Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research
Abstract
:1. Introduction
Contribution of This Survey
- Provide a background for steganography and steganalysis in general;
- Classify the steganalysis techniques based on different aspects;
- Deep review for the recent state-of-the-art in steganalysis;
- Provide a comprehensive overview for new interested researchers in steganalysis.
2. Steganography: An Overview
2.1. Steganography Categories
2.1.1. Pure Steganography
2.1.2. Secret Key Steganography
2.1.3. Public Key Steganography
2.2. Steganography Techniques
2.2.1. Spatial Domain
2.2.2. Transform Domain
2.2.3. Vector Domain
2.2.4. Entropy Coding Domain
2.2.5. Adaptive Domain
2.2.6. Distortion Domain
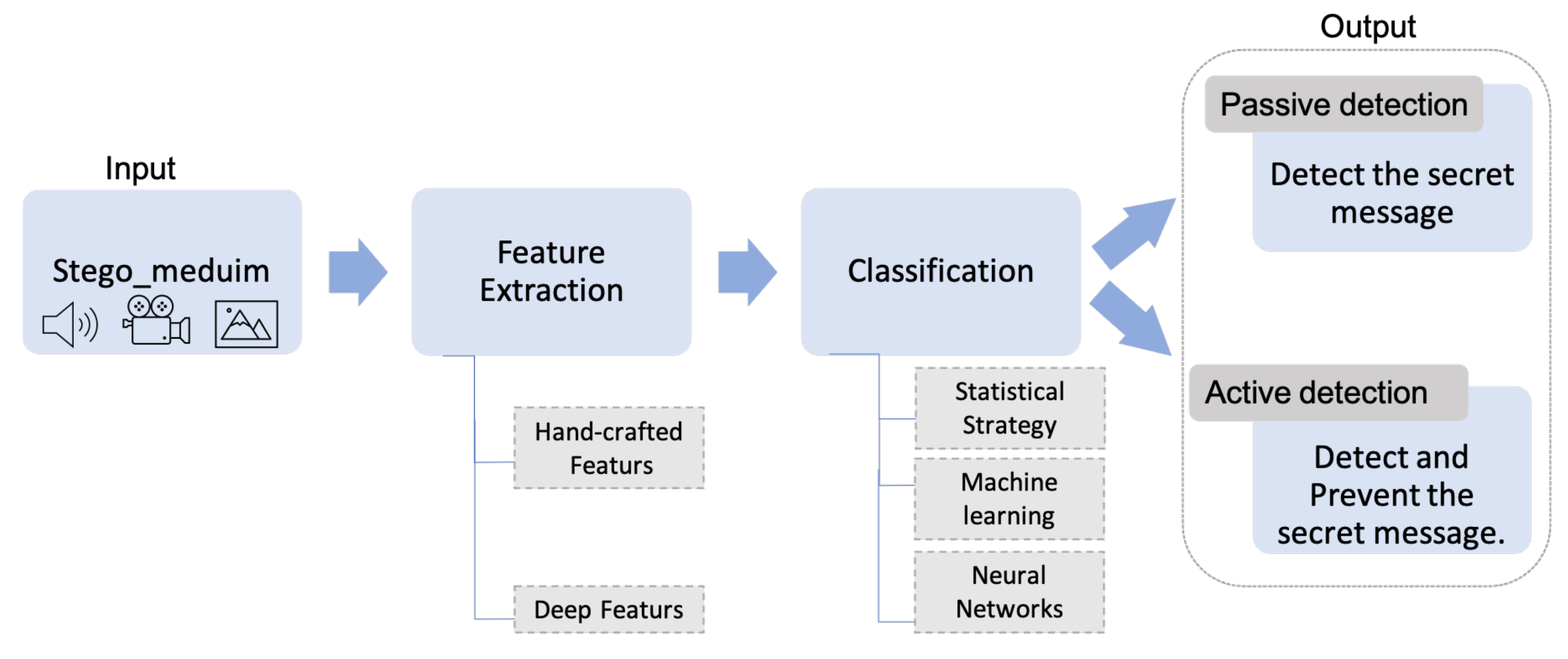
3. Steganalysis: A Common Scheme
3.1. Feature Extraction
3.1.1. Signature Steganalysis
3.1.2. Statistical Steganalysis
3.1.3. Deep Steganalysis
3.2. Classification
3.2.1. Statistical Strategy-Based Techniques
3.2.2. Machine Learning-Based Techniques
3.2.3. Deep Learning-Based Techniques
4. Literature Review
4.1. Audio Steganalysis
4.2. Image Steganalysis
4.3. Video Steganalysis
5. Databases
6. Evaluation metrics
- tp: stego-media classified as stego-media
- tn: cover-media classified as cover-media
- fp: stego-media classified as cover-media
- fn: cover-media classified as stego-media
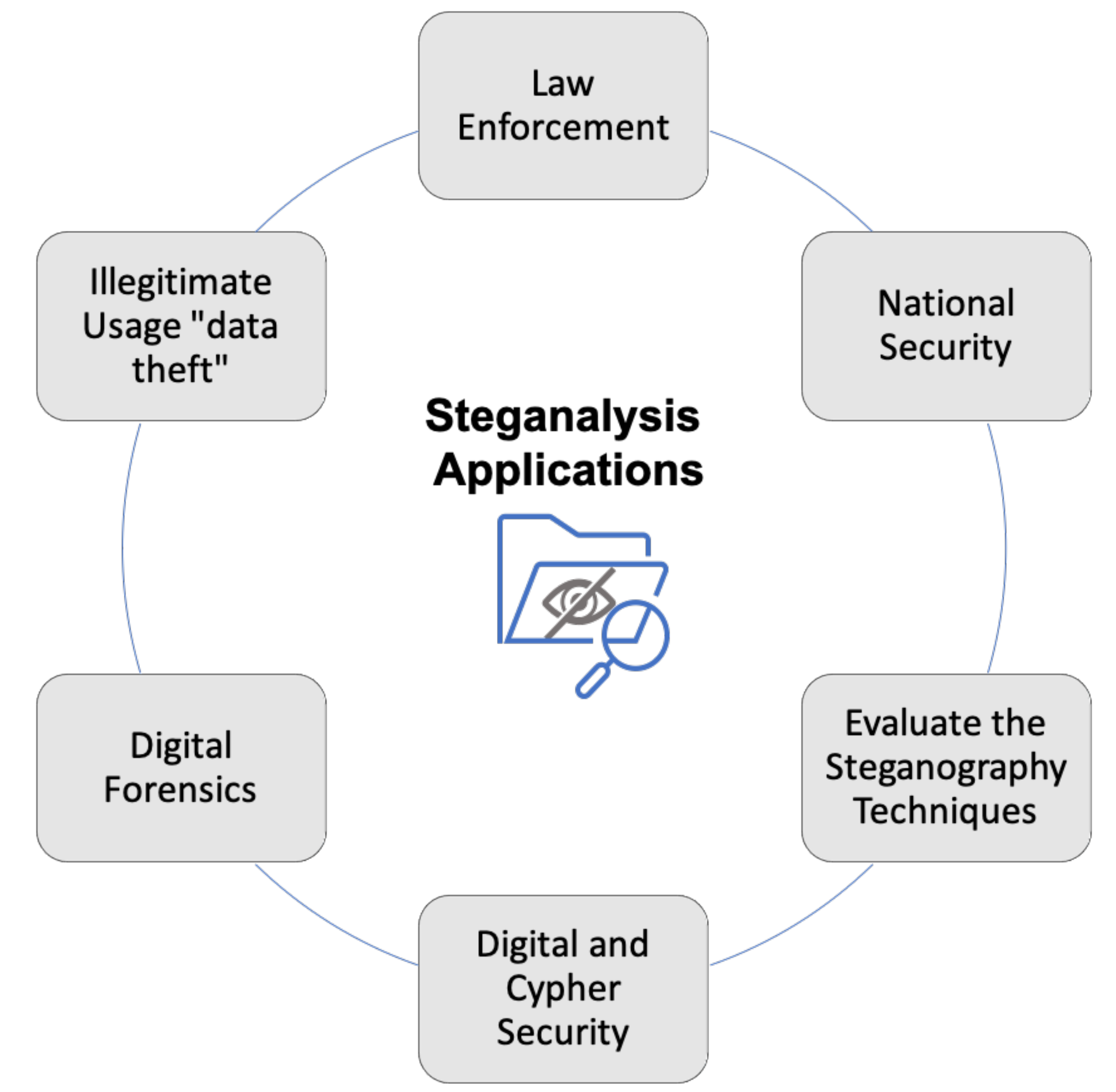
7. Digital Multimedia Steganalysis Tools
8. Perspectives and Open Issues
- Standard dataset: For an easier and fair comparison between the published steganalysis techniques, it is necessary to use a standard and fixed dataset. In image steganalysis, there are standard databases where the most popular are BOSSbase and BOWS2 databases. On the other hand, audio steganalysis was until recent lacked for the standard dataset, where the researchers generated their own datasets. Fortunately, a public dataset for audio steganalysis was generated for WAV, mp3 formats. However, still there is a need for developing a unified and public dataset for video and other formats for audio steganalysis.
- Practical steganalysis techniques: Computation complexity and time consumption are two significant terms that should be considered when developing practical steganalysis techniques. Most of the existing techniques give attention to accuracy detection regardless of the complexity of the computation.Nowadays, the emerging of machines and deep learning opens a new horizon for faster and more accurate detection. Although of their advantages, many issues should be taken into consecration such as avoiding the complexity of the training phase, adjusting and fixing well hyperparameters before training, and avoid overfitting.
- Virtual and online services: The digital technology era increased the chances for criminals to exploit new unsuspicious spots for hiding such as online games, cloud storage systems, and the virtual world. Steganalysis techniques for these network traffic services should be developed.
