Abstract
When imperceptibility is an issue, data-hiding techniques typically become limited to small payloads. In this paper, a novel data-hiding scheme is proposed that allows embedding large payloads while maintaining high stego-image quality. The scheme utilizes an sub-block for constructing a reference matrix as a secret key that allows the symmetric embedding and extraction of secret data from a grayscale cover image, where is a positive integer greater than or equal to two. With proper modification, the proposed method can be directly converted to a symmetric cryptosystem. For cases with acceptable stego-image quality (i.e., PSNR > 34), the experimental results showed that the proposed method can embed, on average, four bits per pixel (bpp), a higher hiding capacity than in previous works, and also offers the ability to adjust the capacity by varying . The number of solutions for a sub-block reaches the factorial of , guaranteeing the security of data embedding and extraction. In addition, the proposed method has low computational complexity and can be implemented in a straightforward manner.
1. Introduction
Technological advancements and near-ubiquitous connectivity have fueled Internet communications. Although cryptography can be used for encrypting and transmitting secret messages on the Internet, encryption has attracted the attention of hackers. Upon identifying encrypted data, attackers may intercept and attempt to decode secret messages. Currently, considerable research has been conducted on data hiding as an alternative to avoiding easy detection, with the primary goal of ensuring secret communication via the Internet. A secret message can be embedded into a cover medium using a concealing algorithm to create a stego-medium. The secret message carried by the stego-medium can then be transmitted through the Internet without being detected, even if it is intercepted. Digital images are commonly used as cover media for data hiding; the resulting images are known as stego-images.
There are two domains of data hiding in image steganography: the spatial [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20] and frequency domains [21,22,23,24,25,26]. In the spatial domain, secret data are embedded by adjusting the least significant bit (LSB) of each pixel. A high embedding capacity can be achieved, and embedding and extraction procedures can be easily implemented. However, stego-images in the spatial domain are easily attacked by steganalysis. In the frequency domain, secret data are embedded in the frequency coefficients of the image, following the discrete cosine transform (DCT). The advantage of the frequency domain is its robustness. In general, secret data are difficult to detect, although only small quantities can be embedded owing to image distortion. This study focuses on the data-hiding mechanism in the spatial domain.
The data-hiding scheme in this work is designed considering two main factors: (1) the embedding capacity (the number of covered bits per pixel) and (2) the image’s visual quality (image distortion). Some existing works have focused on designing reversible data-hiding schemes [12,13,14,15,16,17,18,19,20] to allow full recovery of cover images from stego-images. The embedding capacity of those methods is limited, owing to the need to store information related to the recovery of the original images. For irreversible data-hiding schemes [1,2,3,4,5,6,7,8,9,10,11], achieving high embedding capacity and visual quality is desirable. However, it is difficult to ensure both of these metrics at the same time. Increasing the embedding capacity increases the stego-image distortion, and vice versa. Therefore, the trade-off between embedding capacity and visual quality depends on the user and on the application context. For example, if embedded information is used for authenticating the copyright of cover images, as is the case in digital watermarking [21,22,23,25,26] or image authentication [27], then perhaps a larger acceptable distortion can be tolerated. However, if the goal is to protect the secrecy of the embedded information, then the visual quality should be such that the transmitted information is undetectable, at least to the human visual system.
In the spatial domain, the simplest LSB-based method amounts to replacing the least significant bits of the covering pixels with bits of the binary secret message. This simple method can be easily implemented for concealing confidential data but is prone to common statistical attacks [28,29,30]. In 2006, Mielikainen [2] proposed LSB matching, a revised LSB-like data-hiding method. In the LSB matching approach, pairs of pixels are grouped into basic embedded units. The least significant bits of a single pixel per pair are then modified to embed two bits. However, Mielikainen’s method did not fully explore all special modification cases. Zhang et al. [3] proposed an exploiting-modification direction (EMD) method, expanding Mielikainen’s method and exploiting special cases. The EMD method dynamically groups N pixels of the cover image to conceal -base numeral system digits, where N is a positive integer. Although this minimizes distortion, the embedding capacity of this method is limited. More recently, an LSB-based approach was proposed by Singh [10], using a novel adaptive pixel value differencing (PVD) scheme along with LSB embedding to achieve a high embedding capacity while retaining the visual quality of the cover image.
