A Hybrid Scheme for an Interoperable Identity Federation System Based on Attribute Aggregation Method
Abstract
:1. Introduction
2. Digital Identity and Identity Management
2.1. Digital Identity
2.2. Mobile Digital Identity
- Device-to-device identity: a mobile identity is used to attest the authority of a particular user in order to grant access to services and resources while using different devices;
- Location-to-location identity: this means that a mobile identity is used to certify the individual authority while moving between different locations;
- Context-to-context identity: in this case, the access to resources is granted to individuals according to different societal roles and depending on the context and the application domain.
2.3. Interaction between Identity Elements
2.4. Authentication Methods
- What you know (e.g., password, personal identification number (PIN)): this form of authentication is still the most widely used for online applications by means of a user name (user ID) and password [9]. However, using passwords as an authentication mechanism is far from adequate for providing a high security level [10];
- What you have (e.g., certificate, token, and smart card): to meet the security requirements and to achieve strong authentication, a possession-based authentication scheme has been developed to basically check the user’s credentials validity. This technique is based on the generation of tokens using the login credentials of the users. The latter will be allowed to access protected resources, on a specific time period, without using their credentials repeatedly. Given that the tokens expire within a set time limit, users will be asked to authenticate themselves once more. Thus, this method increases the security and helps users stay safer online. However, possession of a valid token does not prove ownership as it may have been stolen. Thus, possession-based authentication is useless in uncontrolled environments [11].
- What you are (e.g., biometrics): this refers to recognition of a person based on human physiological or behavioral characteristics. Among these characteristics are the following: face, fingerprint, hand geometry, iris, retinal, signature, and voice [12]. This solution avoids risks associated with other authentication methods. It cannot be stolen, forgotten, or borrowed. However, despite the benefits of biometrics, some security issues still must be addressed. In fact, biometrics systems are not always accurate, and there are privacy concerns as they may collect more information than what is needed to grant the access. In addition, there are several attack points in biometrics systems [13].
2.5. Access Control Models
2.6. Identity Management
- End user: person wants to access a resource;
- Digital Identity: a set of attributes and credentials;
- Identity provider (IdP): an organization that issues and manages identities of users;
