Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS
Abstract
:1. Introduction
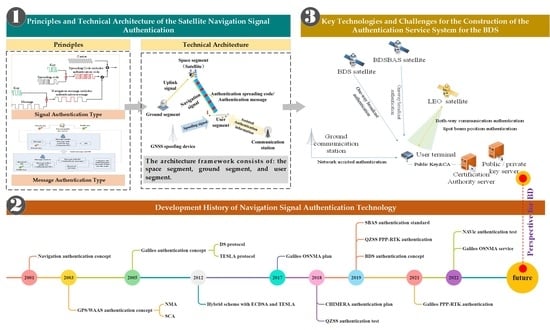
2. Principles and Technical Architecture of the Satellite Navigation Signal Authentication
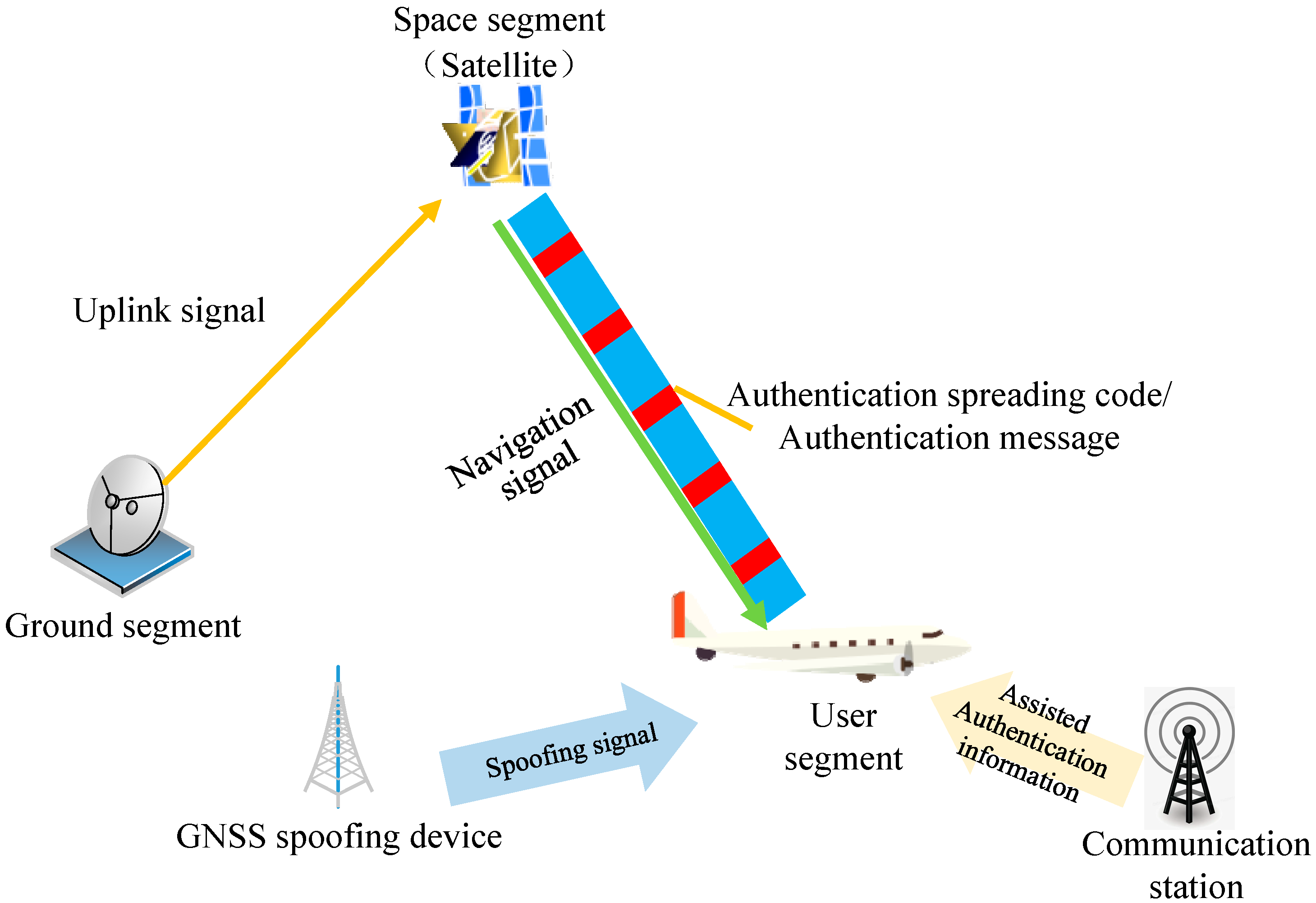
2.1. Principles
- (1)
- One-way broadcast.
