Abstract
To solve problems with limited resources such as power, storage, bandwidth, and connectivity, efficient and effective data management solutions are needed. It is believed that the most successful algorithms for circumventing these constraints are those that self-organise and collaborate. To make the best use of available bandwidth, mobile ad hoc networks (MANETs) employ the strategy of multi-casting. The communication cost of any network can be significantly reduced by multi-casting, and the network can save resources by transmitting only one set of data to numerous receivers at a time. In this study, we implemented multi-casting in the virtual cord protocol (VCP), which uses virtual coordinates (VC) to improve effective routing and control wireless data transmission. We have improved the classic VCP protocol by making it so that intermediate nodes can also forward or re-transmit the dataset to interested nodes. This improves data transmission from the sender to multiple receivers. Simulation results proved efficacy of our proposed enhanced virtual cord protocol-based multi-casting strategy over traditional VCP protocol and helped in reduction of number of MAC transmissions, minimization of end-to-end delay, and maximization of packet delivery ratio.
1. Introduction
Solutions for efficient and effective data management are required to address issues with scarce resources, such as power, storage, bandwidth, and connectivity of communicating devices. The algorithms that self-organize and cooperate are seen to have the best chances of overcoming these restrictions. Mobile ad hoc networks (MANETs) use multi-casting as a way to optimise the utilisation of available bandwidth. Multi-casting allows networks to save resources by sending only one set of data to many receivers at once, dramatically reducing the cost of communication for any network.
Multi-cast routing is an efficient way to establish group communication from the sender to multiple receivers when the same set of data is to be transmitted [1]. The main goal of multi-casting is to make the best use of the available bandwidth. Multiple senders can send their data to multiple receivers, simultaneously. However, each sender node has its group members that receive data via multi-casting. The destination can be a group of multiple receiver nodes or selected nodes from single or multiple groups.
A group of dynamic collection of nodes with rapidly changing multi-hop topology is known as mobile ad-hoc network (MANET) [2,3,4]. In MANET, group members are dynamic and can join and leave multi-cast groups at any time, and the movement of nodes is arbitrary. A node can join a single group or multiple groups simultaneously. In MANETs [5,6,7,8,9,10,11,12,13], communication within the network uses nodes, which can be mobile devices, PDAs, tablets, laptops, etc., with Bluetooth, infrared, and Wi-Fi technologies. MANETs can distribute snapshots, audios and videos through its communication technology. In MANETs, it is also possible for a node to forward data packets as a router, but not be a member of this multi-casting group.
There are two types of routing: first is the traditional routing that is used at the time of network creation, as discussed in [14,15], where various techniques are implemented, typically based on flooding. This technique is easy and simple to implement, but it has a critical issue large communication overhead. Available traditional multi-casting protocols are based on flooding. The distance vector multi-cast routing protocol (DVMRP) [16] is an example of traditional multi-casting. DVMRP constructs a source-based multi-cast tree for each source node by using a backward path algorithm. This protocol relies on flooding to create a multi-cast group. Flooding is a waste of bandwidth and battery power. Moreover, it keeps the processor busy.
The second type of routing in MANETs is distributed hash table (DHT) algorithm, which is applied to the public key or IP/MAC addresses to search/implement unique values for logical or physical identification of the node. These DHT-based routing techniques [17,18,19,20] are reliable, efficient, robust, and effective as compared to traditional routing-based techniques. Various protocols have been introduced to solve all the above problems suitable for MANETs. Some well-known protocols have been studied, classified and compared in [21,22,23,24].
Multi-casting has not yet been implemented in virtual cord protocol (VCP) [25] or any other DHT routing-based protocol. which takes advantage of virtual coordinates to improve efficient routing and manage data communication wirelessly. In the VCP network, all nodes are virtually connected to each other. The main idea of virtual ring routing (VRR) [26,27] is based on location independent hierarchy without flooding in the network. Virtual ring routing provides both traditional point-to-point network routing and DHT routing to the node. The routing protocol discussed in [28,29] is an example of traditional multi-casting. The main contributions of this study are described below.
- In this study, an enhanced VCP protocol for multi-casting in a DHT-based network has been implemented to save network bandwidth and battery power by exploiting virtual coordinates (VC) and low aspect ratio of VCP protocol.
- We modified traditional VCP protocol and transmission of data from the sender to multiple receivers is improved in a way that intermediate nodes can also forward or re-transmit the data to interested nodes.
- Flooding leads to wastage of network resources. In this study, flooding is avoided by using VCP for multi-casting purpose.
- Reduced number of MAC transmissions, minimized end-to-end delay, and maximized packet delivery ratio are the significant contributions of our proposed enhanced virtual cord protocol-based multi-casting strategy.
Rest of the paper is organized as follows. Section 2 uncovers the background and state-of-the-art literature. Problem statement and the proposed system model are described in Section 3 of this paper. Section 4 presents simulation setup, methodology, results and discussions. Section 5 concludes our study with a discussion of future work.
2. Background and Literature Review
This section first introduces the background of routing protocols, especially the virtual cord protocol, and then discusses the current literature.
2.1. Route Discovery
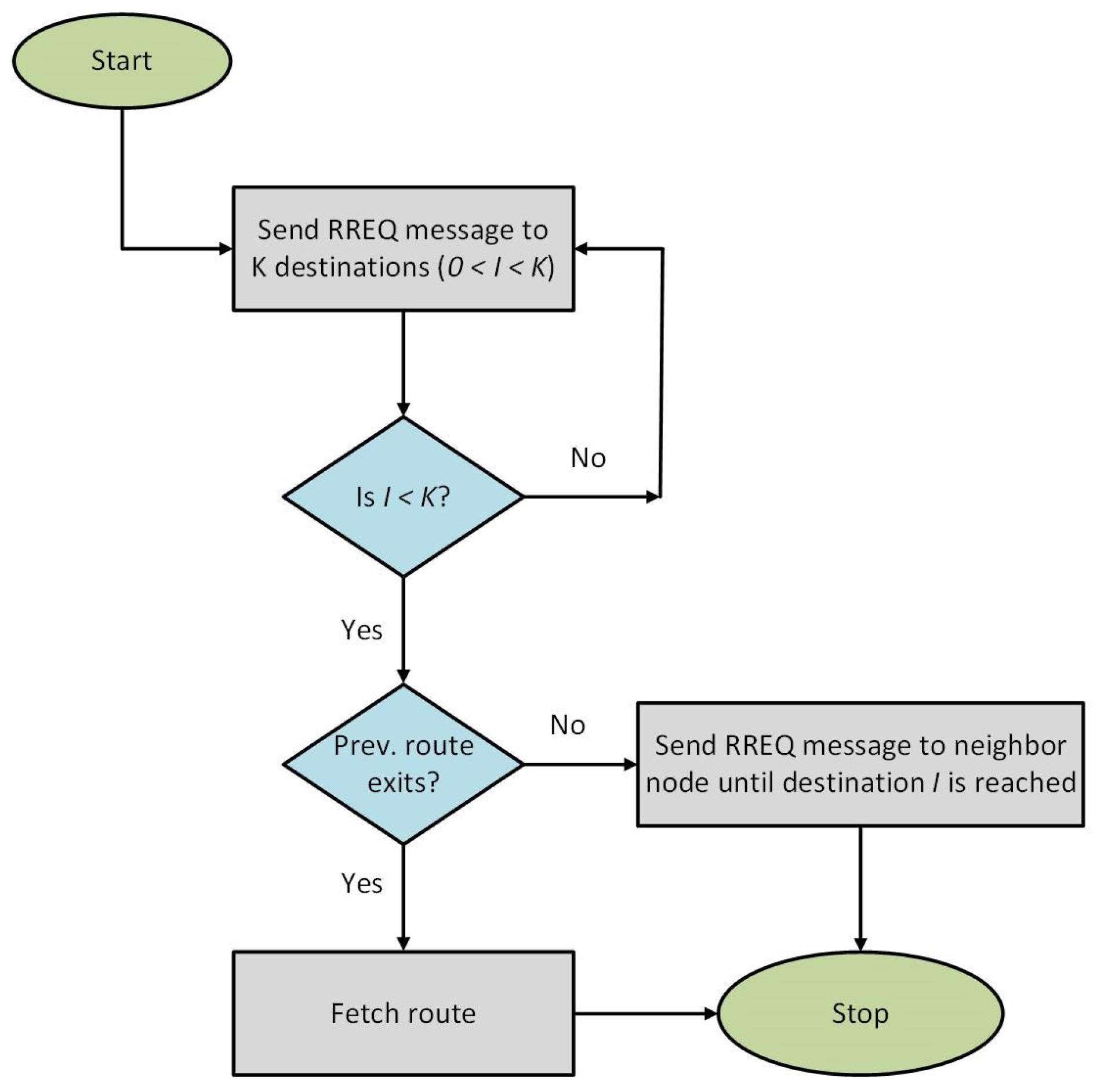
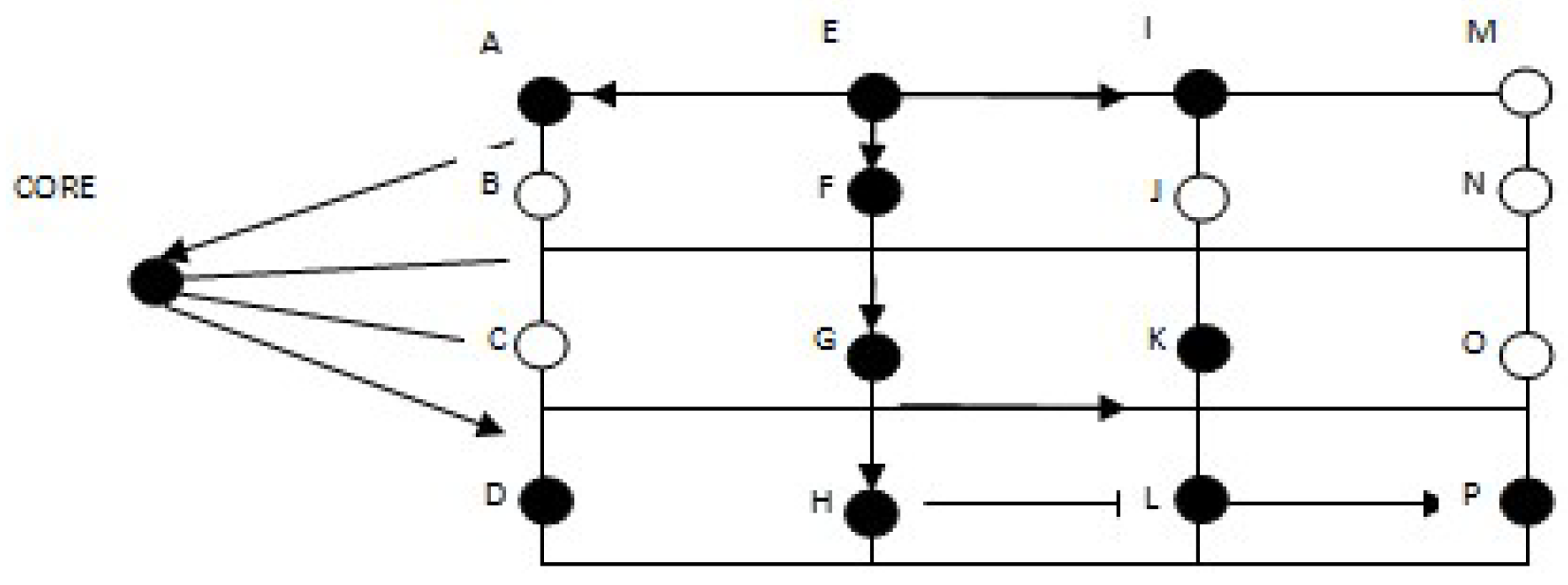
Route discovery is an important feature of all routing protocols where the source node “S” broadcasts its route request message along with its ID and desired destinations IDs. The source node’s neighbor matches its ID with the desired destination IDs of the message. If it is not a destination node and has no path information to the destination node, it re-transmits the same message and adds its ID. In the second case, if the node is a destination node, it replies directly, or if it has a cached route to communicate with, it retrieves the cached route for communication. Data flow diagram for discovery of routes is shown in Figure 1 and a typical route discovery algorithm is shown in Algorithm 1.
