Abstract
The unfolding technique of Petri net can characterize the real concurrency and alleviate the state space explosion problem. Thus, it is greatly suitable to analyze/check some potential errors in concurrent systems. During the unfolding process of a Petri net, the calculations of configurations, cuts, and cut-off events are the key factors for the unfolding efficiency. However, most of the unfolding methods do not specify a highly efficient calculations on them. In this paper, we reveal some recursive relations and structural properties of these factors. Subsequently, we propose an improved method for computing configurations and cuts. Meanwhile, backward conflicts are used to guide the calculations of cut-off events. Moreover, a case study and a series of experiments are done to illustrate the effectiveness and application scenarios of our methods.
1. Introduction
Nowadays, concurrent systems have been successfully applied to various scenarios, e.g., large-scale websites, railway traffic systems, and telecom operation-support systems. Although high concurrency can indeed enhance their performance and throughput, it easily leads to some errors, such as deadlocks, a lack of synchronization, and data inconsistencies, especially when a concurrent system deals with a great amount of data. For example, Apache Httpd (an open-source web server) suffered from deadlocks that were caused by its unix mutex (https://www.sqlite.org/src/info/a6c30be214, (accessed on 2 January 2021)). The errors of data inconsistency in an IPO (Initial Public Offering) Cross system made NASDAQ (Nasdaq OMX Group, Inc, NewYork, USA ) lose $13 million in May, 2012 (https://www.computerworld.com/article/2727012/nasdaq-s-facebook-glitch-came-from-race-conditions.html, (accessed on 5 January 2021)). Therefore, some model-checking-based methods are proposed for checking the correctness and reliability of concurrent systems. Petri net is widely used to model and verify concurrent systems due to its great capability of explicitly specifying parallelism, concurrency, and synchronization [,,]. The classical reachability graph (CRG) of Petri net is a commonly used technique for checking deadlocks, reachability, and soundness of concurrent systems [,,]. However, this technique easily has the problem of the state space explosion because it is based on the interleaving semantics [] of concurrent events/actions. The interleaving semantics of CRG only considers the partial orders of business activities, and utilizes the global states of concurrent systems to describe and analyze their behaviors. Thus, a CRG needs to find out all precedence relations between activities, generate successor states, and eventually form some symmetry diamond structures.
When compared with the reachability-graph-based method, the unfolding technique [] of Petri nets can both alleviate the state space explosion problem and characterize the concurrency relations because it is based on the true concurrency semantics. In fact, some methods are proposed to conduct a concurrency analysis of Petri nets, such as reachability set [], concurrent sequential automata [], and c-exact hypergraphs []. By comparison, the unfolding technique uses an acyclic net to represent all behaviors of a Petri net. On the one hand, this acyclic net can directly record all concurrent operations. On the other hand, it uses a much smaller space to store all states especially when a system has many concurrent events/actions. If a Petri net is unbounded or it is bounded but has a repeatedly firable action sequence, its unfolding is naturally infinite. Thus, an important task in this case is to determine a cut-off event and obtain a finite complete prefix (FCP) of infinite unfoldings. Currently, there have been many methods of Petri nets to generate an FCP [], such as ERV (“ERV” is the abbreviation of authors: Esparza, Romer, and Vogler) unfolding, directed unfolding (DU), and merged process (MP). ERV [] is a classical unfolding method, which proposes partial orders and improves the McMillan’s unfolding algorithm []. The merged process [] generates a condensed unfolding of a Petri net’s behavior based on merged conditions. Directed unfolding [] utilizes heuristic functions to guide the unfolding of Petri nets towards the desired states. Moreover, these unfolding techniques have been successfully applied to many fields, e.g., fault diagnosis [], Artificial Intelligence (AI) planning [], and test cases generation [].
For these methods of generating an FCP, the calculations of configurations, cuts, and cut-off events greatly affect the unfolding efficiency of a Petri net. These related calculations make up an absolutely significant share () of the total unfolding time, as shown in Figure 1. However, most unfolding techniques do not specify a highly efficient calculations on them. On the one hand, the existing computing approaches of configurations and cuts depend on a lot of repetitive work. On the other hand, once a new event is generated and added into a given prefix, the current methods still need to match it up with all existing events so as to determine whether it is a cut-off event.
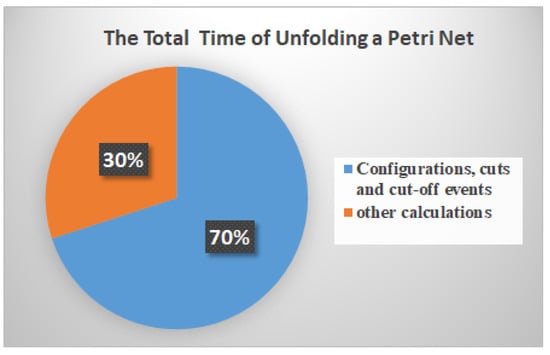
Figure 1.
The ratios of different kinds of calculations (e.g., configurations, cuts, and cut-off events) to the total time of unfolding a Petri net (The statistics come from our experiments on The BPM Academic Initiative Model Collection. https://bpmai.org/download/index.html (accessed on 10 December 2020)).
In this paper, we reveal some deep properties of configuration, cuts, and cut-off events, and then utilize recursion formulas and characterized structures to improve these calculations. Some algorithms are developed to perform these calculations and generate finite complete prefixes (FCPs). What is more, all of these improvements can be applied into the existing unfolding techniques and they contribute to the related model checkings.
The main contributions are summarized, as follows:
- (1)
- Incremental methods are proposed to calculate configurations, cuts and concurrent conditions.
- (2)
- Backward conflicts are used to guide the determination of cut-off events.
- (3)
- A tool is developed to implement our improved methods for unfolding a Petri net.
2. Related Work
2.1. The Unfolding Techniques of Petri Nets
McMillan [] initially proposed the net unfolding technique with partial-order semantics of Petri nets. As an improvement of McMillan’s unfoldings, Esparza et al. [] proposed a family of algorithms (i.e., ERV unfolding method) to construct a finite complete prefix. Whereafter, its parallel unfolding [] came up. Khomenko et al. [] proposed a cutting context to determine static cut-off events and generate canonical prefixes. Bonet et al. [] generalized the notion of cutting context and provided a user-oriented framework of the unfolding technique. Couvreur et al. [] proposed a new model of branching processes without any finiteness or safeness assumptions, which are suitable for describing the behavior of general Petri nets. Bonet [] utilized the problem-specific information as a heuristic function to guide the unfolding of Petri net towards the desired marking. Rodriguez et al. [] combined partial order reductions (POR) with net unfoldings to tackle the state space explosion problem. Chatain et al. [] proposed a goal-driven unfolding technique with model reduction to explore the minimal configurations that can lead to a given marking.
