Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition
Abstract
:1. Introduction
2. Materials and Methods
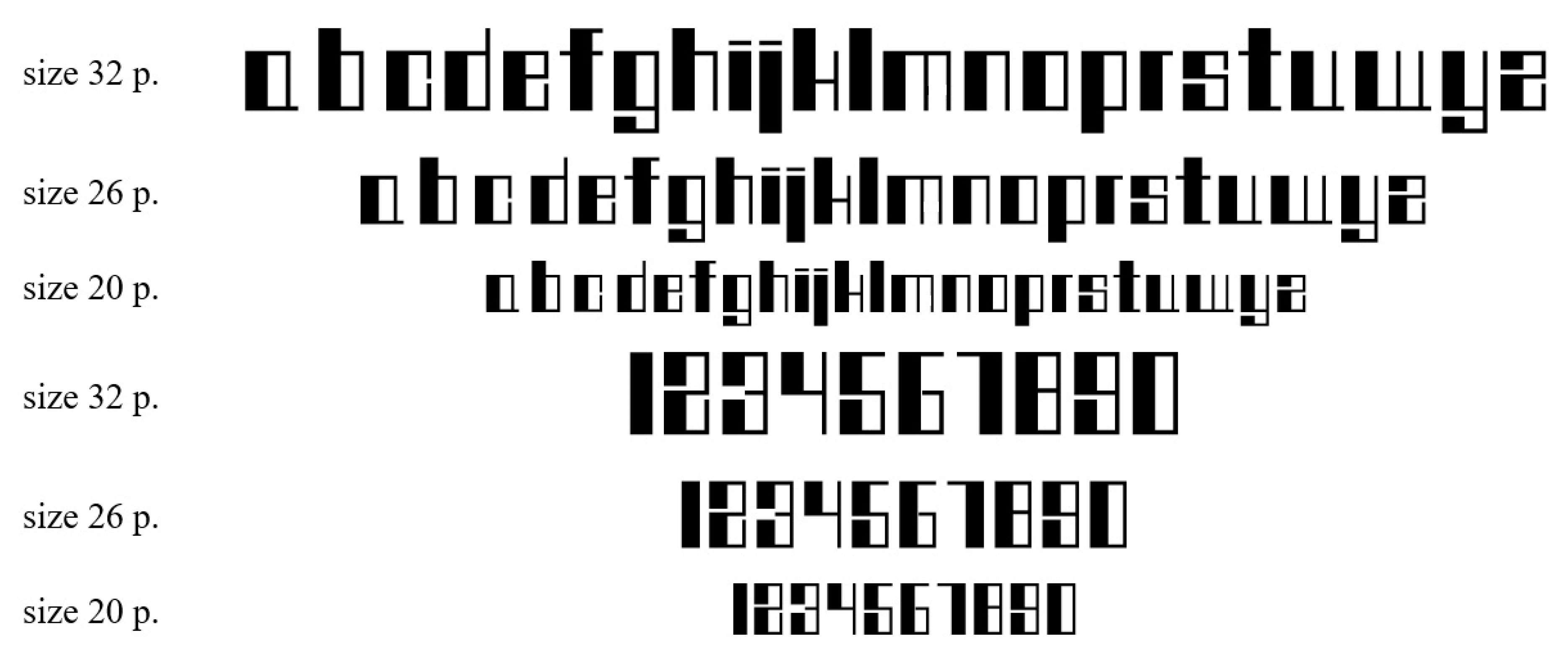
2.1. Construction of the Characters of the Safe Symmetrical Font
- (a)
- Height of the lowercase characters:
- (b)
- Height of characters with ascender or descender (as well as the height of digits and capital letters):
- (c)
- Width of the lowercase letters, capital letters, and digits (with the exception of “m”):
- (d)
- Width of “m” (lowercase and capital letters):
- (e)
- Width of vertical lines and the clearance between the vertical lines:
- (f)
- Width of horizontal lines:
- (g)
- Width of ascenders and descenders:
2.2. Construction of the Characters of the Safe Asymmetrical Font
- (a)
- Height of the lowercase letters:
- (b)
- Height of characters with ascenders or descenders (as well as the height of digits and capital letters):
- (c)
- Width of the lowercase letters, capital letters, and digits (with the exception of “m”):
- (d)
- Width of “m” (i.e., the lowercase and capital letters):
- (e)
- Width of the vertical lines ( and the clearance between the vertical lines (:
- (f)
- Width of the horizontal lines:
- (g)
- Width of ascenders and descenders:
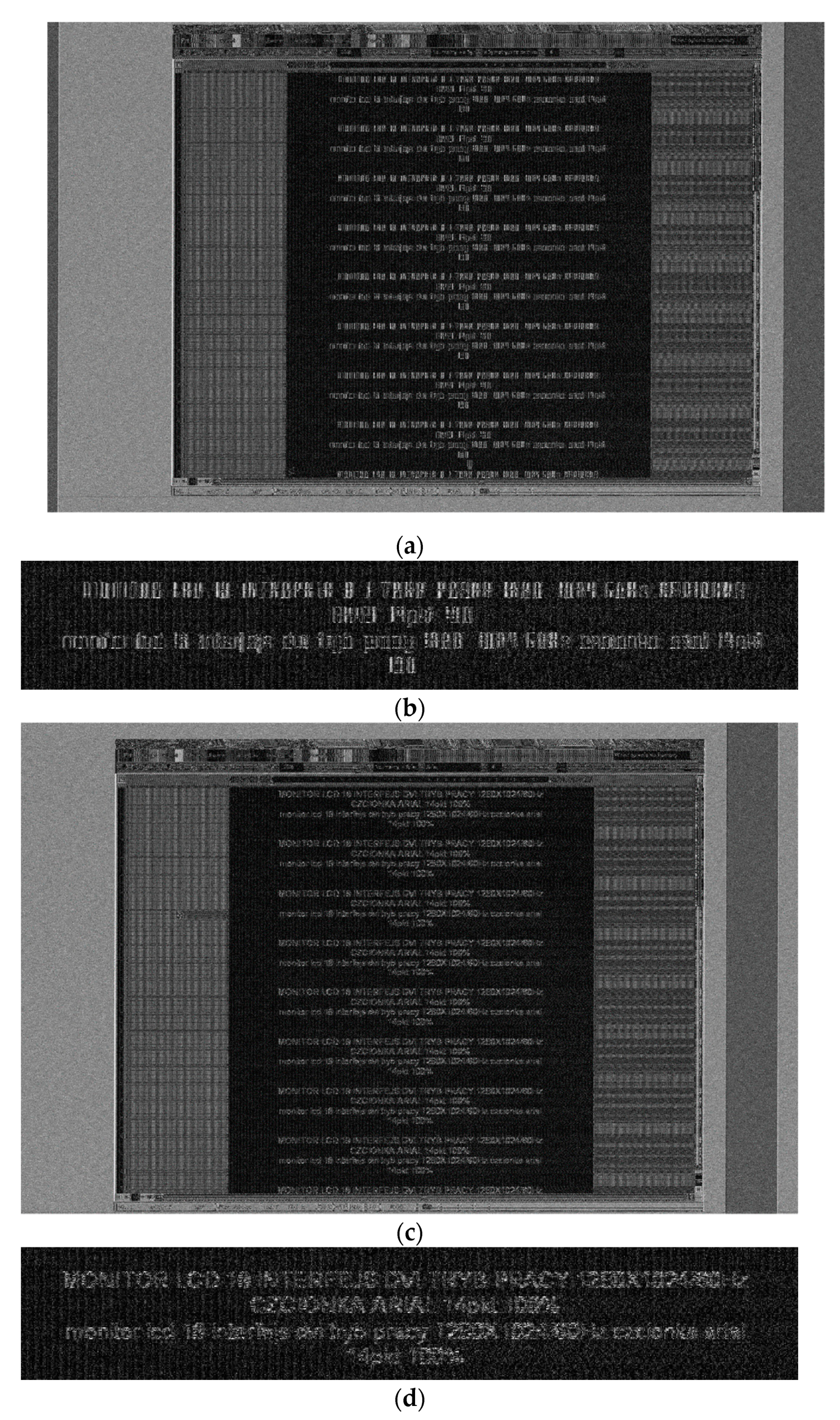
3. Results
4. Discussion
5. Patents
Funding
Conflicts of Interest
Appendix A

References
- Shainir, A.; Rappoport, A. Extraction of Typographic Elements from Outline Representations of Fonts. Comput. Gr. Forum 1996, 15, 259–268. [Google Scholar] [CrossRef]
- Nanxuan, Z.; Ying, C.; Lau, W.H. Modeling Fonts in Context: Font Prediction on Web Designs. Comput. Gr. Forum 2018, 37, 385–395. [Google Scholar] [CrossRef]
- Jun, S.; Yongacoglu, A.; Sun, D.; Dong, W. Computer LCD recognition based on the compromising emanations in cyclic frequency domain. In Proceedings of the IEEE International Symposium on Electromagnetic Compatibility, Ottawa, QC, Canada, 25–29 July 2016; pp. 164–169. [Google Scholar] [CrossRef]