| Algorithm 1: Pseudo-code for route discovery |
| Set S as source Set |
| D1 to DN as destinations |
| Broadcast sourceID, destinationIDs in RREQ |
| For (Destinations 1 to N) |
| While (node != Destination) |
| If any familiar route exists |
| Do not broadcast RREQ Fetch route |
| else |
| Broadcast RREQ |

Figure 1.
Data flow diagram for discovery of routes.
In case of node failure along the path, it is necessary to quickly repair the connection or use an alternate path to deliver the data packet and the failure may result in a lower delivery rate. Mesh protocols are better in terms of robustness [30].
2.2. Virtual Cord Protocol (VCP)
The virtual cord protocol is a DHT-like protocol that, in addition to providing the typical DHT operations such as insert, get, and delete, also provides an effective routing mechanism [25]. Aside from effective routing, the following features of this protocol are crucial.
- It is easier and simpler to be implement the protocol at the MAC layer.
- Since VCP requires only knowledge of direct neighbours for routing, it is scalable.
- A node’s immediate environment includes both its predecessors and successors, reducing the communication load when nodes join or leave the network.
- Greedy routing along the cable always leads to a path to the destination. It cannot be affected by packets stuck in dead ends.
- There is no need to know the exact position, which could be expensive in terms of communications or system requirements. Instead, we use a simple relative position.
- To enable effective and fault resistant routing and data management, the virtual cord protocol uses virtual coordinates.
- Energy, bandwidth, storage, and communication constraints can all be addressed with VCP based on virtual relative position/coordinates and its low aspect ratio.
2.3. Literature Review
The most relevant literature review, with respect to our proposed enhanced multi-cast protocol (EMP) is presented in the following.
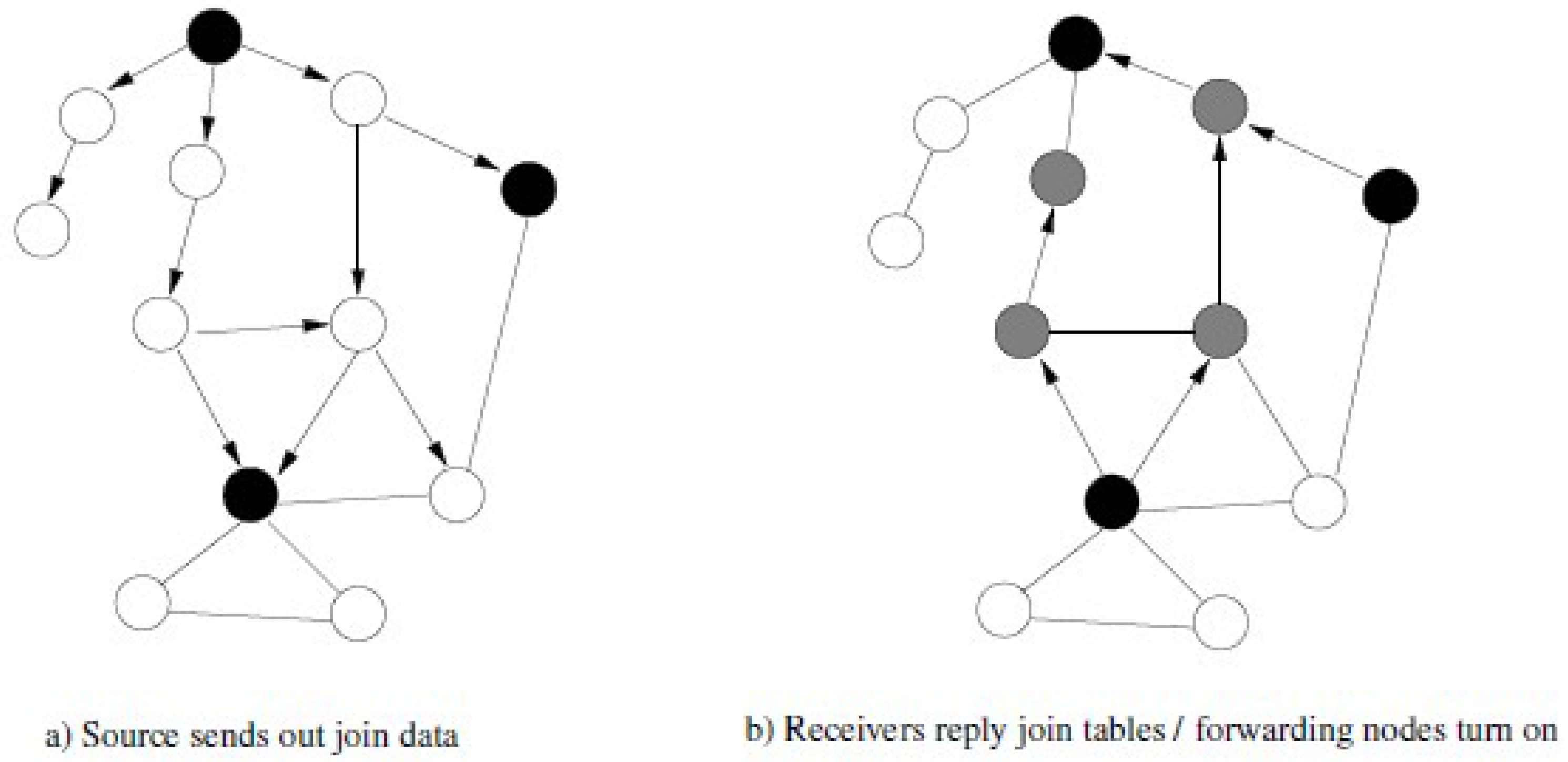
Authors of [31,32] have described dynamic changes in network topology as the main challenge of DHT-based multi-casting. Other challenges include dealing efficiently with frequent and unpredictable changes in the network topology, host failure, link disruption, joining of new nodes, and merging of two networks, etc. The mesh-based multi-cast routing scheme presented in [33] and its results in this paper have been compared with the on-demand multicast routing protocol (ODMRP). Figure 2 depicts the structure of forwarding mesh in ODMRP.
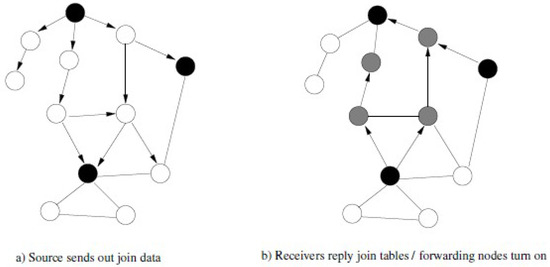
Figure 2.
Structure of forwarding mesh in on-demand multicast routing protocol (ODMRP).
A new multi-cast approach “explicit multi-cast protocol E2M” for a small group of MANETs is discussed in [34] and a multi-cast technique called familiar route retrieval multi-casting (FRRM) is presented in [35] to efficiently retrieve the nodes route based on route awareness. The proposed system was compared with route driven gossip (RDG) protocol in a network simulator and the results proved the effectiveness of FRRM protocol.
