Performance Evaluation of Data Utility for a Differential Privacy Scheme Supporting Fault Tolerance
Abstract
:1. Introduction
- (1)
- The decryption aggregation value cannot be realized due to the lack of part of the key of the faulty meter.
- (2)
- The sum of differential noise added by non-faulty meters cannot meet the requirements of DP, which increases the probability of a DP attack.
- (1)
- We further supplement the previous work by improving the prediction method.
- (2)
- We form a more perfect privacy protection model (DPP-UFT) with fault tolerance based on the previous work (Zhang et al. [2]).
- (3)
- We compare the performance evaluation of our scheme and several other related literature in terms of the impact of faulty meters and differential noise on data utilization.
2. The Scheme DPP-UFT
2.1. System Model
2.2. Security Requirements
2.3. Attack Scenario
- (1)
- External attack: An external attacker may obtain personal information by intercepting communications in the model to infer the personal data of the target user.
- (2)
- Internal attack: It is assumed that the information flow in this model is reliable and untampered. The internal attacker is a participant in the system model. It may be SMs, aggregators, or CCs. It is assumed that they are semi-trusted, that is, execute strictly the protocol, including sending and transmitting data, which are authentic and reliable without malicious tampering [20,21,22]. However, they are curious about the individual fine-grained power consumption. The following attack is possible:
- CC may attack the target user based on the information sent by the SMs to GW or the union of up to N−2 m.
- CC may infer the data of the target user based on the encrypted aggregate value sent to it by GW.
- GW may try to obtain the user information of the target user through decryption or other available information flow according to the encrypted message sent by the user.
- The internal meter node may combine with other nodes to infer the data of the target node by stealing the information flow between the nodes.
- (3)
- Differential attack: The attacker can obtain the data of the target user by interpolating the aggregated values of his presence and absence by attacking the servers in CC. Differential privacy protection must meet two conditions at the same time: protect individual privacy from disclosure and reduce noise error deviation, so as to improve the utility of aggregated value [23].
2.4. The DPP-UFT Scheme
2.4.1. Grouping and Key Initialization
- (1)
- Smart Metering
- (2)
- Grouping
| Algorithm 1: Similar consumption-based grouping |
| Input: A real array C = [c1, c2, …, cN] representing the set of power consumption of N users in the NAN region, a character array U = [u1, u2, …, uN] representing the set of N users, a character empty array G is defined, and an integer constant p, n defined. n is the number of groups, and p is the number of SMs in the group. |
| Output: G |
| 1. U’ = Sort (U with C) |
| 2. n = N/p |
| 3. for (i = 0; i < n; i++){ |
| 4. for (j = 1; j < = p; j++){ |
| 5. G[i + 1]+ = U’[i×p + j]; |
| 6. } |
| 7. } |
| 8. if N%p! = 0{ |
| 9. for (i = n×p + 1; i < = N; i++){ |
| 10. G[n + 1]+ = U’[i] |
| 11. } |
| 12. } |
- (3)
- Key Generation
- For each user , TA first chooses a random number as ‘s key and sends it to securely.
- TA computes so that
- TA securely sends to CC as the private key of CC (assuming that there is a secure communication method to pass the key).
2.4.2. The Encryption and Aggregation of Supporting Fault-Tolerance
2.4.3. Differential Privacy with a Pre-Estimated Failure Rate
2.4.4. Encryption of the Power Consumption
2.4.5. Aggregation and Decryption with Fault-Tolerance
- (1)
- CC will send faulty users to TA. Once it has not received reports from the faulty meter , TA will calculate the keys’ sum of the faulty nodes and send them to CC, where
- (2)
- GW computes and sends it to CC according to Equation (8), where
- (3)
- According to Equation (9), CC computes the aggregated value with noise added by secret key S0 as follows:
2.4.6. Correctness Analysis
2.5. Security Analysis
- (1)
- External attacks. The external attacker A overhears the data sent by individual users to the GW in the form of . According to the semantic security property of the Paillier cipher against plaintext attacks, any attacker A cannot decrypt the data without the individual meter key owned by TA and the individual meter. Therefore, the encrypted aggregate value can be decrypted by the sum of keys to obtain the sum of noisy data from these nodes rather than the individual data .
