Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement
Abstract
:1. Introduction
1.1. Research Background and Motivation
1.2. Contributions of the Work
1.3. Structure of the Paper
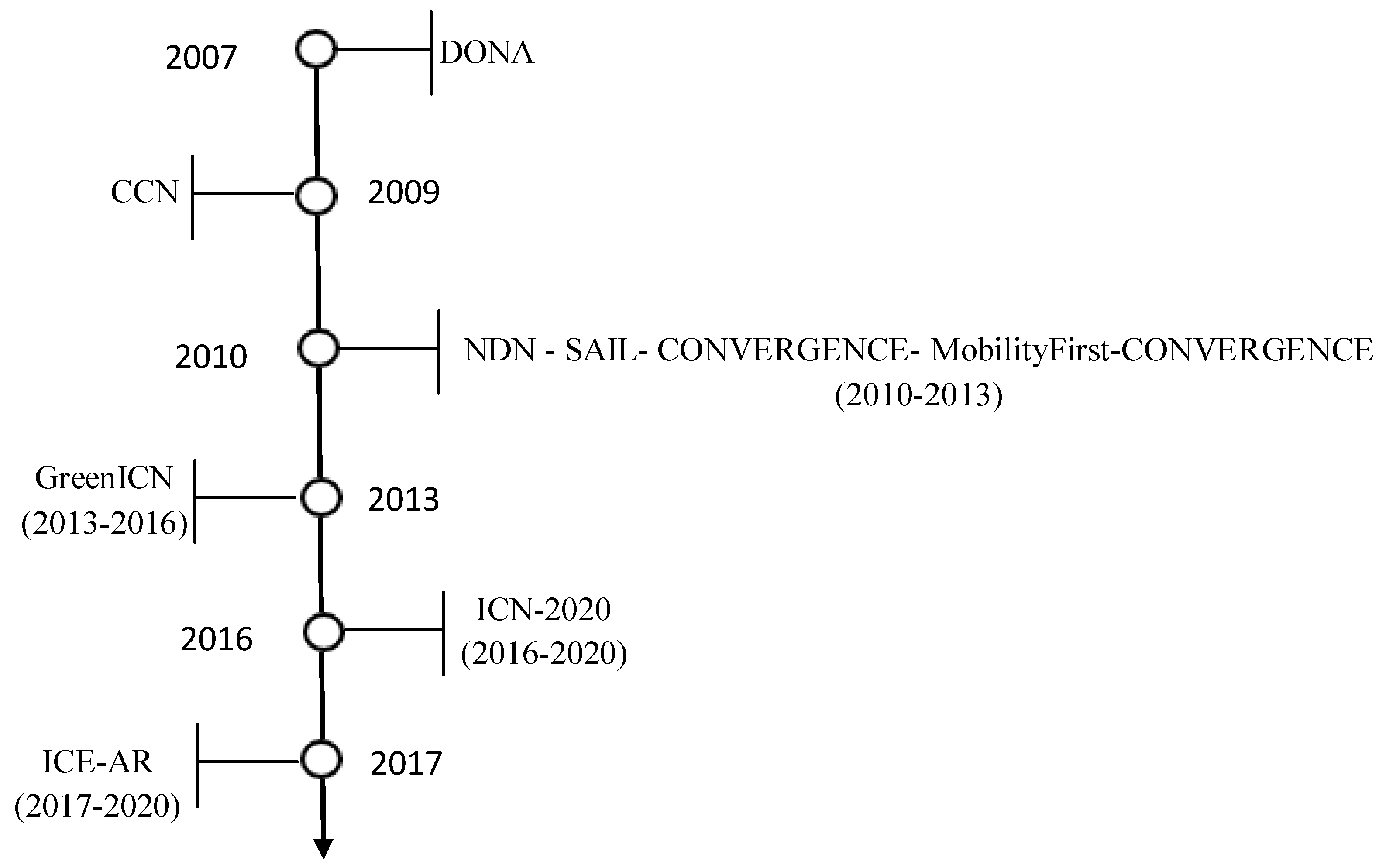
2. Information-Centric Networking
- Nommage: One of the key features of each ICN architecture plan is the structure of the name assigned to the information (or service). Information-relative names are independent of their positions within all ICN architectures. On the other hand, the titles may range from flat to hierarchical, depending on the approach, which may or may not be readable by the recipient.
