Computer Vision Approach in Monitoring for Illicit and Copyrighted Objects in Digital Manufacturing
Abstract
:1. Introduction
2. Legal Framework for Digital Manufacturing and Physical Control at IP Protection
3. Problem Statement and the Related Works
3.1. Shape-Based Methods
- A 3D shape spectrum descriptor [22] is related to the first and second principal curvature along the object’s surface.
- A descriptor [25] compares the similarity of two 3D objects by generating distance histograms and determining the appropriate alignment of the two objects.
- A graph-based approach [26] utilizes hierarchical structures to represent 3D objects, accompanied by graph-matching techniques.
- A spherical function-based descriptor [27] suggests using a volumetric representation of the Gaussian Euclidean Distance Transform for a 3D object, expressed by the norms of spherical harmonic frequencies.
3.2. View-Based Methods
- Ansary et al. [29] selected optimal 2D views of a 3D model and created K-mean clustering of views. Then, the similarity between pairwise 3D objects was measured by applying Bayesian models.
- Wang et al. [30] solved the retrieval problem using group sparse coding. The query object was constructed again by the view sets of each shape; then, the restoration error was considered the similarity measurement for retrieval.
- In [31], it was proposed to project a 3D object to a 2D space and use multi-views. These view-based methods combine a trainable system with 2D projection attributes adopted by the Convolutional Neural Networks (CNNs).
- Ref. [32] introduced a 3D shape descriptor known as the spherical trace transform, which generalizes the 2D trace transform. This approach involves calculating a range of 2D features for a collection of planes that intersect the volume of a 3D model.
3.3. Hybrid Methods
4. System Architecture
- How to store COs securely without unauthorized leakage of their blueprints.
- How to represent the objects in the database of controlled objects.
- How to evaluate objects-in-question quickly and provide a fast search of this information to keep up with 3D printing operations.
- How to describe controlled objects in a compact way that is good for comparison and storage: Confidentiality Preserving Descriptors (CPDs) should be used for object feature representation. Even if a descriptor of a CO is leaked, it cannot be used to manufacture COs.
- How to keep a Database of Controlled Objects (DCO) containing the descriptions of the controlled objects: this database should be maintained by the authorities, who decide which objects should be controlled.
- How to compare an object to be manufactured (an object-under-analysis, OUA) to controlled objects from the DCO in rapid, reliable, and efficient ways.
4.1. Storing of Controlled Objects
- Human knowledge (a border control officer can recognize a forbidden item).
- Databases of 2D photographs for camera/video recognition.
- In a neural network (NN) for photo/video recognition. This NN should first be trained on many cases to extract the patterns typical for the specific class (classes) of objects to recognize.
- Local validation provides performance benefits; large 3D design files do not need to be uploaded through the Internet.
- A deployment model where designs are pre-validated by a cloud service is possible, assuming design owners are ready to get their designs pre-approved from authority services. In some cases, in-device validation could be beneficial as it limits design exposure service. To ensure the confidentiality of designs-to-be-produced, there may be a requirement not to move the blueprint out of the 3D printer to protect intellectual rights and provide secure printing operations.
- Additive manufacturing factories (or devices) could be operating offline.
