Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks
Abstract
1. Introduction
1.1. Significance of Proposed
1.2. Main Contributions
- Support for parameter security and public key exchange is through the establishment of strict rules in the protocol methodology. Completely hiding public key exchange is to prevent any information or parameters from being leaked to adversaries.
- Integration of QUARK with ECDH is to provide robust keys for both user devices and WSN devices in the health sector.
- Providing a security analysis that tests the proposed protocol using the Scyther tool, in addition to comparing performance and security with the results of recent research.
1.3. Paper Structure
2. Keys Exchange Studies of Related Work
3. Preliminary Techniques for Key Exchange
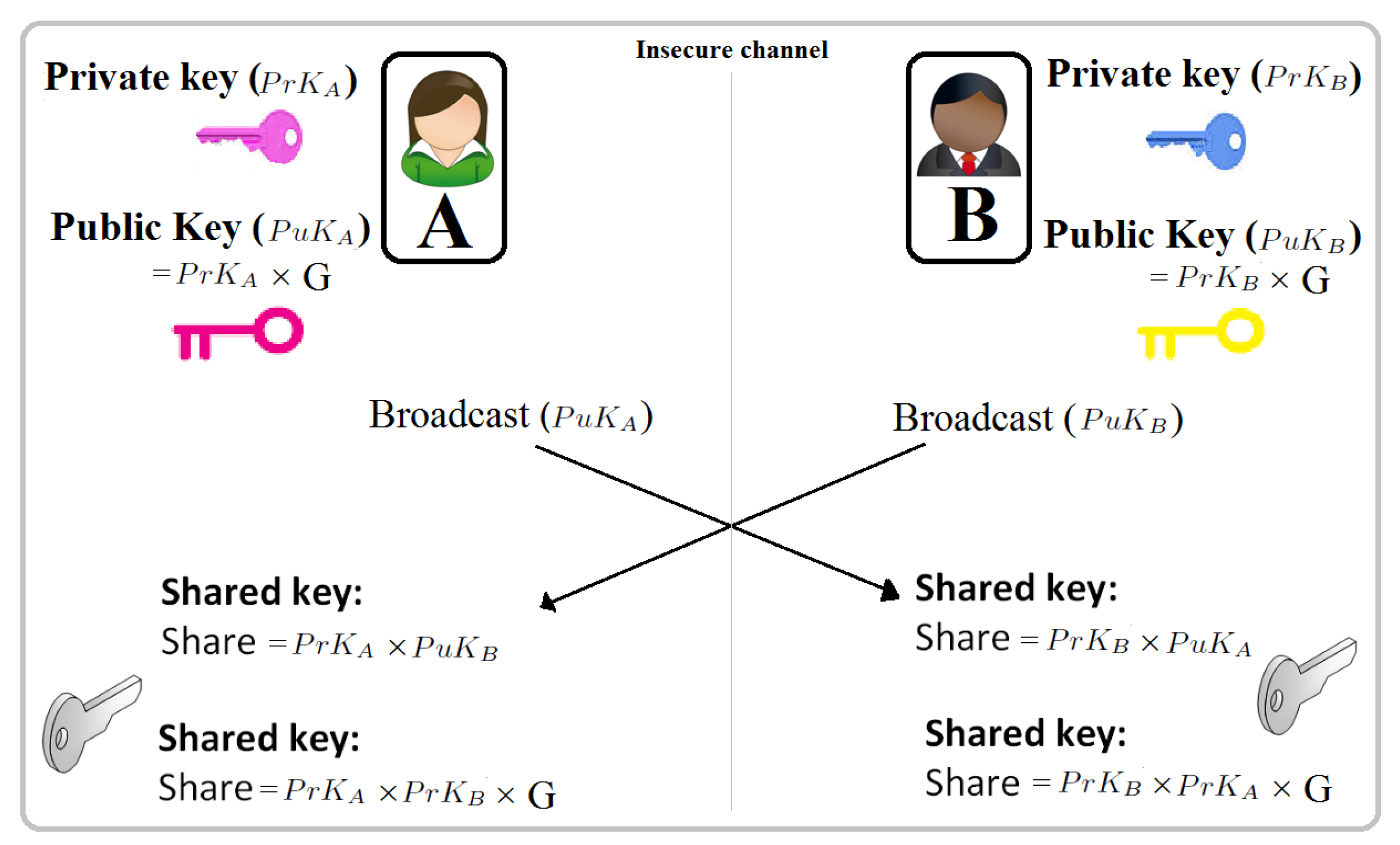
3.1. Elliptic Curve Diffie-Hellman (ECDH)
- First, all parties should agree publicly on elliptic curve parameters (p: prime, a and b: define a curve, G: curve’s generator, n: large integers, h: cofactor) and generate an elliptic curve together.