- Service provider (SP): an organization offering services to end users or other organizations. It also known as a relying party;
- Personal authentication device (PAD): a personal device holding identifiers and credentials.
3. Identity Federation: Architectures and Related Standards
3.1. Full Mesh Federation
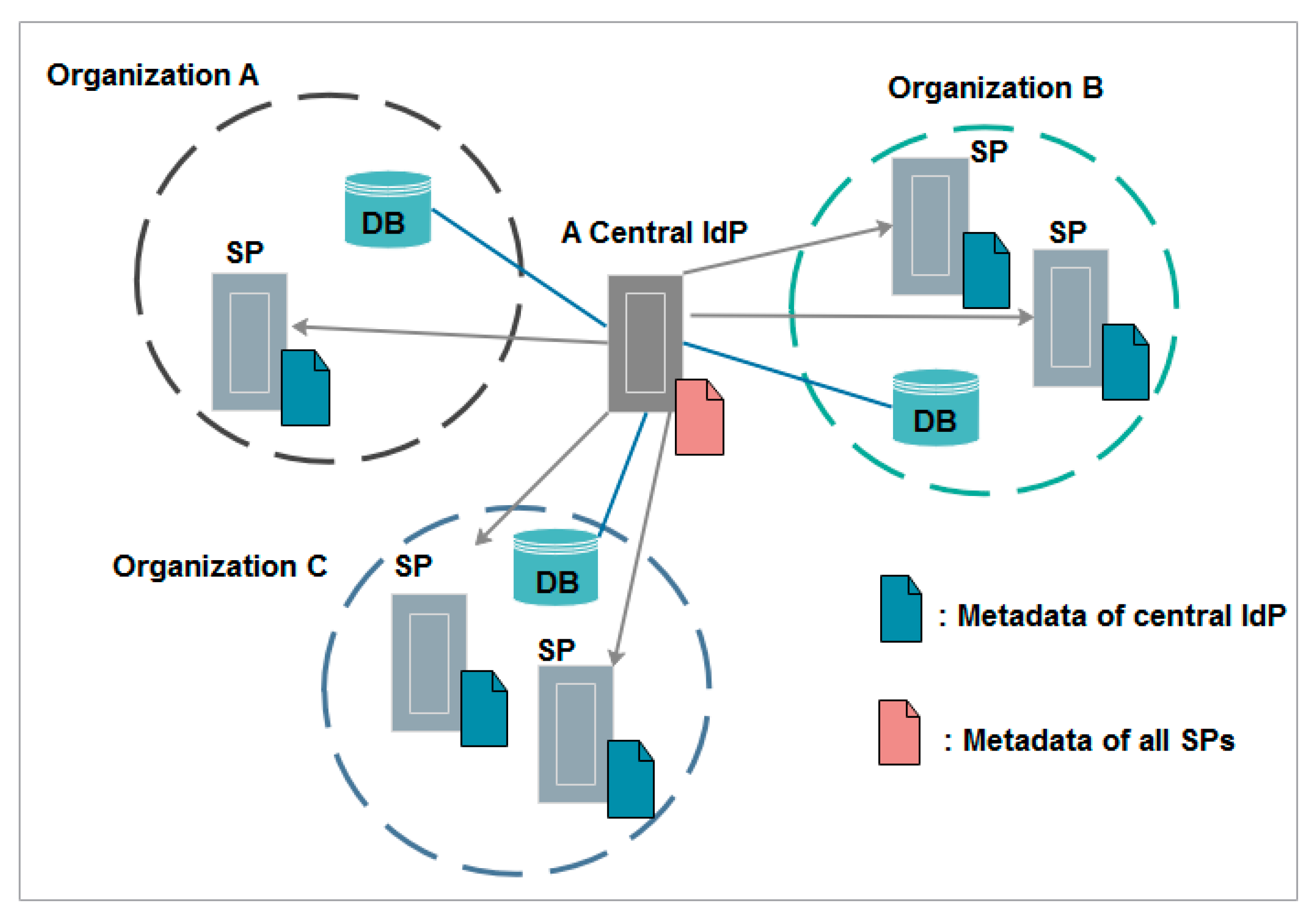
3.2. Hub-and-Spoke Federation with Distributed Login
3.3. Hub-and-Spoke Federation with Centralized Login
3.4. Liberty Alliance
- Identity federation framework (ID-FF): This defines protocols and profiles to enable the identity federation solution. The ID-FF is designed to be used on its own or in conjunction with existing identity management systems using heterogeneous platforms and various network devices. The main functions of the ID-FF protocols are account linkage, simplified single sign-on, simple session management, and real-time discovery and exchange of metadata.
- Web services framework (ID_WSF): This defines web services that can be provided to users in order to support the Liberty Alliance business model. It utilizes the ID-FF for authentication and the federation and privacy mechanisms. ID-WSF offers features including permission-based attribute, identity service discovery, and interaction service.
- Services interface specifications (ID-SIS): This provides interfaces for web services allowing providers to exchange different parts of identity. These services are built on top of Liberty’s ID-WSF and comprise registration, contact book, calendar, geo-location, presence, or alerts.
3.5. Web Service Federation (WS-Federation)
4. Attribute Aggregation in Identity Federation
4.1. Related Work
- Attribute aggregation from many IdPs in a single session: the model has to have the ability to select user attributes from multiple IdPs;
- Signing of attribute assertions by their authoritative sources: to provide adequate assurance of the attribute value correctness, each attribute assertion must be signed by the authority managing this attribute and who the SP is willing to trust;
- Linking and mapping attributes to IdPs with user permission: the user should have the control and be able to select the attributes that will be provided by each IdP;
- Respect of the typical operating principle of identity federation: the model should follow the standard design of an identity federation system;
- Single authentication in one session: end users need to be authenticated only once without asking them to authenticate separately into each IdP;
- Privacy protection of user attributes: during data transmission, the model must ensure the controlled release of attributes and the unlinkability between sessions;
- Efficiency of trust relationships management: the model should optimize the trust relationships, while at the same time avoiding the establishment of trust relationships that are not useful and mandatory.
