CAKE: Compatible Authentication and Key Exchange Protocol for a Smart City in 5G Networks
Abstract
:1. Introduction
1.1. Contributions
1.2. Paper Organization
2. Related Work
- Multi-factor authentication: Remote authentication schemes were developed from the one-factor, i.e., password, authentication [8] to the two-factor and multi-factor authentication. In general, a two-factor authentication adopts smartcards as the additional second factor to avoid replay attacks, and a three-factor authentication adopts biometrics or physical unclonable functions (PUFs) as the additional third factor to avoid smartcard stolen attacks.
- Suitability for a multi-server environment: Traditional client–server AKE protocols were proposed for single-server environments. Nowadays, there are many systems constructed in multi-server architectures. Many AKE protocols for multi-server environments were proposed and users need not to register at different servers.
- Independent authentication: There is a trusted third party who needs to involve the authentication phase in many AKE protocols. On the contrary, some AKE protocols can achieve independent authentication in the sense that two entities can freely authenticate with each other by themselves without the help of any third party.
- User anonymity: In an AAKE protocol, the real identity of a user would not be revealed to others when he/she logs into a server through an untrustworthy channel.
- User untraceability/unlinkability: In ordinary AAKE schemes, even though a user uses an anonymous identity to log in, the relationship between each login is exposed to a third party since the user uses a duplicate anonymous identity in each login. Some AAKE protocols not only achieve user anonymity but also achieve user untraceability/unlinkability, where a user cannot be traced by the login transmissions, i.e., no third party can derive the relationship