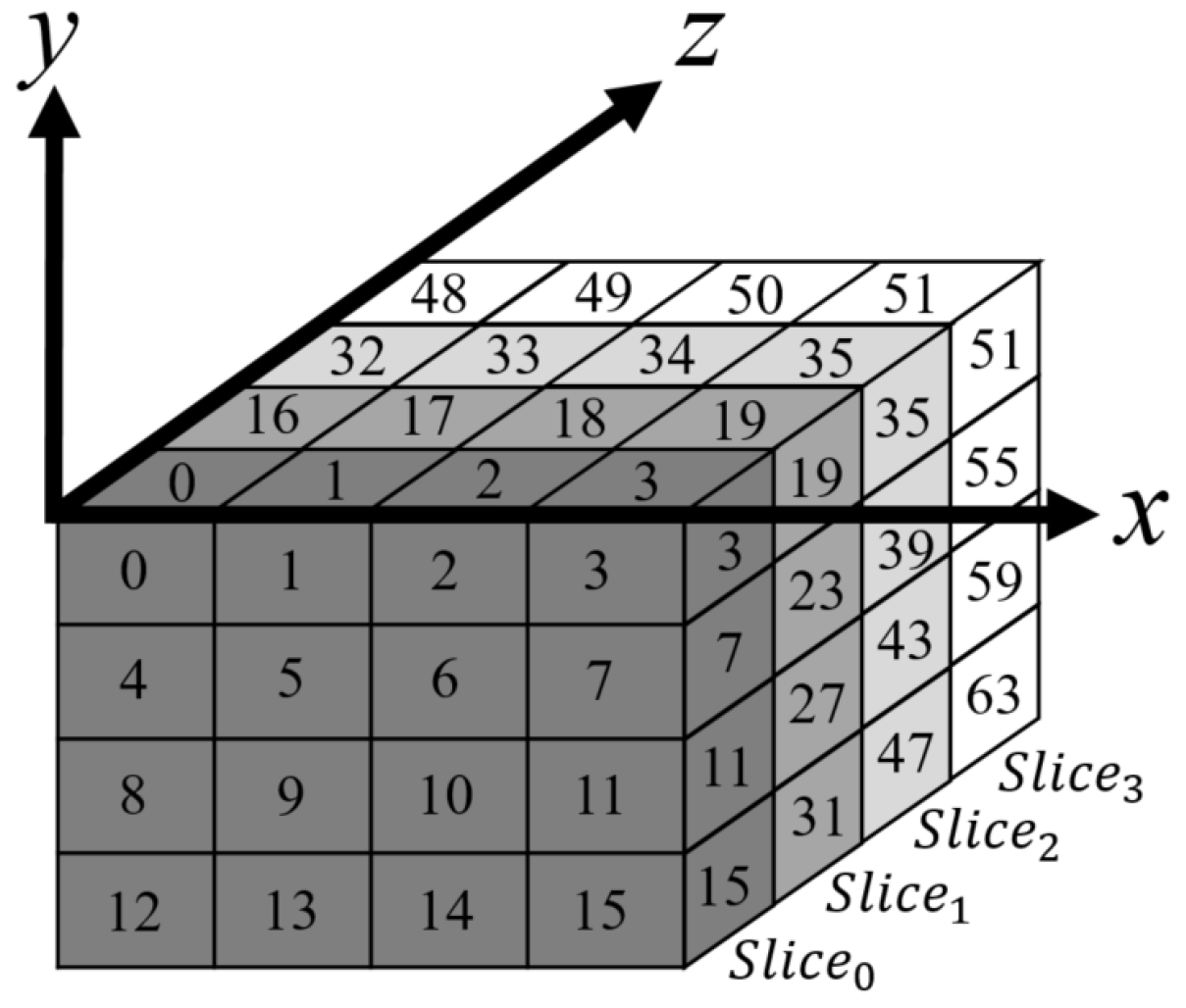
1. Introduction
Cyber security awareness has positively impacted the development of security products on the market. Most people have smartphones to communicate with, browse the Internet, read e-mails, and perform their jobs. According to predictions, the number of mobile users worldwide will likely increase to 7.26 billion by the end of 2022 [
1]. Regarding the potential for cyberattacks, almost everyone in the world needs security protection [
2]. Information security is crucial due to the interception and modification of data, which can lead to loss of availability, integrity, confidentiality, as well as other losses, such as loss of life, money, and assets [
3]. Therefore, encryption is an important tool in security products that must be associated with the smartphone to keep the user’s data safe.
