Formation of Stable and Efficient Social Storage Cloud
Abstract
:1. Introduction
2. Social Storage Cloud Model
2.1. Interaction Structure
2.2. Storage Sharing
2.3. Agent’s Utility and Symmetry
2.4. Pairwise Stability
- for all such that , , and ; and
- for all such that , if , then .
3. Network Structure and Storage Availability
3.1. Effect of Link Alteration on Closeness
- Let us assume there is no path between i and j in , then , thus, and decrease by 1 in .
- Now, let us assume there exists a path between i and j in , the distance between i and j in being at least 1 more than that in . Thus, and decrease by at least in . ☐
3.2. Effect of Closeness on Distances of Agents Not Involved in Link Alteration
- Suppose . As , k observes i before j on all shortest paths . This implies .
- Suppose . As , k observes i before j, and j before l, on all shortest paths . This implies . ☐
3.3. Effect of Link Alteration on Storage Availability
- , and
- implies that . Similarly, if , then .
3.4. Externalities
- Positive externalities if ;
- Negative externalities if ;
- No externalities if .
- Positive externalities if ;
- Negative externalities if ;
- No externalities if .
- By Definition 6,.As agent k does not pay the cost for link , we have .Thus, .
- For Cases 2 and 3, the proof is similar to that of Case 1. ☐
4. Characterization of Stable and Efficient Networks
4.1. Stable Networks: Characterization, Existence, and Uniqueness
- for all , and ; and
- for all if , then .
- 1.
- If , then is the null network.
- 2.
- If , then consists of
- (a)
- a set of connected pairs of agents, if N is even; or
- (b)
- a set of connected pairs of agents and one isolated agent, if N is odd.
4.2. Efficient Network, Price of Anarchy, and Price of Stability
5. Conclusions
5.1. Research Implications
5.2. Limitations
5.3. Future Scope
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
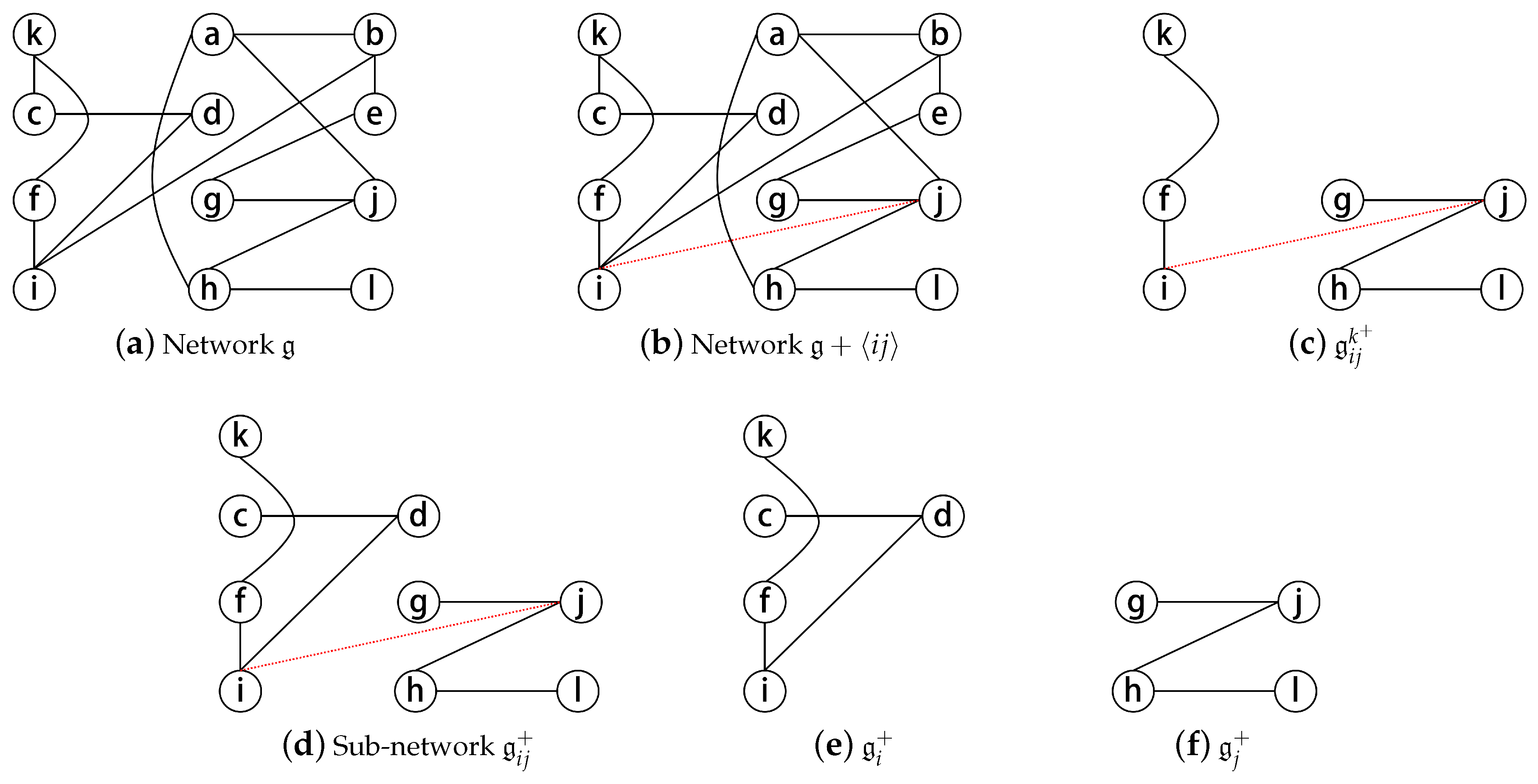
Appendix A. Example
Appendix B. Results Owing to Link Deletion
Appendix B.1. Effect of Closeness on Distances of Agents not Involved in Link Deletion
Appendix B.2. Effect of Link Deletion on Storage Availability
- 1.
- .
- 2.
- If , then . Similarly, if , then .
Appendix C. Proof of Lemma 6

Appendix D. Experimental Results
References
- Chard, K.; Bubendorfer, K.; Caton, S.; Rana, O.F. Social cloud computing: A vision for socially motivated resource sharing. IEEE Trans. Serv. Comput. 2012, 5, 551–563. [Google Scholar] [CrossRef]
- Tran, N.; Chiang, F.; Li, J. Efficient cooperative backup with decentralized trust management. Trans. Storage 2012, 8, 8:1–8:25. [Google Scholar] [CrossRef]
- Gracia-Tinedo, R.; Sánchez-Artigas, M.; García-López, P. F2Box: Cloudifying F2F storage systems with high availability correlation. In Proceedings of the 2012 IEEE Fifth International Conference on Cloud Computing (CLOUD), Honolulu, HI, USA, 24–29 June 2012; pp. 123–130. [Google Scholar]
