1. Introduction
The Internet of Things (IoT) is an important part of the fifth-generation (5G) mobile communication technology, which can connect a large number of devices. Ambient backscatter communications (ABC) has energy-saving characteristics, has become a promising choice for self-sustainable communication systems, and has a good potential for widespread application in the IoT system. ABC utilizes radio frequency signals in the environment, such as TV tower signal, FM broadcast signal [
1], wireless fidelity signal [
2], etc., to supply energy for passive tags. Passive tags utilize RF signals in the environment to transmit information by adjusting the impedance of their antennas. The tag makes itself in the state of reflection or absorption by adjusting its antenna impedance. In the reflection state, the tag reflects the RF signal in the environment to the maximum extent, and a high level will be detected at the reader end, which will be regarded as sending symbol ‘1.’ On the other hand, in the absorption state, the tag absorbs RF signal from the environment as much as possible. Therefore, the reader side will receive weak reflected signals, which are regarded as the symbol ‘0’ sent by the tag. The ABC system has aroused great interest from the academic community. Duan R [
3] present the development trends in ABC prototype designs and discuss potential applications, highlight the specific features of the ABC technology. Chen C [
4] studied the signal detection method of multi-antenna tags which can collect energy and transmit data at the same time in the ABC environment. Tao Q [
5] proposes a novel MFSK( Multiple Frequency Shift Keying) modulation for the tag of ABC systems, and the corresponding detectors are designed depending on the capability of the reader. Yang G [
6] applied orthogonal frequency division multiplexing signals in the ABC system. Long R [
7] has adopted beamforming technology to realize a higher total data rate than the traditional point-to-point system in the cooperative ABC system.
But there are still some challenges. The broadcast nature of wireless signals makes it easy for some eavesdroppers to get the information content. Traditional secure encryption algorithms are not suitable for Internet of Things devices with limited computing power and energy. In this context, the research on physical layer security technology has become a new idea to guarantee communication confidentiality. The basic principle of physical layer security is to use noise and the inherent randomness of the channel to limit the information extracted from the received signal by the illegal receiver. Saad W [
8] characterized the secrecy of the RFID backscattering system. Then, a new method is proposed to maximize the confidentiality by making use of the properties and characteristics of the RFID backscattering channel. Essam G [
9] not only injects noise from the reader but also uses a one-dimensional antenna array to deploy beam steering on the tag side, which effectively protects the information of the RFID tag from eavesdroppers. Goel S [
10] researched the problem of secure communication between two legal nodes in the case of eavesdropping nodes in the wireless channel. The transmitter uses a part of the power to generate artificial noise to ensure the confidentiality of the communication process, which only reducing the channel quality of eavesdropping nodes. Tang X [
11] researched an eavesdropping channel with an auxiliary scrambler. In the presence of an eavesdropper, the transmitter, with the help of an independent scrambler, communicates confidentially with its legal receiver. In discrete memory-less channel and Gaussian channel, respectively, the realized security rate is obtained. Bang I [
12] proposed a user scheduling scheme based on multi-user diversity gain. A single user is scheduled for data transmission, and a number of other users generate independent artificial noise, so as to conduct confidential communication between the scheduling user and the legitimate receiver against the eavesdropper. Feng Y [
13] proposed a user-relay collaborative selection scheme and determined the optimal power allocation between the data signal and the artificial noise at the transmitter on the basis of minimizing the probability of secrecy interruption, so as to improve the physical layer security in the multi-user multi-relay network. Jia S [
14] proposed an artificial noise auxiliary collaboration scheme, one of the cognitive relays that successfully decodes the source signal is selected as the relay to retransmit the secret signal, and the other relays emit artificial noise that confuses the eavesdropper but does not damage the channel quality of the legitimate receiver, so the security performance of the secondary network is enhanced. In addition, Hong T [
15] proposed a design scheme of relay tag antenna based on the genetic algorithm in the ABC environment, which realized the directional communication from the relay tag to the legitimate receiver and enhanced the physical layer security of wireless communication.
However, from the above research, we can find that the research on the physical layer security scheme of wireless communication under the ABC environment is not sufficient. What’s more, in the physical security scheme using the technique of artificial noise often require one or more auxiliary relay nodes, but the security performance under this system model is highly dependent on the relay node, after the failure or damage of the relay, the system secure communication function cannot be realized, so the overall reliability of the system is poor. Even if some scheme does not depend on fixed relay, it is carried out under the condition of a fixed channel model or on the assumption that the channel state information (CSI) is known. Traditional channel estimation methods must send pilot symbols, which cannot be directly applied to the ABC system. Therefore, we proposed an enhanced communication security scheme that generates artificial noise from the tag end in the ABC environment. This scheme does not depend on key relay nodes, so the reliability of the system can be improved. In the IANT scheme, there are K tags to communicate with a legitimate reader, and there are eavesdropping devices to monitor the communication signal. In the RFID environment, the conventional method to improve the physical layer security is to inject noise from the reader end, and then send the signal with noise to the tag. After the reader receives the backscatter signal of the tag, it uses its own noise to remove the noise. In the ABC environment, the reader does not supply energy for tags, so in our scheme, we choose two tags to send signals to the reader at the same time, one to send tag data and the other to generate artificial noise. The symmetry of the content studied in this paper is reflected in the reception of the signal. There are reader, eavesdropper, and passive tags in the system model of this paper. due to the broadcast characteristics of the wireless channel, the signal backscattered by the tag will reach the reader and the eavesdropper at the same time, i.e., the signals they receive are symmetrical. What we have done is to make the reception effect of the reader different from that of the eavesdropper under this condition.