Most mobile encryption applications available on the market rely on conventional standard encryption algorithms, such as the AES block cipher, which has been widely implemented in various industries for more than a decade due to its security strengths [
4]. Since then, numerous block cipher algorithms have been developed, using AES as the design foundation and the security benchmark. Performance evaluations of encryption algorithms in mobile devices have been conducted by comparing cryptographic algorithms, such as AES, DES, TEA, RSA, and REA [
5]. The experimentation results revealed that AES recorded the fastest execution speed for the encryption process. However, a conventional algorithm, such as AES, requires huge memory and high power consumption, which is not practical to be implemented in the software encryption application [
6]. Therefore, there is an important need for a lightweight algorithm design that uses simple cryptographic operations to provide sufficient security to the devices while emphasizing efficiency.
Over the years, a range of lightweight algorithms have been proposed in the literature that include BRIGHT [
7], CRAFT [
8], ACT [
9], LRBC [
10], LWE [
11], PriPresent [
12], T-TWINE [
13], LBC-IoT [
14], and improved SM4 [
15]. Although lightweight algorithm research has been intensively explored using multiple techniques that aim for better efficiency, their security features cannot be ignored [
16]. An algorithm should offer confusion and diffusion characteristics to provide sufficient security [
17]. Confusion obscures the relationship between the plaintext and ciphertext with the substitution method, while diffusion spreads the plaintext statistics through the ciphertext using the permutation method.
One solution to enhance the confusion and diffusion characteristics of a cryptographic algorithm is by implementing the three-dimensional (3D) design on the block cipher. The 3D design invention was introduced by Nakahara [
18], who adopted the model on the AES algorithm. It has been experimentally demonstrated that the deployment of the 3D cipher design can strengthen the security of the AES with provided confusion and diffusion to the algorithm. An alternative 3D design approach has similarly been suggested by Suri and Deora [
19] using a 3D rotation block cipher that produced random outputs. Later on, Ariffin et al. [
20] constructed a 3D−AES using an immune-inspired approach that passed all statistical tests. In another work, Mala [
21] improved the encryption acceleration of the 3D block cipher using a unified byte permutation. Next, Wang and Jin [
22] developed a non-alternate 3D model that was immune to differential and linear attacks. In 2019, Mushtaq et al. [
23] employed 3D hybrid cubes that did not correlate the input and output. Recently, Zakaria et al. [
24] increased the security strength of the RECTANGLE cipher with a 3D bit rotation function.
While the security strength of the block cipher could be improved by adopting the 3D design, there is an issue that needs to be resolved for the method to be applicable. The 3D design forces the algorithm to increase the block size and enlarge the key bits, thus decreasing its efficiency. An algorithm with large blocks and key sizes is not the best option for mobile encryption applications. Due to the above justifications, we propose a new algorithm called LAO-3D, which was developed using an enhanced 3D cipher design to balance its efficiency and security strength. Three contributions can be highlighted in this research. Firstly, the proposed algorithm does not require increasing the block and key sizes of the cipher, which solved the scalability issue highlighted in the previous 3D algorithms. Secondly, the new algorithm provides a better bit permutation for the algorithm. Thirdly, the analyses conducted on the algorithm prove its security strength and performance, which meets the criteria of a lightweight algorithm that require sufficient security strength and is efficient for mobile encryption application.
The research presented in this paper is divided into five major sections.
Section 1 introduces the scope of this research.
Section 2 specifies the 3D cipher design architecture.
Section 3 details the proposed LAO-3D block cipher.
Section 4 performs the security analysis, performance test, and implementation of the proposed algorithm in a mobile encryption application.
Section 5 concludes the overall research work.
4. Security Analysis, Performance Test, and Application
This section presents the security analyses performed in assessing the full 20 rounds of the proposed LAO-3D block cipher. The evaluation methods were implemented to distinguish the strength of the lightweight block cipher and possibly be used in various cryptographic primitives.