- (2)
- Internal attacks. The data sent by SM to GW resists all semi-trusted internal attackers due to the key owned by TA and SM.CC can send the fault information of one or some users to TA; however, it can only get the hash function of the key sum of all faulty meters from TA, where or cannot be obtained. CC and the user have different key authorities, is kept secret by CC, and the private key Si of the faulty meter is known only to TA and SM itself.
- (3)
- Fault-tolerant reliability. The scheme solves the problems of cryptographic and differential fault tolerance. When fails, CC can still report to TA and receive and obtain the correct noise-added aggregation value of non-faulty users. Then, the distributed differential noise is set by predicting the failure rate so that the non-faulty nodes meet the requirements of overall differential privacy through the added differential noise.
- (4)
- Differential Privacy. This scheme considers the sum of distributed differential noise in the case of the pre-estimated failure rate as . This method of adding distributed differential noise to the prior value of the previous failure rate ensures the overall differential privacy requirements and reduces the additional differential noise.
3. Utility Analysis and Performance Evaluation
3.1. Storage Overhead Comparison
- (1)
- GW needs to set up a buffer to store standby passwords. Assuming that the number of meter users is 220, the modulo value in the modulo addition operation is, that is, the width of the random number in the future password is 64 bits, and the meter reading takes up 64 bits, so the total width of a future password is 128 bits. The value of B is set to the aggregated value for one month, and the number of cycles is 2880 (taking 15 min as an example). Without calculating the width of the added differential noise, the total storage capacity is approximately 45 GB. The storage cost will also increase with an increase in the number of meters or cycles.
- (2)
- If the number of time points in B is too low, the meter cannot be repaired for a long time. The fault-tolerant scheme is meaningless. If the number of time points in B is too high, the memory occupancy rate and processing time of the gateway will be seriously challenged, which will bring a higher delay to the whole system.
- (3)
- All meters within each GW send B alternate passwords simultaneously, and the communication bandwidth is also greatly affected because each user node sends (1 + B) encrypted data simultaneously, including one current encrypted data and B alternate encrypted data, the latter including .
