Implementing an Efficient Secure Attribute-Based Encryption System for IoV Using Association Rules
Abstract
:1. Introduction
- (1)
- First, we collect the ECUs communication list of a company. Through the max-miner association rules algorithm, the frequency features are mined between vehicle nodes. The ECU whose communication frequency reaches the threshold value is grouped into one category and regarded as having the same frequency attribute. We find that this part filter unnecessary communications, laying the foundation for the implementation of the ABE pre-isolation system.
- (2)
- Second, we propose an improved attribute-based encryption algorithm to build an attribute isolation architecture of the in-vehicle network after getting the frequency sets. This architecture only allows ECU with the same frequency attribute to communicate, thus reducing the load on the bus while isolating ECU nodes that do not need to communicate. Most importantly, it improves the security of automotive node communication.
- (3)
- Third, we analyze the communication architecture security. Through the performance evaluation based on hardware is performed, as well as the simulation based on vehicle network simulator (IVNS), the results of security analysis and evaluation show that the architecture meets the security and real-time requirements of the in-vehicle network.
2. Related Work
3. ECU Frequency Attribute Classification
3.1. Data Pre-Processing
3.2. Communications Frequency Correlation Analysis
| Algorithm 1 Max-Miner. |
| 1: Input: Data T |
| 2: Output: Maximal frequent item sets |
| 3: Set of Candidate Group C ← {Frequent 1- item sets} |
| 4: Set of Itemset F ← {Frequent 1- item sets} |
| 5: While C is non-empty do |
| 6: Scan T to count the frequency of all candidate groups in C |
| 7: For each such that is frequent do |
| 8: F ← |
| 9: For each such that is infrequent do |
| 10: C ← |
| 11: Remove from F any itemset with a proper superset in F |
| 12: Remove from C any group g such that has a superset in F |
| 13: Return F |
3.3. Results of Clustering
4. Communication Architecture
4.1. System Initialization
- The GECU inputs the security parameter , generate an additive group G and a multiplicative with prime order is a generator in G. Define a bilinear mapping .
- It can be seen from the above that there are a total of six group labels for ECUs, GECU randomly selects six number for group labels and marks them as in .
- The GECU randomly picks , and publishes the public parameters are:. Meanwhile, the master key is .
4.2. Registration
4.2.1. ECU Sends Registration Request Information to GECU
- randomly chooses to generate the request information .
- signs the request information to obtain the signature information .
- sends to GECU.
4.2.2. GECU Verifies ECU Identity
- The GECU verifies the validity of the timestamp by Formula (1). The maximum time difference allowed by the in-vehicle network is T, the current time is .
- If the timestamp is valid, the GECU confirms the integrity and validity of by verifying the signature and certificate of the .
- After verify the legal identity of , the GECU randomly choose to generate response information , and a signature on response information.
- The GECU generates a temporal session key , and uses SK to encrypt master key .
- The GECU sends to .
4.2.3. GECU Sends MK to ECU
- verifies the validity of the timestamp by Formula (2). The maximum time difference allowed by the in-vehicle network is T, the current time is .
- If the timestamp is valid, confirms the integrity and validity of GECU by verifying the signature and certificate of the .
- After verify the legal identity of GECU, decrypts in by and obtains .
