Invariant-Based Safety Assessment of FPGA Projects: Conception and Technique
Abstract
:1. Introduction
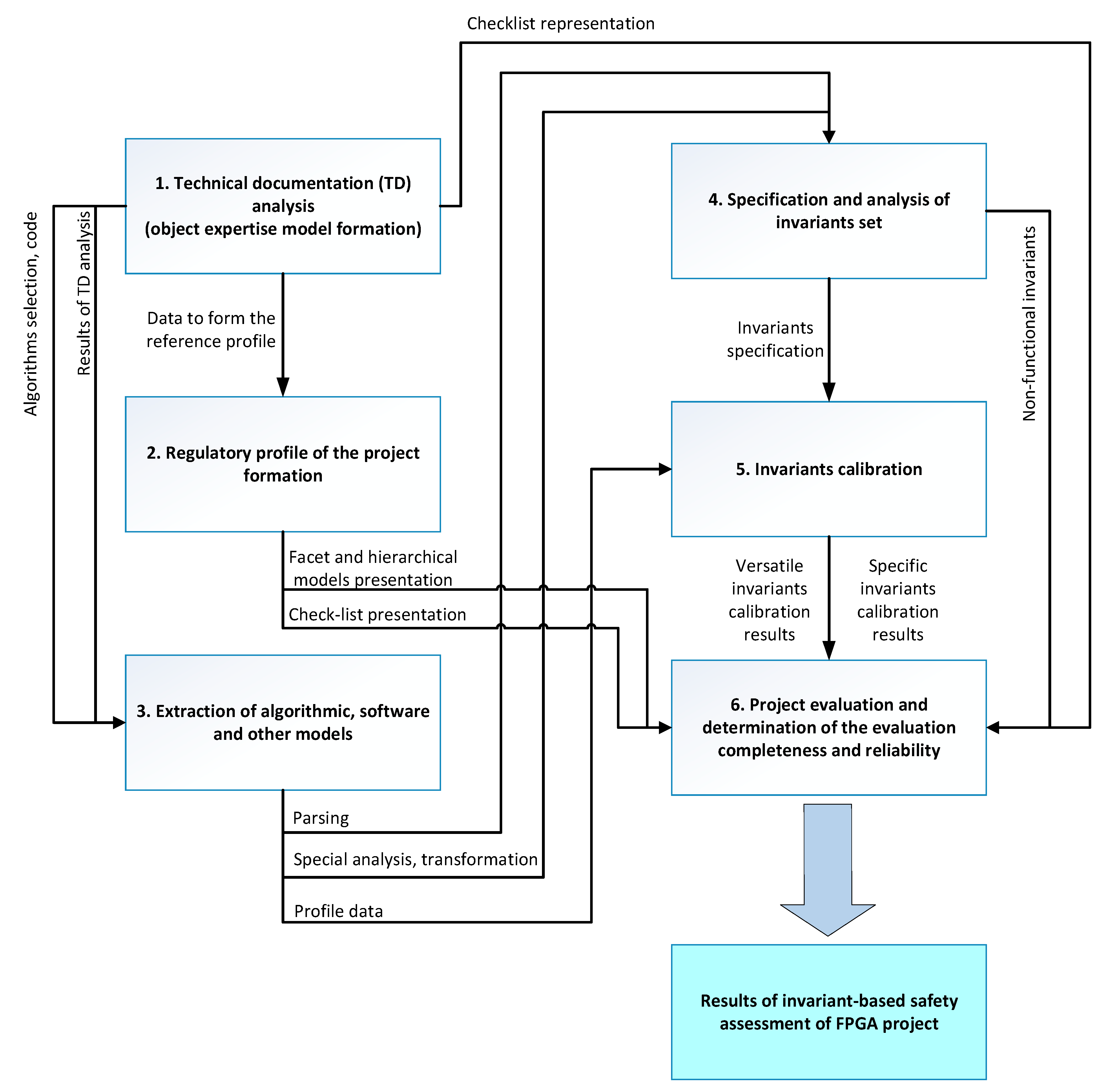
2. Conception and Stages of Invariant-Oriented Assessment of FPGA Projects
2.1. Overall Tasks and Conception Invariant-Oriented Assessment
- analysis of technical documentation and development of a model of the object under assessment (SW and technical documentation) in the FPGA project;
- development of the regulatory profile (set of requirements) of the FPGA-based project based on the purpose and type of system where FPGA is used;
- extraction (development) of algorithmic, software, and other models, which is performed during the analysis of FPGA project documentation;
- specification and analysis of a set of invariants;
- invariant calibration;
- determination of FPGA project assessment reliability and completeness.