3.2. Computation Overhead Analysis
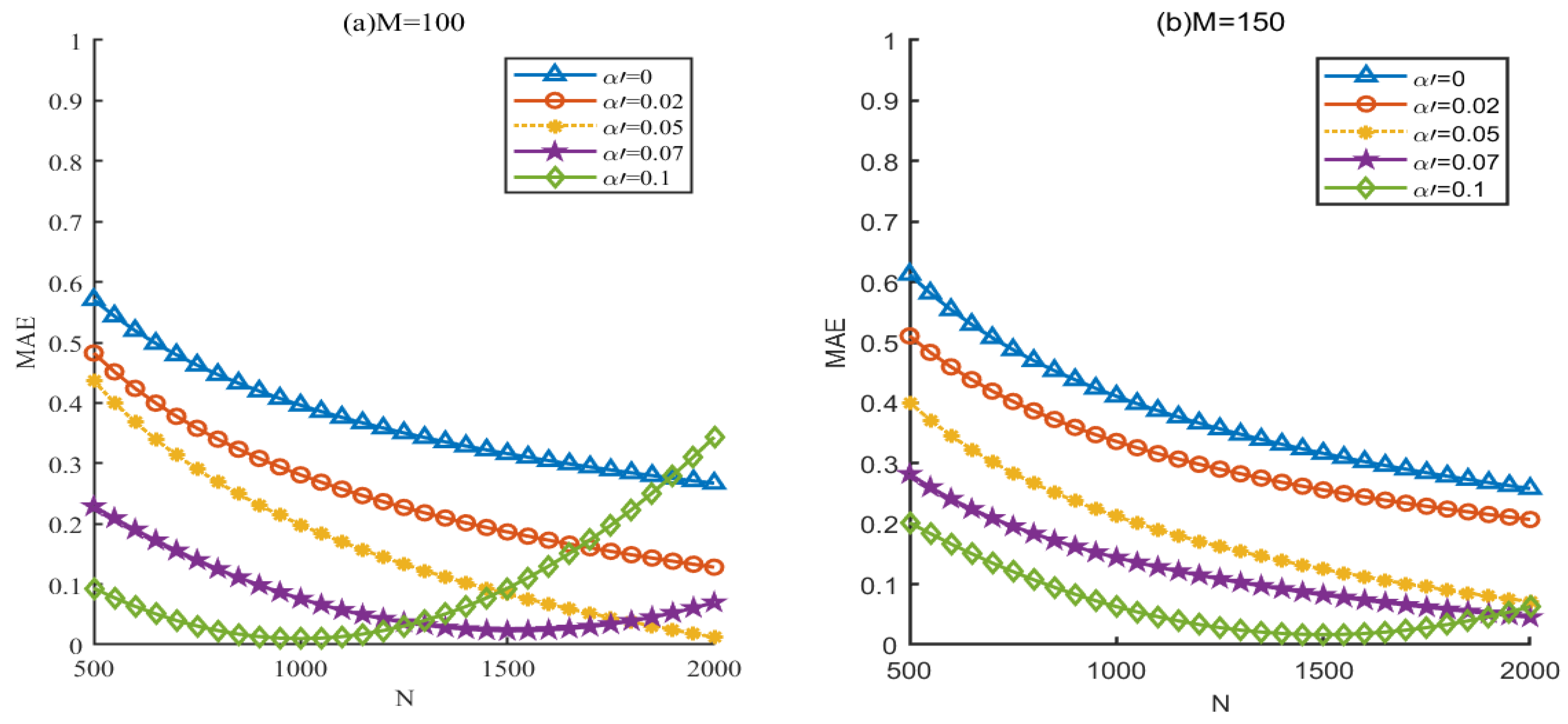
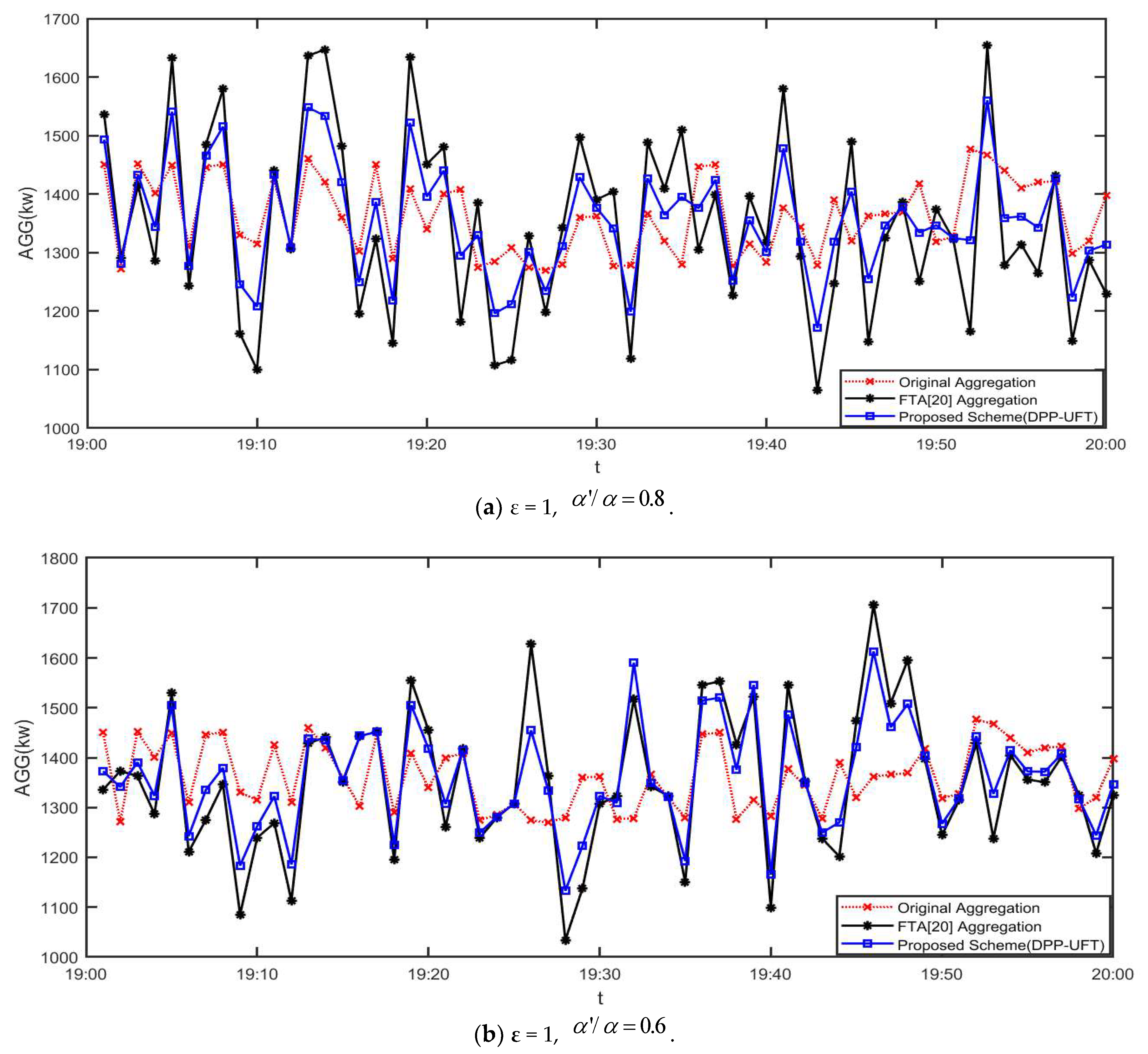
3.3. Aggregated Data Utility
- (1)
- Similar Consumption-based Grouping
- (2)
- Distributed Differential Noise with a Pre-estimated Failure Rate
- (3)
- Utility Comparison
4. Conclusions
- (1)
- The differential privacy is inversely proportional to ε when the highest sensitivity GSf in the group is equal, which satisfies Equation (2).
- (2)
- In the DPP-UFT scheme, the noise value will increase slightly with the decrease in , which satisfies Equations (7) and (14).
- (3)
- The performance evaluation further verifies the effectiveness of the method of adding differential noise based on faulty meters adopted in this scheme for noise reduction.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- National Institute of Standards and Technology. NIST Framework and Roadmap for Smart Grid Interoperability Standards, All Release. 2010. Available online: https://csrc.nist.gov/CSRC/media/Presentations/NIST-and-the-Smart-Grid-Presentation/images-media/nist-and-smart-grid_ALee.pdf (accessed on 19 January 2010).