- −
- Elliptic curve equation values and p,
- −
- Elliptic group from elliptic curve equation values
- −
- G is calculated from that equation of elliptic group
- Next, each party should generate a pair of keys: A private key (), a random point on the curve, and a public key () derived from .
- −
- is a random integer, n, chosen from [1, 1]
- −
- is the product of base point and private key (i.e., )
- Suppose the keys of sender (Alice) be (, ) and keys of the receiver (Bob) be (, ). In order for a message to be encrypted/decrypted, the sender must share their or her with others during communication.
- In the ECDH protocol, a message or data denotes a point in the elliptic curve (x, y).
- The receiver can calculate the point (x, y) and decrypt the message using or .
3.2. QUARK Hash Function
4. The Proposed ECDH Protocol
4.1. Trust Model and Threat Model
4.2. Network Model
4.3. The Proposed Phases
4.3.1. Pre-Deployment Phase
4.3.2. Registration Phase
- retrieves default parameters received from .
- The user’s is computed by one of the input devices either a finger scanner or a camera for IRIS capture. The calculates a timestamp () to use in the following steps.
- The executes a QUARK hash ( or ) on () to obtain a 384-bit MD.
- The user application retrieves the MD from the file stored by default in the user application. This file contains 708 MD (which represents the largest value of time multiplied by 12 × 59). One MD is retrieved depending on the time. For example, if the time is 3:20, the hours are multiplied by minutes to obtain the required input (60). The user application will extract the MD at entry 60 from the file and perform the operation to obtain and to support randomness in the registration phase.
- Then, the user application generates a user registration request () by calculating (where is a user name and is QUARK hash with 384-bit length to specify the user in registration phase), and then sends the to .
- When BS receives the from the user’s device, initially, it truncates to distinguish the user.
- BS specifies , and based on .
- Furthermore, it retrieves based on (the number of hours is multiplied by the number of minutes to specify the entry in the stored file).
- Then extracts by calculating .
- Next, extracts based on , and then calculates through . At this point, tests . If the result matches, it accepts the registration process for that user otherwise the registration process is invalid.
- If the registration is successful, generates new public and private keys and and calculating a new time to check these parameters in the . In addition, it prepares two new and .
- computes confirmation of user registration () through and then sends to the intended .
- The user device receives from and then extracts by truncating the first 384 bits of and compute it with to obtain . In the same way, is obtained, but with the second 384-bit truncation of .
- The user’s device extracts from the third 384 bits in .
- The user’s device calculates the current time and then checks that has reached within the permissible limits of . Then the user’s device stores and in the file instead of the old ones.
- Each sensor uses its stored default parameters (, , and ) to start the registration process.
- Each sensor calculates the current timestamp to prevent many threats such as replay attacks, as well as time is important in our proposal to specify the entry in the hashes file.
- The sensor obtains by calculating the number of hours (Hs) multiplied by the number of minutes (Ms) to arrive at an entry in the file .
- It uses the public key and () to obtain .
- The sensor calculates by calculating the QUARK hash () 256-bit for the input since all sensor parameters (, and ) are hidden and not clearly transmitted in the unsecured channel.
- The sensor performs the operation to hide the public key of .
- At this point, the sensor computes a sensor registration request () by executing , and then sends it to . It is clear that all parameters are hidden when the request goes from the sensor to .
- Receives an SRR request from the sensor. In the same way, it truncates from and characterizes the sensor by .
- In addition, it checks for attacks.
- retrieves the stored to extract via where depends on .
- Then calculates by executing the first 256 bits of and (). Next, use to calculate .
- computes a QUARK hash ( 256-bit) by executing . Then it checks If the result matches, then completes the rest of the registration procedures. Furthermore, matching the result proves that is for a legitimate sensor, the sensor location has not changed and the time is within the specified time period of .
- Furthermore, generates new parameters (, and ) to be used in the next phases.
- prepares new ( and ) to be stored in instead of the old ones, and also sent to the sensor to prevent old from being used.
- prepares a new confirmation of sensor registration () containing , , and and sends them to the sensor where all parameters are hidden and inaccessible to the adversary ().
- When the sensor receives a request from , it uses temporary parameters such as , and the quasi-permanent parameters , and to extract new parameters such as , , and .
- Then checks to make sure that the request was sent within the time specified on the sensor.
- stores the new parameters , and to be used in the next phases.
4.3.3. Keys Update Phase
- Initially the generates keys (private and public ) using the ECDH-384 bits protocol.
- Then the computes by which is used to hide the new public key through user key update ().
- Next, the computes to produce a that depends on the password. This operation is important to hide the new public and private keys on the and store them on the user’s device through the two operations ( and ).
