Fuzzy Logic Testing Approach for Measuring Software Completeness
Abstract
:1. Introduction
2. Preliminaries
2.1. Software Requirements
2.2. Fuzzy Functionality Similarity between Software Modules
2.3. Completeness of Software Components
2.3.1. Complete Membership
2.3.2. Partial Membership
2.3.3. Non-Membership
2.4. Linguistic Variable
2.5. Proof of Software Security Level
2.6. Programming Language Faults
2.6.1. Algorithm Fault
2.6.2. Computational Fault
2.6.3. Syntax Fault
2.6.4. Documentation Fault
2.6.5. Overload Fault
2.6.6. Timing Fault
2.6.7. Hardware Fault
2.6.8. Software Fault
2.6.9. Omission Fault
2.6.10. Commission Fault
3. Related Work
4. Fuzzy Membership Value of the Software Components
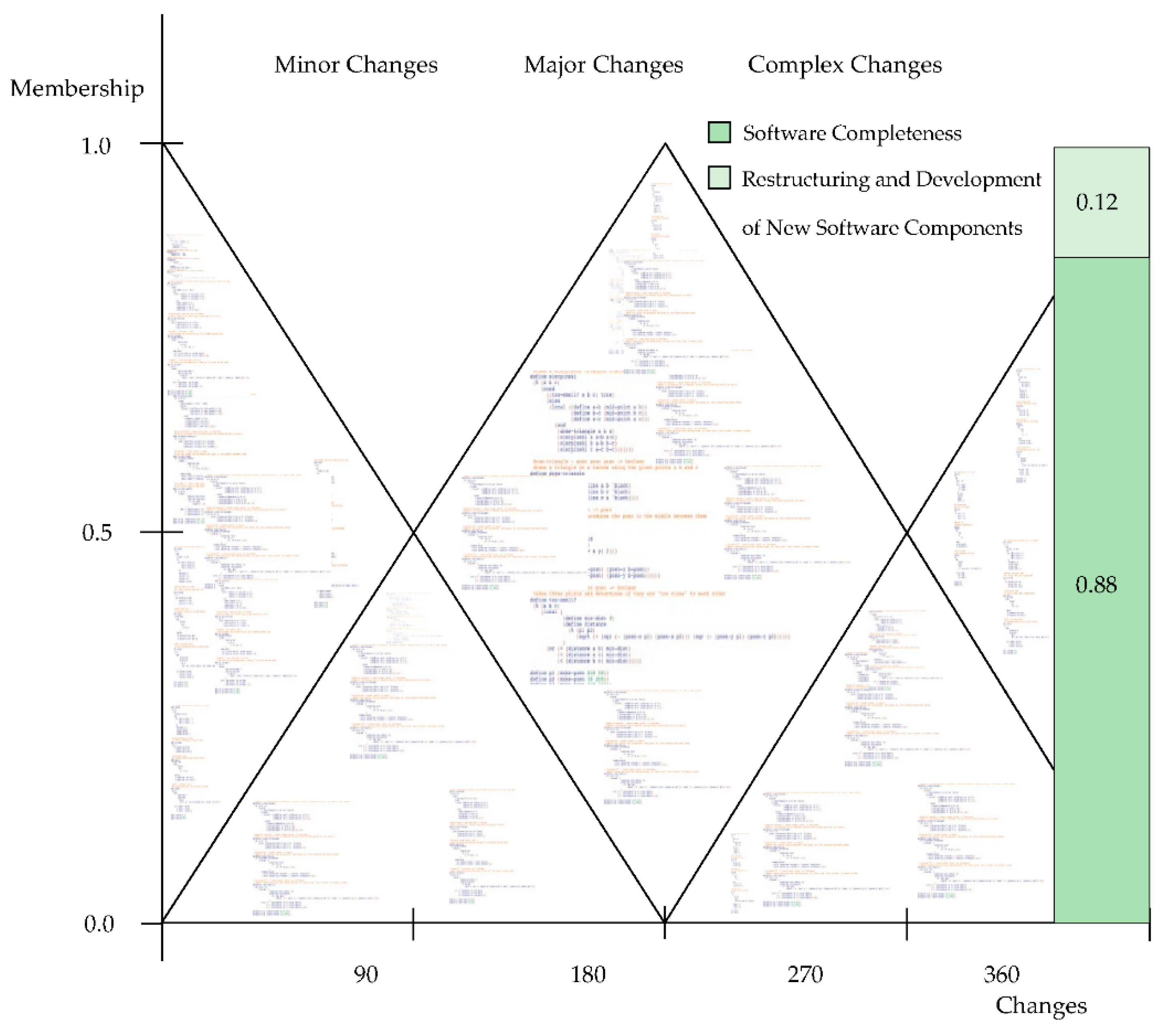
5. Software Completeness
5.1. Proof
5.1.1. Complete Membership Value
5.1.2. Non-Membership Value
5.1.3. Partial Membership Value
6. Materials and Methods
7. Results
- Accuracy = = = 0.97
- Sensitivity = Recall = = = 0.99
- Specificity = = = 0.83
- Precision = = = 0.98
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| Set of features | |
| Requirements | |
| System response tested for the ith software component , that contains k number of system responses | |
| Total system response tested for the ith software component | |
| Functional requirements | |
| Non-functional requirements | |
| Inverse requirements | |
| Non-inverse requirements | |
| Content requirements | |
| Non-content requirements | |
| Software | |
| Software component, where i represents software component number, i = {1, 2, 3, …, n} or i = {a, b, c, …, z} | |
| Represents the ith software component, where j represents the software requirement number | |
| Represents the functionality of the component, i represents the software component and k represents the functionality number of the ith software component | |
| Module, f represents module number | |
| Module, p represents module number | |
| ∈ | Belongs to |
| ≙ | Corresponds to |
| Engineering of software | |
| Complete membership of the software components | |
| Partial membership of the software components | |
| Non-membership of the software components | |
| Total number of software components | |
| Software components completeness index | |
| Software completeness | |
| Membership value of the software response for software component , k response number | |
| Fuzzy membership value (0 ≤ ≤ 1) | |
| Software program | |
| True positive | |
| False positive | |
| False negative | |
| True negative |
References
- Cabrera, I.P.; Cordero, P.; Ojeda-Aciego, M. Fuzzy logic, soft computing, and applications. In Proceedings of the 10th International Work-Conference on Artificial Neural Networks, Salamanca, Spain, 10–12 June 2009; pp. 236–244. [Google Scholar]