In 2008, Chang et al. [4] introduced a novel family of data-hiding schemes that uses Sudoku-based reference matrices for concealing and extracting secrets. Their method utilizes the properties of Sudoku [31] and applies an approach that uses pixel-pairs from the cover image as coordinates for matching their secrets in the digital format within a table. Lin et al. [5] subsequently proposed an approach for improving visual quality, inspired by the Sudoku method of Chang et al. [4]. Recently, Wu et al. [6] used three-dimensional reference tables for improving security and for customizing embedding capacity. Chang et al. [7] also freely adjusted the embedding in a one-dimensional vector. Hsiao et al. [11] extended the Sudoku matrix to a matrix for increasing the possibility of its solution and used a two-layer reference matrix for embedding additional information. The present study focuses on two-dimensional reference matrices. The main goal is to address the idea inspired by combining the EMD [3] and Sudoku [4] methods to improve the visual quality of the Sudoku method and to improve its high embedding capacity and security properties. We present a scalable secret reference matrix (SSRM), a secret matrix composed of many submatrices. The procedure of the proposed method first converts binary secret data into secret digits in the -base numeral system, and then modifies the values of the cover pixel-pairs for concealing the secret digits. Moreover, the SSRM can be also used as a secret key to symmetrically encrypt and decrypt the secret message via a cover image.
2. Related Work
In this section, since the proposed method is mainly based on the EMD method [3] and the Sudoku method [4], we briefly discuss the most relevant works based on these two approaches.
The pioneering work of EMD can date back to an optimal strategy (LSB-re) proposed by Jarno Mielikainen [2] to improve the visual quality of stego-images in the classic LSB-based replacement approach when embedding one bit per pixel (bpp) in a cover image. The LSB-re alters the second least significant bit if the pixel value after the LSB replacement has exceeded a certain predefined range to reduce its distortion. Zhang et al. [3] subsequently proposed an EMD method that described the generalization of all cases in [2] as well as produced the first data-hiding scheme that utilized a reference matrix. The main idea of EMD is to hide a -base digit into cover pixels, where is an integer in the 0– range, and is a non-negative integer. The worst-case implication of embedding a -base digit in cover pixels is that only one out of pixels should be increased or decreased by one. In 2008, Chang et al. [4] proposed a data-hiding scheme using a new reference matrix based on a Sudoku grid, for improving the embedding capacity of the EMD method. In the Sudoku method, each pixel-pair of a cover image can hide a 9-base digit, in contrast to the EMD method, which can only embed a 5-base digit. Chang et al. used the Sudoku solution for creating a reference matrix to guide the modification of the cover image. The number of possible solutions to a Sudoku problem is approximately , showing that the security of the Sudoku method is higher than that of the EMD method.
In early 2016, Wu et al. [6] proposed a magic cube–based (MCB) scheme to improve the efficiency of the Sudoku method of Chang et al. [4] The MCB method utilizes a magic cube for to embed and extract the secret data in base numeral secret digits where the embedding capacity is bpp. A three-dimensional reference table can be constructed by the magic cube with distinct values of 0 to randomly assigned to all magic cubes. That is, every sub-cube in the magic cube stands for a different number. All pixels in the cover image are modified by substitution according to the spatial coordinates mapped from the numeral secret digits of the secret data. Later in 2017, Chang et al. [7] proposed another data-hiding scheme based upon a permutation vector (PV). The PV is concatenated repeatedly to construct a one-dimensional reference matrix in order to improve the visual quality of an embedding capacity less than 1.5 bpp. Recently, Hsiao et al. [11] proposed two methods using the Sudoku matrix and the double-layer magic matrix, respectively. For the first method, the Sudoku matrix is an extended version of the Sudoku matrix in [4]. Note that the numbers in each column, row, and diagonal of the magic matrix must sum to 30. Hsiao et al. designed a double-layer magic matrix (DLMM) to improve embedding capacity compared to the Sudoku matrix. As a result, the bpp of the embedding capacity increases from 2 to 3. The data-hiding scheme proposed by Hsiao et al. also modified the pixels through a reference matrix to complete the embedding of a secret message. A double-layer magic matrix is constructed to help embed the secret message in a base 64 numeral system.
3. The Proposed SSRM Method
The proposed method requires a special scalable secret reference matrix (SSRM) as a key map. This key map guides the cover image to modify its pixels to imply the secret message indirectly. An overall flow diagram of the developed system is shown in Figure 1. The same key map is used to extract the hidden secret message as well. The proposed method is introduced in four subsections. Section 3.1 describes how to create an SSRM and its characteristics. Section 3.2 proves the characteristics of SSRM. Finally, Section 3.3 and Section 3.4 give details of the embedding process and extraction process, respectively.
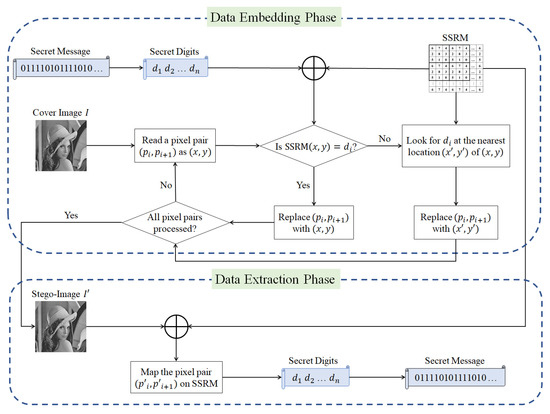
Figure 1.
