Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators
Abstract
:1. Introduction
2. Related Work
2.1. ML and DL for DDoS Detection
2.2. Generative Adversarial Networks
2.3. Adversarial DDoS Attacks
2.4. Detection of Adversarial DDoS Attacks
3. Proposed Approach
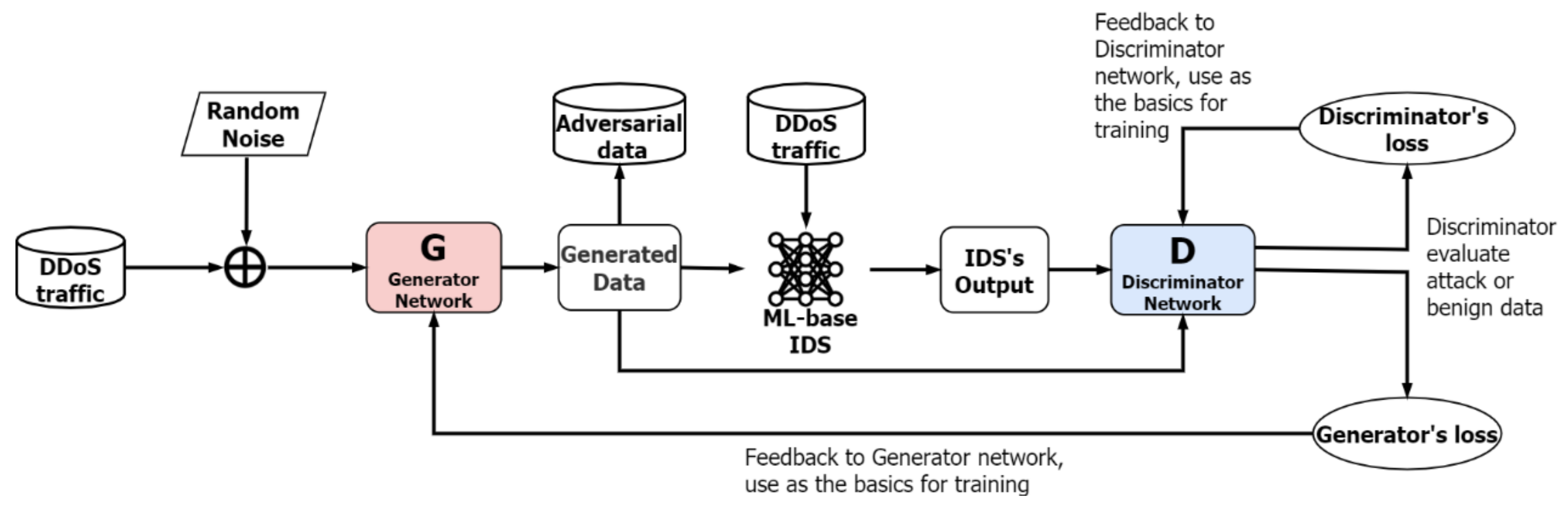
3.1. Synthesis of Adversarial DDoS Attacks Using GP-WGAN
| Algorithm 1 Training of the GP-WGAN. |
| Input: G: generator, D: discriminator, IDS: ML-based DDoS detectors B: benign traffic, A: DDoS traffic A, N: noise for adversarial disturbance Output: Trained GP-WGAN
|
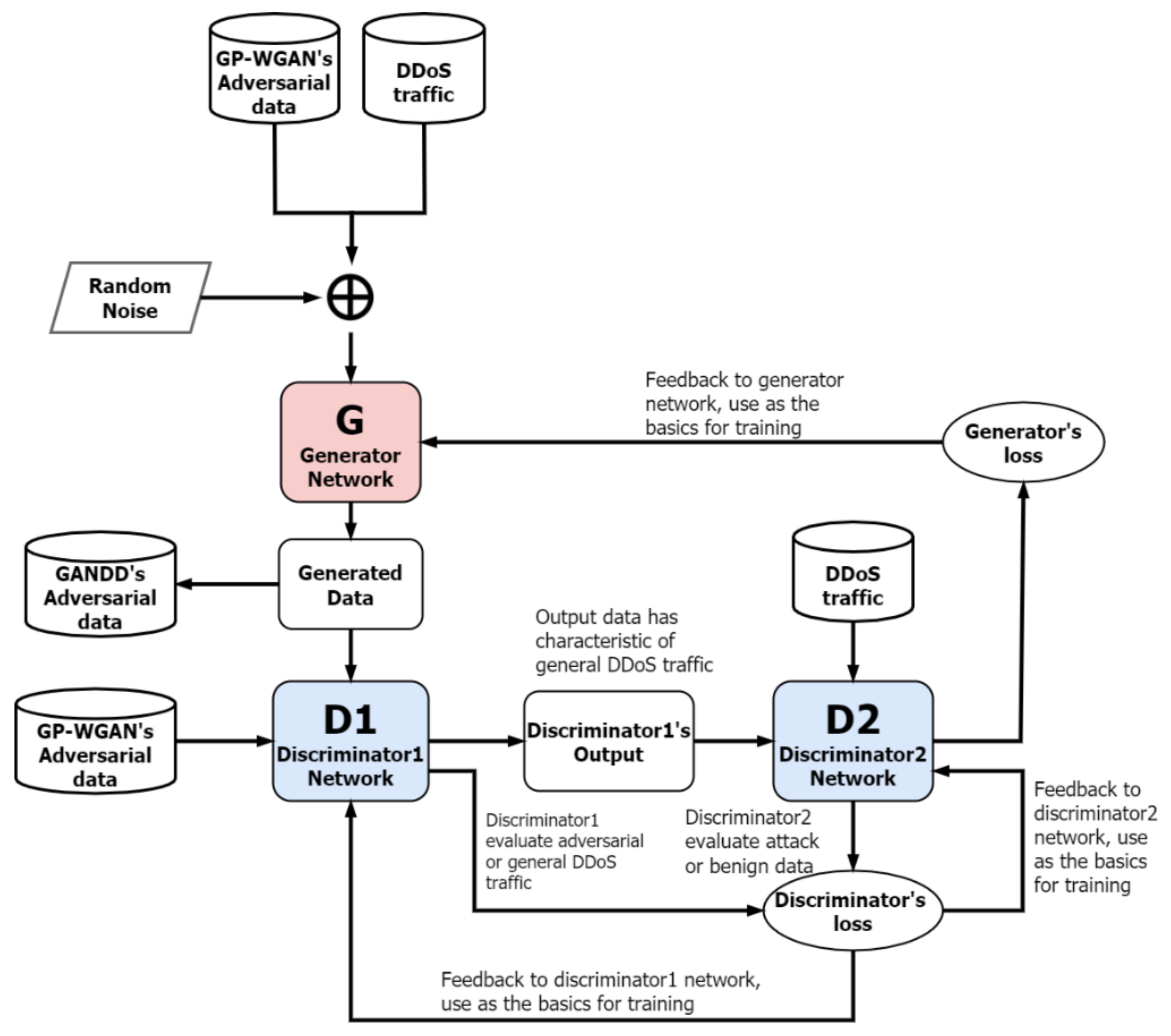
3.2. Detection of Adversarial DDoS Attacks Using GAN with Dual Discriminators (GANDD)
| Algorithm 2 Algorithm for GANDD |
| Input: G: generator, D1: discriminator1, D2: discriminator2, B: benign traffic, N: noise, A: normal DDoS Attack, E: adversarial attack generated by GP-WGAN Output: Trained GANDD |
|
4. Experiments Results and Discussion
- ML-based DDoS detection is highly effective
- Adversarial DDoS attacks can penetrate ML-based DDoS detection
- The proposed GANDD is capable of detecting adversarial DDoS attacks
4.1. Synthesis of Adversarial DDoS Attacks Using GP-WGAN
4.2. Synthesis of Adversarial DDoS Attacks Using GP-WGAN
4.3. Detection of Adversarial DDoS Attacks with GANDD
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Genie-Networks, DDoS Attack Statistics and Trends Report for 2020 and 2021. 2021. Available online: https://www.genie-networks.com/gnnews/ddos-attack-statistics-and-trends-report-for-h1-2020 (accessed on 12 October 2021).
