Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN
Abstract
1. Introduction
2. Related Work
- For the in-vehicle network lack strong security mechanisms, we propose an identity-based certificateless framework that considers device updates and maintenance;
- According to the specification of our proposed protocol, we use CPN Tools to formally model the proposed protocol and complete the model consistency verification;
- We employ a protocol model detection method that combines the Colored Petri Nets (CPN) theory and the Dolev–Yao attack model for security evaluation of the proposed protocol.
3. Background
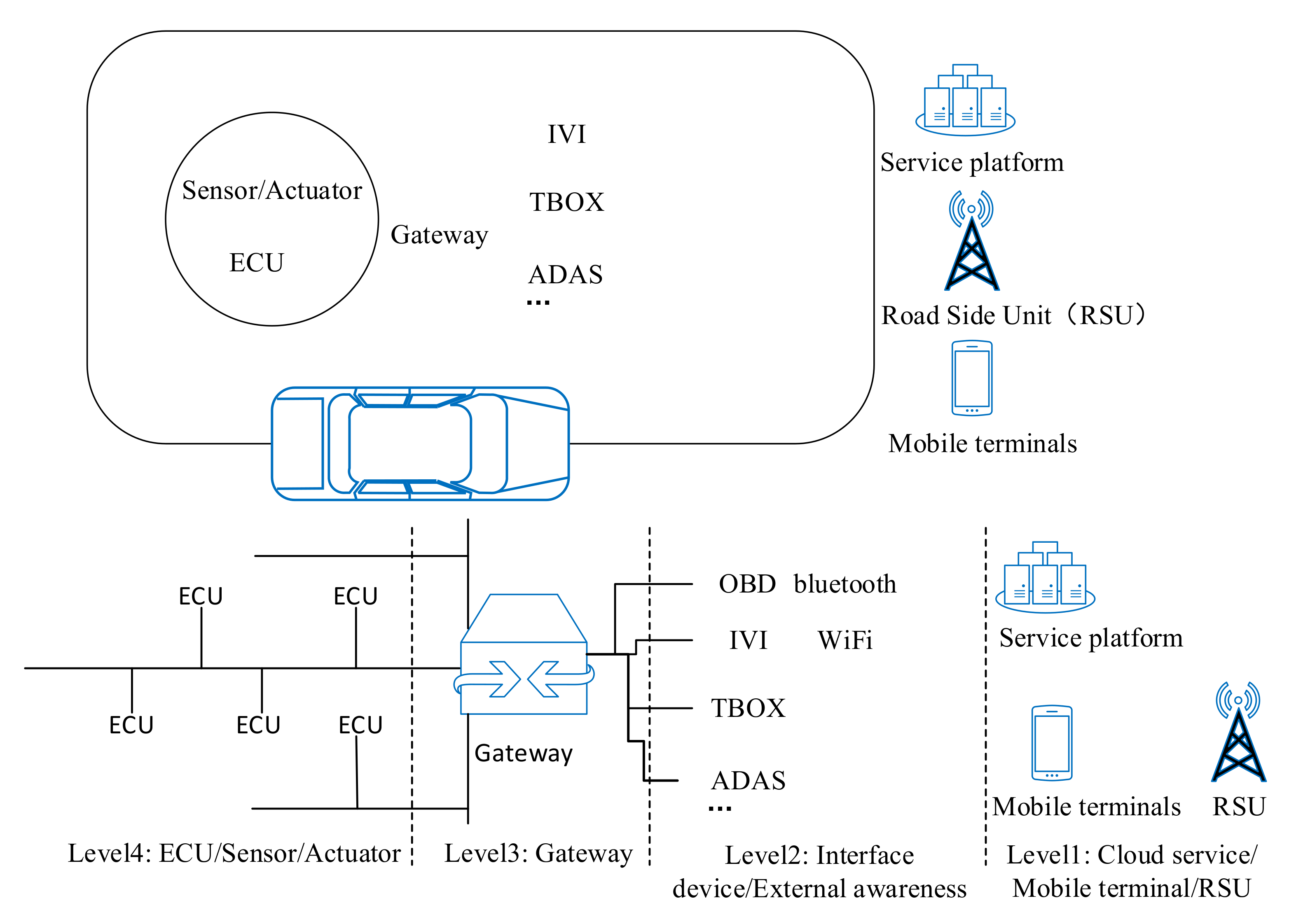
3.1. Vehicle Architecture
3.2. Identity-Based Encryption
3.3. CPN Tools
- ProVerif is a protocol security detection tool based on logic programming, which can calculate the attack path. However, it only contains one attack path, and the calculated attack path is not comprehensive, which makes it difficult for the modeler to extract attack nodes;
- Scyther is a protocol model detection tool with high performance and has the function of multiple path analysis. However, it uses the same algorithm to analyze all security protocols. Although the attack path can be found, the error rate is high, and the attack path cannot be comprehensively found for more complex protocols;
- Tamarin Prover has a powerful state space search capability, which can collect all the state space of the protocol execution and analyze it, but the establishment of the protocol model is not intuitive, and cannot provide the observer with an intuitive description of the protocol execution.
