A Model of Competing Gangs in Networks
Abstract
:1. Introduction
1.1. Motivation
1.2. Related Work
1.3. Organization of the Paper
2. The Model
- We restrict our analysis to two concurrent groups, i.e., that exert negative externalities on each other (communitarian model with two groups).
- All externalities are of the same intensity within group and inter-group .
- We consider the ’full inter-connection case’, where any two agents of different groups are linked. One interpretation of the full interconnection case is that inter-group confrontations are uniform in the sense that the aggregate crime production of the opposite group hurts each agent. Another interpretation is probabilistic: represents the probability of facing each agent of the opposite group.
- (i)
- The crime level is:(For in the second equality.)
- (ii)
- .
- (iii)
- Suppose that is fixed. Then, attains its maximum when .
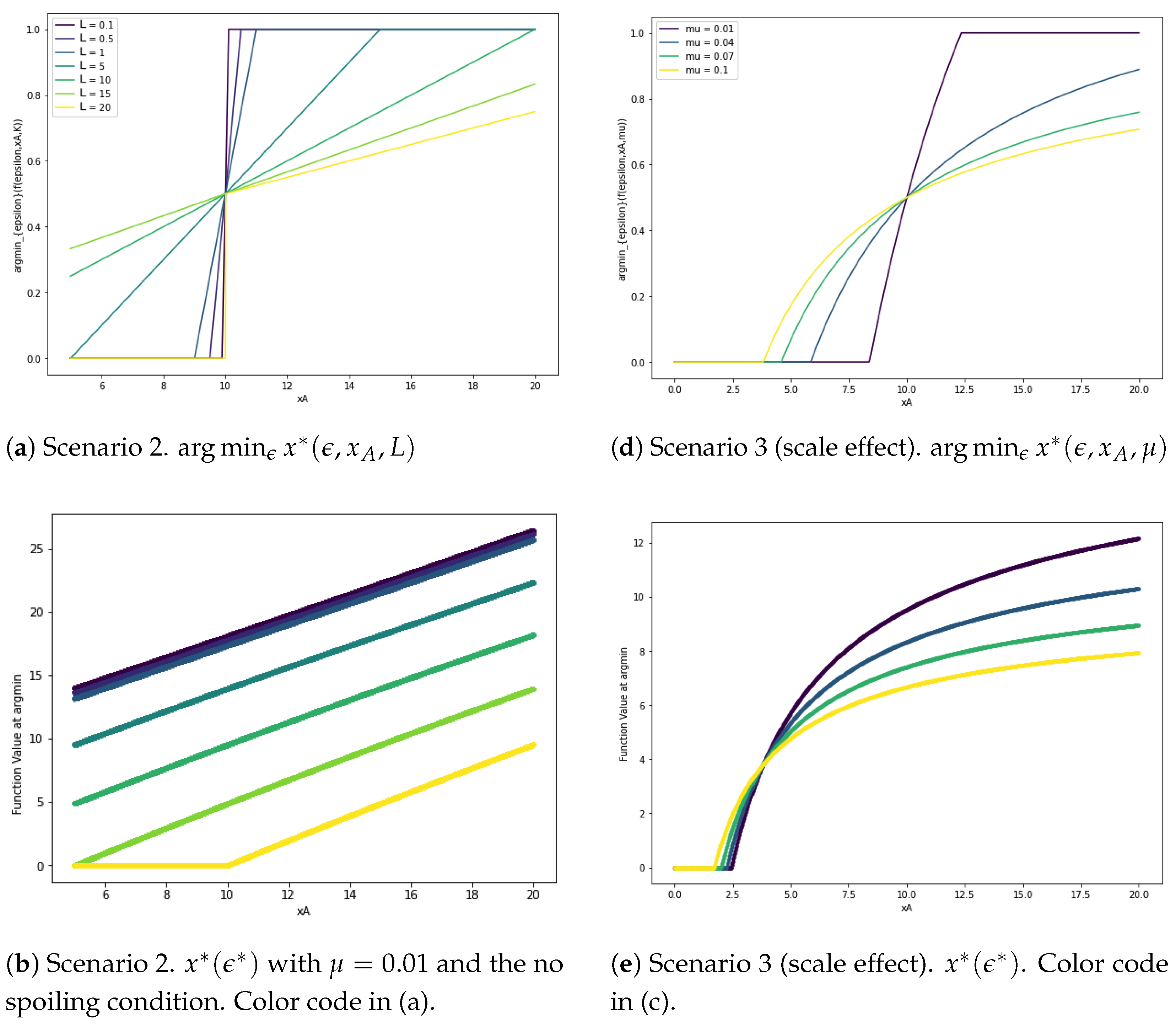
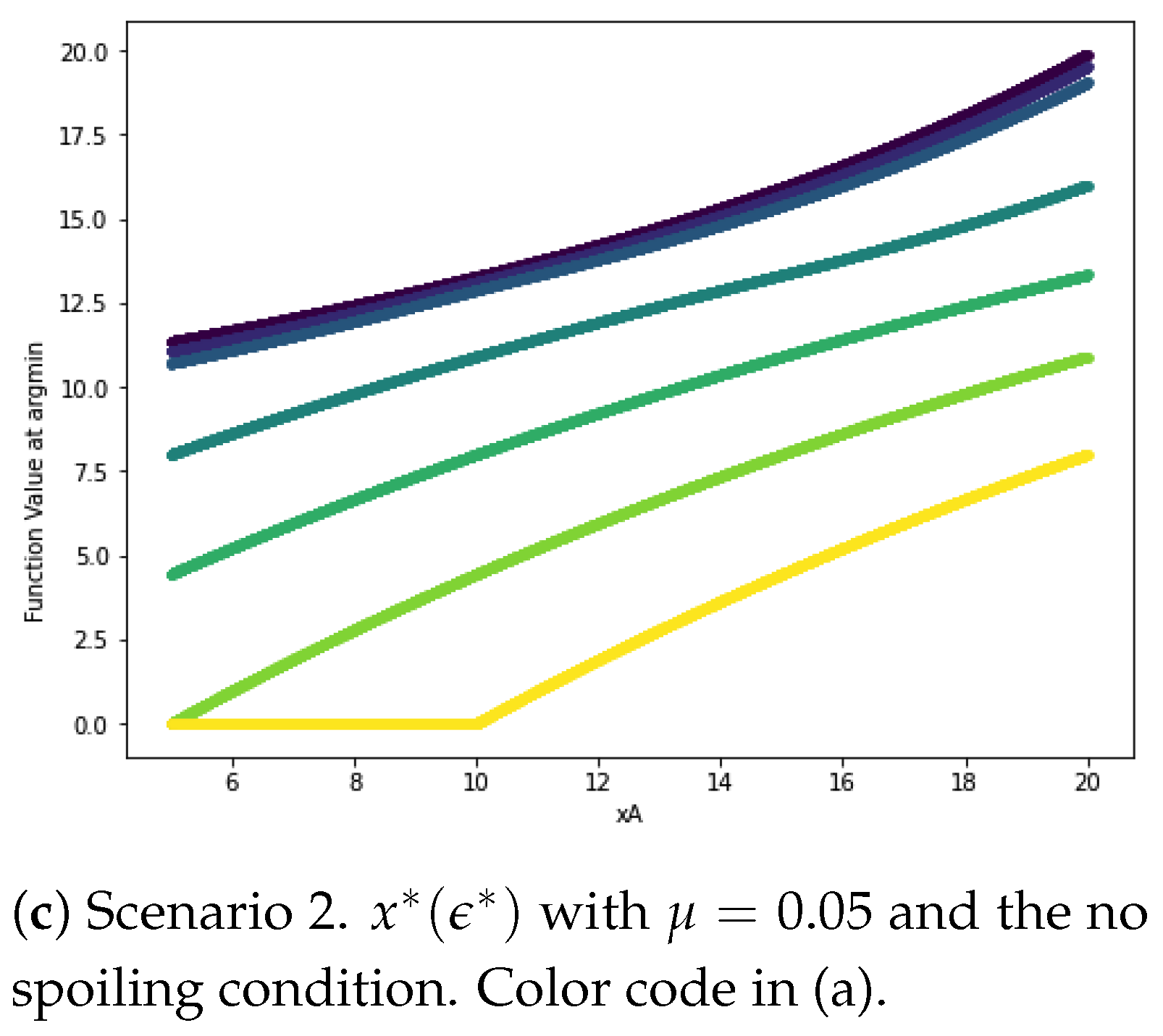
3. Consequence for the Police: Focusing or Splitting the Resources?
4. Conclusions
4.1. Limitations of the Model
- While can be proxied and arguably estimated, the question arises: how would the police observe autarkic activities?