- Data minimization: user attributes will be processed only if it is necessary for the SP with limited access to personal data;
- Mitigation of implementation complexity: the design and the implementation of the model should be as simple as possible by avoiding additional investment and technical complexity;
- Availability: the system should be online and ready to conduct business 24 hours a day, 7 days a week. Besides, the design of the model should take into account the absence of the single point of failure (SPoF) to grant the reliability of the system.
4.2. Analysis and Interpretation
5. Description of the Proposed Model
5.1. Bricks of the Proposed Model
- Service provider/ relying party: entity providing IT solution/services to end users;
- Identity provider: entity managing users’ identities and providing system authentication;
- Account linking provider (ALP): a new component that acts as a gateway between SPs and IdPs allowing users with multiple accounts into several IdPs, in order to federate their identities and aggregate their attributes, while improving the trust relationships between the various stakeholders and respecting the security and privacy concepts;
- ALPs’ discovery service: entity holding the predefined list of all ALPs having trust relationships with the SP.
5.2. Key Components of the ALP
- Authentication authority: this is the brick responsible for the authentication and the authorization process on the ALP;
- Centralized user database: a local database holding the identities of users who are authorized to access the ALP by means of a UserID and password;
- Discovery service: this module holds the predefined list of all IdPs having trust relationships with the ALP. It interacts with end users, allowing them to select an identity provider that manages one of their identities;
- Attribute authority: unlike an ordinary IdP, this brick does not produce SAML attribute assertions. Once the ALP receives user attribute request from an SP, the attribute authority triggers a search process for the corresponding IdPs;
- Account linking table (ALT): the attribute aggregation process is based on the establishment of an ALT (Table 2), which illustrates, for each user, the set of IdPs on which they have accounts with the corresponding attributes that will be provided by these IdPs to SPs. The ALT table also contains authentication assertions for each user in an IdP.
5.3. Properties of the Proposed Model
- The access to resources requires a single authentication with the ALP. Therefore, end users do not need to be authenticated with each IdP during a single access session. Moreover, the system is based on the single sign-on (SSO) mechanism to avoid re-authentication of end users each time they access protected services during a specific period of validity;
- Users have complete control and visibility of the dissemination and the use of their identities and attributes. In addition, no IdP should be aware of user identities on other IdPs so that the privacy requirement is insured;
- IdPs communicate the attribute identifiers (attributeIDs) to ALPs and not the values of those attributes that are stored in appropriate directories;
- The management of trust relationships between stakeholders is optimized. Each IdP must have a trust relationship with the SP and the ALP so that they can communicate successfully. However, IdPs do not need to have trust relationships between each other;
- The SP must be aware of the IdP that initially asserted attributes of the end user and all assertions must be signed by trustworthy sources;
- The ALP communicates to the SP only the selective list of the IdPs managing the required attributes to allow the resource access;
- The proposed model is mapped on the standard protocol SAMLv2 and follows the typical principal of identity federation systems.
6. Operating Principal of the Proposed Model
6.1. Registration and the ALT Filling
- If the user credentials are not valid, the ALP denies the access request and notifies the end user (7.1) who gets an error message (8.1). In this case, the end user may either attempt to retry the access process or decide to withdraw.
- If the user credentials are valid, the ALP initiates the research process in the ALT table (7.2). A treatment of the research request will be launched (8.2) with the verification of the related data 0 existence (9):
- -
- In the case of the prior existance of the end user entry in the ALT, the ALP allows the end user to update his data (10.1). He can view information related to his accounts and aggregated attributes, and he can also update accounts and attributes (11). The ALP receives, prepares, and sends the updated data to the ALT (12). This latter adds and saves the updated data (13).
- -
- If the ALT does not contain any data relating to the end user, a registration phase will be started (10.2).
