Modeling Networked Telemetry
Abstract
:1. Introduction
2. Telemetry Architecture: Test Article and Ground Station
- Spectrum and access management.
- Solutions for the management of telemetry infrastructure.
- Management of telemetry network performance.
- Unified management tools.
2.1. Test Article and Ground Station
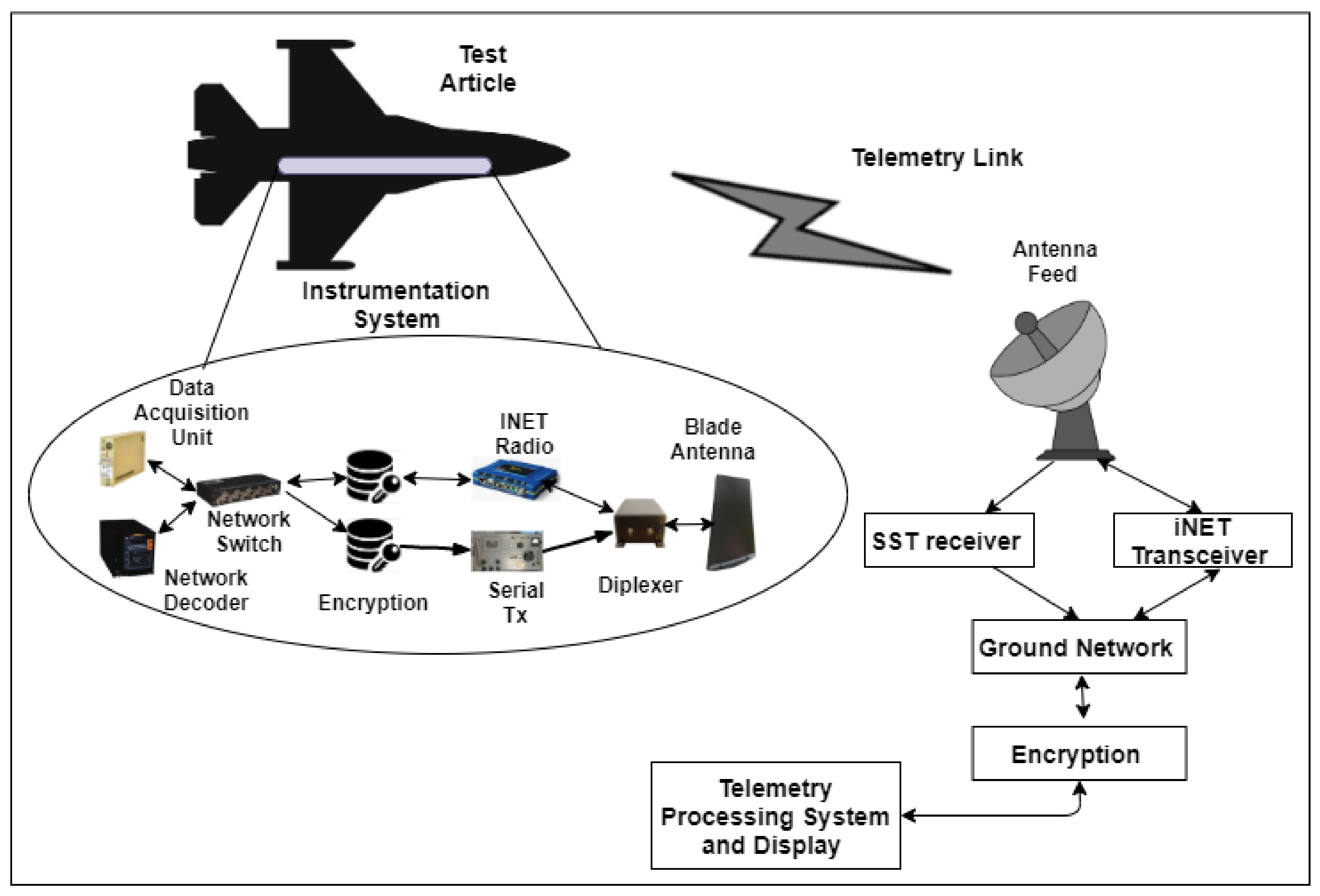
2.1.1. Onboard Instrumentation System
2.1.2. Ground Communication System
2.2. Test and Resource Management Center
2.2.1. Test and Training Environment
- (1)
- The JMETC Secret Network (JSN), which is the T&E enterprise network solution for Secret testingis based on the Secret Defense Research and Engineering Network (SDREN).