- Balancing: There is a clear unbalancing in this domain, starting with the proposed steganography and steganalysis techniques. As illustrating in Figure 12, there is a big gap between the number of published steganography and steganlysis techniques. This gap back to the difficulty and obstecals that faced by researcher and forensic expertsin the steganalysis field. So, there is highly needed for more investigation and work from dedicated and adept researchers in steganalysis domain.Regarding medium based steganalysis, image steganalysis, then audio, receives more attention from the researcher than video steganalysis. However, researchers have shown that by 2021, video traffic will consume 82% of all traffic of the Internet [61]. Besides that, the video medium provides sufficient space for hiding data which makes the video medium a good scope to exploited by steganography technique. So, video steganalysis should attract more attention from the researchers.In addition, the researchers focus on some formats more than others. For example, in audio steganalysis, most of the existing techniques are proposed for mp3 format, especially for Mp3stego steganography. Among these techniques, LSB techniques have the biggest share, where the non-LSB techniques need to more investigate [16].
- General steganalysis technique: Most of the existing steganlysis techniques relied on the training dataset to make the classifier learns and trains on the representation of cover and stego medium (semi-blind) or only cover medium (blind). Hence, there a high relation between classification accuracy and training datasets, where mostly the accuracy reduces as the testing dataset differs from the training dataset. Indeed, most of the existing techniques are belong to the semi-blind approach.In the real world, there are thousands of steganography techniques and different types of cover contents, size, noise, and sampling frequency, etc. This amount of training datasets especially for stego- mediums makes it impossible to restrict them. There are a few techniques that exploit the unsupervised approach to deal with this issue [91], but still, the accuracy needs to be improved.
- Keeping up: The steganalyser should be keeping up with the new trends related to steganography and steganalysis domain. For instance, the recent formats as H.265/HEVC will be highly exploited for steganography, since it contains various advanced features.IoT (Internet of Things) has been utilized by a few researchers for the transfer and storage of data hidden using steganography. So, there is a big chance to used by criminals for hiding the secret data [25].Last but not least, the steganalysis techniques deal with digital medium audio, image, and video separately. However, the video file normally contains video coding format alongside audio data in an audio coding format. The sound-video or audio-video provides a high capacity for embedding secret data for the criminal. Although there are few steganography techniques in this regard [92,93,94], no steganalysis technique available till date. However, the existing image and audio steganalysis could detect that type of steganography, but there are no experiments for evaluation.
