A Robust Color Image Watermarking Algorithm Based on APDCBT and SSVD
Abstract
:1. Introduction
2. Preliminary Concepts
2.1. APDCBT
2.2. SSVD
2.3. Fibonacci Transform
2.4. QR Code
3. Proposed Color Image Watermarking Algorithm
3.1. Watermark Preprocessing
| Algorithm 1.Watermark Preprocessing Algorithm | |
| Variable Declaration: | |
| SDUW: color watermark image | |
| W: read the watermark image | |
| RW, GW, and BW: three components of the color watermark image | |
| Rs, Gs, and Bs: three scrambled components using Fibonacci transform | |
| URs, VRs, UGs, VGs, UBs, and VBs: orthogonal matrices for Rs, Gs, and Bs | |
| SRs, SGs, and SBs: singular value matrices for Rs, Gs, and Bs | |
| WR, WG, and WB: three watermark components for embedding | |
| Watermark Preprocessing Procedure: | |
| Start Procedure: | |
| 1: | Read the color watermark image |
| W ← SDUW.png (color watermark image of size 64 × 64); | |
| RW ← W (:, :, 1); GW ← W (:, :, 2); BW ← W (:, :, 3); | |
| 2: | Scramble the three color components of the watermark image |
| Rs ← Fibonacci transform (RW); Gs ← Fibonacci transform (GW); Bs ← Fibonacci transform (BW); | |
| 3: | Perform SVD on each scrambled color components |
| [URs, SRs, VRs] ← SVD (Rs); [UGs, SGs, VGs] ← SVD (Gs); [UBs, SBs, VBs] ← SVD (Bs); | |
| 4: | Obtain watermark for embedding |
| WR = URs × SRs; WG = UGs × SGs; WB = UBs × SBs; | |
| End Procedure | |
3.2. Watermark Embedding
| Algorithm 2.Watermark Embedding Algorithm | |
| Variable Declaration: | |
| Lena: color host image | |
| I: read the color host image | |
| R, G, and B: three color components of the host image | |
| MC: three DC coefficient matrices obtained by APDCBT, where C = {R, G, B} | |
| UC and VC: orthogonal matrices for MC | |
| SC: singular value matrices for MC | |
| WC: three preprocessed color components of the watermark image, where C = {R, G, B} | |
| α: scaling factor | |
| SCW: three singular value matrices with the embedded watermark | |
| UCW and VCW: the orthogonal matrices for SCW | |
| SCW1: the singular value matrices for SCW | |
| : watermarked DC coefficient matrices | |
| : three watermarked color components, including , , and | |
| : watermarked image | |
| Watermark Embedding Procedure: | |
| Start Procedure: | |
| 1: | Read the color host image |
| I ← Lena.ppm (color host image of size 512 × 512); | |
| R ← I (:, :, 1); G ← I (:, :, 2); B ← I (:, :, 3); | |
| 2: | Perform 8 × 8 APDCBT to three color components |
| MC ← APDCBT (C) //C = {R, G, B} | |
| 3: | Perform SVD on MC |
| [UC, SC, VC] ← SVD (MC) | |
| 4: | Watermark Embedding |
| SCW = SC + α × WC | |
| [UCW, SCW1, VCW] ← SVD (MC) | |
| ← | |
| 5: | Perform the inverse APDCBT |
| ← inverse APDCBT () // | |
| ← cat (3, ) | |
| End Procedure | |
3.3. Watermark Extraction
| Algorithm 3. Watermark Extraction Algorithm | |
| Variable Declaration: | |
| : the suspicious color image | |