- So, S.; Cha, S.; Kwon, Y. Empirical evaluation of a fuzzy logic-based software quality prediction model. Fuzz Sets Syst. 2002, 127, 199–208. [Google Scholar] [CrossRef]
- Bosc, P.; Damiani, E.; Fugini, M. Fuzzy service selection in a distributed object-oriented environment. IEEE Trans. Fuzz Syst. 2001, 9, 682–698. [Google Scholar] [CrossRef]
- Idri, A.; Abran, A. A fuzzy logic based measures for software project similarity: Validation and possible improvements. In Proceedings of the 7th International Software Metrics Symposium, London, UK, 4–6 April 2001; pp. 85–96. [Google Scholar]
- Pang, C. Software Engineering for Agile Application Development; IGI Global Publisher of Timely Knowledge: Uster, Switzerland; Seveco AG: Mönchaltorf, Switzerland, 2020. [Google Scholar]
- Davis, A.; Overmyer, S.; Jordan, K.; Caruso, J.; Dandashi, F.; Dinh, A.; Kincaid, G.; Ledeboer, G.; Reynolds, P.; Sitaram, P.; et al. Identifying and measuring quality in a software requirements specification. In Proceedings of the First International Software Metrics Symposium, Baltimore, MD, USA, 21–22 May 1993; pp. 141–152. [Google Scholar]
- Iqbal, N.; Sang, J.; Gao, M.; Hu, H.; Xiang, H. Forward engineering completeness for software by using requirements validation framework. In Proceedings of the 31st International Conference on Software Engineering and Knowledge Engineering, Lisbon, Portugal, 10–12 July 2019; KSI Research Inc.: Pittsburg, PA, USA, 2019; pp. 523–528. [Google Scholar]
- Laptante, P.A. Requirements Engineering for Software and System, 3rd ed.; CRC Press/Taylor & Francis: Boca Raton, FL, USA, 2017; pp. 15–45. [Google Scholar]
- Menzel, I.; Mueller, M.; Gross, A.; Doerr, J. An experimental comparison regarding the completeness of functional requirements specifications. In Proceedings of the 18th IEEE International Requirements Engineering Conference, Sydney, NSW, Australia, 27 September–1 October 2010; IEEE: New York, NY, USA,, 2010; pp. 15–24. [Google Scholar]
- Xie, G.; Chen, J.; Neamtiu, I. Towards a better understanding of software evolution: An empirical study on open source software. In Proceedings of the IEEE International Conference on Software Maintenance, Edmonton, AB, Canada, 20–26 September 2009; pp. 51–60. [Google Scholar]
- Robbes, R.; Lanza, M. A changed-based approach to software evolution. Electron. Notes Theor. Comput. Sci. 2007, 166, 93–109. [Google Scholar] [CrossRef] [Green Version]
- Robbes, R.; Lanza, M.; Lungu, M. An approach to software evolution based on semantic change. In Proceedings of the 10th International Conference on Fundamental Approaches to Software Engineering, Held as Part of the Joint European Conference on Theory and Practice of Software, Braga, Portugal, 24 March–1 April 2007; pp. 27–41. [Google Scholar]