- Name resolution and data routing: The resolution of the name involves associating an information name with a service or source that can supply it, while data routing involves constructing a route from the provider to the requesting host to transfer information. Whether these two functions are coupled or decoupled is the crucial issue. The request for information is forwarded to the information provider in the coupled method, returning the information to the requesting host after the reverse direction on which the request was returned. The name-resolution feature of the decoupled method does not define or limit the path that the data takes from the supplier to the subscriber.
- Caching: We understand that caching [17] is both on the path and off the path. The network exploits the information stored along the path taken by a name-resolution request in on-path caching, while the network exploits the cached information in off-path caching. This is just hidden outside of this path.
2.1. ICN Architectures
2.1.1. DONA
2.1.2. NDN
2.1.3. PSIRP
2.1.4. NetInf
2.2. ICN Problem
3. Software-Defined Networking
- -
- The planes of control and data are decoupled. The network devices are excluded from the control functionality, which makes it easy to switch objects.
- -
- Transition decisions are based on the flow, not the destination. A flow is generally defined by a set of field values that function as a filter criterion and a set of acts (instructions). A flow is a series of frames between a source and a destination in the sense of SDN/OpenFlow. All the frames in a flow receive similar transfer equipment service policies. The abstraction of flow unites the actions of numerous items of network equipment, including routers, switches, firewalls and middleboxes. Flow programming provides unparalleled precision, restricted only by the capability of the applied flow tables.
- -
- The control logic is passed on to the external party, the SDN controller, or the operating system of the network (NOS). The NOS is a software interface that draws on core server technologies and offers critical mechanisms and abstractions to logically promote forwarding system programming based on an abstract and centralized view of the network. Hence, its function is close to that of a traditional operating system.
- -
- Via software programs running on the NOS, which communicate with the underlying data plane computers, the network is programmable. This is a basic function of SDN, perceived to be its key attribute.
3.1. Current Internet-Architecture Issues
3.2. Current SDN Architectures
3.2.1. ForCES
3.2.2. OpenFlow
4. Related Work
4.1. CroS-NDN
4.2. NDNFlow
4.3. SRSC