- Agents exerting complementary efforts, such as those belonging to the same gang, typically communicate closely. Thus, a more nuanced approach to the problem exists beyond simply targeting groups or key players. We would assume that connected criminals face correlated probabilities of being captured, not only because they could betray each other but simply because they are involved in the same criminal activities. Mathematically, if (indicating that agent j increases agent i criminal activity), then if j is caught, and i should face a higher probability of being caught as well.
- The model can be argued to be excessively quantitative. In contrast to Calvó-Armengol and Zenou [2], which proposes a model where criminals perceive more expected benefits in crime than in the job market, and where agents first decide whether to participate in the job market or the crime market and then determine the level of crime to engage in, our model lacks a qualitative dimension of delinquency. Exerting a strictly positive level of crime, even a small one, is still being involved in crime. Being active should significantly differ from not being active. The absence of a binary decision on criminal activity participation somehow bypasses the decision-making aspect of criminal behavior, the moral dimension of criminality and its sociological implications, along with the intricate dynamics of crime and activity within mafias (including the snowball effect of illegal activities).
4.2. Perspectives
- A more in-depth exploration of the nature of crime is essential. For instance, consider focusing on the quantity of drugs purchased on the drug market. While the negative externality effectively portrays the substitution effect (where a drug consumer shifting from one gang diminishes the sales of another), it fails to adequately represent the heightened competition that should result in a more intense conflict between gangs. This negative externality lacks the depth to capture the potential escalation into a more ferocious fight. It prompts us to question the specific crime under investigation and whether we intend to disregard inter-gang murders in our model.
- Numerous traditional games on networks are static, including this one. Dynamic and endogenous games on agents’ behavior and link formation align more closely with the actual challenges faced by the police in their fight against criminality.
- Finally, it is crucial to recall that, in real life, the network is not fixed. For instance, the war against terrorism is not only focused on eliminating terrorists but also involves shaping the perception of conflicts in the eyes of social groups with access to the media.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
- (i)
- Straightforward from Theorem 1.
- (ii)
- , the harmonic mean of and . But, since it also holds that .
- (iii)
- Let us fix . We have:which attains its maximum when
| 1 | The classical idea according to which aid (for example, in the form of education) creates reservation utility is tested, e.g., in Azam and Thelen [64]; according to Azam [65], the effect of education on the opportunity cost can be mitigated by the ’revelation’ of their type to potential terrorists. One can also mention Collier and Hoeffler [66], who investigate a utility-based model and conditions under which rebels have an interest in sparking a civil war. A version of our model capturing the decision-making of people to engage in gangs would be a significant improvement, as we suggest in the perspectives section. |
References
- Ballester, C.; Calvó-Armengol, A.; Zenou, Y. Who’s who in networks. Wanted: The key player. Econometrica 2006, 74, 1403–1417. [Google Scholar] [CrossRef]
