Challenges of IoT Identification and Multi-Level Protection in Integrated Data Transmission Networks Based on 5G/6G Technologies
Abstract
:1. Introduction
- 1.
- Technological risks:
- the growth of waste volumes due to the rapid obsolescence of equipment and its disposal (E-waste);
- an increase in the volume of data transmitted over networks (“information garbage”, which doubles every one and a half to two years on average);
- the manifestation of vulnerabilities in the software of smart home appliances and other IoT, which lead to a denial of service due to virus attacks (“hole in the teapot”);
- the hacking of personal (particularly medical) smart devices;
- the presence of problems of leakage of personal data of residents, etc.
- 2.
- Legal and political risks:
- the restriction of human rights and freedoms when using digital personal identification;
- the existence of a threat of a one-time disconnection from all public services in the case of failures;
- the use of personal data with criminal intent;
- the possibility of disclosing personal data by various indirect methods (collection of incriminating evidence on the analysis of the media and social networks);
- the growth of political, social and economic costs from cyberattacks and data leaks;
- the development of virtual crime, etc.
- 3.
- Economic risks:
- the development of cryptocurrency turnover makes the commodity-money exchange anonymous (ordering criminal acts, buying narcotic substances and weapons and paying for other asocial acts);
- moving the shadow economy to the Internet (through anonymous networks, such as TOR).
- 4.
- Social risks:
- depriving a part of the population from access to information and services (a “digital divide”);
- the presence of discrimination and the exclusion of certain categories of citizens from the process of consuming public goods when using smart technologies;
- the problem of amateurism with the participation of the population in the management of a SH.
- receive, transmit, process and store relevant information about the life of the SH;
- provide the necessary backup and recovery capabilities as quickly as possible;
- ensure centralized and equal access of consumers to digital services and services of the environment.
- 1.
- Analysis of modern IoT for identification and further categorization to develop options for switching to local centers for collecting and processing information.
- 2.
- Analysis of existing wired and wireless DTFNs in order to organize a “network of networks” to maintain the required level of efficiency and safety of SH operation.
- 3.
- Identification of information-security issues in NTI based on the analysis of the landscape threat in 5G/6G networks.
- 4.
- Organizations of hybrid protection of 5G and 6G networks.
2. Analysis of Modern IoT for Identification and Further Categorization
- Level 1 is associated with the identification of each object (a Body Area Network—BAN);
- Level 2 is a set of services to serve the needs of the consumer (can be considered as a network of owned “things”, a particular example is a “smart home”) (a Local Area Network—LAN);
- Level 3 is associated with the urbanization of urban life, i.e., this is the concept of a “smart city”, where all the information that concerns the inhabitants of this city is pulled together to a specific residential area, to your house and neighboring houses and then to SH (a Wide Area Network—WAN);
- Level 4 is a sensory planet (a Very Wide Area Network—VWAN).
- 1.
- The mandatory identification of each specific object from the IoT (the first level).
- 2.
- The continuous switching of the growing volume of information and objects in the network, which, in turn, will also be combined in the network (interrelation from the second to the fourth level of the four-layer pie).
3. Analysis of Existing Wired and Wireless DTFNs in Order to Organize a “Network of Networks” in SH
- 1.
- Shielded copper twisted pair (UTP, FTP, STP and other types and categories) or “Ethernet”.
- 2.
- Fiber optic communication lines (fiber optic cable—FOC) is a type of communication in which information is transmitted through optical dielectric waveguides, known as “optical fiber”.
- 1.
- First responder communications and disaster relief. This option is essential in response scenarios as it provides not only disaster forecasting but also warnings, emergency response and emergency communications. This duplication of terrestrial networks with non-terrestrial networks will ensure continuity of service and support for emergency management. It is also planned to support voice and data transmission using a video system for the purpose of operational communications with a control point.
- 2.
- High-precision positioning and navigation, which will provide high-quality Vehicle-to-Everything (V2X) services for vehicles, both in the urban environment and accurate positioning and vehicle navigation services in remote and hard-to-reach areas.
- 3.
- Monitoring of the earth’s surface in real time. In this case, optical filming using visible light and partially infrared cameras, as well as radio-frequency scanning, will avoid the limitations of transmitting and receiving communication channels.