6.2. Detailed Description of the Registration Phase
6.3. Attribute Aggregation and Access Phase
7. Prototype Implementation
7.1. Registration and the ALT Filling
7.1.1. Authentication Process
7.1.2. Integration of the Discovery Service into the ALP
7.1.3. Retrieval, Display, and Transmitting of the Selected Attributes to the ALT
7.2. Interaction between SP, ALP, and Local IdPs
7.2.1. Extraction and Sending of the Required Attributes by the SP
7.2.2. Retrieval of IdPs Managing the Required Attributes
7.2.3. Interaction between an SP and linked IdPs
8. Analysis and Evaluation
- Identifying Assets: in the work of [45], Schostack describes assets as valued things that should be protected from attackers. In an identity federation system, user identity is a central part that can be considered as a potential target of attackers. Thus, the main assets of our model are as follows: (a) partial identity with related attributes, (b) associated processes with partial identities (authentication, authorization, …), and (c) web services.
- Identifying threats: among possible threats against assets of our proposed model, we list the following threats:
- -
- Spoofing (Th1): information of user identities stored on IdPs and the ALP may be disclosed to unauthorized users that impersonate legitimate users from trusted sources.
- -
- Information Disclosure (Th2): attributes can be disclosed to SPs without user’s consent.
- -
- Tampering (Th3): exchanged data between stakeholders, through communication channels, can be intercepted by attackers.
- -
- Reply Attacks Threat (Th4): user messages may be captured and used by an attacker to launch a replay attack on SPs.
- -
- Denial of Service Threat (Th5): attackers may send several modified requests to render the ALP unavailable for its intended users.
- Outlining Mitigation Strategies: after the identification of threats, strategies should be planned and implemented to effectively mitigate the underlined threats. In the next subsections, we will highlight the main mechanisms adopted to minimize the identified threats as much as possible.
8.1. Advantages of the Proposed Model
8.2. Limitations
9. Conclusion and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Bertino, E.; Takahashi, K. Identity Management: Concepts, Technologies, and Systems; Artech House: Norwood, MA, USA, 2010. [Google Scholar]
- Ferraiolo, H. A Credential Reliability and Revocation Model for Federated Identifiers; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012.
- Cameron, K. The laws of identity. Microsoft Corp. 2005, 12, 8–11. Available online: http://www.identityblog.com/stories/2005/05/13/TheLawsOfIdentity.pdf (accessed on 3 June 2019).
- Shavers, B.; Bair, J. Digital Identity. In Hiding behind the Keyboard: Uncovering Covert Communication Methods with Forensic Analysis; Syngress: Amsterdam, The Netherlands, 2016; pp. 187–202. [Google Scholar]
- Mobile Identity Management, Enisa Position Paper. 2010. Available online: https://www.enisa.europa.eu/publications/Mobile%20IDM (accessed on 3 June 2019).
- Roussos, G.; Peterson, D.; Patel, U. Mobile Identity Management: An Enacted View. Int. J. Electron. Commer. 2003, 8, 81–100. [Google Scholar] [CrossRef] [Green Version]
- Rose, J.; Rehse, O.; Rober, B. The value of our digital identity. Boston Consult. Group 2012. Available online: https://www.bcg.com/publications/2012/digital-economy-consumer-insight-value-of-our-digital-identity.aspx (accessed on 3 June 2019).
- Jøsang, A.; Pope, S. User centric identity management. In Proceedings of the AusCERT Asia Pacific Information Technology Security Conference, Vienna, Austria, 7–8 July 2005; p. 77. [Google Scholar]
- Conklin, G.D.; Walz, D. Password-based authentication: A system perspective. In Proceedings of the 37th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 5–8 January 2004. [Google Scholar]
- Zhao, Z.; Dong, Z.; Wang, Y. Security analysis of a password-based authentication protocol proposed to IEEE 1363. Theor. Comput. Sci. 2006, 352, 280–287. [Google Scholar] [CrossRef] [Green Version]
- Zviran, M.; Erlich, Z. Identification and authentication: Technology and implementation issues. Commun. Assoc. Inf. Syst. 2006, 17, 4. [Google Scholar] [CrossRef]
- Zimmerman, M. Biometrics and User Authentication; SANS Institute, 2002. Available online: https://www.sans.org/reading-room/whitepapers/authentication/biometrics-user-authentication-122 (accessed on 3 June 2019).