- Calvó-Armengol, A.; Zenou, Y. Social networks and crime decisions: The role of social structure in facilitating delinquent behavior. Int. Econ. Rev. 2004, 45, 939–958. [Google Scholar] [CrossRef]
- Cao, Z.; Gao, H.; Qu, X.; Yang, M.; Yang, X. Fashion, cooperation, and social interactions. PLoS ONE 2013, 8, e49441. [Google Scholar] [CrossRef] [PubMed]
- Calvó-Armengol, A.; Patacchini, E.; Zenou, Y. Peer Effects and Social Networks in Education. Rev. Econ. Stud. 2009, 76, 1239–1267. [Google Scholar] [CrossRef]
- Ballester, C.; Calvó-Armengol, A.; Zenou, Y. Deliquent networks. J. Eur. Econ. Assoc. 2010, 8, 34–61. [Google Scholar] [CrossRef]
- Ushchev, P.; Zenou, Y. Social norms in networks. J. Econ. Theory 2020, 185, 104969. [Google Scholar] [CrossRef]
- Harary, F. On the notion of balance of a signed graph. Mich. Math. J. 1953, 2, 143–146. [Google Scholar] [CrossRef]
- Temurshoev, U. Who’s Who in Networks. Wanted: The Key Group; Working Papers 08-08; NET Institute: Daytona Beach Shores, FL, USA, 2008. [Google Scholar]
- Bloch, F.; Demange, G.; Kranton, R. Rumors and Social Networks. Int. Econ. Rev. 2018, 59, 421–448. [Google Scholar] [CrossRef]
- Galam, S. Sociophysics: A Physicist’s Modeling of Psycho-Political Phenomena; Springer: New York, NY, USA, 2012. [Google Scholar]
- Nyczka, P.; Sznajd-Weron, K.; Cislo, J. Phase transitions in the q-voter model with two types of stochastic driving. Phys. Rev. 2012, 86, 011105. [Google Scholar] [CrossRef]
- Berenbrink, P.; Giakkoupis, G.; Kermarrec, A.; Mallmann-Trenn, F. Bounds on the Voter Model in Dynamic Networks. arXiv 2016, arXiv:1603.01895. [Google Scholar]
- Buechel, B.; Mechtenberg, L. The swing voter’s curse in social networks. Games Econ. Behav. 2019, 118, 241–268. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 5th ed.; Simon and Schuster: New York, NY, USA, 2003. [Google Scholar]
- Rodriguez, M.; Schölkopf, B. Influence maximization in continuous time diffusion networks. In Proceedings of the 29th International Conference on Machine Learning, ICML 2012, Edinburgh, UK, 26 June–1 July 2012; Volume 1. [Google Scholar]
- Banerjee, A.; Chandrasekhar, A.; Duflo, E.; Jackson, M.O. Gossip: Identifying Central Individuals in a Social Network; CEPR Discussion Papers 10120, C.E.P.R. Discussion Papers. National Bureau of Economic Research: Cambridge, MA, USA, 2014. Available online: https://economics.mit.edu/sites/default/files/publications/Gossip-%20Identifying%20Central%20Individuals%20in%20a%20Socia.pdf (accessed on 1 November 2023).
- DeGroot, M.H. Reaching a consensus. J. Am. Stat. Assoc. 1974, 69, 118–121. [Google Scholar] [CrossRef]
- Friedkin, N.; Johnsen, E. Social influences and opinion. J. Math. Sociol. 1990, 15, 193–205. [Google Scholar] [CrossRef]
- Sznajd-Weron, K.; Sznajd, J. Opinion evolution in closed community. Int. J. Mod. Phys. 2001, 11, 1157–1165. [Google Scholar] [CrossRef]
- DeMarzo, P.; Vayanos, D.; Zwiebel, J. Persuasion bias, social influence, and unidimensional opinions. Q. J. Econ. 2003, 118, 909–968. [Google Scholar] [CrossRef]
- Galam, S.; Jacobs, F. The role of inflexible minorities in the breaking of democratic opinion dynamics. Phys. A Stat. Mech. Its Appl. 2007, 381, 366–376. [Google Scholar] [CrossRef]
- Shi, G.; Proutiere, A.; Johansson, M.; Baras, J.S.; Johansson, K.H. The Evolution of Beliefs over Signed Social Networks. Oper. Res. 2013, 64, 585–604. [Google Scholar] [CrossRef]
- Buechel, B.; Hellmann, T.; Klößner, S. Opinion dynamics and wisdom under conformity. J. Econ. Dyn. Control 2015, 52, 240–257. [Google Scholar] [CrossRef]