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Kadhim, I.J.; Premaratne, P.; Vial, P.J.; Halloran, B. Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research. Neurocomputing 2019, 335, 299–326. [Google Scholar] [CrossRef]
- Abikoye, O.C.; Ojo, U.A.; Awotunde, J.B.; Ogundokun, R.O. A safe and secured iris template using steganography and cryptography. Multimed. Tools Appl. 2020, 79, 23483–23506. [Google Scholar] [CrossRef]
- Petitcolas, F.A.; Katzenbeisser, S. Information Hiding Techniques for Steganography and Digital Watermarking (Artech House Computer Security Series); Artech House: Norwood, MA, USA, 2000. [Google Scholar]
- Kahn, D. The history of steganography. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 1996; pp. 1–5. [Google Scholar]
- Cheddad, A.; Condell, J.; Curran, K.; Mc Kevitt, P. Digital image steganography: Survey and analysis of current methods. Signal Process. 2010, 90, 727–752. [Google Scholar] [CrossRef] [Green Version]
- Liao, X.; Yu, Y.; Li, B.; Li, Z.; Qin, Z. A new payload partition strategy in color image steganography. IEEE Trans. Circuits Syst. Video Technol. 2019, 30, 685–696. [Google Scholar] [CrossRef]
- Saravanan, M.; Priya, A. An Algorithm for Security Enhancement in Image Transmission Using Steganography. J. Inst. Electron. Comput. 2019, 1, 1–8. [Google Scholar] [CrossRef]
- Yi, X.; Yang, K.; Zhao, X.; Wang, Y.; Yu, H. AHCM: Adaptive Huffman code mapping for audio steganography based on psychoacoustic model. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2217–2231. [Google Scholar] [CrossRef]
- Rout, H.; Mishra, B.K. Pros and cons of cryptography, steganography and perturbation techniques. IOSR J. Electron. Commun. Eng. 2014, 76–81. [Google Scholar]
- CNN. Documents Reveal al Qaeda’s Plans for Seizing Cruise Ships, Carnage in Europe. 2012. Available online: https://edition.cnn.com/2012/04/30/world/al-qaeda-documents-future/index.html (accessed on 5 October 2021).
- Zielińska, E.; Mazurczyk, W.; Szczypiorski, K. Trends in steganography. Commun. ACM 2014, 57, 86–95. [Google Scholar] [CrossRef]
- Trend Micro. Spam Campaign Targets Japan, Uses Steganography to Deliver the BEBLOH Banking Trojan. 2018. Available online: https://www.trendmicro.com/vinfo/nz/security/news/cybercrime-and-digital-threats/spam-campaign-targets-japan-uses-steganography-to-deliver-the-bebloh-banking-trojan (accessed on 5 October 2021).
- Xiang, L.; Guo, G.; Yu, J.; Sheng, V.S.; Yang, P. A convolutional neural network-based linguistic steganalysis for synonym substitution steganography. Math. Biosci. Eng. 2020, 17, 1041–1058. [Google Scholar] [CrossRef] [PubMed]
- Yousfi, Y.; Butora, J.; Fridrich, J.; Giboulot, Q. Breaking ALASKA: Color separation for steganalysis in JPEG domain. In Proceedings of the ACM Workshop on Information Hiding and Multimedia Security, Paris, France, 3–5 July 2019; pp. 138–149. [Google Scholar]
- Yang, Z.; Yang, H.; Hu, Y.; Huang, Y.; Zhang, Y.J. Real-time steganalysis for stream media based on multi-channel convolutional sliding windows. arXiv 2019, arXiv:1902.01286. [Google Scholar]
- Karampidis, K.; Kavallieratou, E.; Papadourakis, G. A review of image steganalysis techniques for digital forensics. J. Inf. Secur. Appl. 2018, 40, 217–235. [Google Scholar] [CrossRef]
- Banerjee, P. ALASKA2: Image Steganalysis—All You Need to Know. 2020. Available online: https://www.kaggle.com/prashant111/alaska2-image-steganalysis-all-you-need-to-know (accessed on 5 October 2021).