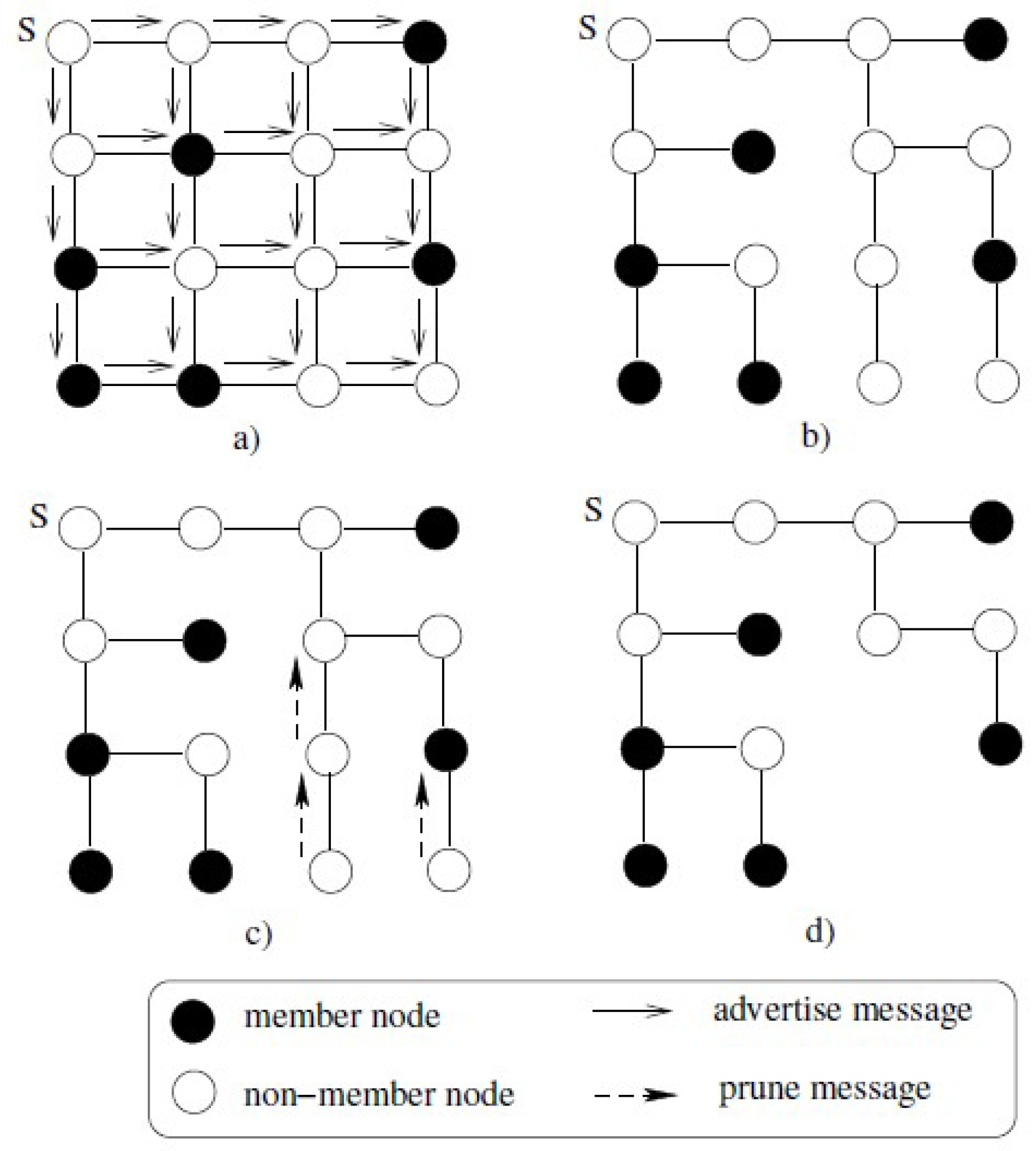
The author of [16] presents a distance vector multi-cast routing protocol (DVMRP) for each source node using the reverse path algorithm. The operation of DVMRP can be divided into two main phases. In the first phase, the source node broadcasts an announcement message to the network. In the second phase, the neighbor or intermediate nodes in the network forward this announcement message to other nodes in the network. DVMRP constructs a source-based multi-cast tree for each source node by using a backward path algorithm. This protocol relies on flooding to create a multi-cast group. Message propagation or joining among member and non-member nodes of DVMRP is shown in Figure 3.

Figure 3.
Message propagation in distance vector multi-cast routing protocol (DVMRP).
The simple mesh-based multi-casting network protocol discussed in [36] uses the concept of forwarding nodes. The mesh-based multi-casting network protocol uses some nodes (group members or non-group members) as forwarding nodes for network communication.
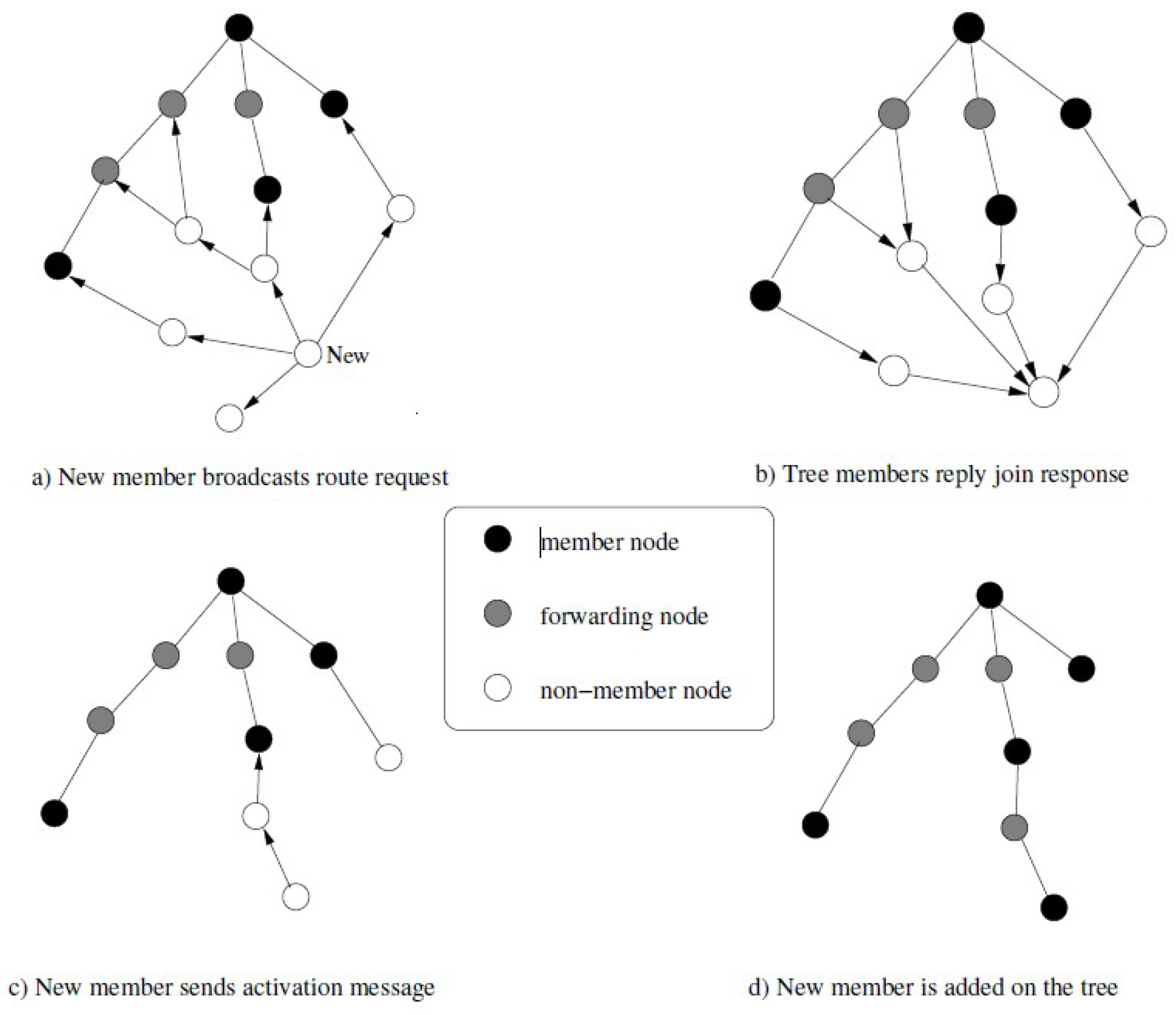
The multi-cast ad hoc on-demand distance vector (MADOV) routing protocol proposed in [37] uses broadcasting and finds the route for multi-casting on demand and then constructs a routing tree based on common ground. When a node wants to connect to a network or has data to transmit, it sends a RREQ message to the network with a route request. MADOV network topology is shown in Figure 4 of this study.

Figure 4.
Network topology of multi-cast ad hoc on-demand distance vector (MADOV) protocol.
Using a single path between multiple nodes using a multi-cast tree can improve the efficiency and simplicity of the network. However, the use of a multi-cast tree (split/unshared) has some disadvantages. For example, in a split multi-cast tree, packets are distributed along with the path in the multi-cast group. This path may be longer between source and destination than the direct shortest path from sender to receivers. For these reasons, the core-assisted mesh protocol (CAMP) was introduced by the authors of [38]. This technique distributes information within each multi-cast group by establishing and maintaining a multi-cast mesh. Figure 5 describes the traffic flow of router in a multi-cast mesh network (MMN).
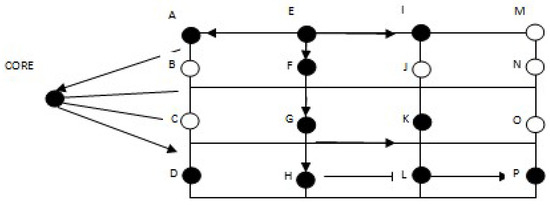
Figure 5.
Traffic flow of router in a multi-cast mesh network (MMN).