- Ghiglino, C.; Goyal, S. Keeping up with the neighbors: Social interaction in a market economy. J. Eur. Econ. Assoc. 2010, 8, 90–119. [Google Scholar] [CrossRef]
- Jackson, M.O.; López-Pintado, D. Diffusion and contagion in networks with heterogeneous agents and homophily. Netw. Sci. 2013, 1, 49–67. [Google Scholar] [CrossRef]
- Golub, B.; Jackson, M.O. Naive learning in social networks and the wisdom of crowds. Am. Econ. J. Microecon. 2010, 2, 112–149. [Google Scholar] [CrossRef]
- Hellmann, T.; Panebianco, F. The transmission of continuous cultural traits in endogenous social networks. Econ. Lett. 2018, 167, 51–55. [Google Scholar] [CrossRef]
- Liljeros, F.; Edling, C.R.; Nunes Amaral, L.A. Sexual networks: Implications for the transmission of sexually transmitted infections. Microbes Infect. 2003, 5, 189–196. [Google Scholar] [CrossRef] [PubMed]
- López-Pintado, D.; Watts, D. Social influence, binary decisions and collective dynamics. Ration. Soc. 2008, 20, 399–443. [Google Scholar] [CrossRef]
- Banerjee, A.V. A simple model of herd behavior. Q. J. Econ. 1992, 107, 797–817. [Google Scholar] [CrossRef]
- Chamley, C.; Gale, D. Information revelation and strategic delay in a model of investment. Econometrica 1994, 62, 1065–1085. [Google Scholar] [CrossRef]
- Chamley, C.P. Rational Herds: Economic Models of Social Learning; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Girard, R. Deceit, Desire and the Novel: Self and Other in Literary Structure; Johns Hopkins University: Baltimore, MD, USA, 1966. [Google Scholar]
- Girard, R. Violence and the Sacred; Johns Hopkins University: Baltimore, MD, USA, 1977. [Google Scholar]
- Girard, R. The Scapegoat; The Johns Hopkins University Press: Baltimore, MD, USA, 1986. [Google Scholar]
- Girard, R. Things Hidden Since the Foundation of the World; Stanford University Press: Redwood City, CA, USA, 1987. [Google Scholar]
- Altafini, C. Consensus Problems on Networks With Antagonistic Interactions. IEEE Trans. Autom. Control 2013, 58, 935–946. [Google Scholar] [CrossRef]
- Touboul, J. The hipster effect: When anticonformists all look the same. Discret. Contin. Dyn. Syst.-B 2019, 24, 4379–4415. [Google Scholar]
- Mahfuze, A. Product Quality and Social Influence. 2022. Available online: https://papers.ssrn.com/sol3/Delivery.cfm/SSRN_ID3853128_code2765587.pdf?abstractid=3853128&mirid=1 (accessed on 1 November 2023).
- Bramoullé, Y.; López-Pintado, D.; Goyal, S.; Vega-Redondo, F. Network formation and anti-coordination games. Int. J. Game Theory 2004, 33, 1–19. [Google Scholar] [CrossRef]
- Bramoullé, Y. Anti-coordination and social interactions. Games Econ. Behav. 2007, 58, 30–49. [Google Scholar] [CrossRef]
- López-Pintado, D. Network formation, cost sharing and anti-coordination. Int. Game Theory Rev. 2009, 11, 53–76. [Google Scholar] [CrossRef]
- Altafini, C. Dynamics of Opinion Forming in Structurally Balanced Social Networks. PLoS ONE 2012, 7, e38135. [Google Scholar] [CrossRef] [PubMed]
- Grabisch, M.; Rusinowska, A. A model of influence based on aggregation functions. Math. Soc. Sci. 2013, 66, 216–330. [Google Scholar] [CrossRef]
- Proskurnikov, A.; Matveev, A.; Cao, M. Opinion Dynamics in Social Networks with Hostile Camps: Consensus vs. Polarization. IEEE Trans. Autom. Control 2016, 61, 1524–1536. [Google Scholar] [CrossRef]
- Granovetter, M. Threshold models of collective behavior. Am. J. Sociol. 1978, 83, 1420–1443. [Google Scholar] [CrossRef]
- Watts, D.J. A simple model of global cascades on random networks. Proc. Natl. Acad. Sci. USA 2002, 99, 5766–5771. [Google Scholar] [CrossRef] [PubMed]
- Bramoullé, Y.; Kranton, R. Public goods in networks. J. Econ. Theory 2007, 135, 478–494. [Google Scholar] [CrossRef]