The main contributions we made in this paper are as follows:
In the ABC environment, we proposed a scheme IANT that uses physical layer strategies to enhance system security. As far as we know, it is the first time to study the physical layer security scheme from the perspective of artificial noise in thje ABC environment system.
Different from previous studies, in order to better adapt to the ABC environment, a new method is adopted to dynamically estimate channel parameters, which does not need pilot symbols.
Compared with the contrast scheme, the IANT scheme achieves a secrecy rate that is approximately twice the contrast scheme under the condition that the bit error rate (BER) is slightly reduced, which effectively enhances the security performance.
2. The System Model
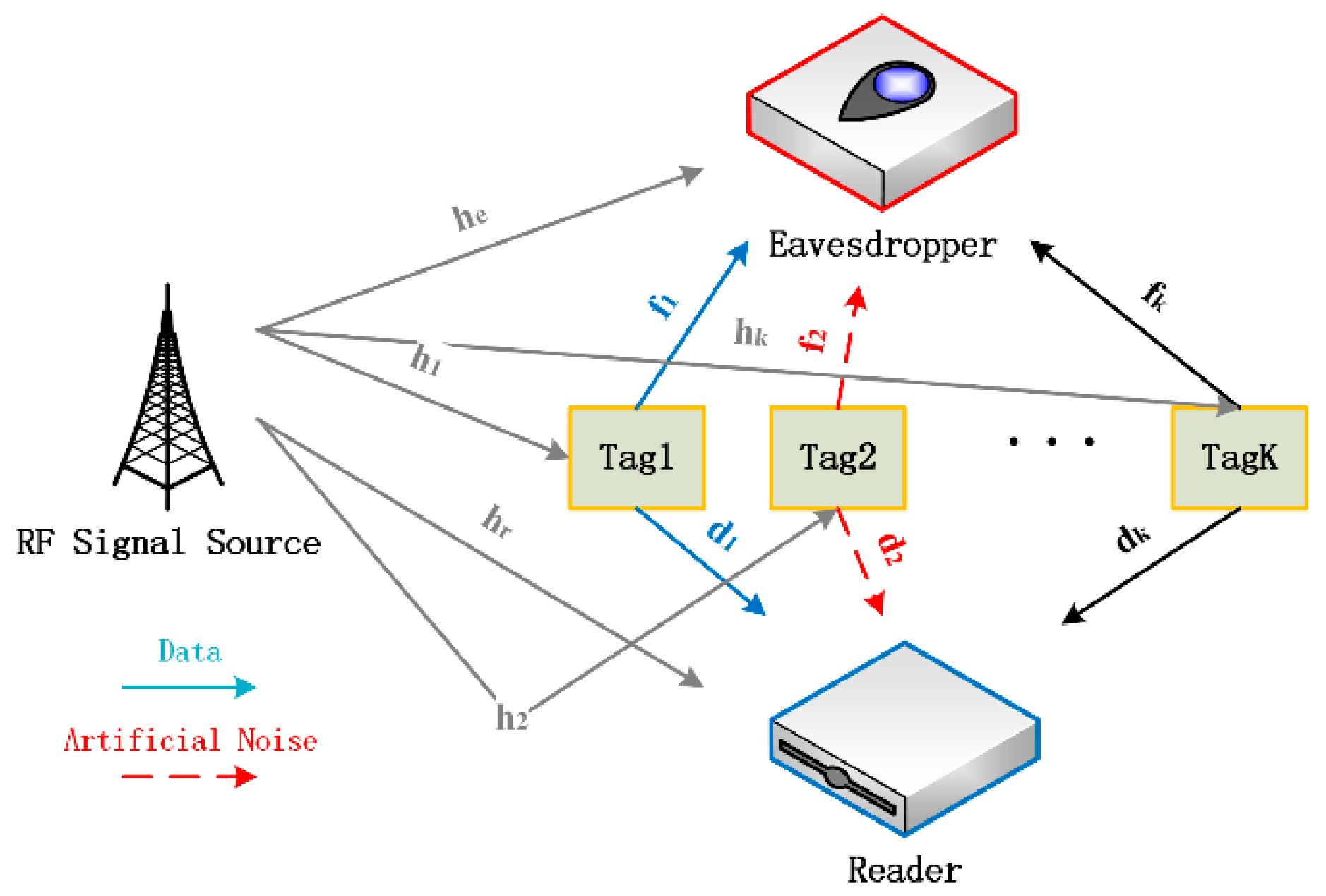
Aiming at the possible scenario of multiple simple IOT devices communicating with the reader in the future, this paper designs a system model in which multiple tags communicate with the reader in the ABC environment, while the eavesdropper tries to monitor the data sent by tags, as shown in
Figure 1. Each passive tag modulates symbol information on the RF signal in the environment by adjusting its antenna impedance, and then sends the modulated signal to the reader. In addition, because of the broadcast nature of the wireless communication channel, the eavesdropper will also receive modulated signals. Suppose the channel parameters between the tags and the RF signal source, the tags and the reader, the tags, and the eavesdropper are
respectively.