- (2)
- Signal disclosure transmission.
- (3)
- Compatible with existing signal structure.
2.1.1. Satellite Navigation Signal Authentication Type
- (1)
- NMA
- (2)
- SCA
2.1.2. Satellite Navigation Message Authentication Type
2.2. Technical Architecture
2.3. Incremental Capability
- (1)
- Anti-spoofing method
- (2)
- Anti-spoofing capability
3. Development History of Navigation Signal Authentication Technology
3.1. Concept
3.2. Technical Research
- GNSS
- SBAS
- High-Precision Augmentation System
3.3. Technical Trials and On-Orbit Tests
- Galileo
- GPS
- QZSS
- NavIC
4. Key Technologies and Challenges for the Construction of the Authentication Service System for the BDS
4.1. Authentication Architecture for BDS
4.2. Security
- (1)
- Cryptographic Algorithm Security
- (2)
- Authentication Protocol Security
4.3. Design and Analysis of a Public Key Infrastructure for BDS Data Authentication Key Management
- (1)
- Three-level key management based on a Merkle tree.
- (2)
- Second-level key management based on ECDSA.
- (3)
- Three-level key management based on TESLA.
4.4. Authentication Mechanism
- (1)
- Navigation message authentication.
- BDS
- BDSBAS
- (2)
- Spreading Code Authentication.
4.5. Authentication Performance Evaluation
- (1)
- Security.
- (2)
- Robustness.
- (3)
- Authentication.
- (4)
- Other indicators.
4.6. Terminal Processing
- (1)
- Message Authentication Processing.
- (2)
- Spreading Code Authentication Processing.
5. Conclusions
- (1)
- Navigation signal authentication technology is a method used to improve the anti-spoofing ability of the GNSS on the system-side, which can solve the generated spoofing.
- (2)
- In the future, authentication services will become the GNSS standard to improve the credible service capabilities of the GNSS.
- (3)
- For the construction of the next-generation BDS, this paper designs a Beidou authentication service system integrating high, medium, and low constellations; standard positioning and augmentation services; and navigation and communication. It involves system security, key management, authentication mechanism, authentication performance evaluation and terminal processing.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- EUSPA EO and GNSS Market Report 2022. Available online: https://www.euspa.europa.eu/euspa-market-report-2022-0 (accessed on 1 December 2022).