A decent algorithm must establish a complex relationship between the plaintext, ciphertext, and key, which is called confusion. The encryption method must also scatter the plaintext modifications over the entire ciphertext, which is called diffusion [
27]. Any encryption algorithm should provide both confusion and diffusion properties to ensure information security. Confusion is obtained through substitution; meanwhile, diffusion is achieved with permutation operations. Confusion and diffusion will produce a certain randomness degree in the block cipher such that no ciphertext pattern can be recognized.
To evaluate the confusion and diffusion properties, three analyses were executed on the proposed block cipher—the correlation coefficient, bit error, and key sensitivity tests. In addition, a randomness evaluation was performed to examine the randomness characteristics of the algorithm. Finally, two cryptanalysis attacks were carried out to observe the strength of the LAO-3D block cipher.
Apart from the security analysis, a performance test was conducted to measure the speed, throughput, and required cycles per byte to execute the encryption. For benchmarking purposes, the experimental results were compared with existing lightweight block ciphers, such as GIFT, KATAN, KLEIN, LED, LRBC, PRESENT, PRINCE, PRINT, QTL, RECTANGLE, SIMECK, SPECK, and TEA. These algorithms were chosen because of their similarity in terms of block and key sizes that were no bigger than 64 bits and 128 bits, respectively, to distinguish their security strengths and performances within the same lightweight category.
In order to demonstrate the implementation of the LAO-3D lightweight block cipher, a mobile encryption application was developed to observe the functionality of the proposed algorithm. The application was built using C++ programming on Microsoft Visual Studio 2008 and Android Studio development software.
4.1. Correlation Coefficient Test
The avalanche effect examines the non-linear properties of a cipher. A non-linear transformation provides a confusion characteristic that relies on the generated output from a particular input data. The correlation coefficient, bit error, and key sensitivity experiments were carried out to monitor the avalanche effect of the block cipher. For the sample generation, a pseudorandom bit generator was used to produce the keys and plaintexts. The avalanche effect,
, is defined in the following equation.
where
s is the plaintext/ciphertext length, while
and
are the
positions of the plaintext and ciphertext bits for
.
The correlation coefficient analyzes the non-linear relationship between plaintext and ciphertext [
28]. The correlation coefficient,
R, is able to discriminate the effect of confusion on the block cipher. The coefficient values range from −1 to +1, where the acceptable result ranges are shown in
Table 5.
For the expression of the correlation coefficient,
R, refer to the following equation:
where
represents the avalanche effect from (6),
indicates the
plaintext bit, and
defines the
ciphertext bit for
.
The correlation values from the analysis conducted on the plaintext and ciphertext were remarked. A total of 1000 random plaintexts and five random keys were examined on the algorithm.
Figure 14 displays the scatter charts of the analysis results. The values in the charts are plotted according to the computed correlation coefficient based on the key and plaintext inputs.
A summary of the results presented in the scatter charts is shown in
Table 6. According to the experimental results, the LAO-3D block cipher offers performance advantages (98.2% of the correlation coefficients, in the range
and
), indicating a weak linear relationship. The results generated by all five keys show that the adoption of the 3D cipher design on the LAO-3D block cipher provided high correlation coefficient characteristics.
4.2. Bit Error Test
The bit error computes the differences in the ciphertext affected by the plaintext modifications. The number of changed ciphertext bits after modification of a plaintext bit is defined as the bit error. For the bit error test, the optimum result is 0.5 or 50% plaintext bit alterations [
29]. The formulation of the bit error rate,
, is defined in the following equation.
The purpose of the bit error test is to measure the relationship between plaintext and ciphertext. A random key and five random plaintexts were used to examine the LAO-3D block cipher. As seen in
Figure 15, the experimental results are presented in the scatter charts. The data plots in each chart display the bit error values that represent the changes of ciphertext upon plaintext modifications.
An overall summarization of the bit error results presented in the scatter charts is shown in
Table 7. After modifying the plaintext bits, the
of the LAO-3D block cipher is more likely to be close to 0.5. The results generated by all five plaintexts prove that the LAO-3D block cipher achieved optimum bit error test results.
By carefully examining the data, it is found that the LAO-3D block cipher obtains an average 50% bit error rate, which verifies that the ciphertext is entirely modified with a single alteration in the plaintext bit.