These studies of unfolding methods mainly focus on how to generate a smaller FCP by unfolding a Petri net, or explore different kinds of Petri net unfoldings, e.g., unbound Petri net [], timed Petri net [], colored Petri net [], contextual Petri net [], and Nested Petri nets (NP-net) []. However, they easily have a low efficiency in the calculations of configurations, cuts, and cut-off events. We propose an improved method for unfolding a Petri net in this paper in order to solve this problem.
2.2. Model Checking Based on Petri Net Unfolding
The unfolding technique of Petri net has been widely used in model checking, e.g., diagnosing faults in asynchronous discrete event systems [], making a concurrent planning [], generating test cases for multi-threads [], and checking deadlock [], soundness [], reachability, and coverability [].
McMillan [] first used the unfolding technique to verify asynchronous circuits. De León et al. [] presented a test generation algorithm for a complete test suite w.r.t. concurrent conformance relation based on the unfolding of IOPN. Jezequel et al. [] extended a distributed unfolding technique with time stamps to build testers for distributed systems. Saarikivi et al. [,] computed the minimal test suites for multi-threaded programs based on unfolding techniques. Liu et al. [] proposed the basic unfolding of Petri net to check the soundness of workflow systems. Lutz-Ley et al. [] analyzed the stability of discrete event systems that are based on the unfolding technique of Petri net. Meyer et al. [] translated finite control processes into a safe Petri net, and utilized the unfolding-based method to verify Mobile Systems. Ponce-de-Leon et al. [] used the unfolding technique of Petri net to discover a process model. Weidlich et al. [] calculated the behavioral consistency of process models based on Petri-net unfoldings. Xiang et al. [] used the unfolding of PD-net to detect the errors of data inconsistency.
When compared with these model checking methods, we can more effectively check errors of concurrent systems based on our unfolding method, since it records as much contextual information as possible and improves the calculational efficiency of Petri net unfolding.
3. Basic Notations
Some basic notations are introduced in this section, e.g., Petri net, occurrence net, and branching process.
Definition 1.
A net is a triple , where
- (1)
- P and T are two disjoint and finite sets, which are, respectively, called place set and transition set; and,
- (2)
- is a flow relation.
A marking of a net is a mapping M: , where is a set of non-negative integers. In this paper, a multiset of places represents a marking. A Petri net is a net N with an initial marking , and denoted as . For a node , its pre-set is denoted as and post-set . For a node set , its pre-set is and post-set . Furthermore, =| and =| are called prep-set and postp-set of x, respectively. Especially, if x is a transition, then (resp. ) is called prep-transitions (resp. posp-transitions).
Given a Petri net , a transition is enabled at a marking M if : , which is denoted by . After firing an enabled transition t at M, a new marking is generated and denoted as , where ∀p∈P: if ; if ; and, otherwise, . A marking is reachable from another marking M, if there exists a firing transition sequence ⋯ such that ⟩⟩⋯⟩. The set of reachable markings from M is denoted by . For example, Figure 2a is a Petri net, where , , , and .
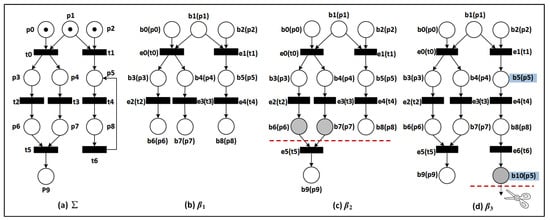
Figure 2.
A Petri net and its branching processes , and .
Definition 2
(Causality, conflict and concurrency). In an acyclic net (P, T, F), given two nodes x, y∈P∪T,
- (1)
- x and y are incausality, which is denoted by x ≤ y, if the net contains a path from x to y. Especially, if , it is denoted as x < y.
- (2)
- x and y are inconflict, which is denoted by , if ∃: ∩≠∅, ≤x, and ≤ y; or,
- (3)
- x and y are inconcurrency, denoted by xcoy, if there is neither , nor , nor .
For the example of Figure 2b, the nodes and are in causality, and are in conflict, and and are in concurrency.
An occurrence net is a special net, and its formal definition is given, as follows.
Definition 3
(Occurrence net []). A net is called an occurrence net if
- (1)
- : ;
- (2)
- : ; and,
- (3)
- no transition is in self-conflict, i.e., :.
In an occurrence net, places and transitions are usually called conditions and events, respectively. In general, we use , E, to denote an occurrence net, where B, E, and G are, respectively, sets of conditions, events, and arcs. is the set of minimal elements of with respect to the causal relation, i.e., . For example, Figure 2b is an occurrence net, where .
Based on occurrence net, a branching process of a Petri net is defined, as follows.
Definition 4
(Branching process []). Let , T, F, ) be a Petri net. is a branching process of if the occurrence net , E, G) and the homomorphism satisfy:
- (1)
- and ;
- (2)
- for every , the restriction of h onto (resp., )) is a bijection between and (resp., between and );
- (3)
- the restriction of h onto is a bijection between and ; and,
- (4)
- for every ,, if and , then .
Definition 5
(Prefix). Let =, , , be two branching processes of a Petri net where . is a prefix of if .
4. The Existing Unfolding Method of Petri Nets
4.1. Finite Complete Prefix
All of the branching processes of a Petri net form a partially ordered set w.r.t. the binary relation prefix. Its greatest element is called Unfolding of , which is denoted as . In order to generate the unfolding of a Petri net, some related definitions and calculations are introduced, such as configuration, co-set, and cut-off event.
Definition 6
(Configuration []). A configuration C of a branching process is defined as a set of events, such that C is causally closed (i.e., : ) and conflict-free (i.e., ∈).
A local configuration of an event e is |, ∈. Especially, if an event set satisfies : , then its local configuration is . The set of all (resp. local) configurations of a branching process is denoted by (resp. ). Obviously, a (local) configuration represents a possible partial run of a Petri net [].
A set of conditions is a co-set if its elements are pairwise in concurrency relation. A cut is a maximal co-set with respect to the set inclusion relation ⊂. The set of all cuts of a branching process is denoted by . For the example of Figure 2c, = , , , =, , and is a cut.
In fact, configurations, cuts, and reachable markings are closely connected by the following formulas [], i.e.,
where C is a finite configuration of a branching process , is a reachable marking, is a cut function that maps a configuration set into a cut set, and the function → represents the reachable marking by firing a finite configuration. Especially, M is called a local marking if . For the example of Figure 2c, = and .
Although the unfolding records all the running information of a Petri net, it is infinite if there exists an infinite firing transition sequence. For example, the unfolding of Figure 2a is infinite, because there is a loop from to . Thus, it is hard to utilize an infinite unfolding to analyze a concurrent system. In order to solve this problem, a finite and complete prefix (FCP) [,,] is proposed.