- Moreno-Martínez, A.; Gracia-Tinedo, R.; Sánchez-Artigas, M.; Garcia-Lopez, P. FRIENDBOX: A cloudified F2F storage application. In Proceedings of the 2012 IEEE 12th International Conference on Peer-to-Peer Computing (P2P), Tarragona, Spain, 3–5 September 2012; pp. 75–76. [Google Scholar]
- Nguyen, T.D.; Li, J. BlockParty: Cooperative offsite backup among friends. In Proceedings of the 4th USENIX Symposium on Networked Systems Design & Implementation, Cambridge, MA, USA, 11–13 April 2007. [Google Scholar]
- Tran, N.; Li, J.; Subramanian, L.; Chow, S.S. Optimal Sybil-resilient node admission control. In Proceedings of the 2011 Proceedings IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 3218–3226. [Google Scholar]
- Zuo, X.; Iamnitchi, A. A survey of socially aware peer-to-peer systems. ACM Comput. Surv. 2016, 49, 9:1–9:28. [Google Scholar] [CrossRef]
- Freeman, L.C. Centrality in social networks conceptual clarification. Soc. Netw. 1978, 1, 215–239. [Google Scholar] [CrossRef]
- Borgatti, S.P.; Everett, M.G. A Graph-theoretic perspective on centrality. Soc. Netw. 2006, 28, 466–484. [Google Scholar] [CrossRef]
- Boldi, P.; Vigna, S. Axioms for centrality. Internet Math. 2014, 10, 222–262. [Google Scholar] [CrossRef]
- Bloch, F.; Jackson, M.O.; Tebaldi, P. Centrality measures in networks. arXiv 2017, arXiv:1608.05845. [Google Scholar] [CrossRef]
- Skibski, O.; Sosnowska, J. Axioms for distance-based centralities. In Proceedings of the Thirty-Second AAAI Conference on Artificial Intelligence, New Orleans, LA, USA, 2–7 February 2018; pp. 1218–1225. [Google Scholar]
- Rao, N.S.V.; Ma, C.Y.T.; He, F.; Yau, D.K.Y.; Zhuang, J. Cyber-physical correlation effects in defense games for large discrete infrastructures. Games 2018, 9, 52. [Google Scholar] [CrossRef]
- Altman, E.; Kameda, H.; Hosokawa, Y. Nash equilibria in load balancing in distributed computer systems. Int. Game Theory Rev. 2002, 04, 91–100. [Google Scholar] [CrossRef]
- Hausken, K. Information sharing among cyber hackers in successive attacks. Int. Game Theory Rev. 2017, 19, 1750010-1–1750010-33. [Google Scholar] [CrossRef]
- Timmer, J.; Scheinhardt, W. Customer and cost sharing in a Jackson network. Int. Game Theory Rev. 2018, 20, 1850002-1–1850002-10. [Google Scholar] [CrossRef]
- Pilling, R.; Chang, S.C.; Luh, P.B. Shapley value-based payment calculation for energy exchange between micro- and utility grids. Games 2017, 8, 45. [Google Scholar] [CrossRef]
- Sanchez-Soriano, J. An overview on game theory applications to engineering. Int. Game Theory Rev. 2013, 15, 1340019-1–1340019-18. [Google Scholar] [CrossRef]
- Dutta, B.; Jackson, M.O. On the formation of networks and groups. In Networks and Groups: Models of Strategic Formation (Studies in Economic Design), 1st ed.; Dutta, B., Jackson, M.O., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; Volume VIII, pp. 1–15. [Google Scholar]