In [39], when a new node wants to join an existing group, it sends a join query (JQ) message to the members of that multi-cast group. The member nodes send a response in the form of a JQ Reply message. When a node wants to leave an ABMRP multi-cast group, it sends a Leave message to separate from the group. If the node was not able to send a Leave message, network partitioning may occur. The adaptive demand-driven multi-cast routing (ADMR) protocol proposed in [40] is a source-based tree multi-casting protocol that uses broadcasting to create a group.
ADMR can adjust its performance based on the application’s transmission model. Data is forwarded using the shortest available path. In this method, data can be forwarded in two ways: using a flooded tree and network flooding. When a node detects a broken link in the network, it starts local repair, sends a repair notification to other nodes, and waits for the repair. In MANETs, multi-casting in the downstream/upstream link state causes a lot of overhead and is, therefore, inefficient. Forward group multi-cast protocol (FGMP) networks track groups of nodes instead of links for multi-casting data packets [41]. In a multi-cast group network, the G is associated with the forwarding group FG. All nodes in the group FG are responsible for the multi-casting of data packets transmitted by G.
The dynamic access routing (DART) protocol discussed in [42] is a proactive routing protocol. DART is similar to tribe at a high level, which works on the basis of node addresses by splitting the address into two parts, where one part is dynamic for routing and the second part is static for node identification. By offering adaptable mesh-oriented structures, the authors of [43] have suggested a unique method named as dense multi-cast zone routing protocol for robust multi-cast in mobile ad hoc networks. The term “dense one,” which refers to a significant concentration of multi-cast participants in a particular network area, is introduced in this paper. For multi-cast data transmission in ad hoc networks, this idea offers greater stability and scalability.
3. Problem Statement and Proposed System Model
3.1. Problem Statement
Today’s highly dynamic networks are very complex and operate cooperatively and self-organised in the face of limited resources such as energy, computing power, storage capacity, and bandwidth. Efficient data management of complex networks is an important issue. Available traditional multi-casting protocols are based on flooding. The distance vector multi-cast routing protocol (DVMRP) is an example of traditional multi-casting protocol. DVMRP constructs a source-based multi-cast tree for each source node by using a backward path algorithm. This protocol relies on flooding to create a multi-cast group. Flooding is a wastage of bandwidth, battery power, and keeps the processor busy. In this study, an enhanced VCP protocol for multi-casting in a DHT-based network was implemented to save network bandwidth and battery power by exploiting the low aspect ratio of the VCP protocol.
To the best of our knowledge, multi-casting has not been implemented in virtual cord protocol or any other DHT-based protocol, prior to this study. We have implemented a source-based-tree structure using the VCP protocol for multi-casting in DHT-based networks. Second, the already traditional multi-casting protocols are based on flooding are implemented. DVMRP [16] is an example of traditional multi-casting. DVMRP constructs a source-based multi-cast tree for each source node using a backward path algorithm. This protocol relies on flooding to create a multi-cast group. Traditional broadcasting in a multi-cast group is shown in Figure 6.
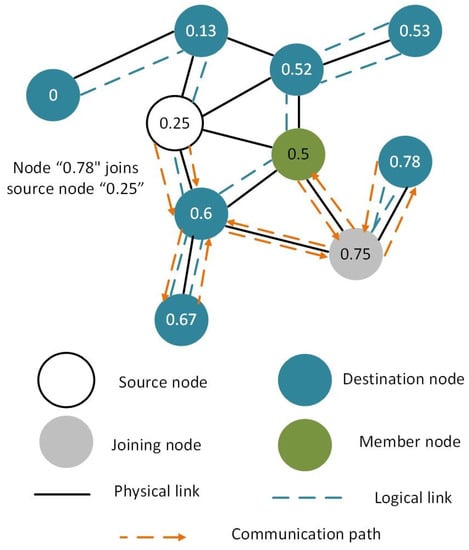
Figure 6.
Traditional broadcasting in multi-cast group.
3.2. Proposed System Model
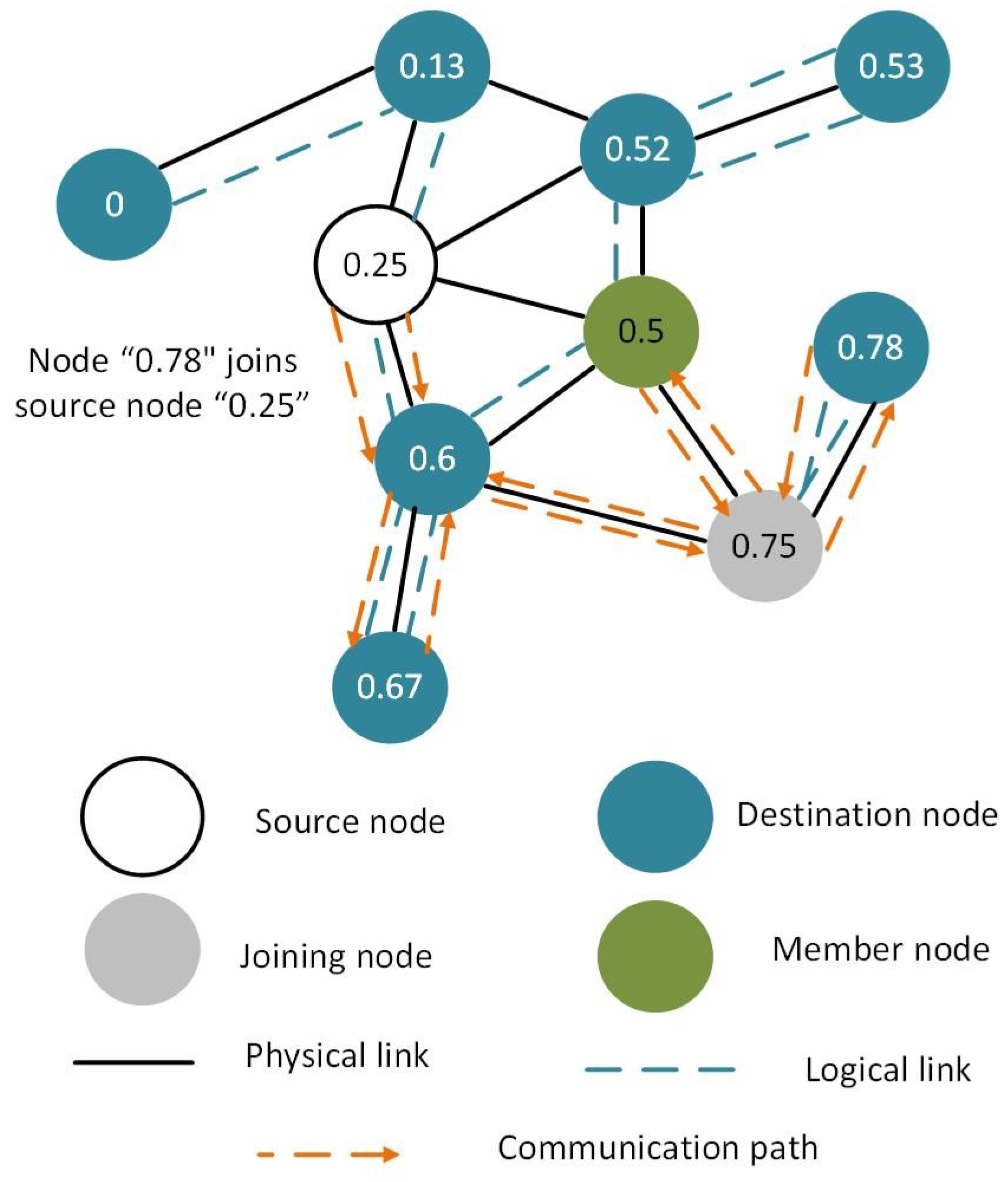
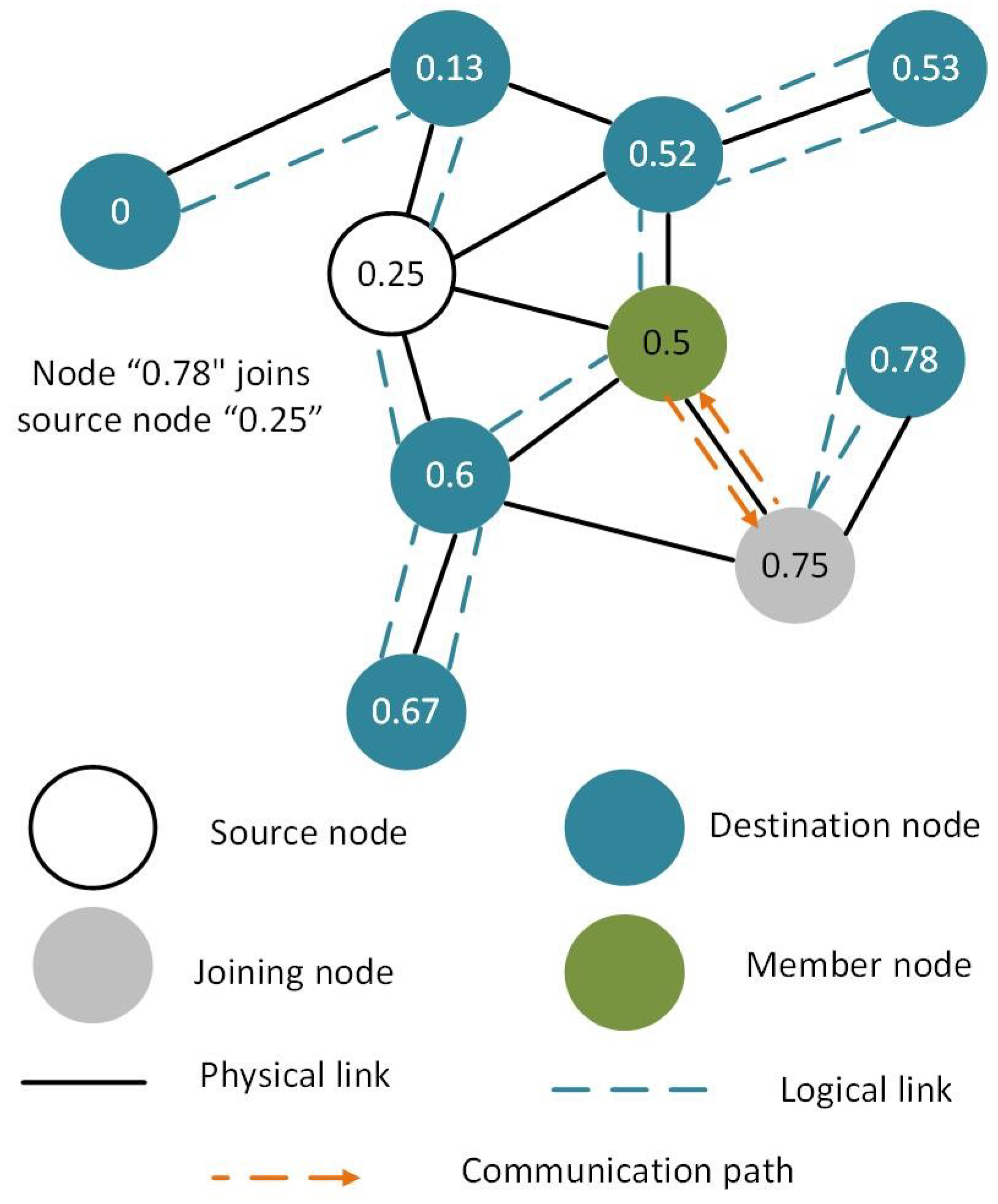
The proposed system model is shown in Figure 7 where all nodes are virtually connected via VCP. The communication between all nodes of the VCP is easier and efficient. It is important to note that the VCP protocol does not allow flooding. However, multi-casting has not been implemented in VCP, so far. In this study, we have implemented multi-casting in VCP without flooding for multi-casting.