Algorithm 2 ECU Registration Protocol. 1: : Generate the registration request information 2: 3: GECU: 4: if 5: if is legal 6: : 7: else 8: Refuse the request information 9: endif 10: 11: if 12: if GECU is legal 13: decrypt in by and obtains 14: else 15: Execute the registration protocol again 16: endif
4.3. Setting the Matching Strategy
4.4. Isolated Communication
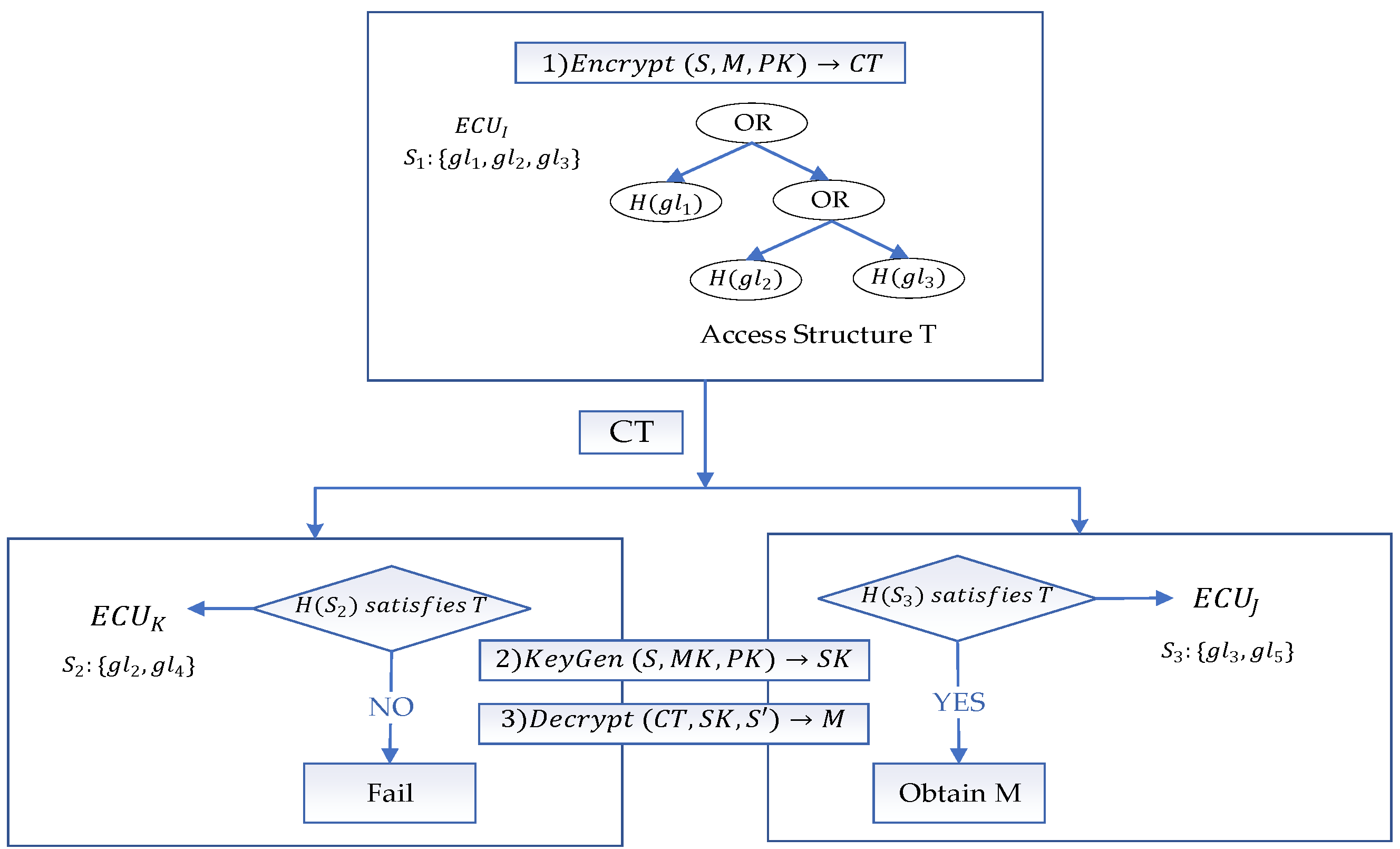
- : generates the ciphertext CT according to the encrypt algorithm. The encrypt algorithm takes frequency attribute set of , a message M and the public parameters PK as input. picks up a random value , where s is secret value. We denote the number of elements in set S as n. randomly picks up n elements for and set ,. For , the algorithm computes ,, and hashes the value of the in and construct an access structure tree T as shown in Figure 7. The ciphertext .