- Ambalakat, P. Security of biometric authentication systems. In 21st Computer Science Seminar; 2005; p. 1. Available online: https://pdfs.semanticscholar.org/e1d7/7b951c55d7d1f322d1f96942daa77ec6c4ee.pdf (accessed on 3 June 2019).
- Multi-Factor Authentication—Australian Cyber Security Centre (ACSC). Available online: https://acsc.gov.au/publications/protect/multi_factor_authentication.htm (accessed on 3 June 2019).
- Karp, H.; Haury, H.; Davis, M.H. From ABAC to ZBAC: The evolution of access control models. J. Inf. Warf. 2010, 9, 38–46. [Google Scholar]
- Sandhu, R.S.; Coyne, E.J.; Feinstein, H.L.; Youman, C.E. Rolebased access control models. Computer 1996, 29, 38–47. [Google Scholar] [CrossRef]
- Hurwitz, J.S.; Bloor, R.; Baroudi, C.; Kaufman, M. Service Oriented Architecture for Dummies; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Friedman, A.R.; Lang, A.J.; Cogdell, M.M.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to attribute based access control (abac) definition and considerations (draft). Nist Spec. Publ. 2013, 800, 162. [Google Scholar]
- Armstrong, M.W. An Introduction to Xacml. 2003. Available online: http://courses.cs.vt.edu/~cs5204/fall05-kafura/Papers/Security/XACML-Short-Introduction.pdf (accessed on 3 June 2019).
- Federation and Attribute Based Access Control: Realization of the IAM (r)Evolution. 2010. Available online: https://www.immagic.com/eLibrary/ARCHIVES/GENERAL/AXIOM_SE/A100901F.pdf (accessed on 3 June 2019).
- Windley, P.J. Digital Identity: Unmasking Identity Management Architecture (IMA); O’Reilly Media, Inc.: Sevastopol, CA, USA, 2005. [Google Scholar]
- Boujezza, H.; Modher, A.-M.; Ayed, H.K.B.; Saidane, L. A taxonomy of identities management systems in IOT. In Proceedings of the 2015 IEEE/ACS 12th International Conference of Computer Systems and Applications (AICCSA), Marrakech, Morocco, 17–20 November 2015; pp. 1–8. [Google Scholar]
- Buecker, A.; Filip, W.; Hinton, H.; Hippenstiel, H.P.; Hollin, M.; Neucom, R.; Weeden, S.; Westman, J. Federated Identity Management and Web Services Security; IBM Redbook, 2005. Available online: https://www.academia.edu/6726901/Federated_e-Identity_Management_across_the_Gulf_Cooperation_Council_048_ (accessed on 3 June 2019).
- Refeds Survey. 2016. Available online: https://geant.app.box.com/s/8f30ptw5houmauurfqfupw3ruz3x9enu (accessed on 3 June 2019).
- Field Mesh Guide to Internet Trust Models: Federation. 2014. Available online: https://identitywoman.net/field-guide-to-internet-trust-models-mesh-federation/ (accessed on 3 June 2019).
- Shibboleth Consortium. Available online: https://www.shibboleth.net/ (accessed on 3 June 2019).
- Cantor, S.; Kemp, J.; Philpot, R.; Maler, E. Assertions and Protocols for the Oasis Security Assertion Markup Language (saml) v2.0 Oasis Standard Mar.15, 2005 Oasis Open. Available online: http://docs.oasis-open.org/security/saml/v2.0/saml-core-2.0-os.pdf (accessed on 3 June 2019).
- Federation Architectures. 2017. Available online: https://wiki.geant.org/display/eduGAIN/Federation+Architectures (accessed on 3 June 2019).
- Scudder, J.; Jøsang, A. Personal federation control with the identity dashboard. In Proceedings of the IFIP Working Conference on Policies and Research in Identity Management, Oslo, Norway, 18–19 November 2010; pp. 85–99. [Google Scholar]
- Watson, T. Introduction to the Liberty Alliance Identity Architecture. 2003, Volume 1. Available online: http://www.projectliberty.org. Revision (accessed on 3 June 2019).