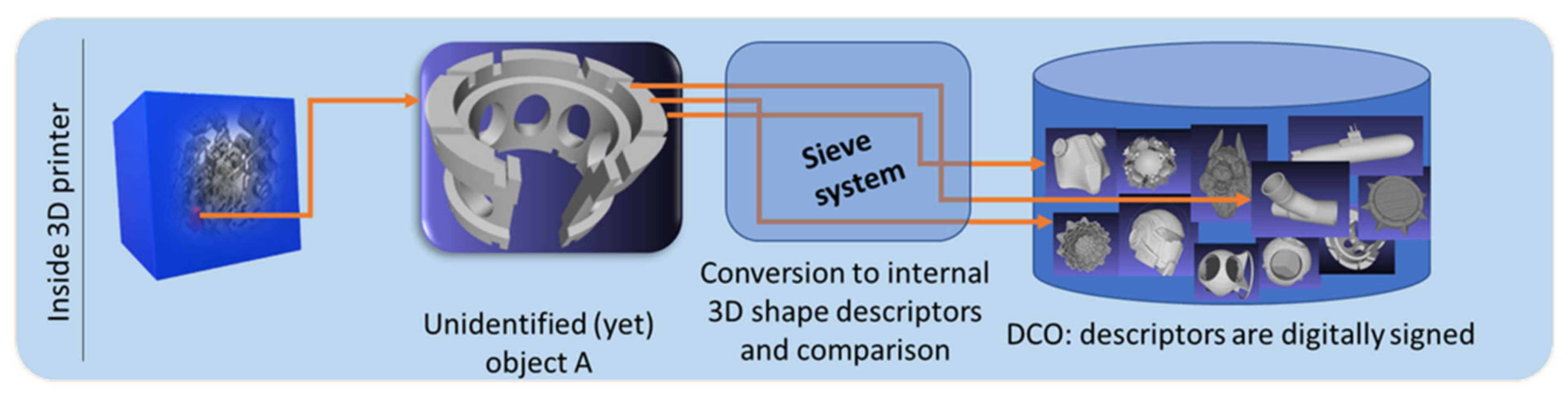
- A DCO will store information about 3D objects in the form of CPDs.
4.2. Confidentiality Preserving Descriptors: Describing CO
- Each of these descriptors describes a distinctive feature of 3D objects. It could [36,37,38] be the number of holes in the object, volume of the object, area of the surface, volume of the convex hull, surface- or boundary-based centroid, center of mass, principal axes, convexity, aspect ratios, sphericity, mean radius, ellipsoidal variance, EGI [39], spherical harmonic coefficients [27], etc. Multiple CPDs are used as an ensemble to facilitate rapid object identification.
- Three-dimensional objects are encoded by their feature vector. Each object’s CPDs contain essential information about the shape of the 3D object in a compressed and low-dimensionality form, sufficient for object identification.
- Descriptors must be lossy and nonreversible, making the restoration of original blueprints from CPDs impossible even if the 3DP device is breached and fully disassembled.
- Descriptors need to be computationally light/fast for in-device processing. We assume k = 102–103 physical objects per 3DP job, so using object-per-object comparison will require k times the number of controlled objects for comparisons. This processing should not create a “bottleneck” for the primary 3D printing process by demanding too many resources.
- At least some descriptors should be able to capture the internal structure of the 3D object, not only the appearance.
- Descriptors could be efficiently stored in the DCO and allow effective comparison of descriptors.
- As objects in the 3DP job may be rotated for better packing of objects in the printing volume, the descriptors should either provide the same output when the 3D objects are rotated and translated or the most efficient method to compare the descriptors of the rotated and translated objects should be known.
4.3. Identification Process
- The decision making about object identification is performed as a cascade of classifiers, i.e., in a hierarchical manner.
- The probability of encountering a CO is low, so we must filter out non-COs quickly and efficiently.
- We start from low-complexity discriminative algorithms to reject the object as being a CO as fast as possible (e.g., it is too small, too “square”, has no holes, etc.).
- Then, at later stages, we progress to complex, computationally expensive, and accurate determination algorithms.
- All objects (models) from a 3D print job should pass through a hierarchy of classifiers (it could be imagined as a set of sieves with smaller and smaller chances to make an inaccurate decision due to being more computationally expensive at each consequent level); refer to Figure 1.
- We aim to identify (eliminate) most objects by the least computationally expensive classifier.
- Ideally, it is expected that identification aims for 100% accuracy within an acceptable time.
- Different methods have different complexity and accuracy (usually, the more complex the approach, the longer the calculations and the better the final accuracy).
- Some models could take a long time to process to reach high-accuracy results.
- The acceptable level of object identification accuracy may depend on the object type. We might need to weigh the importance of correctly identifying the object against the time spent on decision making and the type of the object itself.
- Rotation in R3 (any degree) and translation (as objects in a 3D printing job could be moved to be better packed in the printing volume).
- Remeshing of 3D object mesh.