| , , and : three color components of | |
| : three DC coefficient matrices obtained by APDCBT, where | |
| and : orthogonal matrices for | |
| : singular value matrices for | |
| SC: saved singular value matrices for MC of host image | |
| UCW and VCW: saved orthogonal matrices for SCW in watermark embedding process | |
| : watermarked singular value matrices | |
| α: scaling factor | |
| : extracted watermark | |
| : three reconstructed color components of watermark image | |
| : three inverse scrambled color components of watermark image | |
| : reconstructed watermark image | |
| Watermark Embedding Procedure: | |
| Start Procedure: | |
| 1: | Read the suspicious color image |
| ← Suspicious image.ppm | |
| ← (:, :, 1); ← (:, :, 2); ← (:, :, 3); | |
| 2: | Perform 8 × 8 APDCBT to three color components |
| ← APDCBT (C) // | |
| 3: | Perform SVD on |
| [, , ] ← SVD () | |
| 4: | Watermark Extraction |
| ← // | |
| ← | |
| ← | |
| 5: | Apply inverse Fibonacci transform on |
| ← inverse Fibonacci transform () // | |
| 6: | Reconstruct the final watermark image |
| ← cat (3, ) | |
| End Procedure | |
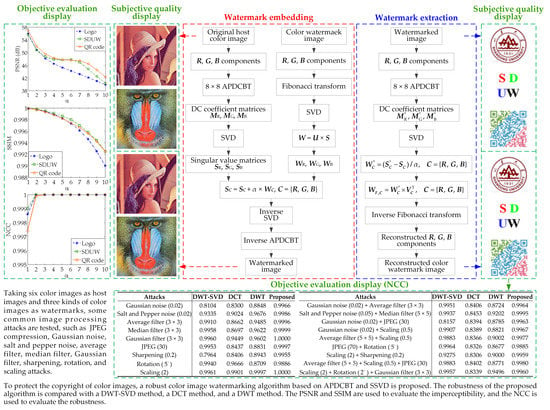
4. Experimental Results and Analysis
4.1. Evaluation Indexes
4.2. Imperceptibility
4.3. Robustness
4.4. Real-Time Analysis
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhang, X.Q.; Wang, X.S. Digital image encryption algorithm based on elliptic curve public cryptosystem. IEEE Access 2018, 6, 70025–70034. [Google Scholar] [CrossRef]
- Denemark, T.; Boroumand, M.; Fridrich, J. Steganalysis features for content-adaptive JPEG steganography. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1736–1746. [Google Scholar] [CrossRef]
- Li, Y.N.; Wang, J.R. Robust content fingerprinting algorithm based on invariant and hierarchical generative model. Digit. Signal Process. 2019, 85, 41–53. [Google Scholar] [CrossRef]
- Schyndel, R.G.V.; Tirkel, A.Z.; Osborne, C.F. A digital watermark. In Proceedings of the 1st IEEE International Conference on Image Processing, Austin, TX, USA, 13–16 November 1994. [Google Scholar]
- Kamaruddin, N.S.; Kamsin, A.; Por, L.Y.; Rahman, H. A review of text watermarking: Theory, methods and applications. IEEE Access 2018, 6, 8011–8028. [Google Scholar] [CrossRef]
- Wang, C.Y.; Zhang, Y.P.; Zhou, X. Robust image watermarking algorithm based on ASIFT against geometric attacks. Appl. Sci. 2018, 8, 410. [Google Scholar] [CrossRef]
- Abdulfetah, A.A.; Sun, X.M.; Yang, H.F.; Mohammad, N. Robust adaptive image watermarking using visual models in DWT and DCT domain. Inf. Technol. J. 2010, 9, 460–466. [Google Scholar] [CrossRef]
- Gupta, R.; Mishra, A.; Jain, S. A semi-blind HVS based image watermarking scheme using elliptic curve cryptography. Multimed. Tools Appl. 2018, 77, 19235–19260. [Google Scholar] [CrossRef]