A prefix is an FCP if it satisfies finiteness and completeness, i.e.,
- only contains finitely many events and conditions; and,
- for every reachable marking M there exists a configuration C in such that , and for every transition t enabled by M there exists a configuration such that and e is labeled by t.
4.2. The Classical Algorithm for Generating an FCP
In order to generate an FCP, cut-off events (Definition. 7) are proposed to determine which events are not added into a given prefix when guaranteeing its finiteness and completeness. In other words, the unfolding of Petri net is truncated by cut-off events. For the example of Figure 2d, is a cut-off event, because ==, and , where is an adequate order and was first used in Petri net unfolding by Esparza et al. [].
Definition 7
(Cut-off event). Let β be a prefix, and , be two events. The event is a cut-off event if =), where ⊲ is an adequate order that is a strict well-founded partial order on a set of prefix and it refines ⊂, i.e., .
An FCP can be generated with many unfolding methods. In general, their basic idea is that for a given finite prefix, one of its possible extensions (corresponding to enabled transitions) is selected and added into it if the possible extension is not a cut-off event; and, then, for this new finite prefix, the above operation is continually conducted until all of the possible extensions are cut-off events or there is no possible extension. In this basic process, possible extensions are those transitions that can be added into a given prefix, while cut-off events determine its boundaries and scales. Corresponding to the basic idea, Algorithm 1 [] shows a general method for producing an FCP. In this algorithm, the function is used to calculate all possible extensions of a given prefix , i.e.,
| Algorithm 1 A finite complete prefix (FCP) algorithm |
| Require: |
| A Petri net ; |
| Ensure : |
| A finite complete prefix of ; |
|
4.3. Discussion
Many unfolding methods of generating FCPs have been proposed based on Algorithm 1, such as merged process and directed unfolding. Although these methods can generate different FCPs for a given Petri net, all of them cannot work without the calculations of configurations, cuts (or concurrent conditions), and cut-off events, since they are performed according to Definitions 6 and 7 and Equations (1)–(3). Obviously, these calculations can directly affect the unfolding efficiency of Petri nets. However, the related computing methods of configurations, cuts, and cut-off events easily suffer from the following problems:
- (1)
- The repeated calculations of configurations and cuts.
The calculations of configurations and cuts need to be repeatedly conducted without considering the causality and recurrence relations between events. For example, in order to calculate the local configuration of in Figure 2d, it needs to find out all of the events that are in casuality with it. Thus, we can get = , , according to Definition 6. In fact, some events of have been previously obtained by calculating the local configurations of ’s prep-sets. This is because and . Similarly, in order to calculate the cut of , it needs to find out all the pre-/post-sets of , i.e., = (. In fact, some results can be calculated by ’s prep-sets since their local configurations have been obtained.
- (2)
- The blindness in determining cut-off events.
According to the definition of cut-off events, we know that, once a new event is generated and added into a given prefix, it needs to match with all of the existing events, so as to determine whether it is a cut-off event. For example, if we determine whether is a cut-off event in of Figure 2d, it has to find out one event e from the existing event set satisfying =. In fact, some transitions with certain structures correspond to these cut-off events. Hence, we can utilize them to guide the determination of cut-off events rather than the blind matchings with all events.
5. An Improved Computing Method for Unfolding Petri Nets
In this section, we propose an incremental and backward-conflict guided method for calculating configurations, cuts, and cut-off events. Furthermore, an improved unfolding algorithm is developed to do some model checkings.
5.1. The Incremental Calculations of Configurations and Cuts
We can easily derive Lemma 1 because a configuration is causally closed and conflict-free.
Lemma 1.
- (1)
- ;
- (2)
- ;
- (3)
- .
From Lemma 1, we can find that the local configuration of an event can be recursively calculated by its prep-sets. Furthermore, these prep-sets can also compute the post-/pre-set of this local configuration.
In this paper, all of the local configurations can be represented by a configuration matrix. Thus, once a new event is added into a given prefix, its new local configuration can be calculated by Lemma 1, and a new configuration matrix of this prefix is accordingly updated. Figure 3 shows the configuration matrices of and in Figure 2b,c, respectively. From Figure 3, we can find that the local configuration of can be calculated by a logical OR operation on the local configurations of and in the configuration matrix of .
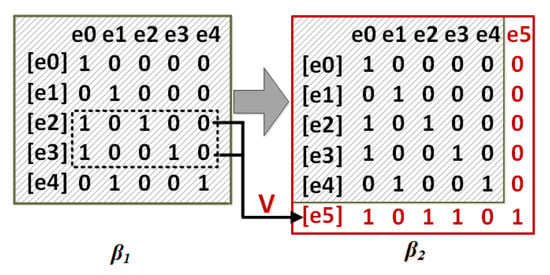
Figure 3.
The configuration matrices of Figure 2b,c.
We propose the following theorems to reveal the recursive relations between an event and its prep-sets in order to improve the calculations of cuts.
Theorem 1.
If C is a configuration of a branching process β, then there exists a set of events satisfying , where .
Proof.
If , then . It is assumed that . From this assumption, we can easily get . Because C is a configuration, then . However, . Obviously, it contradicts the above assumption. Hence, if , then . Therefore, . □
According to Theorem 1, we can further obtain the following formula.
where and . Especially, if and , then
Theorem 2.
Let e be an event of a branching process. If the pre-event set of e is a non-empty set, i.e., ≠∅, then =∪∖.
Proof.
From Equation (2), we can obtain = (∪∖. Let . If ∅, then = (∪ (∪∖ (∪) = ((∪) ∖ (∪)) ∪ (∖ (∪)). Since ∩=∅ and ∩=∅, then = (((∪ ) ∖) ∖) ∪= (∖) ∪= (∪) ∖. □
Based on Theorem 2 and Equation(5), we can utilize these recursive relations between an event and its prep-set to calculate the related cuts. For the example of Figure 2c, ∪∖, where and .
Therefore, the contexts (Definition 8) of every event can be computed and recorded during the process of producing an FCP. What is more, they can be reused in the subsequent calculations of another events. For the example of Figure 2c, the context of is =, , , , , , , and it can be reused to calculate the context of , since .
Definition 8
(Context). The context of an event e is a four-tuple .
Although Equation (3) gives the calculation of possible extensions, it is not easy to find out all of the co-sets in the unfolding process of Petri nets. For example, if we determine whether the transition can be added into the prefix in Figure 2b, it has to find out all related concurrent conditions from the existing ones. In fact, we can utilize the concurrency relation of the prep-sets of a condition to recursively calculate its concurrent conditions, and then compute all possible extensions.
Therefore, in order to determine whether a transition t can be added into a given prefix , it is necessary to find a co-set X in much more efficiently, which satisfies = and ∉. Because of the fact that concurrent conditions make up a co-set, we can utilize the recursive relation between an event and its prep-sets to improve their calculations.