- At this point, the user’s device sends to .
- receives the update request from the . Then it performs the operation (because has databases of , … etc.) to extract the new public key () associated with a given and store it instead of the old one.
- Then generates public and private to connect to the intended user’s device.
- computes key update () to hide the public key of by .
- Then, computes through the operation to hide the public and private keys of the by and and then stores them on the device. At this point, sends to the intended .
- Finally, the receives from and retrieves to extract by the operation and store it on the for use in future connections.
- First, each sensor uses ECDH-224 to generate the public and the private .
- Then each sensor uses through to hide the public key associated with the sensor using the operation.
- Next, each sensor uses to hide the sensor’s public and private keys, then each sensor stores the new keys and sends sensor key update () to to update the public key.
- The receives and retrieves the location of the sensor to extract the new public key by the operation and then stores it in place of the old public key.
- Furthermore, generates the public keys and the private and stores them after they are hidden by the operation.
- computes by and then sends to sensor.
- Sensor receives and retrieves to extract by the operation and then stores the public key for the .
4.3.4. Session Key Distribution Phase
- Initially, the enters , and and generates to increase the randomness of the session key . It then extracts the public and private keys ( and ) using .
- The calculates by , where can be divided into and to be used in the final production. Then, the user’s device performs three processes (, and ) to hide the initial session key, the random number and the user ID (). Then the sends user’s session key request () containing , and to .
- At this point, receives the request from the . uses the public key () to obtain the , then uses the latter to obtain . Then calculates by . Next, uses , and stored plus obtained to find , and then checks the obtained equals computed, if they match, then completes the procedures of the session key distribution phase, otherwise refuses to complete the distribution of the and stops the connection.
- If is validated, generates a new random number and calculates the temporary session key by . Then divides both and into two parts ( and , and ) to obtain a temporary session key through . Finally, completes three processes to hide the temporary session key, , and and to create by then send it to the intended sensor.
- When the sensor receives a request, it uses both the public key () and the sensor identifier () to obtain and . This procedure also enables the sensor to validate both and . Then the sensor extracts the temporary session key by , where consists of and . Then, the sensor computes by which consists of and . The sensor tests for a match of , if it matches it means that the temporary is valid otherwise the sensor will refuse to connect and consider the to be fake.
- If they are identical, the sensor generates a new and calculates the initial session key by which consists of and . At this point, the sensor between the sensor and is consisting of and . It will be used in subsequent encryption and signatures operations that are beyond the scope of this research. Finally, the sensor hides the final session key , the sensor location , and the by , and and then sends these processes after being combined in into .
- receives a request and uses to extract and to extract . Then calculates (where ) by consisting of and . Then tests . If they match then is the final session key between and the sensor otherwise it refuses to connect. Then generates a new with the final session key (that consists of and ) between and user, then hides final and by the processes , and to prevent adversaries from exposing the exchanged keys and network security parameters. Finally, sends a request containing to the to complete the session key distribution phase.
- On the side, the receives the request and extracts to validate the request and extracts to calculate the session key. The user’s device extracts (where ) by . Then the splits into and and tests that if identical then is the final session key between the user and , otherwise the key is modified by adversaries as the will reject it.
4.3.5. Session Key Protection Phase
5. Proposal Results and Findings Discussion
5.1. Analysis of the Proposed Protocol Security
5.1.1. Informal Analysis of the Proposed Protocol Security
- Known session key threat (KSKT) resistance: In insecure environments, the adversary tries to use the keys of the previous sessions to gain access to the keys of the current session. If the adversary can derive the keys of the current session, it becomes legitimate and can perform malicious activities. In the proposed key exchange protocol, all previous and updated session keys are hidden (e.g., ) and not sent explicitly. Furthermore, there is no correlation or relationship between the previous and updated keys. Additionally, there is high randomness using to support robust session key protection. Therefore, the proposal resists this attack with high rigidity.
- Resistance of stolen verify threat (SVT): In this type of attack, the adversary tries to steal security parameters, whether related to users’ devices, sensors, or the network. Stolen validation parameters can simply give the adversary authentication and verification in the network. The adversary tries to access the database containing confidential information by hacking users’ devices and sensors. In the proposed key exchange protocol, all security parameters such as and keys are either session or private keys, even public keys are not explicitly stored. For example, the public key of a particular user’s device is hidden by , also, the password is not stored on the user’s device (). Therefore, the adversary cannot derive the keys and security parameters. The proposed protocol thus successfully counters the threat of a stolen verifier.