- Ghasemzadeh, H.; Kayvanrad, M.H. Comprehensive review of audio steganalysis methods. IET Signal Process. 2018, 12, 673–687. [Google Scholar] [CrossRef] [Green Version]
- Paulin, C.; Selouani, S.A.; Hervet, E. Audio steganalysis using deep belief networks. Int. J. Speech Technol. 2016, 19, 585–591. [Google Scholar] [CrossRef]
- Amsaveni, A.; Vanathi, P. A comprehensive study on image steganography and steganalysis techniques. Int. J. Inf. Commun. Technol. 2015, 7, 406–424. [Google Scholar] [CrossRef]
- Dalal, M.; Juneja, M. Video steganalysis to obstruct criminal activities for digital forensics: A survey. Int. J. Electron. Secur. Digit. Forensics 2018, 10, 338–355. [Google Scholar] [CrossRef]
- Reinel, T.S.; Raul, R.P.; Gustavo, I. Deep learning applied to steganalysis of digital images: A systematic review. IEEE Access 2019, 7, 68970–68990. [Google Scholar] [CrossRef]
- Chutani, S.; Goyal, A. A review of forensic approaches to digital image Steganalysis. Multimed. Tools Appl. 2019, 78, 18169–18204. [Google Scholar] [CrossRef]
- Tabares-Soto, R.; Ramos-Pollán, R.; Isaza, G.; Orozco-Arias, S.; Ortíz, M.A.B.; Arteaga, H.B.A.; Rubio, A.M.; Grisales, J.A.A. Digital media steganalysis. In Digital Media Steganography; Elsevier: Amsterdam, The Netherlands, 2020; pp. 259–293. [Google Scholar]
- Dalal, M.; Juneja, M. Steganography and Steganalysis (in digital forensics): A Cybersecurity guide. Multimed. Tools Appl. 2020, 80, 5723–5771. [Google Scholar] [CrossRef]
- Ruan, F.; Zhang, X.; Zhu, D.; Xu, Z.; Wan, S.; Qi, L. Deep learning for real-time image steganalysis: A survey. J. Real-Time Image Process. 2020, 17, 149–160. [Google Scholar] [CrossRef]
- Chaumont, M. Deep learning in steganography and steganalysis. In Digital Media Steganography; Elsevier: Amsterdam, The Netherlands, 2020; pp. 321–349. [Google Scholar]
- Berthet, A.; Dugelay, J.L. A review of data preprocessing modules in digital image forensics methods using deep learning. In Proceedings of the 2020 IEEE International Conference on Visual Communications and Image Processing (VCIP), Macau, China, 1–4 December 2020; pp. 281–284. [Google Scholar]
- Hussain, I.; Zeng, J.; Xinhong, X.; Tan, S. A survey on deep convolutional neural networks for image steganography and steganalysis. KSII Trans. Internet Inf. Syst. (TIIS) 2020, 14, 1228–1248. [Google Scholar]
- Gokhale, A.; Mulay, P.; Pramod, D.; Kulkarni, R. A bibliometric analysis of digital image forensics. Sci. Technol. Libr. 2020, 39, 96–113. [Google Scholar] [CrossRef]
- Selvaraj, A.; Ezhilarasan, A.; Wellington, S.L.J.; Sam, A.R. Digital image steganalysis: A survey on paradigm shift from machine learning to deep learning based techniques. IET Image Process. 2021, 15, 504–522. [Google Scholar] [CrossRef]
- Alarood, A.A.S. Improved Steganalysis Technique Based on Least Significant BIT Using Artificial Neural Network for Mp3 Files. Ph.D. Thesis, Universiti Teknologi Malaysia, Skudai, Malaysia, 2017. [Google Scholar]
- Alyousuf, F.Q.A.; Din, R.; Qasim, A.J. Analysis review on spatial and transform domain technique in digital steganography. Bull. Electr. Eng. Inform. 2020, 9, 573–581. [Google Scholar]
- Tasdemir, K.; Kurugollu, F.; Sezer, S. Spatio-temporal rich model-based video steganalysis on cross sections of motion vector planes. IEEE Trans. Image Process. 2016, 25, 3316–3328. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sadek, M.M.; Khalifa, A.S.; Mostafa, M.G. Video steganography: A comprehensive review. Multimed. Tools Appl. 2015, 74, 7063–7094. [Google Scholar] [CrossRef]
- Sumathi, C.; Santanam, T.; Umamaheswari, G. A study of various steganographic techniques used for information hiding. arXiv 2014, arXiv:1401.5561. [Google Scholar]
- Khan, S.; Bianchi, T. Ant colony optimization (aco) based data hiding in image complex region. Int. J. Electr. Comput. Eng. 2018, 8, 379–389. [Google Scholar] [CrossRef]
- Filler, T.; Judas, J.; Fridrich, J. Minimizing additive distortion in steganography using syndrome-trellis codes. IEEE Trans. Inf. Forensics Secur. 2011, 6, 920–935. [Google Scholar] [CrossRef] [Green Version]
- Fridrich, J.; Goljan, M.; Lisonek, P.; Soukal, D. Writing on wet paper. IEEE Trans. Signal Process. 2005, 53, 3923–3935. [Google Scholar] [CrossRef]
- AlSabhany, A.A.; Ali, A.H.; Ridzuan, F.; Azni, A.; Mokhtar, M.R. Digital audio steganography: Systematic review, classification, and analysis of the current state of the art. Comput. Sci. Rev. 2020, 38, 100316. [Google Scholar] [CrossRef]
- Nissar, A.; Mir, A.H. Classification of steganalysis techniques: A study. Digit. Signal Process. 2010, 20, 1758–1770. [Google Scholar] [CrossRef]
- Fridrich, J.; Long, M. Steganalysis of LSB encoding in color images. In Proceedings of the 2000 IEEE International Conference on Multimedia and Expo, ICME2000, Latest Advances in the Fast Changing World of Multimedia (Cat. No. 00TH8532), New York, NY, USA, 30 July–2 August 2000; Volume 3, pp. 1279–1282. [Google Scholar]
- Dittmann, J.; Hesse, D. Network based intrusion detection to detect steganographic communication channels: On the example of audio data. In Proceedings of the IEEE 6th Workshop on Multimedia Signal Processing, Siena, Italy, 29 September–1 October 2004; pp. 343–346. [Google Scholar]
- Qian, Y.; Dong, J.; Wang, W.; Tan, T. Feature learning for steganalysis using convolutional neural networks. Multimed. Tools Appl. 2018, 77, 19633–19657. [Google Scholar] [CrossRef]
- Serrano, J. Steganalysis: A Study on the Effectiveness of Steganalysis Tools. Ph.D. Thesis, Utica College, Utica, NY, USA, 2019. [Google Scholar]