Stefan Romer [] gives this recursive relation, and shows that the concurrent conditions of one condition can be recursively calculated by its prep-sets. That is, if denotes the concurrent conditions of a condition b, then
For the example of Figure 2c, and .
In this paper, all the concurrent relations of conditions can be represented by a concurrency matrix. Thus, once a new event is added into a given prefix, the new concurrent conditions can be calculated by Equation (6), and a new concurrency matrix is accordingly updated. Figure 4 shows the concurrency matrices of and in Figure 2b,c, respectively. From Figure 4, we can find that the concurrent conditions of can be calculated by a logical AND operation on the concurrent conditions of and in the concurrency matrix of .
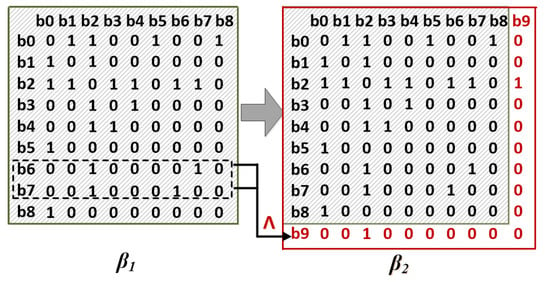
Figure 4.
The concurrency matrices of Figure 2b,c.
Based on the recursive calculation of concurrent conditions, we give a specific algorithm for calculating possible extensions, as shown in Algorithm 2.
| Algorithm 2 Possible extension algorithm |
| Require: |
| A prefix and its concurrency matrix A of conditions; |
| Ensure : |
| A set of possible extensions ; |
|
5.2. The Backward-Conflict Guided Calculations of Cut-Off Events
According to the definition of cut-off events (Definition 7) and Theorem 2, our incremental calculations of configurations and cuts are also conductive to the determination of cut-off events since they are closely related with these calculations. In this part, we utilize backward conflicts (Definition 9) [] to further guide the calculations/matchings of cut-off events.
Definition 9
(Backward conflict). Two different transitions, and , are in backward conflict if ∩ ≠ ∅.
As is well known, the initial marking of a Petri net is possibly equal to the Mark function value of the local configuration of an event e in a prefix, i.e., . In fact, this event is a cut-off event, and it guarantees the finiteness and completeness of this prefix. Therefore, in order to efficiently calculate cut-off events in this case, we first transform the places with tokens and input transitions into backward-conflict structures (Notice that this transformation does not affect the properties of original Petri nets). That is to say, if there exists a place p in a Petri net that satisfies , we add a new place , a new transition and some arcs (i.e., flow relations and ) into . Meanwhile, the new initial marking becomes , and it satisfies ∧∧. Figure 5 shows this transformation process of a Petri net before unfolding it.
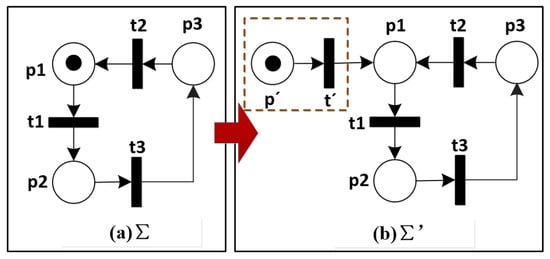
Figure 5.
The pre-process of a Petri net before unfolding it.
After transforming into some backward-conflicts, we can use these structures to guide the related matchings with certain existing events, so as to determine cut-off events.
Lemma 2.
If an event is a cut-off event of a branching process with respect to an event , then : ∩∧: ∩.
Proof.
From the definition of cut-off events, we can get = and =. It is assumed that there is no event satisfying ∩, then : ∩. Hence, ∧. No matter that or , it cannot satisfy =. Therefore, : ∩. Similarly, we can come to the other conclusion that : ∩. □
For example, is a cut-off event with respect to in Figure 2d, where ∩. In fact, the transitions and are in backward conflict. Therefore, Lemma 2 shows the relation between cutoff events and backward-conflict transitions. Furthermore, we can determine whether an event is a cutoff event only when it corresponds to a backward-conflict transition.
Specifically, a function of possible cut-off transitions with respect to a Petri net is given to guide the determination of cut-off events in this paper, i.e.,
Furthermore, we can easily get the following theorem.
Theorem 3.
Let Σ be a Petri net and β be a branching process of Σ. If e is a cut-off event of β, then .
According to Theorem 3, we match a new event with to determine whether it is a cut-off event. For the example of Figure 2d, is a cut-off event with respect to , where ∩≠∅, = , and .
5.3. An Improved Algorithm for Generating an FCP
Based on the above new calculations of configurations, cuts, and cut-off events, we propose an improved method for unfolding a Petri net, as shown in Figure 6. Corresponding to this basic process, we develop an incremental and backward-conflict guided algorithm for generating an FCP, as shown in Algorithm 3.
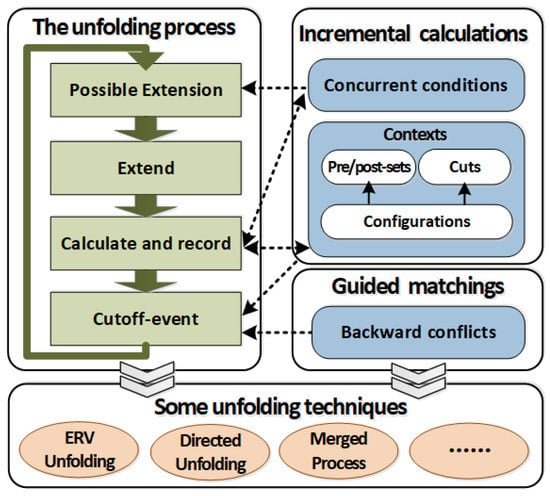
Figure 6.
The basic process of our improved method for unfolding a Petri net.
- The contexts of events are calculated in Lines 10–15 according to Equation (5) and Theorem 2.
- Algorithm 2 is utilized to calculate the possible extensions.
