Preventing Shoulder-Surfing Attacks using Digraph Substitution Rules and Pass-Image Output Feedback
Abstract
:1. Introduction
2. Related Works
3. The Proposed User Authentication Method
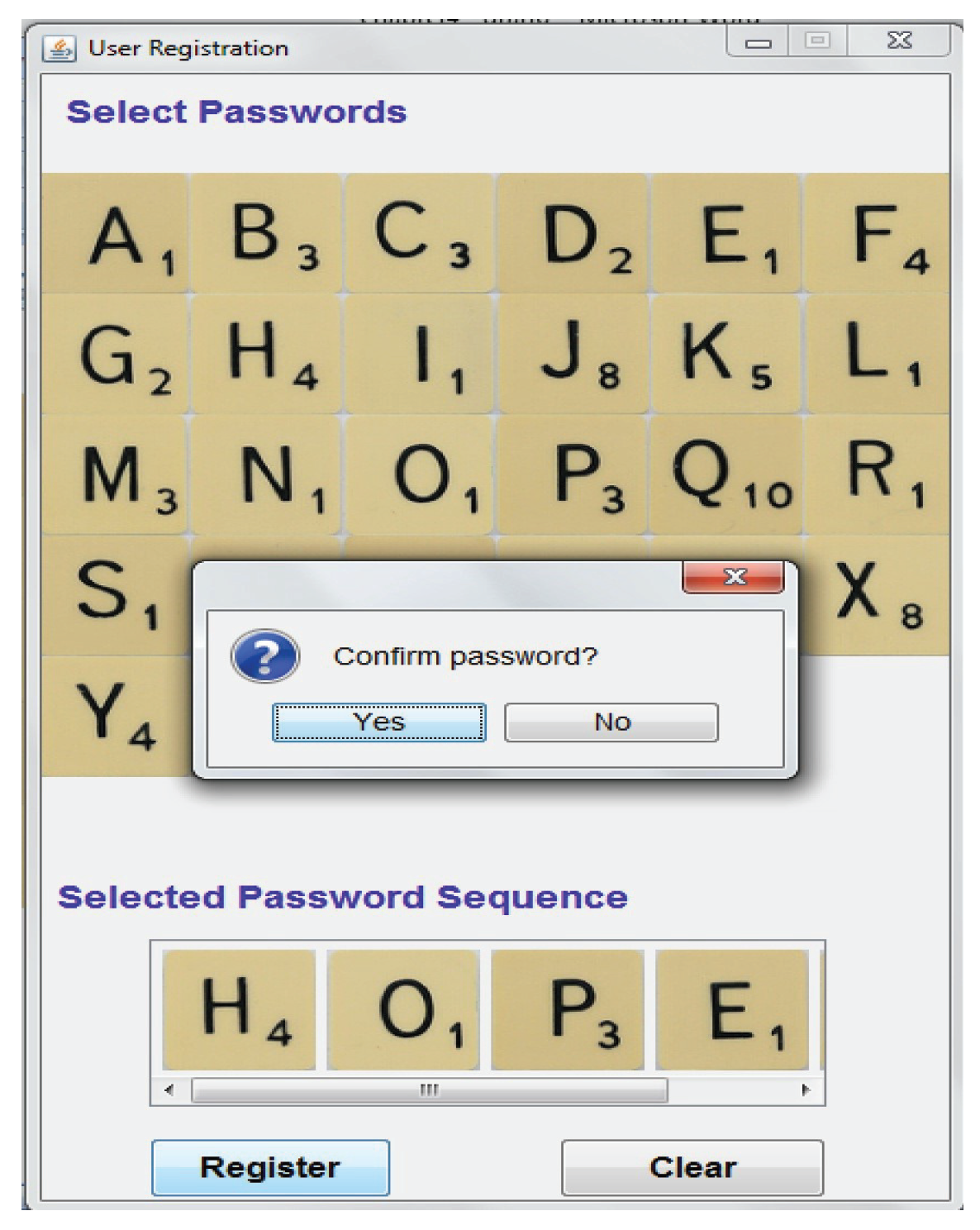
3.1. Enrolment Procedure
3.2. Authentication Procedure
3.3. Proposed Method
- Rule 1: If the letters are not on the same row or column, replace them with the letters on the same row respectively but at the other pair of corners of the rectangle defined by the original pair.
- Rule 2: If the letters appear on the same column, replace them with the letters immediately below respectively (wrapping around to the top side of the column if the letter in located at the bottom of the column).