The overall flow diagram of the developed SSRM system.
3.1. The Generating Process of SSRM
In this section, a SSRM is proposed to be generated as a key map to guide pixel modification while in the embedding phase. It will also be required when extracting the secret data from the stego-image. SSRM is a special matrix that consists of two conditions as follows. First, the SSRM is filled with all digits 0 ~ , where is a positive integer in the range of (i.e., is greater than 1 because the signal in image processing has at least two digits, ‘0′ and ‘1′, to represent the multimedia data. On the other hand, the maximum of can only be 256 due to the full size of the SSRM being ). Secondly, any square window in SSRM has all digits 0 ~ in it. Suppose an empty set of a matrix has been generated, and an table has been created with all digits 0 ~ randomly filled in using a random number generator along with an arbitrary seed as a key. Then a matrix such as the SSRM can be generated by the following steps.
- Step 1:
- Let represents the location of on SSRM where and are the row and column of the upper-left most corner of on SSRM, respectively.
- Step 2:
- From left to right, slide horizontally one column. Then, will be ’s new position, where the leftmost column elements of are slid to the rightmost column of , as an example of is shown in Figure 2a.
- Step 3:
- Repeat Step 2 until the window scans to the right edge of the SSRM.
- Step 4:
- Locate the sliding window back to position (0,0) of the SSRM (i.e., the left end of the SSRM).
- Step 5:
- From top to bottom, vertically slide the window one row. Make the new position of the window and complement ’s bottommost elements with ’s topmost elements. An example of is shown in Figure 2b.
- Step 6:
- Repeat Step 3 to Step 6 until is filled with digits, as shown in Figure 3.
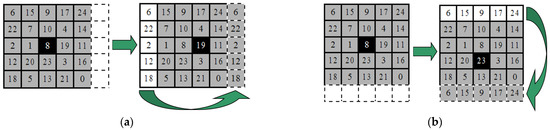
Figure 2.
Steps for generating a 5×5 table–based SSRM. (a) Slides horizontally, (b) Slides vertically.
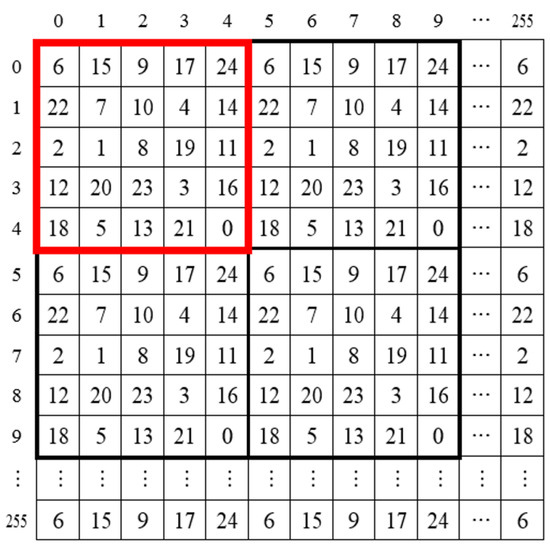
Figure 3.
An example of 5 × 5 table–based SSRM.
The SSRM process can be summarized by tiling an table to a matrix. By using the SSRM, it costs two pixels each time to map on the element of the SSRM (i.e., the SSRM is a two-dimensional matrix), which means that every two pixels can embed an -base digit. Therefore, the embedding capacity increases by adjusting the value of . On the other hand, the distortion also increases by growing the size of the table (i.e., the correct element could be found far from the located element, whereby the difference between the new pixel-pair and the original pixel-pair could be large).
3.2. The Correctness of the Property in SSRM
The SSRM has a property that every coordinate’s element can find other base digits through its surrounding neighbor elements. To prove this phenomenon, a SSRM base on the table () is given as an example for illustration. First, create a table filled up randomly with unrepeated 9 base digits 0–8. Define three sets , , and that respectively include the elements of in columns 0, 1, and 2, where , , . Secondly, suppose a sliding window, , that attaches to table . Then, the three columns of are , , , respectively. While is sliding, the new three columns of can be represented in general form as , , (i.e., variable is defined as the sliding distance of , where is a positive integer at the range of . The fact of the SSRM can be proven by the following mathematical induction.
- Step 1:
- When , then , , , where the element sets as shown in Figure 4a. SW has not moved.