5. Named-Data Networking Based on SDN
- Bootstrapping step: During this step, the controller identifies and associates the nodes with their identity. The nodes therefore know the interface on which their requests are relayed to their handler. Indeed, bootstrapping helps the controller to explore and provide a global view of the network’s topology.
- Routing: The routing stage consists of filling in the nodes’ FIB to allow them to relay messages of interest to the nearest source. Therefore, where a node does not know the interface to which to send a message of interest, the controller is interrogated. This exchange is carried out using NDN interest/data messages via the contact channel (Figure 6).
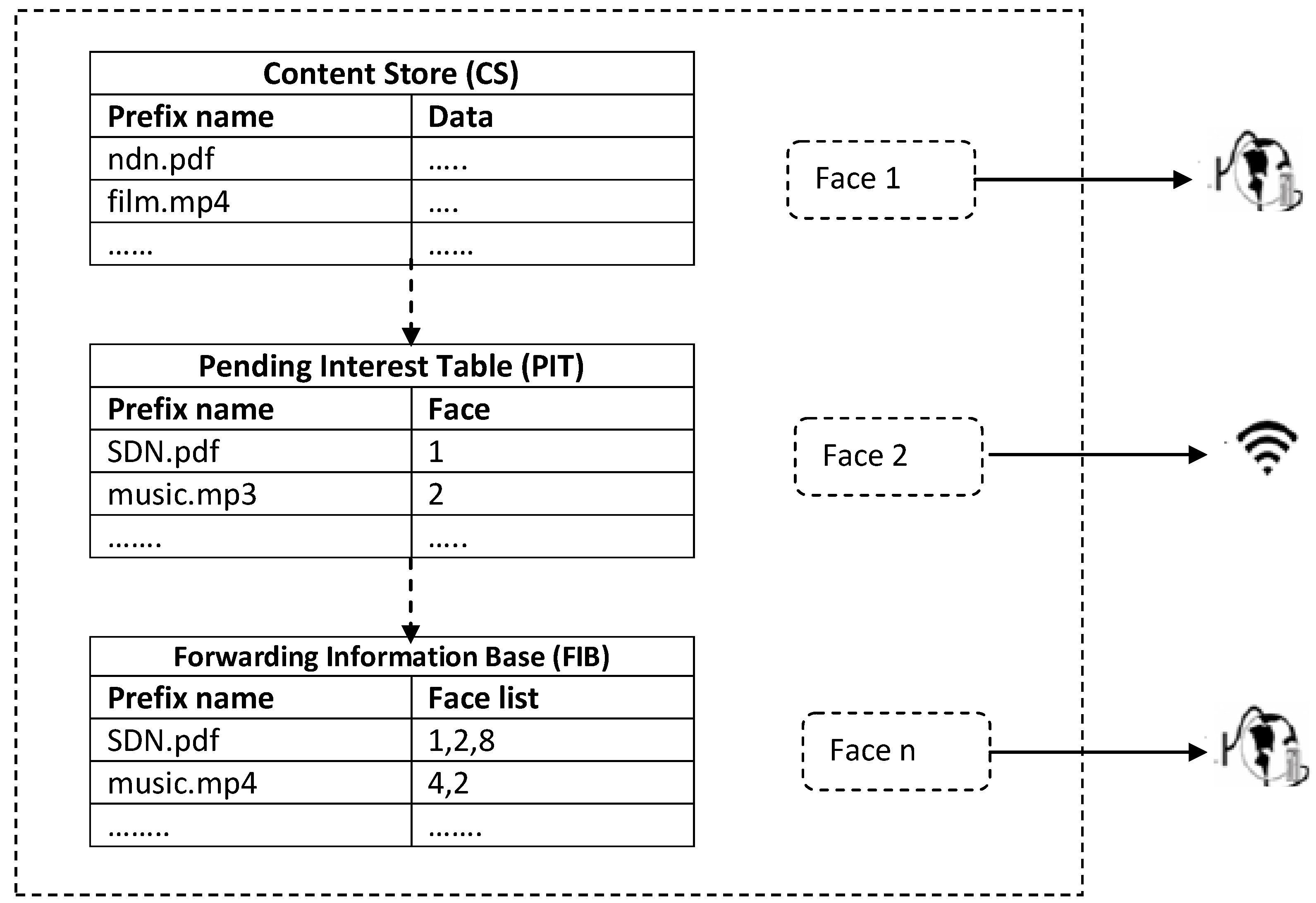
5.1. Structure of an NDN–SDN Switch
- The content store (CS): A cache installed in the NDN Switch.
- The pending interest table (PIT): The PIT table stores the currently-being -processed requests.
- Management information base (MIB): The MIB includes the neighborhood information (node, switch and controller).
5.2. Structure of an NDN–SDN Controller
- The content store (CS): A cache installed in the NDN–SDN controller.
- The management information base (MIB): The MIB table contains information about all the nodes connected to the controller.
- The data information base (DIB): The DIB includes all the prefixes of all the nodes connected to the controller.
- The forwarding information base (FIB): The FIB contains the routing information for the data.
5.3. NDN–SDN Topology Management
5.4. NDN–SDN Data Management
5.5. NDN–SDN Forwarding Management
5.6. NDN–SDN: Detecting Failures
6. Experimentation and Results
- Bandwidth consumption: this is the cost of the communication generated by each switch on the network per second. The average value of all the content switches was taken into account.
- Average latency time: this is the time taken for complete content (that is to say, a file) to be downloaded. The average value of all the content routers was taken into account.
- Cache-hit ratio: this is the proportion of interest requests served by the content store (CS) of switches or SDN controllers. The average value of all the switches was taken into account in our work.
6.1. NDN–SDN Approach and Bandwidth
6.2. NDN–SDN Approach and Delay
6.3. SDN Approach and Cache Hits
6.4. NDN–SDN Approach and Memory Overhead
6.5. Discussion of Results
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cisco. Cisco Annual Internet Report (2018–2023) White Paper. 2020. Available online: www.cisco.com (accessed on 27 February 2021).
- Cisco. Cisco Annual Internet Report. 2020. Available online: www.cisco.com (accessed on 27 February 2021).
