Secure Speech Content Based on Scrambling and Adaptive Hiding
Abstract
:1. Introduction
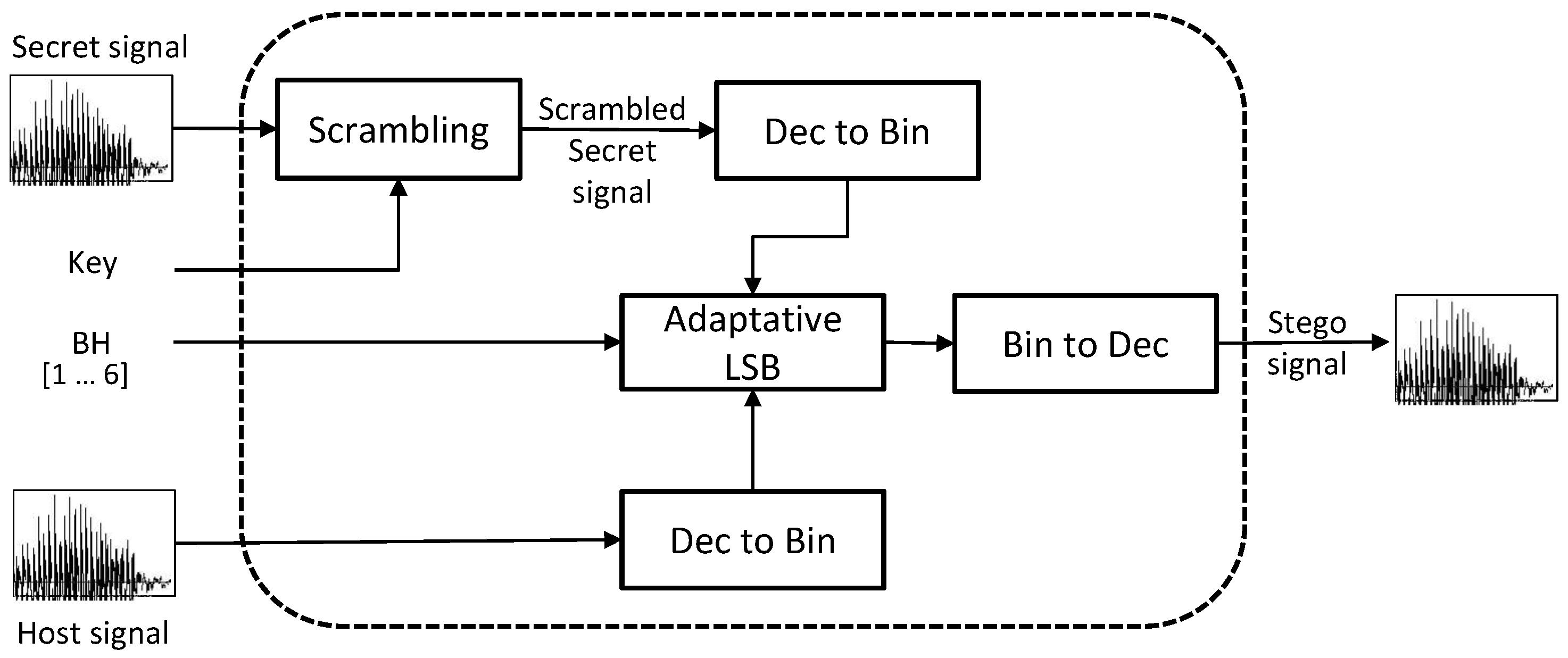
- The proposed system combines scrambling and steganography.
- The scrambling block allows a voice signal to imitate a super-Gaussian noise. The output signal (scrambled) is highly similar to the super-Gaussian noise. The key that permits descrambling the signal is a system out.
- The hiding of the scrambled signal within the host signal is done through an adaptive substitution technique, which allows control of the amount of signal distortion through the parameter bits to hold ().
- The final output signal (stego) is highly similar to the host signal and does not generate suspicion of the existence of a secret message within it. Without knowledge of the seed used to generate the super-Gaussian signal, as well as the value of BIH, a non-authorised user can not reveal the secret content.
2. Imitation Property of Speech Signals
3. Proposed Scheme
3.1. Hiding Module
3.1.1. Scrambling
3.1.2. Binary Representation (Dec to Bin)
3.1.3. Adaptive LSB
- Reading the number of bits to hold ().
- Representing the samples of the host signal in 16-bit format. The resulting signal is called i.
- Determining the minimum quantity of necessary bits to represent the sample of the host signal. This value is assigned to the MSB (most significant bit) variable.
- Converting to zero the less significant () bits from H (Equation (4)). The resulting signal will be called .where is the “Bits to Hold” value, H is the sample of the host signal in 16-bits format, corresponds to the modified H sample, is the minimum quantity of bits to represent H, and is the integer part operator.