between any two login transmissions. Without loss of generality, to avoid the physical location tracking in an AAKE scheme, users either can simply forge their location or use physical layer signatures [9] to simultaneously achieve privacy-preserving location authentication and user untraceability.
- Member revocation: Many AKE protocols did not deal with the member revocation problem when a member is disabled or leaving. As compared with traditional revocable AKE protocols using a certificate revocation list (CRL), the advanced ones adopt time periods to deal with revocation problems, namely, a revoked or disabled member could not obtain the latest secret key in the next time period.
- Table-free: No password table or verification list needs to be stored or maintained.
- Public key issuing-free: No public key needs to be announced; that is, either there are no public keys in the system or the identity can be used as the public key.
- Leakage-resilient: This property helps to resist side channel attacks.
3. Preliminaries
3.1. Physical Unclonable Functions
3.2. Fuzzy Extractors
- Gen is a probabilistic generation procedure, which takes an input R ∈ M and outputs an extracted string SS ∈ {0, 1}l and a helper string HLP ∈ {0, 1}*. For any distribution D on M of min-entropy δ, if (SS, HLP) ← Gen(D), we have SD ((SS, HLP), (Ul, HLP)) ≤ ε.
- Rep is a deterministic reproduction procedure that can recover SS from the corresponding helper string HLP and any vector m’ close to m, namely, for all R’, R ∈ M satisfying dis (R’, R) ≤ d, if (SS, HLP) ← Gen(R), then Rep (R’, HLP) = SS.
3.3. Bilinear Pairing
- Bilinear: ê(aQ, bR) = ê(Q, R)ab for all a, b ∈ Zq* and all Q, R ∈ G1.
- Non-degenerate: There are two points Q, R ∈ G1 such that ê(Q, R) ≠ 1.
- Computability: There is an efficient algorithm to compute ê(Q, R) for all Q, R ∈ G1.
3.4. Hard Problem Assumptions