Table 8 presents the comparison of the avalanche effect on the modification of the plaintext against existing block ciphers [
10]. The results achieved by the proposed LAO-3D surpass the earlier works in terms of non-linearity between the plaintext and its corresponding ciphertext.
4.3. Key Sensitivity Test
The key sensitivity test examines the affected ciphertext upon key alteration [
30]. An algorithm has a high-security level against the key sensitivity attack if changing a small portion of the key will cause major modifications on the ciphertext bits. During the observation of key sensitiveness, the key bit is manipulated by changing one bit from its first to the last bit position.
The bit error rate equation is applied to compute the experimental results. The result of a decent cryptographic algorithm must be close to 0.5 or 50% of the total ciphertext bit modification. In this experiment, a random plaintext and five random keys were included to examine the LAO-3D block cipher. The scatter charts of the experimental results are shown in
Figure 16.
Table 9 summarizes the key sensitivity experimental results presented in the scatter charts. On average, the proposed LAO-3D block cipher obtained 32-bit differences with an approximate 50% bit error rate. The results suggest that LAO-3D has a non-linear relationship between the key and ciphertext that represents a high key sensitivity on the ciphertext.
Similar observations were made on the key alteration while retaining a constant plaintext performed against other algorithms [
10], presented in
Table 10. The 50% key sensitivity result denotes that the entire key bits have an impact on every ciphertext bit. Based on the findings, the LAO-3D block cipher showed some improvements over the existing works on the avalanche effect of the key sensitivity.
4.4. Randomness Test
The randomness of the proposed LAO-3D block cipher was tested using 15 statistical tests of the NIST Special Publication 800-22 [
31]. The NIST accommodates an open-source randomness test application called NIST Statistical Suite. The randomness test application is aimed at varieties of non-random characteristics from the generated ciphertext.
Eight tests inclusive of random excursion (8 p-values), random excursion variant (18 p-values), cumulative sums (2 p-values), binary matrix rank (1 p-value), longest runs of ones (1 p-value), frequency (1 p-value), spectral DFT (1 p-value), and runs (1 p-value) are classified as the non-parameterized tests.
Seven other tests, i.e., non-overlapping (148 p-values), serial (2 p-values), linear complexity (1 p-value), maurer’s universal (1 p-value), approximate entropy (1 p-value), overlapping templates (1 p-value), and block frequency (1 p-value) are labeled as parameterized tests that require parameter inputs.
A significant level, , must be set within 0.1% (0.001) to 1% (0.01) before assessing the randomness test. Moreover, the sample size should at least be the inverse of the significant level ( samples). For the test results, the ciphertext is regarded as random if the p-value . Conversely, if the p-value , the ciphertext is determined as not random.
Equation (
9) defines the proportion of test samples that will determine the randomness of an algorithm.
where
s symbolizes the size of the test sample (1000 ciphertexts) and
indicates the significance level (0.01) that is used in this paper. If the total rejection exceeds the computed proportion
, the sample is regarded as not random.
Nine data categories of block cipher were implemented to generate the keys and plaintexts. Every data category generated unique 1000 samples where each sample consisted of 2081 to 15,744 ciphertexts that equaled 133,184 to 1,007,616 bits of data with a size range of 127 to 960 MB. The block and key lengths determine the total number of blocks for each sample [
32]. The blocks were derived by appending the ciphertexts to establish large bit sequences.
Table 11 listed each of the data categories that generate multiple lengths of derived ciphertext bits based on the input data. All 15 statistical tests can be applied to evaluate CBC, PCC, RPRK, SPA, and SKA data categories [
33]. Due to insufficient data lengths, only 11 tests could be used to examine HDK and LDK, and 10 tests for HDP and LDP.
The experimental results demonstrate that the LAO-3D block cipher passed all data categories and statistical tests as shown in
Table 12 and
Table 13. In addition, the
p-values produced by the block cipher from the NIST Statistical Suite are uniformly distributed since the values are larger than 0.0001, as shown in
Table 14 and
Table 15. The 100% passing rate achieved in the randomness and uniformity test results verified the randomness characteristics of the cipher output. Combinations of substitution and permutation components in LAO-3D have optimized the confusion and diffusion properties of the algorithm that contribute to the randomization of the ciphertext.
