A Cancelable Biometric System Based on Deep Style Transfer and Symmetry Check for Double-Phase User Authentication
Abstract
:1. Introduction
1.1. Background Study
1.2. Motivation, Contribution, and Organization of This Paper
- (1)
- To utilize convolutional neural networks (CNNs) for extracting facial image features.
- (2)
- To utilize convolutional neural networks (CNNs) for extracting unique features from fingerprint images.
- (3)
- To train a model capable of transferring features from fingerprint images to face images.
- (4)
- To investigate a deep learning architecture that focuses on generating an encrypted template based on the obtained feature map.
- (5)
- To explore a loss function for the proposed system that produces an optimal template.
- (6)
- To employ hashing algorithms for generating a textual representation of the cancelable template.
2. Related Work
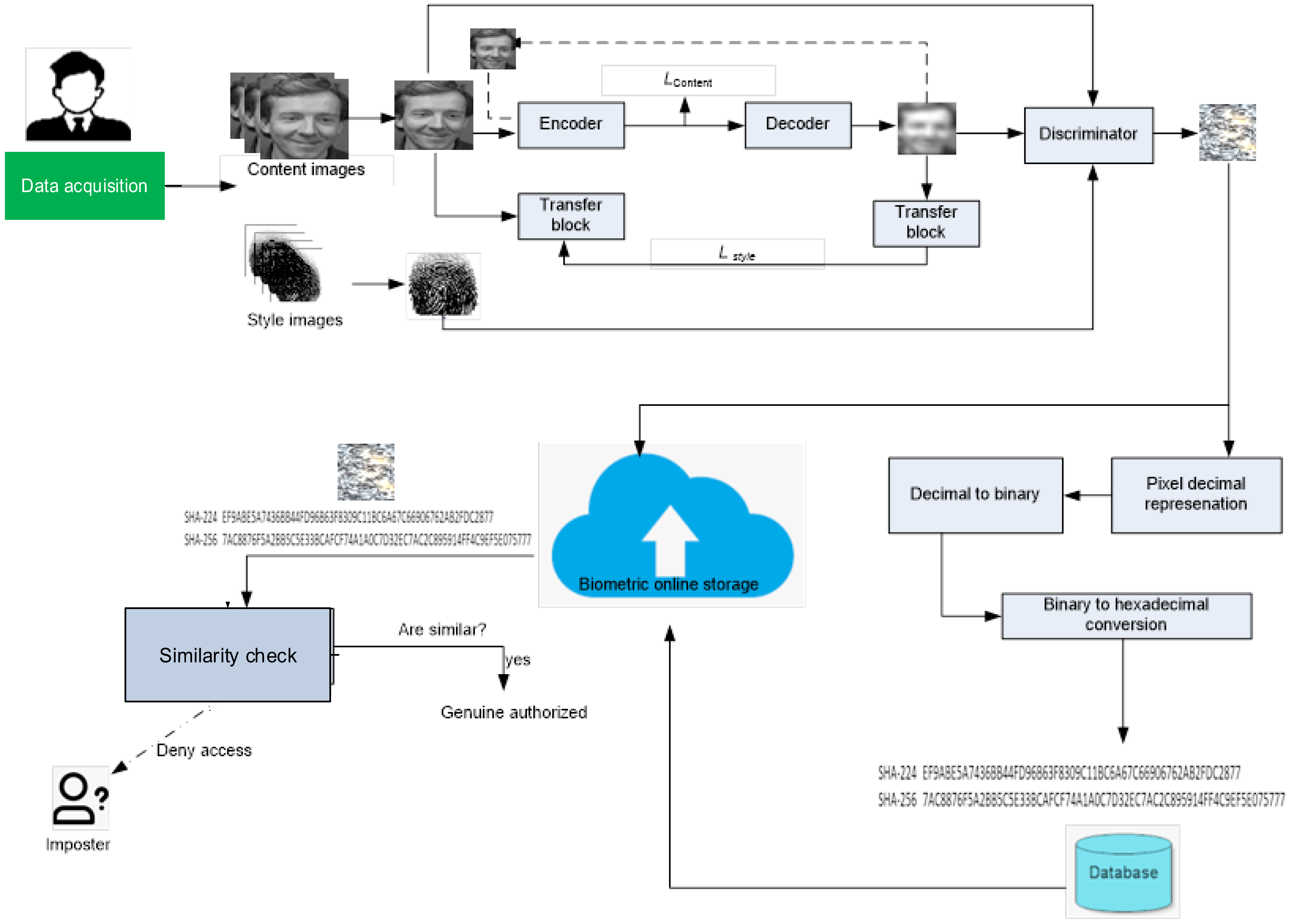
3. Proposed Approach
3.1. Content Image Representation
3.2. Style Image Representation
4. Simulation Results
4.1. Evaluation Metrics
4.1.1. Quantitative Analysis
4.1.2. Qualitative Analysis
Spectral Distortion
- Universal image quality index
4.2. Results of Visual Cancelable Templates
4.3. Results of Bio-Hash Templates
5. More Analysis and Discussion
5.1. Robustness Justification
5.2. Time Complexity and Execution Time
- 1-
- (O(1)) operations to register current biometrics of the user.