- Session key and security condition (SKSC): In order for a session key to be secure, it must be protected from accessing its analysis and derivation by the adversary. In our protocol, the adversary cannot access, derive or analyze security parameters or keys because first the session key is not repeated in subsequent sessions and second, the session key between the user’s device and such as is different from the session key between BS and S as . Furthermore, all security parameters such as sensor location and keys such as the public key are sent to the recipient anonymously as . Therefore, deriving or computing the session key by the adversary is very difficult in our protocol. Thus, the security condition of the session key in our protocol is high and suitable for protecting patients’ data.
- Providing perfect forward secrecy (PFS): In this attack, the adversary tries to take advantage of the current session key and long-term security parameters (assuming that it can access the session key); it cannot take advantage of this key in subsequent sessions because in our protocol the keys for subsequent sessions do not depend on the keys of the current sessions. Furthermore, the session key in our protocol is unique and random through the execution of , even if the adversary can access the long-term parameters such as , ⋯, etc. It cannot be used to derive subsequent (future) session keys because the value in our proposed protocol provides randomness within the implementation of the function. Hence our proposed protocol efficiently provides PFS.
- Random parameters detection threat (RPDT) resistance: The goal of this attack is to obtain random parameters to help expose the session key and other keys to network entities. The adversary tries to detect random parameters such as , , and to obtain the other security parameters. Even if the adversary exposes the random parameters, he/she cannot access the session key because the initial session key for each entity consists of two parts such as and the final session key is agreed as between entities depending on multiple processes as shown in Figure 8. Moreover, random parameters are not explicitly sent over the network such as . Therefore, our proposed protocol withstands RPDT.
- Key recovery threat (KRT) resistance: In this type of attack, the adversary tries to extract the key assuming that the attacker has the plaintext and ciphertext. This attack is not viable if the security parameters are chosen appropriately. The proposed ECDH protocol generates security keys of sufficient length (384 bits) to block this attack. Furthermore, our protocol does not suffer from information leakage or security parameters that help to extract the keys. Moreover, random key generation in addition to the regular generation of these keys prevents hacking of our protocol. Therefore, our proposed protocol successfully counteracts this threat.
- Known-session-specific temporary threat (KSSTT) resistance: Detection of some temporary information can lead to session key exposure in vulnerable key exchange protocols. For example, the adversary tries to reveal temporary random values or parameters to obtain the session key. In our proposed protocol, it is very difficult for the adversary to obtain the random values, such as , but if we assume that the adversary can obtain the random values in the session, he/she cannot obtain the session key () because it relies on other permanent parameters such as or semi-permanent parameters such as and not stored by users’ devices. Even if the adversary can obtain the random value and the value, it will not be able to reveal the session key. Thus, our protocol reliably combats a KSSTT.
- User impersonation threat (UIT) resistance: To accomplish the impersonation threat, the adversary needs to prepare a login request that contains valid information (such as keys and security parameters) for a legitimate user. Fortunately, our protocol relies on the security parameters and (two factors authentication), the adversary does not have access to these security parameters because these parameters are not stored on and are not explicitly transmitted from sender to recipient. Thus, the adversary cannot imitate the user’s device, i.e., our protocol aptly resists this threat.
- Sensor node impersonation threat (SIT) resistance: Similar to the previous attack, the adversary needs secret information to imitate the sensor. In our protocol, the adversary can only imitate sensors when secret parameters such as , , and are obtained. As all these parameters are hidden securely, whether in storage or transmission. For instance, even if the adversary penetrates the sensor, he/she cannot extract the private key . Therefore, our proposed protocol successfully resists the SIT.
- Post-deployment keys threat (PDKT) resistance: Sometimes the adversary exploits key exchange vulnerabilities post-deployment of sensors, adding a user device to the network or in the case of updating the public/private keys of users’ devices and sensors. In all of these cases, the adversary tries to derive, alter or block/intercept the keys. Our protocol generates public and private keys on a regular basis. In the phase of user and sensor key update (Figure 7), the adversary cannot derive the keys because they are hidden () when transmitting via the unsecured channel and protected () when stored in users’ devices or sensors. Furthermore, the adversary cannot prevent the user/sensor update request for the keys from reaching the intended target because the user/sensor device will wait for the request which means the key update is completed. Thus, our protocol successfully resists PDKT.
- User/sensor session key verification (U/SSKV) threat resistance: In this attack, the adversary attempts to fail the session key verification completion to prevent the use of a legitimate session key between entities. In our protocol, all entities (, and S) produce primary keys (, and ) to eventually obtain final keys (, , and ) after completion of in verification request . The adversary does not know the parameters of the verification request and cannot falsify it because it is hidden and any manipulation of it will be clear to the receiver. As a result, our protocol worthily provides U/SSKV property.