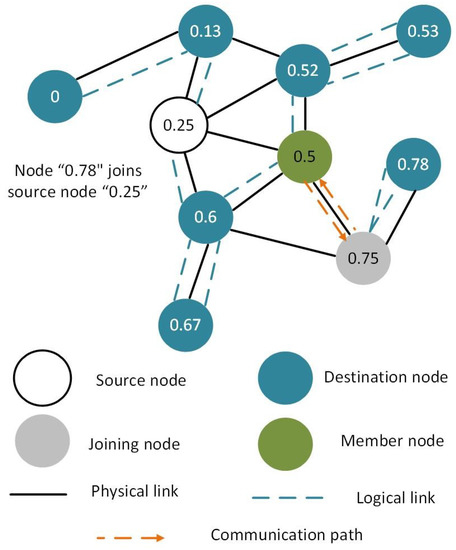
Figure 7.
Proposed system model of enhanced virtual cord protocol.
Assume that in the Figure 7, the source node is node (0.25), which multi-casts the data to the receiver nodes. The node (0.5) is already a member of the multi-cast group that receives messages from the source node (0.25). Now, the leaf node (0.75) is able to receive data from the source node (0.25). In VCP, all nodes arrange themselves in the correct order so that each node knows its predecessor and successor nodes in the network. All nodes also know their logical-physical neighbors in the VCP network. Routing in the network is done by using the virtual cord. Now, the joining node (0.75) applies a hash and obtains ID for the source node (0.25) and its value/address.
The leaf node (0.75) is not physically connected to the source node (0.25). However, it is logically connected to the source node via an intermediate member node (0.5). It sends a uni-cast request through the intermediate connection node (0.5) for joining the multi-cast group. Since, the intermediate node (0.5) is itself a member of the multi-cast group, it responds directly to the requesting node (0.75) and does not send the join message to the source node via uni-cast. The intermediate node (0.5) sends the copy of the message received from a source node (0.25) via uni-cast. This also reduces the additional communication overhead. In addition, VCP also provides the shortest available path between nodes for communication.
4. Experiments and Evaluation
In this section, we present our experiments and results for the evaluation of the proposed VCP protocol model with respect to number of MAC transmissions, end-to-end delay and packet delivery ratio. First, we describe the experimental setup and methodology. Later on, we will present results and discussion.
4.1. Simulation Setup and Methodology
As stated earlier, we have proposed an enhanced VCP protocol for multi-casting in a DHT-based network to save network bandwidth and battery power by exploiting low aspect ratio of VCP protocol. For this purpose we modified traditional VCP protocol and transmission of data from the sender to multiple receivers is improved in a way that intermediate nodes can also forward or re-transmit the data to interested nodes. Flooding is avoided by using VCP for multi-casting purpose to avoid wastage of network resources. The main objectives of this study are; (a) to reduce number of MAC transmissions, (b) minimize end-to-end delay, and (c) to maximize packet delivery ratio.
Network Simulator is an excellent platform for simulation of existing and proposed wired/wireless protocols. Therefore, to implement our proposed enhanced VCP protocol and generate results, we used network simulator-2 (NS-2.35) on the Linux operating system (Ubuntu) using object-oriented language C++ with a combination of TCL. We optimize the results using static and dynamic assignment and compared the difference between results of both cases. Impact of flooding and traffic load performance was analyzed by changing network size. Results of proposed enhanced VCP are compared with traditional VCP protocol.
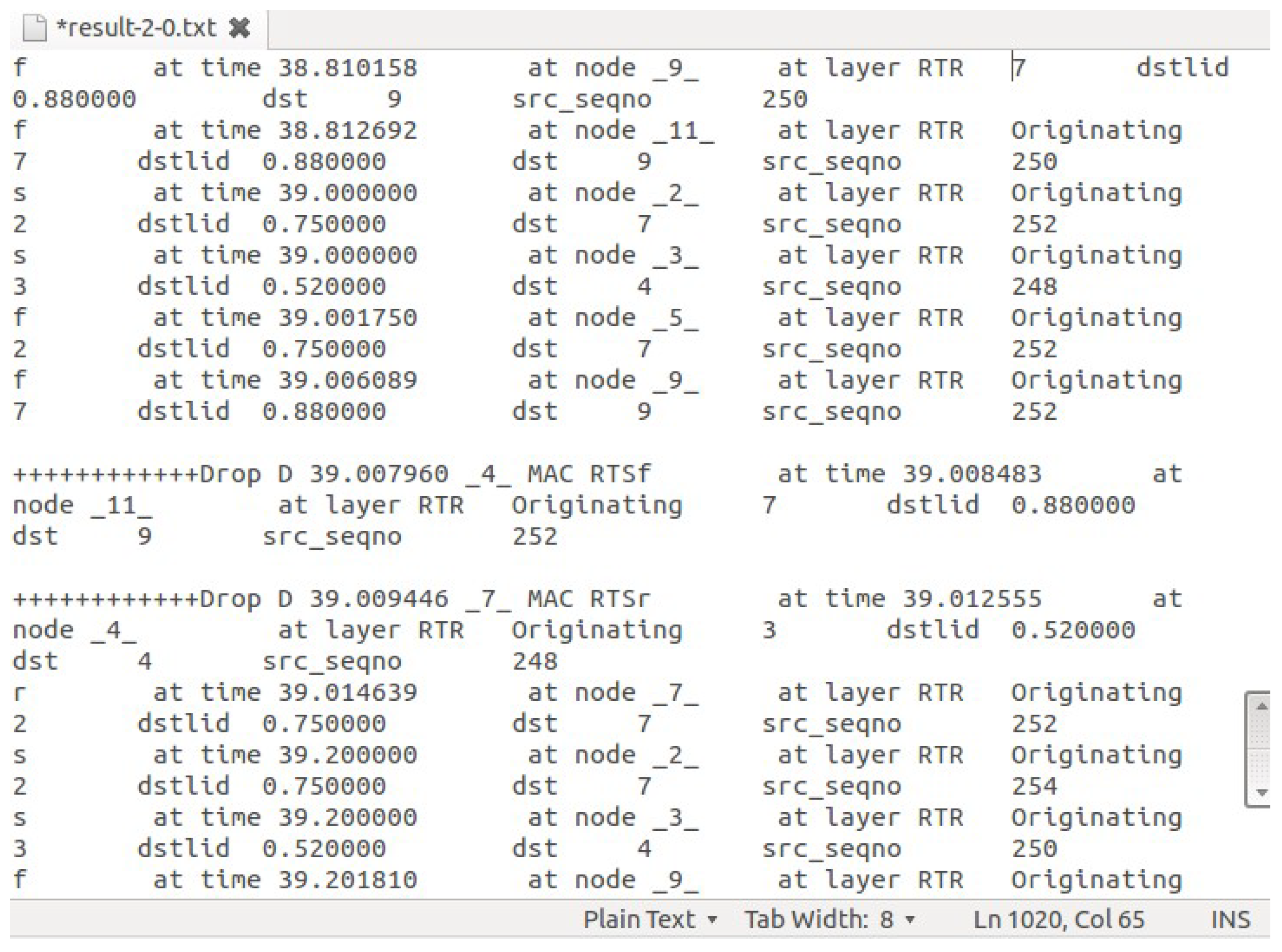
The trace files are automatically generated during simulations at NS-2. Each trace line starts with an event (f, r, d, +, −) descriptor followed by the simulation time (in seconds) of that event, and from source node to the destination node, which identify the link on which the event occurred. Figure 8 shows the trace file indicating source ID, destination ID, layer, sequence number etc. observed during simulations.

Figure 8.
Example of trace file.
4.2. Results and Discussion
Excessive transmission of control messages lead to large overhead and low network performance. The number of transmissions include all transmissions regarding route requests from source node to destination nodes and clear messages from destination node to source node, as well as transmission of data packets such as data ACK, RREQ, RREP, MREQ, MREP, etc. Simulation results for variable number of nodes i.e., from 50 nodes to 150 nodes are summarized in Table 1.