- 2-
- (O(n × (M × N)) operations to perform feature extraction on an M × N image, where n is an integer.
- 3-
- (O(2 × n × (M × N))) operations to fuse the features.
- 4-
- (O(M × N)) operations to reconstruct the fused image.
- 5-
- (O(5 × n × M × N)) operations to perform the deep dream (where 5 is the number of steps).
- 6-
- (O(n × (M × N))) operations to perform the authentication process to accept or reject the user.
5.3. Discussion and Comparisons
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Choudhury, B.; Then, P.; Issac, B.; Raman, V.; Haldar, M.K. A Survey on Biometrics and Cancelable Biometrics Systems. Int. J. Image Graph. 2018, 18, 1850006. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.K.; Xie, L.; Zhang, J. Chaos and NDFT-Based Spread Spectrum Concealing of Fingerprint-Biometric Data into Audio Signals. Digit. Signal Process. 2010, 20, 179–190. [Google Scholar] [CrossRef]
- Kaur, H.; Khanna, P. Cancelable Features Using Log-Gabor Filters for Biometric Authentication. Multimed. Tools Appl. 2017, 76, 4673–4694. [Google Scholar] [CrossRef]
- Nandakumar, K.; Jain, A.K. Biometric Template Protection: Bridging the Performance Gap between Theory and Practice. IEEE Signal Process. Mag. 2015, 32, 88–100. [Google Scholar] [CrossRef] [Green Version]
- Rane, S. Standardization of Biometric Template Protection. IEEE Multimed. 2014, 21, 94–99. [Google Scholar] [CrossRef]
- Maiorana, E.; Campisi, P.; Neri, A. Bioconvolving: Cancelable Templates for a Multi-Biometrics Signature Recognition System. In Proceedings of the 2011 IEEE International Systems Conference, Montreal, QC, Canada, 4–7 April 2011; IEEE: New York, NY, USA; pp. 495–500. [Google Scholar]
- Jin, Z.; Teoh, A.B.J.; Goi, B.-M.; Tay, Y.-H. Biometric Cryptosystems: A New Biometric Key Binding and Its Implementation for Fingerprint Minutiae-Based Representation. Pattern Recognit. 2016, 56, 50–62. [Google Scholar] [CrossRef]
- Kumar, P.; Joseph, J.; Singh, K. Optical Image Encryption Using a Jigsaw Transform for Silhouette Removal in Interference-Based Methods and Decryption with a Single Spatial Light Modulator. Appl. Opt. 2011, 50, 1805–1811. [Google Scholar] [CrossRef] [PubMed]
- Sedik, A.; El-Latif, A.A.A.; Wani, M.A.; El-Samie, F.E.A.; Bauomy, N.A.-S.; Hashad, F.G. Efficient Multi-Biometric Secure-Storage Scheme Based on Deep Learning and Crypto-Mapping Techniques. Mathematics 2023, 11, 703. [Google Scholar] [CrossRef]
- Elazm, L.A.A.; El-Shafai, W.; Ibrahim, S.; Egila, M.G.; Shawkey, H.; Elsaid, M.K.H.; Soliman, N.F.; AlEisa, H.N.; El-Samie, F.E.A. Efficient Hardware Design of a Secure Cancellable Biometric Cryptosystem. Intell. Autom. Soft Comput. 2023, 36, 929–955. [Google Scholar] [CrossRef]
- El-Shafai, W.; Elsayed, M.; Rashwan, M.; Dessouky, M.; El-Fishawy, A.; Soliman, N.F.; Alhussan, A.A.; Abd El-Samie, F.E. Optical Ciphering Scheme for Cancellable Speaker Identification System. Comput. Syst. Sci. Eng. 2023, 45, 563–578. [Google Scholar] [CrossRef]