- Cut-off events are determined by Theorem 3, and Lines 19–22 correspond to this point.
| Algorithm 3 An incremental and backward-conflict guided algorithm for generating an FCP |
| Require: |
| A Petri net ; |
| Ensure : |
| A finite complete prefix of ; |
| (1) Initialize |
|
| (2) Unfolding process |
|
5.4. The Validation of Our Improved Unfolding Method
The prefix generated by Algorithm 3 is finite and complete, since it is the same as that by the classical unfolding. What is more, our new computing methods can improve the unfolding efficiency of Petri nets as compared with Algorithm 1 due to the fact that recursive relations, contextual information, and backward conflicts are considered in our specified calculations. Moreover, the result of our improved method is guaranteed by the following factors. On the one hand, we derive Equations (4)–(6) according to Lemma 1, Theorems 1 and 2. Based on these Equations, we can utilize the prep-transition (i.e., predecessor) of an event e to calculate its cuts if (Algorithm 3). That is, (∪∖, where ∈. Otherwise, some calculated contextual results (Definition 8) can be directly reused in order to compute the cuts of e. By comparison, the classical unfolding methods need a lot of repetitive calculations of pre-sets and post-sets for each event in . Thus, our improved unfolding method saves much time in the runtime of calculating configurations and cuts. On the other hand, we match a new event with (Equation (7)) to determine whether it is a cut-off event according to Lemma 2 and Theorem 3. By comparison, the classical unfolding methods need to match a new event with all existing events. What is more, the time complexity of classical unfolding methods is generally , while our improved calculation is , where L is the number of total events and K is the number of events that map to . Note that, K is much less than L (i.e., ) with the increase of L. Thus, our improved unfolding method saves much time in the runtime of calculating cut-off events. Nevertheless, our method takes up more space than the classical unfolding, because it needs to store many more contextual results.
5.5. Model Checkings Based on the Improved Unfolding Method
Our improved computing method for unfolding Petri nets can be applied to many model checkings.
- (1)
- Embedded into the existing unfolding techniques
The new calculations of configurations, cuts, concurrent conditions (possible extensions), and cut-off events can be applied in various kinds of unfolding techniques, e.g., ERV unfolding, merged process and directed unfolding. As is well known, ERV unfolding proposes a new classical algorithm for improving the McMillan’s unfolding. The merged process (MP) generates a condensed unfolding of a Petri net’s behavior. Directed unfolding (DU) utilizes heuristic functions to guide the unfolding process of Petri nets. Given these unfolding techniques, our improved computing methods can replace their calculations of configurations, cuts, and cut-off events. Meanwhile, our new calculations can be further combined with partial orders, merged conditions and heuristic functions in their related unfolding methods of Petri nets. By this means, our new computing methods can enhance these unfolding techniques and improve their model checkings.
- (2)
- Checking reachability, properly completed, and deadlocks
Some errors can be detected based on the unfolding techniques. In this paper, we refer to some previous studies [,,,,], and utilize our improvements to efficiently check reachability [,], properly completed [,] and deadlocks [,].
- ReachabilityOn the one hand, we can utilize the directed unfolding technique [] to verify the reachability of markings or places. On the other hand, some incremental calculations of configurations (e.g., configuration matrix) can be used to check whether a transition is reachable to the other one in the execution of a Petri net. That is, given two transitions and two events , if the configuration matrix A of an FCP satisfies , then we can come to the conclusion that is reachable to . Notice that and are, respectively, the i-th and j-th elements of E.
- Properly completedAs is well known, a WF-net is properly completed if it satisfies , where o is the sink place []. In order to verify this property, we can determine whether there exist some conditions that are concurrent with sink conditions (i.e., corresponding to the sink places) in our concurrency matrix. If these conditions exist, they indicate that is not properly completed or sound.
- DeadlocksBecause the context of an event is calculated in our improved unfolding method, we can utilize its cuts and Mark functions to check deadlocks, i.e., a marking M is a deadlock if and no transition is enabled at M.
6. Case Study
In order to illustrate the application scenarios of our improved method for unfolding Petri nets, a case study of airport check-in is given, as follows.
A passenger must check in at theairport before boarding an airplane. Figure 7 shows the basic business process of an airport check-in system (IBM: https://www.ibm.com/developerworks/rational/library/2802.html, (accessed on 5 January 2021)). In this business process, the passengers’ reservations are first checked. If their reservations are correct, these passengers can choose/change their seats. Otherwise, the incorrect reservations are sent to the airport travel agency. After choosing seats, the airport can receive the passengers’ baggages and print their receipts. Meanwhile, the boarding cards are concurrently printed. Finally, all travel of the documents is provided to passengers.
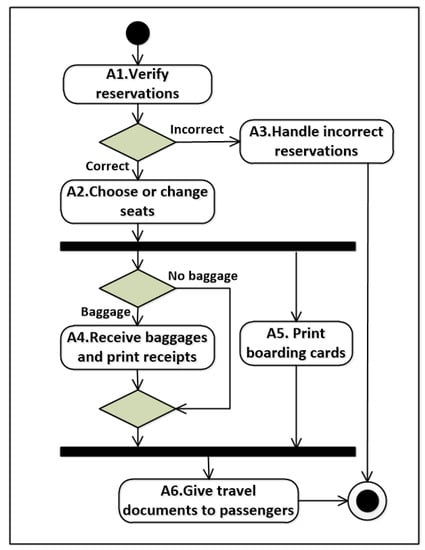
Figure 7.
The business process of an airport check-in system.
As for the above business process, we first use a Petri net of Figure 8a to model it. Table 1 lists the meanings of all transitions in , where the backward-conflict transition set is . Thus, we can obtain the possible cut-off transitions, i.e.,
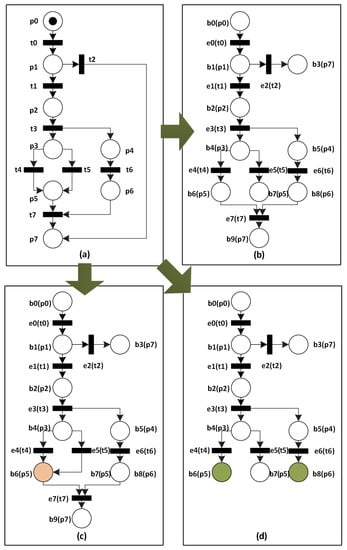
Figure 8.
(a) A Petri net that models an airport check-in system; (b) the ERV unfolding of ; (c) the merged process of ; and, (d) the directed unfolding of , where is a reachable marking.

Table 1.
Activities.
According to Algorithm 3, we unfold and generate its FCP, as shown in Figure 8b. During this unfolding process, Table 2 records all contexts of events and Figure 9 shows the incremental calculations of configurations and concurrent conditions. Meanwhile, backward-conflict transitions are utilized to guide the matchings between events and , where = and . Thus, is a cut-off event with respect to .

Table 2.
The contexts of events.
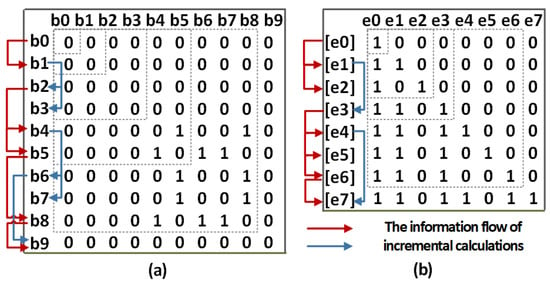
Figure 9.
(a) The incremental calculations of concurrent conditions; (b) the incremental calculations of configurations.