- (2)
- The JMETC Multiple Independent Levels of Security (MILS), whereas The T&E Enterprise network solution for all classifications and cyber testing is Network (JMN).
2.2.2. Net-Centric Systems Test Environment
2.2.3. Distributed Live and Simulated Systems T&E Environment
2.2.4. T&E Simulated and Cyberspace Threat Environment
3. General Networked Telemetry Architecture
3.1. Industrial Control System (ICS)
- (5)
- The master terminal unit (MTU) gathers and logs data collected by the field layers, shows data to the human–machine interface (HMI), and may create activity dependent on distinguished events.
- (6)
- Supervisory System
3.2. General Integrated Networked Telemetry (iNET) Architecture
3.3. Mapping the Old Scada System to the Industrial 4.0
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Grace, T.B.; Abbott, B.A. Telemetry Network Standards Overview. Eur. Test Telem. Conf. ettc 2018, 2018. [Google Scholar] [CrossRef]
- Reynolds, R.S. IRIG Telemetry Standards 1969. In Proceedings of the International Telemetering Conference, Washington, DC, USA, 15–17 September 1969; Volume 5. [Google Scholar]
- Document 106-17 Telemetry Standards July 2017 Prepared by Telemetry Group; Secretariat Range Commanders Council: US Army White Sands Missile Range, NM, USA, 2017.
- Young, T. I integrated Network Enhanced Telemetry, iNET: Impacts to Telemetry Community, Distribution A: Approved for Public Release. 412TW-PA-18138. 17 May 2018. Available online: https://www.itea.org/wp-content/uploads/2018/05/Young-Tom.pdf (accessed on 2 April 2021).
- Young, T. Integrated Network Enhanced Telemetry (iNET): Impact to the Telemetry Community for the ettc2018. In Proceedings of the European Test and Telemetry Conference, Nürnberg, Germany, 26–28 June 2018. [Google Scholar] [CrossRef]
- Rakas, S.V.B.; Stojanović, M.D.; Marković-Petrović, J.D. A Review of Research Work on Network-Based SCADA Intrusion Detection Systems. IEEE Access 2020, 8, 93083–93108. [Google Scholar] [CrossRef]
- Urias, V.; Leeuwen, B.V.; Richardson, B. Supervisory Command and Data Acquisition (SCADA) system Cyber Security Analysis using a Live, virtual, and constructive (LVC) testbed. In Proceedings of the 2012 IEEE Military Communications Conference, Orlando, FL, USA, 29 October–1 November 2012. [Google Scholar] [CrossRef]
- Markovic-Petrovic, J.D.; Stojanovic, M.D. An Improved Risk Assessment Method for SCADA Information Security. Elektron. Elektrotech. 2014, 20, 69–72. [Google Scholar] [CrossRef] [Green Version]
- Hu, Y.; Yan, A.; Li, H.; Sun, Y.; Sun, L. A survey of intrusion detection on industrial control system. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718794615. [Google Scholar] [CrossRef] [Green Version]
- Nazir, S.; Patel, S.; Patel, D. Assessing and augmenting SCADA cyber security: A survey of techniques. Comput. Secur. 2017, 70, 436–454. [Google Scholar] [CrossRef] [Green Version]
- Stojanovic, M.; Bostjancic-Rakas, S.; Markovic-Petrovic, J. SCADA systems in the cloud and fog environments: Migration scenarios and security issues. Facta Univ. Ser. Electron. Energ. 2019, 32, 345–358. [Google Scholar] [CrossRef] [Green Version]
- Probst, C.; Hunker, J.; Bishop, M.; Gollman, D. Countering Insider Threats. ENISA Q. Rev. 2009, 5, 13–14. [Google Scholar]
- Madon, P.; Young, T.; O’Brien, T.; Radke, M. Spectrum Management System—Frequency Assignment De-Confliction and RF Link Quality Prediction. In Proceedings of the International Telemetering Conference Proceedings, Glendale, AZ, USA, 5–8 November 2018; Volume 54. [Google Scholar]
- Oyediran, D.; Dean, R.; Farzad, M. Spectrum sharing mac protocol applications for the proposed 3.5 GHz Band. Int. Telem. Conf. Proc. Int. Found. Telem. 2018, 54, 11. [Google Scholar]
- U.S. Army Program Executive Office for Simulation Training & Instrumentation. Cyberspace Test Technology Science & Technology (CTT S&T) Test Technology Area (TTA). Broad Agency W900KK-12-R-0010 ISSUE DATE: 31 January 2012, Expiration Date: 30 September 2016.
