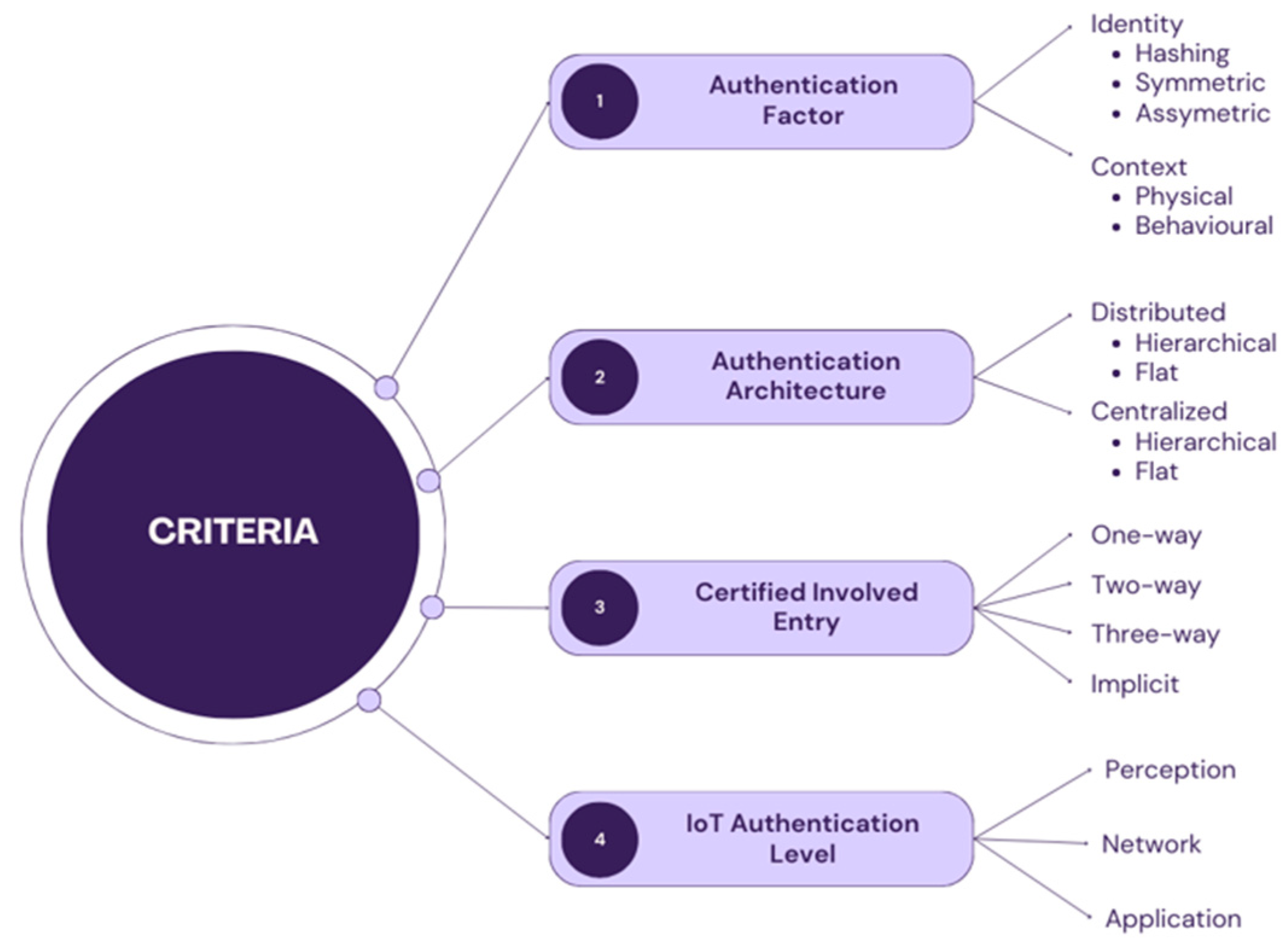
Within this section, the study addresses all Research Questions (RQs) through a comprehensive analysis of the results originating from the compilation of primary studies. The process involves a detailed review and synthesis of the findings, delivering a thorough response to each RQ in the study.