- Erkucuk, S.; Krishnan, S.; Zeytinoglu, M. A robust audio watermark representation based on linear chirps. IEEE Trans. Multimed. 2006, 8, 925–936. [Google Scholar] [CrossRef]
- Mohammed, A.A.; Ali, N.A. Robust video watermarking scheme using high efficiency video coding attack. Multimed. Tools Appl. 2018, 77, 2791–2806. [Google Scholar] [CrossRef]
- Sathya, S.P.A.; Ramakrishnan, S. Fibonacci based key frame selection and scrambling for video watermarking in DWT–SVD domain. Wireless Pers. Commun. 2018, 102, 2011–2031. [Google Scholar] [CrossRef]
- Himeur, Y.; Boukabou, A. A robust and secure key-frames based video watermarking system using chaotic encryption. Multimedia Tools Appl. 2018, 77, 8603–8627. [Google Scholar] [CrossRef]
- Chou, C.H.; Wu, T.L. Embedding color watermarks in color images. EURASIP J. Appl. Signal Process. 2003, 1, 32–40. [Google Scholar] [CrossRef]
- Su, Q.T.; Yuan, Z.H.; Liu, D.C. An approximate Schur decomposition-based spatial domain color image watermarking method. IEEE Access 2019, 7, 4358–4370. [Google Scholar] [CrossRef]
- Su, Q.T.; Liu, D.C.; Yuan, Z.H.; Wang, G.; Zhang, X.F.; Chen, B.J.; Yao, T. New rapid and robust color image watermarking technique in spatial domain. IEEE Access 2019, 7, 30398–30409. [Google Scholar] [CrossRef]
- Barni, M.; Bartolini, F.; Piva, A. Multichannel watermarking of color image. IEEE Trans. Circuits Syst. Video Technol. 2002, 12, 142–156. [Google Scholar] [CrossRef]
- Liu, K.C. Wavelet-based watermarking for color images through visual masking. AEU - Int. J. Electron. Commun. 2010, 64, 112–124. [Google Scholar] [CrossRef]
- Patvardhan, C.; Kumar, P.; Lakshmi, C.V. Effective color image watermarking scheme using YCbCr color space and QR code. Multimed. Tools Appl. 2018, 77, 12655–12677. [Google Scholar] [CrossRef]
- Roy, S.; Pal, A.K. A blind DCT based color watermarking algorithm for embedding multiple watermarks. Aeu-Int. J. Electron. Commun. 2017, 72, 149–161. [Google Scholar] [CrossRef]
- Niu, P.P.; Wang, X.Y.; Liu, Y.N.; Yang, H.Y. A robust color image watermarking using local invariant significant bitplane histogram. Multimed. Tools Appl. 2017, 76, 3403–3433. [Google Scholar]
- Liu, X.Y.; Wang, Y.F.; Du, J.Y.; Liao, S.H.; Lou, J.T.; Zou, B.J. Robust hybrid image watermarking scheme based on KAZE features and IWT-SVD. Multimed. Tools Appl. 2019, 78, 6355–6384. [Google Scholar] [CrossRef]
- Chang, T.J.; Pan, I.H.; Huang, P.S.; Hu, C.H. A robust DCT-2DLDA watermark for color images. Multimed. Tools Appl. 2019, 78, 9169–9191. [Google Scholar] [CrossRef]
- Lakrissi, Y.; Saaidi, A.; Essahlaoui, A. Novel dynamic color image watermarking based on DWT-SVD and the human visual system. Multimed. Tools Appl. 2018, 77, 13531–13555. [Google Scholar] [CrossRef]
- Li, J.Z.; Yu, C.Y.; Gupta, B.B.; Ren, X.C. Color image watermarking scheme based on quaternion Hadamard transform and Schur decomposition. Multimed. Tools Appl. 2018, 77, 4545–4561. [Google Scholar] [CrossRef]