- problem statement and description of goal of the current stage;
- description of the solution and implementation of the obtained results;
- input and output data for the particular stage;
- requirements for tools development.
2.2. Analysis of Technical Documentation and Developing the Model of the FPGA Project Assessment
2.3. Formation of the Regulatory Profile of the FPGA Project Based on the Purpose and Type of the System
2.4. Extraction of Algorithmic, Software and Other Models, Carried out According to the Design Documentation Analysis Results
2.5. Specification and Analysis of Set of Invariants
2.6. Invariant Calibration
2.7. Project and Determination of the Trustworthiness Assessment
3. General Requirements of Invariants
4. Classification and Analysis of Invariants
4.1. Classification Attributes
- universality degree—determines the possibility or expediency of using the invariant to test different FPGA projects;
- used model type (for which the invariant is being developed)—the model is the primary basis for invariant development;
- controlled attribute—determined by developing and checking the invariant method;
- type of a particular invariant—determined by the model type (a feature concerning a hierarchy with a previous feature, i.e., dependent on it). Each invariant belongs to a group characterized by a controlled trait;
- calibration method—defines the rules, procedures, and software used to evaluate sensitivity;
- scope—sets the project capacity or indicates the set of its components on which the invariant is used;
- source object for which the invariant is synthesized. This feature depends on the previous feature, the scope of the invariant;
- sensitivity values—determines the set of sensitivity values for the invariant (with a general fixed range of values (0–1));
- rigidity degree—allows invariant differentiation based on the mandatory implementation. It may be in a hierarchical relationship with the previous attribute;
- verification sign—specifies the type of invariant based on its verification features and objectives;
- parameterization ability—determined by the adaptability of the invariant to change depending on the type of project and the requirements for sensitivity.
- Figure 2 shows the structured classification scheme of invariants for FPGA projects.
4.2. Grouping the Invariants
- precision invariants—based on the identification and fixing of restrictions on the system variables (i.e., setting the range of permissible changes);
- semantic invariants—based on the system variables physical dimension invariance determination during their transformations in the process of computing or restrictions on an allowable change in dimension, considering the known laws of physics;
- functional invariants—based on the behavior of the system control. Being in a certain state, getting out of it, and transitions between states when performing different functions;
- logical invariants—based on the start and verification of the fulfillment of the necessary pre- and post-conditions for the occurrence of events, calling procedures or functions.
- conditional (i.e., soft) invariants, which fulfillment is not mandatory. (e.g., they may relate to the style of programming in the VHDL language);
- unconditional (i.e., hard) invariants, which the fulfillment is mandatory from the point of view of safety requirements. Invariants of this type are hierarchically related to the previous taxonomic group. Conditional invariants, as a rule, are a subset of normalized invariants and a scale from 0 to 1 is used to estimate them, and unconditional invariants are a subset of, primarily, binary invariants, and two discrete values 0 and 1 are used to estimate them.
- positive invariants that should always be fulfilled for the entire FPGA project or within the specified local zone;
- negative invariants defined by constraints (rules) that should never be violated. In other words, in a binary sensitivity estimation-positive estimation, positive invariants should always be equal to “1”, and negative invariants should never turn to “0”.
- By parameterization ability, the invariants are divided into two groups:
- non-parametrizable which cannot be customized for a specific project and are fixed in their view;
- parameterizable which can be changed (e.g., be configured, adapted) depending on
- ○
- project type—this type of parameterization consists of considering project type features and the corresponding mathematical representation of invariant correction (e.g., variation in “width”);
- ○
- sensitivity requirements—this type of parameterization for sensitivity is also implemented by correcting the mathematical representation (e.g., variation in “depth” and “width”).
5. FPGA Project Invariant Development
5.1. Development Principles
- Based on the system requirements analysis. It is implemented in the early stages of system development and requires minimal specific design results data. This path is general and does not depend on the type of system (e.g., FPGA design, microprocessor or other systems). The specificity of FPGA projects is manifested here through a method for checking invariants.