- Elliptic curve discrete logarithm (ECDL) problem: Given a point aP in G1, find the integer a.
- Elliptic curve computational Diffie–Hellman (ECCDH) problem: Given P, aP, and bP in G1, find abP in G1.
- Decisional bilinear Diffie–Hellman (DBDH) problem: Given P, aP, bP, and cP in G1 and ê(P, P)d in G2, determine whether ê(P, P)d = ê(P, P)abc.
- ECDL assumption: No probabilistic polynomial time (PPT) algorithm can solve the ECDL problem with a non-negligible advantage.
- ECCDH assumption: No PPT algorithm can solve the ECCDH problem with a non-negligible advantage.
- DBDH assumption: No PPT algorithm can solve the DBDH problem with a non-negligible advantage.
- Hash function assumption: There is a one-way and collision-resistant cryptographic hash function H: A → B satisfying the following three conditions:
- Preimage resistance: For any given b ∈ B, it is hard to find a ∈ A such that H(a) = b.
- Second preimage resistance: For any given a ∈ A, it is hard to find c ∈ A such that a ≠ c and H(a) = H(c).
- Collision resistance: It is hard to find a, c ∈ A such that a ≠ c and H(a) = H(c).
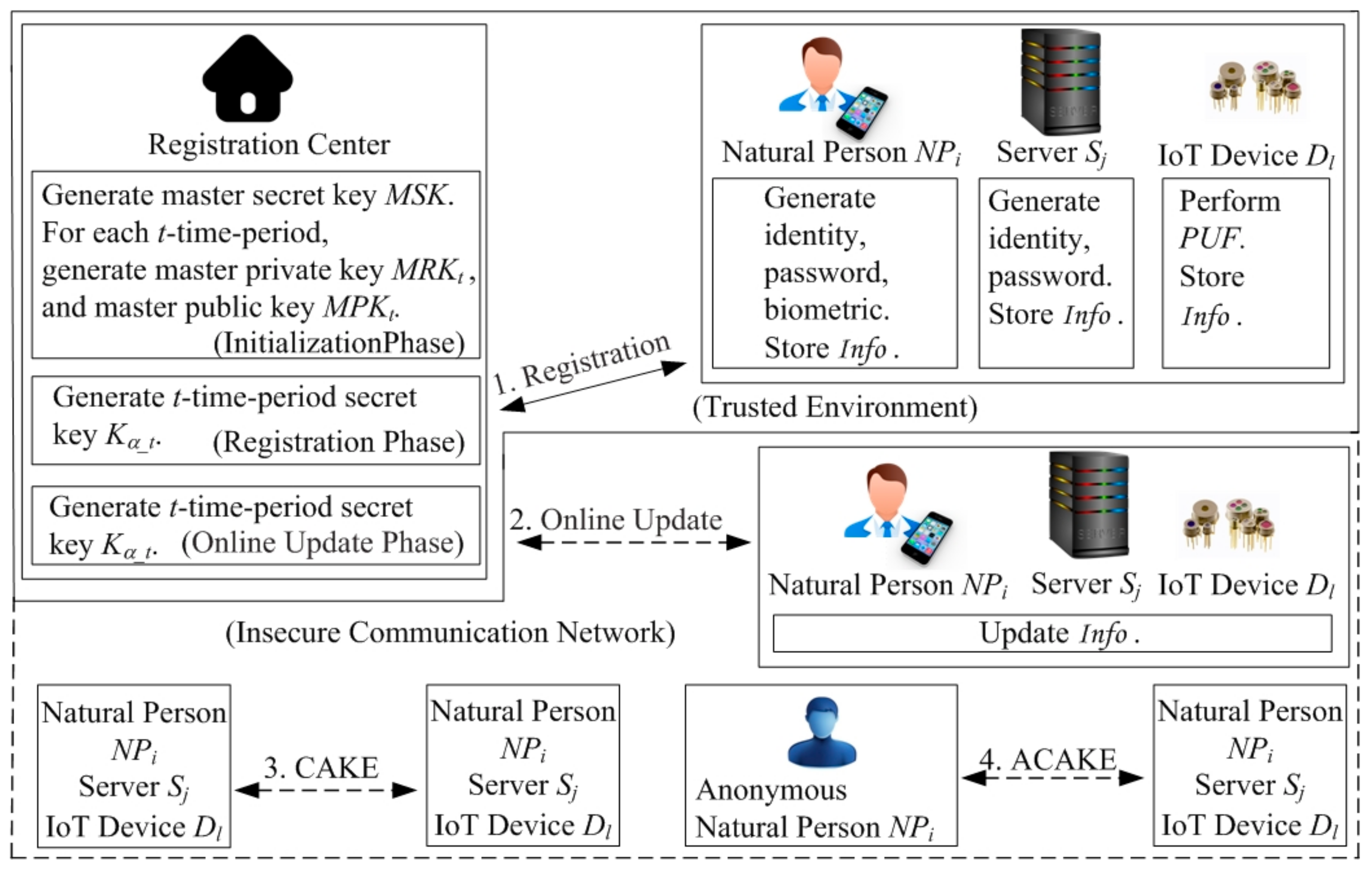
4. Proposed Protocols
4.1. Framework of CAKE and ACAKE Protocols
4.2. Proposed CAKE Protocol
4.2.1. Initialization Phase
4.2.2. Registration Phase: Natural Person
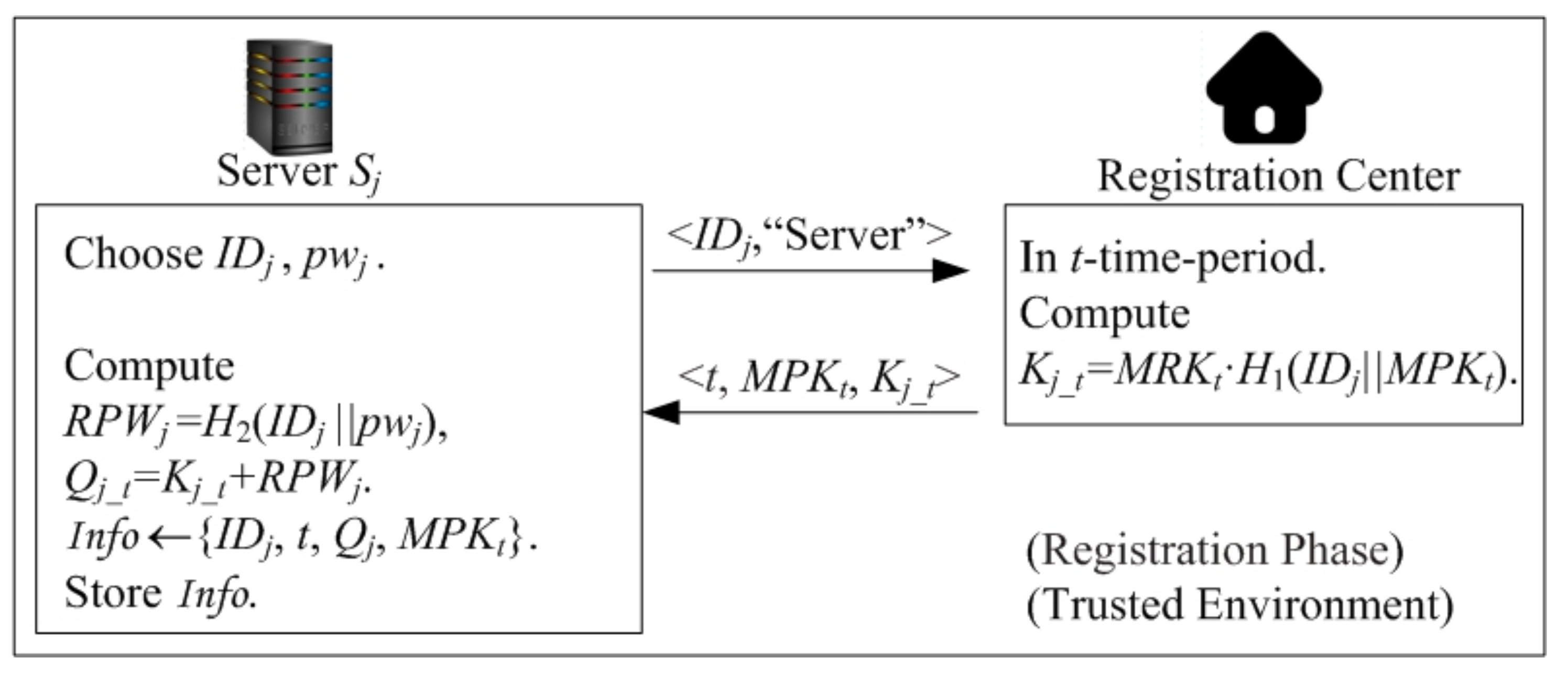
4.2.3. Registration Phase: Server
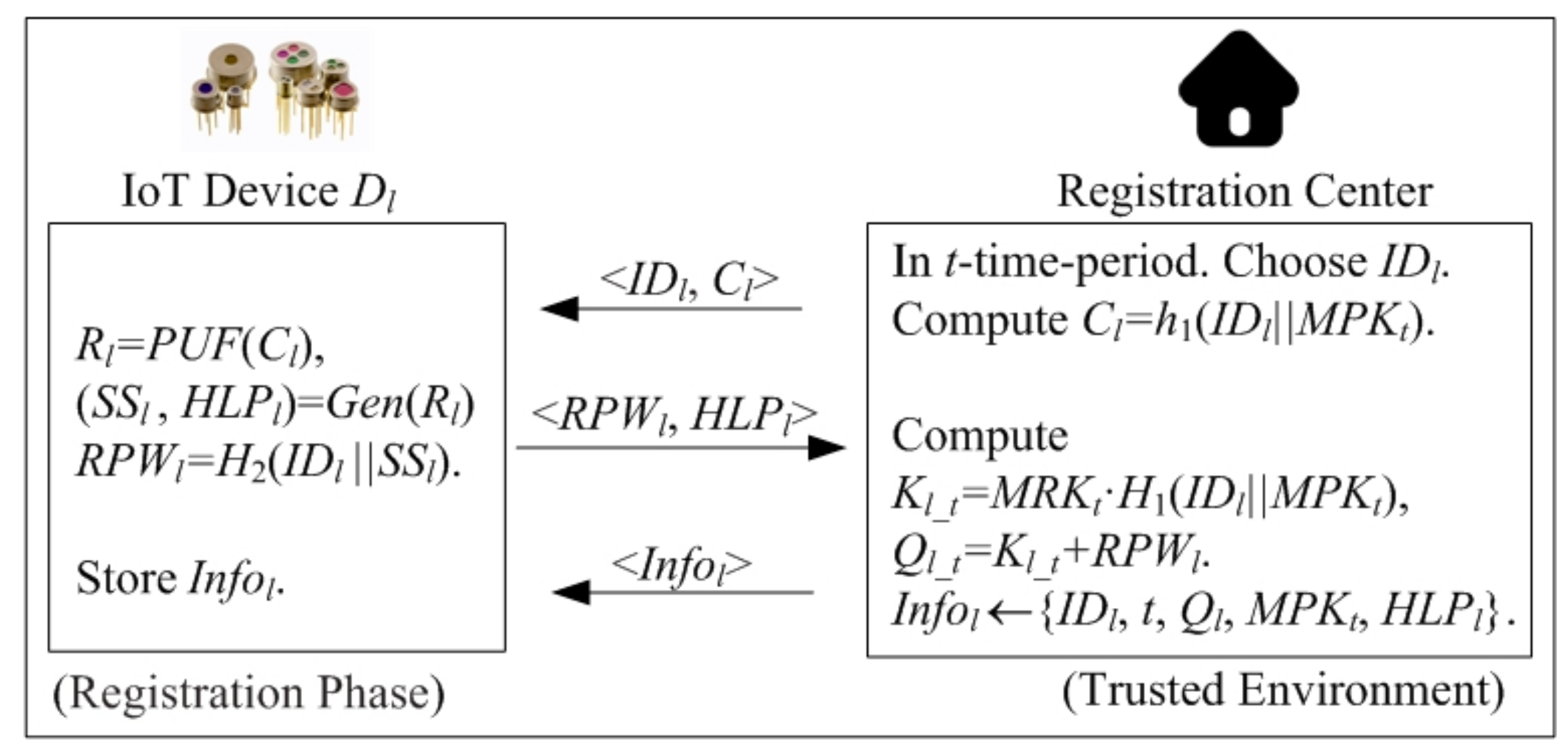
4.2.4. Registration Phase: IoT Device
4.2.5. GETKEY(A) Algorithm
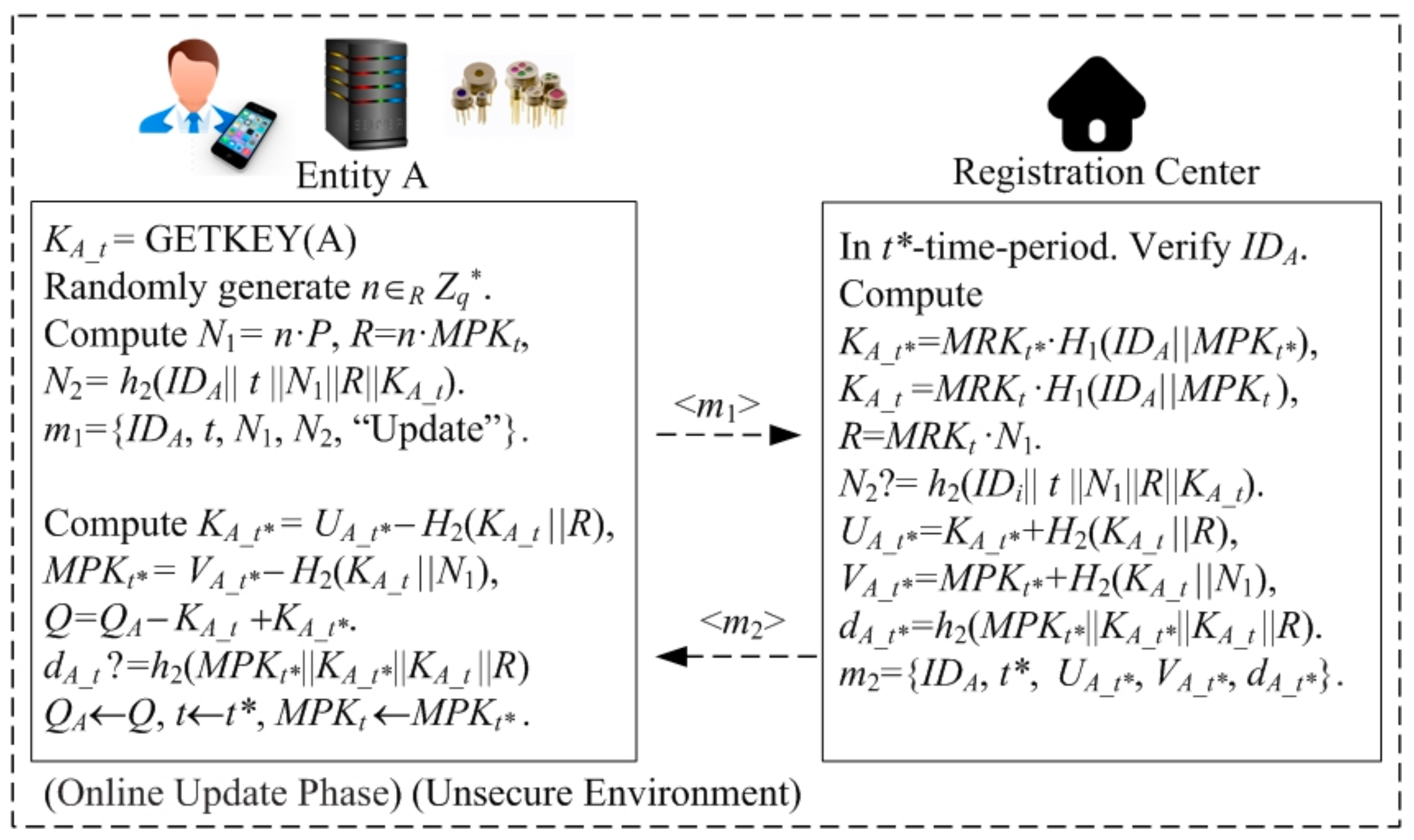
4.2.6. Online Update Phase
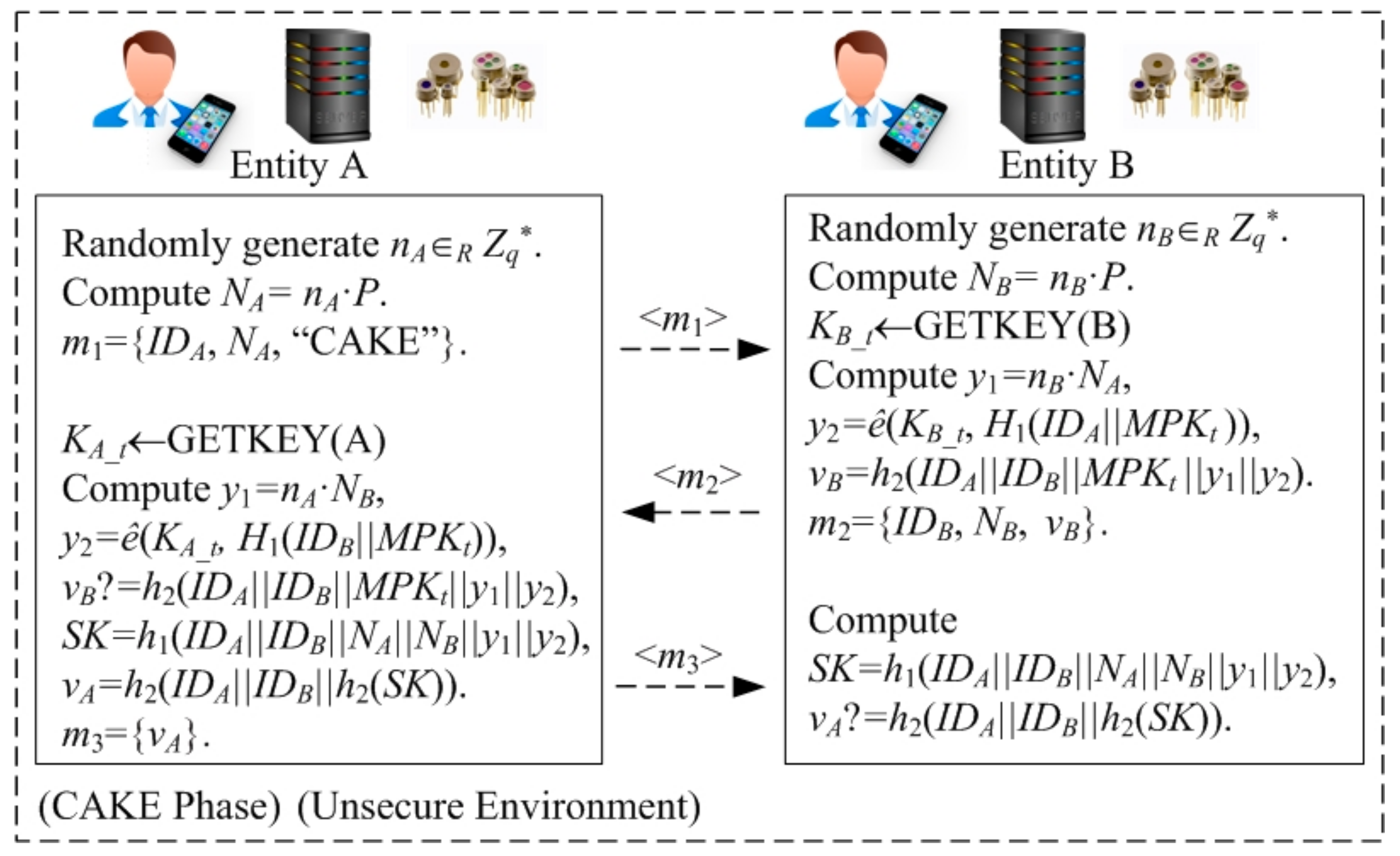
4.2.7. CAKE Phase
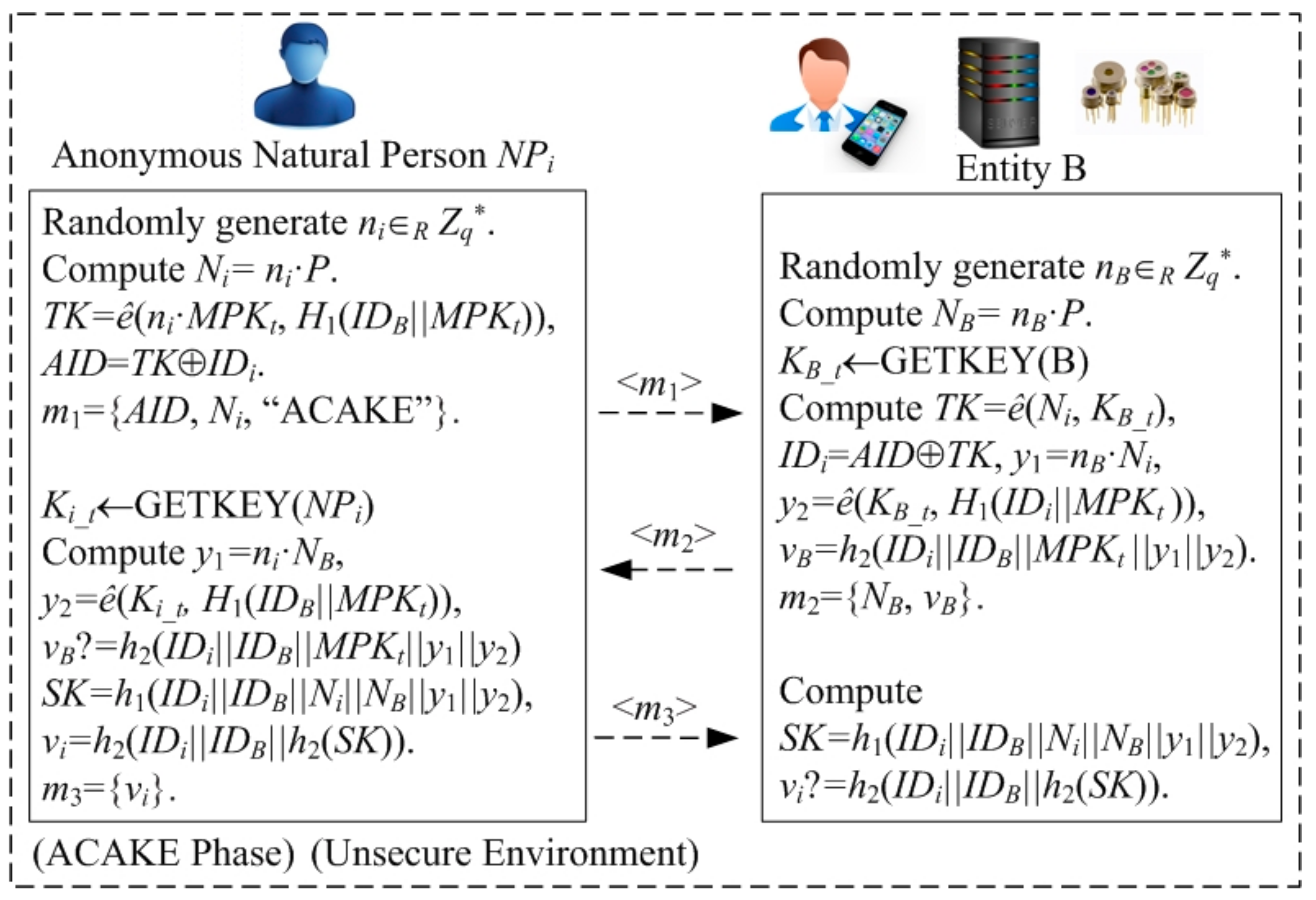
4.3. Proposed ACAKE Protocol
ACAKE phase
5. Security Analysis
5.1. Threat Assumptions
- AC1: Be an outsider or any one of the legitimate members [8].
- AC2: Eavesdrop, delete, replay, or modify any message transmitted over an untrustworthy channel [8].