- Bakr, A.; Ahmed, A.E.; Hefny, H.A. A Survey on mitigation techniques against DDoS attacks on cloud computing architecture. J. Adv. Sci. 2019, 28, 187–200. [Google Scholar]
- Priya, S.S.; Sivaram, M.; Yuvaraj, D.; Jayanthiladevi, A. Machine learning based DDoS detection. In Proceedings of the 2020 International Conference on Emerging Smart Computing and Informatics, Pune, India, 12–14 March 2020; pp. 234–237. [Google Scholar]
- Szegedy, C.; Zaremba, W.; Sutskever, I.; Bruna, J.; Erhan, D.; Goodfellow, I.; Fergus, R. Intriguing properties of neural networks. In Proceedings of the 2nd International Conference on Learning Representations, ICLR 2014, Banff, AB, Canada, 14–16 April 2014. [Google Scholar]
- Han, W.; Xue, J.; Wang, Y.; Zhu, S.; Kong, Z. Review: Build a roadmap for stepping into the field of anti-malware research smoothly. IEEE Access 2019, 7, 143573–143596. [Google Scholar] [CrossRef]
- Kong, Z.; Xue, J.; Wang, Y.; Huang, L.; Niu, Z.; Li, F. A Survey on Adversarial Attack in the Age of Artificial Intelligence. Wirel. Commun. Mob. Comput. 2021, 2021, 4907754. [Google Scholar] [CrossRef]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative adversarial networks. In Proceedings of the 27th International Conference on Neural Information Processing Systems, Montreal, QC, Canada, 8–13 December 2014; Volume 2, pp. 2672–2680. [Google Scholar]
- Arjovsky, M.; Chintala, S.; Bottou, L. Wasserstein generative adversarial networks. In Proceedings of the 34th International Conference on Machine Learning, Sydney, NSW, Australia, 6–11 August 2017; pp. 214–223. [Google Scholar]
- Gulrajani, I.; Ahmed, F.; Arjovsky, M.; Dumoulin, V.; Courville, A.C. Improved training of Wasserstein GANs. In Proceedings of the 31st International Conference on Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; pp. 5769–5779. [Google Scholar]
- Nguyen, T.D.; Le, T.; Vu, H.; Phung, D. Dual Discriminator Generative Adversarial Nets. In Proceedings of the Advances in Neural Information Processing Systems 30, Long Beach, CA, USA, 4–9 December 2017; pp. 2667–2677. [Google Scholar]
- Zhang, X.; Zhao, Y.; Zhang, H. Dual-discriminator GAN: A GAN way of profile face recognition. In Proceedings of the 2020 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), Dalian, China, 27–29 June 2020; pp. 162–166. [Google Scholar]
- Cheng, J.; Yin, J.; Liu, Y.; Cai, Z.; Wu, C. DDoS attack detection using IP address feature interaction. In Proceedings of the IEEE International Conference on Intelligent Networking and Collaborative Systems, Barcelona, Spain, 4–6 November 2009; pp. 113–118. [Google Scholar]
- Vu, N.H. DDoS attack detection using K-Nearest Neighbor classifier method. In Proceedings of the International Conference on Telehealth/Assistive Technologies, Baltimore, MD, USA, 16–18 April 2008; pp. 248–253. [Google Scholar]
- Fadlil, A.; Riadi, I.; Aji, S. Review of detection DDoS attack detection using naive bayes classifier for network forensics. Bull. Electr. Eng. Inform. 2017, 6, 140–148. [Google Scholar] [CrossRef]