- Humphreys, T.E.; Ledvina, B.M.; Psiaki, M.L.; O’Hanlon, B.W.; Kintner, P.M., Jr. Assessing the spoofing threat: Development of a portable GPS civilian spoofer. In Proceedings of the 21st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS 2008), Savannah, GA, USA, 16–19 September 2008; pp. 2314–2325. [Google Scholar]
- Bhatti, J.; Humphreys, T.E. Hostile Control of Ships via False GPS Signals: Demonstration and Detection. Navigation 2017, 64, 51–66. [Google Scholar] [CrossRef]
- Wang, K.; Chen, S.; Pan, A. Time and Position Spoofing with Open Source Projects. In Proceedings of the Black Hat Europe 2015, Amsterdam, The Netherlands, 10–13 November 2015. [Google Scholar]
- Moafipoor, S.; Bock, L.; Fayman, J.A. Resilient Sensor Management for Dismounted Assured-PNT. In Proceedings of the 2020 International Technical Meeting of the Institute of Navigation, San Diego, CA, USA, 21–24 January 2020; pp. 1135–1147. [Google Scholar]
- Khanafseh, S.; Roshan, N.; Langel, S.; Chan, F.-C.; Joerger, M.; Pervan, B. GPS spoofing detection using RAIM with INS coupling. In Proceedings of the Position, Location and Navigation Symposium-PLANS, Monterey, CA, USA, 5–8 May 2014; pp. 1232–1239. [Google Scholar]
- Yang, Q.; Zhang, Y.; Tang, C.K. A combined antijamming and antispoofing algorithm for GPS Arrays. Int. J. Antennas Propag. 2019, 2019, 8012569. [Google Scholar] [CrossRef]
- Lee, Y.S.; Yeom, J.S.; Noh, J.H.; Lee, S.J.; Jung, B.C. A novel GNSS spoofing detection technique with array antenna-based multi-PRN diversity. J. Position. Navig. Timing 2021, 10, 169–177. [Google Scholar]
- de Castro, H.V.; van der Maarel, G.; Safipour, E. The possibility and added-value of authentication in future Galileo open signal. In Proceedings of the 23th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION 2010), Portland, OR, USA, 21–24 September 2010. [Google Scholar]
- Fernandez-Hernandez, I.; Rijmen, V.; Seco-Granados, G.; Simón, J.; Rodríguez, I. Design Drivers, Solutions and Robustness Assessment of Navigation Message Authentication for the Galileo Open Service. In Proceedings of the 27th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2014), Tampa, FL, USA, 8–12 September 2014; pp. 2810–2827. [Google Scholar]
- Walker, P.; Rijmen, V.; Fernandez-Hernandez, I.; Bogaardt, L.; Seco-Granados, G.; Simón, J.; Calle, D.; Pozzobon, O. Galileo Open Service Authentication: A Complete Service Design and Provision Analysis. In Proceedings of the 28th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2015), Tampa, FL, USA, 14–18 September 2015; pp. 3383–3396. [Google Scholar]
- Fernandez-Hernandez, I.; Rijmen, V.; Seco-Granados, G.; Simon, J.; Rodríguez, I.; David Calle, J. A Navigation Message Authentication Proposal for the Galileo Open Service. Navig. J. Inst. Navig. 2016, 63, 85–102. [Google Scholar] [CrossRef]
- Nicola, M.; Motella, B.; Pini, M.; Falletti, E. Galileo OSNMA Public Observation Phase: Signal Testing and Validation. IEEE Access 2022, 10, 27960–27969. [Google Scholar] [CrossRef]
- Manandhar, D.; Shibasaki, R. Authenticating GALILEO Open Signal using QZSS Signal. In Proceedings of the 31st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2018), Miami, FL, USA, 24–28 September 2018; pp. 3995–4003. [Google Scholar]
- Pravin, P. Navigation Message Authentication (NMA) for NavIC SPS; ICG-16: Abu Dhabi, United Arab Emirates, 2022. [Google Scholar]
- Anderson, J.M.; Carroll, K.L.; DeVilbiss, N.P.; Gillis, J.T.; Hinks, J.C.; O’Hanlon, B.W.; Rushanan, J.J.; Scott, L.; Yazdi, R.A. Chips-Message Robust Authentication (CHIMERA) for GPS Civilian Signals. In Proceedings of the 31th International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS + 2018, Portland, OR, USA, 25–29 September 2018. [Google Scholar]
- Margaria, D.; Motella, B.; Anghileri, M.; Floch, J.-J.; FernandezHernandez, I.; Paonni, M. Signal structure-based authentication for civil GNSSs: Recent solutions and perspectives. IEEE Signal Process. Mag. 2017, 34, 27–37. [Google Scholar] [CrossRef]
- Fernández-Hernández, I.; Walter, T.; Neish, A.M.; Anderson, J.; Mabilleau, M.; Vecchione, G.; Châtre, E. SBAS message authentication: A review of protocols, figures of merit and standardization plans. In Proceedings of the 2021 International Technical Meeting of the Institute of Navigation, Auditorium UPC, Barcelona, Spain, 25–28 January 2021; pp. 111–124. [Google Scholar]
- Cai, H.; Meng, Y.; Geng, C.; Gao, W.; Zhang, T.; Li, G.; Shao, B.; Xin, J.; Lu, H.; Mao, Y.; et al. BDS-3 performance assessment: PNT, SBAS, PPP, SMC and SAR. Acta Geod. Et Cartogr. Sin. 2021, 50, 427–435. [Google Scholar]
- The State Council Information Office of the People’s Republic of China. 2022. Available online: http://www.scio.gov.cn/zfbps/32832/Document/1732789/1732789.htm (accessed on 4 November 2022).