- Step 2:
- Let , then , , . Because of is an empty set, the vacant elements is . Therefore, the column 0′s elements have to complement column 3′s empty set, where is assigned to to contain the three sets of as shown in Figure 4b. SW has moved by 1.
- Step 3:
- When , then , , . Suppose this consists of the expression as shown in Figure 4c. SW has moved by .
- Step 4:
- Let , then , , . Since is an empty set, the lacking elements should be at column . Therefore, assign column ’s elements to as shown in Figure 4d to consist of . SW has moved by .
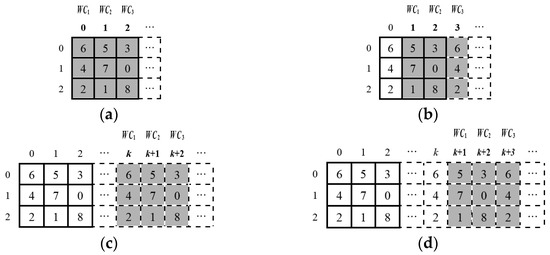
Figure 4.
The inductive proof of the property in SSRM. (a) SW sliding with distance Δ = 0, (b) SW sliding with distance Δ = 1, (c) SW sliding with distance Δ = k, (d) SW sliding with distance Δ = k + 1.
From the deduction above, the horizontal sliding is proven to have the characteristic that every location can find other digits around its neighbors. On the other hand, the same proof method can be used while sliding vertically. Thus, the characteristic of SSRM is proven to be accurate.
3.3. The Embedding Section
The main procedure of the embedding process can be summarized as the upper part of Figure 1. First, an grayscale cover image , where and represent the height and width of the cover image, respectively. Any possible pairing technique can be used to group every two pixels on the cover image. Secondly, prepare a size SSRM that contains digits from 0 to , where is a positive integer. Suppose the embedded secret message is a bit stream , where represents the bits length of . Then will be divided into segments of bits. Each bit can be converted into an -base digit. The value of can be calculated by . If the digit converted by bits is greater than , catch an bits segment to range the conversion in 0– digits. After the bit stream is converted into -base secret digits, each pair of pixels will be guided by the SSRM for modification to imply a secret digit.
Suppose an -base digit, , is about to embed into a pixel-pair . Locate the pixel-pair as a coordinate on the SSRM. The element of the coordinate on SSRM is . If , then embed d without any modification on . If , then search for the neighbor elements to find digit . To find the modification that maintains a higher quality of PSNR, the Euclidean distance should be used as a measurement standard. The Euclidean distances for two locations and in the SSRM can be calculated by (1).
The reason for selecting Euclidean distance over other distance metrics, such as city-block distance or chessboard distance, is because Euclidean distance tends to have a more precise estimation when distance is actually the value differences between two pixel-pairs. That is, a diagonal step (alter each of the two pixels by one) is better than two vertical or horizontal steps (alter one of the two pixels by two) in terms of PSNR. For example, given four coordinates in a two-dimensional space: , , , and . The city-block distance tends to overestimate the cost of a diagonal step since it estimates that the distance between and is the same as that between and . On the contrary, the chessboard distance tends to underestimate the cost of a diagonal step since it estimates that the distance between and is the same as that between and . However, the distortions caused by the substitution of is . Therefore, only the Euclidean distance that applies the straight-line distance is more consistent with the cost of value differences between two pixel-pairs.
Before finding the candidate element of , an size block will be marked as a searching area (SA). Try to locate on the center of the SA as possible. That way, the searched neighborhood elements can nearly stay around the coordinate , where a suitable element with the closest Euclidean distance can be found. Due to the fact that the candidate element in the SA can only exist once, which is also the optimal one to have the closest Euclidean distance, the search need only be in the SA. Suppose is the beginning location for searching the SA. The pseudo code of the search procedure is described in Algorithm 1 as follows.
| Algorithm 1 The step by step searching process of the SSRM algorithm. |
|
|
| if , then |
| end if |
|
| if and then , |
| else if and then |
| else if and then |
| else if and then , |
| else if and then , |
| else if and then , |
| else if and then , |
| else if and then , |
| else and then , |
| end if |
|
| for do |
| for do |
| ; |
| end for |
|
The search starts from the element on the leftmost column and topmost row, and sequentially continues from left to right, top to bottom. Suppose the optimal pixel-pair is found to have . The value of pixel-pair is switched to as the stego pixel-pair, implying an -base digit, .
Consider the following example to illustrate the embedding process. Suppose embedding a segment of binary streams into the pixel-pair . First, turn to a 25-base digit , and create a SSRM that contains 0–24 digits as shown in Figure 5. Secondly, map the pixel-pair on the SSRM in Figure 5 to match the element with . The location of SSRM is discovered as . Therefore, a big Oh searching area (SA) is marked in gray, as shown in Figure 5. The process of searching is defined as initializing the first searching element as the location of the leftmost column and topmost row in the searching area. Follow the sequential index from left to right, top to bottom in SA to search for the digit , as shown in Figure 5. The digit is, however, found at on the SSRM, as shown in Figure 5. Substitute with as a means of hiding in pixel-pair .
