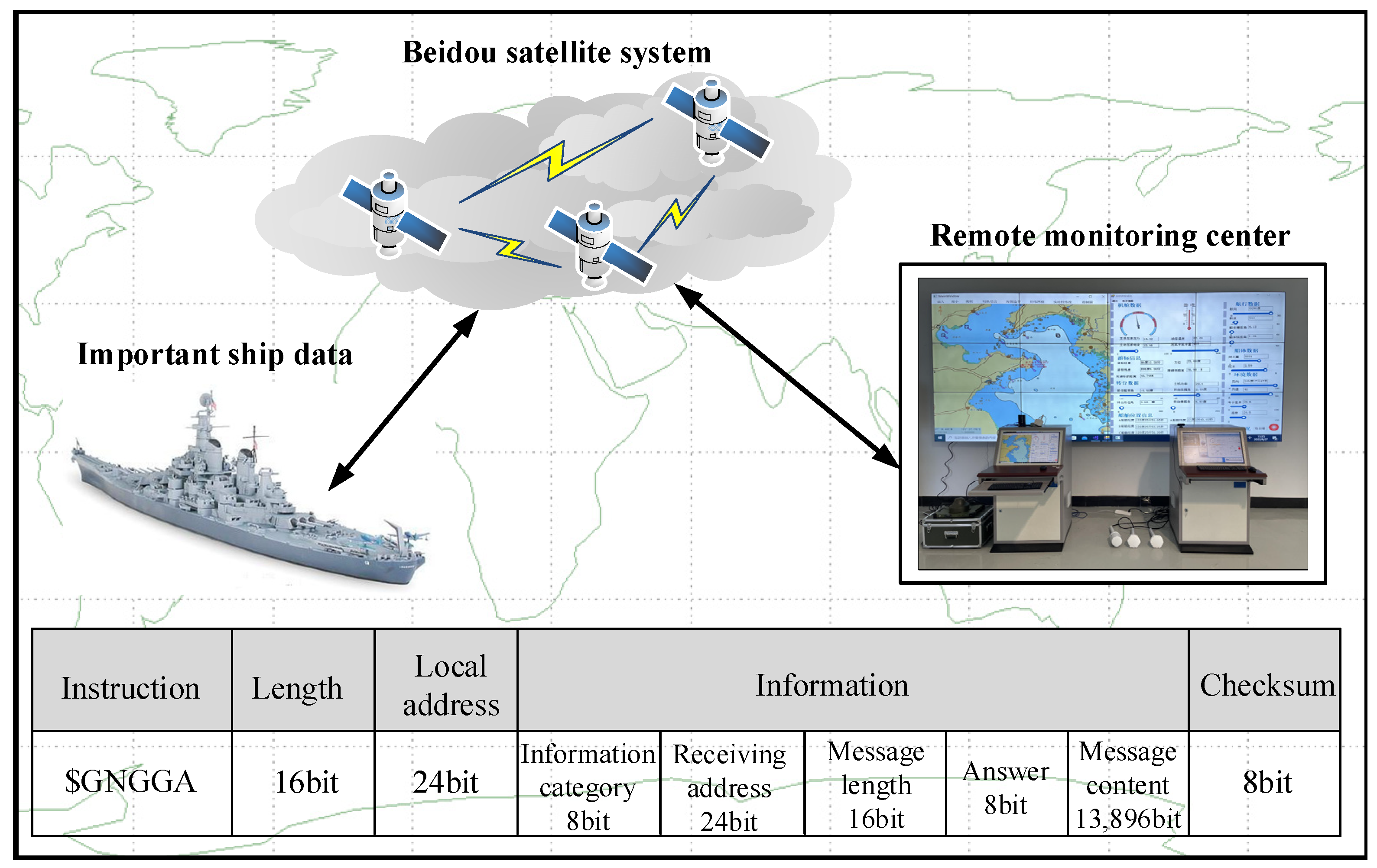
- BeiDou satellite-information transmission mechanism
- 2.