- Session key computation threat (SKCT) resistance: This attack relies on obtaining a session key creation/updating request. The adversary tries to analyze the session key request to compute it. In our protocol, each session key consists of two parts (, and ), one part is used to produce the final session key and the other part is used for verification (see Figure 8). For example, (on the user’s device side) is used to produce the session key while is used to verify the session key. In our protocol, the adversary cannot compute the session key because first, all the parameters are hidden, secondly, the adversary does not know how to generate the initial and final keys for the session keys. Thus, our protocol ably resists this threat.
- Resistance of off-line password guessing threat (OPGT): In this threat, the adversary tries to guess the passwords in the requests transmitted between the sender and the recipient. After the adversary obtains some key exchange or registration request, he/she tries different methods, such as a dictionary and brute force, to guess the correct passwords. In our protocol, first, the passwords are not stored on . Furthermore, users’ passwords are not explicitly transmitted over the network. Throughout our protocol phases (Figure 6, Figure 7 and Figure 8), passwords are used within a QUARK hash of length 256 MD with or 384 MD with (i.e., ) which it is impossible for an adversary to extract the password from even if the adversary has some parameters such as and . Therefore, our protocol successfully resists the OPGT.
- Resistance of jamming threat (JT): This is a type of service obfuscation threat that mainly targets servers and . The adversary sends unnecessary packets at the same network frequency to stop services. The adversary can use it in many forms such as constant, deceptive, random and reactive. Our protocol uses authentication procedures that greatly mitigate this threat. Since our protocol uses in to authenticate the registration of both the user and sensor. Thus, our protocol provides resistance to this type of threat.
5.1.2. Formal Analysis of the Proposed Protocol Security
- Scyther Summary:
- Secret: Keeping secret terms
- Alive: Proof that key exchange protocol steps are implemented in the network entity.
- Weakagree: Ensuring that an impersonation threat will not be carried out by an adversary
- Nisynch: Verifying that send and receive requests are between two connected entities
- Niagree: Ensuring that transmission and receiving requests are transmitted in the correct order and integrated data between network entities
- Match: Testing the equality of two variables or assigning a value to a variable
- Proposed ECDH-QUARK Protocol with Scyther:
- Results:
5.2. Performance Analysis of the Proposed Protocol
- Computational costAll key exchange protocols require a computational cost evaluation of the embedded security measures to demonstrate their applicability. Therefore, we tested the execution of security processes to obtain the execution time for all these processes, Table 2 shows the execution time for key exchanges such as , and . To illustrate the computational costs, we compare our protocol with existing key exchange protocols ([3,23,26,28,30,31,38]), where costs are evaluated across all network components (, and S) and then the total cost and time cost are calculated (see Table 3). For comparing costs of computation, there are some acronyms that should be defined and some of which may not be used in our protocol.
- −
- Execution time for symmetric encryption ()
- −
- Execution time for fuzzy extractor ()
- −
- Execution time for hash function ()
- −
- Standard hash function () and lightweight hash function ()
We tested the computation costs in the user device and sensor session key distribution phase (Figure 8) with existing key exchange protocols, because the registration and update phases are not applied continuously. Furthermore, the costs of the and XOR operations are small and negotiable so we do not include them in the computation costs comparison. We can see from Table 3 that the computational costs in our protocol are + + , + + and + + , as well as the total cost, is + + that is the best of all recent key exchange protocols. Furthermore, our protocol implements a lightweight hash () algorithm that is QUARK to generate light session keys compared to existing protocols that implement standard hash (SH). Moreover, the cost of execution time for existing protocols such as [3] = 0.1453 s, [26] = 8.9730 ms, [28] = 94.903 ms, [31] = 110.50 s and [38] = 421.25 ms consumes a big execution time (which will negatively affect resource-constrained sensors) compared to our protocol which needs ≈0.012816 ms.In Baghbanijam and Sanaei [3], the key exchange phase requires encryption and therefore the execution time cost will be very large compared to our proposed protocol. Phimphinith et al. [23] and Wu et al. [30] did not specify execution time costs and thus it is difficult to make a comparison with our protocol. Rangwani et al. [26] and Gope and Sikdar [28] used many parameters such as using more than six hashes, which makes key exchange complicated to calculate. In Wu et al. [31], the authors used the AKE protocol which performs complex operations due to the execution of 11 which greatly affects the performance. Similarly, another paper Qi and Chen [38] relied on AKE with ECC to apply key exchange with two factors authentication. However, AKE is not compatible with WSN-based health networks. The authors of this paper indicated that the sensor computation cost is 136.35 ms, while in our protocol the sensor computation cost is 0.004272 ms. After evaluating the computation costs, we note that the proposed key exchange protocol offers the best performance out of the existing protocols. - Communication cost Another important aspect of evaluating key exchange protocols is the calculation of communication costs. In our user and sensor session key distribution phase (Figure 8), each entity has a communication cost, for example, needs = 384 bits, = 64 bits and = 32 bits, where the cost of = 384 bits, = 64 and = 384 bits. Thus, the communication cost of becomes 832 bits, which is similar to the costs of = 832 bits and S = 832 bits. As a result, the total cost of communication in our protocol is 2496 bits. By comparing our protocol with the communication costs in Table 4, we notice that our protocol outperforms the protocols in [30,31] in terms of data size. Although the protocol in [38] performs three handshakes and a data size of 2368 bits, compared to our protocol that performs four handshakes and a data size of 2496 bits; this does not reflect the overall performance of the protocol [38], as our protocol (which uses 1) outperforms the protocol in Qi and Chen [38] (which uses 6) in computation cost. In addition, their protocol contains a clear security breach when it reduces the number of handshakes from 4 to 3, as there are no parameters checked (third handshake) in between S and . Thus, our protocol balances security and performance to outperform existing protocols in terms of communication cost.