- Based on the entire system analysis and identification of its properties, which can be represented by invariants. It can be implemented during the verification of a completed project. This approach is also general, and the specificity of the project affects the way of checking the invariant.
- Based on the analysis of the results obtained at each stage of the project development. It is realized during step-by-step detailing and verification of stages, starting from the verbal specification and ending with the generation of program code with a proof of the correctness of the project. Such a path to the greatest extent considers the specifics of the FPGA project.
- Based on the analysis of each system component property identification. It should be implemented during and after completion of the individual components of the system development: software, hardware, or based on FPGAs; in turn, each component can be decomposed into subcomponents to extract invariants.
- Based on the analysis of typical defects characteristic of individual components and the system as a whole or detected at different stages of its development. This approach can be considered a derivative or part of approaches 1–4.
- “top-down”—when a method synthesizes (generates) an invariant (or system of invariants) and then the defects that are “covered” by this invariant are determined;
- “bottom-top”—when the possible defects of the FPGA design are first determined and invariants are developed for certain types of these defects.
5.2. The Invariants Development Stages
5.2.1. Overall Development Stages Description
- Requirements, system design, results of individual steps’ analyses;
- Clarification of the requirements for the estimation reliability (selection of the optimality criteria for a set of invariants);
- Software, algorithmic, automaton and other mathematical models set formation and their corresponding invariants;
- Each of the invariant calibration;
- The choice of a subset of invariants that is optimal by some criteria.
5.2.2. The Invariants Synthesis Algorithm
- The requirements set RS = {Ri} to the system is analyzed and normalized (priority ones that need to be verified are selected and specified). Many RSs include both functional and nonfunctional requirements;
- For each requirement Ri or their subset ∆R a “covering” invariant Ij or a “covering” subset of ∆Ir is defined. It is solved in three ways:
- a degenerate case: each requirement is an invariant, and its verification is carried out by an expert or other ways. The most convenient form for presenting the results is a checklist;
- each requirement or a subset is associated with an invariant (a subset of invariants) based on the physical meaning of the requirements, the possibility of their semantic compression and compact mathematical representation. An intermediate step here may be to obtain a mathematical model according to the requirements;
- a combination of methods “a” and “b”. Within this combination method “a” is used to verify nonfunctional requirements and method “b” is used to verify functional requirements;
- The problem of covering requirements is solved with the invariant set IS = {Ij} and the minimal invariants systems ISys belonging to IS are determined;
- The optimal system of invariants ISysopt is selected according to given criteria, considering the calibration results of each invariant.
5.2.3. Invariant Synthesis Based on the Property Analysis
- The property set of the system PS = {Pf} is analyzed and formed. Among the elements of the set, priority ones (critical for the system) can also be selected.
- For each property Pf or their subset ∆P the “covering” invariant If or the “covering” subset ∆If are defined.
- The problem of covering requirements is solved by the invariant set IS = {If} and the minimal systems of invariants ISysw belonging to IS are determined.
- The optimal invariants system ISopt is selected according to a given criterion considering the calibration results of each invariant.
5.2.4. The of Invariant Synthesis Based on the Stages of Project Development Analysis Results
- Requirements set RSz for the development stage Sz are analyzed (and the RSz properties identified at this stage) and their prioritization and preliminary selection are conducted.
- For each requirement Rza belonging to RSz (properties Pzb belonging to RSz) or their subsets ∆Rz the “covering” invariant Iza (b) or the “covering” subset of the invariants ∆Iza (b) are defined.
- Operations 1 and 2 are repeated for all stages (z = 1, …, E).
- The problem of covering the requirements of RS or RSz with invariants sets IS = {ISz} is solved and the minimal systems of invariants ISysh, belonging to IS re determined (by stages or/and as a whole).
- The optimal invariants system ISysopt is selected according to a given criterion, considering the calibration results of each of the invariants.
5.2.5. Invariant Synthesis Based on the System Components’ Properties Analysis and Identification
- The system components set CS = {Kd} is formed.
- Component properties are set CPSd = {CPdf} for each component Cd and priorities (critical for the system) are selected.
- For each property CPdf or it’s subset ∆CPdf a “covering” invariant If or a “covering” subset of invariants ∆If is defined.
- The problem of covering the component properties with the invariants set ISd = {Idf} and the minimal invariants systems ISysdv, belonging to ISd is determined.
- Minimal invariant systems ISysx are obtained: to obtain them, the Cartesian product of the sets, ISysdv, found for the individual components is performed, and then the groups that meet the criterion of minimality are selected.