- Belarmino, A.; Koh, Y. A critical review of research regarding peer-to-peer accommodations. Int. J. Hosp. Manag. 2020, 84, 102315. [Google Scholar] [CrossRef]
- Salah, H.; Zimmermann, S.; Cabrera G., J.A. Chapter 5—Content distribution. In Computing in Communication Networks; Fitzek, F.H., Granelli, F., Seeling, P., Eds.; Academic Press: New York, NY, USA, 2020; pp. 93–103. [Google Scholar]
- Fotiou, N. Information-Centric Networking (ICN). Future Internet 2020, 12, 35. [Google Scholar] [CrossRef] [Green Version]
- Yu, K.; Eum, S.; Kurita, T.; Hua, Q.; Sato, T.; Nakazato, H.; Asami, T.; Kafle, V.P. Information-Centric Networking: Research and Standardization Status. IEEE Access 2019, 7, 126164–126176. [Google Scholar] [CrossRef]
- Singh, S.; Jha, R.K. A Survey on Software Defined Networking: Architecture for Next Generation Network. J. Netw. Syst. Manag. 2016, 25, 321–374. [Google Scholar] [CrossRef]
- Masoudi, R.; Ghaffari, A. Software defined networks: A survey. J. Netw. Comput. Appl. 2016, 67, 1–25. [Google Scholar] [CrossRef]
- Isyaku, B.; Zahid, M.S.M.; Kamat, M.B.; Bakar, K.A.; Ghaleb, F.A. Software Defined Networking Flow Table Management of OpenFlow Switches Performance and Security Challenges: A Survey. Future Internet 2020, 12, 147. [Google Scholar] [CrossRef]
- Kalghoum, A.; Saidane, L.A. FCR-NS: A novel caching and forwarding strategy for Named Data Networking based on Software Defined Networking. Clust. Comput. 2019, 22, 981–994. [Google Scholar] [CrossRef]
- Jmal, R.; Fourati, L.C. Content-Centric Networking Management Based on Software Defined Networks: Survey. IEEE Trans. Netw. Serv. Manag. 2017, 14, 1128–1142. [Google Scholar] [CrossRef]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A Survey of Information-Centric Networking Research. IEEE Commun. Surv. Tutor. 2014, 16, 24–49. [Google Scholar] [CrossRef]
- Yovita, L.V.; Syambas, N.R.; Edward, I.J.M.; Kamiyama, N. Performance Analysis of Cache Based on Popularity and Class in Named Data Network. Future Internet 2020, 12, 227. [Google Scholar] [CrossRef]
- Vasilakos, A.V.; Li, Z.; Simon, G.; You, W. Information centric network: Research challenges and opportunities. J. Netw. Comput. Appl. 2015, 52, 1–10. [Google Scholar] [CrossRef]
- Saxena, D.; Raychoudhury, V.; Suri, N.; Becker, C.; Cao, J. Named Data Networking: A survey. Comput. Sci. Rev. 2016, 19, 15–55. [Google Scholar] [CrossRef] [Green Version]
- Dannewitz, C.; Kutscher, D.; Ohlman, B.; Farrell, S.; Ahlgren, B.; Karl, H. Network of Information (NetInf)—An information-centric networking architecture. Comput. Commun. 2013, 36, 721–735. [Google Scholar] [CrossRef]
- Naeem, M.A.; Rehman, M.A.U.; Ullah, R.; Kim, B.S. A Comparative Performance Analysis of Popularity-Based Caching Strategies in Named Data Networking. IEEE Access 2020, 8, 50057–50077. [Google Scholar] [CrossRef]
- Naeem, M.A.; Nor, S.A.; Hassan, S. Future Internet Architectures. 2020, pp. 520–532. Available online: https://www.researchgate.net/publication/336989259_Future_Internet_Architectures (accessed on 27 February 2021).