- AC3: Offline, try all the (identity, password) pairs within probabilistic polynomial time [37].
- AC5: Fake the biometric [40].
- AC6: Correctly predict the PUF’s responses to arbitrary challenges with high probability [41].
- AC7: Individually obtain the (identity, password) pair, obtain the secret data in the smart card, fake the biometric, and correctly predict the PUF’s responses. However, breaking them all in polynomial time is not feasible.
5.2. Adversarial Model of CAKE Protocols
- Hash (M): B maintains a hash list to ensure the identical responses and avoid the collision. If Hash (M) has been asked before, then B returns the same response. Otherwise, B generates a random value h, appends (M, h) to the hash list, and returns h.
- Extract (α): This query can be asked for entity α, who is not one of the existing members. B executes the registration phase of the protocol and responds to the corresponding results. (AC1)
- Send (, M): B responds to the corresponding results, which should be responded to by α after α receives the message M, by executing the protocol. It models the active attack. (AC1) (AC2)
- Execute (, ): B returns the complete transcripts of an honest execution between entity α in its s-session and its partner . It models the passive attack. (AC2)
- Reveal (): If entity α has accepted a session key, say SK, in its s-session, then B returns SK. Otherwise, B returns “NULL”. It models the known session key attack.
- Corrupt (α): B returns the secret key of α, who is one of the existing members. (AC1) (AC3) (AC4) (AC5) (AC6)
- TestSK (): B flips an unbiased bit b ∈ {0,1}. If b = 1, then B returns the session key of entity α in its s-session. If b = 0, then B returns a random value.
5.3. Adversarial Model of ACAKE Protocols
- TestID (): B flips an unbiased bit b in {0, 1} and returns the real identity of entity α if b = 1. If b = 0, then a random value is returned.