- According to a given criterion, the optimal invariants system ISysopt is selected considering the calibration results of each invariant and the costs associated with their use.
6. Case Study to FPGA Safety Invariant-Based Assessment
- usage of the explicit principle of mapping component ports to the signals arriving at them in the port map (=>);
- “sensitivity list” should contain signals that are used in the body of the process;
- the use of conditional operators must be accompanied by a post-condition (full condition);
- not to use a “hard” index when working with a signal vector, etc.
- It should be emphasized that the control of the rules for the use of the VHDL programming language are quality assurance and risk management mechanisms in the development of electronic FPGA projects that implement functions important to safety.
6.1. Explicit Principle of Mapping Components to the Signals in the PORT MAP Section
- Explicit port assignment
- HKDFF: DFFE port map (d => D_I, clk => CLK_I, q => Q_O, ena => Enable_I, clrn => Clear_I, prn => Set_I);
- Implicit port assignment
- HKDFF: DFFE port map (D_I, CLK_I, Q_O, Enable_I, Clear_I, Set_I);
- Mixed port assignment
- HKDFF: DFFE port map (D_I, CLK_I, q => Q_O, ena => Enable_I, clrn => Clear_I, prn => Set_I);
- Captured CAD
- HKDFF: DFFE port map (q => Q_O, ena => Enable_I, clrn => Clear_I, prn => Set_I, D_I, CLK_I);
- Searching for the PORT MAP (); construction.
- Reading the contents of the brackets.
- Invariant check: whether it worked or not?
- Injecting the defect: replacing the explicit principle of specifying ports with positional one: replacing each design x => y with y.
- Invariant check: whether it worked or not?
- Injecting the defect: replacing the explicit principle of specifying mixed ports: replacing the first structure (s) x => y with y.
- Invariant check: whether it worked or not?
6.2. Using of the Signals from PROCESS “Sensitivity List” in Its Body
6.3. Calibration of the Invariant
- Search for the PROCESS (); construction
- Reading the contents of the brackets and searching the process body for all input signals
- Invariant check: whether it worked or not?
- Injecting the defect (if the list contains two or more signals): replacing the complete sensitivity list with an incomplete one: remove the signal that is used in the body of the process from the list.
- Invariant check: whether it worked or not?
- Injecting the defect: redundant sensitivity list formation: supplementing the sensitivity list with an input signal that is not used in the process body.
- Invariant check: whether it worked or not?
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Grimm, T.; Lettnin, D.; Hübner, M. A Survey on Formal Verification Techniques for Safety-Critical Systems-on-Chip. Electronics 2018, 7, 81. [Google Scholar] [CrossRef] [Green Version]
- Yasko, A.; Babeshko, E.; Kharchenko, V. Verification of FPGA Based NPP I&C Systems Considering Multiple Faults: Technique and Automation Tool. In Proceedings of the 25th International Conference on Nuclear Engineering, Shanghai, China, 2–6 July 2017; Volume 9. [Google Scholar] [CrossRef]
- Bernardeschi, C.; Cassano, L.; Domenici, A. SRAM-based FPGA systems for safety-critical applications: A survey on design standards and proposed methodologies. J. Comput. Sci. Technol. 2015, 30, 373–390. [Google Scholar] [CrossRef]
- IEC 61508-1:2010. Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems, 2nd ed.; International Electrotechnical Commission: Geneva, Switzerland, 2010; p. 127. [Google Scholar]
- Naser, J.; Fink, B.; Killian, C.; Nguyen, T.; Druilhe, A. Guidelines on the Use of Field Programmable Gate Arrays in Nuclear Power Plant I&C Systems; EPRI: Palo Alto, CA, USA, 2009; p. 1019181. [Google Scholar]
- Babeshko, E.; Kharchenko, V.; Leontiiev, K.; Ruchkov, E. Practical aspects of operating and analytical reliability assessment of FPGA-based I&C systems. Radioelectron. Comput. Syst. 2020, 3, 75–83. [Google Scholar] [CrossRef]
- Abrial, J.-R. Modeling in Event-B: System and Software Engineering; Cambridge University Press: Cambridge, UK, 2009; p. 612. [Google Scholar]