- Fernandez-Hernandez, I. Snapshot and Authentication Techniques for Satellite Navigation; Aalborg University: Aalborg, Denmark, 2015. [Google Scholar]
- Curran, J.T.; Paonni, M. Securing GNSS: An End-to-end Feasibility Analysis for the Galileo Open-service. In Proceedings of the 27th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2014), Tampa, FL, USA, 8–12 September 2014; pp. 2828–2842. [Google Scholar]
- Gkougkas, E.; Pany, T.; Eissfeller, B. Sensitivity Analysis of Potential Future Authentication Components for Open Service GNSS Signals. In Proceedings of the 31st International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS + 2018), Miami, FL, USA, 24–28 September 2018. [Google Scholar]
- Shen, C.; Guo, C. Study and Evaluation of GNSS Signal Cryptographic Authentication Defenses. GNSS World China 2018, 43, 7–12. [Google Scholar]
- European Union. GALILEO Open Service Navigation Message Authentication (OSNMA) Receiver Guidelines for the Test Phase; European Union Issue 1.0; European Union: Luxembourg, 2021. [Google Scholar]
- Air Force Research Laboratory Space Vehicles Directorate Advanced GPS Technology. Chips Message Robust Authentication (Chimera) Enhancement for the L1C Signal: Space Segment/User Segment Interface. 16 April 2019. CHAPMAN D C. Chips Message Robust Authentication (Chimera) Enhancement for the L1C Signal: Space Seg-ment/User Segment Interface (IS-AGT-100)[R]: Advanced GPS Technologies Program. 2019.
- Hiroshi, Y. Angō Gijutsu Nyūmon, 3rd ed.; Post & Telecom Press: Beijing, China, 2016. (In Chinese) [Google Scholar]
- Neish, A.; Walter, T.; Powell, J.D. SBAS data authentication: A concept of operations. In Proceedings of the 32nd International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2019), Miami, FL, USA, 16–20 September 2019; pp. 1812–1823. [Google Scholar]
- Neish, A.; Walter, T.; Enge, P. Parameter selection for the TESLA keychain. In Proceedings of the 31st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2018), Miami, FL, USA, 24–28 September 2018; pp. 2155–2171. [Google Scholar]
- Perrig, A.; Canetti, R.; Tygar, J.D. Efficient authentication and signing of multicast streams over lossy channels. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 56–73. [Google Scholar]
- Caparra, G.; Sturaro, S.; Laurenti, N.; Wullems, C. Evaluating the Security of One-Way Key Chains in TESLA-Based GNSS Navigation Message Authentication Schemes. In Proceedings of the 2016 International Conference on Localization and GNSS (ICL-GNSS), Barcelona, Spain, 28–30 June 2016; pp. 1–6. [Google Scholar]
- Zhao, X.; Liu, C. GPS Military Signal Security Protection and Password Management. Mod. Navig. 2020, 11, 14–19. [Google Scholar]
- Li, J.Z.; Zhu, X.W.; Ouyang, M.J.; Li, W.Q.; Chen, Z.K.; Dai, Z.Q. Research on multi-peak detection of small delay spoofing signal. IEEE Access 2020, 8, 151777–151787. [Google Scholar] [CrossRef]
- Khan, A.M.; Ahmad, A. Global navigation satellite systems spoofing detection through measured autocorrelation function shape distortion. Int. J. Satell. Commun. Netw. 2022, 40, 148–156. [Google Scholar] [CrossRef]
- Dehghanian, V.; Nielsen, J.; Lachapelle, G. GNSS spoofing detection based on receiver C/N0 estimates. In Proceedings of the International Technical Meeting of the Satellite Division of the Institute of Navigation, Nashville, TN, USA, 17–21 September 2012; pp. 2875–2884. [Google Scholar]
- Elezi, E.; Cankaya, G.; Boyaci, A.; Yarkan, S. A detection and identification method based on signal power for different types of electronic jamming attacks on GPS signals. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–5. [Google Scholar]
