Monte-Carlo Simulation-Based Accessibility Analysis of Temporal Systems
Abstract
:1. Introduction
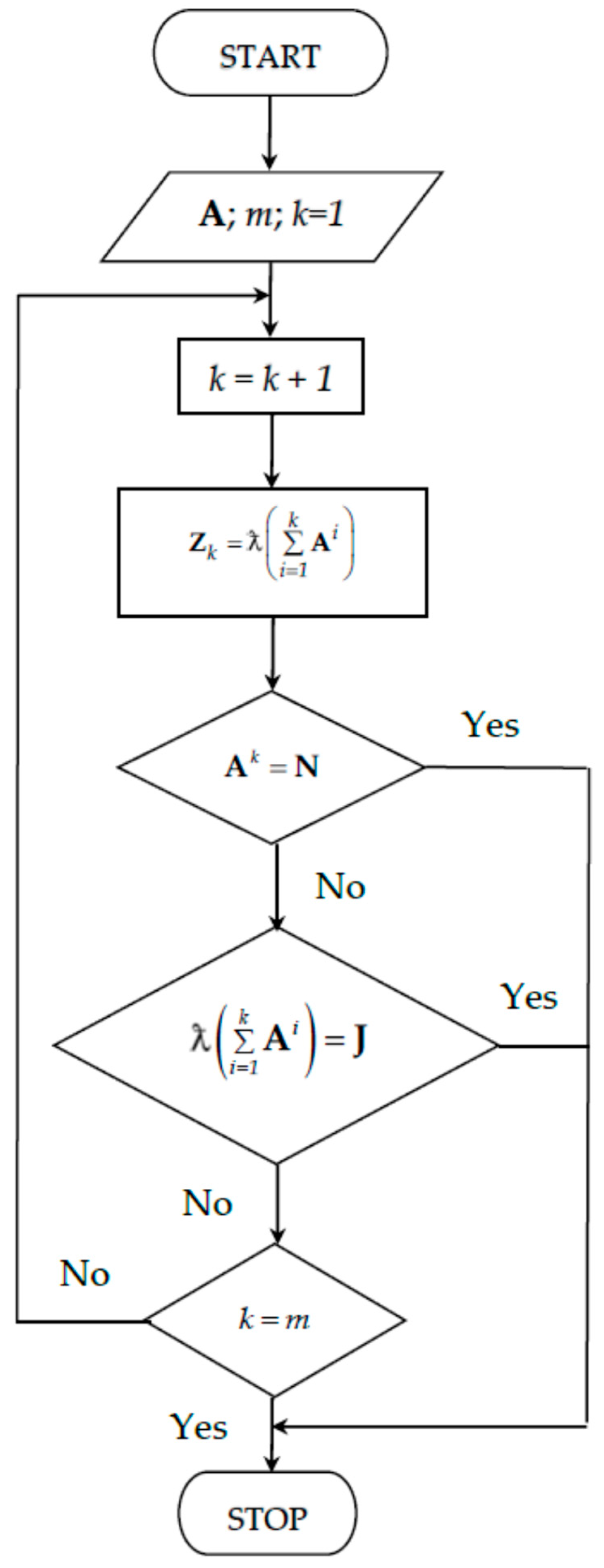
2. The Core Method
- If there exists k such thatwhere N is zero (null) matrix, then the length of the longest path of graph is k − 1; so further calculation is unnecessary.
- Ifwhere J is matrix of ones, then all nodes have connection with all other ones; so further calculation is unnecessary too.
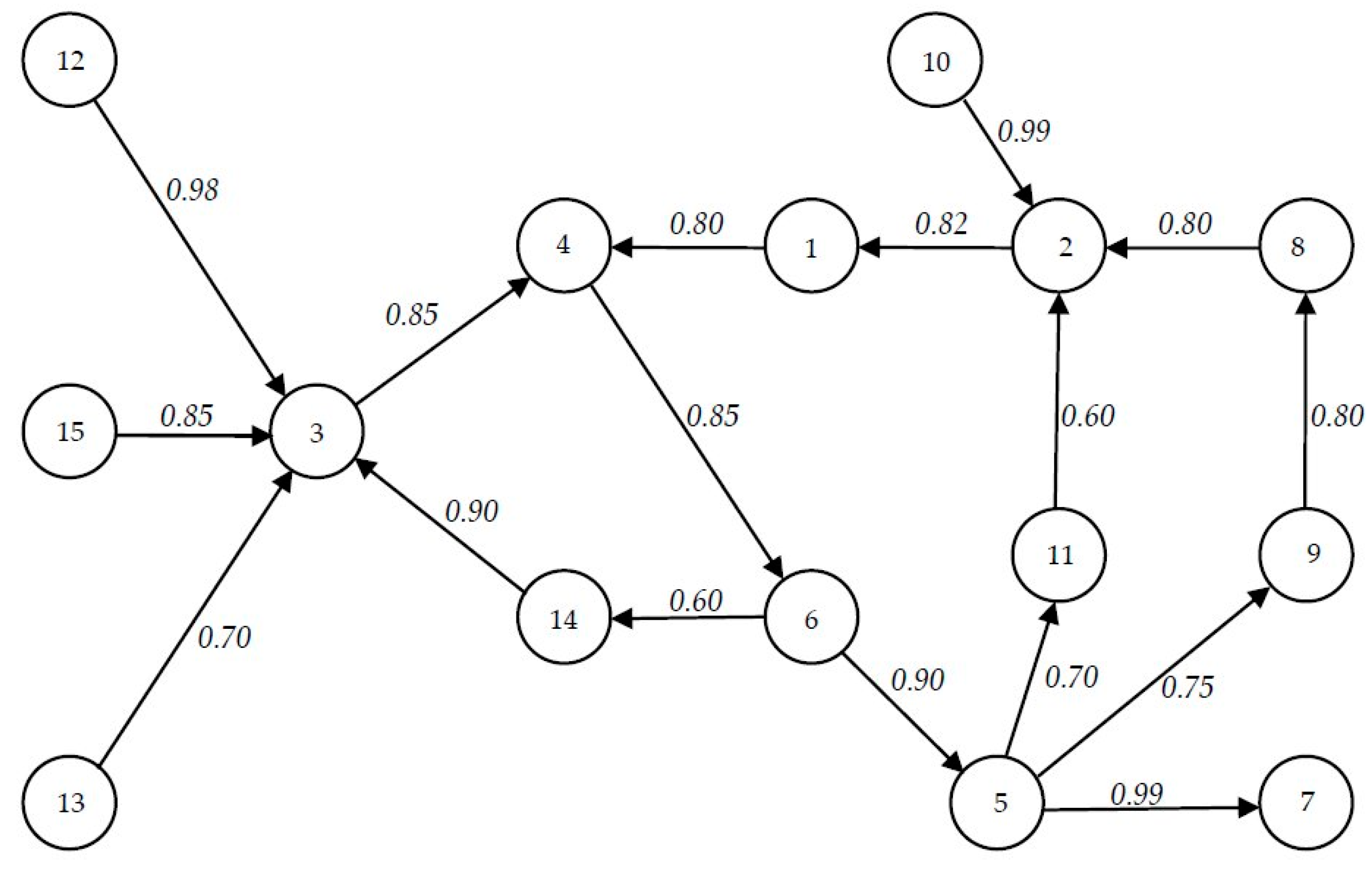
3. Structural Analysis
4. Functional Analysis
5. Conclusions
- (2.a)
- the exposure vector e illustrates that the components 10; 12; 13 and 15 are not affected by a dysfunction of an-other system element;
- (2.b)
- the impact vector i shows that failures of component 7 has no effect on the work of the other system elements;
- (2.c)
- application of the weighted impact vector provides that element 15 has the most weighted effect on the work of other system elements;
- (3.a)
- the maximum accessibility is from element 5 to element 2 (z5.2 = 0.82);
- (3.b)
- the minimal, but not zero, (0.21) accessibility is from element 9 to elements 3, 7, 9 and 11;
- (3.c)
- the average impact vector i1M shows that failure of component 6 has the maximum effect on the work of the other system elements (i6.1M = 7.15);
- (3.d)
- element 9 has the minimal, but not zero, impact on the other nodes;
- (3.e)
- element 10 has the highest weighted average impact;
- (3.f)
- element has smallest, but not zero, weighted average impact;
- (3.g)
- components 10; 12; 13 and 15 are not affected by a dysfunction of another system element—compare with conclusion 2.a).
- (3.h)
- element 8 has the minimum, but not zero, exposure.
- structural accessibility;
- structural impact;
- structural exposure.
- (4.a)
- the maximum average accessibility is from element 5 to element 7 (z5.7 = 0.99);
- (4.b)
- the minimal, but not zero, (0.21) average accessibilities are from element 1 to element 8;
- (4.c)
- component 6 has the maximum average effect on the work of the other system elements (i6.1M = 7.18);
- (4.d)
- element 11 has a minimal, but not zero, average impact on other nodes;
- (4.e)
- element 10 has the highest weighted average impact;
- (4.f)
- element 11 has smallest, but not zero, weighted average impact;
- (4.g)
- the element 14 has the minimum, but not zero, average exposure;
- (4.h)
- element 4 has the maximum average exposure.