- Diller, A.Z. An Introduction to Formal Methods; Wiley: Hoboken, NJ, USA, 1994; p. 354. [Google Scholar]
- Lecomte, T.; Servat, T.; Pouzancre, G. Formal Methods in Safety-Critical Railway Systems. In Proceedings of 10th Brasilian Symposium on Formal Methods, Ouro Preto, Brazil, 29–31 August 2007. [Google Scholar]
- Howar, F.; Barnat, J. (Eds.) Formal Methods for Industrial Critical Systems. In Proceedings of the 23rd International Conference on Formal Methods for Industrial Critical Systems, FMICS, Maynooth, Ireland, 3–4 September 2018. [Google Scholar]
- Clarke, E.M.; Henzinger, T.A.; Veith, H.; Bloem, R. Handbook of Model Checking; Springer: Berlin/Heidelberg, Germany, 2018; ISBN 978-3-319-10574-1. [Google Scholar] [CrossRef]
- Knauss, E.; Goedicke, M. Requirements Engineering: Foundation for Software Quality. In Proceedings of the 25th International Working Conference, REFSQ 2019, Essen, Germany, 18–21 March 2019. [Google Scholar]
- Shuja, S.; Srinivasan, S.K.; Jabeen, S.; Nawarathna, D. A formal verification methodology for DDD mode pacemaker control programs. J. Electr. Comput. Eng. 2015, 2015, 57. [Google Scholar] [CrossRef] [Green Version]
- Jabeen, S.; Srinivasan, S.K.; Shuja, S.; Dubasi, M.A.L. A formal verification methodology for FPGA-based stepper motor control. IEEE Embed. Syst. Lett. 2015, 7, 85–88. [Google Scholar] [CrossRef]
- Bui, M.; Lu, M.; Hojabr, R.; Chen, M.; Shriraman, A. Real-Time Formal Verification of Autonomous Systems with An FPGA. arXiv 2020, arXiv:2012.04011. Available online: https://arxiv.org/pdf/2012.04011.pdf (accessed on 10 September 2021).
- Ceesay-Seitz, K.; Boukabache, H.; Perrin, D. A Functional Verification Methodology for Highly Parametrizable, Continuously Operating Safety-Critical FPGA Designs: Applied to the CERN RadiatiOn Monitoring Electronics (CROME). In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Lisbon, Portuga, 16–18 September 2020; Springer: Cham, Switzerland, 2020; pp. 67–81. [Google Scholar] [CrossRef]
- Toner, C.; Boukabache, H.; Ducos, G.; Pangallo, M.; Danzeca, S.; Widorski, M.; Roesler, S.; Perrin, D. Fault Resilient FPGA Design for 28 nm ZYNQ System-on-Chip Based Radiation Monitoring System at CERN. Microelectron. Reliab. 2019, 100–101, 113492. [Google Scholar] [CrossRef]
- Pakonen, A.; Tahvonen, T.; Hartikainen, M.; Pihlanko, M. Practical applications of model checking in the Finnish nuclear industry. In Proceedings of the 10th International Topical Meeting on Nuclear Plant Instrumentation, Control and Human Machine Interface Technologies (NPIC & HMIT 2017), San Francisco, CA, USA, 11–15 June 2017. [Google Scholar]
- Pakonen, A.; Buzhinsky, I.; Björkman, K. Model checking reveals design issues leading to spurious actuation of nuclear instrumentation and control systems. Reliab. Eng. Syst. Saf. 2021, 205, 107–237. [Google Scholar] [CrossRef]
- Buzhinsky, I.; Pakonen, A. Model-checking detailed fault-tolerant nuclear power plant safety functions. IEEE Access 2019, 7, 162139–162156. [Google Scholar] [CrossRef]
- Jabeen, S.; Srinivasan, S.S. Formal verification methodology for real-time Field Programmable Gate Array, IET. Comput. Digit. Tech. 2017, 11, 197–203. [Google Scholar] [CrossRef]
- Kharchenko, V.; Letychevskyi, O.; Odarushchenko, O.; Peschanenko, V.; Volkov, V. Modeling method for development of digital system algorithms based on programmable logic devices. Cybern. Syst. Anal. 2020, 56, 710–717. [Google Scholar] [CrossRef]
- Swierczynski, P.; Fyrbiak, M.; Koppe, P.; Paar, C. FPGA trojans through detecting and weakening of cryptographic primitives. IEEE TCAD 2015, 34, 1236–1249. [Google Scholar] [CrossRef]
- Booch, G.; Rumbaugh, J.; Jacobson, I. Unified Modeling Language User Guide; Addison-Wesley: Boston, MA, USA, 2008. [Google Scholar]
- Coelho, D. The VHDL Handbook; Springer Science & Business Media: New York, NY, USA, 1989. [Google Scholar]
- System Verilog. Available online: www.asic-world.com/systemverilog/tutorial.html (accessed on 10 September 2021).