- He, L.; Li, H.; Lu, M.Q. Global navigation satellite system spoofing detection technique based on the doppler ripple caused by vertical reciprocating motion. IET Radar Sonar Navig. 2019, 13, 1655–1664. [Google Scholar]
- He, L.; Li, H.; Lu, M.Q. Dual-antenna GNSS spoofing detection method based on doppler frequency difference of arrival. GPS Solut. 2019, 23, 1–14. [Google Scholar] [CrossRef]
- Bian, S.; Hu, Y.; Ji, B. Research status and prospect of GNSS anti-spoofing technology. Sci. Sin. Inf. 2017, 47, 275–287. [Google Scholar] [CrossRef] [Green Version]
- Zhao, X.; Chen, X.; Guo, X. A Repeater Spoofing Method for GNSS Clock of receiver. Telecommun. Eng. 2020, 60, 1415–1419. [Google Scholar]
- Arizabaleta, M.; Gkougkas, E.; Pany, T. A Feasibility Study and Risk Assessment of Security Code Estimation and Replay (SCER) Attacks. In Proceedings of the 32nd International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2019), Miami, FL, USA, 16–20 September 2019. [Google Scholar]
- Volpe, J.A. Vulnerability Assessment of the Transportation Infrastructure Relying on the Global Positioning System. National Transportation System Center: Washington, DC, USA, 2001. [Google Scholar]
- Scott, L.D. Anti-Spoofing & Authenticated Signal Architectures for Civil Navigation Systems. In Proceedings of the 16th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GPS/GNSS 2003), Portland, OR, USA, 9–12 September 2003; pp. 1543–1552. [Google Scholar]
- Pozzobon, O.; Wullems, C.; Kubik, K. Secure Tracking using Trusted GNSS Receivers and Galileo Authentication Services. J. Glob. Position. Syst. 2004, 3, 200–207. [Google Scholar] [CrossRef] [Green Version]
- Wullems, C.; Pozzobon, O.; Kubik, K. Signal authentication and integrity schemes for next generation global navigation satellite systems. In Proceedings of the European Navigation Conference (ENC-GNSS 2005), Munich, Germany, 19–22 July 2005. [Google Scholar]
- Kuhn, M.G. An Asymmetric Security Mechanism for Navigation Signals. In Proceedings of the Information Hiding: 6th International Workshop, IH 2004, Toronto, ON, Canada, 23–25 May 2004. [Google Scholar]
- Wesson, K.; Rothlisberger, M.; Humphreys, T. Practical cryptographic civil GPS signal authentication. Navigation 2012, 59, 177–193. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, Y.; Liu, R. BD-II NMA&SSI: An Scheme of Anti-Spoofing and Open BeiDou II D2 Navigation Message Authentication. IEEE Access 2020, 8, 23759–23775. [Google Scholar]
- Yuan, M.; Lv, Z.; Chen, H.; Li, J.; Ou, G. An Implementation of Navigation Message Authentication with Reserved Bits for Civil BDS Anti-Spoofing. In Proceedings of the China Satellite Navigation Conference (CSNC), Shanghai, China, 23–25 May 2017; pp. 69–80. [Google Scholar]
- Wang, S.; Liu, H.; Tang, Z.; Ye, B. Binary phase hopping based spreading code authentication technique. Satell. Navig. 2021, 2, 4. [Google Scholar] [CrossRef]
- Yan, T.; Li, T.; Tian, Y.; Wang, Y.; Bian, L.; Meng, Y. Spreading code authentication method for GNSS signals based on chip-level amplitude modulation. Chin. Space Sci. Technol. 2023, 43, 69–78. [Google Scholar]
- Chiara, A.D.; Broi, G.D.; Pozzobon, O.; Sturaro, S.; Caparra, G.; Laurenti, N.; Fidalgo, J.; Odriozola, M.; Lopez, G.M.; Fernandez-Hernandez, I. SBAS authentication proposals and performance assessment. In Proceedings of the 30th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS + 2017), Portland, OR, USA, 25–29 September 2017; pp. 2106–2116. [Google Scholar]
- Chen, Y.; Gao, W.; Chen, X.; Liu, T.; Liu, C.; Su, C.; Lu, J.; Wang, W.; Mu, S. Advances of SBAS authentication technologies. Satell. Navig. 2021, 2, 12. [Google Scholar] [CrossRef]