Additionally, we can generate a merged process and directed unfolding of , respectively, as shown in Figure 8c,d. Based on these unfoldings, we can verify some properties, such as deadlocks, properly completed, and reachability.
- (1)
- There is no deadlock in because there always exist enabled transitions at any local markings (except for the final state).
- (2)
- is properly completed, because no condition is concurrent with the sink condition in the concurrency matrix of Figure 9a.
- (3)
- Because events and are included in the directed unfolding and satisfy ∧∧, the marking is reachable from the initial marking .
- (4)
- According to the configuration matrix of Figure 9b, the transition is reachable to the transition in the execution of , since the events and satisfy ∧∧.
From this case study, we can find that our improved computing method for unfolding a Petri net is feasible, and its result is correct. Moreover, this method can be applied to different unfolding techniques and model checkings.
7. Experiments and Results
7.1. Data Collections and Tool
The experiments in this paper are respectively done on the benchmarks of BPM_AIMC (The BPM Academic Initiative Model Collection: https://bpmai.org/download/index.html (accessed on 30 December 2020)) and Dining Philosophers []. BPM_AIMC is a famous data collection of formal models, and it has 100 + Petri nets. By now, this benchmark has been utilized by hundreds of academic institutes. The n-Dining-Philosopher is a classical problem in the synchronization of concurrent events/actions, and we can use Petri nets to formalize this problem, where n is from two to 20. For these two benchmarks, we use our tool DICER (DICER is developed based on PIPE (an open source tool), which can unfold Petri nets and PD-nets, and detect errors of data inconsistency.) [] to implement the new methods and conduct a group of experiments.
7.2. Implementation and Results
In order to illustrate the unfolding efficiency of our improved computing method, we compare it with some unfolding methods in terms of runtime, such as ERV unfolding, merged process (MP), and directed unfolding (DU). That is, our improved calculations of configurations/cuts, concurrent conditions, and cut-off events are applied to these unfolding techniques, i.e., improved ERV unfolding (IERV), improved merged process (IMP), and improved directed unfolding (IDU), respectively.
- (1)
- The experiments on BPM_AIM
Because to the fact that Petri nets in BPM_AIMC are JSON documents, we first utilize the parsers of JSON and XML to transform them into some PNML (Petri Net Markup Language) [] documents, which can be loaded by DICER. After getting PNML-based Petri nets, we select bounded ones from them with more than 10 transitions. Meanwhile, we assume that their initial places only have one token. Finally, we import 37 Petri nets of BPM_AIMC into DICER, and then generate their unfoldings. All of these experiments are done in a PC with Intel Core i5-2400 CPU (3.10GHz) and 4.0G memory.
Figure 10, Figure 11 and Figure 12 are the results of our experiments on BPM_AIMC. From Figure 10, we can see that IERV spends less time than ERV to generate an FCP. Similarly, IMP (resp. IDU) takes less time than MP (resp. DU). Obviously, our improved computing method is more effective than others in the runtime of unfolding Petri nets, although the scale of BPM_AIMC is not too large in reality.
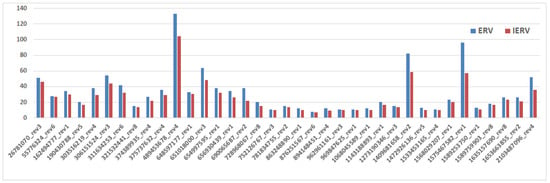
Figure 10.
The unfolding time (ms) of Esparza, Romer, and Vogler (ERV) and improved ERV unfolding (IERV), where ERV is an unfolding technique and IERV applies our improved computing method to ERV.
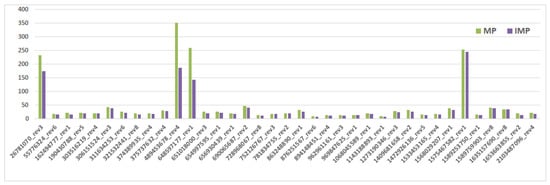
Figure 11.
The unfolding time (ms) of merged process (MP) and IMP, where MP is an unfolding technique and IMP applies our improved computing method to MP.
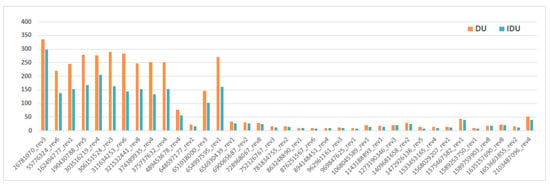
Figure 12.
The unfolding time (ms) of directed unfolding (DU) and IDU, where DU is an unfolding technique and IDU applies our improved computing method to DU.
- (2)
- The experiments on Dining Philosophers
Some experiments are done on Dining Philosophers in order to further show the advantage of our method. We first import 10 Petri nets of Dining Philosophers into DICER, and then generate their unfoldings. For example, Figure 13 shows a Petri net of two-philosophers’ dining problem in DICER.
Figure 13.
The Petri net of 2-philosophers’ dining problem in DICER.
Figure 14a–c are the results of our experiments on Dining Philosophers. From these results, we can see that ERV (resp. MP, DU) spends much more time than IERV (resp. IMP, IDU) to generate FCPs with the increment of n philosophers.
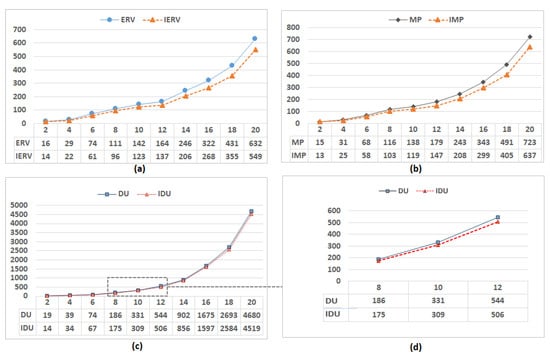
Figure 14.
The unfolding time (ms) of different unfolding techniques on n-philosophers’ dining problem, where n is from 2 to 20. (a) IERV vs. ERV; (b) IMP vs. MP; (c) IDU vs. DU; and, (d) is a part of (c).
8. Conclusions
Concurrent systems easily suffer from some errors, such as deadlocks, lack of synchronization, and data inconsistencies. Although reachability-graph-based methods are proposed to check these errors, they generally have the problems of state space explosion. This is because these methods are based on the interleaving semantics, and the need to consider all partial orders of business activities to analyze their global behaviors of concurrent systems. By comparison, the unfolding technique of Petri net can characterize the real concurrency and alleviate the state space explosion problem, since it uses an acyclic net to represent the system running. Thus, it is greatly suitable to analyze/check some potential errors in a concurrent system.
