Secure Registration Protocol for the Internet of Drones Using Blockchain and Physical Unclonable Function Technology
Abstract
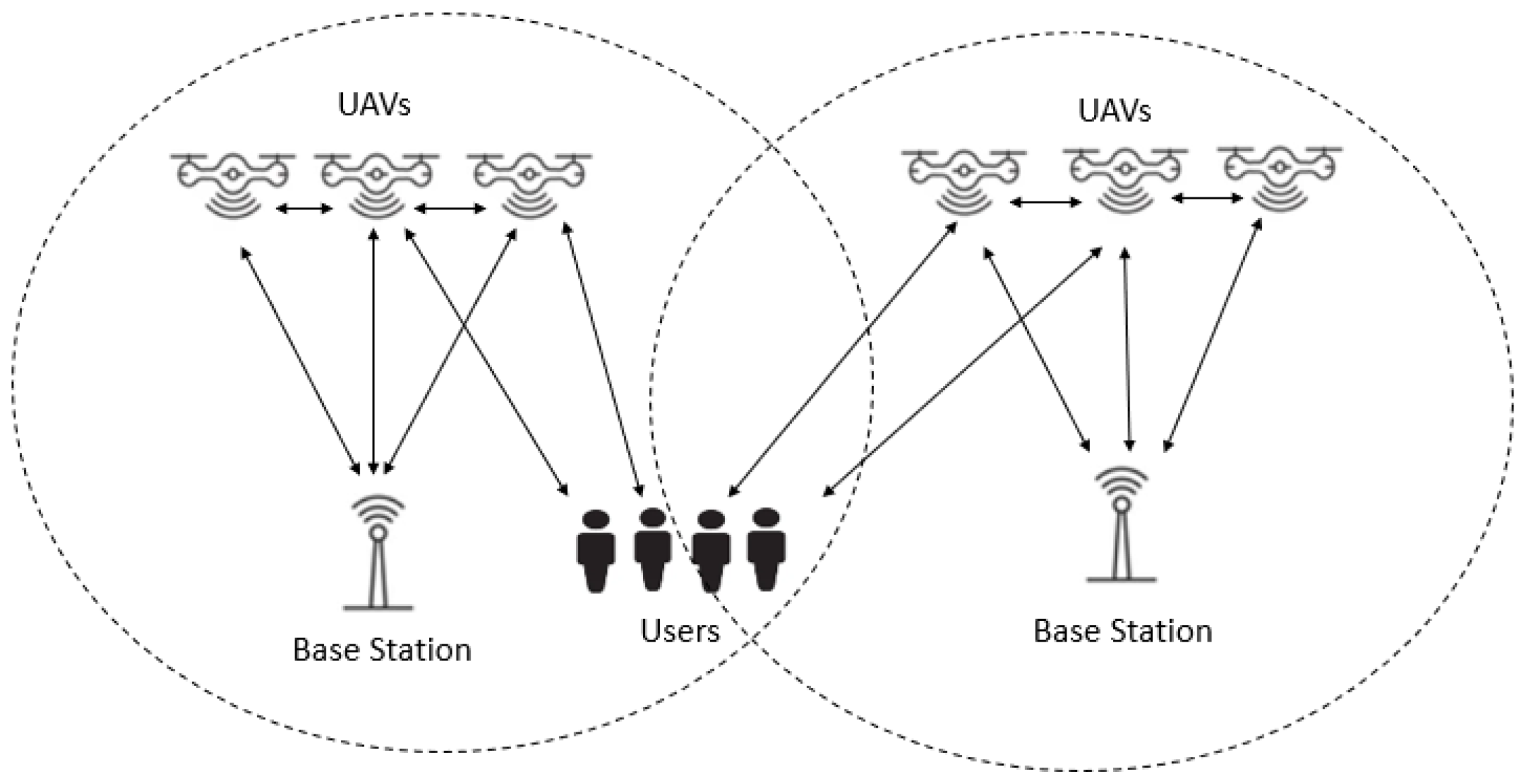
:1. Introduction
1.1. Related Work
1.2. Our Contribution
1.3. Outline of Article
2. Preliminaries
- is a probabilistic algorithm and requires the security parameter κ, which determines the length of the key as an input to generate a key. The output key K is .