- Wang, C.; Zheng, J.; Li, X. Research on DDoS attacks detection based on RDF-SVM. In Proceedings of the 10th International Conference on Intelligent Computation Technology and Automation, Changsha, China, 9–10 October 2017. [Google Scholar]
- Dincalp, U. Anomaly based distributed denial of service attack detection and prevention with machine learning. In Proceedings of the 2nd International Symposium on Multidisciplinary Studies and Innovative Technologies, Ankara, Turkey, 19–21 October 2018. [Google Scholar]
- Ahanger, T.A. An effective approach of detecting DDoS using artificial neural networks. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking, Chennai, India, 22–24 March 2017; pp. 707–711. [Google Scholar]
- Li, Y.; Lu, Y. LSTM-BA: DDoS detection approach combining LSTM and Bayes. In Proceedings of the 7th International Conference on Advanced Cloud and Big Data, Suzhou, China, 21–22 September 2019; pp. 180–185. [Google Scholar]
- Yang, K.; Zhang, J.; Xu, Y.; Chao, J. DDoS attack detection with AutoEncoder. In Proceedings of the IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–9. [Google Scholar]
- Li, Z.; Sun, C.; Liu, C.; Chen, X.; Wang, M.; Liu, Y. RCC-Dual-GAN: An Efficient Approach for Outlier Detection with Few Identified Anomalies. arXiv 2020, arXiv:2003.03609. [Google Scholar]
- Sun, D. A new mimicking attack by LSGAN. In Proceedings of the 2017 IEEE 29th International Conference on Tools with Artificial Intelligence, Boston, MA, USA, 6–8 November 2017. [Google Scholar]
- Hu, W.; Tan, Y. Generating adversarial malware examples for black-box attacks based on GAN. arXiv 2017, arXiv:1702.05983. [Google Scholar]
- Kolosnjaji, B.; Demontis, A.; Biggio, B.; Maiorca, D.; Giacinto, G.; Eckert, C.; Roli, F. Adversarial malware binaries: Evading deep learning for malware detection in executables. In Proceedings of the 2018 26th European Signal Processing Conference (EUSIPCO), Rome, Italy, 3–7 September 2018; pp. 533–537. [Google Scholar]
- Song, W.; Li, X.; Afroz, S.; Garg, D.; Kuznetsov, D.; Yin, H. Automatic generation of adversarial examples for interpreting malware classifiers. arXiv 2021, arXiv:2003.03100v3. [Google Scholar]
- Ebrahimi, M.; Zhang, N.; Hu, J.; Raza, M.T.; Chen, H. Binary black-box evasion attacks against deep learning based static malware detectors with adversarial byte-level language model. arXiv 2020, arXiv:2012.07994. [Google Scholar]
- IBM. Security: Adversarial Detection Module. CYBERSEC. 2020. Available online: https://www.ithome.com.tw/news/139848 (accessed on 12 October 2021).
- Canadian Institute for Cybersecurity. NSL-KDD. Available online: https://www.unb.ca/cic/datasets/nsl.html (accessed on 12 October 2021).
- Canadian Institute for Cybersecurity. IDS-2017. Available online: https://www.unb.ca/cic/datasets/ids-2017.html (accessed on 12 October 2021).
- University of California, Irvine, KDD Cup 1999 Data. Available online: http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 12 October 2021).
- Canadian Institute for Cybersecurity. CICFlowMeter. Available online: https://github.com/CanadianInstituteForCybersecurity/CICFlowMeter (accessed on 12 October 2021).