4.5. Differential and Linear Cryptanalysis
A cryptanalysis attack is an experimental method used to distinguish a cryptosystem from a random function [
34]. To ensure that the confidentiality of the proposed LAO-3D output is robust, it is necessary to examine the security strength of the algorithm against a variety of attack types. Differential cryptanalysis (DC) and linear cryptanalysis (LC) are methods used to attack cryptographic algorithms, thereby, it is important to consider a secure cipher to withstand these attacks.
To apply differential cryptanalysis on an
n-bit block cipher, a predictable difference has to be propagated in all (except for a few) rounds with probabilities greater than
. For the LAO-3D block cipher to be immune to differential cryptanalysis, there should be no difference propagation with a probability higher than
.
Table 16 represents the differential trails with the optimal probability for six rounds of LAO-3D that are depicted in
Figure 17.
The highest probability of difference propagation found in the sixth round is
, which is lower than
. Differential cryptanalysis results of lightweight block ciphers are shown in
Table 17. An effective differential distinguisher with more than five rounds for the algorithm was impossible to be constructed; the 20-round LAO-3D is sufficient to resist differential cryptanalysis.
To apply linear cryptanalysis on an
n-bit block cipher, there should be a predictable linear propagation overall but a few rounds with a significant amplitude greater than
. For the LAO-3D block cipher to be immune to linear cryptanalysis, there should be no linear propagation with an amplitude greater than
.
Table 18 represents the linear trails with the optimal bias for seven rounds of LAO-3D that are depicted in
Figure 18.
The highest probability of linear propagation at the seventh round is
, which is lower than
. Linear cryptanalysis results of block ciphers are shown in
Table 17. The clustering of linear trails of LAO-3D is limited and it is impossible to construct an effective linear propagation over six rounds. Hence, the 20-round LAO-3D is sufficient to resist linear cryptanalysis.
For a comparison with other existing lightweight algorithms,
Table 19 shows the number of active differential and linear S-boxes of seven encryption rounds. The results show that the LAO-3D block cipher has higher active S-boxes from the second round onward. Referring to
Table 17 [
35,
36] and
Table 19 [
37], LAO-3D recorded the lowest allowable probabilities of differential trails (
) with 17 active S-boxes at the fifth round. In addition, LAO-3D achieved the lowest allowable correlation potentials of linear trails (
) at the sixth round with 11 active S-boxes. Therefore, LAO-3D has a high-security strength and is resistant to differential and linear attacks.
4.6. Performance Test
The proposed LAO-3D was implemented using C++ on an Intel(R) Core(TM) i7 2.70 GHz CPU with 8 GB RAM on Windows 10. Speed tests were conducted on the execution process of the proposed LAO-3D and compared with other existing algorithms. The speed tests were carried out on the full rounds of each encryption algorithm to observe the time required to process a ciphertext block that consisted of 64-bit data. In addition, the throughput tests evaluate the impact of cipher design such as the key size, block size, number of rounds, and encryption components on the algorithm throughput.
The performance of a cryptographic algorithm is determined by evaluating the running speed that can be measured by the average encryption time, encryption throughput, and the required number of cycles to encrypt one byte or block plaintext, which permits researchers to compare the running speeds of different algorithms working on different platforms. The encryption throughput and the number of cycles are defined in the following equations.
Table 20 shows that the LAO-3D block cipher achieved a better performance against the other competitors in terms of execution speed and throughput [
38]. Factors that contribute to the results are the number of encryption rounds and the components of the algorithm. LAO-3D has low encryption rounds with optimum component operations. Substitution (SubColumn) and permutation (Double3DRotation) functions of the proposed block cipher ensure security without the need for implementing a high number of encryption rounds. These findings are supported by the security analysis results presented in previous sections. Therefore, these observations justify that the performance of the proposed algorithm is competitive and suitable to be applied in mobile encryption applications.