- Zhang, L.; Zhang, J. Differential privacy protection scheme supporting high data utility and fault tolerance. J. Zhejiang Univ. (Eng. Sci.) 2019, 53, 1496. [Google Scholar] [CrossRef]
- Peng, C.; Sun, H.; Yang, M.; Wang, Y.L. A survey on security communication and control for smart grids under malicious cyber attacks. IEEE Trans. Syst. Man. Cybern. Syst. 2019, 49, 1554–1569. [Google Scholar] [CrossRef]
- Liu, H.; Gu, T.; Liu, Y.; Song, J.; Zeng, Z. Fault-tolerant privacy-preserving data aggregation for smart grid. Wirel. Commun. Mob. Comput. 2020, 2020, 457–459. [Google Scholar] [CrossRef]
- Zia, M.T.; Khan, M.A.; El-Sayed, H. Application of Differential Privacy Approach in Healthcare Data–A Case Study. In Proceedings of the 14th International Conference on Innovations in Information Technology (IIT), Al Ain, United Arab Emirates, 17–18 November 2020. [Google Scholar]
- Ni, J.; Zhang, K.; Alharbi, K.; Lin, X.; Zhang, N.; Shen, X.S. Differentially private smart metering with fault tolerance and range-based filtering. IEEE Trans. Smart Grid 2017, 8, 2483–2493. [Google Scholar] [CrossRef]
- Jia, W.; Zhu, H.; Cao, Z.; Dong, X.; Xiao, C. Human-Factor-Aware Privacy-Preserving Aggregation in Smart Grid. IEEE Syst. J. 2017, 8, 598–607. [Google Scholar] [CrossRef]
- Oksuz, O. Providing Anonymous Communication, Privacy-Preserving Data Aggregation and Dynamic Billing System in Smart Grid Using Permissioned Blockchain. Int. J. Netw. Secur. Its Appl. 2020, 12, 17–36. [Google Scholar] [CrossRef]
- Narayanan, A.; Shmatikov, V. Myths and fallacies of Personally Identifiable Information. Commun. ACM 2015, 53, 24–26. [Google Scholar] [CrossRef]
- Cao, H.; Liu, S.; Guan, Z.; Wu, L.; Wang, T. Achieving Differential Privacy of Data Disclosure from Non-intrusive Load Monitoring in Smart Grid. In Proceedings of the International Symposium on Cyberspace Safety and Security (CSS 2017), Xi’an, China, 22–23 October 2017. [Google Scholar]
- Ford, V.; Siraj, A.; Rahman, M.A. Secure and efficient protection of consumer privacy in advanced metering infrastructure supporting fine-grained data analysis. J. Comput. Syst. Sci. 2017, 83, 84–100. [Google Scholar] [CrossRef]
- Gong, Y.; Ying, C.; Guo, Y.; Fang, Y. A privacy-preserving scheme for incentive-based demand response in the smart grid. IEEE Trans. Smart Grid 2017, 7, 1304–1313. [Google Scholar] [CrossRef]
- Dimitriou, T.; Karame, G.O. Enabling anonymous authorization and rewarding in the smart grid. IEEE Trans. Dependable Secur. Comput. 2017, 14, 565–572. [Google Scholar] [CrossRef]
- Ambrosin, M.; Hossini, H.; Mandal, K.; Conti, M.; Poovendran, R. Despicable meter: Anonymous and fine-grained metering data reporting with dishonest meters. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (IEEE CNS 2016), Philadelphia, PA, USA, 17–19 October 2016. [Google Scholar]
- Dwork, C.; Mcsherry, F.; Nissim, K.; Smith, A. Calibrating noise to sensitivity in private data analysis. In Proceedings of the VLDB Endowment, New York, NY, USA, 11–12 August 2006. [Google Scholar]
- Bao, H.; Li, B. A novel privacy preserving data aggregation scheme with data integrity and fault tolerance for smart grid communications. Front. Comput. Sci. China 2021, 15, 155812. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X.; Zhang, H.; Lin, H.; Tode, H.; Pan, M.; Han, Z. Data-Driven Optimization for Utility Providers with Differential Privacy of Users Energy Profile. In Proceedings of the Conference of IEEE Global Communications, Waikoloa Village, HI, USA, 9–13 December 2019. [Google Scholar]
- Barbosa, P.; Brito, A.; Almeida, H. A technique to provide differential privacy for appliance usage in smart metering. Inf. Sci. 2016, 370–371, 355–367. [Google Scholar] [CrossRef]
- Gai, N.; Xue, K.; Zhu, B.; Yang, J.; Liu, J.; He, D. An efficient data aggregation scheme with local differential privacy in smart grid. Digit. Commun. Netw. 2022, 8, 333–342. [Google Scholar] [CrossRef]
- Won, J.; Ma, C.; Yau, D.; Rao, N. Proactive fault-tolerant aggregation protocol for privacy-assured smart metering. In Proceedings of the IEEE Conference on Computer Communications, Toronto, ON, Canada, 2–4 April 2014. [Google Scholar]
- Shi, Z.; Sun, R.; Lu, R.; Chen, L.; Chen, J.; Sherman Shen, X. Diverse grouping-based m aggregation protocol with error detection for smart grid communications. IEEE Trans. Smart Grid 2015, 6, 2856–2868. [Google Scholar] [CrossRef]
- Erkin, Z.; Tsudik, G. Private computation of spatial and temporal powerconsumption with. smart meters. In Proceedings of the 2013 International Conference of Applied CryptographyNetwork Security, Banff, AL, Canada, 25–28 June 2013. [Google Scholar]
- Chim, T.W.; Yiu, S.; Li, V.O.; Hui, L.C.; Zhong, J. Prga: Privacy-preserving recording & gateway-assisted authentication of power usage information for smart grid. IEEE Trans. Dependable Secur. 2015, 12, 85–97. [Google Scholar] [CrossRef]
- Shamus.com. Multiprecision Integer and Rational Arithmetic c/c++ Library. 2017. Available online: http://www.shamus.ie/ (accessed on 20 January 2017).