5. Results and Discussion
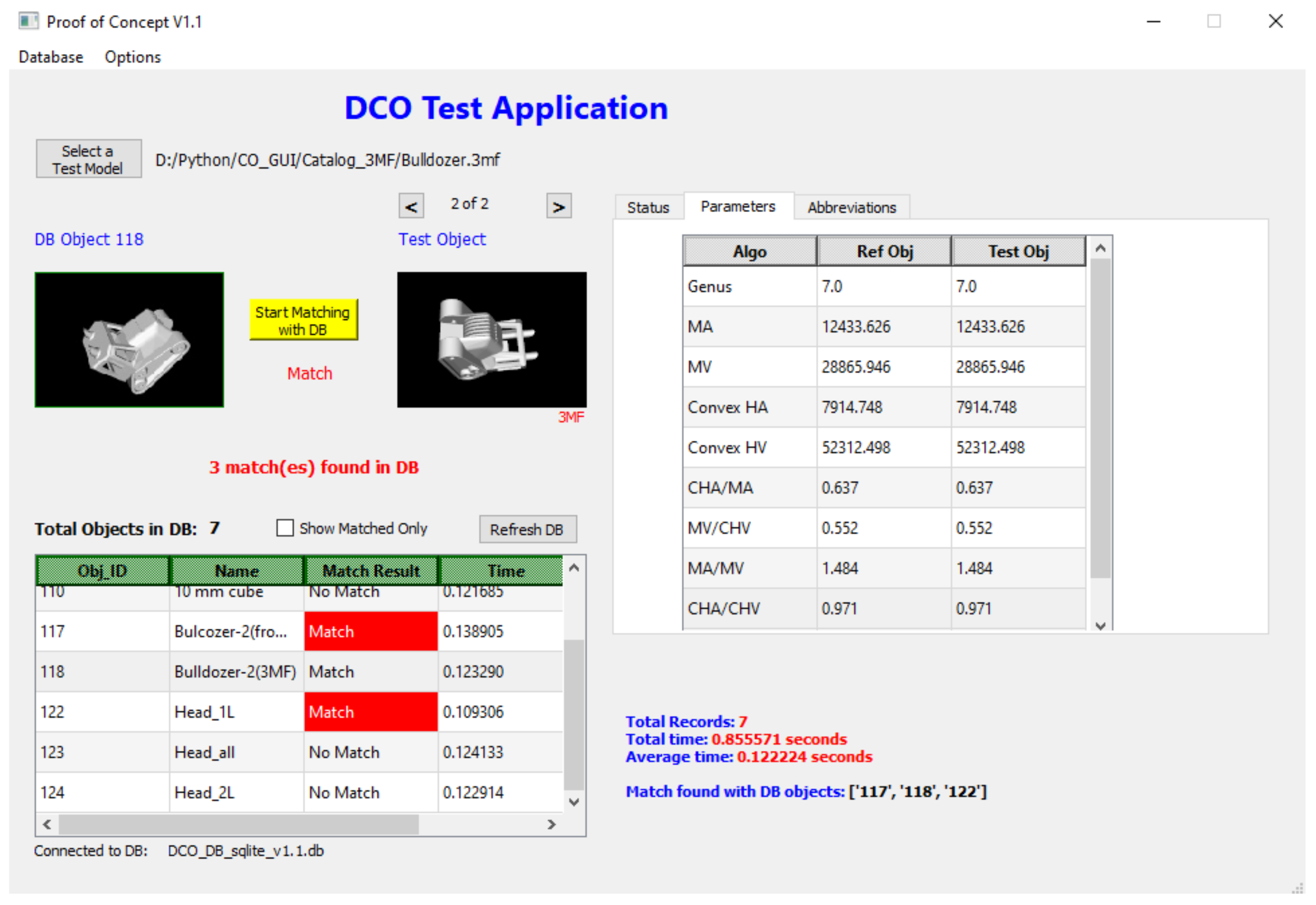
5.1. Efficiency of Search in a Big Database of Controlled Objects
5.2. Possible Future Directions
- Making the identification of a CO possible even if no blueprint for this CO is available. This could be done by scanning the object and representing it as a point cloud.
- Identifying a CO even if an intentional change in the design (to escape detection) is made. We assume that this design change does not affect the object’s functionality.