- To generate a tag for a message, the algorithm inputs a key K and the message . The output tag t is denoted by . must be a deterministic algorithm.
- To verify the authenticity of a message, the verification algorithm inputs a key K, a message m, and a tag t. The algorithm’s output is a bit b, where indicates validity and indicates invalidity. It is assumed that is deterministic, and we express this as .
- is a probabilistic algorithm and inputs the security parameter to generate a key. The output of the algorithm is a random key .
- is a probabilistic encryption algorithm that requires key K and plaintext , and outputs a ciphertext c.
- is a deterministic decryption algorithm that inputs key K and ciphertext c. The output of is the plaintext m.
3. The Proposed Scheme
3.1. Registration
ARP Table
3.2. Communication
4. Security Analysis
4.1. Security Requirements
- Authentication of parties.
- (a)
- Authentication of a new drone: it should not be possible for an adversary to act like a legitimate drone.
- (b)
- Authentication of the base station: adversaries should not be able to impersonate a legal base station.
- (c)
- Authentication of the other drones: adversaries should not be able to impersonate the other legal drones.
- Secrecy of the key: during the key exchange, the newly generated key remains confidential, and an adversary should not have any information about the new key.
- Key freshness: a new, randomly chosen key should be exchanged during a protocol runs.
- Parties must confirm that the other party knows the new symmetric key and their ability to use it.
4.2. Adversarial Model
- The entire network is controlled by the adversary, who can act like a legitimate drone, intercepting, composing and creating any message, and is only constrained by the limitations of cryptographic techniques.
- The adversary can initiate the protocol with any party and can be a receiver to any party.
4.3. Formal Model
4.4. Security Properties
- Drone capture attack: When physically capturing a drone, it is of the utmost importance to ensure that the attacker cannot extract any sensitive data. This precautionary measure is necessary to defend against potential breaches of secrecy of the information. In our case, the drone does not store the secret keys in the memory because of the PUF solution. PUF values cannot be extracted from the drones after they are closed. In our case, after the production, the PUF value is retrieved and stored on the blockchain by the manufacturer, who closes the system. Hence, the adversaries cannot gain information about the PUF value, not even by physical tampering.
- Denial of service: Since most of the drones are resource-constrained, it is essential for them to be able to withstand various denial-of-service attacks. We consider the DOS attack only on the protocol level. Regarding the registration protocol, it is an important aspect that all messages are authenticated. If the validation fails, the incoming request is dropped. On the other hand, all calculations, including verifications, are chosen to be lightweight, and a time limit is also set for incoming responses.
- Forward and backward key secrecy: In the case of registration, the secret keys exchanged are randomized, and hence they are independent. If a secret key is leaked, neither the previous keys nor the latter ones can be calculated. Hence, forward and backward secrecy of the keys is assured.
- Jamming attacks: Many anti-jamming techniques exist today, including frequency and channel hopping, frame masking or special antenna designs for spatial filtering, but most of them are not suitable in practice. However, LoRa can utilize redundancy to improve packet resilience against jamming attacks by configuring a code rate (CR) parameter, controlling the ratio of the actual data to the forward-error-correcting capability added to the payload. The disadvantage of this solution is that the data rate may be reduced.