- Ghasemzadeh, H.; Arjmandi, M.K. Universal audio steganalysis based on calibration and reversed frequency resolution of human auditory system. IET Signal Process. 2017, 11, 916–922. [Google Scholar] [CrossRef] [Green Version]
- Wang, Y.; Yi, X.; Zhao, X. MP3 steganalysis based on joint point-wise and block-wise correlations. Inf. Sci. 2020, 512, 1118–1133. [Google Scholar] [CrossRef]
- Jin, C.; Wang, R.; Yan, D. Steganalysis of MP3Stego with low embedding-rate using Markov feature. Multimed. Tools Appl. 2017, 76, 6143–6158. [Google Scholar] [CrossRef]
- Han, C.; Xue, R.; Zhang, R.; Wang, X. A new audio steganalysis method based on linear prediction. Multimed. Tools Appl. 2018, 77, 15431–15455. [Google Scholar] [CrossRef]
- Lin, Y.; Wang, R.; Yan, D.; Dong, L.; Zhang, X. Audio steganalysis with improved convolutional neural network. In Proceedings of the ACM Workshop on Information Hiding and Multimedia Security, Paris, France, 3–5 July 2019; pp. 210–215. [Google Scholar]
- Ren, Y.; Liu, D.; Xiong, Q.; Fu, J.; Wang, L. Spec-resnet: A general audio steganalysis scheme based on deep residual network of spectrogram. arXiv 2019, arXiv:1901.06838. [Google Scholar]
- Chaeikar, S.S.; Zamani, M.; Manaf, A.B.A.; Zeki, A.M. PSW statistical LSB image steganalysis. Multimed. Tools Appl. 2018, 77, 805–835. [Google Scholar] [CrossRef]
- Soltanian, M.; Ghaemmaghami, S. Blind consecutive extraction of multi-carrier spread spectrum data from digital images. In Proceedings of the 2017 Iranian Conference on Electrical Engineering (ICEE), Tehran, Iran, 2–4 May 2017; pp. 1835–1839. [Google Scholar]
- Li, M.; Kulhandjian, M.K.; Pados, D.A.; Batalama, S.N.; Medley, M.J. Extracting spread-spectrum hidden data from digital media. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1201–1210. [Google Scholar]
- Lu, W.; Li, R.; Zeng, L.; Chen, J.; Huang, J.; Shi, Y.Q. Binary image steganalysis based on histogram of structuring elements. IEEE Trans. Circuits Syst. Video Technol. 2019, 30, 3081–3094. [Google Scholar] [CrossRef]
- Laimeche, L.; Merouani, H.F.; Mazouzi, S. A new feature extraction scheme in wavelet transform for stego image classification. Evol. Syst. 2018, 9, 181–194. [Google Scholar] [CrossRef]
- Guttikonda, J.B.; Sridevi, R. A new steganalysis approach with an efficient feature selection and classification algorithms for identifying the stego images. Multimed. Tools Appl. 2019, 78, 21113–21131. [Google Scholar] [CrossRef]
- Wu, S.; Zhong, S.; Liu, Y. Deep residual learning for image steganalysis. Multimed. Tools Appl. 2018, 77, 10437–10453. [Google Scholar] [CrossRef]
- Wang, Z.; Chen, M.; Yang, Y.; Lei, M.; Dong, Z. Joint multi-domain feature learning for image steganalysis based on CNN. EURASIP J. Image Video Process. 2020, 2020, 1–12. [Google Scholar] [CrossRef]
- Wang, P.; Cao, Y.; Zhao, X. Segmentation based video steganalysis to detect motion vector modification. Secur. Commun. Netw. 2017, 2017, 8051389. [Google Scholar] [CrossRef] [Green Version]
- Sadat, E.S.; Faez, K.; Saffari Pour, M. Entropy-based video steganalysis of motion vectors. Entropy 2018, 20, 244. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Su, Y.; Yu, F.; Zhang, C. Digital Video Steganalysis Based on a Spatial Temporal Detector. TIIS 2017, 11, 360–373. [Google Scholar]
- Li, Z.; Meng, L.; Xu, S.; Shi, Y. A HEVC video steganalysis algorithm based on pu partition modes. Comput. Mater. Contin. 2019, 59, 607–624. [Google Scholar] [CrossRef]
- Ghamsarian, N.; Schoeffmann, K.; Khademi, M. Blind MV-based video steganalysis based on joint inter-frame and intra-frame statistics. Multimed. Tools Appl. 2020, 80, 9137–9159. [Google Scholar] [CrossRef]
- Liu, P.; Li, S. Steganalysis of Intra Prediction Mode and Motion Vector-based Steganography by Noise Residual Convolutional Neural Network. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2020; Volume 719, p. 012068. [Google Scholar]
- Huang, X.; Hu, Y.; Wang, Y.; Liu, B.; Liu, S. Deep Learning-based Quantitative Steganalysis to Detect Motion Vector Embedding of HEVC Videos. In Proceedings of the 2020 IEEE Fifth International Conference on Data Science in Cyberspace (DSC), Hong Kong, China, 27–30 July 2020; pp. 150–155. [Google Scholar]
- Kodovsky, J.; Fridrich, J.; Holub, V. Ensemble classifiers for steganalysis of digital media. IEEE Trans. Inf. Forensics Secur. 2011, 7, 432–444. [Google Scholar] [CrossRef] [Green Version]
- Johnson, N.F.; Jajodia, S. Steganalysis of images created using current steganography software. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 1998; pp. 273–289. [Google Scholar]
- Chandramouli, R.; Li, G.; Memon, N.D. Adaptive steganography. In Security and Watermarking of Multimedia Contents IV; International Society for Optics and Photonics: Bellingham, WA, USA, 2002; Volume 4675, pp. 69–78. [Google Scholar]
- Wilson, L. Zipf, George K: Human Behavior and the Principle of Least Effort; Addison Wesley: New York, NY, USA, 1949. [Google Scholar]
- Zhang, H.; Cao, Y.; Zhao, X. A steganalytic approach to detect motion vector modification using near-perfect estimation for local optimality. IEEE Trans. Inf. Forensics Secur. 2016, 12, 465–478. [Google Scholar] [CrossRef]
- Wang, P.; Cao, Y.; Zhao, X.; Wu, B. Motion vector reversion-based steganalysis revisited. In Proceedings of the 2015 IEEE China Summit and International Conference on Signal and Information Processing (ChinaSIP), Chengdu, China, 12–15 July 2015; pp. 463–467. [Google Scholar]
- BOSS Web Page. Retrieved: 2020. Available online: http://agents.fel.cvut.cz/boss/index.php?mode=VIEW&tmpl=materials (accessed on 5 October 2021).
- BOWS2 Web Page. Retrieved: 2020. Available online: http://bows2.ec-lille.fr/index.php?mode=VIEW&tmpl=index1 (accessed on 5 October 2021).