- The relevant theory of the GAN network
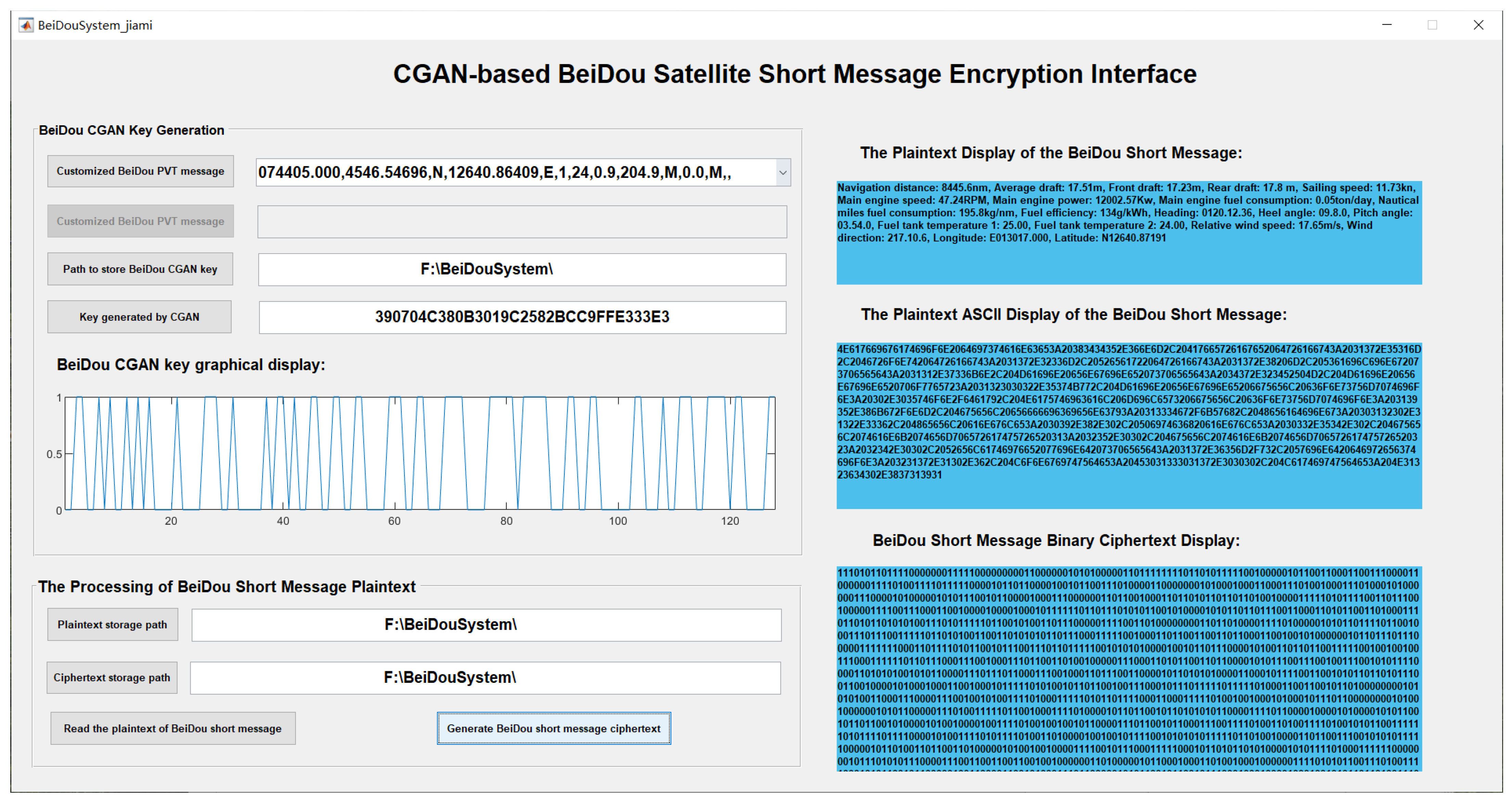
2.2. BeiDou PVT-Key-Generation Based on a CGAN
2.3. Design of the Dynamic Tolerance Region
3. Results and Discussion
3.1. Simulation and Analysis
3.2. Experimental Verification of BeiDou Short-Message Encryption/Decryption
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ji, S.Y.; Weng, D.J.; Ji, S.Y.; Wang, Z.J.; Chen, W.; Lu, Y.W. Ocean Real-Time Precise Point Positioning with the BeiDou Short-Message Service. Remote Sens. 2020, 12, 4167. [Google Scholar]
- Li, X.J.; Guo, R.; Chen, J.B.; Liu, S.; Chang, Z.Q.; Xin, J.; Guo, J.L.; Tian, Y.J. New Orbit Determination Method for GEO Satellites Based on BeiDou Short-Message Communication Ranging. Remote Sens. 2022, 14, 4602. [Google Scholar] [CrossRef]
- Zhang, P.F.; Tu, R.; Zhang, R.; Gao, Y.P.; Cai, H.B. Combining GPS, BeiDou, and Galileo Satellite Systems for Time and Frequency Transfer Based on Carrier Phase Observations. Remote Sens. 2018, 10, 324. [Google Scholar] [CrossRef] [Green Version]
- Dong, Y.H.; Zhao, G.; Ma, Y.J.; Pan, Z.; Wu, R. A novel image encryption scheme based on pseudo-random coupled map lattices with hybrid elementary cellular automata. Inf. Sci. 2022, 593, 121–154. [Google Scholar] [CrossRef]
- Sathiyamurthi, P.; Ramakrishnan, S. Speech encryption using hybrid-hyper chaotic system and binary masking technique. Multimed. Tools Appl. 2022, 81, 6331–6349. [Google Scholar] [CrossRef]
- Zhang, X.Q.; Gong, Z.J. Color image encryption algorithm based on 3D Zigzag transformation and view planes. Multimed. Tools Appl. 2022, 81, 31753–31785. [Google Scholar] [CrossRef]
- Wang, X.Y.; Liu, P.B. A New Full Chaos Coupled Mapping Lattice and Its Application in Privacy Image Encryption. IEEE Trans. Circuits Syst. I-Regul. Pap. 2022, 69, 1291–1301. [Google Scholar] [CrossRef]
- Ding, D.W.; Xiao, H.; Yang, Z.L. Coexisting multi-stability of Hopfield neural network based on coupled fractional-order locally active memristor and its application in image encryption. Nonlinear Dyn. 2022, 108, 4433–4458. [Google Scholar] [CrossRef]
- Lai, Q.; Wan, Z.Q.; Zhang, H.; Chen, G.R. Design and Analysis of Multiscroll Memristive Hopfield Neural Network with Adjustable Memductance and Application to Image Encryption. IEEE Trans. Neural Netw. Learn. Syst. 2022, 1–14. [Google Scholar] [CrossRef]
- Zhang, X.Q.; Tian, J.X. Fast DNA encoding algorithm inspired by the SPOOLing system. Med. Biol. Eng. Comput. 2022, 60, 2707–2720. [Google Scholar] [CrossRef]
- Bo, J.; Bi, X.R.; Tian, Y.L.; Liu, X.M.; Wu, D.P. Toward Lightweight, Privacy-Preserving Cooperative Object Classification for Connected Autonomous Vehicles. IEEE Internet Things J. 2022, 9, 2787–2801. [Google Scholar]