- Lee, H.K.; Kim, J.H.; Kim, S.C. Emission Security Limits for Compromising Emanations Using Electromagnetic Emanation Security Channel Analysis. IEICE Trans. Commun. 2013, E96, 2639–2649. [Google Scholar] [CrossRef]
- Tae-Lim, S.; Yi-Ru, J.; Jong, Y. Modeling of Leaked Digital Video Signal and Information Recovery Rate as a Function of SNR. IEEE Trans. Electromagn. Compat. 2015, 57, 164–172. [Google Scholar]
- Kubiak, I. Video signal level (colour intensity) and effectiveness of electromagnetic infiltration. Bull. Pol. Acad. Sci. Tech. Sci. 2016, 64, 207–218. [Google Scholar] [CrossRef] [Green Version]
- Kubiak, I. Laser printer as a source of sensitive emissions. Turk. J. Electr. Eng. Comput. Sci. 2018, 26, 1354–1366. [Google Scholar] [CrossRef]
- Mahshid, Z.; Saeedeh, H.T.; Ayaz, G. Security limits for Electromagnetic Radiation from CRT Display. In Proceedings of the Second International Conference on Computer and Electrical Engineering, Dubai, UAE, 28–30 January 2009; pp. 452–456. [Google Scholar]
- Nan, Z.; Yinghua, L.; Qiang, C.; Yiying, W. Investigation of Unintentional Video Emanations from a VGA Connector in the Desktop Computers. IEEE Trans. Electromagn. Compat. 2017, 59, 1826–1834. [Google Scholar]
- Licciardo, G.D.; Cappetta, C.; Benedetto, L. Design of a Convolutional Two-Dimensional Filter in FPGA for Image Processing Applications. Computers 2017, 6, 19. [Google Scholar] [CrossRef]
- Kubiak, I. LED printers and safe fonts as an effective protection against the formation of unwanted emission. Turk. J. Electr. Eng. Comput. Sci. 2017, 25, 4268–4279. [Google Scholar] [CrossRef]
- Kubiak, I. TEMPEST font counteracting a non-invasive acquisition of text data. Turk. J. Electr. Eng. Comput. Sci. 2018, 26, 582–592. [Google Scholar] [CrossRef]
- Kubiak, I. Industrial Design. Polish Patent No. 24487, 31 September 2018. [Google Scholar]
- Kubiak, I. Method for Protecting Transmission of Information. Polish Patent No. P.408372, 29 March 2019. [Google Scholar]