- VC Formal. Available online: https://www.synopsys.com/verification/static-and-formal-verification/vc-formal.html (accessed on 10 September 2021).
- Vivado Verification. Available online: https://www.xilinx.com/products/design-tools/vivado/verification.html (accessed on 10 September 2021).
- JasperGold. Available online: https://www.cadence.com/ko_KR/home/tools/system-design-and-verification/formal-and-static-verification/jasper-gold-verification-platform.html (accessed on 10 September 2021).
- Letichevsky, A.; Letychevskyi, O.; Peschanenko, V. Insertion Modeling and Its Applications. Comput. Sci. J. Mold. 2016, 24, 357–370. [Google Scholar]
- Letichevsky, A.; Gilbert, D. Interaction of agents and environments. In Recent Trends in Algebraic Development Technique; Bert, D., Choppy, C., Eds.; Springer: Verlag, Germany, 1999. [Google Scholar]
- Letichevsky, A. Algebra of Behavior Transformations and its Applications. In Structural Theory of Automata, Semigroups, and Universal Algebra; Kudryavtsev, V.B., Rosenberg, I.G., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 241–272. [Google Scholar]
- ITU-T Recommendation, Z.120, Message Sequence Charts (MSC). Available online: https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-Z.120-201102-I!!PDF-E&type=items (accessed on 10 September 2021).
- Letychevskyi, O.; Peschanenko, V.; Volkov, V. Algebraic Virtual Machine Project. In Proceedings of the17th International Conference ICTERI, Ukraine, Kherson, 28 September–2 October 2021. [Google Scholar]
- Ehlers, T.; Nowotka, D.; Sieweck, P. Finding Race Conditions in Real-Time Code by Using Formal Software Verification, Department of Computer Science, Kiel University. 2014. Available online: https://www.researchgate.net/publication/288563365_Finding_race_conditions_in_real-time_code_by_using_formal_software_verification (accessed on 10 September 2021).
- Didier, J.-Y.; Mallem, M. A New Approach to Detect Potential Race Conditions in Component-Based Systems. Available online: https://hal.archives-ouvertes.fr/hal-01024478 (accessed on 10 September 2021).
- Beckman, N.E. (Ed.) A Survey of Methods for Preventing Race Conditions. Available online: https://www.cs.cmu.edu/~nbeckman/papers/race_detection_survey.pdf (accessed on 10 September 2021).
- Letichevsky, A.; Letychevskyi, O.; Peschanenko, V. An Interleaving Reduction for Reachability Checking in Symbolic Modeling. In Proceedings of the 11th Int. Conf. ICTERI 2015, Lviv, Ukraine, 14–16 May 2015; Ermolayev, V., Ed.; CEUR-WS.org/Vol-1356, ISSN 1613-0073. pp. 338–353. Available online: Ceur-ws.org/Vol-1356/paper_74.pdf (accessed on 10 September 2021).
- Jonson, G. The INSAG Defense in Depth Concept and D-in-D&D In Instrumentation and Control. Proceedings of 7th ANS Topical Meeting on NPIC-HMIT, Las Vegas, LA, USA, 7–11 November 2010. [Google Scholar]
- Kharchenko, V.; Bakhmach, E.; Siora, A. Diversity-scalable decisions for FPGA-based safety-critical I&C systems: From theory to implementation. In Proceedings of the 6th American Nuclear Society International Topical Meeting on Nuclear Plant Instrumentation, Control, and Human-Machine Interface Technologies, Knoxville, TN, USA, 5–9 April 2009; pp. 1494–1505. [Google Scholar]
- Karam, R.; Hoque, T.; Ray, S.; Tehranipoor, M.; Bhunia, S. MUTARCH: Architectural diversity for FPGA device and IP security. In Proceedings of the 2017 22nd Asia and South Pacific Design Automation Conference (ASP-DAC), Chiba City, Japan, 16–19 January 2017; pp. 611–616. [Google Scholar] [CrossRef]
- Kharchenko, V. Independent Verification and Diversity: Two Echelons of Cyber Physical Systems Safety and Security Assurance. In Proceedings of the 2nd International Workshop on Information-Communication Technologies & Embedded Systems (ICTES 2020), Mykolaiv, Ukraine, 12 November 2020; pp. 19–29, CEUR-WS.org/Vol-2762, ISSN 1613-0073. Available online: Ceur-ws.org/Vol-2762/invited2.pdf (accessed on 10 September 2021).