- Siano, P.; Cecati, C.; Yu, H.; Kolbusz, J. Real time operation of smart grids via fcn networks and optimal power flow. IEEE Trans. Ind. Inform. 2012, 8, 944–952. [Google Scholar] [CrossRef]
- Office for National Statistics. Families and Household, 2001 to 2011. 2017. Available online: https://www.nationalarchives.gov.uk/webarchive/ (accessed on 20 January 2017).
- Bao, H.; Lu, R. A new differentially private data aggregation with fault tolerance for smart grid communications. IEEE Internet Things J. 2015, 2, 248–258. [Google Scholar] [CrossRef]
- Hui, C.; Liu, S.; Wu, L.; Guan, Z.; Du, X. Achieving differential privacy against non-intrusive load monitoring in smart grid: A fog computing approach. Concurr. Comp. Pract. Exp. 2018, 31, e4528. [Google Scholar] [CrossRef]


| Scheme | DP | RN | RMSE | U | Data/State Privacy | Encryption Method | Encryption Overhead | FT |
|---|---|---|---|---|---|---|---|---|
| PPADF [16] | ✖ | ✖ | — | ✖ | Data | Pre-computed auxiliary information | O(N) | ✔ |
| FTA [20] | ✔ | ✔ | ✔ | Data | Modular addition | O(N×K×B) | ✔ | |
| DPA-FT [27] † | ✔ | ✖ | O(1) † | ✖ | Data | Diffie–Hellman | O(N) | ✔ |
| DP-NILM [28] | ✔ | ✖ | — | ✖ | State | Markov, Laplace noise | O(N×A) | ✖ |
| DPP-UFT [ours] | ✔ | ✔ | O(1) | ✔ | Data | Paillier | O(N) | ✔ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, L.; Wang, M.; Xiu, J. Performance Evaluation of Data Utility for a Differential Privacy Scheme Supporting Fault Tolerance. Symmetry 2023, 15, 1962. https://doi.org/10.3390/sym15101962
Zhang L, Wang M, Xiu J. Performance Evaluation of Data Utility for a Differential Privacy Scheme Supporting Fault Tolerance. Symmetry. 2023; 15(10):1962. https://doi.org/10.3390/sym15101962
Chicago/Turabian StyleZhang, Lei, Mingxiang Wang, and Jianxin Xiu. 2023. "Performance Evaluation of Data Utility for a Differential Privacy Scheme Supporting Fault Tolerance" Symmetry 15, no. 10: 1962. https://doi.org/10.3390/sym15101962
APA StyleZhang, L., Wang, M., & Xiu, J. (2023). Performance Evaluation of Data Utility for a Differential Privacy Scheme Supporting Fault Tolerance. Symmetry, 15(10), 1962. https://doi.org/10.3390/sym15101962