- Anari, V.; Razzazi, F.; Amirfattahi, R. A Sparse Analysis-Based Single Image Super-Resolution. Computers 2019, 8, 41. [Google Scholar] [CrossRef]
- Mingyuan, X.; Yong, W. Research on image classification model based on deep convolution neural network. EURASIP J. Image Video Process. 2019, 2019, 40. [Google Scholar] [Green Version]
- Manson, J.; Schaefer, S. Wavelet Rasterization. Comput. Gr. Forum 2011. [Google Scholar] [CrossRef]
- Jinming, L.; Jiemin, Z.; Taikang, L.; Yongmei, L. The reconstitution of LCD compromising emanations based on wavelet denoising. In Proceedings of the 12th International Conference on Computer Science and Education (ICCSE), Houston, TX, USA, 22–25 August 2017; pp. 294–297. [Google Scholar] [CrossRef]
- Salem, M.; Taheri, S.; Yuan, J.S. Utilizing Transfer Learning and Homomorphic Encryption in a Privacy Preserving and Secure Biometric Recognition System. Computers 2019, 8, 3. [Google Scholar] [CrossRef]
- Litao, W. Analysis and Measurement on the Electromagnetic Compromising Emanations of Computer Keyboards. In Proceedings of the Seventh International Conference on Computational Intelligence and Security, Sanya, China, 3–4 December 2011; pp. 640–643. [Google Scholar] [CrossRef]
- Litao, W.; Bin, Y. Research on the compromising electromagnetic emanations from digital signals. In Proceedings of the International Conference on Automatic Control and Artificial Intelligence (ACAI 2012), Xiamen, China, 3–5 March 2012; pp. 1761–1764. [Google Scholar] [CrossRef]
- Kubiak, I. The Influence of the Structure of Useful Signal on the Efficacy of Sensitive Emission of Laser Printers. Measurement 2018, 119, 63–76. [Google Scholar] [CrossRef]
- Kubiak, I. Computer Font Resistant to Electromagnetic Infiltration; Publisher House of Military University of Technology: Warsaw, Poland, 2014; ISBN 978-83-7938-018-3. [Google Scholar]