- Lawrence, K.; Kaler, C.; Nadalin, A.; Monzillo, R.; Hallam-Baker, P. Web Services Security: Soap Message Security 1.1 (Ws-Security 2004). OASIS Standard 2006. OASIS. Available online: https://www.oasis-open.org/committees/download.php/16790/wss-v1.1-spec-os-SOAPMessageSecurity.pdf (accessed on 3 June 2019).
- Lockhart, H.; Andersen, S.; Bohren, J.; Sverdlov, Y.; Hondo, M.; Maruyama, H.; Nadalin, A.; Nagaratnam, N.; Boubez, T.; Morrison, K.; et al. Web Services Federation Language (Ws-Federation) Version 1.1. 2006, 15, 2008. Available online: http://seine.afnet.fr/referentiel/gestion_identites/documents/normes_travaux_spec/WS-Federation-V1-1B.pdf (accessed on 3 June 2019).
- Inman, G.; Chadwick, D.W.; Klingenstein, N. Authorisation Using Attributes from Multiple Authorities—A Study of Requirements. In Proceedings of the HCSIT Summit-ePortfolio International Conference, Maastricht, The Netherlands, 16–19 October 2007; Volume 366. [Google Scholar]
- Chadwick, D.W.; Inman, G.; Klingenstein, N. A conceptual model for attribute aggregation. Future Gener. Comput. Syst. 2010, 26, 1043–1052. [Google Scholar] [CrossRef] [Green Version]
- Hulsebosch, B.; Wegdam, M.; Zoetekouw, B.; Dijk, N.; Wijnen, R. Virtual Collaboration Attribute Management; Surf Net: Utrecht, The Netherlands, 2011; Volume 1. [Google Scholar]
- Ferdous, M.S.; Poet, R. Analysing attribute aggregation models in federated identity management. In Proceedings of the 6th International Conference on Security of Information and Networks, Aksaray, Turkey, 26–28 November 2013; pp. 181–188. [Google Scholar]
- Haddouti, S.E.; Kettani, M.D.E.C.E. Towards an interoperable identity management framework: A comparative study. Int. J. Comput. Sci. Issues (IJCSI) 2015, 12, 98. [Google Scholar]
- López, G.; Cánovas, Ó.; Gómez-Skarmeta, A.F.; Girao, J. A swift take on identity management. Computer 2009, 42, 5. [Google Scholar]
- Pérez, A.; López, G.; Cánovas, Ó.; Gómez-Skarmeta, A.F. Formal description of the swift identity management framework. Future Gener. Comput. Syst. 2011, 27, 1113–1123. [Google Scholar] [CrossRef]
- Vossaert, J.; Lapon, J.; De Decker, B.; Naessens, V. User-centric identity management using trusted modules. Math. Comput. Model. 2013, 57, 1592–1605. [Google Scholar] [CrossRef] [Green Version]
- Desmet, L.; Jacobs, B.; Piessens, F.; Joosen, W. Threat modelling for web services based web applications. In Communications and Multimedia Security; Springer: Boston, MA, USA, 2005; pp. 131–144. [Google Scholar]
- Myagmar, S.; Lee, A.J.; Yurcik, W. Threat modeling as a basis for security requirements. In Proceedings of the Symposium on Requirements Engineering for Information Security (SREIS), Paris, France, 29 August–2 September 2005; Volume 2005, pp. 1–8. [Google Scholar]
- Khattak, Z.A.; Sulaiman, S.; Ab Manan, J.L. A study on threat model for federated identities in federated identity management system. In Proceedings of the 2010 International Symposium on Information Technology, Kuala Lumpur, Malaysia, 15–17 June 2010; Volume 2, pp. 618–623. [Google Scholar]
- Abdu, N.J.; Lechner, U. A Threat Analysis Model for Identity and Access Management. In Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP 2016), Rome, Italy, 19–21 February 2016; pp. 498–502. [Google Scholar]
- Shostack, A. Threat Modeling: Designing for Security; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]









| Attribute Aggregation Models | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Application Database | SP-Mediated Attribute Aggregation | Identity Proxying | Identity Relay | Client-Mediated Assertion Collection | Identity Federation or IdP Mediated Attribute Aggregation | SWIFT Identity Framework | Linking Service | ||