- Zave, P. An experiment in feature engineering. In Programming Methodology; Springer: Berlin/Heidelberg, Germany, 2003; pp. 353–377. [Google Scholar]
- Graham, D.; Black, R.; Veenendaal, E.V. Foundations of Software Testing, 4th ed.; Cengage Learning EMEA: Somerset West, UK, 2019. [Google Scholar]
- Patton, R. Software Testing, 2nd ed.; Sams Publishing: Carmel, IN, USA, 2005. [Google Scholar]
- Homès, B. Fundamentals of Software Testing; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2013. [Google Scholar]
- Jorgensen, P.C. Software Testing: A Craftsman’s Approach, 4th ed.; Auerbach Publications: Boca Raton, FL, USA, 2013. [Google Scholar]
- Naik, K.; Tripathy, P. Software Testing and Quality Assurance: Theory and Practice; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2008. [Google Scholar]
- Apel, S.; Kastner, C.; Batory, D. Program refactoring using functional aspects. In Proceedings of the 7th International Conference on Generative Programming and Component Engineering, Nashville, TN, USA, 19–23 October 2008; pp. 161–170. [Google Scholar]
- Liu, W.; He, C.; Zhang, K. Service-based domain requirements completeness analysis. In Proceedings of the Asia-Pacific Conference on Computational Intelligence and Industrial Applications, Wuhan, China, 28–29 November 2009; pp. 110–115. [Google Scholar]
- Bezdek, J.C. Fuzzy models-what are they, and why? IEEE Trans. Fuzz Syst. 1993, 1, 1–6. [Google Scholar] [CrossRef]
- Bandler, W.; Kohout, L.J. Fuzzy power sets and fuzzy implication operators. Fuzz Sets Syst. 1980, 4, 13–30. [Google Scholar] [CrossRef]
- Zadeh, L. Fuzzy sets. Inf. Control. 1965, 8, 338–353. [Google Scholar] [CrossRef] [Green Version]
- Sleimi, A.; Sannier, N.; Sabetzadeh, M.; Briand, L.C.; Dann, J. Automated extraction of semantic legal metadata using natural language processing. In Proceedings of the 26th IEEE International Requirements Engineering Conference, Banff, AB, Canada, 20–24 August 2018; pp. 124–135. [Google Scholar]
- Brooks, R. Data Privacy: What You Need to Know and How to Get Started. Available online: https://blog.netwrix.com/2019/08/08/data-privacy/ (accessed on 10 February 2021).
- Wegener, J.; Grochtmann, M. Verifying Timing Constraints of Real-Time Systems by Means of Evolutionary Testing. Real Time Syst. 1998, 15, 275–298. [Google Scholar] [CrossRef]
- Iqbal, N.; Sang, J.; Chen, J.; Xia, X. Measuring Software Maintainability with Naïve Bayes Classifier. Entropy 2021, 23, 136. [Google Scholar] [CrossRef] [PubMed]
- Ansari, M.Z.A. Softrology: Learn Software Technologies. Available online: https://softrology.blogspot.com/search?q=inverse (accessed on 25 November 2020).