- Norman, R. Improving Distributed Test & Evaluation with JMETC & TENA. Joint Mission Environment Test Capability (JMETC) Program Overview; JMETC Program in; Test Resource Management Center (TRMC). 2018. Available online: https://ndiastorage.blob.core.usgovcloudapi.net/ndia/2017/systems/Thursday/Track2/19925_Norman.pdf (accessed on 1 August 2020).
- Arnwine, M. Cheaper, Faster, and with Less Risk Using Distributed Testing to Accelerate T&E Capabilities Joint Mission Environment Test Capability (JMETC), Joint Mission Environment Test Capability. 19 September 2012. Available online: https://www.itea.org/images/pdf/Events/2012_Proceedings/2012_Annual_Symposium/track_4_arnwine_cheaperfasterandwithlessriskusingdistributedtestingtoacceleratetecapabilities.pdf (accessed on 1 August 2020).
- Macdonald, T. The DoD T&E/S&T Program, Test Resource Management Center: Net-Centric Systems Test (NST) Overview, Industry/Academia Days. 9 August 2011. Available online: https://web.wpi.edu/Images/CMS/ECE/Test_and_Evaluation-Tom_Macdonald(1).pdf (accessed on 1 August 2020).
- Rumford, G. TheDoD T&E/S&T Program, NDIA. In Proceedings of the 12th Annual Science & Engineering Technology Conference, North Charleston, SC, USA, 21–23 June 2011. [Google Scholar]
- US-CERT. Cybersecurity and Infrastructure Security Agency, Control Systems Security Program. US Department of Homeland Security, 2021. Available online: https://us-cert.cisa.gov/ics (accessed on 11 November 2020).
- Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and Other Control System Configurations such as Programmable Logic Controllers (PLC), NIST Special Publication 800-82 Revision 2. Available online: http://dx.doi.org/10.6028/NIST.SP.800-82r2 (accessed on 1 December 2020).
- Galloway, B.; Hancke, G.P. Introduction to industrial control networks. IEEE Commun. Surv. Tuts. 2013, 15, 860–880. [Google Scholar] [CrossRef] [Green Version]
- Cardenas, A.A.; Amin, S.; Sastry, S. Research Challenges for the Security of Control Systems. In Proceedings of the 3rd USENIX Workshop on Hot Topics in Security (HotSec ’08), Associates with the 17th USENIX Security Symposium, San Jose, CA, USA, 29 July 2008. [Google Scholar]
- Stouffer, K.; Falco, J.; Kent, K. Guide to Supervisory Control and Data Acquisition (Scada) and Industrial Control Systems Security; Sp800-82; NIST: Gaithersburg, MD, USA, 2006. [Google Scholar]
- Cybersecurity for Critical Infrastructure (ICS, SCADA &IIoT); Palo Alto Networks: Santa Clara, CA, USA, 2020.





| Process Control Network | Purdue Reference Architecture | |||
|---|---|---|---|---|
| Manufacturing Operations | Level 3 | Enterprise | Business | Level 4 |
| Control Systems | Level 2 | DMZ | DMZ or 3.5 | |
| Intelligent Devices | Level 1 | Manufacturing | Manufacturing Operations | Level 3 |
| Process | Level 0 | Plant HMI | Control Systems | Level 2 |
| Intelligent Devices | Level 1 | |||
| Process | Level 0 | |||
| IoT/ IIoT Reference Architecture | ||
|---|---|---|
| The Cloud | Business | Level 4 |
| DMZ or 3.5 | ||
| The Edge | Manufacturing Operations | Level 3 |
| Control Systems | Level 2 | |
| Intelligent Devices | Level 1 | |
| Process | Level 0 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zegeye, W.; Dean, R.; Dugda, M.; Moazzami, F.; Bezabih, A. Modeling Networked Telemetry. Computers 2021, 10, 45. https://doi.org/10.3390/computers10040045
Zegeye W, Dean R, Dugda M, Moazzami F, Bezabih A. Modeling Networked Telemetry. Computers. 2021; 10(4):45. https://doi.org/10.3390/computers10040045
Chicago/Turabian StyleZegeye, Wondimu, Richard Dean, Mulugeta Dugda, Farzad Moazzami, and Andargachew Bezabih. 2021. "Modeling Networked Telemetry" Computers 10, no. 4: 45. https://doi.org/10.3390/computers10040045
APA StyleZegeye, W., Dean, R., Dugda, M., Moazzami, F., & Bezabih, A. (2021). Modeling Networked Telemetry. Computers, 10(4), 45. https://doi.org/10.3390/computers10040045