- Verifying that the blueprint object was not modified during printing (parts of the blueprint should not be changed during manufacturing due to a malicious attack).
- Performing modeling of attacks and countering attacks.
- Incorporating ML/DL techniques to detect similarity to the class of COs even if we have a limited number (or even one only) of class representatives (e.g., the object looks like a known CO) using one-shot learning.
6. Conclusions
- Patents, copyrights, and trademarks holders;
- Three-dimensional manufacturers (this could help address current and future regulatory challenges for the production of COs);
- Law enforcement organizations (to tighten controls for high-risk items).
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- HP Helps U.S. Clamp Down on Counterfeiting. Imaging Expertise Used to Deter Digital Fakes. Available online: https://www.hpl.hp.com/news/2003/july_sept/counterfeit.html (accessed on 31 October 2023).
- Secret Code in Colour Printers Lets Government Track You. Available online: https://www.eff.org/press/archives/2005/10/16 (accessed on 31 October 2023).
- When 3D Printing Gets into the Wrong Hands. Available online: https://www.forbes.com/sites/zurich/2016/05/06/when-3d-printing-gets-into-the-wrong-hands/ (accessed on 31 October 2023).
- Elangovan, N. Parliament Enacts New Law to Keep 3D-Printed Guns off the Streets, Better Regulate Weapons. Available online: https://www.todayonline.com/singapore/parliament-enacts-new-law-keep-3d-printed-guns-streets-better-regulate-weapons (accessed on 31 October 2023).
- Fact Sheet: The Biden Administration Cracks Down on Ghost Guns, Ensures that ATF Has the Leadership it Needs to Enforce Our Gun Laws. Available online: https://www.whitehouse.gov/briefing-room/statements-releases/2022/04/11/fact-sheet-the-biden-administration-cracks-down-on-ghost-guns-ensures-that-atf-has-the-leadership-it-needs-to-enforce-our-gun-laws/ (accessed on 31 October 2023).
- Spain Dismantles Workshop Making 3D-Printed Weapons. Available online: https://www.bbc.com/news/world-europe-56798743 (accessed on 31 October 2023).
- Bridges, S.M.; Keiser, K.; Sissom, N.; Graves, S.J. Cyber security for additive manufacturing. In Proceedings of the 10th Annual Cyber and Information Security Research Conference (CISR’15), Oak Ridge, TN, USA, 7–9 April 2015. [Google Scholar]
- Printing Insecurity: Tackling the Threat of 3D Printed Guns in Europe. Available online: https://www.europol.europa.eu/media-press/newsroom/news/printing-insecurity-tackling-threat-of-3d-printed-guns-in-europe (accessed on 31 October 2023).
- Fey, M. 3D Printing and International Security: Risks and Challenges of an Emerging Technology; Report No. 144; Peace Research Institute Frankfurt: Frankfurt am Main, Germany, 2017. [Google Scholar]
- Ebrahim, T. 3D Printing: Digital Infringement & Digital Regulation. Northwest. J. Technol. Intellect. Prop. 2016, 14, 2. [Google Scholar]
- U.S. Code. Title 17. Ch. 1. § 102—Subject Matter of Copyright: In General. Available online: https://www.law.cornell.edu/uscode/text/17/102 (accessed on 31 October 2023).
- Ogburu-Ogbonnay, H. 3D Printing as a Copyright Infringement, JIPEL Blog 2016–2017. Available online: https://blog.jipel.law.nyu.edu/2017/03/3d-printing-as-a-copyright-infringement/ (accessed on 31 October 2023).
- WIPO Copyright Treaty (Adopted in Geneva on December 20, 1996), WIPO IP Portal. Available online: https://wipolex.wipo.int/en/text/295166 (accessed on 31 October 2023).
- Malaty, E.; Rostama, G. 3D printing and IP law. WIPO Mag. 2017, 1, 6. [Google Scholar]
- Blockchain to Play a Key Part in Ensuring Copyright Laws Can Be Used for 3D Printing. Available online: https://news-archive.exeter.ac.uk/homepage/title_908509_en.html (accessed on 31 October 2023).