- Zadeh, L.A. The concept of a linguistic variable and its application to approximate reasoning-I. Inf. Sci. 1975, 8, 199–249. [Google Scholar] [CrossRef]
- Kacprzyk, J.; Yager, R. Linguistic summaries of data using fuzzy logic. Int. J. Gen. Syst. 2001, 30, 133–154. [Google Scholar] [CrossRef]
- Murray, T. Proofs and Side Effects. Available online: https://verse.systems/blog/post/2018-10-02-Proofs-And-Side-Effects/ (accessed on 11 February 2021).
- Cadar, C.; Dunbar, D.; Engler, D. KLEE: Unassisted and automatic generation of high-coverage tests for complex systems programs. In Proceedings of the 8th USENIX Conference on Operating Systems Design and Implementation, San Diego, CA, USA, 8–10 December 2008; pp. 209–224. [Google Scholar]
- Beurdouche, B.; Lavaud, A.D.; Kobeissi, N.; Pironti, A.; Bhargavan, K. FLEXTLS: A tool for testing TLS implementations. In Proceedings of the 9th USENIX Workshop on Offensive Technologies, Washington, DC, USA, 10–11 August 2015; pp. 1–10. [Google Scholar]
- Teplyuk, P.A.; Yakunin, A.G.; Sharlaev, E.V. Study of security flaws in the Linux kernel by fuzzing. In Proceedings of the 2020 International Multi-Conference on Industrial Engineering and Modern Technologies, Vladivostok, Russia, 6–9 October 2020; pp. 1–5. [Google Scholar]
- Bhargavan, K.; Fournet, C.; Kohlweiss, M.; Pironti, A.; Strub, P. Implementing TLS with verified cryptographic security. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 445–459. [Google Scholar]
- MacDonell, S.G.; Gray, A.R. Applying fuzzy logic modeling to software project management. Softw. Eng. Comput. 2003, 731, 17–43. [Google Scholar]
- Boehm, B.W. Software Engineering Economics. IEEE Trans. Softw. Eng. 1984, SE-10, 4–21. [Google Scholar] [CrossRef]
- Gustafson, D. Schaum’s Outlines Software Engineering, 1st ed.; McGraw-Hill Education: New York, NY, USA, 2002. [Google Scholar]
- Bano, M.; Zowghi, D. A systematic review on the relationship between user involvement and system success. Inf. Softw. Technol. 2015, 58, 148–169. [Google Scholar] [CrossRef]
- Pagano, D.; Maalej, W. User feedback in the appstore: An empirical study. In Proceedings of the IEEE 21st International Requirements Engineering Conference, Rio de Janeiro, RJ, Brazil, 15–19 July 2013; pp. 125–134. [Google Scholar]
- Carreno, L.V.G.; Winbladh, K. Analysis of user comments: An approach for software requirements evolution. In Proceedings of the 35th International Conference on Software Engineering, San Francisco, CA, USA, 18–26 May 2013; pp. 582–591. [Google Scholar]
- Pagano, D.; Bruegge, B. User involvement in software evolution practice: A case study. In Proceedings of the 35th International Conference on Software Engineering, San Francisco, CA, USA, 18–26 May 2013; pp. 953–962. [Google Scholar]
- Sram, N. Practical application of fuzzy logic: Experiences and current state in software engineering. In Proceedings of the 12th IEEE International Symposium on Computational Intelligence and Informatics, Budapest, Hungary, 21–22 November 2011; pp. 579–581. [Google Scholar]
- Yadav, H.B.; Yadav, D.K. A fuzzy logic based approach for phase-wise software defects prediction using software metrics. Infor. Softw. Tech. 2015, 63, 44–57. [Google Scholar] [CrossRef]
- Al-Refai, M.; Cazzola, W.; Ghosh, S. A fuzzy logic based approach for model-based regression test selection. In Proceedings of the 2017 ACM/IEEE 20th International Conference on Model Driven Engineering Languages and systems, Austin, TX, USA, 17–22 September 2017; pp. 55–62. [Google Scholar]