- ImageNet Web Page, Retrieved: 2020. Available online: http://www.image-net.org (accessed on 5 October 2021).
- Center for Statistics and Applications in Forensic Evidence. Stegoappdb Homepage. Retrieved: 2020. Available online: https://forensicstats.org/stegoappdb/ (accessed on 5 October 2021).
- Coral. Corel Image Database. Retrieved: 2020. Available online: http://www.corel.com (accessed on 5 October 2021).
- University of Southern California. The USC-SIPI Image Database. Retrieved 2020. Available online: http://sipi.usc.edu/database/ (accessed on 5 October 2021).
- Wang, K.Y.; Yang, Y.J.X. Audio Steganalysis Dataset. 2019. Available online: https://ieee-dataport.org/documents/audio-steganalysis-dataset (accessed on 5 October 2021).
- Lin, Z.; Huang, Y.; Wang, J. RNN-SM: Fast Steganalysis of VoIP Streams Using Recurrent Neural Network. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1854–1868. [Google Scholar] [CrossRef]
- Meghanathan, N.; Nayak, L. Steganalysis algorithms for detecting the hidden information in image, audio and video cover media. Int. J. Netw. Secur. Its Appl. (IJNSA) 2010, 2, 43–55. [Google Scholar]
- spyhunter. StegSpy. 2004. Available online: http://www.spy-hunter.com/stegspy (accessed on 5 October 2021).
- Provos, N. stegdetect. 2002. Available online: https://github.com/abeluck/stegdetect (accessed on 5 October 2021).
- Muñoz, A. stegsecret. 2007. Available online: http://stegsecret.sourceforge.net (accessed on 5 October 2021).
- WetStone Technologies. StegoHunt. 2019. Available online: https://www.wetstonetech.com/products/stegohunt-steganography-detection/ (accessed on 5 October 2021).
- Boehm, B. StegExpose. 2014. Available online: https://github.com/b3dk7/StegExpose (accessed on 5 October 2021).
- Backbone Security. StegAlyzerAS. Retrieved: 2020. Available online: https://www.backbonesecurity.com (accessed on 5 October 2021).
- Backbone Security. StegAlyzerSS. Retrieved: 2020. Available online: https://www.backbonesecurity.com (accessed on 5 October 2021).
- Backbone Security. StegAlyzerFS. Retrieved: 2020. Available online: https://www.backbonesecurity.com (accessed on 5 October 2021).
- SourceForge. Virtual Steganographic Laboratory. Retrieved: 2020. Available online: https://sourceforge.net/projects/vsl/ (accessed on 5 October 2021).
- Lerch-Hostalot, D.; Megías, D. Unsupervised steganalysis based on artificial training sets. Eng. Appl. Artif. Intell. 2016, 50, 45–59. [Google Scholar] [CrossRef] [Green Version]
- Kakde, Y.; Gonnade, P.; Dahiwale, P. Audio-video steganography. In Proceedings of the 2015 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 19–20 March 2015; pp. 1–6. [Google Scholar]
- Lalwani, D.; Sawant, M.; Rane, M.; Jogdande, V.; Ware, S. Secure Data Hiding in Audio-Video Steganalysis by Anti-Forensic Technique. Int. J. Eng. Comput. Sci. 2016, 5, 15996–16000. [Google Scholar] [CrossRef]
- Mudusu, R.; Nagesh, A.; Sdanandam, M. Enhancing Data Security Using Audio-Video Steganography. Int. J. Eng. Technol. 2018, 7, 276–279. [Google Scholar] [CrossRef] [Green Version]









| Ref | Published Year | Journal or Conference | Mediums | Contributions |
|---|---|---|---|---|
| [20] | 2015 | Int. J. of Information | Image | Provide an overview of steganography for different kinds of multimedia. |
| and Communication | - Review different image steganography and steganalysis techniques. | |||
| technology | - Explain the way in which each algorithm works. | |||
| [18] | 2018 | IET Signal Processing | Audio | - Provide a comprehensive review of audio steganalysis. |
| - Classify the literature into different categories. | ||||
| - Conduct comparison between different works. | ||||
| [16] | 2018 | Journal of information security and | Image | - Discuss and present various steganalysis techniques from earlier ones to state of the art. |
| applications | - Classify the literature into different categories. | |||
| [21] | 2018 | Int. J. Electronic | Video | - Present an overview of video steganalysis techniques |
| Security and Digital Forensics | - Discuss the challenging and open issues. | |||
| [22] | 2019 | IEEE Access | Image | - Provide a systematic review of DL applied to steganalysis |
| - Show the evolution of steganalysis in recent years using the DL techniques. | ||||
| - Highlight the most significant results and possible future work. | ||||
| [23] | 2019 | Image | - Provide an overview of the steganalysis techniques considering: the embedding algorithm, | |
| Multimedia Tools | estimation of the secret message payload and stego key determination. | |||
| and Applications | - Describe and compare various features of the steganalysis techniques. | |||
| - Discuss the challenges and future recommendations. | ||||
| [24] | 2020 | book (Digital media | Audio, Video, | - Provide an explanation for the vital elements of steganalysis applied to digital media. |
| steganography) in Elsevier | Image, Text | - Present a review for the existing works based on ML and DL over the last 10 years. | ||
| (ScienceDirect) | - Provide a short discussion for the challenging and open issues. | |||
| [25] | 2020 | Multimedia Tools | Image, Video | - Provide a basic guide for the research in steganography and steganalysis domain. |
| and Applications | - Mention the applications, dataset, tools and techniques available. | |||
| - Discuss the challenges and future recommendations. | ||||
| [26] | 2020 | Journal of Real-Time | Image | - Discuss the impacts of the real-time Image Steganalysis (IS). |
| Image Processing | - Provide a brief overview of the IS based on deep NNs. | |||
| - Analyze a practical real-time IS application and prospect the future issues of real-time IS. | ||||
| [27] | 2020 | book(Digital media | Image | - Present different NNs structures of the existing literature from the period 2015–2018 |
| steganography) in Elsevier | - Discussed the memory and time complexity, and practical problems for efficiency. | |||