- Jackson, M.O. A survey of network formation models: Stability and efficiency. In Group Formation in Economics: Networks, Clubs, and Coalitions; Demange, G., Wooders, M., Eds.; Cambridge University Press: Cambridge, UK, 2005; pp. 11–57. [Google Scholar]
- Marini, M.A. Games of coalition and network formation: A survey. In Networks, Topology and Dynamics, 1st ed.; Naimzada, A.K., Stefani, S., Torriero, A., Eds.; Lecture Notes in Economics and Mathematical Systems; Springer: Berlin/Heidelberg, Germany, 2009; Volume 613, pp. 67–93. [Google Scholar]
- Borkotokey, S.; Gogoi, L.; Sarangi, S. A survey of player-based and link-based allocation rules for network games. Stud. Micro. 2014, 2, 5–26. [Google Scholar] [CrossRef]
- Mane, P.C.; Ahuja, K.; Krishnamurthy, N. Stability, efficiency, and contentedness of social storage networks. Ann. Oper. Res. 2019, 1–32. [Google Scholar] [CrossRef]
- Morrill, T. Network formation under negative degree-based externalities. Internat. J. Game Theory 2011, 40, 367–385. [Google Scholar] [CrossRef]
- Möhlmeier, P.; Rusinowska, A.; Tanimura, E. A degree-distance-based connections model with negative and positive externalities. J. Public Econ. Theory 2016, 18, 168–192. [Google Scholar] [CrossRef]
- Jackson, M.O.; Wolinsky, A. A strategic model of social and economic networks. J. Econ. Theory 1996, 71, 44–74. [Google Scholar] [CrossRef]
- Opsahl, T.; Agneessens, F.; Skvoretz, J. Node centrality in weighted networks: Generalizing degree and shortest paths. Soc. Networks 2010, 32, 245–251. [Google Scholar] [CrossRef]
- Marchiori, M.; Latora, V. Harmony in the small-world. Phys. A 2000, 285, 539–546. [Google Scholar] [CrossRef] [Green Version]
- Lillibridge, M.; Elnikety, S.; Birrell, A.; Burrows, M.; Isard, M. A cooperative Internet backup scheme. In Proceedings of the Annual Conference on USENIX Annual Technical Conference, San Antonio, TX, USA, 9–14 June 2003; pp. 29–41. [Google Scholar]
- Landers, M.; Zhang, H.; Tan, K.L. PeerStore: Better performance by relaxing in peer-to-peer backup. In Proceedings of the Fourth International Conference on Peer-to-Peer Computing, Zurich, Switzerland, 27–27 August 2004; pp. 72–79. [Google Scholar]
- Cox, L.P.; Murray, C.D.; Noble, B.D. Pastiche: Making backup cheap and easy. SIGOPS Oper. Syst. Rev. 2002, 36, 285–298. [Google Scholar] [CrossRef]
- Jackson, M.O. Social and Economic Networks, 2nd ed.; Princeton University Press: Princeton, NJ, USA, 2010; pp. 215–216. [Google Scholar]
- Sharma, R.; Datta, A.; DeH’Amico, M.; Michiardi, P. An empirical study of availability in friend-to-friend storage systems. In Proceedings of the 2011 IEEE International Conference on Peer-to-Peer Computing, Kyoto, Japan, 31 August–2 September 2011; pp. 348–351. [Google Scholar]
- Zuo, X.; Blackburn, J.; Kourtellis, N.; Skvoretz, J.; Iamnitchi, A. The power of indirect ties in friend-to-friend storage systems. In Proceedings of the 14-th IEEE International Conference on Peer-to-Peer Computing, London, UK, 8–12 September 2014; pp. 1–5. [Google Scholar]