- Rosales-Roldan, L.; Chao, J.H.; Nakano-Miyatake, M.; Perez-Meana, H. Color image ownership protection based on spectral domain watermarking using QR codes and QIM. Multimed. Tools Appl. 2018, 77, 16031–16052. [Google Scholar] [CrossRef]
- Roy, S.; Pal, A.K. A hybrid domain color image watermarking based on DWT-SVD. Iran. J. Sci. Technol.-Trans. Electr. Eng. 2019, 43, 201–217. [Google Scholar] [CrossRef]
- Vaidya, P.S.; Mouli, C.P.V.S.S.R. A robust semi-blind watermarking for color images based on multiple decompositions. Multimed. Tools Appl. 2017, 76, 25623–25656. [Google Scholar]
- Mohammad, M.; Gholamhossein, E. A new DCT-based robust image watermarking method using teaching-learning-based optimization. J. Inf. Secur. Appl. 2019, 47, 28–38. [Google Scholar]
- Laur, L.; Rasti, P.; Agoyi, M.; Anbarjafari, G. A robust color image watermarking scheme using entropy and QR decomposition. Radio Eng. 2015, 24, 1025–1032. [Google Scholar] [CrossRef]
- Cedillo-Hernandez, M.; Cedillo-Hernandez, A.; Garcia-Ugalde, F.J.; Nakano-Miyatake, M.; Perez-Meana, H. Copyright protection of color imaging using robust-encoded watermarking. Radio Eng. 2015, 24, 240–251. [Google Scholar] [CrossRef]
- Su, Q.T.; Wang, G.; Jia, S.L.; Zhang, X.F.; Liu, Q.M.; Liu, X.X. Embedding color image watermark in color image based on two-level DCT. Signal Image Video Process. 2015, 9, 991–1007. [Google Scholar] [CrossRef]
- Su, Q.T.; Chen, B.J. An improved color image watermarking scheme based on Schur decomposition. Multimed. Tools Appl. 2017, 76, 24221–24249. [Google Scholar] [CrossRef]
- Pandey, M.K.; Parmar, G.; Gupta, R.; Sikander, A. Non-blind Arnold scrambled hybrid image watermarking in YCbCr color space. Microsyst. Technol. 2019, 25, 3071–3081. [Google Scholar] [CrossRef]
- Jia, S.L.; Zhou, Q.P.; Zou, H. A novel color image watermarking scheme based on DWT and QR decomposition. J. Appl. Sci. Eng. 2017, 20, 193–200. [Google Scholar]
- Hou, Z.X.; Wang, C.Y.; Yang, A.P. All phase biorthogonal transform and its application in JPEG-like image compression. Signal Process. Image Commun. 2009, 24, 791–802. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, H.; Wang, C.Y. A robust image watermarking technique based on DWT, APDCBT, and SVD. Symmetry 2018, 10, 77. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, C.Y.; Zhou, X. Image watermarking scheme based on DWT-DCT and SSVD. Int. J. Secur. Its Appl. 2016, 10, 191–205. [Google Scholar]
- Cai, Y.J.; Niu, Y.G.; Su, Q.T. Blind watermarking algorithm for color images based on DWT-SVD and Fibonacci transformation. Appl. Res. Comput. 2012, 29, 3025–3028. [Google Scholar]
- University of Granada, Computer Vision Group: CVG-UGR Image Database. Available online: http://decsai.ugr.es/cvg/dbimagenes/c512.php (accessed on 12 July 2019).
- Scholar Homepage of Chengyou Wang. Available online: http://www.scholat.com/wangchengyou (accessed on 15 July 2019).