6. Limitations of Proposed Protocol
7. Conclusions and Future Work
- Test the proposed protocol on actual health applications such as surgeries that require high speed and security to exchange keys in joining and leaving the network. Especially when the surgeon is not present in the surgical procedure, but rather supervises it online.
- This proposal deals with the exchange of keys and the distribution of session keys securely between network entities, we intend to develop this proposal in the use of these keys to accomplish the processes of encryption and signing of patient data and information.
- Test our proposal on wearable and implantable health sensors in the human body to assess energy consumption and calculate the computational cost and complexity.
Funding
Conflicts of Interest
Abbreviations
| , , , | Adversary, base station, sensor, user device |
| Public keys of users, sensors, and | |
| Private keys of users, sensors, and | |
| Session keys between sensors and , users and | |
| Temporary session key | |
| Identifiers of users and sensors | |
| Sensors locations | |
| , | Users’ passwords and biometrics |
| User name | |
| Random numbers for sensors, users and | |
| or | One-way QUARK hash function |
| Concatenation and exclusive or operations |
References
- Frimpong, E.; Michalas, A. IoT-cryptodiet: Implementing a lightweight cryptographic library based on ECDH and ECDSA for the development of secure and privacy-preserving protocols in contiki-NG. In Proceedings of the IoTBDS 2020, Prague, Czech Republic, 7–9 May 2020; pp. 101–111. [Google Scholar]
- Awaad, M.H.; Jebbar, W.A. Prolong the lifetime of WSN by determining a correlation nodes in the same zone and searching for the best not the closest CH. Int. J. Mod. Educ. Comput. Sci. 2014, 6, 31. [Google Scholar] [CrossRef][Green Version]
- Baghbanijam, S.; Sanaei, H. An improved authentication & key exchange protocol based on ECDH for WSNs. arXiv 2021, arXiv:2109.11450. [Google Scholar]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. REISCH: Incorporating lightweight and reliable algorithms into healthcare applications of WSNs. Appl. Sci. 2020, 10, 2007. [Google Scholar] [CrossRef]
- Awaad, M.H. The use of dynamic sliding window with IPSec. J. Educ. Pure Sci. 2014, 4, 278–289. [Google Scholar]
- Awaad, M.H. Improve the effectiveness of sensor networks and extend the network lifetime using 2BSs and determination of area of CHs choice. J. Comput. Sci. Control. Syst. 2014, 7, 15. [Google Scholar]
- Abdulhameed, H.A.; Abdalmaaen, H.F.; Mohammed, A.T.; Mosleh, M.F.; Abdulhameed, A.A. A lightweight hybrid cryptographic algorithm for WSNs tested by the diehard tests and the raspberry Pi. In Proceedings of the 2022 International Conference on Computer Science and Software Engineering (CSASE), Duhok, Iraq, 15–17 March 2022; pp. 271–276. [Google Scholar]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. RAMHU: A new robust lightweight scheme for mutual users authentication in healthcare applications. Secur. Commun. Netw. 2019, 2019, 3263902. [Google Scholar] [CrossRef]
- Heigl, M.; Schramm, M.; Fiala, D. A lightweight quantum-safe security concept for wireless sensor network communication. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 906–911. [Google Scholar]
- Ametepe, A.F.-X.; Ahouandjinou, A.S.; Ezin, E.C. Robust encryption method based on AES-CBC using elliptic curves Diffie–Hellman to secure data in wireless sensor networks. Wirel. Netw. 2022, 28, 991–1001. [Google Scholar] [CrossRef]
- Marhoon, A.F.; Awaad, M.H.; Jebbar, W.A. A new algorithm to improve LEACH protocol through best choice for cluster-head. Int. J. Adv. Eng. Sci. 2014, 4, 1–12. [Google Scholar]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. PAX: Using pseudonymization and anonymization to protect patients’ identities and data in the healthcare system. Int. J. Environ. Res. Public Health 2019, 16, 1490. [Google Scholar] [CrossRef]
- Aikins-Bekoe, S.; Hayfron-Acquah, J.B. Elliptic curve diffie-hellman (ECDH) analogy for secured wireless sensor networks. Int. J. Comput. Appl. 2020, 176, 1–8. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. Efficient and secure ECDSA algorithm and its applications: A survey. Int. J. Commun. Netw. Inf. Secur. (IJCNIS) 2019, 11, 7–35. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. User authentication into electronic health record based on reliable lightweight algorithms. In Handbook of Research on Cyber Crime and Information Privacy; IGI Global: Hershey, PA, USA, 2021; pp. 700–738. [Google Scholar]