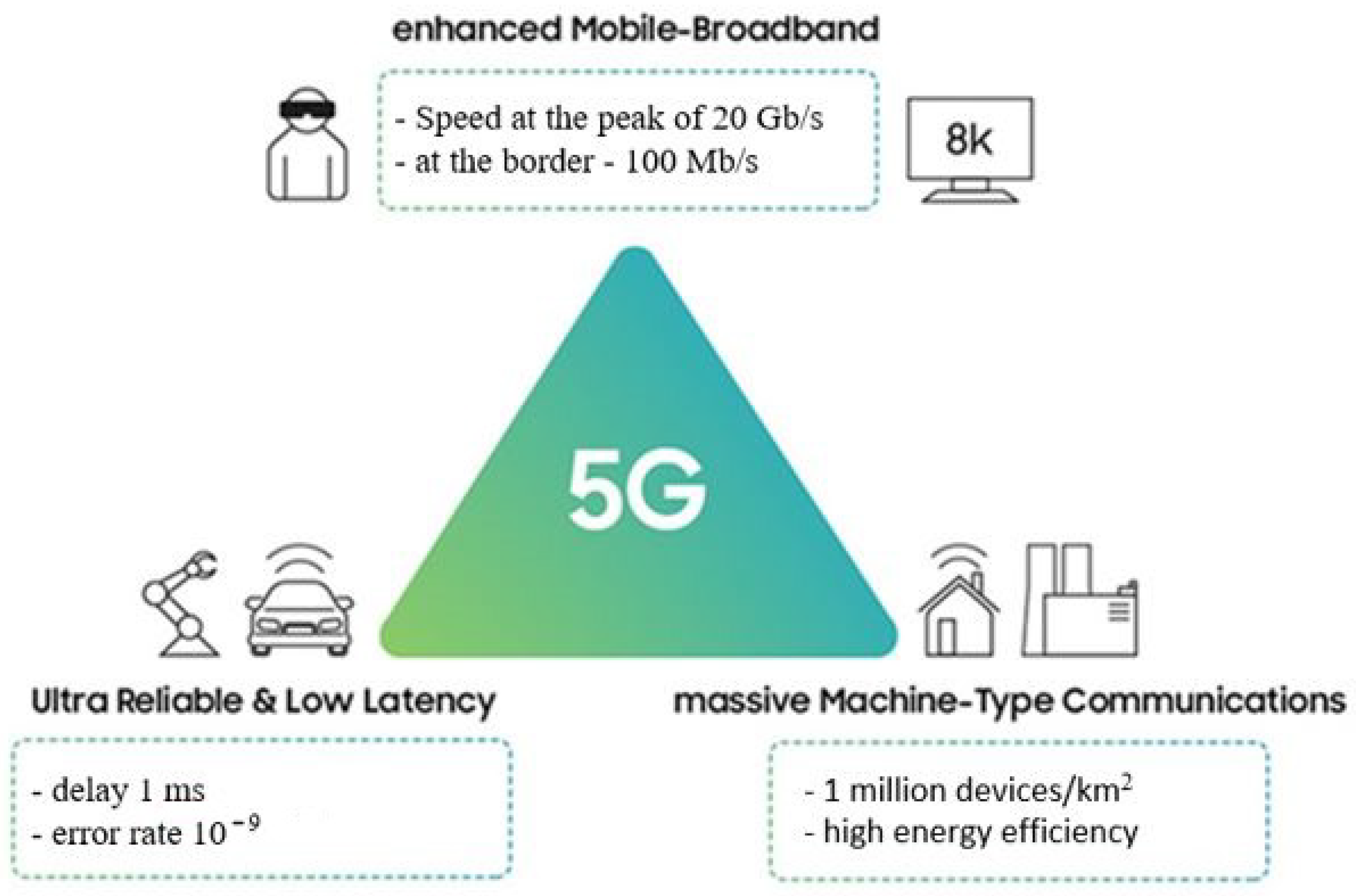
- 1.
- Enhanced mobile broadband (eMBB): up to 25 Gbps peak data rate. Applications: 4K, 8K, 3D live streaming; Augmented Reality (AR)/Virtual Reality (VR) services; cloud gaming; and other high-traffic services.
- 2.
- Ultra-Reliable and Low-Latency Communication (URLLC): Reducing data transfer delays to 1 ms and always having a connection. Applications: unmanned vehicles (V2X) and remote technologies (automation of production lines and robotic surgery).