- The system is set up according to the initialization and registration phases of the protocol.
- A may ask the following queries and obtain the corresponding results: Test, Hash, Execute, Send, Extract, Corrupt, and Reveal.
- There is no Corrupt (α) or Reveal () query asked before the Test () query.
5.4. Formal Proof
6. Comparisons and Performance Analysis
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
- Hash (M): B checks the hash lists and returns the corresponding value if it is in the list. Otherwise, B randomly generates r ∈ Zq* and m ∈ {0,1}l and returns the value by the following three different types of hash queries.
- HashH1 (M): Compute R = r·P, append (M, r, R) to list LH1, and return R.
- HashH2 (M): Compute R = r·P, append (M, r, R) to list LH2, and return R.
- Hashh1 (M): Append (M, m) to list Lh1 and return m.
- Hashh2 (M): Append (M, m) to list Lh2 and return m.
- GETKEY(A) algorithm: If A is NP, then it inputs IDA, pwA, and Bi, computes SSA = Rep(BA, HLPA), asks the Hashh1 query to obtain RPWA = H2(IDA||pwA||SSA), computes KA = QA − RPWA, and returns KA. If A is a server, then it inputs IDA and pwA, asks the HashH query to obtain RPWA = H2(IDA||pwA), computes KA_t = QA − RPWA, and returns KA. If A is an IoT, then A computes CA = h1(IDA||MPK), performs RA = PUF(CA), computes SSA = Rep(RA, HLPA), asks the Hashh1 query to obtain RPWA = H2(IDA||SSA), computes KA = QA − RPWA, and returns KA.
- Extract (α, M): If α is one of the members, then it returns “Reject”. Otherwise, it returns the corresponding registration parameters as follows. B checks the current time period t and list Lseed to obtain (t, st, MRKt, MPKt).
- M = <IDα, RPWα, “NP”>: B asks the HashH1 query to obtain H1(IDα||MPKt), computes Kα_t = MRKt·H1(IDα||MPKt) and Qα_t = Kα_t + RPWα, lets Info ←{IDα, t, Qα, MPKt}, and returns Info.
- M = <IDα, “Server”>: B asks the HashH1 query to obtain H1(IDα||MPKt), computes Kα_t = MRKt·H1(IDα||MPKt), and returns <t, MPKt, Kα_t>.
- M = <“IoT”>: B chooses IDα, asks the Hashh1 query to obtain Cα = h1(IDα||MPKt), returns <Cα>, and waits for the input <RPWα, HLPα>. B asks the HashH1 query to obtain H1(IDα||MPKt), computes Kα_t = MRKt·H1(IDα||MPKt) and Qα_t = Kα_t + RPWα, lets Info ←{ IDα, t, Qα, MPKt, HLPα}, and returns Info.
- Send (, M): There are three different types of Send query in the proposed protocols: Update, CAKE, and ACAKE. Assume that the current time is in t*-time period. B checks list Lseed to obtain (t*, st*, MRKt*, MPKt*) and responds according to the type of Send query.
- Send (RC, <IDA, t, N1, N2, “Update”>): B checks list Lseed to obtain (t, st, MRKt, MPKt), asks the HashH1 query to obtain H1(IDA||MPKt) and H1(IDA||MPKt*), and computes KA_t = MRKt·H1(IDA||MPKt), KA_t* = MRKt* ·H1(IDA||MPKt*), and R = MRKt·N1. B asks the HashH2 query to obtain H2(KA_t||R), computes UA_t* = KA_t* + H2(KA_t||R) and VA_t* = MPKt* + H2(KA_t||N1), and asks the Hashh2 query to obtain dA_t* = h2(MPKt*||KA_t*||KA_t||R). B then returns <IDA, t*, UA_t*, VA_t*, dA_t*>.
- Send (, <IDA, NA, “CAKE”>): B randomly generates nβ ∈ R Zq*, computes Nβ = nβ·P, conducts the GETKEY(β) algorithm to obtain Kβ_t, and computes y1 = nβ·NA. B asks the HashH1 query to obtain H1(IDA||MPKt), computes y2 = ê(Kβ_t, H1(IDA||MPKt)), and asks the Hashh2 query to obtain vβ = h2(IDA||IDβ||MPKt||y1||y2). B returns <IDβ, Nβ, vβ>.
- Send (, <AID, NA, “ACAKE”>): B randomly generates nβ ∈ R Zq*, computes Nβ = nβ·P, conducts the GETKEY(β) algorithm to obtain Kβ_t, and computes TK = ê(NA, Kβ_t), IDA = AID ⊕ TK, and y1 = nβ·NA. B asks the HashH1 query to obtain H1(IDA||MPKt), computes y2 = ê(Kβ_t, H1(IDA||MPKt)), and asks the Hashh2 query to obtain vβ = h2(IDA||IDβ||MPKt||y1||y2). B then returns <IDβ, Nβ, vβ>.
- Execute (, ): If . and , then B lets Nα = X, Nβ = Y, y1= NULL, and Tag = IDU||IDV||X||Y and randomly chooses vβ∈ R{0, 1}l. Otherwise, B randomly generates nα, nβ∈ R Zq* and computes Nα = nα·P, Nβ = nβ·P, and y1 = nβ·Nα. Suppose that the current time is in t-time period. B checks list Lseed to obtain (t, st, MRKt, MPKt).
- ExecuteUD (α, RC): B chooses tOLD-time period, lets N1 = Nα, computes R = nα·MPK(t OLD), asks the Hashh2 query to obtain N2 = h2(IDA||tOLD||N1||R||KA_(t OLD)), and asks the Send (RC, <IDα, tOLD, N1, N2, “Update”>) query to obtain <IDα, t, Uα_t, Vα_t, d_t>. B then returns <IDα, tOLD, N1, N2, “Update”> and <IDα, t, Uα_t, Vα_t, dα_t>.
- ExecuteCAKE (, ): B conducts the GETKEY(β) algorithm to obtain Kβ_t, asks the HashH query to obtain H(IDα||MPKt), and computes y2 = ê(Kβ_t, H1(IDα||MPKt)). If or , then B asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and asks the Hashh1 query to obtain SK = h1(IDα||IDβ||Nα||Nβ||y1||y2). B then asks the Hashh2 query to obtain h2(SK) and vα = h2(IDα||IDβ||h2(SK)) and returns <IDα, Nα, “CAKE”>, <IDβ, Nβ, vβ>, <vα>.
- ExecuteACAKE (, ): B computes TK = ê(nα·MPKt, H1(IDβ||MPKt)) and AID = TK ⊕ IDα. B conducts the GETKEY(β) algorithm to obtain Kβ_t, asks the HashH1 query to obtain H1(IDα||MPKt), and computes y2 = ê(Kβ_t, H1(IDα||MPKt)). If or , then B asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and asks the Hashh1 query to obtain SK = h1(IDα||IDβ||Nα||Nβ||y1||y2). B then asks the Hashh2 query to obtain vα = h2(IDα||IDβ||h2(SK)) and returns <AID, Nα, “ACAKE”>, <IDβ, Nβ, vβ>, and <vα>.
- Reveal (): If entity α has accepted a session key, say SK, in its s-session, then B returns SK. Otherwise, B returns “NULL”.
- Corrupt (α): If entity α is one of the system members, then B runs the same procedures as the Extract (α, M) query and returns the corresponding result.
- TestSK (): B flips an unbiased bit b ∈ {0,1}. B returns entityα’s real session key in its s-session if b = 1 and returns a random value if b = 0.