- Anderson, J.; Lo, S.; Neish, A.M.; Walter, T. On SBAS Authentication with OTAR Schemes. In Proceedings of the 34th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2021), St. Louis, MO, USA, 20–24 September 2021. [Google Scholar]
- Walter, T.; Anderson, J.H.; Lo, S. SBAS Message Schemes to Support Inline Message Authentication. In Proceedings of the 34th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2021), St. Louis, MO, USA, 20–24 September 2021. [Google Scholar]
- Chen, X.; Tian, X.; Luo, R. Design of message authentication based on TESLA protocol for BDSBAS. J. Beijing Univ. Aeronaut. Astronaut. 2021. [Google Scholar] [CrossRef]
- Mu, S.L.; Chen, Y.; Liu, T.; Liu, C.; Chen, X. Design of message authentication and OTAR broadcast strategy for BDSBAS. J. Beijing Univ. Aeronaut. Astronaut. 2021, 47, 1453–1461. (In Chinese) [Google Scholar]
- Hirokawa, R.; Fujita, S. A Message Authentication Proposal for Satellite Based Nationwide PPP-RTK Correction Service. In Proceedings of the 32nd International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2019), Miami, FL, USA, 16–20 September 2019. [Google Scholar]
- Fernández-Hernández, I.; Hirokawa, R.; Rijmen, V.; Aikawa, Y. PPP/PPP-RTK Message Authentication. In Proceedings of the 34th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2021), St. Louis, MO, USA, 20–24 September 2021. [Google Scholar]
- Cancela, S.; Calle, D.; Arroyo, G. Designing and evaluating next generation of resilience receivers. In Proceedings of the 30th International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS + 2017, Portland, OR, USA, 25–29 September 2017. [Google Scholar]
- European Union. GALILEO Open Service Navigation Message Authentication (OSNMA) User ICD for the Test Phase; European Union Issue 1.0; European Union: Luxembourg, 2021. [Google Scholar]
- European Union. Agency for the Space Programme, GALILEO Open Service Navigation Message Authentication (OSNMA); European Union Issue 1.0; European Union: Luxembourg, 2021. [Google Scholar]
- Fernández-Hernández, I.; Winkel, J.; O’Driscoll, C.; Cancela, S.; Terris-Gallego, R.; López-Salcedo, J.A.; Seco-Granados, G.; Chiara, A.D.; Sarto, C.; Blonski, D.; et al. Semi-Assisted Signal Authentication for Galileo: Proof of Concept and Results. IEEE Trans. Aerosp. Electron. Syst. 2023. [Google Scholar] [CrossRef]
- Hinks, J.; Gillis, J.T.; Shawn, P.L.; Myer, G.; Rushanan, J.J.; Stoyanov, S. Signal and Data Authentication Experiments on NTS-3. In Proceedings of the 34th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS + 2021), St. Louis, MO, USA, 20–24 September 2021; pp. 3621–3641. [Google Scholar]
- NIST. FIPS Pub 186-4: Digital Signature Standard (dss); Technical Report; Digital Signature Standard (DSS); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2013. [Google Scholar]
- NIST. Announcing the Advanced Encryption Standard (aes); FIPS Standard; Federal Information Processing Standards Publication, 2001; Volume 197, pp. 1–51. Available online: https://doi.org/10.6028/NIST.FIPS.197 (accessed on 30 January 2023). [CrossRef]
- General Administration of Quality Supervision, Inspection and Quarantine of the People’s Republic of China, Standardization Administration of the People’s Republic of China, Information Security Techniques. SM2 Elliptic Curve Signature Algorithm, Part 1: General Rules; Standards Press of China: Beijing, China, 2017. [Google Scholar]
- General Administration of Quality Supervision, Inspection and Quarantine of the People’s Republic of China, Standardization Administration of the People’s Republic of China, Information Security Techniques. SM2 Elliptic Curve Signature Algorithm, Part 2: Digital Signature Algorithm; Standards Press of China: Beijing, China, 2017. [Google Scholar]