- Gao, Y.; Wang, W.; Jin, Y.; Zhou, C.; Xu, W.; Jin, Z. ThermoTag: A hidden ID of 3D printers for fingerprinting and watermarking. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2805–2820. [Google Scholar] [CrossRef]
- 3D-Printed Counterfeits on the Rise: How to Protect Your Brand. Available online: https://www.nanomatrixsecure.com/3d-printed-counterfeits-on-the-rise-how-to-protect-your-brand/ (accessed on 31 October 2023).
- Roche, S. The New World of 3D Printing… and Counterfeiting. Available online: https://www.linkedin.com/pulse/new-world-3d-printing-counterfeiting-sebastien-roche (accessed on 31 October 2023).
- O’Heir, J. Protecting a New World of 3D-Printed Products, the American Society of Mechanical Engineers. Available online: https://www.asme.org/topics-resources/content/protecting-new-world-3dprinted-products (accessed on 31 October 2023).
- Counterfeit Product Alert: How to Identify Counterfeit BMW Group Vehicle Parts. Available online: https://www.thecounterfeitreport.com/product/599/BMW-Group-Vehicle-Parts.html (accessed on 31 October 2023).
- Zhuang, T.; Zhang, X.; Hou, Z.; Zuo, W.; Liu, Y. A novel 3D CAD model retrieval method based on vertices classification and weights combination optimization. Math. Probl. Eng. 2017, 2017, 6049750. [Google Scholar] [CrossRef]
- Zaharia, T.; Petreux, F. 3D shape-based retrieval within the mpeg-7 framework. In Proceedings of the SPIE Conference on Nonlinear Image Processing and Pattern Analysis XII, San Jose, CA, USA, 30–31 July 2001; pp. 133–145. [Google Scholar]
- Osada, R.; Funkhouser, T.A.; Chazelle, B.; Bobkin, D.B. Shape distribution. ACM Trans. Graph. 2002, 21, 807–832. [Google Scholar] [CrossRef]
- Shih, J.-L.; Lee, C.-H.; Wang, J.T. 3D object retrieval system based on grid D2. Electron. Lett. 2005, 41, 179–181. [Google Scholar] [CrossRef]
- Novotni, M.; Klein, R. A geometric approach to 3D object comparison. In Proceedings of the International Conference on Shape Modeling and Applications, Genoa, Italy, 7–11 May 2001; pp. 167–175. [Google Scholar]
- Zhang, J.; Siddiqi, K.; Macrini, D.; Shokoufandeh, A.; Dickinson, S. Retrieving articulated 3-d models using medial surfaces and their graph spectra. In Proceedings of the Energy Minimization Methods in Computer Vision and Pattern Recognition: 5th International Workshop, EMMCVPR 2005, St. Augustine, FL, USA, 9–11 November 2005. [Google Scholar]
- Kazhdan, M.; Funkhouser, T.; Rusinkiewicz, S. Rotation invariant spherical harmonic representation of 3D shape descriptors. In Proceedings of the 2003 Eurographics/ACM SIGGRAPH Symposium on Geometry Processing (SGP ‘03), Aachen, Germany, 23–25 June 2003; pp. 156–164. [Google Scholar]
- Gao, Y.; Dai, Q. View-based 3D object retrieval: Challenges and approaches. IEEE Multimed. 2014, 21, 52–57. [Google Scholar] [CrossRef]
- Ansary, T.F.; Daoudi, M.; Vandeborre, J. Bayesian 3D search engine using adaptive views clustering. IEEE Trans. Multimed. 2007, 9, 78–88. [Google Scholar] [CrossRef]
- Wang, X.; Nie, W. 3D model retrieval with weighted locality constrained group sparse coding. Neurocomputing 2015, 151, 620–625. [Google Scholar] [CrossRef]
- Hoang, L.; Lee, S.-H.; Kwon, K.-R. A deep learning method for 3D object classification and retrieval using the global point signature plus and deep wide residual network. Sensors 2021, 21, 2644. [Google Scholar] [CrossRef] [PubMed]