- TestID (): B flips an unbiased bit b ∈ {0,1}. B returns entityα’s real identity if b = 1 and returns a random value if b = 0.
- The Hash, Reveal, Corrupt, and Test queries are identical to those in the proof of Theorem 1.
- Extract (α, M): If α is one of the members, then it returns “Reject”. Otherwise, it returns the corresponding registration parameters as follows. B checks the current time period t and list Lseed to obtain (t, at, MPKt).
- M = <IDα, RPWα, “NP”>: B asks the HashH1 query for (IDα||MPKt), finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH to obtain r, and computes Kα_t = at·r·X. Note that Kα_t = MRKt·H1(IDα||MPKt) = at·r·X. B computes Qα_t = Kα_t + RPWα, lets Info ←{ IDα, t, Qα, MPKt}, and returns Info.
- M = <IDα, “Server”>: B asks the HashH1 query for (IDα||MPKt), finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH1 to obtain r, and computes Kα_t = at·r·X. B returns <t, MPKt, Kα_t>.
- M = <“IoT”>: B chooses IDα, asks the Hashh1 query to obtain Cα = h1(IDα||MPKt), returns <Cα>, and waits for the input <RPWα, HLPα>. B asks the HashH1 query for (IDα||MPKt), finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH1 to obtain r, computes Kα_t = at·r·X and Qα_t = Kα_t + PWl, lets Info←{ IDα, t, Qα, MPKt, HLPα}, and returns Info.
- Send (, M): There are three different types of Send query in the proposed protocols: Update, CAKE, and ACAKE. Assume that the current time is in t-time period. B checks list Lseed to obtain (t, at, MPKt) and responds according to the type of Send query.
- Send (RC, <IDα, tOLD, N1, N2, “Update”>): B checks list Lseed to obtain (tOLD, at OLD, MPKtOLD), asks the HashH1 query for (IDα||MPKt), and finds ((IDα||MPKt), rt, H1(IDα||MPKt)) and ((IDα||MPKtOLD), rtOLD, H1(IDα||MPKtOLD)) in LH1 to obtain rt and rtOLD. If α ∈ {U, V}, then B finds ((IDA||tOLD||N1||R||Kα_(tOLD)), N2) in list Lh2 to obtain R and Kα_(tOLD) and computes Kα_t = at·atOLD-1·rt·rtOLD-1·Kα_(tOLD). If α∉{U, V}, then B computes Kα_(tOLD) =at·rtOLD·X and Kα_t = at·rt·X. B then asks the HashH2 query to obtain H2(Kα_(tOLD)||R) and dα_t = H2(MPKt||Kα_t||Kα_(tOLD)||R), computes Uα_t = Kα_t + H2(Kα_(tOLD)||R) and Vα_t = MPKt + H2(Kα_(tOLD)||N1), and returns <IDα, t, Uα_t, Vα_t, dα_t>.
- Send (, <IDα, Nα, “CAKE”>): B randomly generates nβ ∈ R Zq*, computes Nβ = nβ·P and y1 = nβ·Nα, and asks the HashH query to obtain H1(IDα||MPKt) and H1(IDβ||MPKt). If α ∈ {U, V} and β ∈ {U, V}, then B randomly chooses y2 = g. If α ∉ {U, V} and β ∈ {U, V}, then B finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH1 to obtain r and computes Kα_t = at·r·X and y2 = ê(Kα_t, H1(IDβ||MPKt)). If β ∉ {U, V}, then B finds ((IDβ||MPKt), r, H1(IDβ||MPKt)) in LH1 to obtain r and computes Kβ_t = at·r·X and y2 = ê(Kβ_t, H1(IDα||MPKt)). B then asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and returns <IDβ, Nβ, vβ>.
- Send (, <AID, Nα, “ACAKE”>): B randomly generates nβ ∈ R Zq*, computes Nβ = nβ·P and y1 = nβ·Nα, and asks the HashH1 query to obtain H1(IDα||MPKt) and H1(IDβ||MPKt). If β ∈ {U, V}, then B randomly chooses y2 = g. If β ∉ {U, V}, then B finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH1 to obtain r and computes Kβ_t = at·r·X, TK = ê(Nα, Kβ_t), IDα = AID ⊕ TK, y2 = ê(Kβ_t, H1(IDα||MPKt)). B then asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and returns <Nβ, vβ>.
- Execute (, ): B asks the corresponding Sendquery to obtain the result and return it.
- The Hash, Reveal, Corrupt, and Test queries are identical to those in the proof of Theorem 1, and the Extract query is identical to that in the proof of Theorem 2.
- Send (, M): There are three different types of Send query in the proposed protocols: Update, CAKE, and ACAKE. Assume that the current time is in t-time period. B checks list Lseed to obtain (t, at, MPKt), asks the HashH query to obtain H1(IDβ||MPKt), finds ((IDβ||MPKt), rβ, H1(IDβ||MPKt)) in LH1 to obtain rβ, and responds according to the type of Send query.
- Send (RC, <IDα, tOLD, N1, N2, “Update”>): B checks list Lseed to obtain (tOLD, at OLD, MPKtOLD), asks the HashH query for (IDα||MPKt), and finds ((IDα||MPKt), rt, H1(IDα||MPKt)) and ((IDα||MPKtOLD), rtOLD, H1(IDα||MPKtOLD)) in LH1 to obtain rt and rtOLD. If α = U, then B finds ((IDA||tOLD||N1||R||Kα_(tOLD)), N2) in list Lh2 to obtain R and Kα_(tOLD) and computes Kα_t = at·atOLD-1·rt·rtOLD-1·Kα_(tOLD). If α ≠ U, then B computes Kα_(tOLD) = at·rtOLD·X and Kα_t = at·rt·X. B then asks the HashH2 query to obtain H2(Kα_(tOLD)||R), asks the Hashh2 query to obtain dα_t = h2(MPKt||Kα_t||Kα_(tOLD)||R), computes Uα_t = Kα_t + H2(Kα_(tOLD)||R) and Vα_t = MPKt + H2(Kα_(t OLD) ||N1), and returns <IDα, t, Uα_t, Vα_t, dα_t>.
- Send (, <IDα, Nα, “CAKE”>): B randomly generates nβR Zq*, computes Nβ = nβ·P and y1 = nβ·Nα, and asks the HashH query to obtain H(IDα||MPKt). If β ≠ U, then B computes Kβ_t = at·rβ·X and y2 = ê(Kβ_t, H1(IDα||MPKt)). If β = U, then B finds ((IDα||MPKt), r, H1(IDα||MPKt)) in LH1 to obtain r and computes Kα_t = at·r·X and y2 = ê(Kα_t, H1(IDβ||MPKt)). B then asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and returns <IDβ, Nβ, vβ>.
- Send (, <AID, Nα, “ACAKE”>): B randomly generates nβ ∈ R Zq* and computes Nβ = nβ·P and y1 = nβ·Nα. If β = U, then B randomly chooses vβ ∈ R{0, 1}l. If β≠U, then B computes Kβ_t = at·rβ·X, TK = ê(Nα, Kβ_t), and IDα = AID ⊕ TK, asks the HashH1 query to obtain H1(IDα||MPKt), computes y2 = ê(Kβ_t, H1(IDα||MPKt)), and asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2). B then returns <Nβ, vβ>.