- 3.
- Mass machine-to-machine communication (enhanced Mobile BroadBand-MTC): support up to 1 million connections to the base station per 1 square kilometer with data transfer rates up to tens of gigabits per second. Applications: development of consumer and industrial IoT (power supply, manufacturing, smart city, SH, etc.) (Figure 6).
4. Identification of Problematic Issues of Information Security in NTI Based on the Analysis of the Security Threat Landscape for SHs
- 1.
- A significantly increased attack surface. This circumstance is primarily due to the ever-increasing number of IoT devices, which, in turn, leads to a proportional increase in entry points for organizing targeted attacks. In addition, according to the concept of converged architecture, WiFi radio access networks, 4G-LTE, etc. must also connect to a single core 5G/6G network, making the connected devices less resistant to outside hacking. This will give hackers more IoT devices to collect and use for DDoS attacks, which will cause an increase in the frequency of such attacks. As a result, risks are possible: a large number of connections and high bandwidth increases the attack surface, while the number of IoT devices that are less resistant to hacking is growing.
- 2.
- The architecture of the core network (network core or 5G Core) is based on cloud technologies and the virtualization of network functions—software-defined networks (SDNs) and virtualization of network functions (NFV), allowing the creation of many independent segments, thus, supporting services with different sets of characteristics. In addition, segmentation will allow operators to provide network infrastructure as a separate service. At the same time, the network infrastructure used will depend on 5G/6G, much more than on their predecessors, and a protection breach in any area could become critical; thus, the consequences could be catastrophic. Thus, the risks should include the fact that such a construction of a network infrastructure leads to more serious consequences in case of failures and cyber-attacks when considering the scale of use.
- 3.
- Ample opportunities are opening for more aggressive conduct of various types of so-called “espionage”. It is known than any IoT device with the ability to capture video or audio information (the presence of cameras and microphones) can be used by cybercriminals or software or hardware manufacturers for them to view and listen to uninformed users. In this case, the risks are clear.
- 4.
- An analysis conducted by an international team of protection researchers from Purdue University and Iowa State University (USA) found almost a dozen vulnerabilities in the 5G mobile communication standard [29]. The exploitation of the vulnerabilities allowed for several attacks, such as location tracking, the transmission of false alarms and the complete disconnection of the phone’s 5G connection from the network. A group of researchers was able to track and fix the location of the device in real time. Moreover, experts were able to intercept the phone’s paging channel to broadcast fake emergency alerts, which, according to the research team, could cause “artificial chaos”.It should also be considered that a new kind of security threat can exploit vulnerabilities in all AKE protocols, including 5G protocols, and invade the privacy of mobile device users, causing more serious damage than before. Such “snoop activity monitoring” attacks use fake base station attacks that attackers have used to target vulnerable AKE protocols and protection leaks in 3G and 4G networks, as well as an encryption vulnerability for sequence numbers (SQNs).Although the AKE protocols used in 5G/6G networks have improved protection against base station spoof attacks, researchers have shown that relay attacks can break the SQN security of cellular networks, thereby, rendering it useless. These attacks are much more dangerous than the previous attacks due to having an important feature: previously, a user could avoid an intrusion by leaving the attack zone; however, now hackers can continue to monitor a user’s activity even if the user leaves the range of a fake base station using a new fake attack. In this case, the risks include attacks, such as “monitoring subscriber activity”, which, in addition to physical tracking of the subscriber or certain devices, create prerequisites for the protection of encryption protocols.
- 5.
- 5G networks, and then 6G, involve the active use of edge-computing technology—mobile edge computing (MEC). These can be, in particular, corporate applications running on the network of operators: intelligent services, financial services and multimedia. In this case, the operator’s 5G/6G networks are integrated into the corporate infrastructure. At the same time, one of the advantages of 5G/6G networks is a significantly low latency, which can be “successfully” used in the same DDoS attacks [11], because hackers will be able to strike faster—in seconds, not minutes.To confirm the theory, the researchers created a malicious base radio and, using the 5GReasoner tool, successfully performed several attacks on a smartphone connected to 5G. In one of the scenarios, a DoS attack on a phone resulted in a complete cut of the connection from the cellular network [29]. Thus, the risks include new opportunities for penetration into corporate networks, placement of MEC equipment outside the protected perimeter of the organization and the fact that the speed of a malicious attack becomes significantly higher.