Table 1.
Simulation results.
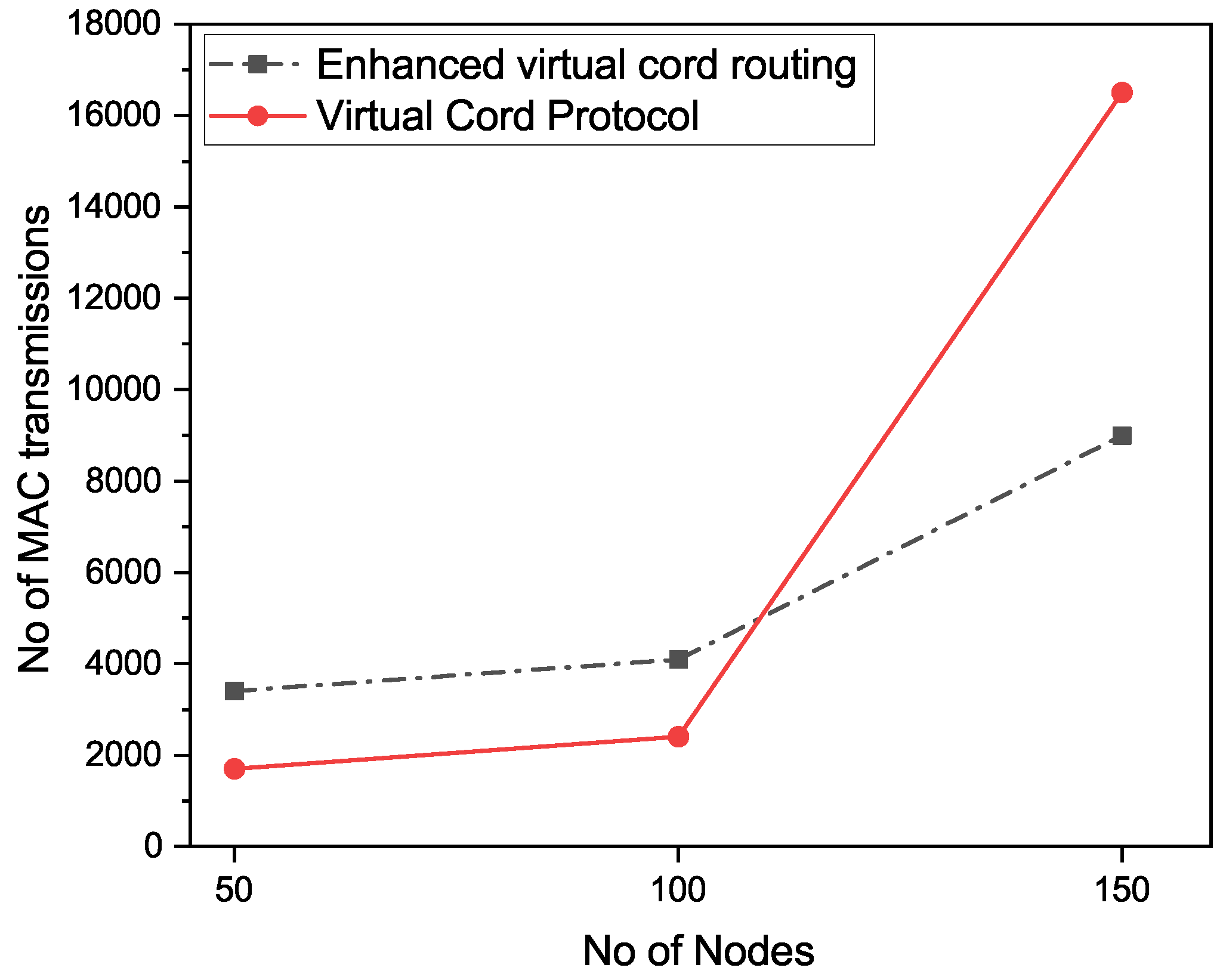
Number of MAC transmissions are shown in Figure 9. The Y-axis in Figure 9 shows the number of MAC transmissions and the X-axis shows the number of nodes. Results show that the number of MAC transmissions in VCP are larger than the number of transmissions in our proposed approach. This clearly shows that our proposed enhanced VCP approach performs better than the existing VCP multi-casting approach.
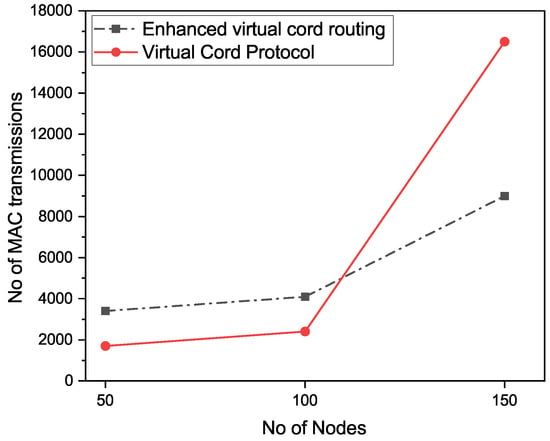
Figure 9.
MAC transmission.
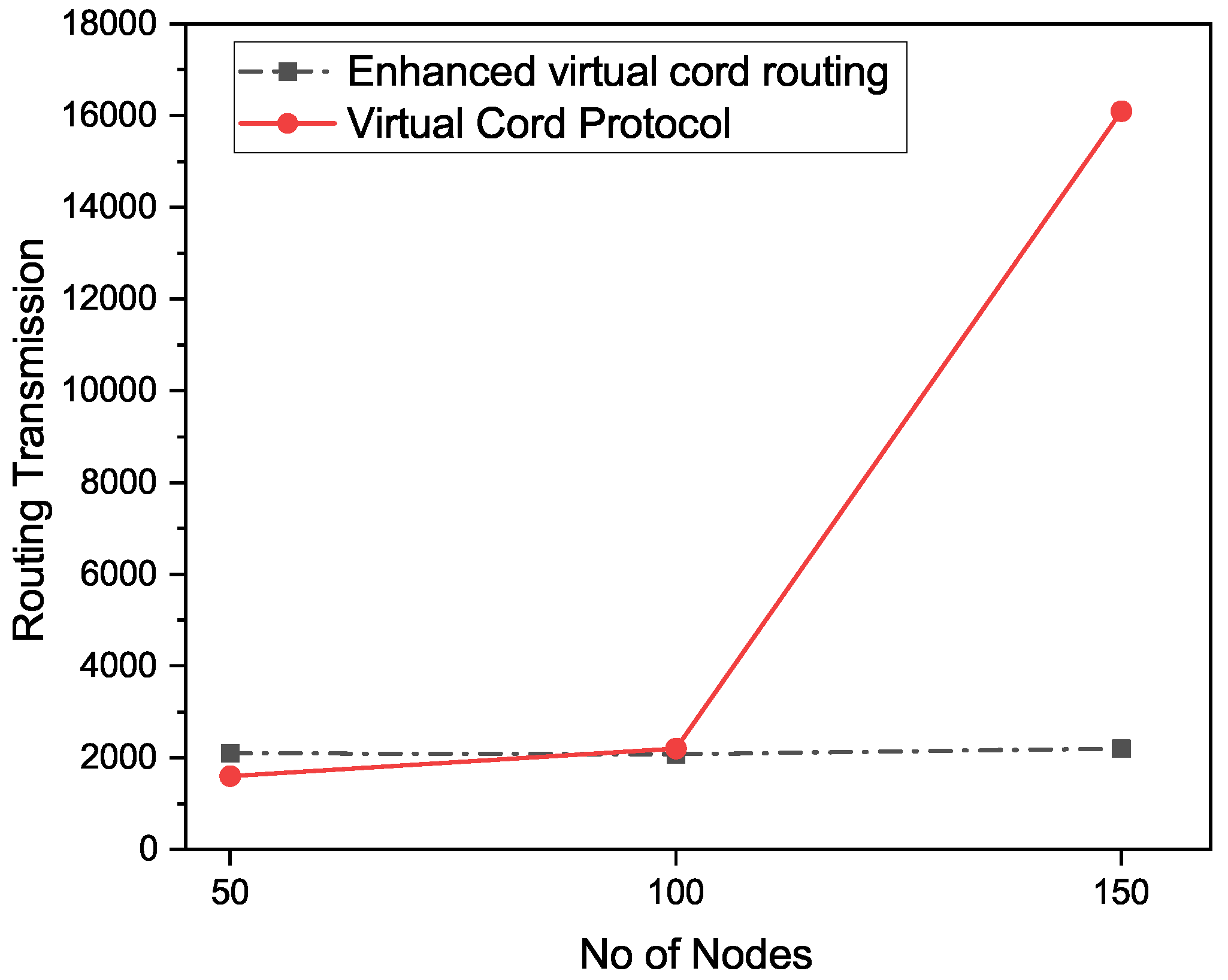
Figure 10 describes the routing information and packet delivery rates. The X-axis represents the number of nodes and the other axis, the y-axis, shows the ratio of delivered packets. The packet delivery in our proposed approach is better than that of the existing VCP approach because the existing approach is not implemented for multi-casting and there is usually more than one receiver in multi-casting techniques, so the delivery rate is better in our proposed system. In this way, the delivery of the packets is increased. As shown above, the performance of the our proposed enhanced VCP approach is better than the performance of VCP.
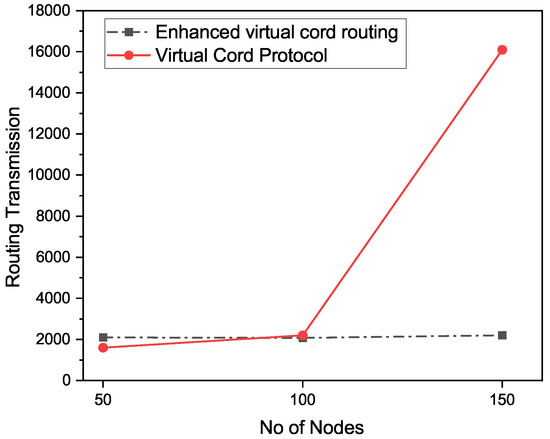
Figure 10.