As for the unfolding technique of Petri nets, the calculations of configurations, cuts, and cut-off events are key factors that make up an absolutely significant share of the total unfolding time. However, most of the unfolding methods do not specify highly efficient calculations on them. They mainly focus on how to generate a smaller FCP, or explore different kinds of Petri net unfoldings and their model checkings. In fact, their calculations of configurations and cuts need a lot of repetitive work, and new events need to match them up with all existing events so as to determine whether they are cut-off events. In order to solve these problems, we propose an improved computing method for unfolding Petri nets. Some recursion formulas and theorems are derived to calculate configurations and cuts. Backward conflicts are used to guide the determinations of cut-off events. Furthermore, we develop some improved algorithms for generating FCPs.
In the future work, we plan to carry out the following studies:
- (1)
- we apply our new calculations with heuristic functions into many more model checkings of concurrent systems;
- (2)
- timed concurrent systems are simulated and analyzed based on the unfolding techniques of Petri nets; and,
- (3)
- we explore the unfolding-based technique of WFD-net [] to check concurrency bugs [,,].
Author Contributions
D.X. proposed the idea in this paper and prepared the software application; D.X. and X.T. designed the experiments; D.X. performed the experiments; Y.L. analyzed the data; D.X. wrote the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by Zhejiang Provincial Natural Science Foundation of China under Grant LQ20F020002, and in part by the Key Laboratory of Embedded System and Service Computing (Ministry of Education) under Grant ESSCKF 2019-02.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Moutinho, F.; Gomes, L. Asynchronous-channels within Petri net-based GALS distributed embedded systems modeling. IEEE Trans. Ind. Inform. 2014, 10, 2024–2033. [Google Scholar] [CrossRef]
- Zhou, M.C.; Wu, N. System Modeling and Control with Resource-Oriented Petri Nets; CRC Press, Inc.: Boca Raton, FL, USA, 2009. [Google Scholar]
- Qi, L.; Zhou, M.; Luan, W. A two-level traffic light control strategy for preventing incident-based urban traffic congestion. IEEE Trans. Intell. Transp. Syst. 2016, 19, 13–24. [Google Scholar] [CrossRef]
- Esparza, J.; Schröter, C. Unfolding based algorithms for the reachability problem. Fundam. Inform. 2001, 47, 231–245. [Google Scholar]
- Liu, G.; Reisig, W.; Jiang, C. A Branching-process-based method to check soundness of workflow systems. IEEE Access 2016, 4, 4104–4118. [Google Scholar] [CrossRef]
- Liu, M.; Wang, S.; Zhou, M.; Liu, D.; Al-Ahmari, A.; Qu, T.; Wu, N.; Li, Z. Deadlock and liveness characterization for a class of generalized Petri nets. Inf. Sci. 2017, 420, 403–416. [Google Scholar] [CrossRef]
- Franco, A.; Baldan, P. True Concurrency and Atomicity: A Model Checking Approach with Contextual Petri Nets; LAP LAMBERT Academic Publishing: Saarbrucken, Germany, 2015. [Google Scholar]
- McMillan, K.L. Using unfoldings to avoid the state explosion problem in the verification of asynchronous circuits. In Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 1992; pp. 164–177. [Google Scholar]
- Buchholz, P.; Kemper, P. Hierarchical Reachability Graph Generation for Petri Nets. Form. Methods Syst. Des. 2002, 21, 281–315. [Google Scholar] [CrossRef]
- Wisniewski, R.; Karatkevich, A.; Adamski, M.; Costa, A.; Gomes, L. Prototyping of Concurrent Control Systems with Application of Petri Nets and Comparability Graphs. IEEE Trans. Control Syst. Technol. 2017, 26, 575–586. [Google Scholar] [CrossRef]
- Wiśniewski, R.; Wiśniewska, M.; Jarnut, M. C-exact hypergraphs in concurrency and sequentiality analyses of cyber-physical systems specified by safe Petri nets. IEEE Access 2019, 7, 13510–13522. [Google Scholar] [CrossRef]
- Bonet, B.; Haslum, P.; Khomenko, V.; Thiébaux, S.; Vogler, W. Recent advances in unfolding technique. Theor. Comput. Sci. 2014, 551, 84–101. [Google Scholar] [CrossRef]
- Esparza, J.; Römer, S.; Vogler, W. An improvement of McMillan’s unfolding algorithm. Form. Methods Syst. Des. 2002, 20, 285–310. [Google Scholar] [CrossRef]
- Khomenko, V.; Kondratyev, A.; Koutny, M.; Vogler, W. Merged processes: A new condensed representation of Petri net behaviour. Acta Inform. 2006, 43, 307–330. [Google Scholar] [CrossRef]
- Bonet, B.; Haslum, P.; Hickmott, S.; Thiébaux, S. Directed unfolding of petri nets. In Transactions on Petri Nets and Other Models of Concurrency I; Springer: Berlin/Heidelberg, Germany, 2008; pp. 172–198. [Google Scholar]
- Haar, S. Types of asynchronous diagnosability and the reveals-relation in occurrence nets. IEEE Trans. Autom. Control 2010, 55, 2310–2320. [Google Scholar] [CrossRef][Green Version]
- Hickmott, S.L.; Rintanen, J.; Thiébaux, S.; White, L.B. Planning via Petri Net Unfolding. In Proceedings of the International Joint Conference on Artificial Intelligence, Hyderabad, India, 6–12 January 2007; Volume 7, pp. 1904–1911. [Google Scholar]
- Leon, H.P.d.; Saarikivi, O.; Kahkonen, K.; Heljanko, K.; Esparza, J. Unfolding Based Minimal Test Suites for Testing Multithreaded Programs. In Proceedings of the 15th International Conference on Application of Concurrency to System Design, Brussels, Belgium, 21–26 June 2015; pp. 40–49. [Google Scholar]
- Heljanko, K.; Khomenko, V.; Koutny, M. Parallelisation of the Petri net unfolding algorithm. In Proceedings of the 8th International Conference on Tools and Algorithms for Construction and Analysis of Systems (TACAS), LNCS, Grenoble, France, 8–12 April 2002; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2280, pp. 371–385. [Google Scholar]
- Khomenko, V.; Mokhov, A. An algorithm for direct construction of complete merged processes. In Proceedings of the International Conference on Application and Theory of Petri Nets and Concurrency, Paris, France, 24–25 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 89–108. [Google Scholar]
- Couvreur, J.M.; Poitrenaud, D.; Weil, P. Branching processes of general Petri nets. Fundam. Inform. 2013, 122, 31–58. [Google Scholar] [CrossRef]
- Rodríguez, C.; Sousa, M.; Sharma, S.; Kroening, D. Unfolding-based Partial Order Reduction. In Proceedings of the 26th International Conference on Concurrency Theory (CONCUR 2015), Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik, Madrid, Spain, 1–4 September 2015. [Google Scholar]