| Requirements | Attribute aggregation from many IdPs in a single session | 🗶 | 🗸 | 🗸 | 🗸 | 🗸 | 🗶 | 🗸 | 🗸 |
| Signing of attributes assertions by their authoritative sources | 🗶 | 🗸 | 🗶 | 🗸 | 🗸 | 🗶 | 🗶 | 🗸 | |
| Linking and mapping attributes to IdPs with user permission | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | |
| Respect of the typical operating principle of Identity Federation | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗶 | |
| Single authentications in one session | 🗸 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | 🗸 | |
| Privacy protection of user attributes | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | |
| Efficiency of trust relationships management | 🗸 | 🗸 | 🗸 | 🗸 | - | - | 🗸 | 🗶 | |
| Data minimization | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | |
| Mitigation of implementation complexity | 🗸 | 🗶 | 🗸 | 🗸 | 🗶 | 🗶 | 🗶 | 🗶 | |
| Availability | 🗶 | - | 🗶 | 🗶 | - | - | 🗶 | 🗶 | |
| UserId (at ALP level) | Identity Providers (IdP) | UId (at IdPs Level) | AttributeID | Authentication Assertion |
| IdP1 | UId1 | Email NIN a | OK | |
| IdP2 | UId2 | GivenName DisplayName | OK | |
| ... | ... | … | ||
| IdPn | UIdn | Telephone Number | OK |
| Attribute Aggregation Models | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Application Database | SP-Mediated Attribute Aggregation | Identity Proxying | Identity Relay | Client-Mediated Assertion Collection | Identity Federation or IdP Mediated Attribute Aggregation | SWIFT Identity Framework | Linking Service | Our proposed Model | ||
| Requirements | Attribute aggregation from many IdPs in a single session | 🗶 | 🗸 | 🗸 | 🗸 | 🗸 | 🗶 | 🗸 | 🗸 | 🗸 |
| Signing of attributes assertions by their authoritative sources | 🗶 | 🗸 | 🗶 | 🗸 | 🗸 | 🗶 | 🗶 | 🗸 | 🗸 | |
| Linking and mapping attributes to IdPs with user permission | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | |
| Respect of the typical operating principle of identity federation | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗶 | 🗸 | |
| Single authentications in one session | 🗸 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | 🗸 | 🗸 | |
| Privacy protection of user attributes | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | |
| Efficiency of trust relationships management | 🗸 | 🗸 | 🗸 | 🗸 | - | - | 🗸 | 🗶 | 🗸 | |
| Data minimization | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | |
| Mitigation of implementation complexity | 🗸 | 🗶 | 🗸 | 🗸 | 🗶 | 🗶 | 🗶 | 🗶 | 🗸 | |
| Availability | 🗶 | - | 🗶 | 🗶 | - | - | 🗶 | 🗶 | 🗶 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
EL Haddouti, S.; Dafir Ech-Cherif EL Kettani, M. A Hybrid Scheme for an Interoperable Identity Federation System Based on Attribute Aggregation Method. Computers 2019, 8, 51. https://doi.org/10.3390/computers8030051
EL Haddouti S, Dafir Ech-Cherif EL Kettani M. A Hybrid Scheme for an Interoperable Identity Federation System Based on Attribute Aggregation Method. Computers. 2019; 8(3):51. https://doi.org/10.3390/computers8030051
Chicago/Turabian StyleEL Haddouti, Samia, and Mohamed Dafir Ech-Cherif EL Kettani. 2019. "A Hybrid Scheme for an Interoperable Identity Federation System Based on Attribute Aggregation Method" Computers 8, no. 3: 51. https://doi.org/10.3390/computers8030051
APA StyleEL Haddouti, S., & Dafir Ech-Cherif EL Kettani, M. (2019). A Hybrid Scheme for an Interoperable Identity Federation System Based on Attribute Aggregation Method. Computers, 8(3), 51. https://doi.org/10.3390/computers8030051