5. Practical Issues
5.1. Prototype
5.2. Proof of Concept
5.3. LoRa
5.4. Advantages of LoRa Technology for the Internet of Drones
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A

| Listing A1. Smart contract for extracting and adding PUF keys. |
 |
References
- Jan, S.U.; Khan, H.U. Identity and aggregate signature-based authentication protocol for IoD deployment military drone. IEEE Access 2021, 9, 130247–130263. [Google Scholar] [CrossRef]
- Haque, M.S.; Chowdhury, M.U. A new cyber security framework towards secure data communication for unmanned aerial vehicle (UAV). In Proceedings of the Security and Privacy in Communication Networks: SecureComm 2017 International Workshops, ATCS and SePrIoT, Niagara Falls, ON, Canada, 22–25 October 2017; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2018; pp. 113–122. [Google Scholar]
- Nyangaresi, V.; Petrovic, N. Efficient PUF Based Authentication Protocol for Internet of Drones. In Proceedings of the 2021 International Telecommunications Conference (ITC-Egypt), Alexandria, Egypt, 13–15 July 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.U.; Amin, N.U. An Efficient and Provably Secure Certificateless Key-Encapsulated Signcryption Scheme for Flying Ad-hoc Network. IEEE Access 2020, 8, 36807–36828. [Google Scholar] [CrossRef]
- Li, J.; Wang, Y.; Ding, Y.; Wu, W.; Li, C.; Wang, H. A certificateless pairing-free authentication scheme for unmanned aerial vehicle networks. Secur. Commun. Netw. 2021, 2021, 1–10. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Abdullah, A.M.; Mohsan, S.A.H.; Noor, F. An Efficient and Conditional Privacy-Preserving Heterogeneous Signcryption Scheme for the Internet of Drones. Sensors 2023, 23, 1063. [Google Scholar] [CrossRef] [PubMed]
- Won, J.; Seo, S.H.; Bertino, E. A secure communication protocol for drones and smart objects. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, New York, NY, USA, 14 April–17 March 2015; pp. 249–260. [Google Scholar]
- Singh, J.; Venkatesan, S. Blockchain mechanism with Byzantine fault tolerance consensus for Internet of Drones services. Trans. Emerg. Telecommun. Technol. 2021, 32, e4235. [Google Scholar] [CrossRef]
- Aggarwal, S.; Shojafar, M.; Kumar, N.; Conti, M. A new secure data dissemination model in internet of drones. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Alqarni, K.S.; Almalki, F.A.; Soufiene, B.O.; Ali, O.; Albalwy, F. Authenticated Wireless Links between a Drone and Sensors Using a Blockchain: Case of Smart Farming. Wirel. Commun. Mob. Comput. 2022, 2022, 4389729. [Google Scholar] [CrossRef]
- Semal, B.; Markantonakis, K.; Akram, R.N. A Certificateless Group Authenticated Key Agreement Protocol for Secure Communication in Untrusted UAV Networks. In Proceedings of the 2018 IEEE/AIAA 37th Digital Avionics Systems Conference (DASC), London, UK, 23–27 September 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Pu, C.; Li, Y. Lightweight authentication protocol for unmanned aerial vehicles using physical unclonable function and chaotic system. In Proceedings of the 2020 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), London, UK, 10–11 July 2023; IEEE: New York, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted internet of drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Gope, P.; Millwood, O.; Saxena, N. A provably secure authentication scheme for RFID-enabled UAV applications. Comput. Commun. 2021, 166, 19–25. [Google Scholar] [CrossRef]
- Alladi, T.; Naren; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A Novel Authentication Scheme for UAV-Ground Station and UAV-UAV Communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Bera, B.; Saha, S.; Das, A.K.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-Envisioned Secure Data Delivery and Collection Scheme for 5G-Based IoT-Enabled Internet of Drones Environment. IEEE Trans. Veh. Technol. 2020, 69, 9097–9111. [Google Scholar] [CrossRef]