- Reading the chain of binary values derived from the Binary Representation block. Selecting a quantity of bits equal to ().
- Converting the previous binary value to decimal and adding the result to . The result is called S.
- Repeating the previous steps until hiding all the bits of the binary chain in the host signal.
3.1.4. Decimal-Binary Conversion
3.2. Recovery Module
3.2.1. Adaptive LSB Extraction
- Reading the stego signal and the value.
- Representing the samples of the stego signal in a 16-bit format. The resulting signal will be referred to as S.
- Extracting the least significant bits from every sample (Equation (5)).where T corresponds to the decimal value of extracted bits, which is later converted into a binary value.Equation (5) is applied on all the samples of the stego signal, creating a bit sequence.
3.2.2. Bit to Sample Conversion
- Calculating the value of by using Equation (6).
- Taking the first from the binary sequence obtained in the “adaptive LSB extraction” block.
- Dividing the previous result in groups of non-overlapped .
- Converting each group of Nbits into decimal values (thus obtaining a sample).
- Normalisation is applied to each sample, in order for the dynamic range to be the same as the one from the secret message (e.g., [−1 1] V).
3.2.3. Descrambling
4. Method Implementation and Validation
4.1. Testing Protocol
- Ten 2-s host signals
- Ten 1-s secret messages
- A sampling frequency of 8 kHz for all signals
- is an integer within the range [1 6]
- Each secret message was hidden in each host signal, with different values. The total number of tests was 600 (number of host signals × number of secret messages × amount of values)
- The secret messages, host signals, stego signals, and recovered signals with correct and incorrect key are published in [18], “Speech steganography based on scrambling and hiding (Spanish audios)”, Mendeley Data, v1.
4.2. Preliminary Results
4.3. Imperceptibility
4.4. Quality of the Recovered Message
4.5. Comparison with State-of-the-Art Methods
5. Security Analysis
5.1. Exhaustive Key Search
5.2. Ciphertext Only Attack
5.3. Statistical Attack and Perfect Secrecy
6. Conclusions and Future Work
- Measuring the resistance of the stego signal against signal manipulation attacks like MP3 (Moving Picture Experts Group Layer-3 Audio) compression, additive noise and filtering.
- Propose alternative ways to obtain the super-Gaussian signal to be imitated by the secret message.
- Explore alternative ways of dynamic LSB substitution.
Author Contributions
Funding
Conflicts of Interest
References
- Khan, M.F.; Baig, F.; Beg, S. Steganography Between Silence Intervals of Audio in Video Content Using Chaotic Maps. Circ. Syst. Signal Process. 2014, 33, 3901–3919. [Google Scholar] [CrossRef] [Green Version]
- Kapotas, S.K.; Varsaki, E.E.; Skodras, A.N. Data Hiding in H. 264 Encoded Video Sequences. In Proceedings of the 2007 IEEE 9th Workshop on Multimedia Signal Processing, Chania, Greece, 1–3 October 2007. [Google Scholar]
- Liu, W.L.; Leng, H.S.; Huang, C.K.; Chen, D.C. A Block-Based Division Reversible Data Hiding Method in Encrypted Images. Symmetry 2017, 9, 308. [Google Scholar] [CrossRef]
- Liu, Y.; Chang, C.C.; Huang, P.C.; Hsu, C.Y. Efficient Information Hiding Based on Theory of Numbers. Symmetry 2018, 10, 19. [Google Scholar] [CrossRef]
- Ali, A.H.; George, L.E.; Zaidan, A.A.; Mokhtar, M.R. High capacity, transparent and secure audio steganography model based on fractal coding and chaotic map in temporal domain. Multimed. Tools Appl. 2018, 77, 31487–31516. [Google Scholar] [CrossRef]
- Rekik, S.; Guerchi, D.; Selouani, S.A.; Hamam, H. Speech steganography using wavelet and Fourier transforms. EURASIP J. Audio Speech Music Process. 2012, 2012. [Google Scholar] [CrossRef]
- Gopalan, K. Audio steganography by modification of cepstrum at a pair of frequencies. In Proceedings of the 2008 9th International Conference on Signal Processing, Beijing, China, 26–29 October 2008. [Google Scholar]
- Ballesteros, L.D.M.; Moreno, A.J.M. Highly transparent steganography model of speech signals using Efficient Wavelet Masking. Expert Syst. Appl. 2012, 39, 9141–9149. [Google Scholar] [CrossRef]