- Zarpalas, D.; Daras, P.; Axenopoulos, A.; Tzovaras, D.; Strintzis, M.G. 3D model search and retrieval using the spherical trace transform. EURASIP J. Adv. Signal Process. 2006, 2007, 23912. [Google Scholar] [CrossRef]
- Daras, P.; Axenopoulos, A.; Litos, G. Investigating the effects of multiple factors towards more accurate 3-D object retrieval. IEEE Trans. Multimed. 2012, 14, 374–388. [Google Scholar] [CrossRef]
- Jayanti, S.; Kalyanaraman, Y.; Iyer, N.; Ramani, K. Developing an engineering shape benchmark for CAD models. Comput.-Aided Des. 2006, 38, 939–953. [Google Scholar] [CrossRef]
- Papadakis, P.; Pratikakis, I.; Theoharis, T.; Perantonis, S. Panorama: A 3D shape descriptor based on panoramic views for unsupervised 3d object retrieval. Int. J. Comput. Vis. 2010, 89, 177–192. [Google Scholar] [CrossRef]
- Peura, M.; Iivarinen, J. Efficiency of simple shape descriptors. In Proceedings of the 3rd International Workshop on Visual Form (IWVF3), Capri, Italy, 28–30 May 1997; pp. 443–451. [Google Scholar]
- Wäldchen, J.; Mäder, P. Plant species identification using computer vision techniques: A systematic literature review. Arch. Comput. Methods Eng. 2008, 25, 507–543. [Google Scholar] [CrossRef] [PubMed]
- Sonka, M.; Hlaváč, V.; Boyle, R.D. Image Processing, Analysis and Machine Vision, 4th ed.; Springer: New York, NY, USA, 1993. [Google Scholar]
- Kang, S.B.; Horn, P.K. Extended Gaussian image (EGI). In Computer Vision; Ikeuchi, K., Ed.; Springer: Cham, Switzerland, 2021; pp. 420–424. [Google Scholar]
- Volkau, I.; Krasovskii, S.; Mujeeb, A.; Balinsky, H. Whether 3D object is copyright protected? Controlled object identification in additive manufacturing. In Proceedings of the IEEE 22nd International Conference on Cyberworlds (CW2023), Sousse, Tunisia, 3–5 October 2023. [Google Scholar]
- Horn, В.К.P. Robot Vision; The MIT Press: Cambridge, MA, USA, 1986. [Google Scholar]
- Shilane, P.; Min, P.; Kazhdan, M.; Funkhouser, T. Princeton Shape Benchmark. Available online: https://shape.cs.princeton.edu/benchmark/benchmark.pdf (accessed on 15 May 2023).
- Engineering Shape Benchmark (ESB, Purdue University). Available online: https://engineering.purdue.edu/cdesign/wp/downloads/ (accessed on 31 October 2023).
- Wu, Z.; Song, S.; Khosla, A.; Yu, F.; Zhang, L.; Tang, X.; Xiao, J. 3D ShapeNets: A Deep Representation for Volumetric Shapes. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR 2015), Boston, MA, USA, 7–12 June 2015; pp. 1912–1920. [Google Scholar]
- List of 3D Printed Weapons and Parts. Available online: https://en.wikipedia.org/wiki/List_of_3D_printed_weapons_and_parts (accessed on 31 October 2023).

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Volkau, I.; Krasovskii, S.; Mujeeb, A.; Balinsky, H. Computer Vision Approach in Monitoring for Illicit and Copyrighted Objects in Digital Manufacturing. Computers 2024, 13, 90. https://doi.org/10.3390/computers13040090
Volkau I, Krasovskii S, Mujeeb A, Balinsky H. Computer Vision Approach in Monitoring for Illicit and Copyrighted Objects in Digital Manufacturing. Computers. 2024; 13(4):90. https://doi.org/10.3390/computers13040090
Chicago/Turabian StyleVolkau, Ihar, Sergei Krasovskii, Abdul Mujeeb, and Helen Balinsky. 2024. "Computer Vision Approach in Monitoring for Illicit and Copyrighted Objects in Digital Manufacturing" Computers 13, no. 4: 90. https://doi.org/10.3390/computers13040090