3.4. Dolev–Yao Attacker Model
- The cryptographic system is absolutely secure; the security protocol itself is distinguished from the cryptographic mechanism used within the security protocol. We do not research the security of the specific cryptographic algorithms of the protocol but take the inherent security properties of the protocol as the research goal;
- The attacker can act as one of the legitimate entities and can communicate with the entities in the protocol;
- Attackers have powerful computing power and can eavesdrop, block and intercept, replay, and tamper with all information in the system network;
- Attackers can store, encrypt, decrypt, synthesize, and decompose the intercepted information and participate in the protocol interaction process as a legal entity;
- If the attacker obtains the corresponding key, the attacker can decrypt the ciphertext.
4. Modeling of Vehicle Safety Protocol Framework
4.1. The Message Flow Model of the Protocol
4.1.1. Initialization Stage
- The MC defines the serial number SNi for each ECU, defines the effective period Ti, and generates the identity of the ECUi as IDECUi = (Ti||SNi);
- The MC defines the serial number SNSM and generates the identity of the SM as IDSM = (Ti||SNSM).
- MC selects a large prime number q, G1 and G2 are two groups of large prime numbers q, and defines the bilinear map e: G1 × G1 → G2;
- MC selects the random number s ∈ Z*q as the master key, defines a random number generator P ∈ G1, and generates the public key PK = sP of the system;
- MC defines the hash H1: {0,1} * → Z*q, H2: {0,1} * × G1 × G2 → Z*q, H3: G2 → {0,1} n;
- MC generates system parameters p = {q, G1, G2, e, n, g, PK, H1, H2}.
- MC generates the private key for each ECUi as SECUi = H1(IDECUi)s;
- MC generates the private key for SM as SSM = H1(IDSM)s.
4.1.2. Protocol Process Stage
- SM selects a random number, n0, generates the message , selects a random number r, generates U and W. SM uses the public key to calculate , generates the ciphertext , calculates the hash value , and uses the private key to calculate the signature , SM encapsulates the ciphertext , signature , to message request, and sends it to ECUi.
- ECUi uses the private key to calculate , calculates . ECUi calculates the hash value , and uses the public key to verify the signature .
- ECUi selects a random number, n1, and the key Ksym generates the message , uses the public key to calculate . ECUi generates the ciphertext , calculates the hash value , and uses the private key to calculate the signature . ECUi encapsulates the ciphertext , signature to message respond and sends it to the SM.
- SM uses the private key to calculate , generates . SM calculates the hash value , and uses the public key to verify the signature .
- SM selects the message to be sent, calculates the hash value , encrypts it with the key Ksym, generates the message , and sends it to ECUi.
- ECUi decrypts with the key Ksym to get the message , calculates the hash value and verifies the data.