- Kathamuthu, N.D.; Chinnamuthu, A.; Iruthayanathan, N.; Ramachandran, M.; Gandomi, A.H. Deep Q-Learning-Based Neural Network with Privacy Preservation Method for Secure Data Transmission in Internet of Things (IoT) Healthcare Application. Electronics 2022, 11, 157. [Google Scholar] [CrossRef]
- Zhang, Q.; Xin, C.S.; Wu, H.Y. SecureTrain: An Approximation-Free and Computationally Efficient Framework for Privacy-Preserved Neural Network Training. IEEE Trans. Netw. Sci. Eng. 2022, 9, 187–202. [Google Scholar] [CrossRef]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M. Generative Adversarial Nets. Commun. ACM 2014, 27, 2672–2680. [Google Scholar]
- Awan, S.E.; Bennamoun, M.; Sohel, F.; Sanfilippo, F.; Dwivedi, G. Imputation of missing data with class imbalance using conditional generative adversarial networks. Neuromputing 2021, 453, 164–171. [Google Scholar] [CrossRef]
- Zhang, W.J.; Luo, Y.H.; Zhang, Y.; Srinivasan, D. SolarGAN: Multivariate Solar Data Imputation Using Generative Adversarial Network. IEEE Trans. Sustain. Energy 2021, 12, 743–746. [Google Scholar] [CrossRef]
- Otberdout, N.; Daoudi, M.; Kacem, A.; Ballihi, L.; Berretti, S. Dynamic Facial Expression Generation on Hilbert Hypersphere with Conditional Wasserstein Generative Adversarial Nets. IEEE Trans. Pattern Mach. Intell. 2022, 44, 848–863. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.F.; Li, D.; Li, X.; Yang, M. PC-GAIN: Pseudo-label conditional generative adversarial imputation networks for incomplete data. Neural Netw. 2021, 141, 395–403. [Google Scholar] [CrossRef]
- Coutinho, M.; Albuquerque, R.D.; Borges, F.; Villalba, L.J.G.; Kim, T.H. Learning Perfectly Secure Cryptography to Protect Communications with Adversarial Neural Cryptography. Sensors 2018, 18, 1306. [Google Scholar] [CrossRef] [Green Version]
- Gomez, A.N.; Huang, S.; Zhang, I. Unsupervised Cipher Cracking Using Discrete GANs. arXiv 2018, arXiv:1801.04883. [Google Scholar]
- Chen, S.S.; Chang, C.C.; Echizen, I. Steganographic Secret Sharing With GAN-Based Face Synthesis and Morphing for Trustworthy Authentication in IoT. IEEE Acccess 2021, 9, 116427–116439. [Google Scholar] [CrossRef]
- Wu, Z.J.; Liu, R.S.; Cao, H.J. ECDSA-Based Message Authentication Scheme for BeiDou-II Navigation Satellite System. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 1666–1682. [Google Scholar] [CrossRef]
- Yan, Q.Y.; Li, W.; Zhang, J. Real-Time Air-to-Ground Data Communication Technology of Aeroengine Health Management System with Adaptive Rate in the Whole Airspace. Math. Probl. Eng. 2021, 201, 9912574. [Google Scholar] [CrossRef]
- Deng, L.Q.; Ye, S.P.; Qiu, H.Y. Transmission Security Platform for Transportation Information based on BeiDou Navigation Satellite System. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 October 2018; pp. 2110–2113. [Google Scholar]
- Huang, A.B.; Liu, Y.; Chen, T.Z. StarFL: Hybrid Federated Learning Architecture for Smart Urban Computing. ACM Trans. Intell. Syst. Technol. 2021, 12, 1–23. [Google Scholar] [CrossRef]