- Ladislav, P.; Jan, K.; Ondrej, Z.; Ondrej, K.; Libor, B.; Martin, S.; Tomas, K. Study of advanced compression tools for stereoscopic video by objective metrics. In Proceedings of the 26th International Conference Radioelektronika, Kosice, Slovakia, 19–20 April 2016. [Google Scholar]





| Size of Image | 4 × 4 | 8 × 8 | 16 × 16 | 32 × 32 | 64 × 64 | 128 × 128 | 256 × 256 |
| Period | 6 | 12 | 24 | 48 | 96 | 192 | 384 |
| Host Images | Logo | SDUW | QR Code | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PSNR (dB) | SSIM | NCC | PSNR (dB) | SSIM | NCC | PSNR (dB) | SSIM | NCC | ||
| Baboon | 1 | 55.90 | 1.0000 | 0.9992 | 55.49 | 1.0000 | 0.9993 | 56.88 | 1.0000 | 0.9980 |
| 3 | 47.88 | 0.9998 | 1.0000 | 48.25 | 0.9998 | 1.0000 | 49.20 | 0.9998 | 1.0000 | |
| 5 | 44.84 | 0.9992 | 1.0000 | 46.53 | 0.9995 | 1.0000 | 46.78 | 0.9995 | 1.0000 | |
| 7 | 42.91 | 0.9982 | 1.0000 | 45.97 | 0.9988 | 1.0000 | 45.80 | 0.9989 | 1.0000 | |
| Airplane | 1 | 55.69 | 0.9997 | 0.9979 | 55.20 | 0.9998 | 0.9986 | 56.63 | 0.9998 | 0.9965 |
| 3 | 47.17 | 0.9979 | 1.0000 | 47.15 | 0.9984 | 1.0000 | 48.32 | 0.9984 | 1.0000 | |
| 5 | 43.63 | 0.9942 | 1.0000 | 44.34 | 0.9955 | 1.0000 | 45.15 | 0.9960 | 1.0000 | |
| 7 | 41.43 | 0.9877 | 1.0000 | 43.11 | 0.9914 | 1.0000 | 43.40 | 0.9922 | 1.0000 | |
| Sailboat | 1 | 55.98 | 0.9999 | 0.9995 | 55.46 | 0.9999 | 0.9998 | 56.85 | 0.9999 | 0.9992 |
| 3 | 48.09 | 0.9993 | 1.0000 | 48.18 | 0.9994 | 1.0000 | 49.09 | 0.9995 | 1.0000 | |
| 5 | 45.43 | 0.9979 | 1.0000 | 46.52 | 0.9986 | 1.0000 | 46.62 | 0.9985 | 1.0000 | |
| 7 | 44.10 | 0.9960 | 1.0000 | 46.56 | 0.9973 | 1.0000 | 45.78 | 0.9970 | 1.0000 | |
| House | 1 | 55.78 | 0.9997 | 0.9991 | 55.29 | 0.9998 | 0.9995 | 56.71 | 0.9998 | 0.9975 |
| 3 | 47.49 | 0.9972 | 1.0000 | 47.57 | 0.9984 | 1.0000 | 48.60 | 0.9985 | 1.0000 | |
| 5 | 44.25 | 0.9934 | 1.0000 | 45.22 | 0.9963 | 1.0000 | 45.73 | 0.9965 | 1.0000 | |
| 7 | 42.33 | 0.9879 | 1.0000 | 44.45 | 0.9932 | 1.0000 | 44.36 | 0.9936 | 1.0000 | |
| Peppers | 1 | 56.13 | 0.9826 | 0.9984 | 55.79 | 0.9844 | 0.9990 | 57.16 | 0.9843 | 0.9977 |
| 3 | 48.80 | 0.9729 | 1.0000 | 49.70 | 0.9793 | 1.0000 | 50.36 | 0.9775 | 1.0000 | |
| 5 | 46.34 | 0.9685 | 1.0000 | 48.89 | 0.9808 | 1.0000 | 49.07 | 0.9777 | 1.0000 | |
| 7 | 44.13 | 0.9662 | 1.0000 | 46.06 | 0.9824 | 1.0000 | 46.21 | 0.9806 | 1.0000 | |
| Watermarks | Logo | SDUW | QR Code |
|---|---|---|---|