- 6.
- The centralized network management infrastructure (Operations and Maintenance—O&M) used in 5G and then 6G networks is complicated by the need to simultaneously support a large number of service segments. In this case, risks can be attributed to the more serious consequences of misuse of resources and/or O&M configuration errors.
5. 5G/6G Network Protection Organization
- 1.
- The use of a powerful firewall between users and the outside world, multi-level isolation and integrity protection of SDN and VNF components—hypervisor, virtual machines, OS, controllers and containers.
- 2.
- MEC application authentication, using an additional authentication factor when accessing the corporate network, whitelisting devices and services ands authorizing API requests.
- 3.
- Providing high availability of virtual machines for fast recovery after attacks.
- 4.
- A trusted hardware environment—a secure device boot and the application of Trusted Execution Environment (TEE) technology.
- 5.
- Real-time attack detection on network nodes and virtual infrastructure elements using artificial intelligence algorithms.
- 1.
- Secure management of not only user data but also service, technical, analytical and other types of information involved in solving SH problems (the so-called attack on a subscriber and an attack on a mobile operator), using encryption, anonymization, depersonalization, etc.
- 2.
- Centralized management of identified vulnerabilities, as well as policies and levels of information security, the use of information during the ongoing analysis of big data to detect anomalies and quickly respond to attacks.
- 3.
- Comprehensive use of counterfeit base station detection tools based on the real-time monitoring of operation and maintenance events.
- 4.
- The application of multi-factor authentication algorithms and organization of access control to segments by O&M.
- 1.
- Separating the layers of the data transmission and reception protocol into three planes: the User Plane, Control Plane and Management Plane. Each separate plane has its own entire isolation, encryption and integrity control.
- 2.
- Using encryption methods for subscriber and technological traffic with an increase in the length of the encryption key from 128 to 256 bits.
- 3.
- Using a single subscriber authentication mechanism for various types of wireless communications.
- 4.
- Supporting flexible protection policies for segments.
- 5.
- Using unified standards.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Streitz, N. Beyond ‘Smart-Only’ Cities: Redefining the ‘Smart-Everything’ Paradigm. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 791–812. [Google Scholar] [CrossRef]
- The International Telecommunication Union (ITU). Available online: https://www.itu.int/en/mediacentre/backgrounders/Pages/smart-sustainable-cities.aspx (accessed on 8 November 2022).
- Bogdanov, A.; Shchegoleva, N.; Dik, G.; Khvatov, V.; Dik, A. “Smart Habitat”: Features of Building It Infrastructure, Main Problems of Building Data Networks Using 5G (6G) Technologies. In Computational Science and Its Applications—ICCSA 2022 Workshops; Lecture Notes in Computer Science; Gervasi, O., Murgante, B., Misra, S., Rocha, A.M.A.C., Garau, C., Eds.; Springer: Cham, Switzerland, 2022; Volume 13380, pp. 628–639. [Google Scholar]
- Trindade, E.P. Sustainable Development of Smart Cities: A Systematic Review of the Literature. J. Open Innov. Technol. Mark. Complex. 2017, 3, 11. [Google Scholar] [CrossRef] [Green Version]
- Drozhzhinov, V.I.; Kupriyanovskii, V.P.; Namiot, D.E.; Sinyagov, S.A.; Kharitonov, A.A. Smart cities: Models, tools, rankings and standards. Int. J. Open Inf. Technol. 2017, 5, 19–48. [Google Scholar]
- Argunova, M. The “Smart City’’ Model as a Manifestation of the New Technological Mode. Sci. Sch. 2016, 3, 14–23. [Google Scholar]
- Mityagin, S.; Karsakov, A.; Bukhanovsky, A.; Vasiliev, V. “Smart St. Petersburg”: An integrated approach to the implementation of information technologies for managing a metropolis. Control. Eng. Russ. 2019, 1, 19–25. [Google Scholar]
- Popov, E.V.; Semyachkov, K.A. Optimization of the urban environment digitalization processes. Probl. Territ. Dev. 2019, 5, 53–63. [Google Scholar] [CrossRef]
- Recupero, D.R. An Innovative, Open, Interoperable Citizen Engagement Cloud Platform for SmartGovernment and Users’ Interaction. J. Knowl. Econ. 2016, 7, 388–412. [Google Scholar] [CrossRef] [Green Version]
- Anti-Malware. Available online: https://www.anti-malware.ru/analytics/Threats_Analysis/smart-cities-threats-opportunities (accessed on 6 November 2022).