- : generates key SK according to the keygen algorithm. The keygen algorithm takes frequency attribute set of , the master key MK and the public parameters PK as input. denotes the number of elements in is m, and randomly picks up m elements for . randomly chooses and computes ,. For , the algorithm computes and . The secret key . The steps for are the same as for .
- : decrypts the ciphertext CT according to the decrypt algorithm. The decrypt algorithm takes the frequency attribute set of , the ciphertext CT and secret key SK as input. computes the hash value of the elements in the set and denotes it as the set . The algorithm chooses for , which the hash value matches the T. computes as follows:
5. Security Analysis of the Proposed Scheme111
6. Simulation and Evaluation
6.1. Hardware-Based Performance Evaluation
6.2. Network Simulator-Based Evaluation
6.2.1. Analysis of Calculation Time Consumption
- (1)
- Sender-ECU encrypts data frames based on the set of frequency attributes.
- (2)
- Sender-ECU broadcasts the ciphertext and access structure tree T on the network.
- (3)
- Receiver-ECU receives ciphertext and access structure tree T.
- (4)
- If the frequency attributes set of receiver-ECU meets the requirements of the access structure tree T, decryption will be carried out and plaintext will be obtained. Otherwise, decryption fails.
6.2.2. Analysis of Bus Load Rate
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| Prefix of node g | |
| Suffix of node g | |
| Parent node of g | |
| Child node of g | |
| The I-th ECU | |
| Identity of | |
| Signature of | |
| Certificate of | |
| Temporal session key | |
| S | Set of frequency attributes of ECU |
| The i-th frequency attribute |
References
- Trubia, S.; Severino, A.; Curto, S.; Arena, F.; Pau, G. Smart Roads: An Overview of What Future Mobility Will Look Like. Infrastructures 2020, 5, 107. [Google Scholar] [CrossRef]
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.; Liu, X. Internet of Vehicles: Motivation, Layered Architecture, Network Model, Challenges, and Future Aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Han, M.; Cheng, P.; Ma, S. PPM-InVIDS: Privacy Protection Model for In-Vehicle Intrusion Detection System Based Complex-Valued Neural Network. Veh. Commun. 2021, 100374. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Kim, J.H.; Seo, S.; Hai, N.; Cheon, B.M.; Lee, Y.S.; Jeon, J.W. Gateway Framework for In-Vehicle Networks Based on CAN, FlexRay, and Ethernet. IEEE Trans. Veh. Technol. 2015, 64, 4472–4486. [Google Scholar] [CrossRef]
- Miller, C.; Valasek, C.J.B.H.U. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 2015, S91. [Google Scholar]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Radu, A.-I.; Garcia, F.D. LeiA: A Lightweight Authentication Protocol for CAN. In Proceedings of the Computer Security—ESORICS 2016, Heraklion, Greece, 26–30 September 2016; pp. 283–300. [Google Scholar]
- Dariz, L.; Selvatici, M.; Ruggeri, M.; Costantino, G.; Martinelli, F. Trade-off analysis of safety and security in CAN bus communication. In Proceedings of the 2017 5th IEEE International Conference on Models and Technologies for Intelligent Transportation Systems (MT-ITS), Naples, Italy, 26–28 June 2017; pp. 226–231. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ‘07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Li, J.; Zhang, Y.; Ning, J.; Huang, X.; Poh, G.S.; Wang, D. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT. IEEE Trans. Cloud Comput. 2020, 1. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Larson, U.E.; Jonsson, E. Efficient In-Vehicle Delayed Data Authentication Based on Compound Message Authentication Codes. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, AB, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Hartwich, F. CAN with flexible data-rate. In Proceedings of the Proc. iCC, Palatinate, Germany, 5 March 2012; pp. 1–9. [Google Scholar]