- Chatain, T.; Paulevé, L. Goal-Driven Unfolding of Petri Nets. In Proceedings of the 28th International Conference on Concurrency Theory (CONCUR 2017), Berlin, Germany, 5–8 September 2017. [Google Scholar]
- Lu, F.; Tao, R.; Du, Y.; Zeng, Q.; Bao, Y. Deadlock detection-oriented unfolding of unbounded Petri nets. Inf. Sci. 2019, 497, 1–22. [Google Scholar] [CrossRef]
- Jiroveanu, G.; Boel, R.K.; Schutter, B.D. Fault Diagnosis for Time Petri Nets. In Proceedings of the International Workshop on Discrete Event Systems, Ann Arbor, MI, USA, 10–12 July 2006. [Google Scholar]
- Chatain, T.; Fabre, E. Factorization Properties of Symbolic Unfoldings of Colored Petri Nets. In Proceedings of the International Conference on Applications & Theory of Petri Nets, Braga, Portugal, 21–25 June 2010. [Google Scholar]
- Rodriguez, C.; Schwoon, S.; Baldan, P. Efficient Contextual Unfolding. In Proceedings of the International Conference on Concurrency Theory, Aachen, Germany, 6–9 September 2011. [Google Scholar]
- Lomazova, I.A.; Ermakova, V.O. Verication of Nested Petri Nets Using an Unfolding Approach. In Proceedings of the International Workshop on Petri Nets & Software Engineering, Torun, Poland, 20–21 June 2016. [Google Scholar]
- Khomenko, V.; Koutny, M. LP deadlock checking using partial order dependencies. In Proceedings of the International Conference on Concurrency Theory, State College, PA, USA, 22–25 August 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 410–425. [Google Scholar]
- Rodriguez, C.; Schwoon, S. Verification of Petri nets with read arcs. In Proceedings of the International Conference on Concurrency Theory, Newcastle, UK, 4–7 September 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 471–485. [Google Scholar]
- De León, H.P.; Haar, S.; Longuet, D. Model-based testing for concurrent systems: Unfolding-based test selection. Int. J. Softw. Tools Technol. Transf. 2016, 18, 305–318. [Google Scholar] [CrossRef]
- Jezequel, L.; Madalinski, A.; Schwoon, S. Distributed computation of vector clocks in Petri nets unfolding for test selection. In Proceedings of the Workshop on Discrete Event Systems (WODES), Sorrento Coast, Italy, 30 May–1 June 2018. [Google Scholar]
- Kähkönen, K.; Saarikivi, O.; Heljanko, K. Using unfoldings in automated testing of multithreaded programs. In Proceedings of the 27th IEEE/ACM International Conference on Automated Software Engineering, Essen, Germany, 3–7 September 2012; pp. 150–159. [Google Scholar]
- Saarikivi, O.; Ponce-De-León, H.; Kähkönen, K.; Heljanko, K.; Esparza, J. Minimizing test suites with unfoldings of multithreaded programs. ACM Trans. Embed. Comput. Syst. (TECS) 2017, 16, 45. [Google Scholar] [CrossRef]
- Lutz-Ley, A.; López-Mellado, E. Stability Analysis of Discrete Event Systems Modeled by Petri Nets Using Unfoldings. IEEE Trans. Autom. Sci. Eng. 2018, 15, 1964–1971. [Google Scholar] [CrossRef]
- Meyer, R.; Khomenko, V.; Strazny, T. A practical approach to verification of mobile systems using net unfoldings. Fundam. Inform. 2009, 94, 439–471. [Google Scholar] [CrossRef]
- Ponce-de León, H.; Rodríguez, C.; Carmona, J.; Heljanko, K.; Haar, S. Unfolding-based process discovery. In Proceedings of the International Symposium on Automated Technology for Verification and Analysis, Shanghai, China, 12–15 October 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 31–47. [Google Scholar]
- Weidlich, M.; Elliger, F.; Weske, M. Generalised computation of behavioural profiles based on petri-net unfoldings. In Proceedings of the International Workshop on Web Services and Formal Methods, Hoboken, NJ, USA, 16–17 September 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 101–115. [Google Scholar]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. Detecting data inconsistency based on the unfolding technique of petri nets. IEEE Trans. Ind. Inform. 2017, 13, 2995–3005. [Google Scholar] [CrossRef]
- Römer, S. Theorie und Praxis der Netzentfaltungen als Grundlage Für die Verifikation Nebenläufiger Systeme. Ph.D. Thesis, Technical University, Munich, Germany, 2000. [Google Scholar]
- Dong, L.; Liu, G.; Xiang, D. Verifying CTL with Unfoldings of Petri Nets. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing, Melbourne, Australia, 9–11 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 47–61. [Google Scholar]
- Liu, C.; Zeng, Q.; Duan, H.; Wang, L.; Tan, J.; Ren, C.; Yu, W. Petri net based data-flow error detection and correction strategy for business processes. IEEE Access 2020, 8, 43265–43276. [Google Scholar] [CrossRef]
- Liu, G.; Jiang, C.; Zhou, M. Process nets with channels. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2012, 42, 213–225. [Google Scholar] [CrossRef]
- Wynn, M.T. Soundness of workflow nets: Classification, decidability, and analysis. Form. Asp. Comput. 2011, 23, 333–363. [Google Scholar]
- Guo, X.; Wang, S.; You, D.; Li, Z.; Jiang, X. A siphon-based deadlock prevention strategy for S 3 PR. IEEE Access 2019, 7, 86863–86873. [Google Scholar] [CrossRef]
- Zhou, M.C.; Fanti, M.P. Deadlock Resolution in Computer-Integrated Systems; CRC Press, Inc.: Boca Raton, FL, USA, 2004. [Google Scholar]
- Hillah, L.M.; Kordon, F.; Petrucci, L.; Treves, N. PNML Framework: An extendable reference implementation of the Petri Net Markup Language. In Proceedings of the International Conference on Applications and Theory of Petri Nets, Braga, Portugal, 21–25 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 318–327. [Google Scholar]
- Xiang, D.; Liu, G.; Yan, C.G.; Jiang, C. A Guard-driven Analysis Approach of Workflow Net With Data. IEEE Trans. Serv. Comput. 2019, 1. [Google Scholar] [CrossRef]
- Kim, K.H.; Yavuz-Kahveci, T.; Sanders, B.A. JRF-E: Using model checking to give advice on eliminating memory model-related bugs. Autom. Softw. Eng. 2012, 19, 491–530. [Google Scholar] [CrossRef]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. Detecting data-flow errors based on Petri nets with data operations. IEEE/CAA J. Autom. Sin. 2017, 5, 251–260. [Google Scholar] [CrossRef]
- Zhang, M.; Wu, Y.; Shan, L.U.; Qi, S.; Ren, J.; Zheng, W. A Lightweight System for Detecting and Tolerating Concurrency Bugs. IEEE Trans. Softw. Eng. 2016, 42, 899–917. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).