- Execute (, ): Suppose that the current time is in t-time period. B checks list Lseed to obtain (t, at, MPKt). B asks the HashH1 query to obtain H1(IDα||MPKt) and H1(IDβ||MPKt) and finds ((IDα||MPKt), H1(IDα||MPKt), rα) and ((IDβ||MPKt), H1(IDβ||MPKt), rβ) in LH1 to obtain rα and rβ.
- ExecuteUD (α, RC): B chooses tOLD, checks list Lseed to obtain (tOLD, atOLD, MPKtOLD), randomly generates n ∈ R Zq*, and computes N1= n·P and R = n·MPKtOLD. If β = U, then B randomly chooses N2 ∈ R{0, 1}l. If β ≠ U, then B asks the Hashh2 query to obtain N2 = h2(IDA||tOLD||N1||R||atOLD·rα·X). B asks the Send (RC, <IDα, tOLD, N1, N2, “Update”>) query to obtain <IDα, t, Uα_t, Vα_t, dt>. B then returns <IDα, tOLD, Nα, “Update”> and <IDα, t, Uα_t, Vα_t, dα_t>.
- ExecuteCAKE (, ): There must be one out of α ≠ U and β ≠ U that is true. If α ≠ U, then B computes Kα_t = at·rα·X, asks the HashH1 query to obtain H1(IDβ||MPKt), and computes y2 = ê(Kα_t, H1(IDβ||MPKt)). If β≠U, then B computes Kβ_t = at·rβ·X, asks the HashH query to obtain H1(IDα||MPKt), and computes y2 = ê(Kβ_t, H1(IDα||MPKt)). B randomly generates nα, nβ ∈ R Zq* and computes Nα = nα·P, Nβ = nβ·P, and y1 = nα·nβ·P. B asks the Hashh1 query to obtain SK = h1(IDα||IDβ||Nα||Nβ||y1||y2) and asks the Hashh2 query to obtain h2(SK), vα = h2(IDα||IDβ||h2(SK)), vβ = h2(IDα||IDβ||MPKt||y1||y2).
- ExecuteACAKE (, ): If β = U, then B lets Nα = Z, TK = g. If β ≠ U, then B randomly generates nα ∈ R Zq* and computes Nα = nα·P and TK = ê(Nα, at·rβ·X). B computes AID= TK ⊕ IDU, randomly generates nβ ∈ R Zq* and computes Nβ = nβ·P, y1 = nβ·NU, and y2= ê(at·rα·X, H1(IDβ||MPKt)). B asks the Hashh2 query to obtain vβ = h2(IDα||IDβ||MPKt||y1||y2) and asks the Hashh1 query to obtain SK = h1(IDα||IDβ||NU||Nβ||y1||y2). B then asks the Hashh2 query to obtain vα = h2(IDα||IDβ||h2(SK)) and returns {<AID, NU, “ACAKE”>, <Nβ, vβ>, <vα>}.
References
- Alam, T. A reliable communication framework and its use in Internet of Things (IoT). Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 2, 450–456. [Google Scholar]
- Agiwal, M.; Roy, A. Next generation 5G wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 1617–1655. [Google Scholar] [CrossRef]
- Borkar, S.; Pande, H. Application of 5G next generation network to Internet of Things. In Proceedings of the IoT and Applications (IOTA), Pune, India, 22–24 January 2016; pp. 443–447. [Google Scholar]
- Raol, S.K.; Prasad, R. Impact of 5G technologies on smart city implementation. Wirel. Pers. Commun. 2018, 100, 161–176. [Google Scholar]
- Cia, M.D.; Mason, F.; Peron, D.; Chiariotti, F. Using smart city data in 5G self-organizing networks. IEEE IoT 2019, 5, 645–654. [Google Scholar]
- Tiburski, R.T.; Amaral, L.A.; Hessel, F. Security challenges in 5G-Based IoT middleware systems. In Internet of Things (IoT) in 5G Mobile Technologies; Springer: Cham, Switzerland, 2016; pp. 399–418. [Google Scholar]
- Chuang, Y.H.; Lei, C.L.; Shiu, H.J. Cryptanalysis of four biometric based authentication schemes with privacy-preserving for multi-server environment and design guideline. In Proceedings of the 15th Asia Joint Conference on Information Security (AsiaJCIS), Taipei, Taiwan, 20–21 August 2020; pp. 66–73. [Google Scholar]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Wang, W.; Chen, Y.; Zhang, Q. Privacy-preserving location authentication in Wi-Fi networks using fine-grained physical layer signature. IEEE Trans. Wirel. Commun. 2016, 15, 1218–1225. [Google Scholar] [CrossRef]
- Chuang, Y.H.; Lei, C.L. An independent three-factor mutual authentication and key agreement scheme with privacy preserving for multiserver environment and a survey. Int. J. Commun. Syst. 2021, 34, e4660. [Google Scholar]
- Li, X.; Sangaiah, A.K.; Kumari, S.; Wu, F.; Shen, J.; Khan, M.K. An efficient authentication and key agreement scheme with user anonymity for roaming service in smart city. Pers. Ubiquit Comput. 2017, 21, 791–805. [Google Scholar] [CrossRef]
- Li, J.L.; Zhang, W.G.; Dabra, V.; Choo, K.K.R.; Kumari, S.; Hogrefe, D. AEP-PPA: An anonymous, efficient and provably-secure privacy- preserving authentication protocol for mobile services in smart cities. J. Netw. Comput. Appl. 2019, 134, 52–61. [Google Scholar] [CrossRef]
- Reddy, A.G.; Suresh, D.; Phaneendra, K.; Shin, J.S.; Odelude, V. Provably secure pseudo-identity based device authentication for smart cities environment. Sustain. Cities Soc. 2018, 41, 878–885. [Google Scholar] [CrossRef]
- Xie, Q.; Hwang, L. Security enhancement of an anonymous roaming authentication scheme with two-factor security in smart city. Neurocomputing 2019, 347, 131–138. [Google Scholar] [CrossRef]
- Jegadeesan, S.; Azees, M.; Kumar, P.M.; Manogaran, G.; Chilamkurti, N.; Varatharajan, R.; Hsu, C.H. An efficient anonymous mutual authentication technique for providing secure communication in mobile cloud computing for smart city applications. Sustain. Cities Soc. 2019, 49, 101522. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Chaudhry, S.A.; Barnawi, A.; Al-Barakati, A.; Alsharif, M.H. A privacy preserving authentication scheme for roaming in IoT-based wireless mobile networks. Symmetry 2020, 12, 287. [Google Scholar] [CrossRef] [Green Version]
- Chuang, Y.H.; Tseng, Y.M.; Lei, C.L. Efficient mutual authentication and key agreement with user anonymity for roaming services in global mobility networks. Int. J. Innov. Comput. Inf. Control 2012, 8, 6415–6428. [Google Scholar]
- Tseng, Y.M.; Huang, S.S.; You, M.L. Strongly secure ID-based authenticated key agreement protocol for mobile multi-server environments. Int. J. Commun. Syst. 2017, 30, e3251. [Google Scholar] [CrossRef]
- Yu, Y.; Hu, L.; Chu, J. A secure authentication and key agreement scheme for IoT-based cloud computing environment. Symmetry 2020, 12, 150. [Google Scholar] [CrossRef] [Green Version]
- Chuang, Y.H.; Tseng, Y.M. Towards generalized ID-based user authentication for mobile multi-server environment. Int. J. Commun. Syst. 2012, 25, 447–460. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Huang, S.S.; Tsai, T.T.; Ke, J.H. List-free ID-based mutual authentication and key agreement protocol for multi-server architectures. IEEE Trans. Emerg. Top. Comput. 2016, 4, 102–122. [Google Scholar] [CrossRef]
- Chuang, Y.H.; Lei, C.L. Privacy protection for telecare medicine information systems with multiple servers using a biometric-based authenticated key agreement scheme. IEEE Access 2019, 7, 186480–186490. [Google Scholar]
- Odelu, V.; Das, A.K.; Goswami, A. A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Park, Y.; Park, Y. Three-Factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef]