- Tan, Y.; Liu, J.; Kato, N. Blockchain-Based Key Management for Heterogeneous Flying Ad Hoc Network. IEEE Trans. Ind. Informatics 2021, 17, 7629–7638. [Google Scholar] [CrossRef]
- Samanth, S.; Kv, P.; Balachandra, M. Security in Internet of Drones: A Comprehensive Review. Cogent Eng. 2022, 9, 2029080. [Google Scholar] [CrossRef]
- Dworkin, M. Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2007. [Google Scholar]
- Alasmary, H.; Tanveer, M. ESCI-AKA: Enabling Secure Communication in an IoT-Enabled Smart Home Environment Using Authenticated Key Agreement Framework. Mathematics 2023, 11, 3450. [Google Scholar] [CrossRef]
- Tanveer, M.; Badshah, A.; Khan, A.U.; Alasmary, H.; Chaudhry, S.A. CMAF-IIoT: Chaotic map-based authentication framework for Industrial Internet of Things. Internet Things 2023, 23, 100902. [Google Scholar] [CrossRef]
- Menezes, A.; Vanstone, S.; Okamoto, T. Reducing elliptic curve logarithms to logarithms in a finite field. In Proceedings of the Twenty-Third Annual ACM Symposium on Theory of Computing, New Orleans, LA, USA, 5–8 May 1991; pp. 80–89. [Google Scholar]
- Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse fuzzy extractors: Enabling lightweight mutual authentication for PUF-enabled RFIDs. In Proceedings of the Financial Cryptography and Data Security: 16th International Conference, FC 2012, Kralendijk, Bonaire, 27 Februray–2 March 2012; Revised Selected Papers 16. Springer: Berlin/Heidelberg, Germany, 2012; pp. 374–389. [Google Scholar]
- Delvaux, J.; Gu, D.; Verbauwhede, I.; Hiller, M.; Yu, M.D. Efficient fuzzy extraction of PUF-induced secrets: Theory and applications. In Proceedings of the International Conference on Cryptographic Hardware and Embedded Systems, Santa Barbara, CA, USA, 17–19 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 412–431. [Google Scholar]
- Bashir, I. Mastering Blockchain; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Buterin, V. Ethereum White Paper: A Next Generation smart Contract & Decentralized Application Platform (2013). Available online: https://github.com/ethereum/wiki/wiki/White-Paper (accessed on 1 January 2023).
- Alom, I.; Ferdous, M.S.; Chowdhury, M.J.M. BlockMeter: An Application Agnostic Performance Measurement Framework for Private Blockchain Platforms. IEEE Trans. Serv. Comput. 2023, 1–14. [Google Scholar] [CrossRef]
- Blanchet, B. Modeling and Verifying Security Protocols with the Applied Pi Calculus and ProVerif; INRIA: Paris, France, 2016; Volume 1, pp. 1–135. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wang, X.; Yin, Y.L.; Yu, H. Finding collisions in the full SHA-1. In Proceedings of the Advances in Cryptology–CRYPTO 2005: 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Proceedings 25. Springer: Berlin/Heidelberg, Germany, 2005; pp. 17–36. [Google Scholar]
- Prototype GitHub Link. Available online: https://github.com/Gepsonka/TDK (accessed on 1 January 2023).
- Semtech. What Is LoRa? Available online: Https://www.semtech.com/lora/what-is-lora (accessed on 1 January 2023).
- Sponas, J.G. Things You Should Know About Bluetooth Range. Available online: https://blog.nordicsemi.com/getconnected/things-you-should-know-about-bluetooth-range (accessed on 1 January 2023).
- Mitchell, B. What Is the Range of a Typical Wi-Fi Network? 2020. Available online: https://www.lifewire.com/range-of-typical-wifi-network-816564 (accessed on 1 January 2023).
- Simmons, A. Cell Tower Range: How Far Do They Reach? 2022. Available online: https://dgtlinfra.com/cell-tower-range-how-far-reach/ (accessed on 1 January 2023).