- Mittal, A.; Parkash, K.; Mittal, H. Software cost estimation using fuzzy logic. ACM SIGSOFT Softw. Eng. Notes 2017, 35, 1–7. [Google Scholar] [CrossRef]
- Yadav, D.K.; Dutta, S. Test case prioritization technique based on early fault detection using fuzzy logic. In Proceedings of the 3rd International Conference on Computing for Sustainable Global Development, New Delhi, India, 16–18 March 2016; pp. 1033–1036. [Google Scholar]
- Idri, A.; Abran, A.; Khoshgoftaar, T.M. Fuzzy case-based reasoning models for software cost estimation. Soft Comput. Softw. Eng. 2004, 159, 64–96. [Google Scholar]
- Nisar, M.W.; Wang, Y.J.; Elahi, M. Software development effort estimation using fuzzy logic—A survey. In Proceedings of the 2008 Fifth International Conference on Fuzzy Systems and Knowledge Discovery, Shandong, China, 18–20 October 2008; pp. 421–427. [Google Scholar]
- Kataev, M.; Bulysheva, L.; Xu, L.; Ekhlakov, Y.; Permyakova, N.; Jovanovic, V. Fuzzy model estimation of the risk factors impact on the target of promotion of the software product. J. Enterp. Inf. Syst. 2020, 14, 797–811. [Google Scholar] [CrossRef]
- Lima, D.C.; Freitas, F.; Campos, G.; Souza, J. A fuzzy approach to requirements prioritization. In Proceedings of the 3rd International Symposium on Search Based Software Engineering, Szeged, Hungary, 10–12 September 2011; pp. 64–69. [Google Scholar]
- Konar, A. Fuzzy pattern recognition. In Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2005; pp. 125–138. [Google Scholar]
- Chang, C.L. Fuzzy-Logic-Based Programming; World Scientific Publishing: Singapore, 1997. [Google Scholar]
- Jurado, F.; Redondo, M.A.; Ortega, M. Using fuzzy logic applied to software metrics and test cases to assess programming assignments and give advice. J. Netw. Comput. Appl. 2012, 35, 695–712. [Google Scholar] [CrossRef]
- Taratuknin, V.; Yadgarova, Y. A fuzzy logic approach for product configuration and requirements management. In Proceedings of the 2015 Annual Conference of the North American Fuzzy Information Processing Society held jointly with 2015 5th World Conference on Soft Computing, Redmond, WA, USA, 17–19 August 2015; pp. 1–5. [Google Scholar]
- Pressman, R.S. Software Engineering: A Practitioner’s Approach, 8th ed.; McGraw-Hill Education: New York, NY, USA, 2014. [Google Scholar]
- Young, R.R. Recommended requirements gathering practices. J. Def. Softw. Eng. 2002, 15, 9–12. [Google Scholar]
- Zowghi, D.; Coulin, C. Requirements elicitation: A survey of techniques, approaches, and tools. In Engineering and Managing Software Requirements, 1st ed.; Aurum, A., Wohlin, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 19–46. [Google Scholar]
- Duggan, E.W.; Thachenkary, C.S. Integrating nominal group technique and joint application development for improved systems requirements determination. Inf. Manag. 2004, 41, 399–411. [Google Scholar] [CrossRef]
- Coughlan, J.; Lycett, M.; Macredie, R.D. Communication issues in requirements elicitation: A content analysis of stakeholder experiences. Inf. Softw. Technol. 2003, 45, 54–61. [Google Scholar] [CrossRef] [Green Version]
- Peruma, A.; Almalki, K.; Newman, C.D.; Mkaouer, M.W.; Ouni, A.; Palomba, F. Tsdetect: An open source test smells detection tool. In Proceedings of the 28th ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Virtual Event, New York, NY, USA, 8–13 November 2020; pp. 1650–1654. [Google Scholar]
- Brownlee, J. What Is a Confusion Matrix in Machine Learning. Available online: https://machinelearningmastery.com/confusion-matrix-machine-learning/ (accessed on 15 December 2020).