- Qi, M.; Chen, Y. A secure biometrics-based authentication key exchange protocol for multi-server TMIS using ECC. Comput. Meth. Prog. Bio. 2018, 164, 101–109. [Google Scholar] [CrossRef]
- Mukhopadhyay, D. PUFs as promising tools for security in internet of things. IEEE Des. Test. 2016, 33, 103–115. [Google Scholar] [CrossRef]
- Tuyls, P.; Skoric, B. Secret key generation from classical physics: Physical uncloneable functions. Amiware Hardw. Technol. Driv. Ambient Intell. 2006, 5, 421–447. [Google Scholar]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 8, 1126–1141. [Google Scholar] [CrossRef]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. Siam J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef] [Green Version]
- Kang, H.; Hori, Y.; Katashita, T.; Hagiwara, M.; Iwamura, K. Cryptographie key generation from PUF data using efficient fuzzy extractors. In Proceedings of the 16th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 16–19 February 2014; pp. 23–26. [Google Scholar]
- Delvaux, J.; Gu, D.; Verbauwhede, I.; Hiller, M.; Yu, M.M. Efficient fuzzy extraction of PUF-induced secrets: Theory and applications. In Proceedings of the 18th International Conference on Cryptographic Hardware and Embedded Systems (CHES), Santa Barbara, CA, USA, 17–19 August 2016; pp. 412–431. [Google Scholar]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans. Dependable Secur. Comput. 2019, 16, 424–437. [Google Scholar] [CrossRef]
- Choi, K.Y.; Hwang, J.Y.; Lee, D.H.; Seo, I.S. ID-based authenticated key agreement for low-power mobile devices. In Proceedings of the 10th Information Security and Privacy (ACISP), Brisbane, Australia, 4–6 July 2005; Volume 3574, pp. 494–505. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the 21th Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 14–16 August 2001; Volume 2139, pp. 213–229. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef] [Green Version]
- Choi, K.Y.; Hwang, J.Y.; Lee, D.H. Efficient ID-based group key agreement with bilinear maps. In Proceedings of the Public Key Cryptography (PKC), Singapore, 1–4 March 2004; Volume 2947, pp. 130–144. [Google Scholar]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the 19th Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 19–23 August 1999; pp. 388–397. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef] [Green Version]
- Rane, S.; Wang, Y.; Draper, S.C.; Ishwar, P. Secure biometrics: Concepts, authentication architectures, and challenges. IEEE Signal. Process. Mag. 2013, 30, 51–64. [Google Scholar] [CrossRef] [Green Version]
- Rührmair, U.; Sölter, J.; Sehnke, F.; Xu, X.; Mahmoud, A.; Stoyanova, V.; Dror, G.; Schmidhuber, J.; Burleson, W.; Devadas, S. PUF modeling attacks on simulated and silicon data. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1876–1891. [Google Scholar] [CrossRef] [Green Version]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security (CCS), Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Scott, M.; Costigan, N.; Abdulwahab, W. Implementing cryptographic pairings on smartcards. In Proceedings of the Cryptographic Hardware and Embedded Systems (CHES), Yokohama, Japan, 10–13 October 2006; Volume 4249, pp. 134–147. [Google Scholar]
- Cao, X.; Zeng, X.; Kou, W.; Hu, L. Identity-based anonymous remote authentication for value-added services in mobile networks. IEEE Trans. Veh. Technol. 2009, 58, 3508–3517. [Google Scholar] [CrossRef]
- Xiong, H.; Qin, Z. Revocable and scalable certificateless remote authentication protocol with anonymity for wireless body area networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1442–1455. [Google Scholar] [CrossRef]
- Cavalieri, S.; Cutuli, G. Implementing encryption and authentication in KNX using Diffie-Hellman and AES algorithms. In Proceedings of the 35th Annual Conference of IEEE Industrial Electronics, Porto, Portugal, 3–5 November 2009; pp. 2459–2464. [Google Scholar]

| Symbol | Meaning | Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|---|---|
| RC | Registration center | MSK | Master secret key | IDα | Identity of member α |
| NPi | i-th natural person | MRK | Master private key | pwα | Password of member α |
| Sj | j-th server | MPK | Master public key | Bi | Biometric of NPi |
| Dl | l-th IoT device | t | Index of time period | SK | Session key |
| CA/RA | Challenge/response string of PUF function | Gen/Rep | Generation/reproduction procedure of fuzzy extractor | Kα_t | Secret key of member α in t-time period |
| SSi/HLPi | Secret/helper string | || | Concatenation operation | ⊕ | XOR operation |
| [11] | [12] | [13] | [14] | [15] | [16] | [17] | [18] | [19] | [20] | [21] | [22] | [23] | [24] | [25] | Our ACAKE | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Compatible authentication | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | Y |
| Multi-factor authentication a | N | N | N | N | N | N | N | N | N | N | N | Y | Y | Y | Y | Y |
| Multi-server environment b | N | N | N | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| Independent authentication c | N | Y | Y | N | Y | N | N | Y | Y | Y | Y | Y | N | N | N | Y |
| User anonymity | Y | Y | Y | Y | Y | Y | Y | N | Y | Y | N | Y | Y | Y | Y | Y |
| User untraceability/unlinkability | Y | Y | Y | Y | Y | Y | Y | N | Y | N | N | Y | Y | Y | Y | Y |
| Entity revocation | N | N | N | N | N | N | Y | N | N | Y | Y | N | Y d | N | N | Y |
| IoT Device | Natural Person | Server | RC | ||
|---|---|---|---|---|---|
| (36-MHz) [43] | (206-MHz) [44] | (624-MHz) [45] | (3 GHz) [44] | ||
| TGê | 290 | 291.84 (estimated) | 96.2 | 20.04 | |
| TGmul | 270 | 92.91 | 30.67 | 6.38 | |
| TH | 253 (estimated) | 44.27 | 14.62 (estimated) | 3.04 | |
| Executing updating | 1299 | 318.63 | 105.2 | 21.88 | 31.3 |
| Executing CAKE | 1336 | 566.2 | 186.78 | 38.88 | - |
| Executing ACAKE | 1896 | 950.95 | 313.65 | 65.3 | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chuang, Y.-H.; Tseng, Y.-M. CAKE: Compatible Authentication and Key Exchange Protocol for a Smart City in 5G Networks. Symmetry 2021, 13, 698. https://doi.org/10.3390/sym13040698
Chuang Y-H, Tseng Y-M. CAKE: Compatible Authentication and Key Exchange Protocol for a Smart City in 5G Networks. Symmetry. 2021; 13(4):698. https://doi.org/10.3390/sym13040698
Chicago/Turabian StyleChuang, Yun-Hsin, and Yuh-Min Tseng. 2021. "CAKE: Compatible Authentication and Key Exchange Protocol for a Smart City in 5G Networks" Symmetry 13, no. 4: 698. https://doi.org/10.3390/sym13040698