- Rule 3: If the letters appear on the same row of the table, replace them with the letters to their immediate right respectively (wrapping around to the left side of the row if the letter is located at the right most of the row).
- Scenario A: Both password images appear diagonal to each other
- Scenario B: Both password images appear on the same vertical vector
- Scenario C: Both password images appear on the same horizontal vector
- Scenario D: Both password images appear at the same location
4. User Study Descriptions
5. Results and Discussions
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gokhale, A.; Waghmare, V. A Study of Various Passwords Authentication Techniques. Int. J. Comput. Appl. 2014, 1–5. [Google Scholar]
- Text Password Survey: Transition from First Generation to Second Generation. Available online: http://blogs.ubc.ca/computersecurity/les/2012/04/Text-Password-SurveyGAYA.pdf (accessed on 20 April 2017).
- Tank, H.; Harsora, V. A Survey on Secure Virtual Password and Phishing Attack. In Proceedings of the 4th International Conference on Computer Science and Information Technology (ICCIT 2015), Gujarat, India, 1–15 March 2015. [Google Scholar]
- Ho, P.F.; Kam, Y.H.S.; Wee, M.C.; Chong, Y.N.; Por, L.Y. Preventing Shoulder-Surfing Attack with the Concept of Concealing the Password Objects’ Information. Sci. World J. 2014, 2014, 838623. [Google Scholar] [CrossRef] [PubMed]
- Elftmann, P. Secure Alternatives to Password-Based Authentication Mechanisms. Diploma Thesis, Laboratory for Dependable Distributed Systems RWTH Aachen University, Aachen, Germany, 2006. [Google Scholar]
- Golar, P.C.; Adane, D.S. Critical analysis of 2-dimensional graphical authentication systems. In Proceedings of the 2016 International Conference on Computing, Analytics and Security Trends (CAST), Pune, India, 19–21 December 2016. [Google Scholar]
- Bhanushali, A.; Mange, B.; Vyas, H.; Bhanushali, H.; Bhogle, P. Comparison of Graphical Password Authentication Techniques. Int. J. Comput. Appl. 2015, 116, 11–14. [Google Scholar] [CrossRef]
- Jermyn, I.H.; Mayer, A.; Monrose, F.; Reiter, M.K.; Rubin, A.D. The Design and Analysis of Graphical Passwords; USENIX Association: Berkeley, CA, USA, 1999. [Google Scholar]
- Chiasson, S.; Paul, C.; Van Oorschot, P.C.; Biddle, R. Graphical password authentication using cued click points. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2007; pp. 359–374. [Google Scholar]
- Biddle, R.; Chiasson, S.; Van Oorschot, P. Graphical passwords: Learning from the first twelve years. J. ACM Comput. Surv. 2012, 44, 19–41. [Google Scholar] [CrossRef]
- Gao, H.C.; Wei, J.; Ye, F.; Ma, L.C. A survey on the use of graphical passwords in security. J. Softw. 2013, 8, 1678–1698. [Google Scholar] [CrossRef]
- Por, L.Y.; Ku, C.S.; Amaul, I.; Ang, T.F. Graphical password: Prevent shoulder-surfing attack using digraph substitution rules. Front. Comput. Sci. 2017, 11, 1098–1108. [Google Scholar] [CrossRef]
- Por, L.Y.; Kiah, M.L.M. Shoulder surfing resistance using penup event and neighbouring connectivity manipulation. Malays. J. Comput. Sci. 2010, 23, 121–140. [Google Scholar]
- Simha, T.S.; Srinivasulu, D. Pass Matrix checks for Login Authentication. Int. J. Comput. Sci. Trends Technol. 2017, 5, 5–13. [Google Scholar]
- Khedr, W.I. Improved keylogging and shoulder-surfing resistant visual two-factor authentication protocol. J. Inf. Secur. Appl. 2018, 39, 41–57. [Google Scholar] [CrossRef]
- Dhamija, R.; Perrig, A. Deja Vu: A User Study Using Images for Authentication. In Proceedings of the 9th USENIX Security Symposium, Denver, CO, USA, 14–17 August 2000. [Google Scholar]
- The Science Behind Passfaces. Available online: Http://www.realuser.com/published/ScienceBehindPassfaces.pdf (accessed on 20 April 2017).