- Wyrzykowski, R. Mobile Connectivity in Sub-Saharan Africa: 4G and 3G Connections Overtake 2G for the First Time; GSMA: London, UK, 2020; Volume 16. [Google Scholar]







| Comparison | D2D & D2BS | Lightweight | PUF | Blockchain | Sec. Analys. | Impl. |
|---|---|---|---|---|---|---|
| Gope et al. ([14]) | ✔ | ✔ | ✔ | ✔ | ||
| Alladi et al. ([15]) | ✔ | ✔ | ✔ | ✔ | ✔ | |
| Tan et al. ([17]) | ✔ | ✔ | ✔ | ✔ | ||
| Bera et al. [16] | ✔ | ✔ | ✔ | ✔ | ||
| Our scheme | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Operation | Raspberry | ESP32 | PC |
|---|---|---|---|
| AES-GCM | 0.0000016 | 0.00155 | 0.0000033 |
| HMAC | 0.0000059 | 0.0082 | 0.0000011 |
| EC scalar mult. | 0.0205 | 0.2945 | 0.002880 |
| Device\Number of Operation | Key Generation | HMAC | EC Multiplication |
|---|---|---|---|
| New Drone | 1 | 3 + i | 3 + i |
| Base station | - | 4 + i | 2 |
| Registered drones | - | 3 | 2 |
| Features | Gope [14] | Alladi [15] | Berra [16] | Our Scheme |
|---|---|---|---|---|
| Hash | 13 | 6 | 12 | 8 |
| PUF | 2 | 2 | - | 1 |
| EC multiplication | - | - | 10 | 4 |
| EC addition | - | - | 3 | - |
| Interactions | 5 | 3 | 8 | 4 |
| Storage cost at the UAV | 96 bytes | 44 bytes | 152 bytes | 18 bytes |
| Communication cost | 224 bytes | 200 bytes | 280 bytes | 384 bytes (180 bytes) |
| Name | Description | Size |
|---|---|---|
| Source Device Address | The device which transmits the packet. | 1 byte |
| Destination Device Address | The device which receives the packet | 1 byte |
| Number of Packets | The number of packets the total message is made of. | 1 byte |
| Packet Number | The number of the packet, among the packets. | 1 byte |
| Payload Size | The number of bytes the packet’s payload is made of. | 1 byte |
| Header CRC | 16-bit cyclic redundancy check for error-checking purposes. | 2 bytes |
| Name | Description | Size |
|---|---|---|
| Payload | The data of the packet | Max. 246 bytes |
| Payload CRC | 16 bit cyclic redundancy check for payload | 2 bytes |
| Name | Description | Size |
|---|---|---|
| Address | The registered device’s address | 1 byte |
| Device Status | Describes the device status | 1 byte |
| AES key | Symmetric AES key | 16 bytes |
| Received Initialization Vectors | Storing IVs to prevent replay attacks. Expiration time is required when working with low-resource devices, the exact value is platform and mission specific. | Not Specified |
| Standpoint | LoRa | Bluetooth | BLE 5 Long Range | Wi-Fi (2.4 GHz) | Cellular (4G) |
|---|---|---|---|---|---|
| Range | 5–10 km | 50–100 m | 400–1000 m | 45–75 m | 600–40,000 m |
| Affordability | EUR 7–EUR 8 per module | built-in or EUR 5–EUR 20 per module | built-in or EUR 5–EUR 20 per module | built-in or EUR 3–EUR 50 per module | EUR 20–EUR 50 per module + service provider fees |
| Maximum Possible Data Rate | 22 kbps | 2 Mbps | 2 Mbps | 72–600 Mbps (802.11n) | 4–12 Mbps are common |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oláh, N.; Molnár, B.; Huszti, A. Secure Registration Protocol for the Internet of Drones Using Blockchain and Physical Unclonable Function Technology. Symmetry 2023, 15, 1886. https://doi.org/10.3390/sym15101886
Oláh N, Molnár B, Huszti A. Secure Registration Protocol for the Internet of Drones Using Blockchain and Physical Unclonable Function Technology. Symmetry. 2023; 15(10):1886. https://doi.org/10.3390/sym15101886
Chicago/Turabian StyleOláh, Norbert, Botond Molnár, and Andrea Huszti. 2023. "Secure Registration Protocol for the Internet of Drones Using Blockchain and Physical Unclonable Function Technology" Symmetry 15, no. 10: 1886. https://doi.org/10.3390/sym15101886