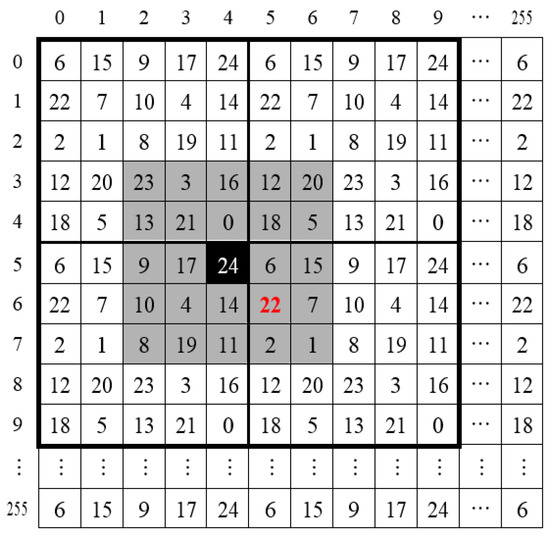
Figure 5.
The searching area for hiding digit in (5, 4).
3.4. The Extracting Section
The main procedure for data extraction is as shown in the lower part of Figure 1. Before extracting the secret message, the same stego-image and SSRM in the embedding section is required. The SSRM should contain digits 0 ~ , where is a positive integer greater than 2. Before extracting the secret message, the same grouping technique that is used in the embedding section is first used to identify the same location of pixel-pairs on the stego-image. Every pair of stego pixels is seen as a coordinate on the SSRM. The location on the SSRM contains an element which points out the -base secret digit that is implied by the modified pixel-pair . Then extract all by using the same mapping technique. After every has been extracted, the original secret message can be recovered by converting every into binary form. Here is an example for the extraction section. A pixel-pair is cached to locate onto the SSRM in Figure 5 (i.e., ). The element on the SSRM is a 25-base digit . Convert the back into its binary form, and the binary stream can be obtained as , which is part of the original secret message.
4. Experimental Results
In this section, the experimental results and comparisons between the related work and proposed method are presented. The proposed data-hiding method was implemented using the Java IDE Eclipse 4.18 on a machine with CPU i5-8250U and 8.00 GB RAM. The source code is available at GitHub [32]. Comparisons are made with OPAP [1], LSB-re [2], EMD [3], Sudoku [4], MCB [6], PV [7], and DLMM [11]. The test images in this experiment are nine grayscale natural images, ‘Lena’, ‘Baboon’, ‘Pepper’, ‘Scene’, ‘Boats’, ‘F-16’, ‘Goldhill’, ‘Barbara’, and ‘Tiffany’, with resolutions of , as shown in Figure 6. These test images are available from the USC–SIPI image database [33]. The secret messages used in the experiments are randomly generated by a random number generator.
Figure 6.
Nine grayscale test images. (a) Lena, (b) Baboon, (c) Pepper, (d) Scene, (e) Boats, (f) F-16, (g) Goldhill, (h) Barbara, (i) Tiffany.
To evaluate the performance of the data-hiding technique, visual qualities and embedding capacity, two important factors, must be taken into consideration. To compare the visual quality, the peak signal-to-noise ratio (PSNR) is used as an international measure standard to present the visual quality of the stego-images. PSNR can be calculated by (2).
where MSE represents the mean square error, which indicates the pixels’ difference between the cover image and the stego-image . Its formula is defined in (3), where and respectively denote the height and width of the image. Higher values of PSNR mean lower distortion in the stego-image.
For embedding capacity, bits-per-pixel (bpp) is a basic unit being used in the measurement. The formula for calculating the embedding capacity is defined in (4).
where represents the embedded capacity with the unit bits-per-pixel (bpp). is the total number of bits of random secret message that are to be embedded into the cover image. and denote the height and width of the cover image, respectively. If the value of is high, it means the data-hiding system exhibits a high embedding capacity.
For algorithmic efficiency, since all methods take the same input size pixels as a cover image, the main difference between these methods lies in the search of the secret digit on the reference matrix for the data embedding. However, this operation only requires constant time , where . Furthermore, the extraction of the secret data is merely an act of direct access to the LSBs or lookup table. Therefore, the time complexity for all methods in this section is estimated as .