- Bala, V.; Goyal, K. A noncooperative model of network formation. Econometrica 2000, 68, 1181–1229. [Google Scholar] [CrossRef]
- Johnson, C.; Gilles, R. Spatial social networks. Rev. Econ. Des. 2000, 5, 273–299. [Google Scholar] [CrossRef]
- Moscibroda, T.; Schmid, S.; Wattenhofer, R. Topological implications of selfish neighbor selection in unstructured peer-to-peer networks. Algorithmica 2011, 61, 419–446. [Google Scholar] [CrossRef]
- Buechel, B. Network Formation with Closeness Incentives. In Networks, Topology and Dynamics: Theory and Applications to Economics and Social Systems, 1st ed.; Naimzada, A.K., Stefani, S., Torriero, A., Eds.; Lecture Notes in Economics and Mathematical Systems; Springer: Berlin/Heidelberg, Germany, 2009; Volume 613, pp. 95–109. [Google Scholar]
| 1. | http://www.buddybackup.com (accessed on 21 June 2019). |
| 2. | https://support.crashplan.com (accessed on 21 June 2019). |
| 3. | https://developers.facebook.com/docs/graph-api (accessed on 21 June 2019). |
| 4. | |
| 5. | |
| 6. | |
| 7. | We assume, , that is, a pair of agents involved in a link share the cost . |
| 8. | For simplicity, we assume uniform data loss rate . |
| 9. | https://www.backblaze.com/blog/backblaze-hard-drive-stats-q1-2019/ (accessed on 04 September 2019). |
| social storage cloud. | |
| set of agents (or vertices). | |
| N | the number of elements in the set , which is the number of agents in . |
| set of links (or edges). | |
| link between agents i and j. | |
| cost incurred by each agent to maintain a link. | |
| probability that an agent loses its data. | |
| worth (or value) that each agent has for its data. | |
| closeness of agent i in . | |
| probability that agent i obtains storage space from agent j in . | |
| probability that agent i obtains storage space from at least one agent in . | |
| neighborhood size of agent i in . Also denotes the set of neighbors of i. | |
| a path from agent to in such that . | |
| the length of the shortest path connecting agents i and j in . | |
| new link is added to . | |
| existing link is deleted from . | |
| the set of all networks on N agents. | |
| utility of agent i in . |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mane, P.C.; Krishnamurthy, N.; Ahuja, K. Formation of Stable and Efficient Social Storage Cloud. Games 2019, 10, 44. https://doi.org/10.3390/g10040044
Mane PC, Krishnamurthy N, Ahuja K. Formation of Stable and Efficient Social Storage Cloud. Games. 2019; 10(4):44. https://doi.org/10.3390/g10040044
Chicago/Turabian StyleMane, Pramod C., Nagarajan Krishnamurthy, and Kapil Ahuja. 2019. "Formation of Stable and Efficient Social Storage Cloud" Games 10, no. 4: 44. https://doi.org/10.3390/g10040044
APA StyleMane, P. C., Krishnamurthy, N., & Ahuja, K. (2019). Formation of Stable and Efficient Social Storage Cloud. Games, 10(4), 44. https://doi.org/10.3390/g10040044