Where
and
,
represent the distance between the tags and the RF signal source, the tags and the reader, the tags and the eavesdropper, respectively. Moreover, we define both the channel between the RF signal source and the reader, and the channel between the RF signal source and the eavesdropper as Rayleigh fading channel with zero mean and unit variance, i.e.,
, The signals received by reader and eavesdropper can be respectively expressed as:
where
represents the complex equivalent signal of the RF signal,
represents the symbol sent by the
k-th tag by changing the antenna impedance,
represents the signal attenuation factor inside the tag,
and
represent the additive white Gaussian noise with zero mean and unit variance.
4. Numerical Simulation Results
In this section, in order to evaluate the performance of the IANT scheme proposed in this paper, we compare it with the multi-tag physical layer security scheme proposed by You J team [
18] in the ABC system. The latter only selected a single tag with optimal channel gain according to the achievable secrecy rate but did not select other tags to generate artificial noise. In addition, from the point of view of achievable secrecy rate, the difference of noise removal effect caused by different channel estimation errors on the physical layer security scheme in this paper is shown in the following.
Figure 3 shows the BER performance of the IANT scheme when the channel quality between tags and reader changes. We set the number of tags K to different values to study the influence of the number of tags on the system BER. As can be seen from the figure above, when the number of tags increases, the BER difference between the IANT scheme and the contrast maximum power scheduling scheme is gradually decreasing. From the point of view of BER, the performance of IANT scheme is worse than that of the security scheme without noise removal method. Even if we adopt the noise removal method, the BER of the IANT scheme is only close to that of the conventional scheduling scheme, but the artificial noise of the IANT scheme has a positive impact on the achievable secrecy rate of the system, that is, we choose to sacrifice certain BER performance to improve the physical layer security of the communication process.
Figure 4 shows the change in the achievable secrecy rate of the system when the number of tags K and the channel quality between tags and reader change. We can draw a conclusion from
Figure 4 that in the case of a small number of tags, the artificial noise will greatly affect the achievable secrecy rate. Furthermore, when the number of tags is set to 5, the IANT scheme has no advantage over the contrast security scheme in terms of the achievable secrecy rate. However, on the whole, the achievable secrecy rate of the system has improved with the increase in the number of tags. In addition, after the noise cancellation method is used to remove the influence of artificial noise, the achievable secrecy rate is correspondingly improved again.
Therefore, the IANT scheme proposed in this paper is superior to the contrast security scheme in terms of the achievable secrecy rate of the system. In addition, regardless of the number of tags, the IANT scheme proposed in this paper using the noise cancellation method still achieves a higher secrecy rate.
In order to further research the relationship between the number of tags and the achievable secrecy rate of the system, in the case of a fixed channel SNR, we show the changes in the achievable secrecy rate of IANT scheme and the contrast scheme, as shown in
Figure 5. We can observe that the IANT scheme with noise cancellation method can always get a better secrecy rate than the contrast scheme, and the secrecy rate of the former is about twice that of the latter, which implies that the IANT scheme proposed in this paper has better security performance when the number of tags is relatively large.
Figure 6 shows the effect of noise removal methods with different channel estimation errors on achievable secrecy rate when the number of tags K = 8. In this paper, we draw lessons from the channel estimation expression adopted by Yoo T team [
19]:
We can clearly observe from
Figure 6 that as the quality of the channel between tags and reader increases, the achievable secrecy rate of the system also increases. Besides, we can also draw the conclusion that the size of the channel estimation error also has a relatively large impact on the system security rate, i.e., larger channel estimation error
corresponds to lower security rate. Even under the premise that the channel estimation error is relatively large, the IANT scheme proposed in this paper is still superior to the contrast scheduling scheme in the entire area after adopting the noise elimination method.
Through the numerical simulation results, we find that the number of tags has no obvious effect on the channel estimation error, but we find that in the first sub-slot, the signal length
N0 transmitted by each tag has a strong correlation with the channel estimation error. As shown in
Figure 7, the horizontal axis represents the different signal length
N0 sent by tag in the first sub-slot. We set the channel signal-to-noise ratio to 0, 5, and 10 respectively, and showed the channel estimation error under different channel conditions. We can conclude that the channel estimation error keeps decreasing as the signal length increases, but when the signal length
N0 is greater than 20, the change rate of the channel estimation error slows down significantly. Moreover, when the channel quality is relatively good, a smaller channel estimation error can be obtained.