- Kupriyanovskiy, V.P. On Standardization of Smart Cities, Internet of Things and Big Data. The Considerations on the Practical Use in Russia. Int. J. Open Inf. Technol. 2016, 2, 34–40. (In Russian) [Google Scholar]
- Postscapes. Available online: https://www.postscapes.com/iot-voices/interviews/iot-interview-series-5-questions-rob-van-kranenburg-internet-things-council (accessed on 5 November 2022).
- IETF Journal. Available online: https://www.ietfjournal.org/the-internet-of-things-unchecked/ (accessed on 27 November 2022).
- Gupta, A. Big Data & Analytics for Societal Impact: Recent Research and Trends. Inf. Syst. Front. 2018, 20, 185–194. [Google Scholar]
- Boyes, H.; Hallaq, B.; Conningham, J.; Watson, T. The industrial internet of things (IIoT): An analysis framework. Comput. Ind. 2018, 101, 1–12. [Google Scholar] [CrossRef]
- Shchegoleva, N.; Zalutskaya, N.; Dambaeva, A.; Kiyamov, J.; Dik, A. New Technologies for Storing and Transferring Personal Data. In Computational Science and Its Applications—ICCSA 2022 Workshops; Lecture Notes in Computer Science; Gervasi, O., Murgante, B., Misra, S., Rocha, A.M.A.C., Garau, C., Eds.; Springer: Cham, Switzerland, 2022; Volume 13380. [Google Scholar] [CrossRef]
- Cnews. Available online: https://www.cnews.ru/articles/2020-04-21_cherez_tri_goda_na_kazhdogo_rossiyanina (accessed on 27 November 2022).
- Jakovlevich, C.V. Internet of Things as a Global Infrastructure for the Information Society; Modern Management Technology: Kirov, Russia, 2017; Volume 6, p. 7803. ISSN 2226-9339. Available online: https://sovman.ru/article/7803/ (accessed on 5 November 2022).
- Minerva, R.; Biru, A.; Rotondi, D. Towards a Definition of the Internet of Things (IoT). 2015. Available online: http://iot.ieee.org/images/files/pdf/IEEE_IoT_Towards_Definition_Internet_of_Things_Revision1_27MAY15.pdf (accessed on 27 November 2022).
- Derevyashkin, V.M.; Virkunin, A.O.; Maksimov, A.S.; Rozhentsev, V.L. Analysis of radio access technologies for the implementation of the smart house system. Mod. Probl. Telecommun. 2018, 1, 526–529. [Google Scholar]
- Roberto Sandre. Thread and ZigBee for Home and Building Automation Systems Engineer. Texas Instruments. 2018. Available online: https://www.ti.com/lit/wp/sway012/sway012.pdf (accessed on 5 November 2022).
- Control Engineering Russia. Available online: https://controleng.ru/besprovodny-e-tehnologii/putivoditel-iot-3-wi-fi/ (accessed on 5 November 2022).
- Bluetooth. Available online: https://www.bluetooth.com/learn-about-bluetooth/tech-overview (accessed on 5 November 2022).
- Olsson, J. 6LoWPAN Demystified. Texas Instruments. 2014. Available online: https://www.ti.com/lit/wp/swry013/swry013.pdf (accessed on 5 November 2022).
- Wltd. Available online: https://wltd.org/posts/thedifferences-between-z-wave-versions-made-easy (accessed on 5 November 2022).
- Letfullin, I.R. Standards and Technologies of Short-Range Wireless Communication Networks; Trudy MAI: Moscow, Russia, 2022; p. 124. [Google Scholar] [CrossRef]
- Onizawa, T.; Tatsuda, T.; Kita, N.; Yamashita, F. Recent research and developments focusing on fixed wireless and satellite communication systems. IEICE Tech. Rep. 2019, 32, 53–58. [Google Scholar]
- Nakamura, T. 5G Evolution and 6G. In Proceedings of the 2020 International Symposium on VLSI Design, Automation and Test (VLSI-DAT), Hsinchu, Taiwan, 10–13 August 2020; p. 1. [Google Scholar] [CrossRef]
- Securitylab. Available online: https://www.securitylab.ru/news/502542.php (accessed on 6 November 2022).