4.2. RQ2: In Which Domains Has Authentication in the IoT Been Extensively Applied?
To address this research question (RQ), an analysis was undertaken regarding three fundamental aspects of the primary studies. These included the publication year, type of publication channels, and the primary source that has disseminated the most relevant studies, encompassing journals and conference proceedings. The section meticulously dissects distinct domains and their affiliated research papers in IoT-based authentication by referring to
Figure 5 and
Table 5. It categorizes them into ten domains: Industrial, Healthcare, Cloud and Fog, Blockchain, Communication, Farming, Networks, RFID, Smart IoT, and Mobile. Each domain is accompanied by a specified number of research papers and the respective percentage representation, offering a comprehensive understanding of the research landscape.
Industrial: This sector, represented by research papers [
7,
9,
17,
27,
28,
29,
30,
31,
32,
33], accounts for 15% of the total. The central focus revolves around the crucial requirement for authorization frameworks in industrial settings to counter unauthorized access, strengthen data security, and guarantee the unwavering reliability and safety of critical industrial processes.
Healthcare: In the convergence of privacy and security within healthcare ecosystems, research papers [
12,
34,
35,
36,
37,
38,
39], make substantial contributions, comprising 11% of notable advancements in IoT-based authentication. The focus is on crafting resilient authentication mechanisms specifically tailored to the sensitive nature of healthcare information.
Cloud and Fog: In this domain, researchers [
10,
15,
40,
41,
42], collaboratively contribute 8%, highlighting the pivotal role of identity verification for securing access to both cloud services and fog computing nodes. The common objectives underscore the imperative for robust authentication mechanisms in these distributed environments.
Blockchain: This domain distinguishes itself with a significant 12% contribution, as evidenced by research papers [
6,
14,
43,
44,
45,
46,
47,
48,
49,
50,
51,
52] centering on secure authentication through decentralized identity, smart contracts, and cryptographic measures. The focus lies on fortifying security through innovative approaches.
Communication: Leading with the highest percentage at 25%, the research papers [
11,
14,
43,
44,
45,
46,
47,
48,
49,
50,
51,
52,
53,
54], in this domain delve into advancing secure communication protocols, sophisticated encryption techniques, and advanced authentication methods. The pronounced emphasis on secure communication underscores the domain’s significance.
Farming: Focusing on the enduring security and performance of IoT systems in agricultural contexts, research papers [
55,
56,
57] make a 3% contribution to IoT-based authentication technologies. The research underscores the importance of consistently monitoring device behaviour, network traffic, and data interactions in farming environments.
Networks: Comprising 12% of the total, research papers [
57,
58,
59,
60,
61,
62,
63,
64,
65] in this domain emphasize advanced protocols and encryption strategies to foster trusted connections. The primary focus is on fortifying network security to mitigate unauthorized access and potential data breaches.
RFID: In the realm of RFID, research papers [
65,
66,
67,
68] centre around the authentication and authorization of RFID devices, particularly in supply chain management, access control, and asset tracking. This domain contributes 6% to IoT-based authentication technologies, underscoring its significance in diverse applications.
Smart IoT: Spanning smart cities, smart homes, and intelligent applications, research papers [
65,
69,
70], contributing 8% in this domain, are dedicated to the development of IoT authentication mechanisms.
Mobile: The domain of Mobile IoT is accentuated by 3%, and the research [
70,
71], is dedicated to enhancing security in the mobile IoT environment. The spotlight is on a mutual identity authentication scheme for mobile IoT devices, showcasing a nuanced approach to bolstering security.
The article further augments its comprehensiveness by providing insights into the distribution of research papers within each domain (outlined in
Table 5). This detailed breakdown offers a nuanced perspective on the distribution of research efforts across these diverse domains, with the communication domain emerging as the focal point with the highest percentage of research papers at 25%. As discussed in the context of RQ2, it illustrates the distribution of research percentages across different domains, contributing to a clearer understanding of the analysis.