| Watermarked images (PSNR (dB)/SSIM) |  45.24/0.9982 |  47.66/0.9986 |  47.70/0.9982 |
| Extracted watermarks (NCC) |  1.0000 |  1.0000 |  1.0000 |
| Watermarked images (PSNR (dB)/SSIM) |  44.84/0.9992 |  46.53/0.9995 |  46.78/0.9995 |
| Extracted watermarks (NCC) |  1.0000 |  1.0000 |  1.0000 |
| Algorithms | Patvardhan et al. [18] | Su et al. [31] | Jia et al. [34] | Proposed |
|---|---|---|---|---|
| Host images | 512 × 512 × 3 | 512 × 512 × 3 | 512 × 512 × 3 | 512 × 512 × 3 |
| Watermark images | gray | color | color | color |
| PSNR (dB) | 52.13 | 46.07 | 41.45 | 49.03 |
| SSIM | 0.9975 | 0.9913 | 0.9842 | 0.9992 |
| NCC | 0.9962 | 0.9999 | 1.0000 | 1.0000 |
| Capacity | 128 × 128 | 64 × 64 × 3 | 32 × 32 × 3 | 64 × 64 × 3 |
| Attacks | Parameter | Lena | Baboon | Sailboat |
|---|---|---|---|---|
| JPEG | QF = 30 |  0.9999 |  0.9999 |  0.9998 |
| QF = 60 |  1.0000 |  1.0000 |  1.0000 | |
| Gaussian noise | 0.01 |  0.9997 |  0.9998 |  0.9997 |
| 0.02 |  0.9986 |  0.9994 |  0.9990 | |
| Salt and Pepper noise | 0.01 |  0.9998 |  0.9999 |  0.9999 |
| 0.02 |  0.9995 |  0.9998 |  0.9997 | |
| Average filter | 5 × 5 |  0.9991 |  0.9988 |  0.9984 |
| Median filter | 5 × 5 |  0.9999 |  0.9988 |  0.9995 |
| Gaussian filter | 5 × 5 |  1.0000 |  1.0000 |  1.0000 |
| Sharpening | 0.2 |  0.9977 |  0.9971 |  0.9974 |
| Rotation |  0.9922 |  0.9905 |  0.9941 | |
| Scaling | 0.5 |  1.0000 |  1.0000 |  1.0000 |
| Attacks | Parameter | Lena | Baboon | Sailboat |
|---|---|---|---|---|
| JPEG | QF = 30 |  0.9997 |  0.9998 |  0.9996 |
| QF = 60 |  0.9999 |  0.9999 |  0.9999 | |
| Gaussian noise | 0.01 |  0.9991 |  0.9994 |  0.9994 |
| 0.02 |  0.9966 |  0.9979 |  0.9978 | |
| Salt and Pepper noise | 0.01 |  0.9996 |  0.9998 |  0.9999 |
| 0.02 |  0.9986 |  0.9993 |  0.9991 | |
| Average filter | 5 × 5 |  0.9978 |  0.9971 |  0.9963 |
| Median filter | 5 × 5 |  0.9996 |  0.9972 |  0.9988 |
| Gaussian filter | 5 × 5 |  1.0000 |  0.9999 |  0.9999 |
| Sharpening | 0.2 |  0.9955 |  0.9932 |  0.9941 |
| Rotation |  0.9886 |  0.9855 |  0.9900 | |
| Scaling | 0.5 |  1.0000 |  1.0000 |  1.0000 |
| Attacks | Patvardhan et al. [18] | Su et al. [31] | Jia et al. [34] | Proposed |
|---|---|---|---|---|
| Gaussian noise (0.02) | 0.8104 | 0.8300 | 0.8848 | 0.9966 |
| Salt and Pepper noise (0.02) | 0.9335 | 0.9024 | 0.9676 | 0.9986 |
| Average filter (3 × 3) | 0.9910 | 0.8662 | 0.9485 | 0.9996 |
| Median filter (3 × 3) | 0.9958 | 0.8697 | 0.9622 | 0.9999 |
| Gaussian filter (3 × 3) | 0.9960 | 0.9449 | 0.9602 | 1.0000 |