- General Administration of Quality Supervision, Inspection and Quarantine of the People’s Republic of China, Standardization Administration of the People’s Republic of China, Information Security Techniques. SM3 Cryptographic Hash Algorithm GB/T 32905—2016; Standards Press of China: Beijing, China, 2017. [Google Scholar]
- General Administration of Quality Supervision, Inspection and Quarantine of the People’s Republic of China, Standardization Administration of the People’s Republic of China, Information Security Techniques. SM4 Block Cipher Algorithm GB/T 32907-2016; Standards Press of China: Beijing, China, 2017. [Google Scholar]
- Fernández-Hernández, I.; Ashur, T.; Rijmen, V. Analysis and Recommendations for MAC and Key Lengths in Delayed Disclosure GNSS Authentication Protocols. IEEE Trans. Aerosp. Electron. Syst. 2021, 57, 1827–1839. [Google Scholar] [CrossRef]
- Neish, A.; Walter, T.; Powell, J.D. Design and analysis of a public key infrastructure for SBAS data authentication. Navigation 2019, 66, 831–844. [Google Scholar] [CrossRef]
- BeiDou Navigation Satellite System Signal in Space Interface Control Document Open Service Signal B1C, Version 1. China Satellite Navigation Office: Beijing, China, 2018.
- Jia, X.; Su, R.; Liang, W.; Shen, F.; Zheng, C.; Wang, X.; Xu, L. Research on Civil GNSS Signal Authentication Service Design. In China Satellite Navigation Conference (CSNC 2021) Proceedings, Nanchang, China, 2–25 May 2021; Yang, C., Xie, J., Eds.; Lecture Notes in Electrical Engineering; Springer: Singapore, 2021; Volume 773. [Google Scholar]













| Type | Indicators | Receiver Processing | Feature |
|---|---|---|---|
| NMA [25] | Galileo-OSNMA Time Between Authentication: 10 s | Message bit authentication using Message Authentication Code (MAC) | The project implementation is less difficult, the security level is not as good as SCA, and it can be processed in real time at the terminal. |
| SCA [26] | NTS3-CHIMERA Time Between Authentication for slow channel: 180 s Time Between Authentication for fast channel: 1.5 s or 6 s | Power Domain Authentication Using Sampled Data for Spreading Code Correlation Processing | The pseudorange can be authenticated. The authentication requires data caching, and the project implementation is costly. |
| Protocol | Cryptographic Algorithm | Calculated Amount | Authentication Information Truncation | Key Distribution Requirements | Key Length under the Same Security Level |
|---|---|---|---|---|---|
| TESLA [28,29,30,31] | Hash, HMAC | Small | Yes | Yes | Short |
| DS [18,27] | DS | Big | No | No | Long |
| Anti-Spoofing Method | Description | Effect |
|---|---|---|
| Navigation signal encryption [32] | Encrypted signals serve authorized users, making it difficult for attackers to predict signals | High |
| Navigation signal authentication [17] | It is difficult for spoofed attackers to predict the authentication message/spreading code | High |
| DOA detection based on multi-array antennas [7,8] | The spoofing signal is generally emitted from a single transmitting antenna, and its satellites come from the same direction, while the real satellites of the signal come from different directions | High |
| Multiple correlation peaks [33,34] | The superposition of the spoofed signal and the real signal will bring multiple correlation peaks, and it will also cause distortion of the correlation peaks | Medium |
| Signal power [35,36] | The spoofing signal has more power, and the signal power changes during the spoofing implementation | Medium |