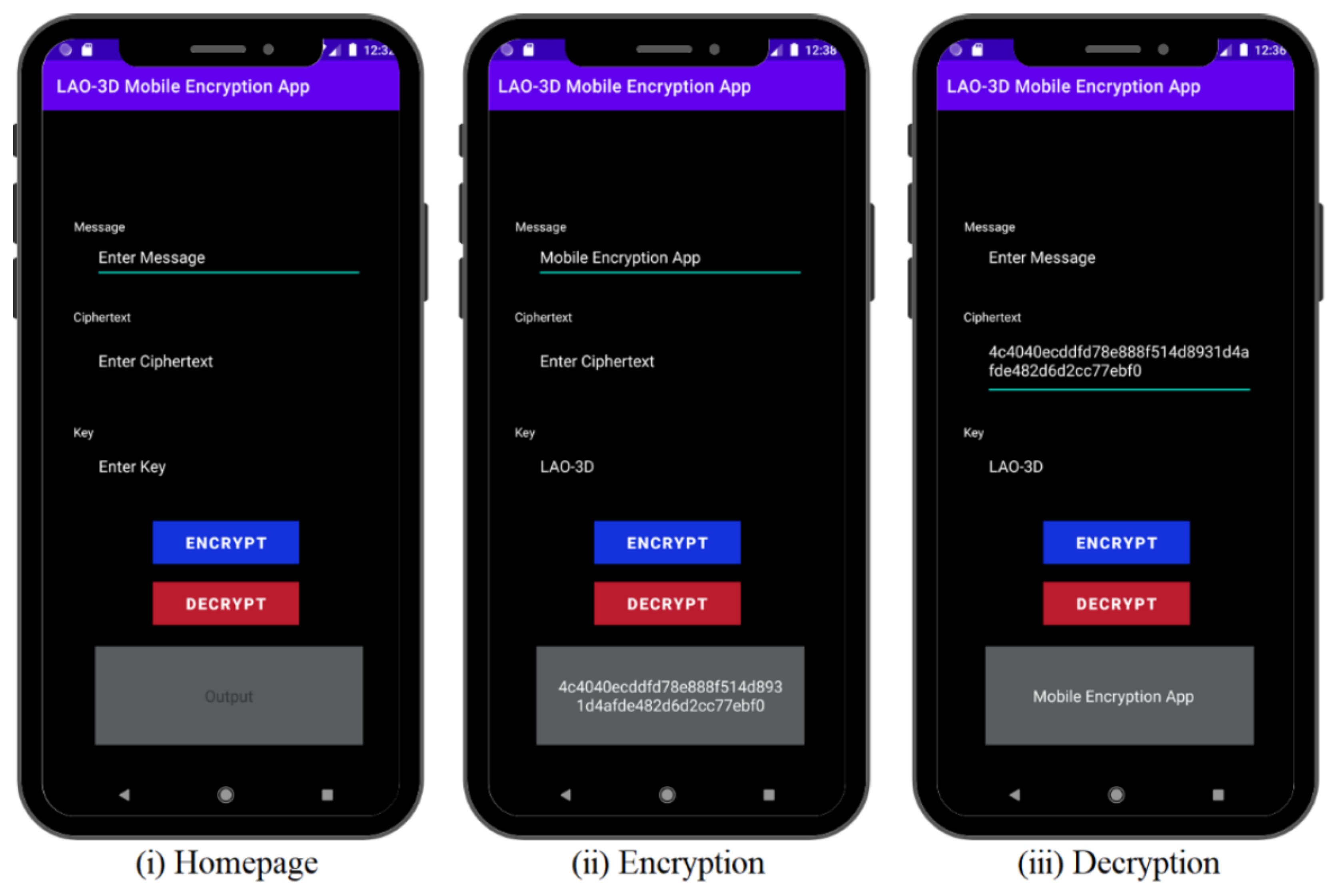
4.7. Mobile Encryption Application
This section presents the implementation of the LAO-3D lightweight block cipher on the mobile encryption application that was built using Android Studio (Bumblebee 2021.1.1) development software. Three steps are required to use the application—entering the encryption key, entering the message, and executing the data encryption in the mobile encryption application, as shown in
Figure 19. Meanwhile, the decryption process requires entering the decryption key, entering the ciphertext, and executing the data decryption. Apart from the security analysis and performance test presented in
Section 4, the development of the mobile encryption application proved the functionality of the proposed LAO-3D lightweight block cipher in a real application.