- Salama, G.M.; El-Gazar, S.; Omar, B.; Nassar, R.M.; Khalaf, A.A.M.; El-Banby, G.M.; Hamed, H.F.A.; El-Shafai, W.; Abd El-Samie, F.E. Cancelable Biometric System for IoT Applications Based on Optical Double Random Phase Encoding. Opt. Express 2022, 30, 37816–37832. [Google Scholar] [CrossRef] [PubMed]
- Faragallah, O.S.; Naeem, E.A.; El-Shafai, W.; Ramadan, N.; Ahmed, H.E.H.; Elnaby, M.M.A.; Elashry, I.; El-khamy, S.E.; El-Samie, F.E.A. Efficient Chaotic-Baker-Map-Based Cancelable Face Recognition. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 1837–1875. [Google Scholar] [CrossRef]
- Takahashi, K.; Hitachi, S.H. Generating Provably Secure Cancelable Fingerprint Templates Based on Correlation-Invariant Random Filtering. In Proceedings of the 2009 IEEE 3rd International Conference on Biometrics: Theory, Applications, and Systems, Washington, DC, USA, 28–30 September 2009; IEEE: New York, NY, USA, 2009; pp. 1–6. [Google Scholar]
- Sandhya, M.; Prasad, M.V.N.K. Cancelable Fingerprint Cryptosystem Using Multiple Spiral Curves and Fuzzy Commitment Scheme. Int. J. Pattern Recognit. Artif. Intell. 2017, 31, 1756004. [Google Scholar] [CrossRef]
- Qiu, J.; Li, H.; Dong, J. Design of Cancelable Palmprint Templates Based on Look up Table. IOP Conf. Ser. Mater. Sci. Eng. 2018, 322, 52050. [Google Scholar] [CrossRef]
- Ali, M.A.M.; Tahir, N.M. Cancelable Biometrics Technique for Iris Recognition. In Proceedings of the 2018 IEEE Symposium on Computer Applications & Industrial Electronics (ISCAIE), Penang, Malaysia, 28–29 April 2018; IEEE: New York, NY, USA, 2018; pp. 434–437. [Google Scholar]
- Soliman, R.F.; Amin, M.; Abd El-Samie, F.E. A Modified Cancelable Biometrics Scheme Using Random Projection. Ann. Data Sci. 2019, 6, 223–236. [Google Scholar] [CrossRef]
- Soliman, R.F.; Ramadan, N.; Amin, M.; Ahmed, H.H.; El-Khamy, S.; Abd El-Samie, F.E. Efficient Cancelable Iris Recognition Scheme Based on Modified Logistic Map. Proc. Natl. Acad. Sci. India Sect. A Phys. Sci. 2020, 90, 101–107. [Google Scholar] [CrossRef]
- Soliman, R.F.; Amin, M.; Abd El-Samie, F.E. A Double Random Phase Encoding Approach for Cancelable Iris Recognition. Opt. Quantum Electron. 2018, 50, 326. [Google Scholar] [CrossRef]
- Gowthami, A.T.; Mamatha, H.R. Fingerprint Recognition Using Zone Based Linear Binary Patterns. Procedia Comput. Sci. 2015, 58, 552–557. [Google Scholar] [CrossRef] [Green Version]
- Butt, M.; Damer, N. Helper Data Scheme for 2D Cancelable Face Recognition Using Bloom Filters. In Proceedings of the IWSSIP 2014 Proceedings, Dubrovnik, Croatia, 12–15 May 2014; IEEE: New York, NY, USA, 2014; pp. 271–274. [Google Scholar]
- Teoh, A.B.J.; Kuan, Y.W.; Lee, S. Cancellable Biometrics and Annotations on Biohash. Pattern Recognit. 2008, 41, 2034–2044. [Google Scholar] [CrossRef]