| (ScienceDirect) | - Explored the link between some past approaches sharing similarities. | |||
| - Discuss steganography by deep learning. | ||||
| [28] | 2020 | IEEE International | Image | |
| Conference on Visual Communications and Image Processing | - Review the preprocessing modules associated with CNN models. | |||
| [29] | 2020 | KSII Transactions on Internet and Information and Systems | Image | - Analyze current research states from the latest image steganography and steganalysis techniques based on DL. |
| - Highlights the strengths and weakness of existing up-to-date techniques. | ||||
| - Discuss the challenges and future recommendations. | ||||
| [30] | 2020 | Science Technology Libraries | Image | - Provide a bibliometric analysis of digital image steganalysis from 2014 to early 2020. |
| - Use a mind map approach to analyze the results obtained from various of aspects like renowned authors, funding agencies, and affiliations. | ||||
| [31] | 2021 | IET Image Processing | Image | - Review the recent research works in DL based digital image steganalysis. |
| - Introduce the paradigm shift from ML approaches to employing more promising DL architectures. | ||||
| - Conduct comparison between different works. |
| Ref | Image | Audio | Video | Steganography Background | Steganalysis Classification | Datasets | Available Tools | Systematic Review |
|---|---|---|---|---|---|---|---|---|
| [20] | ✓ | x | x | ✓ | ✓ | x | x | x |
| [24] | ✓ | ✓ | ✓ | x | ✓ | x | x | x |
| [16] | ✓ | x | x | x | ✓ | ✓ | x | x |
| [18] | x | ✓ | x | x | ✓ | x | x | x |
| [21] | x | x | ✓ | x | ✓ | x | x | x |
| [22] | x | x | x | x | x | ✓ | x | ✓ |
| [23] | ✓ | x | x | x | ✓ | x | x | x |
| [25] | ✓ | x | ✓ | ✓ | ✓ | ✓ | ✓ | x |
| [26] | ✓ | x | x | x | x | x | x | x |
| [27] | ✓ | x | x | ✓ | x | ✓ | x | x |
| [28] | ✓ | x | x | x | ✓ | x | x | x |
| [29] | ✓ | x | x | ✓ | ✓ | x | x | x |
| [30] | ✓ | x | x | x | ✓ | x | x | ✓ |
| [31] | ✓ | x | x | ✓ | ✓ | x | x | x |
| Our | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | x |
| Ref. | Year | Type of Features | Detection Method | Database | Steganography Technique | Advantage | Limitation |
|---|---|---|---|---|---|---|---|
| [46] | 2017 | Hand crafted Statistical (Markov features) | Machine learning SVM | Unknown dataset consists of 1000 stereo WAV audios | MP3Stego steganography. | Detecting low embedding-rate in the MP3 audios | Time consumption for the feature construction phase. |
| [47] | 2020 | Hand crafted Statistical (Multi-scale correlations measure for QMDCT coefficients) | Machine learning (ensemble classifier) | General dataset consists of 10,000 mp3 files with 10 s duration. | Different steganography techniques includes HCM, MP3Stego, and EECS | good performance in several MP3 steganography algorithms, bitrates, duration, and relative payloads. | High dimensionality |
| [48] | 2017 | Hand crafted Statistical (Markov features) | Machine learning SVM | Two datasets consist of 4169 wave music clips and 1029 speech wave files. | Different steganography techniques includes LSB, SS, DCT, and others | High accuracy detection against target and universal techniques | The detection accuracy decreases in the low embedding rate for speech datasets in most of the cases. |
| [49] | 2018 | Hand crafted Statistical (LP features) | Machine learning SVM | General datasets consist of 2000 WAV files with rate of 44.1 kHz. | Different steganography techniques includes Hide4PGP, S-Tools, StegoMagic, and Xiao | High accuracy detection for high embedding ratio | The accuracy detection for low embedding ratio not sufficient comparing with high embedding |
| [50] | 2019 | Deep features using CNN | Fully connected Layer (softmax) | A dataset cotains 6300 mono WAV files with rate of 16 kHz. | LSB matching and STC steganography techniques | Improving the architecture of CNN to enhance the detection performance. | Moderate detection accuracy for low embedding rate |
| [51] | 2019 | Deep features using (S-ResNet) | Machine learning SVM | Two datasets cotain 10,000 with 16-kHz rate and (2 s) duration in AAC format, and 9000 with 44.1 kHz rate and (5 s) duration in mp3 format | Different steganography techniques includes LSB, MIN, SIGN, and MP3Stego | High detection accuracy | High dimensionality |
| Ref. | Year | Type of Features | Detection Method | Database | Steganography Technique | Advantage | Limitation |
|---|---|---|---|---|---|---|---|
| [52] | 2018 | Hand crafted Statistical feature (color correlativity) | Machine learning SVM | UW image database consisting of 1333 images | LSB flipping image steganography. | High efficiency with single dimension analysis | Low detection accuracy in case the low embedding rates |
| [53] | 2017 | Statistical feature (variance) | Hand crafted Statistical strategy | BossBase image database | SS steganography. | Fast and low computation complexity comparing with [54] | The extraction performance decrease with high embedding distortion. |
| [55] | 2019 | Hand crafted Statistical feature (histograms of SE) | Machine learning SVM | DBLST and BIVC database | Different steganography techniques including distortion-based, pattern-based, and others. | Simple and high performance | Not taking in to account the frequencies of different SEs patterns. |
| [56] | 2018 | Hand crafted Statistical feature (Zipf’s law in the wavelet transform) | Machine learning RF | UCID database | Different steganography techniques including spatial-based, transform-based. | Adapting new and effective statistical law for extracting features in the wavelet transform domain | The pre-processing steps before features extraction may produced high execution time. |
| [57] | 2019 | Hand crafted Statistical features from transform and spatial domains) | Machine learning CIML | BSD300 dataset contains 150 JPEG images | Different steganography techniques including distortion-based, spatial-based, and others. | Low computation complexity, low time consumption, and high performance | Small dataset |