| Actual Predicted | Attack | Normal |
|---|---|---|
| Attack | TP (True Positive) | FP (False Positive) |
| Normal | FN (False Negative) | TN (True Negative) |
| Model | TPR | FPR | F1-Score |
|---|---|---|---|
| RF | 0.901 | 0.066 | 0.918 |
| KNN | 0.868 | 0.124 | 0.913 |
| SVM | 0.880 | 0.152 | 0.860 |
| Model | TPR | FPR | F1-Score |
|---|---|---|---|
| RF | 0.942 | 0.039 | 0.951 |
| KNN | 0.914 | 0.094 | 0.909 |
| SVM | 0.873 | 0.173 | 0.843 |
| Layer | Configuration |
|---|---|
| Input (Noise) | (None, 20) |
| Input (Normal DDoS) | (None, 41) |
| Concatenate Input (Normal DDoS, Noise) | (None, 61) |
| Dense | (None, 32) |
| Leaky ReLU | (None, 32) |
| Dense | (None, 8) |
| Leaky ReLU | (None, 8) |
| Dense | (None, 2) |
| Leaky ReLU | (None, 2) |
| Input (Noise) | (None, 20) |
| Input (Normal DDoS) | (None, 41) |
| Epoch/Batch Size | Learning Rate | Optimizer | Lambda | CRITIC_ITERS |
|---|---|---|---|---|
| 500/1024 | 0.000139 | Adam | 10 | 5 |
| NSL-KDD | CIC-IDS2017 | |
|---|---|---|
| RF | 0.024 | 0.097 |
| KNN | 0.013 | 0.066 |
| SVM | 0.006 | 0.004 |
| Layer | Configuration |
|---|---|
| Input (Adversarial DDoS Attack) | (None, 41) |
| Dense | (None, 32) |
| PReLU | (None, 32) |
| Dense | (None, 32) |
| PReLU | (None, 8) |
| Dense | (None, 8) |
| Dropout | (None, 8) |
| Dense | (None, 2) |
| PReLU | (None, 2) |
| Layer | Configuration |
|---|---|
| Input (Conventional DDoS Attack, Benign) | (None, 41) |
| Dense | (None, 32) |
| PReLU | (None, 32) |
| Dense | (None, 32) |
| PReLU | (None, 8) |
| Dense | (None, 8) |
| Dropout | (None, 8) |
| Dense | (None, 2) |
| PReLU | (None, 2) |
| Epoch/Batch Size | Learning Rate | Optimizer | Lambda | CRITIC_ITERS |
|---|---|---|---|---|
| 500/1024 | 0.000144 | Adam | 10 | 5 |
| Model | TPR | FPR | F1-Score |
|---|---|---|---|
| DNN | 0.924 | 0.068 | 0.929 |
| LSTM | 0.957 | 0.031 | 0.962 |
| GAN | 0.941 | 0.058 | 0.942 |
| GANDD | 0.985 | 0.041 | 0.971 |
| Model | TPR | FPR | F1-Score |
|---|---|---|---|
| DNN | 0.913 | 0.085 | 0.914 |
| LSTM | 0.928 | 0.063 | 0.932 |
| GAN | 0.955 | 0.096 | 0.925 |
| GANDD | 0.983 | 0.053 | 0.963 |
| DNN | LSTM | GAN | GANDD | |
|---|---|---|---|---|
| TPR | 0.087 | 0.117 | 0.106 | 0.843 |
| DNN | LSTM | GAN | GANDD | |
|---|---|---|---|---|
| TPR | 0.022 | 0.074 | 0.066 | 0.713 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shieh, C.-S.; Nguyen, T.-T.; Lin, W.-W.; Huang, Y.-L.; Horng, M.-F.; Lee, T.-F.; Miu, D. Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators. Symmetry 2022, 14, 66. https://doi.org/10.3390/sym14010066
Shieh C-S, Nguyen T-T, Lin W-W, Huang Y-L, Horng M-F, Lee T-F, Miu D. Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators. Symmetry. 2022; 14(1):66. https://doi.org/10.3390/sym14010066
Chicago/Turabian StyleShieh, Chin-Shiuh, Thanh-Tuan Nguyen, Wan-Wei Lin, Yong-Lin Huang, Mong-Fong Horng, Tsair-Fwu Lee, and Denis Miu. 2022. "Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators" Symmetry 14, no. 1: 66. https://doi.org/10.3390/sym14010066
APA StyleShieh, C.-S., Nguyen, T.-T., Lin, W.-W., Huang, Y.-L., Horng, M.-F., Lee, T.-F., & Miu, D. (2022). Detection of Adversarial DDoS Attacks Using Generative Adversarial Networks with Dual Discriminators. Symmetry, 14(1), 66. https://doi.org/10.3390/sym14010066