- Cox, J.H.; Chung, J.; Donovan, S.; Ivey, J.; Clark, R.J.; Riley, G.; Owen, H.L. Advancing Software-Defined Networks: A Survey. IEEE Access 2017, 5, 25487–25526. [Google Scholar] [CrossRef]
- Zhang, X.; Cui, L.; Wei, K.; Tso, F.P.; Ji, Y.; Jia, W. A survey on stateful data plane in software defined networks. Comput. Netw. 2021, 184, 107597. [Google Scholar] [CrossRef]
- Haleplidis, E.; Salim, J.H.; Halpern, J.M.; Hares, S.; Pentikousis, K.; Ogawa, K.; Weiming, W.; Denazis, S.; Koufopavlou, O. Network Programmability with ForCES. IEEE Commun. Surv. Tutor. 2015, 17, 1423–1440. [Google Scholar] [CrossRef]
- Lara, A.; Kolasani, A.; Ramamurthy, B. Network Innovation using OpenFlow: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 493–512. [Google Scholar] [CrossRef] [Green Version]
- Torres, J.V.; Alvarenga, I.D.; Boutaba, R.; Duarte, O.C.M. An autonomous and efficient controller-based routing scheme for networking Named-Data mobility. Comput. Commun. 2017, 103, 94–103. [Google Scholar] [CrossRef]
- van Adrichem, N.L.M.; Kuipers, F.A. NDNFlow: Software-defined Named Data Networking. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015; pp. 14–20. [Google Scholar]
- Aubry, E.; Silverston, T.; Chrisment, I. SRSC: SDN-based routing scheme for CCN. In Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft), London, UK, 13–17 April 2015. [Google Scholar]
- Mastorakis, S.; Afanasyev, A.; Moiseenko, I.; Zhang, L. ndnSIM 2.0: A New Version of the NDN Simulator for NS-3. Technical Report NDN-0028. 2015. Available online: www.named-data.net/ (accessed on 27 February 2021).
- Lal, N.; Kumar, S.; Kadian, G.; Chaurasiya, V.K. Caching methodologies in Content centric networking (CCN): A survey. Comput. Sci. Rev. 2019, 31, 39–50. [Google Scholar] [CrossRef]
- Afanasyev, A.; Shi, J.; Zhang, B.; Zhang, L.; Moiseenko, I.; Yu, Y. NFD Developer’s Guide. Technical Report NDN-0021. 2017. Available online: www.named-data.net/ (accessed on 27 February 2021).
- Kalghoum, A.; Gammar, S.M. Towards New Information Centric Networking Strategy Based on Software Defined Networking. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]











| CroS-NDN [23] | NDNFlow [24] | SRSC [25] | |
|---|---|---|---|
| Clean-slate design | Yes, based only on NDN protocol | No, based on IP protocol | Yes, based only on CCN protocol |
| ICN protocol | NDN-based | NDN-based | CCN-based |
| SDN protocol | SDN-based | OpenFlow-based | SDN-based |
| Routing schema | controller-based | IP-based | Controller-based |
| Security | Signature-based | Signature-based | firewall-based |
| Parameter | Value |
|---|---|
| Router percentage | 5% |
| Number of nodes | 150, 300, 400, 600, 1000 |
| Cache strategy | LRU |
| Forwarding strategy | Flooding, NCC, best-route |
| Topology | Hierarchical |
| Number of consumers | 30% |
| Number of producers | 10% |
| Distance between nodes | 200 m |
| SDN protocol | OpenFlow |
| Time of simulation | 120 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guesmi, T.; Kalghoum, A.; Alshammari, B.M.; Alsaif, H.; Alzamil, A. Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement. Symmetry 2021, 13, 441. https://doi.org/10.3390/sym13030441
Guesmi T, Kalghoum A, Alshammari BM, Alsaif H, Alzamil A. Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement. Symmetry. 2021; 13(3):441. https://doi.org/10.3390/sym13030441
Chicago/Turabian StyleGuesmi, Tawfik, Anwar Kalghoum, Badr M. Alshammari, Haitham Alsaif, and Ahmed Alzamil. 2021. "Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement" Symmetry 13, no. 3: 441. https://doi.org/10.3390/sym13030441
APA StyleGuesmi, T., Kalghoum, A., Alshammari, B. M., Alsaif, H., & Alzamil, A. (2021). Leveraging Software-Defined Networking Approach for Future Information-Centric Networking Enhancement. Symmetry, 13(3), 441. https://doi.org/10.3390/sym13030441