- Bramoullé, Y.; Kranton, R.; D’Amours, M. Strategic interaction and networks. Am. Econ. Rev. 2014, 104, 898–930. [Google Scholar] [CrossRef]
- Ballester, C.; Zenou, Y. Key player policies when contextual effects matter. J. Math. Sociol. 2014, 38, 233–248. [Google Scholar] [CrossRef]
- Buchholz, W.; Cornes, R.; Rübbelke, D. Public goods and public bads. J. Public Econ. Thory 2018, 10, 525–540. [Google Scholar] [CrossRef]
- Cabrales, A.; Calvó-Armengol, A.; Zenou, Y. Social Interactions and Spillovers. Games Econ. Behav. 2011, 72, 339–360. [Google Scholar] [CrossRef]
- Friedkin, N. A formal theory of social power. J. Math. Sociol. 2010, 12, 103–126. [Google Scholar] [CrossRef]
- de Swart, H.; Rusinowska, A. On Some Properties of the Hoede-Bakker Index. J. Math. Sociol. 2007, 31, 267–293. [Google Scholar]
- van den Brink, R.; Steffen, F. Positional Power in Hierarchies. In Power, Freedom, and Voting; Braham, M., Steffen, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 57–81. [Google Scholar]
- Acemoglu, D.; Como, G.; Fagnani, F.; Ozdaglar, A. Opinion Fluctuations and Disagreement in Social Network. Math. Oper. Res. 2010, 38, 1–27. [Google Scholar] [CrossRef]
- Bonacich, P. Power and centrality: A family of measures. Am. J. Sociol. 1987, 92, 1170–1182. [Google Scholar] [CrossRef]
- Martins, A. Mobility and Social Network Effects on Extremist Opinions. Phys. Rev. Stat. Nonlinear Soft Matter Phys. 2008, 78, 036104. [Google Scholar] [CrossRef] [PubMed]
- Bloch, F.; Jackson, M.O.; Tebaldi, P. Centrality Measures in Networks. SSRN Electron. J. 2016, 61, 413–453. [Google Scholar] [CrossRef]
- Allouch, N.; Meca, A.; Polotskaya, K. The Bonacich Shapley Centrality. 2021. Available online: https://www.kent.ac.uk/economics/repec/2106.pdf (accessed on 1 November 2023).
- Jackson, M.O. Social and Economic Networks; Princeton University Press: Princeton, NJ, USA, 2008. [Google Scholar]
- Bramoullé, Y.; Galeotti, A.; Rogers, B. The Oxford Handbook of the Economics of Networks; Oxford University Press: Oxford, UK, 2016. [Google Scholar]
- Allouch, N. On the private provision of public goods on networks. J. Econ. Theory 2015, 157, 527–552. [Google Scholar] [CrossRef]
- Azam, J.P.; Thelen, V. The roles of foreign aid and education in the war on terror. Public Choice 2008, 135, 375–397. [Google Scholar] [CrossRef]
- Azam, J.P. Why suicide-terrorists get educated, and what to do about It. Public Choice 2012, 153, 357–373. [Google Scholar] [CrossRef]
- Collier, P.; Hoeffler, A. On economic causes of civil war. Oxf. Econ. Pap. 1998, 50, 563–573. [Google Scholar] [CrossRef]
- Parise, F.; Ozdaglar, A. A variational inequality framework for network games: Existence, uniqueness, convergence and sensitivity analysis. Games Econ. Behav. 2020, 114, 47–82. [Google Scholar] [CrossRef]
- Horn, R.A.; Johnson, C.R. Matrix Analysis; Cambridge University Press: Cambridge, UK, 2012. [Google Scholar]
- Hager, W. Updating the inverse of a matrix. SIAM Rev. 1989, 31, 221–239. [Google Scholar] [CrossRef]
- Weyl, H. Das asymptotische Verteilungsgesetz der Eigenwerte linearer partieller Differentialgleichungen (mit einer Anwendung auf die Theorie der Hohlraumstrahlung. Math. Ann. 1912, 71, 441–479. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Poindron, A.; Allouch, N. A Model of Competing Gangs in Networks. Games 2024, 15, 6. https://doi.org/10.3390/g15020006
Poindron A, Allouch N. A Model of Competing Gangs in Networks. Games. 2024; 15(2):6. https://doi.org/10.3390/g15020006
Chicago/Turabian StylePoindron, Alexis, and Nizar Allouch. 2024. "A Model of Competing Gangs in Networks" Games 15, no. 2: 6. https://doi.org/10.3390/g15020006