- Djebbar, F.; Abed-Meraim, K.; Guerchi, D.; Hamam, H. Dynamic energy based text-in-speech spectrum hiding using speech masking properties. In Proceedings of the 2010 The IEEE 2nd International Conference on Industrial Mechatronics and Automation, Wuhan, China, 30–31 May 2010. [Google Scholar]
- Radhakrishnan, R.; Kharrazi, M.; Memon, N. Data Masking: A New Approach for Steganography? J. VLSI Signal Process. Syst. Signal Image Video Technol. 2005, 41, 293–303. [Google Scholar] [CrossRef]
- Ballesteros, L.D.M.; Moreno, A.J.M. Speech Scrambling Based on Imitation of a Target Speech Signal with Non-confidential Content. Circ. Syst. Signal Process. 2014, 33, 3475–3498. [Google Scholar] [CrossRef]
- Ballesteros, L.D.M.; Renza, D.; Camacho, S. An unconditionally secure speech scrambling scheme based on an imitation process to a gaussian noise signal. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 233–242. [Google Scholar]
- Lim, Y.C.; Lee, J.W.; Foo, S.W. Quality Analog Scramblers Using Frequency-Response Masking Filter Banks. Circ. Syst. Signal Process. 2009, 29, 135–154. [Google Scholar] [CrossRef]
- Elshamy, E.M.; El-Rabaie, E.S.M.; Faragallah, O.S.; Elshakankiry, O.A.; El-Samie, F.E.A.; El-sayed, H.S.; El-Zoghdy, S.F. Efficient audio cryptosystem based on chaotic maps and double random phase encoding. Int. J. Speech Technol. 2015, 18, 619–631. [Google Scholar] [CrossRef]
- Madain, A.; Dalhoum, A.L.A.; Hiary, H.; Ortega, A.; Alfonseca, M. Audio scrambling technique based on cellular automata. Multimed. Tools Appl. 2012, 71, 1803–1822. [Google Scholar] [CrossRef] [Green Version]
- Augustine, N.; George, S.N.; Deepthi, P.P. Sparse representation based audio scrambling using cellular automata. In Proceedings of the 2014 IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 6–7 January 2014. [Google Scholar]
- Bhowal, K.; Bhattacharyya, D.; Pal, A.J.; Kim, T.H. A GA based audio steganography with enhanced security. Telecommun. Syst. 2011, 52, 2197–2204. [Google Scholar] [CrossRef]
- Ballesteros, L.D.M.; Renza, D. Speech steganography based on scrambling and hiding (Spanish audios). Mendeley Data 2018. [Google Scholar] [CrossRef]
- Lin, Y.; Abdulla, W.H. Audio Watermark; Springer International Publishing: Berlin, Germany, 2015. [Google Scholar]
- Gomez-Coronel, S.; Escalante-Ramirez, B.; Acevedo-Mosqueda, M.; Mosqueda, M. Steganography in audio files by Hermite Transform. Appl. Math. Inf. Sci. 2014, 8, 959–966. [Google Scholar] [CrossRef]
- Chhabra, A.; Mathur, S. Modified RSA Algorithm: A Secure Approach. In Proceedings of the 2011 International Conference on Computational Intelligence and Communication Networks, Gwalior, India, 7–9 October 2011. [Google Scholar]
- Kar, D.; Mulkey, C. A multi-threshold based audio steganography scheme. J. Inf. Secur. Appl. 2015, 23, 54–67. [Google Scholar] [CrossRef]
- Xin, G.; Liu, Y.; Yang, T.; Cao, Y. An Adaptive Audio Steganography for Covert Wireless Communication. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]








| Reference | [20] | [21] | [22] | [23] | Ours |
|---|---|---|---|---|---|
| Method | Hermite Transform (HT) and Threshold | RSA + 2-bit LSB | LSB Multi-Threshold Based Criterion | Variable Low Bit Coding (Up To 3-Bit LSB) | Adaptive Scrambling + Adaptive LSB |
| 0.988 | NR | NR | NR | 0.992 | |
| 32.7 dB | 34.27 dB | NR | 47 dB | 23.61 dB | |
| 0.961 | NR | NR | NR | 0.974 | |
| NR | 18% | NR | 24% | NR | |
| <0.125 | <0.13 | >0.5 | |||
| Key space | NR | NR | 280 | NR |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ballesteros, D.M.; Renza, D. Secure Speech Content Based on Scrambling and Adaptive Hiding. Symmetry 2018, 10, 694. https://doi.org/10.3390/sym10120694
Ballesteros DM, Renza D. Secure Speech Content Based on Scrambling and Adaptive Hiding. Symmetry. 2018; 10(12):694. https://doi.org/10.3390/sym10120694
Chicago/Turabian StyleBallesteros, Dora M., and Diego Renza. 2018. "Secure Speech Content Based on Scrambling and Adaptive Hiding" Symmetry 10, no. 12: 694. https://doi.org/10.3390/sym10120694
APA StyleBallesteros, D. M., & Renza, D. (2018). Secure Speech Content Based on Scrambling and Adaptive Hiding. Symmetry, 10(12), 694. https://doi.org/10.3390/sym10120694