- Kharchenko, V.; Siora, A.; Sklyar, V.; Volkoviy, A.; Bezsaliy, V. Multi-diversity versus common cause failures: FPGA-based multi-version NPP I&C systems. In Proceedings of the 7th International Topical Meeting on Nuclear Plant Instrumentation, Control, and Human-Machine Interface Technologies 2010, NPIC and HMIT, Las Vegas, NV, USA, 7–11 November 2010; Volume 2, pp. 1081–1092. [Google Scholar]
- Eriksson, J. Tool-Supported Invariant-Based Programming. Ph.D. Thesis, Åbo Akademi University, Turku, Finland, 2010. [Google Scholar]
- Kharchenko, V.; Konorev, B.; Sklyar, V.; Reva, L. Invariant-oriented verification of HDL-based safety critical systems. In Proceedings of the East-West Design & Test Symposium (EWDTS 2013), Rostov on Don, Russia, 27–30 September 2013; pp. 1–4. [Google Scholar] [CrossRef]
- Ostroumov, S.; Tsiopoulos, L. VHDL Code Generation from Formal Event-B Models. Proceedings of 4th Euromicro Conference on Digital System Design, Oulu, Finland, 31 August–2 September 2011; pp. 127–134. [Google Scholar] [CrossRef]
- Ostroumov, S.; Troubitsyna, E.; Laibinis, L.; Kharchenko, V. Towards Designing FPGA-Based Systems by Refinement in B. In Dependability and Computer Engineering: Concepts for Software-Intensive Systems; Petre, L., Sere, K., Troubitsyna, E., Eds.; IGI Global: Hershey, PA, USA, 2012; pp. 92–112. [Google Scholar] [CrossRef] [Green Version]
- Andrashov, A.; Kharchenko, V.; Sklyar, V.; Reva, L.; Dovgopolyi, V.; Golovir, V. Verification of FPGA electronic designs for nuclear reactor trip systems: Test- and invariant-based methods. In Proceedings of the 2010 East-West Design & Test Symposium (EWDTS), St. Petersburg, Russia, 17–20 September 2010; pp. 92–97. [Google Scholar] [CrossRef]
- Perepelitsyn, A.; Illiashenko, O.; Duzhyi, V.; Kharchenko, V. Application of the FPGA Technology for the Development of Multi-Version Safety-Critical NPP Instrumentation and Control Systems. Nucl. Radiat. Saf. 2020, 2, 52–61. [Google Scholar] [CrossRef]
- Kharchenko, V.; Illiashenko, O. Diversity for security: Case assessment for FPGA-based safety-critical systems. In Proceedings of the MATEC Web of Conferences 20th International Conference on Circuits, Systems, Communications and Computers (CSCC 2016), Corfu Island, Greece, 14–17 July 2016; Volume 76. [Google Scholar] [CrossRef]
- Illiashenko, O.; Kharchenko, V.; Kor, A.-L.; Panarin, A.; Sklyar, V. Hardware diversity and modified NUREG/CR-7007 based assessment of NPP I&C safety. In Proceedings of the IEEE 9th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications, IDAACS, Bucharest, Romania, 21–23 September 2017; Volume 2, pp. 907–911. [Google Scholar] [CrossRef]
- IEEE. 1076-2019—IEEE Standard for VHDL Language Reference Manual; IEEE: Piscataway, NJ, USA, 2019; pp. 1–673. [Google Scholar] [CrossRef]
- Tyurin, S. Hyper redundancy for super reliable FPGAs. Radioelectron. Comput. Syst. 2021, 1, 119–132. [Google Scholar] [CrossRef]

| Requirement | Description |
|---|---|
| Conciseness and formality of description | The invariant must be characterized by a number or a compact mathematical construction: a tuple of numbers, a predicate, an equation or an inequality, an expression of temporal logic, a simple graph containing several vertices and arcs, a fragment of an automaton table that defines the functions of transitions and outputs, etc. |
| Clarity and physicality | The invariant has a clear physical meaning and purpose (it limits the permissible values range of a certain system variable, determines the compatibility of events, or sets the logic for changing system states). The purpose is determined by the type of invariant, based on the used test feature (e.g., accuracy, logical, functional, semantic, etc.). |
| Measurability | The invariant should be subject to simple verification, and it should be evaluated using simple metrics within the given scale. |