Routing transmission/Packet delivery ratio.
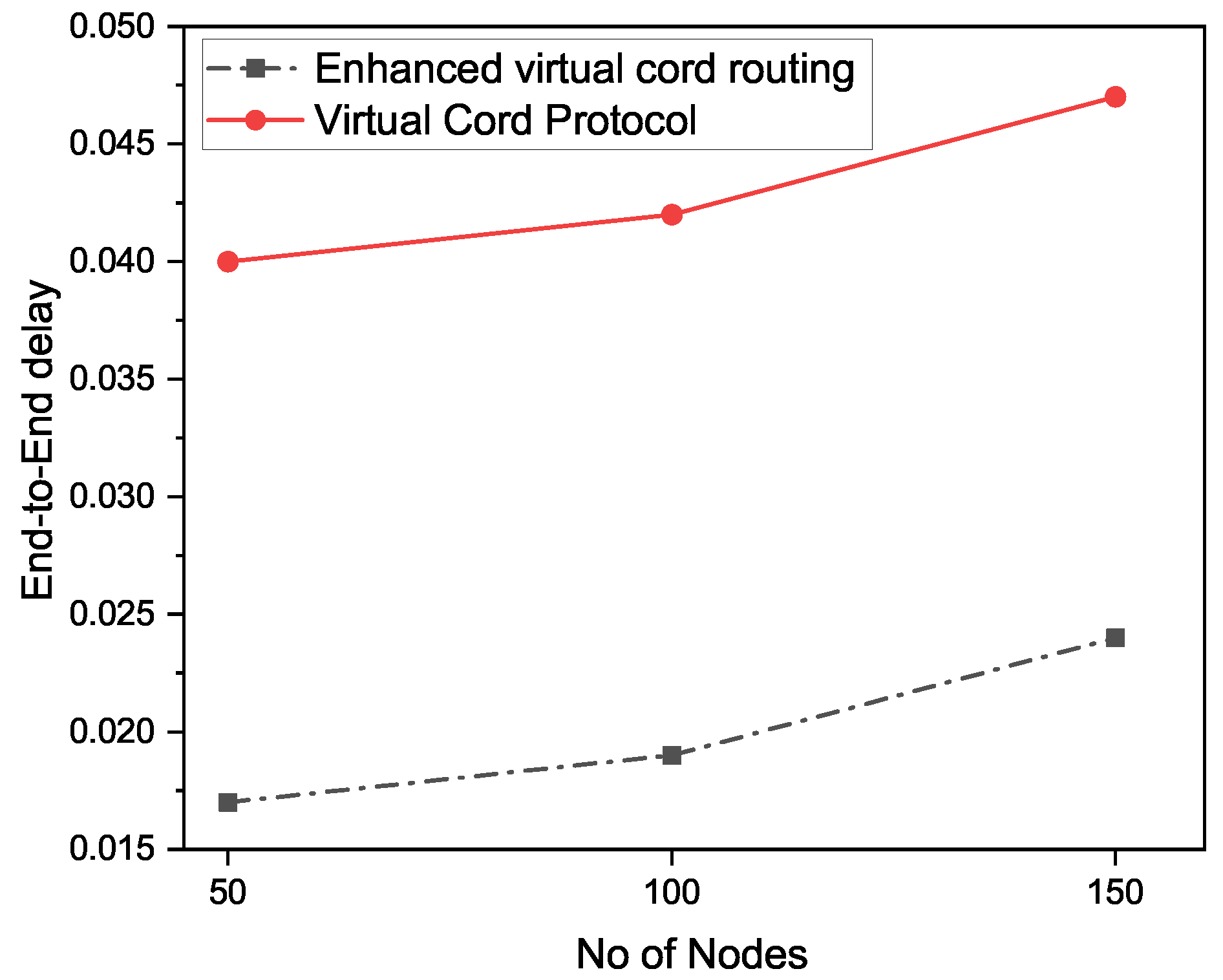
The amount of time taken by a packet to be transmitted from source to destination over a network is known as end-to-end delay or one-way delay (OWD). The end-to-end delay is another performance parameter that is commonly used when comparing existing routing protocols. We also consider this performance parameter for validating our proposed enhanced virtual cord protocol.
Figure 11 shows the comparison of the average end-to-end delay. The end-to-end delay is calculated from the transmission of data from the source to the destination node. The X-axis in Figure 11 shows the number of nodes, and the Y-axis shows the average end-to-end delay. The results in Figure 11 show that our proposed enhanced VCP outperforms the existing approach of VCP.

Figure 11.
Comparison of end to end delay in transmission.
5. Conclusions
In this work, we have proposed an enhanced VCP routing protocol for multi-casting. As far as we know, VCP has not yet been implemented for multi-casting. In our proposed model, we extended VCP for multi-casting purposes and transmitted our data from the source to leaf nodes and then from leaf nodes to other interested receivers of the network nodes. The joining of nodes and the construction of the network are the same in our proposed protocol, as in VCP. However, the transmission of data from the sender to multiple receivers is improved as the intermediate nodes are also able to forward or re-transmit the same data set to interested nodes in the network.
Our proposed enhanced VCP approach is simple and very efficient for implementing multi-casting and also for communication in MANETs. The proposed technique is implemented on VCP with some slight modifications using variable number of nodes i.e., from 50 nodes to 150 nodes to improve the applicability of VCP. For 150 nodes, our proposed technique reduces the number of MAC transmissions by 51.51%, reduces end-to-end delay by 16.36% and increases the packet delivery ratio by 46.80%. This means that our proposed improved VCP multi-cast protocol provides satisfactory results compared to the existing VCP protocol. Our proposed enhanced VCP approach can be used in many scientific and engineering application areas such as smart grid, security surveillance, and traffic monitoring, where data transmission is performed from network station to home stations and vice versa. Furthermore, network interruption detection, attack prevention and energy efficiency of the proposed system need further research, which will be considered in the future.
Author Contributions
S.L.: Conceptualization, Data curation, Methodology, Writing—original draft, Software, Writing—review and editing; X.F.: Supervision, Conceptualization, Methodology, Software, Writing—review and editing, Formal analysis, Project administration, Visualization, Investigation; S.M.M.: Project administration, Visualization, Investigation, Writing—review and editing; Formal analysis; S.M.A.A.: Writing—review and editing; Formal analysis, Methodology, Project administration; S.A.: Writing—review and editing; Formal analysis, Methodology, Investigation, Project administration, Funding acquisition; H.M.: Writing—review and editing; Formal analysis, Methodology, Investigation, Project administration, Funding acquisition; K.U.: Writing—review and editing; Formal analysis, Methodology, Investigation, Project administration. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
Author hereby agree to submit this version of the article at Computers–MDPI and declare no known conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ADMR | Adaptive demand-driven multi-cast routing |
| CAMP | Core-assisted mesh protocol |
| DART | Dynamic access routing |
| DHT | Distributed hash table |
| DVMRP | Distance vector multi-cast routing protocol |
| EMP | Enhanced multi-cast protocol |
| FGMP | Forward group multi-cast protocol |
| FRMM | Familiar route retrieval multi-casting |
| JQ | Join query |
| MADOV | Mmulti-cast ad hoc on-demand distance vector |
| MMN | Multi-cast mesh network |
| MANETs | Mobile ad hoc networks |
| NS-2 | Network imulator-2 |
| ODMRP | On-demand multicast routing protocol |
| RDG | Route driven gossip |
| VC | Virtual coordinates |
| VCP | Virtual cord protocol |
References
- Aghdam, S.M.; Khansari, M. On the better performance of ADMR versus ODMRP. In Proceedings of the 6th International Symposium on Telecommunications (IST), Tehran, Iran, 6–8 November 2012; pp. 621–625. [Google Scholar]
- Sivaram, M.; Porkodi, V.; Mohammed, A.S.; Manikandan, V.; Yuvaraj, N. Retransmission DBTMA protocol with fast retransmission strategy to improve the performance of MANETs. IEEE Access 2019, 7, 85098–85109. [Google Scholar] [CrossRef]
- Liu, G.; Dong, H.; Yan, Z.; Zhou, X.; Shimizu, S. B4SDC: A blockchain system for security data collection in MANETs. IEEE Trans. Big Data 2022, 8, 739–752. [Google Scholar] [CrossRef]
- Thomas, Y.; Fotiou, N.; Toumpis, S.; Polyzos, G.C. Improving mobile ad hoc networks using hybrid IP-information centric networking. Comput. Commun. 2020, 156, 25–34. [Google Scholar] [CrossRef]
- Bianchi, A.; Pizzutilo, S.; Vessio, G. Preliminary description of NACK-based ad-hoc On-demand Distance Vector routing protocol for MANETs. In Proceedings of the 2014 9th International Conference on Software Engineering and Applications (ICSOFT-EA), Vienna, Austria, 29–31 August 2014; pp. 500–505. [Google Scholar]
- Sa, P.K.; Sahoo, M.N.; Murugappan, M.; Wu, Y.; Majhi, B. (Eds.) Progress in Intelligent Computing Techniques: Theory, Practice, and Applications: Proceedings of ICACNI 2016; Springer: Berlin/Heidelberg, Germany, 2017; Volume 2. [Google Scholar]
- Molia, H.K.; Kothari, A.D. TCP variants for mobile adhoc networks: Challenges and solutions. Wirel. Pers. Commun. 2018, 100, 1791–1836. [Google Scholar] [CrossRef]
- Goyal, P.; Parmar, V.; Rishi, R. Manet: Vulnerabilities, challenges, attacks, application. IJCEM Int. J. Comput. Eng. Manag. 2011, 11, 32–37. [Google Scholar]
- Elamparithi, P.; Soundar, K.R. Trusted sensing model for mobile ad HoC network using differential evolution algorithm. Inf. Technol. Control 2020, 49, 556–563. [Google Scholar] [CrossRef]
- Khan, D.M.; Aslam, T.; Akhtar, N.; Qadri, S.; Rabbani, I.M.; Aslam, M. Black hole attack prevention in mobile ad-hoc network (manet) using ant colony optimization technique. Inf. Technol. Control 2020, 49, 308–319. [Google Scholar] [CrossRef]
- Perumal, T. Statistical Markov model based natural inspired glowworm swarm multi-objective optimization for energy efficient data delivery in MANET. Inf. Technol. Control 2020, 49, 333–347. [Google Scholar] [CrossRef]
- Rathish, C.R.; Karpagavadivu, K.; Sindhuja, P.; Kousalya, A. A Hybrid Efficient Distributed Clustering Algorithm Based Intrusion Detection System to Enhance Security in MANET. Inf. Technol. Control 2021, 50, 45–54. [Google Scholar] [CrossRef]
- Saifan, R.; Abu-Zant, S.; Alnabelsi, S.H.; Hawa, M.; Jubair, F. LDAB-GPSR: Location PreDiction with Adaptive Beaconing–Greedy Perimeter Stateless Routing Protocol for Mobile Ad Hoc Networks. Inf. Technol. Control 2022, 51. [Google Scholar] [CrossRef]
- Sirajuddin, M.D.; Rupa, C.; Prasad, A. Advanced congestion control techniques for MANET. In Information Systems Design and Intelligent Applications; Springer: New Delhi, India, 2016; pp. 271–279. [Google Scholar]
- Perkins, C.; Belding-Royer, E.; Das, S. RFC3561: Ad Hoc On-Demand Distance Vector (AODV) Routing. 2003. Available online: https://dl.acm.org/doi/10.17487/RFC3561 (accessed on 1 July 2022).