| Requirement Type | Requirement Class | Number of Requirements | Percentage |
|---|---|---|---|
| FR | Functional | 365 | 65.18% |
| NFR | Security | 14 | 2.50% |
| Usability | 21 | 3.75% | |
| Portability | 10 | 1.79% | |
| Availability | 7 | 1.25% | |
| Capacity | 11 | 1.96% | |
| Efficiency | 12 | 2.14% | |
| Reliability | 15 | 2.68% | |
| Performance | 13 | 2.32% | |
| Maintainability | 15 | 2.68% | |
| Accuracy | 8 | 1.43% | |
| Error-handling | 10 | 1.79% | |
| Operational | 19 | 3.39% | |
| Scalability | 11 | 1.96% | |
| IR | Inverse | 9 | 1.61% |
| NIR | Security | 2 | 0.36% |
| Availability | 1 | 0.18% | |
| Performance | 1 | 0.18% | |
| CR | Content | 11 | 1.96% |
| NCR | Security | 1 | 0.18% |
| Usability | 1 | 0.18% | |
| Performance | 1 | 0.18% | |
| Operational | 2 | 0.36% | |
| Total | 560 | 100% |
| Description | Software Components |
|---|---|
| : The system must display a drop-down list for the selection of the course category (professional compulsory course, professional elective course, public basic course, public compulsory course). = 0.81 |  |
| : The system must display the selected course category and ask the user to select a course code offered by the university during the current semester. = 0.88 |  |
| : The system must calculate the CGPA according to the university format and ask the user to enter obtain marks and total marks for each subject. = 0.87 |  |
| : The system must display the recommended books for the entered course code. = 0.64 |  |
| : The system must display a text box to enter a student ID. (The system generates a student card) = 0.91 |  |
| : The system must display a text box to enter a faculty ID. (The system generates a faculty card) = 0.88 |  |
| : The system must display a text box to enter a faculty ID and research interest. (The system generates a profile) = 0.83 |  |
| : The system must display a text box to enter the ID of a degree course. (The system generates a list of courses offered during the current semester) = 0.94 |  |
| : The system must display a text box to enter a student class ID. (The system generates a timetable for the student) = 0.92 |  |
| : The system must display a text box to enter a faculty class ID. (The system generates a timetable for the faculty member) = 0.88 |  |
| : The system must display a text box to enter a student ID and a degree ID. (The system generates a transcript) = 0.95 |  |
| Description | Software Components |
|---|---|
| : The system shall not print a semester invoice after the due date. (This option is for offline payment and bank name will be printed on the semester invoice) = 0.91 |  |
| : The system shall display the text box in red if a user enters more than or less than eight digits for their national identity card number. = 0.83 |  |
| : The system shall display the text box for age in red if the age of a candidate is less than 18 years or more than 35 years. A text box in lighter blue indicates that the age will be automatically calculated. (Red text box indicates the ineligibility of a candidate) = 0.80 |  |
| : The system shall not accept a native language other than Chinese/English. = 0.89 |  |
| : The system shall not accept a nationality of a candidate other than that of their country of residence. = 0.91 |  |
| : The system shall display a red text box if a user enters a percentage of completeness of a master degree that is less than 70%. = 0.88 |  |
| : The system shall not upload a photograph for a user profile if its size is less than (300 × 400) pixels. = 0.73 |  |
| : The system shall not accept journal publications other than those from the SCI/SCIE. = 0.60 |  |
| : The system shall not accept conference publications that are not recognized by the CCF/EC. = 0.70 |  |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Iqbal, N.; Sang, J. Fuzzy Logic Testing Approach for Measuring Software Completeness. Symmetry 2021, 13, 604. https://doi.org/10.3390/sym13040604
Iqbal N, Sang J. Fuzzy Logic Testing Approach for Measuring Software Completeness. Symmetry. 2021; 13(4):604. https://doi.org/10.3390/sym13040604
Chicago/Turabian StyleIqbal, Nayyar, and Jun Sang. 2021. "Fuzzy Logic Testing Approach for Measuring Software Completeness" Symmetry 13, no. 4: 604. https://doi.org/10.3390/sym13040604