4.2. Modeling the Protocol Based on CPN
4.3. The Attacker Model of the Protocol
5. Model Consistency and Security Evaluation of the Protocol
6. Security Analysis and Performance Analysis
6.1. Security Analysis
6.2. Performance Analysis
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lo Bello, L.; Mariani, R.; Mubeen, S. Recent Advances and Trends in On-Board Embedded and Networked Automotive Systems. IEEE Trans. Ind. Inform. 2019, 15, 1038–1051. [Google Scholar] [CrossRef]
- Inam, M.; Li, Z.; Asghar, A. A Novel Protocol for Vehicle Cluster Formation and Vehicle Head Selection in Vehicular Ad-hoc Networks. Electron. Inf. Eng. 2019, 10, 103–119. [Google Scholar]
- Zhang, H.; Meng, X.; Zhang, X. CANsec: A Practical in-Vehicle Controller Area Network Security Evaluation Tool. Sensors 2020, 20, 4900. [Google Scholar] [CrossRef] [PubMed]
- Xiao, L.; Lu, X.; Xu, T. Reinforcement Learning-Based Physical-Layer Authentication for Controller Area Networks. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2535–2547. [Google Scholar] [CrossRef]
- Ying, X.; Bernieri, G.; Conti, M. Covert Channel-Based Transmitter Authentication in Controller Area Networks. IEEE Trans. Dependable Secur. Comput. 2022, 19, 2665–2679. [Google Scholar] [CrossRef]
- Bella, G.; Biondi, P.; Costantino, G. TOUCAN: A protocol to secure Controller Area Network. 2021. In Proceedings of the ACM Workshop on Automotive Cybersecurity, Richardson, TX, USA, 27 March 2019; pp. 3–8. [Google Scholar]
- Aliwa, E.; Rana, O.; Perera, C. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Hartzell, S.; Stubel, C.; Bonaci, T. Security Analysis of an Automobile Controller Area Network Bus. IEEE Potentials 2020, 39, 19–24. [Google Scholar] [CrossRef]
- Yan, R.; Dunnett, S.J.; Jackson, L.M. Model-Based Research for Aiding Decision-Making During the Design and Operation of Multi-Load Automated Guided Vehicle Systems. Reliab. Eng. Syst. Saf. 2022, 219, 108264. [Google Scholar] [CrossRef]
- Daohua, W.; Debiao, L.; Tao, T. Qualitative and Quantitative Safety Evaluation of Train Control Systems (CTCS) with Stochastic Colored Petri Nets. IEEE Trans. Intell. Transp. Syst. 2022, 23, 10223–10238. [Google Scholar]
- Koscher, K.; Czeskis, A.; Roesner, F. Experimental security analysis of a modern automobile. In Proceedings of the 2010 31st IEEE Symposium on Security and Privacy (S & P 2010), Berleley/Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Szilagyi, C.; Koopman, P. Flexible multicast authentication for time-triggered embedded control network applications. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks, Lisbon, Portugal, 29 June–2 July 2009; pp. 165–174. [Google Scholar]
- Szilagyi, C.; Koopman, P. Low cost multicast authentication via validity voting in time-triggered embedded control networks. In Proceedings of the 5th Workshop on Embedded Systems Security, Scottsdale, AZ, USA, 24 October 2010. [Google Scholar]
- Lin, C.W.; Sangiovannin, V.A. Cyber-security for the Controller Area Network (CAN) communication protocol. In Proceedings of the 2012 ASE International Conference on Cyber Security, Washington, DC, USA, 14–16 December 2012; pp. 1–7. [Google Scholar]
- Herrewege, A.V.; Singelee, D.; Verbauwhede, I. CANAuth-A Simple, Backward Compatible Broadcast Authentication Protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography, Louvain-la-Neuve, Belgium, 28–29 November 2011. [Google Scholar]
- Groza, B.; Murvay, S. Efficient Protocols for Secure Broadcast in Controller Area Networks. IEEE Trans. Ind. Inform. 2013, 9, 2034–2042. [Google Scholar] [CrossRef]
- Wang, Q.; Sawhney, S. VeCure: A practical security framework to protect the CAN bus of vehicles. In Proceedings of the 2014 International Conference on the Internet of Things (IOT 2014), Cambridge, MA, USA, 6–8 October 2014; pp. 13–18. [Google Scholar]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2014, 16, 993–1006. [Google Scholar] [CrossRef]