| [58] | 2018 | Deep features from spatial domain using DRN | Fully connected layer (softmax classifier) | BOSSbase dataset contains 10,000 images | Spatial UNIversal WAvelet Relative Distortion (S-UNIWARD) steganography. | High detection accuracy | High computation complexity |
| [59] | 2020 | Deep features from spatial and transform domains using CNN | Fully connected layer (softmax classifier) | BOSSbase dataset contains 10,000 images | Spatial UNIversal WAvelet Relative Distortion (S-UNIWARD) and Wavelet Obtained Weights steganography. | Considering the spatial and transform domains to increase the accuracy | An ordinary accuracy although the high computational complexity |
| Ref. | Year | Type of Features | Detection Method | Database | Steganography Technique | Advantage | Limitation |
|---|---|---|---|---|---|---|---|
| [60] | 2017 | Hand crafted features NPELO (36-dimensional) + MVRBR | Machine learning (SVM) | Contains 100 YUV sequences (H.264/AVC standard), each sequence has 150 to 300 frames | MV steganography | Takes into account the motion characteristic of video content. | Uses small datasets |
| [61] | 2018 | Hand crafted features (entropy, motion, and statistic features) | Machine learning (SVM) | 284 uncompressed video (H.264/AVC standard) from internet | MV steganography | The detection accuracy does not affect by the bit rate variations | Their experiment limited and can not detect the currently best steganography methods |
| [62] | 2017 | Hand crafted features (motion intensity and texture histograms) | Machine learning (SVM) | Contains 14 YUV sequences (H.264/AVC standard), only the first 90 frames from each sequences | SS steganography | Exploit the videos spatial and temporal redundancies simultaneously | Uses small datasets |
| [63] | 2019 | Hand crafted features (statistic change in distribution of the PU) | Machine learning (SVM) | 33 videos each contains 80 frames in 720P and 30 videos each contains 50 frames in 1080P (HEVC standard), only the first 90 frames from each sequences | PU partition modes steganography | Exploit the videos spatial and temporal redundancies simultaneously | Considering as a targeted steganalysis technique |
| [64] | 2020 | Hand crafted features (statistical features of inter-frame and intra-frame) | mMchine learning (SVM) | 22 PAL QCIf video dataset (H.264/AVC standard) | MV steganography | Blind steganalysis technique and can be adjusted to various video codec standards. | computational complexity due to the high dimensionality of features |
| [65] | 2020 | Deep features (steganographic noise residual features) using CNN | Fully connected Layer(softmax classifier) | Unknown dataset contains (200,000 frames for training and testing | MV and Intra Prediction Mode steganography | Universal steganalysis technique | Did not taking into account the temporal domain. |
| [66] | 2020 | Deep features (512-dimensional) using CNN | Fully connected Layer (softmax classifier) | Xiph Video Test Media database(HEVC standard) | MV steganography | Extract deep features and estimates the embedding rate | Extract the features from fixed-size block motion estimation |
| Name | Media Type | Description | Availability |
|---|---|---|---|
| BOSSBase V1.01 [73] | Image | No. of images: 10,000, Format: Portable Gray Map (PGM) of 8 bits, Size: 512 × 512 | Public |
| BOWS2 [74] | Image | No. of images: 10,000, Format: PGM of 8 bits, Size: 512 × 512 | Public |
| ImageNet [75] | Image | No. of images:more than 14 million, Format: mostly JPEG, Size: different sizes | Public |
| Stegoappdb [76] | image | No. of images: 960,000, Format:DNG and JPEG, Size: different sizes | Public |
| Corel [77] | Image | No. of images: 10,800, Format: DNG and JPEG, Size: different sizes | Public |
| USC-SIPI [78] | Image and video | No. of images: 237 and 96 in 4 sequences, Format: TIFF, Size: different sizes | Public |
| Audio Steganalysis Dataset IIE (ASDIIE) 1 | Audio | No. of clips: 22,671, Format:WAV with a sampling rate of 44.1 kHz and duration of 10 s | Public |
| Audio Steganalysis Dataset [79] | Audio | No. of clips: 33,038, Format: MP3-WAV, Sampling rate: 44.1 kHz, Duration: 10 s | Public |
| Speech dataset [80] | Audio | No. of clips: 320 Chinese and English speech, Format: PCM | Public |
| Software | Producer | Platform | Medium Type | Availability |
|---|---|---|---|---|
| StegSpy [82] | SpyHunter | Windows | Image | Freeware |
| StegDetect [83] | Niels Provos | Linux, windwos | Image | Freeware |
| StegSecret [84] | Alfonso Muñoz | Java-based | Image, Audio, Video | Freeware |
| StegoHunt [85] | WetStone Technologies | Windows | Image, Audio, Video | License purchase |
| StegExpose [86] | Benedikt Boehm | Java-based | image | Freeware |
| StegAlyzerAS [87] | Backbone Security | Windows | Image | License purchase |
| StegalyzerSS [88] | Backbone Security | Windows | Image | License purchase |
| StegAlyzerFS [89] | Backbone Security | Windows, Linux, Apple OS | Image, Audio, Video | License purchase |
| VSL [90] | Michal Wegrzyn | Java-based | Image | Freeware |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shehab, D.A.; Alhaddad, M.J. Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research. Symmetry 2022, 14, 117. https://doi.org/10.3390/sym14010117
Shehab DA, Alhaddad MJ. Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research. Symmetry. 2022; 14(1):117. https://doi.org/10.3390/sym14010117
Chicago/Turabian StyleShehab, Doaa A., and Mohmmed J. Alhaddad. 2022. "Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research" Symmetry 14, no. 1: 117. https://doi.org/10.3390/sym14010117
APA StyleShehab, D. A., & Alhaddad, M. J. (2022). Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research. Symmetry, 14(1), 117. https://doi.org/10.3390/sym14010117