| JPEG (30) | 0.9953 | 0.8437 | 0.8831 | 0.9997 |
| Sharpening (0.2) | 0.7964 | 0.8406 | 0.8943 | 0.9955 |
| Rotation () | 0.9940 | 0.9666 | 0.8709 | 0.9886 |
| Scaling (2) | 0.9961 | 0.9901 | 0.9997 | 1.0000 |
| Gaussian noise (0.02) + Average filter (3 × 3) | 0.9951 | 0.8406 | 0.8724 | 0.9964 |
| Salt and Pepper noise (0.05) + Median filter (5 × 5) | 0.9937 | 0.8453 | 0.9202 | 0.9995 |
| Gaussian noise (0.02) + JPEG (30) | 0.8157 | 0.8394 | 0.8785 | 0.9963 |
| Salt and Pepper noise (0.05) + JPEG (50) | 0.8402 | 0.8432 | 0.8923 | 0.9934 |
| Average filter (3 × 3) + JPEG (30) | 0.9910 | 0.8413 | 0.8801 | 0.9995 |
| Median filter (3 × 3) + JPEG (70) | 0.9950 | 0.8405 | 0.9062 | 0.9999 |
| Gaussian noise (0.02) + Scaling (0.5) | 0.9907 | 0.8389 | 0.8821 | 0.9967 |
| Salt and Pepper noise (0.05) + Scaling (2) | 0.9639 | 0.8580 | 0.9668 | 0.9938 |
| Average filter (5 × 5) + Scaling (0.5) | 0.9883 | 0.8366 | 0.9002 | 0.9977 |
| Median filter (5 × 5) + Scaling (2) | 0.9917 | 0.8826 | 0.9260 | 0.9996 |
| JPEG (30) + Scaling (0.5) | 0.9895 | 0.8424 | 0.8822 | 0.9998 |
| JPEG (50) + Sharpening (0.2) | 0.9394 | 0.8462 | 0.8801 | 0.9969 |
| JPEG (70) + Rotation () | 0.9964 | 0.8326 | 0.8677 | 0.9885 |
| Scaling (2) + Sharpening (0.2) | 0.9275 | 0.8306 | 0.9000 | 0.9959 |
| Gaussian noise (0.02) + Median filter (3 × 3) + Sharpening (0.2) | 0.8190 | 0.8320 | 0.8777 | 0.9925 |
| Salt and Pepper noise (0.05) + Average filter (3 × 3) + Scaling (0.5) | 0.9889 | 0.8306 | 0.8849 | 0.9936 |
| Average filter (5 × 5) + Scaling (0.5) + JPEG (30) | 0.9883 | 0.8402 | 0.8771 | 0.9980 |
| Scaling (2) + Rotation () + Gaussian filter (3 × 3) | 0.9957 | 0.8339 | 0.9496 | 0.9960 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, X.; Wang, C.; Zhou, X. A Robust Color Image Watermarking Algorithm Based on APDCBT and SSVD. Symmetry 2019, 11, 1227. https://doi.org/10.3390/sym11101227
Yu X, Wang C, Zhou X. A Robust Color Image Watermarking Algorithm Based on APDCBT and SSVD. Symmetry. 2019; 11(10):1227. https://doi.org/10.3390/sym11101227
Chicago/Turabian StyleYu, Xiaoyan, Chengyou Wang, and Xiao Zhou. 2019. "A Robust Color Image Watermarking Algorithm Based on APDCBT and SSVD" Symmetry 11, no. 10: 1227. https://doi.org/10.3390/sym11101227
APA StyleYu, X., Wang, C., & Zhou, X. (2019). A Robust Color Image Watermarking Algorithm Based on APDCBT and SSVD. Symmetry, 11(10), 1227. https://doi.org/10.3390/sym11101227