- Almansoori, M.N.; Elshamy, A.A.; Mustafa, A.A.M. Secure Z-MAC protocol as a proposed solution for improving security in WSNs. Information 2022, 13, 105. [Google Scholar] [CrossRef]
- Nagesh, O.; Naresh, V.S. Comparative analysis of MOD-ECDH algorithm with various algorithms. Int. J. Ind. Eng. Prod. Res. 2020, 31, 301–308. [Google Scholar]
- Wu, T.-Y.; Yang, L.; Meng, Q.; Guo, X.; Chen, C.-M. Fog-driven secure authentication and key exchange scheme for wearable health monitoring system. Secur. Commun. Netw. 2021, 2021, 8368646. [Google Scholar] [CrossRef]
- Kim, M.; Moon, J.; Won, D.; Park, N. Revisit of password-authenticated key exchange protocol for healthcare support wireless communication. Electronics 2020, 9, 733. [Google Scholar] [CrossRef]
- Alzahrani, B.A. Secure and efficient cloud-based IoT authenticated key agreement scheme for e-health wireless sensor networks. Arab. J. Sci. Eng. 2021, 46, 3017–3032. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and privacy in IoT-cloud-based e-health systems—A comprehensive review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Kardi, A.; Zagrouba, R. Hybrid cryptography algorithm for secure data communication in WSNs: DECRSA. In Congress on Intelligent Systems; Springerr: Berlin/Heidelberg, Germany, 2020; pp. 643–657. [Google Scholar]
- Phimphinith, A.; Anping, X.; Zhu, Q.; Jiang, Y.; Shen, Y. An enhanced mutual authentication scheme based on ECDH for IoT devices using ESP8266. In Proceedings of the 2019 IEEE 11th International Conference on Communication Software and Networks (ICCSN), Chongqing, China, 12–15 June 2019; pp. 490–496. [Google Scholar]
- Hasan, N.A.; Farhan, A.K. Security improve in ZigBee protocol based on RSA public algorithm in WSN. Eng. Technol. J. 2019, 37, 67–73. [Google Scholar] [CrossRef]
- Lin, H.Y. Integrate the hierarchical cluster elliptic curve key agreement with multiple secure data transfer modes into wireless sensor networks. Connect. Sci. 2022, 34, 274–300. [Google Scholar] [CrossRef]
- Rangwani, D.; Sadhukhan, D.; Ray, S.; Khan, M.K.; Dasgupta, M. An improved privacy preserving remote user authentication scheme for agricultural wireless sensor network. Trans. Emerg. Telecommun. Technol. 2021, 32, e4218. [Google Scholar] [CrossRef]
- Thabit, F.; Alhomdy, S.; Al-Ahdal, A.H.; Jagtap, S. A new lightweight cryptographic algorithm for enhancing data security in cloud computing. Glob. Transitions Proc. 2021, 2, 91–99. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. A privacy-aware reconfigurable authenticated key exchange scheme for secure communication in smart grids. IEEE Trans. Smart Grid. 2021, 12, 5335–5348. [Google Scholar]
- Mehra, P.S.; Doja, M.N.; Alam, B. Codeword authenticated key exchange (cake) light weight secure routing protocol for WSN. Int. J. Commun. Syst. 2019, 32, 1–27. [Google Scholar]
- Wu, T.-Y.; Yang, L.; Lee, Z.; Chu, S.-C.; Kumari, S.; Kumar, S. A provably secure three-factor authentication protocol for wireless sensor networks. Wirel. Commun. Mob. Comput. 2021, 2021, 5537018. [Google Scholar] [CrossRef]
- Wu, T.-Y.; Lee, Z.; Yang, L.; Luo, J.-N.; Tso, R. Provably secure authentication key exchange scheme using fog nodes in vehicular ad hoc networks. J. Supercomput. 2021, 77, 6992–7020. [Google Scholar] [CrossRef]
- Lu, X.; Li, B.; Liu, M.; Lin, D. Improved conditional differential attacks on lightweight hash family QUARK. Cybersecurity 2022, 5, 1–16. [Google Scholar] [CrossRef]
- Abed, S.; Jaffal, R.; Mohd, B.J.; Al-Shayeji, M. An analysis and evaluation of lightweight hash functions for blockchain-based IoT devices. Clust. Comput. 2021, 24, 3065–3084. [Google Scholar] [CrossRef]
- Gupta, D.N.; Kumar, R. Sponge based lightweight cryptographic hash functions for IoT applications. In Proceedings of the 2021 International Conference on Intelligent Technologies (CONIT), Hubli, India, 25–27 June 2021; pp. 1–5. [Google Scholar]
- Cremers, C. Scyther User Manual-Draft 18 February 2014. 2014. Available online: https://people.cispa.io/cas.cremers/scyther/ (accessed on 3 August 2022).