The proposed method uses a scalable secret reference matrix (SSRM) to embed and extract data. The SSRM is composed of several sub-blocks. The value of affects the visual quality, embedding capacity, and security. First of all, Figure 7 is a trend diagram of PSNR from to . It is discovered that the reduction of PSNR is very slow. When , PSNR is 30 dB. On the other hand, Figure 8 shows that the embedding capacity from to can be adjusted very flexible. It can achieve a high embedding capacity of 4.5 bpp, which is much higher than that of most previous data-hiding techniques. Table 1 demonstrates that a decent PSNR has been achieved while the embedding capacity increases proportional to . These results are reflected in comparison with the Sudoku method. In Table 2, let the proposed method set in the case of . For the same embedding capacity, the proposed method has a visual quality of, on average, 5.07 dB higher than that of the Sudoku method. Moreover, when the proposed method is under the case of , not only the embedding capacity is 0.74 (bpp) higher than the Sudoku method, but also the PSNR is on average 0.3 dB higher than their PSNR. To summarize these two factors, the visual quality and the embedding capacity of the proposed method, the visual quality of SSRM is not inferior to most of the recent methods, as shown in Table 3. On the other hand, the proposed SSRM method shared the same flexibility as the PV method to adjust the embedding capacity from 1 to 8 bpp, as shown in Table 4. Although the MCB method can also do similar adjustments, it only considers the cases of integer bpp. As for the security aspect, the DLMM method used a Sudoku matrix to increase the number of possible solutions to the reference matrix. However, it sacrificed the visual quality of the stego-image, which can be obviously seen in Table 3 when the embedding capacity is set to 2. Under the comprehensive evaluation, the proposed SSRM method has relatively more advantages than the other related works.
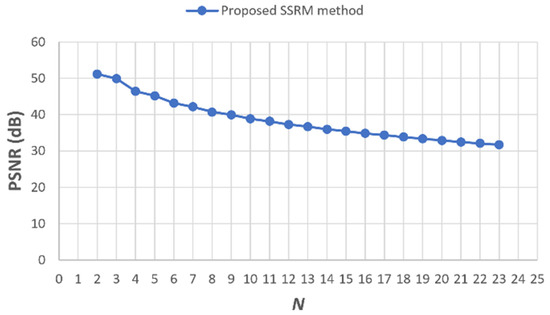
Figure 7.
The PSNR trend diagram.
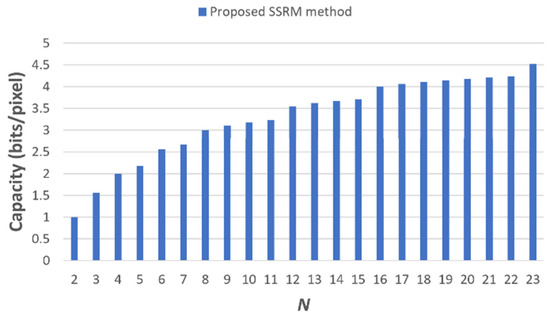
Figure 8.
The embedding capacity trend diagram.

Table 1.
The visual quality and embedding capacity in different values of .

Table 2.
The visual quality and embedding capacity of the proposed SSRM method in N = 3 to N = 5.

Table 3.
Comparisons of related works in visual quality with embedding capacity C = 2 and C = 3.

Table 4.
Comparisons of related works in the flexibility of embedding capacity and the size of solutions.
In addition, an experiment was conducted on all nine test images to compare the performance between the proposed SSRM and the LSB-based approaches. From Table 5, the experimental results show that at the same condition for embedding capacity (), the PSNR of the proposed method is higher than the traditional LSB technique with an average of 2 dB higher PSNR. On the other hand, when the PSNR is compared with the OPAP [1], it is nearly the same in any condition for the embedding capacity. The slightly difference in the resulting stego-image is not easily detected by the naked eye. As a real-life example, for the two Lena images in Figure 9 it is difficult to distinguish which has more distortion than the other. Normally, the human eye cannot perceive the loss of stego-image quality when PSNR is greater than 40 dB. In the spatial domain, OPAP is known as the state-of-the-art baseline algorithm for large-payload data hiding. However, the main goal of the proposed method is to pursue an additional advantage in terms of security with the same performance of visual quality and embedding capacity. More specifically, the secret data that uses the OPAP can be easily attacked by trying to extract the least significant bits of every pixel. That is, at most eight attempts are required to obtain the secret message (i.e., every pixel value is represented by 8 bits). However, for the proposed method, the SSRM acts as a key for embedding and extracting the secret data. Therefore, it takes, at most, attempts to find the correct SSRM for the corresponding stego-image.

Table 5.
The comparison of visual quality and embedding capacity.

Figure 9.
Two grayscale Lena images, of which (a) is the original image and (b) is the stego-image (PSNR = 34.84 dB, C = 4 bpp).