- Pusateri, T. Distance Vector Routing Protocol. Draft-IETF-IDMR-DVMRP-v3-07. 2003. Available online: https://datatracker.ietf.org/doc/draft-ietf-idmr-dvmrp-v3/ (accessed on 1 July 2022).
- Sampath, D.; Garcia-Luna-Aceves, J.J. PROSE: Scalable routing in MANETs using prefix labels and distributed hashing. In Proceedings of the 2009 6th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Rome, Italy, 22–26 June 2009; pp. 1–9. [Google Scholar]
- Abid, S.A.; Othman, M.; Shah, N.; Ali, M.; Khan, A.R. 3D-RP: A DHT-based routing protocol for MANETs. Comput. J. 2015, 58, 258–279. [Google Scholar] [CrossRef]
- Hassanzadeh-Nazarabadi, Y.; Taheri-Boshrooyeh, S.; Otoum, S.; Ucar, S.; Özkasap, Ö. DHT-based Communications Survey: Architectures and Use Cases. arXiv 2021, arXiv:2109.10787. [Google Scholar]
- Jahir, Y.; Atiquzzaman, M.; Refai, H.; Paranjothi, A.; LoPresti, P.G. Routing protocols and architecture for disaster area network: A survey. Ad Hoc Netw. 2019, 82, 1–4. [Google Scholar] [CrossRef]
- Morais, C.C.; Gossain, H.; Agrawal, D.P. Multicast over wireless mobile ad hoc networks: Present and future directions. IEEE Netw. 2003, 17, 52–59. [Google Scholar]
- Lee, S.J.; Su, W.; Hsu, J.; Gerla, M.; Bagrodia, R. A performance comparison study of ad hoc wireless multicast protocols. In Proceedings of the IEEE INFOCOM 2000. Conference on Computer Communications. Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies (Cat. No. 00CH37064), Tel Aviv, Israel, 26–30 March 2000; Volume 2, pp. 565–574. [Google Scholar]
- Geetha, A.; Sreenath, N. Byzantine attacks and its security measures in mobile adhoc networks. Int. J. Comput. Commun. Instrum. Eng. IJCCIE 2016, 3, 42–47. [Google Scholar]
- Khan, R.A. Routing Protocols Evaluation Review in Simple and Cloud Environment. Lahore Garrison Univ. Res. J. Comput. Sci. Inf. Technol. 2019, 3, 1–8. [Google Scholar]
- Awad, A.; Sommer, C.; German, R.; Dressler, F. Virtual cord protocol (VCP): A flexible DHT-like routing service for sensor networks. In Proceedings of the 2008 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Atlanta, GA, USA, 29 September–2 October 2008; pp. 133–142. [Google Scholar]
- Tan, S.; Kim, K. Secure Route Discovery for preventing black hole attacks on AODV-based MANETs. In Proceedings of the 2013 IEEE 10th International Conference on High Performance Computing and Communications & 2013 IEEE International Conference on Embedded and Ubiquitous Computing, Zhangjiajie, China, 13–15 November 2013; pp. 1159–1164. [Google Scholar]
- Bianchi, A.; Pizzutilo, S.; Vessio, G. Comparing AODV and N-AODV Routing Protocols for Mobile Ad-hoc Networks. In Proceedings of the 13th International Conference on Advances in Mobile Computing and Multimedia, Brussels, Belgium, 11–13 December 2015; pp. 159–168. [Google Scholar]
- Narra, H.; Cheng, Y.; Cetinkaya, E.K.; Rohrer, J.P.; Sterbenz, J.P. Destination-sequenced distance vector (DSDV) routing protocol implementation in ns-3. In Proceedings of the 4th International ICST Conference on Simulation Tools and Techniques, Barcelona, Spain, 22–24 March 2011; pp. 439–446. [Google Scholar]
- Clausen, T.; Jacquet, P. (Eds.) RFC3626: Optimized Link State Routing Protocol (OLSR). Scientific Research. 2017. Available online: https://datatracker.ietf.org/doc/rfc3626/ (accessed on 1 July 2022).
- Afzal, S. Implementation of Flooding Free Routing in Smart Grid: VCP Routing in Smart Gird. In Smart Grid as a Solution for Renewable and Efficient Energy; IGI Global: Hershey, PA, USA, 2016; pp. 298–322. [Google Scholar]
- Haas, Z. The Zone Routing Protocol (ZRP) for Ad Hoc Networks. IETF Internet Draft, Draft-IETF-Manet-Zone-ZRP-01. 2002. Available online: https://datatracker.ietf.org/doc/draft-ietf-manet-zone-zrp/ (accessed on 1 July 2022).
- Tantawy, M.M. A proposed IP multicast hardware-routing algorithm using partitioned lookup table. In Proceedings of the 7th WSEAS International Conference on Telecommunications and Informatics, Corfu Island, Greece, 27 May 2008; pp. 31–36. [Google Scholar]
- Biradar, R.; Manvi, S.; Reddy, M. Mesh based multicast routing in MANET: Stable link based approach. Int. J. Comput. Electr. Eng. 2010, 2, 371. [Google Scholar] [CrossRef]
- Gossain, H.; An, K.; Cordeiro, C.; Agrawal, D.P. A scalable explicit multicast protocol for MANETs. J. Commun. Netw. 2005, 7, 294–306. [Google Scholar] [CrossRef]
- Kumar, S.S.; Parthasarathy, V.; Malini, P. Familiar route retrieval for multicasting in MANETs. In Proceedings of the 2014 International Conference on Science Engineering and Management Research (ICSEMR), Chennai, India, 27–29 November 2014; pp. 1–5. [Google Scholar]
- Sreenath, N.; Amuthan, A.; Selvigirija, P. Countermeasures against multicast attacks on enhanced-on demand multicast routing protocol in MANETs. In Proceedings of the 2012 International Conference on Computer Communication and Informatics, Coimbatore, India, 10–12 January 2012; pp. 1–7. [Google Scholar]
- Toh, C.K.; Guichal, G.; Bunchua, S. Abam: On-demand associativity-based multicast routing for ad hoc mobile networks. In Proceedings of the Vehicular Technology Conference Fall 2000. IEEE VTS Fall VTC2000. 52nd Vehicular Technology Conference (Cat. No. 00CH37152), Boston, MA, USA, 24–28 September 2000; Volume 3, pp. 987–993. [Google Scholar]
- Vadivel, R.; Bhaskaran, V.M. Adaptive reliable and congestion control routing protocol for MANET. Wirel. Netw. 2017, 23, 819–829. [Google Scholar] [CrossRef]
- Sharma, V.K.; Kumar, M. Adaptive congestion control scheme in mobile ad-hoc networks. Peer-to-Peer Netw. Appl. 2017, 10, 633–657. [Google Scholar] [CrossRef]
- Biagi, M.; Greco, S.; Lampe, L. Neighborhood-knowledge based geo-routing in PLC. In Proceedings of the 2012 IEEE International Symposium on Power Line Communications and Its Applications, Beijing, China, 27–30 March 2012; pp. 7–12. [Google Scholar]
- Bumiller, G.; Lampe, L.; Hrasnica, H. Power line communication networks for large-scale control and automation systems. IEEE Commun. Mag. 2010, 48, 106–113. [Google Scholar] [CrossRef]
- Garrity, T.F. Getting smart. IEEE Power Energy Mag. 2008, 6, 38–45. [Google Scholar] [CrossRef]
- Chelius, G.; Fleury, E.; Valois, F. Adaptive and robust adhoc multicast structure. In Proceedings of the 14th IEEE Proceedings on Personal, Indoor and Mobile Radio Communications (PIMRC 2003), Beijing, China, 7–10 September 2003; Volume 1, pp. 760–764. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).