- Wiedenbeck, S.; Waters, J.; Sobrado, L.; Birget, J.C. Design and evaluation of a shoulder-surfing resistant graphical password scheme. In Proceedings of the Working Conference on Advanced Visual Interfaces, Venezia, Italy, 23–26 May 2006. [Google Scholar]
- Khot, R.A.; Kumaraguru, P.; Srinathan, K. WYSWYE: Shoulder surfing defense for recognition based graphical passwords. In Proceedings of the 24th Australian Computer-Human Interaction Conference, Melbourne, Australia, 26–30 November 2012. [Google Scholar]
- Sonal, G.; Poonam, K.; Ketaki, M.; Bhagyashri, S. Shoulder Surfing Resistant Graphical Password Scheme. Int. J. Sci. Res. Dev. 2015, 3, 105–111. [Google Scholar]
- Kolay, R.; Vora, A.; Yadav, V. Graphical Password Authentication Using Image Segmentation. Int. Res. J. Eng. Technol. 2017, 4, 1694–1698. [Google Scholar]
- Dhandha, C. Parekh: Enhancement of Password Authentication System Using Recognition based Graphical password for web Application. Int. J. Adv. Res. Comput. Sci. 2017, 8, 1135–1138. [Google Scholar]
- Yu, X.; Wang, Z.; Li, Y.; Li, L.; Zhu, W.T.; Song, L. EvoPass: Evolvable graphical password against shoulder-surfing attacks. Comput. Secur. 2017, 70, 179–198. [Google Scholar] [CrossRef]
- Por, L.Y. Frequency of occurrence analysis attack and its countermeasure. Int. Arab J. Inf. Technol. 2014, 10, 189–197. [Google Scholar]
- William, S. Cryptography and Network Security: Principles and Practice, 4th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Weinshall. Cognitive authentication schemes safe against spyware. In Proceedings of the IEEE2006 Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 21–24 May 2006. [Google Scholar]
- Yamamoto, T.; Kojima, Y.; Nishigaki, M. A shoulder-surfing resistant image-based authentication system with temporal indirect image selection. In Proceedings of the International Conference on Security and Management, Las Vegas, NV, USA, 13–16 July 2009; pp. 188–194. [Google Scholar]
- Haque, M.A.; Imam, B. A New Graphical Password: Combination of Recall & Recognition Based Approach. World Academy of Science, Engineering and Technology. Int. J. Comput. Electr. Autom. Control Inf. Eng. 2014, 8, 320–324. [Google Scholar]
- Islam, A.; Por, L.Y.; Othman, F.; Ku, C.S. A Review on Recognition-Based Graphical Password Techniques. In Computational Science and Technology, Lecture Notes in Electrical Engineering; Alfred, R., Lim, Y., Ibrahim, A., Anthony, P., Eds.; Springer: Singapore, 2019. [Google Scholar]
- Maybank2u: An Online Banking System. Available online: https://www.maybank2u.com.my/home/m2u/common/login.do (accessed on 24 August 2019).











| Graphical Authentication System | Resist Direct Observation | Resist Video Recorded Attack |
|---|---|---|
| Cognitive Authentication System (CAS) [26] | YES | NO |
| Temporal Indirect Image-Based Authentication (TI-IBA) [27] | YES | NO |
| Por [24] | YES | NO |
| Haque and Imam [28] | YES | NO |
| Proposed Method | YES | YES |
| Week | No. of Participant | Average Login Time (Second) |
|---|---|---|
| 0 | 187 | 58.3 |
| 1 | 92 | 134.7 |
| 2 | 68 | 144.1 |
| 3 | 44 | 115.0 |
| 4 | 21 | 43.8 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Por, L.Y.; Ku, C.S.; Ang, T.F. Preventing Shoulder-Surfing Attacks using Digraph Substitution Rules and Pass-Image Output Feedback. Symmetry 2019, 11, 1087. https://doi.org/10.3390/sym11091087
Por LY, Ku CS, Ang TF. Preventing Shoulder-Surfing Attacks using Digraph Substitution Rules and Pass-Image Output Feedback. Symmetry. 2019; 11(9):1087. https://doi.org/10.3390/sym11091087
Chicago/Turabian StylePor, Lip Yee, Chin Soon Ku, and Tan Fong Ang. 2019. "Preventing Shoulder-Surfing Attacks using Digraph Substitution Rules and Pass-Image Output Feedback" Symmetry 11, no. 9: 1087. https://doi.org/10.3390/sym11091087