The final goal of the steganography is to securely cover the secret message to prevent hackers from extracting the secret message. The proposed method offers a further advantage for security. There are two reasons behind these advantages. The first is that the same SSRM is required to embed and extract the secret message. Second, due to the multiple solutions of the SSRM, it is difficult to decide on the correct one. Both the method of Chang et al. and the proposed method offer high security for a data-hiding scheme, but the proposed method is safer due to the SSRM’s possible solutions, which number about , that is, possibilities, as shown in Table 6. It is higher than the Sudoku solutions of Chang et al. of when .

Table 6.
The size of SSRM solutions in different N.
5. Conclusions
This study proposes a data-hiding scheme that utilizes a scalable secret reference matrix (SSRM). The characteristics of the EMD method and Sudoku method are combined to achieve a high embedding capacity, low distortion, and high security. Empirical evidence suggests that in the acceptable range of the stego-image quality values (), the embedding capacity of the proposed method is, on average, 4 bpp higher than that associated with the EMD method (on average 1.16 bpp). The PSNR of the proposed method is, on average, higher than that of the EMD method, and is slightly higher than the values yielded by other methods. On the other hand, compared with the Sudoku method, both visual quality and embedding capacity are higher than those produced by the Sudoku method for the cases of to . The embedding capacity can be dynamically adjusted according to user requirements (i.e., by changing the value of ). In addition, compared with the best large-payload data-hiding method, OPAP, in the spatial domain, the proposed method offers the advantage of high security while embedding and extracting data owing to the various solutions of the SSRM. The SSRM solutions can be multiplied by changing the value of , where the solution can be computed in . The proposed method is not only a simple and sufficient algorithm, but also represents a novel and secure idea for data-hiding in the spatial domain. Future work will further explore data-hiding for the SSRM edge cases. The possibility of combining other data-hiding schemes with edge detection will be considered for reducing the distortion of stego-images.
Author Contributions
Conceptualization, J.L. and C.-W.Y.; methodology, J.L., C.-W.T., and C.-W.Y.; software, J.L. and K.-H.L.; investigation, J.L. and K.-H.L.; formal analysis, J.L.; writing—original draft, J.L. and C.-W.T.; writing—review and editing, J.L. and C.-W.Y.; project administration, C.-W.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was partially supported by the Ministry of Science and Technology, Taiwan, R.O.C. (Grant Nos. MOST 110-2221-E-039-004, MOST 110-2221-E-143-003, MOST 110-2221-E-259-001, MOST 110-2221-E-143-004, MOST 110-2222-E-005-006, MOST 110-2634-F-005-006, MOST 110-2218-E-005-008-MBK, and MOST 111-2218-E-005-007-MBK) and by China Medical University, Taiwan (Grant No. CMU110-S-21).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chan, C.K.; Cheng, M. Hiding data in images by simple LSB substitution. Pattern Recognit. 2004, 37, 469–474. [Google Scholar] [CrossRef]
- Mielikainen, J. LSB matching revisited. IEEE Signal Process. Lett. 2006, 13, 285–287. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, S. Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett. 2006, 10, 781–783. [Google Scholar] [CrossRef]
- Chang, C.C.; Chou, Y.C.; Kieu, T.D. An information hiding scheme using Sudoku. In Proceedings of the 2008 3rd International Conference on Innovative Computing Information and Control, Dalian, China, 18–20 June 2008; p. 17. [Google Scholar]
- Lin, C.; Chang, C.; Lee, W.; Lin, J. A novel secure data hiding scheme using a secret reference matrix. In Proceedings of the 2009 Fifth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kyoto, Japan, 12–14 September 2009; pp. 369–373. [Google Scholar]
- Wu, Q.; Zhu, C.; Li, J.-J.; Chang, C.-C.; Wang, Z.-H. A magic cube based information hiding scheme of large payload. J. Inf. Secur. Appl. 2016, 26, 1–7. [Google Scholar] [CrossRef]
- Chang, C.-C.; Chang, J.-C.; Chou, Y.-H.; Wu, H.-L. A high embedding capacity data hiding scheme based upon permutation vectors. In International Workshop on Digital Watermarking: Digital Forensics and Watermarking; Springer: Berlin/Heidelberg, Germany, 2017; pp. 578–587. [Google Scholar]