- Kho, J.B.; Kim, J.; Kim, I.-J.; Teoh, A.B.J. Cancelable Fingerprint Template Design with Randomized Non-Negative Least Squares. Pattern Recognit. 2019, 91, 245–260. [Google Scholar] [CrossRef]
- Simonyan, K.; Zisserman, A. Very Deep Convolutional Networks for Large-Scale Image Recognition. arXiv 1409, arXiv:1409.1556. [Google Scholar]
- Jia, Y.; Shelhamer, E.; Donahue, J.; Karayev, S.; Long, J.; Girshick, R.; Guadarrama, S.; Darrell, T. Caffe: Convolutional Architecture for Fast Feature Embedding. In Proceedings of the 22nd ACM International Conference on Multimedia, Orlando FL, USA, 3–7 November 2014; pp. 675–678. [Google Scholar]
- Zhu, C.; Byrd, R.H.; Lu, P.; Nocedal, J. Algorithm 778: L-BFGS-B: Fortran Subroutines for Large-Scale Bound-Constrained Optimization. ACM Trans. Math. Softw. 1997, 23, 550–560. [Google Scholar] [CrossRef]
- Elshazly, E.A.; Hashad, F.G.; Sedik, A.; Abd El-Samie, F.E.; Abdel-Salam, N. Compression-Based Cancelable Multi-Biometric System. Res. Sq. 2022; in press. [Google Scholar] [CrossRef]
- Tarif, E.B.; Wibowo, S.; Wasimi, S.; Tareef, A. A Hybrid Encryption/Hiding Method for Secure Transmission of Biometric Data in Multimodal Authentication System. Multimed. Tools Appl. 2018, 77, 2485–2503. [Google Scholar] [CrossRef]
- Benrhouma, O.; Hermassi, H.; Abd El-Latif, A.A.; Belghith, S. Chaotic Watermark for Blind Forgery Detection in Images. Multimed. Tools Appl. 2016, 75, 8695–8718. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical Image Encryption Based on Input Plane and Fourier Plane Random Encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef]
- Lai, Y.-L.; Jin, Z.; Teoh, A.B.J.; Goi, B.-M.; Yap, W.-S.; Chai, T.-Y.; Rathgeb, C. Cancellable Iris Template Generation Based on Indexing-First-One Hashing. Pattern Recognit. 2017, 64, 105–117. [Google Scholar] [CrossRef]
- Tarek, M.; Ouda, O.; Hamza, T. Pre-Image Resistant Cancelable Biometrics Scheme Using Bidirectional Memory Model. Int. J. Netw. Secur. 2017, 19, 498–506. [Google Scholar]
- Wu, J.; Zhu, Z.; Guo, S. A Quality Model for Evaluating Encryption-as-a-Service. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Guangzhou, China, 12–15 December 2017; Springer: Cham, Switzerland, 2017; pp. 557–569. [Google Scholar]
- Algarni, A.D.; El Banby, G.M.; Soliman, N.F.; El-Samie, F.E.A.; Iliyasu, A.M. Efficient Implementation of Homomorphic and Fuzzy Transforms in Random-Projection Encryption Frameworks for Cancellable Face Recognition. Electronics 2020, 9, 1046. [Google Scholar] [CrossRef]
- Sinha, A.; Singh, K. Image Encryption by Using Fractional Fourier Transform and Jigsaw Transform in Image Bit Planes. Opt. Eng. 2005, 44, 57001. [Google Scholar] [CrossRef]
- Sree, S.R.S.; Radha, N. Cancellable Multimodal Biometric User Authentication System with Fuzzy Vault. In Proceedings of the 2016 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 7–9 January 2016; IEEE: New York, NY, USA, 2016; pp. 1–6. [Google Scholar]