- Patsakis, C.; Dellios, K.; Bouroche, M. Towards a distributed secure in-vehicle communication architecture for modern vehicles. Comput. Secur. 2014, 40, 60–74. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Kim, I.S.; Lee, D.H. A Practical Security Architecture for In-Vehicle CAN-FD. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2248–2261. [Google Scholar] [CrossRef]
- Han, M.; Wan, A.; Zhang, F.; Ma, S. An Attribute-Isolated Secure Communication Architecture for Intelligent Connected Vehicles. IEEE Trans. Intell. Veh. 2020, 5, 545–555. [Google Scholar] [CrossRef]
- Agrawal, M.; Huang, T.; Zhou, J.; Chang, D. CAN-FD-Sec: Improving Security of CAN-FD Protocol. In Proceedings of the Security and Safety Interplay of Intelligent Software Systems, Barcelona, Spain, 6–7 September 2019; pp. 77–93. [Google Scholar]
- Groza, B.; Murvay, S.; Van Herrewege, A.; Verbauwhede, I. LiBrA-CAN: Lightweight Broadcast Authentication for Controller Area Networks. ACM Trans. Embed. Comput. Syst. 2017, 16, 28. [Google Scholar] [CrossRef] [Green Version]
- Dhanaseelan, R.; Jeya Sutha, M. Diagnosis of coronary artery disease using an efficient hash table based closed frequent itemsets mining. Med. Biol. Eng. Comput. 2018, 56, 749–759. [Google Scholar] [CrossRef] [PubMed]
- Tran, T.; Vo, B.; Le, T.T.N.; Nguyen, N.T. Text Clustering Using Frequent Weighted Utility Itemsets. Cybern. Syst. 2017, 48, 193–209. [Google Scholar] [CrossRef]
- Burdick, D.; Calimlim, M.; Flannick, J.; Gehrke, J.; Yiu, T. MAFIA: A maximal frequent itemset algorithm. IEEE Trans. Knowl. Data Eng. 2005, 17, 1490–1504. [Google Scholar] [CrossRef]
- Bayardo Jr, R.J. Efficiently mining long patterns from databases. In Proceedings of the ACM SIGMOD International Conference on Management of Data, Seattle, WA, USA, 1–4 June 1998; pp. 85–93. [Google Scholar]
- Lex, A.; Gehlenborg, N.; Strobelt, H.; Vuillemot, R.; Pfister, H. UpSet: Visualization of Intersecting Sets. IEEE Trans. Vis. Comput. Graph. 2014, 20, 1983–1992. [Google Scholar] [CrossRef] [PubMed]
- Mundhenk, P.; Mrowca, A.; Steinhorst, S.; Lukasiewycz, M.; Fahmy, S.A.; Chakraborty, S. Open source model and simulator for real-time performance analysis of automotive network security. ACM Sig. Rev. 2016, 13, 8–13. [Google Scholar] [CrossRef] [Green Version]










| ID | EMS | TCU | GSM | ICU | ESP | …… |
|---|---|---|---|---|---|---|
| FB | T | R | R | |||
| 1A1 | R | T | ||||
| 1A3 | R | T | R | |||
| 431 | R | T | ||||
| 211 | R | R | T | |||
| …… | ||||||
| Tools | Remarks |
|---|---|
| Hardware | STM32H743, STM32H743IIT6 |
| Compiler | MDK5 |
| Software | IVNS |
| CPU | Intel core i5-8259U 1.6 GHz |
| RAM | 8GB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, M.; Zhu, M.; Cheng, P.; Yin, Z.; Qu, H. Implementing an Efficient Secure Attribute-Based Encryption System for IoV Using Association Rules. Symmetry 2021, 13, 1177. https://doi.org/10.3390/sym13071177
Han M, Zhu M, Cheng P, Yin Z, Qu H. Implementing an Efficient Secure Attribute-Based Encryption System for IoV Using Association Rules. Symmetry. 2021; 13(7):1177. https://doi.org/10.3390/sym13071177
Chicago/Turabian StyleHan, Mu, Mengli Zhu, Pengzhou Cheng, Zhikun Yin, and Haixin Qu. 2021. "Implementing an Efficient Secure Attribute-Based Encryption System for IoV Using Association Rules" Symmetry 13, no. 7: 1177. https://doi.org/10.3390/sym13071177