- Malik, A.; Kumar, R.; Singh, S. A new image steganography technique based on pixel intensity and similarity in secret message. In Proceedings of the 2018 International Conference on Advances in Computing, Communication Control and Networking (ICACCCN), Greater Noida, India, 12–13 October 2018; pp. 828–831. [Google Scholar]
- Chen, Y.; Sun, W.; Li, L.; Chang, C.C.; Wang, X. An efficient general data hiding scheme based on image interpolation. J. Inf. Secur. Appl. 2020, 54, 102584. [Google Scholar] [CrossRef]
- Singh, S. Adaptive PVD and LSB based high capacity data hiding scheme. Multimed. Tools Appl. 2020, 79, 18815–18837. [Google Scholar] [CrossRef]
- Hsiao, T.-C.; Liu, D.-X.; Chen, T.-L.; Chen, C.-C. Research on image steganography based on Sudoku matrix. Symmetry 2021, 13, 387. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef] [Green Version]
- Ni, Z.; Shi, Y.-Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Malik, A.; Singh, S.; Kumar, R. Recovery based high capacity reversible data hiding scheme using even-odd embedding. Multimed. Tools Appl. 2018, 77, 15803–15827. [Google Scholar] [CrossRef]
- Chen, Y.-C.; Hung, T.-H.; Hsieh, S.-H.; Shiu, C.-W. A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic algorithms. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3332–3343. [Google Scholar] [CrossRef]
- Chen, Y.-C.; Shiu, C.-W. Distributed encrypted image-based reversible data hiding. J. Internet Technol. 2021, 22, 101–107. [Google Scholar]
- Xu, S.; Chang, C.-C.; Liu, Y. A high-capacity reversible data hiding scheme for encrypted images employing vector quantization prediction. Multimed. Tools Appl. 2021, 80, 20307–20325. [Google Scholar] [CrossRef]
- Wang, X.; Chang, C.-C.; Lin, C.-C. High capacity reversible data hiding in encrypted images based on prediction error and block classification. Multimed. Tools Appl. 2021, 80, 29915–29937. [Google Scholar] [CrossRef]
- Gao, K.; Horng, J.-H.; Chang, C.-C. High-capacity reversible data hiding in encrypted images based on adaptive block encoding. J. Vis. Commun. Image Represent. 2022, 84, 103481. [Google Scholar] [CrossRef]
- Nguyen, T.-S.; Chang, C.-C.; Lin, C.-C. High capacity reversible data hiding scheme based on AMBTC for encrypted images. J. Internet Technol. 2022, 23, 55–66. [Google Scholar]
- Barni, M.; Bartolini, F.; Cappellini, V.; Piva, A. A DCT-domain system for robust image watermarking. Signal Process. 1998, 66, 357–372. [Google Scholar] [CrossRef]
- Lin, S.D.; Chen, C.F. A robust DCT-based watermarking for copyright protection. IEEE Trans. Consum. Electron. 2000, 46, 415–421. [Google Scholar] [CrossRef]
- Chu, W.C. DCT-based image watermarking using subsampling. IEEE Trans. Multimed. 2003, 5, 34–38. [Google Scholar] [CrossRef]
- Wong, K.; Qi, X.; Tanaka, K. A DCT-based Mod4 steganographic method. Signal Process. 2007, 87, 1251–1263. [Google Scholar] [CrossRef]
- Zhang, D.; Pan, Z.; Li, H. A contour-based semi-fragile image watermarking algorithm in DWT domain. In Proceedings of the 2nd International Workshop Education Technology and Computer Science, Wuhan, China, 6–7 March 2010; Volume 3, pp. 228–231. [Google Scholar]
- Wu, X.; Sun, W. Robust copyright protection scheme for digital images using overlapping DCT and SVD. Appl. Soft Comput. 2013, 13, 1170–1182. [Google Scholar] [CrossRef]
- Hong, W.; Chen, J.; Chang, P.S.; Wu, J.; Chen, T.S.; Lin, J. A color image authentication scheme with grayscale invariance. IEEE Access 2021, 9, 6522–6535. [Google Scholar] [CrossRef]
- Ker, A.D. A general framework for structural steganalysis of LSB replacement. In Proceedings of the 7th International Conference on Information Hiding, Barcelona, Spain, 6–8 June 2005; Volume 3727, pp. 296–311. [Google Scholar]
- Ker, A.D. A fusion of maximum likelihood and structural steganalysis. In Proceedings of the 9th International Conference on Information Hiding, Saint Malo, France, 11–13 June 2007; pp. 204–219. [Google Scholar]
- Ker, A.D.; Böhme, R. Revisiting weighted stego-image steganalysis. In Proceedings of the Security, Forensics, Steganography, and Watermarking of Multimedia Contents X, San Jose, CA, USA, 2 April 2008. [Google Scholar]
- Sudoku. Available online: https://en.wikipedia.org/wiki/Sudoku (accessed on 14 April 2022).
- GitHub Repository. Available online: https://github.com/senyalin/SSRM (accessed on 14 April 2022).
- SIPI Image Database. Available online: http://sipi.usc.edu/database/ (accessed on 14 April 2022).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).