| Criticality | Following the criticality characteristic, invariants can form a priority series, which should be considered during evaluations, as well as when forming a system of invariants to ensure the required reliability while minimizing costs. For critical applications, in which development implies using formal methods, the invariants must control the observance of properties associated primarily with safety functions. |
| Traceability | For each invariant, it should be clearly understood which requirement verification fulfillment it meets, and which violation of this requirement is monitored. The traceability characteristics can be described by the matrix “FPGA design requirements—invariants”. The invariant allows one to verify the performance of one or more system properties and their corresponding requirements. |
| Globality | The invariant must be true constantly on the whole set of states or only when the system is in a certain state. For invariants, the field of their action must be known (i.e., the entire system and its model or individual components of the system). |
| Controllability | For an invariant, the following conditions should be met: a subset of controlled requirements (i.e., completeness of control, degree of coverage) is established; the reliability of the control of the requirement(s) is provided; the possible control errors are specified. These characteristics can be determined experimentally by defect injection and evaluating the invariant sensitivity. |
| Diagnostic ability | The diagnostic ability of an invariant consists of the possibility of determining the cause (defect or another anomaly) by which the invariant violation occurred. This characteristic is not fundamental, since the main purpose of any invariant is to solve the monitoring problem. |
| Flexibility and scalability | This characteristic consists of varying (i.e., adjusting) the mathematical representation of the invariant possibility depending on the requirements for a controlling or other ability, as well as on the design features. |
| Non-redundancy | Invariants should not repeat the checks and can be used to control defects detected by standard tools (compiler, supplied tools). The presence of such invariants increases the cost of verification. Simultaneously, excessive invariants can be used within the system, if their use allows increasing the verification trustworthiness |
| Full Sensitivity List | Incomplete Sensitivity List | Excess Sensitivity List | |
|---|---|---|---|
| 1. | Activation: PROCESS (CLK_I, Data_I) IS | Activation: PROCESS (CLK_I) IS | Activation: PROCESS (CLK_I, Data_I, test) IS |
| 2. | BEGIN | BEGIN | BEGIN |
| 3. | IF RISING_EDGE(CLK_I) THEN | IF RISING_EDGE(CLK_I) THEN | IF RISING_EDGE(CLK_I) THEN |
| 4. | IF Data_I = ‘1’ THEN Data_O <= ‘0’; | IF Data_I = ‘1’ THEN Data_O <= ‘0’; | IF Data_I = ‘1’ THEN Data_O <= ‘0’; |
| 5. | ELSE Data_O <= ‘1′; | ELSE Data_O <= ‘1′; | ELSE Data_O <= ‘1’; |
| 6. | END IF; | END IF; | END IF; |
| 7. | END IF; | END IF; | END IF; |
| 8. | END PROCESS Activation; | END PROCESS Activation; | END PROCESS Activation; |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kharchenko, V.; Illiashenko, O.; Sklyar, V. Invariant-Based Safety Assessment of FPGA Projects: Conception and Technique. Computers 2021, 10, 125. https://doi.org/10.3390/computers10100125
Kharchenko V, Illiashenko O, Sklyar V. Invariant-Based Safety Assessment of FPGA Projects: Conception and Technique. Computers. 2021; 10(10):125. https://doi.org/10.3390/computers10100125
Chicago/Turabian StyleKharchenko, Vyacheslav, Oleg Illiashenko, and Vladimir Sklyar. 2021. "Invariant-Based Safety Assessment of FPGA Projects: Conception and Technique" Computers 10, no. 10: 125. https://doi.org/10.3390/computers10100125
APA StyleKharchenko, V., Illiashenko, O., & Sklyar, V. (2021). Invariant-Based Safety Assessment of FPGA Projects: Conception and Technique. Computers, 10(10), 125. https://doi.org/10.3390/computers10100125