| Doppler consistency [37,38] | It is difficult for spoofing signals to keep the carrier Doppler shift consistent with the pseudocode Doppler shift | Medium |
| Auxiliary information of external sensors [4,5] | Spoofing signals cannot deceive sensors such as inertial navigation, chip-scale atomic clocks, and lidar | High |
| Spoofing | NMA | SCA | |
|---|---|---|---|
| Generated spoofing | Primary generated spoofing (low-cost software radio or commercial signal simulator) | High | High |
| Intermediate generated spoofing (receive GNSS signal first and then generate spoofing signal) | High | High | |
| SCER | Low | High/Medium | |
| Advanced generated spoofing (multiple intermediate generative spoofing) | High/Medium | High | |
| Meaconing | Simple meaconing (same delay for each satellite channel) | Low | Low |
| Multichannel meaconing (the delay of each satellite channel is inconsistent) | Low | Low | |
| System | Service Type | Signal | Authentication Type | Authentication Protocol | Status |
|---|---|---|---|---|---|
| Galileo | Open service [61,62] | E1 | NMA | TESLA | On-orbit testing |
| Authorization service [63] | E6 | SCE + SCA | --- | On-orbit testing | |
| PPP-RTK service [59] | E6 | NMA | TESLA or ECDSA | Simulation verification | |
| GPS | Open service [16,64] | L1C | NMA + SCA | ECDSA | Simulation verification |
| QZSS | Open service [14] | L1 | NMA | ECDSA | On-orbit testing |
| PPP-RTK service [58] | L6 | NMA | TESLA | On-orbit testing | |
| NavIC | Open service [15] | L5, S | NMA | TESLA | On-orbit testing |
| SBAS | Open service [52,53,54,55,56,57] | SBAS-L1 SBAS-L5 | NMA | TESLA | Simulation verification |
| Cryptographic Algorithm | Type | Functional | Quantum Computing Impact |
|---|---|---|---|
| AES, SM4 [66,70] | Symmetric cipher | Encryption and decryption | Need to increase key length |
| SHA-2, SHA-3, SM3 [27,69] | Hash | Hash Function | Need to increase output length |
| RSA, ECDSA, DSA, SM2 [27,65,67,68] | Public key cryptography | Digital signature, key distribution | No longer safe |
| System | Key Length | MAC Length | Keychain Update Cycle | Time Synchronization Requirements |
|---|---|---|---|---|
| Galileo [13] | 128 bits | 40 bits | 168 h (1 week) | ≤30 s |
| SBAS-BigMAC [28] | 30 bits | 115 bits | - | need |
| SBAS-LittleMAC [28] | 30 bits | 15 bit | - | need |
| NavIC [15] | 116 bits | 30 bits | - | ≤48 s |
| System | Key Management | First-Level | Second-Level | Third-Level | Receiver Built-In Key |
|---|---|---|---|---|---|
| Galileo [25,26] | Three-level scheme based on the Merkle tree | Merkle tree root key | TESLA public key | TESLA shared key | Built-in Merkle tree root key |
| SBAS [72] | Second-level scheme based on ECDSA | CA public key | Message authentication public and private key | -- | Built-in CA public key |
| SBAS [72] | Three-level scheme based on TESLA protocol | CA public key | TESLA public key | TESLA shared key | Built-in CA public key |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, X.; Luo, R.; Liu, T.; Yuan, H.; Wu, H. Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS. Remote Sens. 2023, 15, 1462. https://doi.org/10.3390/rs15051462
Chen X, Luo R, Liu T, Yuan H, Wu H. Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS. Remote Sensing. 2023; 15(5):1462. https://doi.org/10.3390/rs15051462
Chicago/Turabian StyleChen, Xiao, Ruidan Luo, Ting Liu, Hong Yuan, and Haitao Wu. 2023. "Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS" Remote Sensing 15, no. 5: 1462. https://doi.org/10.3390/rs15051462
APA StyleChen, X., Luo, R., Liu, T., Yuan, H., & Wu, H. (2023). Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS. Remote Sensing, 15(5), 1462. https://doi.org/10.3390/rs15051462