- He, W.X.; Cong, L.H. Intelligent security system based on location information. In Proceedings of the 2020 5th International Conference on Mechanical, Control and Computer Engineering (ICMCCE), Harbin, China, 25–27 December 2020; pp. 981–985. [Google Scholar]
- Wu, D.; Liu, S.; Sun, H.F. Short Message Communication Lossy Data Compression Algorithm for BeiDou-3 Satellites Information Transmission. Multimed. Tools Appl. 2022, 81, 12833–12855. [Google Scholar] [CrossRef]
- Liu, S.; Wu, D.; Sun, H.F. A Novel BeiDou Satellite Transmission Framework with Missing Package Imputation Applied to Smart Ships. IEEE Sens. J. 2022, 22, 13162–13176. [Google Scholar] [CrossRef]
- Scott, L.; Denning, D. Geo-encryption: Using GPS to Enhance Data Security. GPS World 2013, 14, 40–46. [Google Scholar]
- Al-Fuqaha, A.; Al-Ibrahim, O. Geo-encryption protocol for mobile networks. Comput. Commun. 2007, 30, 2510–2517. [Google Scholar] [CrossRef]














| Key Length | Number of Test Networks | Number of Successful Encryptions | Encryption Success Rate | |
|---|---|---|---|---|
| 1 | 16 bit | 50 | 50 | 100% |
| 2 | 32 bit | 50 | 50 | 100% |
| 3 | 64 bit | 50 | 50 | 100% |
| Algorithms | Data Size (MB) | Encryption Time (s) | Average Speed (MB/s) | |
|---|---|---|---|---|
| 1 | DES | 1024 | 42 | 24.38 |
| 2 | AES | 1024 | 20 | 51.20 |
| 3 | GAN-AES | 1024 | 28 | 36.57 |
| 4 | CGAN-AES | 1024 | 24 | 42.67 |
| Simulation Experiments | Simulation-Experiment Results |
|---|---|
| The specified latitude and longitude | Longitude: 120.020866 Latitude: 35.816002 |
| The actual latitude and longitude | Longitude: 120.020866 Latitude: 35.816012 |
| Dynamic tolerance parameters | 50,50 |
| A key generated based on CGAN | 1B0313952878650D0AC95B4EA5476AB5 |
| BeiDou satellite plaintext | Ship remote support |
| BeiDou satellite ciphertext | 0010011001100011111011111010000111110000000010100000100001 11010101110011110011111000000000000101111 |
| The decrypted BeiDou plaintext | Ship remote support |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, S.; Wu, D.; Zhang, L. CGAN BeiDou Satellite Short-Message-Encryption Scheme Using Ship PVT. Remote Sens. 2023, 15, 171. https://doi.org/10.3390/rs15010171
Liu S, Wu D, Zhang L. CGAN BeiDou Satellite Short-Message-Encryption Scheme Using Ship PVT. Remote Sensing. 2023; 15(1):171. https://doi.org/10.3390/rs15010171
Chicago/Turabian StyleLiu, Sheng, Di Wu, and Lanyong Zhang. 2023. "CGAN BeiDou Satellite Short-Message-Encryption Scheme Using Ship PVT" Remote Sensing 15, no. 1: 171. https://doi.org/10.3390/rs15010171
APA StyleLiu, S., Wu, D., & Zhang, L. (2023). CGAN BeiDou Satellite Short-Message-Encryption Scheme Using Ship PVT. Remote Sensing, 15(1), 171. https://doi.org/10.3390/rs15010171