- Tokarev, A.B.; Pitolin, V.M.; Beletskaya, S.Y.; Bulgakov, A.V. Detection of informative components of compromising electromagnetic emanations of computer hardware. Int. J. Comput. Technol. Appl. 2016, 9, 9–19. [Google Scholar]














| Character Correlation Coefficient R | Number of Relationships | |||||||
|---|---|---|---|---|---|---|---|---|
| (1) | (2) | (3) | (4) | (5) | (6) | (7) | (8) | |
lack relationship | 0 | 0 | 4 | 9 | 1 | 0 | 13 | 89 |
weak relationship | 1 | 6 | 87 | 98 | 35 | 35 | 167 | 129 |
moderate relationship | 78 | 95 | 129 | 129 | 165 | 175 | 73 | 35 |
rather strong relationship | 129 | 111 | 31 | 17 | 44 | 43 | 0 | 0 |
very strong relationship | 45 | 41 | 2 | 0 | 8 | 0 | 0 | 0 |
| Character | Arial Font | Times New Roman Font | Safe Symmetrical Font | Safe Asymmetrical Font |
|---|---|---|---|---|
| VGA Standard | ||||
| a | 1 | 2 | 1 | 4 |
| c | 3 | 5 | 7 | 350 |
| h | 51 | 0 | 310 | 6 |
| n | 31 | 39 | 283 | 183 |
| s | 1 | 3 | 40 | 204 |
| DVI (HDMI) Standard | ||||
| a | 1 | 4 | 91 | 21 |
| c | 3 | 11 | 97 | 509 |
| h | 3 | 4 | 50 | 60 |
| n | 7 | 6 | 431 | 80 |
| s | 1 | 1 | 156 | 70 |
| Laser Printer (Double-Diode System, Resolution: 600 dpi × 600 dpi) | ||||
| a | 3 | 5 | 3 | 122 |
| c | 0 | 5 | 19 | 98 |
| h | 5 | 0 | 20 | 95 |
| n | 3 | 10 | 73 | 104 |
| s | 2 | 3 | 3 | 75 |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kubiak, I. Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition. Computers 2019, 8, 70. https://doi.org/10.3390/computers8040070
Kubiak I. Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition. Computers. 2019; 8(4):70. https://doi.org/10.3390/computers8040070
Chicago/Turabian StyleKubiak, Ireneusz. 2019. "Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition" Computers 8, no. 4: 70. https://doi.org/10.3390/computers8040070
APA StyleKubiak, I. (2019). Font Design—Shape Processing of Text Information Structures in the Process of Non-Invasive Data Acquisition. Computers, 8(4), 70. https://doi.org/10.3390/computers8040070