- functional accessibility;
- functional impact;
- functional exposure.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Nomenclature
| A | adjacency matrix; |
| e | exposure vector |
| i | impact vector; |
| iw | weighted impact vector |
| J | matrix of ones; |
| N | zero (null) matrix; |
| pi | ith node of graph; |
| Q | number of excitation |
| Z | accessibility matrix; |
| ZQ | average accessibility matrix; |
| η | general variable. |
| IIoT | Industrial Internet of Things; |
| ITS | Intelligent Transportation System; |
| MANET | Mobile Ad-hoc NETwork; |
| MCS | Monte-Carlo Simulation; |
| RSU | Road Side Unit |
| VANET | Industrial Internet of Things |
| WSN | Wireless Sensor Network. |
References
- Lentz, H.; Selhorst, T.; Sokolov, M. Unfolding Accessibility Provides a Macroscopic Approach to Temporal Networks. Phys. Rev. Lett. 2013, 25, 788–795. [Google Scholar] [CrossRef] [PubMed]
- Funel, A. Causal Paths in Temporal Networks of Face-to-Face Human Interactions. Complex Syst. 2021, 30, 33–46. [Google Scholar] [CrossRef]
- Mboup, D.; Diallo, C.; Cherifi, H. Temporal Networks Based on Human Mobility Models: A Comparative Analysis With Real-World Networks. IEEE Access 2022, 10, 5912–5935. [Google Scholar] [CrossRef]
- Wersényi, G.; Csapó, Á.; Budai, T.; Baranyi, P. Internet of Digital Reality: Infrastructural Background—Part II. Acta Polytech. Hung. 2021, 18, 91–104. [Google Scholar] [CrossRef]
- Boucetta, S.I.; Guichi, Y.; Johanyák, Z.C. Simulation-Based Comparison and Analysis of Time-Based and Topology-Based Emergency Dissemination Protocols in Vehicular Ad-hoc NETworks. In Proceedings of the 6th International Conference on Systems and Informatics (ICSAI 2019), Shanghai, China, 2–4 November 2019. [Google Scholar]
- Boucetta, S.I.; Johanyák, Z.C. Review of Mobility Scenarios Generators for Vehicular Ad-Hoc Networks Simulators. J. Phys. Conf. Ser. 2021, 1935, 012006. [Google Scholar] [CrossRef]
- Péter, T.; Háry, A.; Szauter, F.; Szabó, K.; Vadvári, T.; Lakatos, I. Analysis of Network Traversal and Qualification of the Testing Values of Trajectories. Acta Polytech. Hung. 2021, 18, 151–161. [Google Scholar] [CrossRef]
- Péter, T.; Szauter, F.; Rózsás, Z.; Lakatos, I. Integrated application of network traffic and intelligent driver models in the test laboratory analysis of autonomous vehicles and electric vehicles. Int. J. Heavy Veh. Syst. 2020, 27, 227–245. [Google Scholar] [CrossRef]
- Nagy, I. Hierarchical Mapping of an Electric Vehicle Sensor and Control Network. Acta Polytech. Hung. 2021, 18, 161–180. [Google Scholar] [CrossRef]
- Dagdeviren, Z.A. Weighted Connected Vertex Cover Based Energy-Efficient Link Monitoring for Wireless Sensor Networks Towards, Secure Internet of Things. IEEE Access 2021, 9, 10107–10119. [Google Scholar] [CrossRef]
- Židek, K.; Pitel’, J.; Adámek, M.; Lazorík, P.; Hošovský, A. Digital Twin of Experimental Smart Manufacturing Assembly System for Industry 4.0 Concept. Sustainability 2020, 12, 3658. [Google Scholar] [CrossRef]
- Mourtzis, D.; Vlachou, E.; Milas, N.; Xanthopoulos, N. A Cloud-based Approach for Maintenance of Machine Tools and Equipment Based on Shop-floor Monitoring. Procedia CIRP 2016, 41, 655–660. [Google Scholar] [CrossRef] [Green Version]
- Pranowo, I.D.; Artanto, D. Smart monitoring system using NodeMCU for maintenance of production machines. Indones. J. Elec. Eng. Comp. Sci. 2022, 25, 788–795. [Google Scholar] [CrossRef]
- Pokorádi, L. Availability assessment with Monte-Carlo simulation of maintenance process model. Polytech. Univ. Buchar. Sci. Bull. Ser. D Mech. Eng. 2016, 78, 43–54. [Google Scholar]
- Metropolis, N.; Ulam, S. The Monte Carlo Method. J. Am. Stat. Assoc. 1949, 44, 335–341. [Google Scholar] [CrossRef]
- Pokorádi, L. Graph model-based analysis of technical systems. IOP Conf. Ser. Mater. Sci. Eng. 2018, 393, 012007. [Google Scholar] [CrossRef]
- Pokorádi, L. Methodology of Advanced Graph Model-based Vehicle Systems’ Analysis. In Proceedings of the IEEE 18th International Symposium on Computational Intelligence and Informatics (CINTI 2018), Budapest, Hungary, 20–22 November 2018. [Google Scholar]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pokorádi, L. Monte-Carlo Simulation-Based Accessibility Analysis of Temporal Systems. Symmetry 2022, 14, 983. https://doi.org/10.3390/sym14050983
Pokorádi L. Monte-Carlo Simulation-Based Accessibility Analysis of Temporal Systems. Symmetry. 2022; 14(5):983. https://doi.org/10.3390/sym14050983
Chicago/Turabian StylePokorádi, László. 2022. "Monte-Carlo Simulation-Based Accessibility Analysis of Temporal Systems" Symmetry 14, no. 5: 983. https://doi.org/10.3390/sym14050983
APA StylePokorádi, L. (2022). Monte-Carlo Simulation-Based Accessibility Analysis of Temporal Systems. Symmetry, 14(5), 983. https://doi.org/10.3390/sym14050983