- Mun, H.; Han, K.; Lee, D.H. Ensuring Safety and Security in CAN-based Automotive Embedded Systems: A Combination of Design Optimization and Secure Communication. IEEE Trans. Veh. Technol. 2020, 69, 7078–7091. [Google Scholar] [CrossRef]
- Palaniswamy, B.; Camtepe, S.; Foo, E. An Efficient Authentication Scheme for Intra-Vehicular Controller Area Network. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3107–3122. [Google Scholar] [CrossRef]
- Mundhenk, P.; Paverd, A.; Mrowca, A. Security in Automotive Networks: Lightweight Authentication and Authorization. ACM Trans. Des. Autom. Electron. Syst. 2017, 22, 1084–4309. [Google Scholar] [CrossRef]
- Groza, B.; Murvay, P.S. Identity-Based Key Exchange on In-Vehicle Networks: CAN-FD & FlexRay. Sensors 2019, 19, 4919. [Google Scholar]
- Han, M.; Wan, A.; Zhang, F. An Attribute-Isolated Secure Communication Architecture for Intelligent Connected Vehicles. IEEE Trans. Intell. Veh. 2020, 5, 545–555. [Google Scholar] [CrossRef]
- Jeong, W.; Choi, E.; Choi, J.W. Autocorrelation-based Intrusion Detection System for Controller Area Network (CAN). J. Inst. Control. Robot. Syst. 2021, 27, 92–97. [Google Scholar] [CrossRef]
- Musuroi, A.; Groza, B.; Popa, L.; Murvay, P.S. Fast and Efficient Group Key Exchange in Controller Area Networks (CAN). IEEE Trans. Veh. Technol. 2021, 70, 9385–9399. [Google Scholar] [CrossRef]
- Lin, H.; Du, L. Optimization and Simulation of Controller Area Network Communication Model Based on Industrial Internet of Things Platform. Complexity 2020, 2020, 1076–2787. [Google Scholar] [CrossRef]
- Gu, Y.; Liu, J.; Li, X.; Chou, Y.; Ji, Y. State space model identification of multirate processes with time-delay using the expectation maximization. J. Frankl. Inst. 2019, 356, 1623–1639. [Google Scholar] [CrossRef]
- Wu, Y.; Feng, T. An Anonymous Authentication and Key Update Mechanism for IoT Devices Based on EnOcean Protocol. Sensors 2022, 22, 6713. [Google Scholar] [CrossRef] [PubMed]
- Assaf, G.; Heiner, M.; Liu, F. Coloured fuzzy Petri nets for modelling and analysing membrane systems. Biosystems 2022, 212, 104592. [Google Scholar] [CrossRef] [PubMed]
- Yao, L.; Liu, J.; Wang, D. Formal Analysis of SDN Authentication Protocol with Mechanized Protocol Verifier in the Symbolic Model. Int. J. Netw. Secur. 2018, 20, 1125–1136. [Google Scholar]
- Liu, Z.; Liu, J. Formal verification of blockchain smart contract based on colored petri net models. In Proceedings of the 2019 International Computer Software and Applications Conference, Milwaukee, WI, USA, 15–19 July 2019; pp. 555–560. [Google Scholar]
- Dolev, D.; Yao, C. On the security of public key protocols. IEEE Trans. Inf. Theory 1981, 29, 198–208. [Google Scholar] [CrossRef]
- Wu, Y.; Feng, T. Formal Security Analysis and Improvement Based on LonTalk Authentication Protocol. Secur. Commun. Netw. 2022, 2022, 8104884. [Google Scholar]
- Gong, X.; Feng, T. Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things. Sensors 2022, 22, 7191. [Google Scholar] [CrossRef]















| Main Contribution | Drawbacks | |
|---|---|---|
| Szilagyi et al. [12] | Proposed a time-triggered message authentication protocol | Real-time performance is not considered |
| Koopman and Lin et al. [13,14] | Proposed authentication protocols based on symmetric encryption | The cost of computation is not considered |
| Van et al. [15] | Proposed a broadcast authentication protocol based on HMAC | Without key management |
| Goza et al. [16] | Proposed a lightweight broadcast group authentication protocol | Inefficient key exchange |
| Wang et al. [17] | Proposed a protocol based on a trust-based key distribution method | Relies on a fixed group, which reduces the security accordingly |
| Woo et al. [18] | Proposed a protocol based on the AES lightweight symmetric encryption | Inefficient key management |
| Mun et al. [19] | Proposed a protocol based on the segregation of critical functionalities | Lack receiver authentication and message confidentiality |