- Dang, T.K.; Truong, Q.C.; Le, T.T.B.; Truong, H. Cancellable Fuzzy Vault with Periodic Transformation for Biometric Template Protection. IET Biom. 2016, 5, 229–235. [Google Scholar] [CrossRef] [Green Version]












| Image | NCRP (%) | PSNR (dB) | SSIM | UIQ | SD | UACI |
|---|---|---|---|---|---|---|
| 1 | 98.76 | 21.95 | 0.042 | 0.78 | 75.21 | 30.14 |
| 2 | 98.72 | 24.05 | 0.034 | 0.74 | 56.55 | 22.78 |
| 3 | 98.12 | 22.57 | 0.05 | 0.72 | 57.84 | 24.43 |
| 4 | 98.19 | 22.45 | 0.04 | 0.77 | 58.89 | 25.29 |
| 5 | 98.28 | 23.83 | 0.034 | 0.73 | 57.24 | 26.33 |
| 6 | 98.98 | 22.88 | 0.032 | 0.71 | 59.06 | 26.54 |
| 7 | 99.25 | 22.35 | 0.039 | 0.75 | 56.92 | 24.96 |
| 8 | 98.31 | 21.61 | 0.057 | 0.79 | 57.49 | 23. 19 |
| 9 | 99.28 | 23.71 | 0.031 | 0.79 | 60. 39 | 24.46 |
| 10 | 98.67 | 21.35 | 0.051 | 0.76 | 75.95 | 28.74 |
| 11 | 98.47 | 22.53 | 0.036 | 0.74 | 57.39 | 22.78 |
| 12 | 98.12 | 23.73 | 0.06 | 0.72 | 56.84 | 23.33 |
| 13 | 99. 29 | 21.58 | 0.033 | 0.77 | 60.99 | 26.81 |
| 14 | 98.23 | 24.23 | 0.04 | 0.70 | 60.28 | 27.03 |
| 15 | 98.78 | 24.08 | 0.038 | 0.71 | 58.0688 | 26.54 |
| 16 | 98.71 | 22.34 | 0.031 | 0.76 | 57.2120 | 23. 69 |
| 17 | 98.91 | 22.08 | 0.059 | 0.78 | 56.4679 | 24. 12 |
| 18 | 99.07 | 24.28 | 0.0315 | 0.72 | 61.7939 | 26.86 |
| Method | Total |
|---|---|
| IFL followed by Gaussian RP [35] | 13.14 |
| Homomorphic transform followed by Gaussian RP [35] | 12.19 |
| The proposed MBCS method | 16.52 |
| Method | EER | FAR | FRR | AROC |
|---|---|---|---|---|
| Proposed (Style Transfer) | 7.6842 × 10−13 | 2.1573 × 10−15 | 1.0295 × 10−11 | 0.9999 |
| Ref. [18] | 0.0058 | 0.0985 | 1.6822 × 10−4 | 0.8630 |
| Ref. [31] | 9.5647 × 10−5 | 0.0056 | 2.5216 × 10−3 | 0.8684 |
| Ref. [36] | 0.0046 | 2.3550 × 10−4 | 0.9292 | 0.8837 |
| Ref. [8] | 0.0178 | 0.0017 | 0.8769 | 0.8967 |
| Ref. [29] | 5.6942 × 10−10 | 3.0414 × 10−7 | 0.9671 | 0.9076 |
| Ref. [37] | 0.0016 | 0.1955 | 4.5354 × 10−4 | 0.8737 |
| Ref. [38] | 8.7546 × 10−9 | 0.0435 | 6.1101 × 10−3 | 0.7187 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sedik, A.; El-Latif, A.A.A.; El-Affendi, M.; Mostafa, H. A Cancelable Biometric System Based on Deep Style Transfer and Symmetry Check for Double-Phase User Authentication. Symmetry 2023, 15, 1426. https://doi.org/10.3390/sym15071426
Sedik A, El-Latif AAA, El-Affendi M, Mostafa H. A Cancelable Biometric System Based on Deep Style Transfer and Symmetry Check for Double-Phase User Authentication. Symmetry. 2023; 15(7):1426. https://doi.org/10.3390/sym15071426
Chicago/Turabian StyleSedik, Ahmed, Ahmed A. Abd El-Latif, Mohammed El-Affendi, and Hala Mostafa. 2023. "A Cancelable Biometric System Based on Deep Style Transfer and Symmetry Check for Double-Phase User Authentication" Symmetry 15, no. 7: 1426. https://doi.org/10.3390/sym15071426