- Mohammad, Z. Cryptanalysis and improvement of the yak protocol with formal security proof and security verification via Scyther. Int. J. Commun. Syst. 2020, 33, e4386. [Google Scholar] [CrossRef]
- Amin, R.; Lohani, P.; Ekka, M.; Chourasia, S.; Vollala, S. An enhanced anonymity resilience security protocol for vehicular ad hoc network with Scyther simulation. Comput. Electr. Eng. 2020, 82, 106554. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J. Secure authenticated key exchange for WSNs in IoT applications. J. Supercomput. 2021, 77, 13897–13910. [Google Scholar] [CrossRef]








| TR | Ametepe et al. [10] | Kardi and Zagrouba [22] | Lin [25] | Rangwani et al. [26] | Thabit et al. [27] | Gope and Sikdar [28] | Mehra et al. [29] | Wu et al. [30] | Wu et al. [31] | Proposed |
|---|---|---|---|---|---|---|---|---|---|---|
| KSKT | √ | |||||||||
| SVT | √ | √ | √ | √ | ||||||
| SKSC | √ | √ | √ | |||||||
| PFS | √ | √ | √ | √ | √ | √ | ||||
| RPDT | √ | √ | √ | |||||||
| KRT | √ | √ | √ | |||||||
| KSSTT | √ | √ | √ | √ | ||||||
| UIT | √ | √ | √ | √ | √ | √ | ||||
| SIT | √ | √ | √ | |||||||
| PDKT | √ | |||||||||
| U/SSKV | √ | √ | √ | |||||||
| SKCT | √ | √ | √ | √ | √ | |||||
| OPGT | √ | √ | √ | √ | √ | |||||
| JT | √ | √ |
| Notation | Description | Time Cost |
|---|---|---|
| c-QUARK hash function | 0.002892 ms | |
| Key exchange (ECDH) | 0.000847 ms | |
| Scalar multiplication | 0.000533 ms | |
| Symmetric encryption | - | |
| Fuzzy extractor | - | |
| One-way hash function | - |
| Protocol | S | Total | Exchange Type | Hash | Time Cost | ||
|---|---|---|---|---|---|---|---|
| Baghbanijam and Sanaei [3] | + + | + + | + | + + | ECDH | SH | 0.1453 s |
| Phimphinith et al. [23] | + + | + + | - | + + | ECDH | - | - |
| Rangwani et al. [26] | + + | + + | + + | + + | ECDH | SH | 8.9730 ms |
| Gope and Sikdar [28] | + | + | - | + | AES-CBC | SH | 94.903 ms |
| Wu et al. [30] | + + | + | + | + + | - | - | - |
| Wu et al. [31] | + + + | + + | + + | + + + | ECDH | SH | 110.50 s |
| Qi and Chen [38] | + + | + + | + + | + + | ECC + AKE | SH | 421.25 ms |
| Proposed | + + | + + | + + | + + | ECDH | LH | 0.012816 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Zubaidie, M. Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks. Symmetry 2023, 15, 152. https://doi.org/10.3390/sym15010152
Al-Zubaidie M. Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks. Symmetry. 2023; 15(1):152. https://doi.org/10.3390/sym15010152
Chicago/Turabian StyleAl-Zubaidie, Mishall. 2023. "Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks" Symmetry 15, no. 1: 152. https://doi.org/10.3390/sym15010152
APA StyleAl-Zubaidie, M. (2023). Implication of Lightweight and Robust Hash Function to Support Key Exchange in Health Sensor Networks. Symmetry, 15(1), 152. https://doi.org/10.3390/sym15010152