| Palaniswamy et al. [20] | Proposed a symmetric key-based key management protocol | Relies on the assumption of pre-shared keys |
| Mundhenk et al. [21] | Proposed LASAN, a lightweight authentication protocol | Use a third external party and impractical for large-scale vehicle production |
| Groza et al. [22] | Proposed an identity-based key exchange protocol | The cost of computation and implementation performance for practical use is not considered |
| Han et al. [23] | Proposed an attribute-based encryption solution protocol | Isolated ECUs according to their attributes and impractical for vehicle production |
| Notation | Description |
|---|---|
| ID | Identity |
| The public key of SM | |
| The public key of ECUi | |
| The private key of SM | |
| The private key of ECUi | |
| Ksym | Session key |
| Hx() | Hash function |
| nx | Random number |
| Tx | Timestamp |
| mx | Vehicle additional information |
| s | Master key |
| PK | System public key |
| M, | Plaintext |
| C | Ciphertext |
| Key Elements | Color Set Definition |
|---|---|
| MESS | colset MESS = record n: R * ts: TS * am: AM |
| K | colset K = record p: W * hid: HID * hash: HASH |
| K’ | colset K’ = record p: U * hid: SID * hash: HASH |
| C | colset C = record k: K * m: MESS |
| HDATA | colset HDATA = record h: HASH * d: DATA |
| MESS3 | colset MESS3 = product R * TS * AM * DATA * HDATA |
| V | colset V = product HASH * H * U * SID |
| V’ | colset V’ = product HASH * H * W * HID |
| Tran | colset Tran = record c: C * v: V * u: U |
| Type | Original Model | Original Attack Model |
|---|---|---|
| State Space Node | 42 | 1063 |
| State Space Arc | 40 | 2867 |
| SCC Graph Node | 42 | 1063 |
| SCC Graph Arc | 40 | 2867 |
| MainState Space Node | 0 | 0 |
| Live Transition Instances | 0 | 0 |
| Dead Transition Instances | 0 | 0 |
| Dead Marking | 1 | 1 |
| Security Attributes | Woo et al. [18] | Groza et al. [16] | Palaniswamy et al. [20] | Mun et al. [19] | Our Scheme |
|---|---|---|---|---|---|
| Session key security | No | Yes | Yes | Yes | Yes |
| Entity authentication | No | No | No | No | Yes |
| Resistance to reply attack | No | No | Yes | Yes | Yes |
| Resistance to tampering attack | Yes | Yes | Yes | Yes | Yes |
| Resistance to spoofing attack | No | No | No | No | Yes |
| Provable security | No | No | Yes | Yes | Yes |
| Formal verification | No | No | Yes | No | Yes |
| Phase | Woo et al. [18] | Groza et al. [16] | Palaniswamy et al. [20] | Mun et al. [19] | Our Scheme |
|---|---|---|---|---|---|
| SM1 | 3THM + TH | 2THM + TH | TS + TCV + TSV + TH | THM + 2TH | TS + TH + TE/D |
| ECU1 | 3THM + TH | 2THM + 2TH | TS + TCV + TSV + TE/D | THM + 2TH | TS + TSV + TH + 2TE/D |
| connection | 6THM + 2TH | 4THM + 3TH | 2TS + 2TCV + 2TSV + TE/D + TH | 2THM + 4TH | 2TS + TSV + 2TH +3TE/D |
| SM2 | THM + 2TH + TE/D | TH + 2TE/D | TS + TSV | THM + 2TH + 2TE/D | TSV + 2TH + TE/D |
| ECU2 | THM + 2TH + TE/D | TH + 2TE/D | TS + TSV | THM + 2TH + 2TE/D | TH + TE/D |
| certification | 2THM + 4TH + 2TE/D | 2TH + 4TE/D | 2TS + 2TSV | 2THM + 4TH + 4TE/D | TSV + 3TH + 2TE/D |
| computational complexity (ms) | 8THM + 6TH + 2TE/D ≈ 1062.62 | 4THM + 5TH + 4TE/D ≈ 1023 | 4TS + 2TCV + 4TSV + TE/D + TH ≈ 1086.91 | 4THM + 8TH + 4TE/D ≈ 1029.26 | 2TS + 2TSV + 5TH + 5TE/D ≈ 1041 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zheng, L.; Feng, T. Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN. Symmetry 2022, 14, 2398. https://doi.org/10.3390/sym14112398
Zheng L, Feng T. Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN. Symmetry. 2022; 14(11):2398. https://doi.org/10.3390/sym14112398
Chicago/Turabian StyleZheng, Lu, and Tao Feng. 2022. "Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN" Symmetry 14, no. 11: 2398. https://doi.org/10.3390/sym14112398
APA StyleZheng, L., & Feng, T. (2022). Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN. Symmetry, 14(11), 2398. https://doi.org/10.3390/sym14112398