| The Main Branches and Directions of Vitality | Scope of Application |
|---|---|
| IT and means of communication | Modern types of communications and communications (5G/6G); cloud services; providing remote access; billing in telecommunications. |
| Engineering and dispatching | Intelligent planning and control systems production, quality management, etc.; intelligent warning systems (city services, etc.); smart technologies for emergency and urban services. |
| Trade | New forms of mutual settlements; remote banking technologies; using big data to conduct targeted marketing campaigns; using q-code; electronic services and service delivery portals. |
| Smart transport | Intelligent control systems/traffic restrictions; video mapping; smart city navigation systems; intelligent public management systems transport; systems for collecting fees, fees, duties, taxes, etc. |
| Industry [15] | Intelligent technologies for enterprise resource planning (ERP solutions), finding bottlenecks and auditing; green technologies; systems that reduce emissions of CO2 and harmful substances; monitoring and notification of emergencies; robotization of production. |
| Healthcare | Intelligent technologies for diagnosis patients based on big data analysis; IoT to control the distribution of drugs, etc.; bionics—new biomaterials and cell technologies in transplantology; telemedicine; color QR codes according to images of faces and a device for implementation [16]. |
| Consumer sector and home | Ensuring energy efficiency (classes, BREAM/LEED); modern automated control systems in the management of buildings and structures; home systems for individual analysis resource and energy consumption. |
| Power industry [17] | Management information system for resource and energy saving in production; electricity supply and demand management—smart energy market; micro grid—ensuring energy autonomous objects. |
| Construction | Building information modeling and structures; smart houses; energy-passive and active houses; green houses; technologies that ensure the mobility of personnel and their ability to perform more tasks per unit of time. |
| Agriculture | Smart devices and monitoring applications patients’ conditions; satellite monitoring systems for animals (where they are and whether they got lost during the walk); intelligent systems for managing financial and economic activities. |
| Logistics | Big data in the management of logistics companies; satellite monitoring systems for transport routes. |
| Wireless Technology | ZigBee | Wi-Fi | Bluetooth LE | LoRaWan | Z-Wave |
|---|---|---|---|---|---|
| frequency range | 2.4–2.483 GHz | 2.4–2.483 GHz | 2.4–2.483 GHz | 2.4–2.483 GHz | 868.42 MHz, 908.42 MHz, 921.42 MHz, 919.8 MHz, 865.2 MHz, 868.20 MHz, 951–956 MHz, 922–926 MHz. |
| Bandwidth, kbp/s | 250 | 11,000 | 1024 | 250 | 42 |
| Protocol stack size, Kb | 32–64 | 1000 and more | 250 and more | 20 and more | 32 |
| Maximum number of nodes in the network | 65,536 | 10 | 7 | 500 | 232 |
| Action range, m (average value) | 10–100 | 20–300 | 10–100 | 10–110 | 40–120 |
| Current consumption, active mA/sleep mkA | 30/1 | 450/- | 15/10 | 20/1 | 22/1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dik, G.; Bogdanov, A.; Shchegoleva, N.; Dik, A.; Kiyamov, J. Challenges of IoT Identification and Multi-Level Protection in Integrated Data Transmission Networks Based on 5G/6G Technologies. Computers 2022, 11, 178. https://doi.org/10.3390/computers11120178
Dik G, Bogdanov A, Shchegoleva N, Dik A, Kiyamov J. Challenges of IoT Identification and Multi-Level Protection in Integrated Data Transmission Networks Based on 5G/6G Technologies. Computers. 2022; 11(12):178. https://doi.org/10.3390/computers11120178
Chicago/Turabian StyleDik, Gennady, Alexander Bogdanov, Nadezhda Shchegoleva, Aleksandr Dik, and Jasur Kiyamov. 2022. "Challenges of IoT Identification and Multi-Level Protection in Integrated Data Transmission Networks Based on 5G/6G Technologies" Computers 11, no. 12: 178. https://doi.org/10.3390/computers11120178
APA StyleDik, G., Bogdanov, A., Shchegoleva, N., Dik, A., & Kiyamov, J. (2022). Challenges of IoT Identification and Multi-Level Protection in Integrated Data Transmission Networks Based on 5G/6G Technologies. Computers, 11(12), 178. https://doi.org/10.3390/computers11120178