4.3. RQ3 What Kinds of Problems Are Present in IoT Authentication?
Several underlying problems have been identified in the reviewed papers as outlined in
Table 6 and illustrated in
Figure 6. In general, authentication processes in IoT are challenged by the need for security in information sharing and data transmission [
6,
28,
68], wireless communication [
49,
51,
56,
57,
62], proximity-based authentication [
36], false-positive identification [
13], or service operations [
38]. Another similar aspect is the ability to resist/detection of evolving cyberattacks [
14,
15,
28,
37,
41,
47,
52,
53,
57,
65,
66,
68], leading to the adoption of fog computing that compliments the needs of IoT [
40,
72]. From the cybersecurity research perspective, the problem with group key distribution or multi-owned devices from an industrial capacity was prevalent [
9,
16,
26,
29,
31,
44,
73], as well as an identity-based authentication protocol for IoT [
43,
60,
70,
74].
Among the most popular problems involves addressing the issue of computational constraints associated with authentication processes in IoT, which leads to the proposal of a lightweight authentication framework [
7,
44,
55,
59,
61,
64,
65,
67,
70], especially when integrating blockchain technology [
80]. Another problem arose from the risk to personal data (or data privacy), which requires a secure communication protocol to protect the privacy and reliability of IoT communications [
10,
30,
32,
33,
50,
52,
53,
65,
71,
77]. Some studies opt for mutual authentication protocols to address privacy protection problems [
45,
70], while others are dependent on highly flawed centralized authentication [
78,
79]. Others were motivated to have the authentication process in IoT integrated into another practical, real-world system or hardware (such as pollution detection systems [
39], digital health solutions [
11,
35,
48], medical devices [
34,
37], automated monitoring systems [
49,
54], intelligent transport systems [
49], multiple integrated access control systems [
32], and the vulnerability of servers in cyber-physical systems [
75,
76]. Some emerging problems involve addressing cross-domain authentication in IoT devices [
12,
42,
69,
70], multi-layered architecture communication [
8,
69], resource-friendly security mechanisms [
36,
58,
64], and Internet-enabled smart devices [
9,
27,
60].
4.5. RQ5: Which Performance Metrics Are Most Commonly Utilized?
The output of the reviewed papers, categorized by the identified performance metrics based on years, is given in
Figure 8. Generally, the majority of the papers concentrated on computational costs, which make up about 52% of the total papers, followed by communication costs, which account for about 47%, time consumption, which accounts for about 33%, storage costs, which account for about 24%, and the rest, which account for less than 13%. These trends are also associated with recent research that showed upward paper output behavior in 2022 compared to 2021 when compared to the year 2023.
The summary of the performance metrics identified in the reviewed paper is tabulated in
Table 8. Most research works focused on assessing the computational cost (or computational overhead) that was involved in the authentication process [
65], complex operations (i.e., hashing, extraction function) [
29,
30,
56], and response time (i.e., time measured to execute the mathematical operations of protocol/certification [
11,
80], or time required for processing the signature [
33,
80]).
The second most adopted performance metric was the communication cost (or communication overhead), which encompasses the overhead associated with the communication process that transmits security parameters between interacting entities [
7,
10,
12,
40,
43,
44,
47,
65], such as the size of the network bandwidth [
39], data transmission amount [
36,
51,
64,
67,
69,
76] or transmission delays [
52], network latency [
28,
42,
69,
75], key exchange protocols [
27], and cryptographic processes associated with it [
32,
38,
50].
Meanwhile, time consumption involves key performance that involves the average execution time of critical steps in the information sharing protocol (such as sharing processing, reputation value computation, and voting mechanism) [
6] or execution protocol [
31,
53], period of physical presence such as on time on air [
39] or alive time that crucial for network longevity [
52,
61], the response time for signature, verification, execution, or analysis time of associated encryption or decryption processes [
11,
30,
34,
43,
44,
45,
60,
73,
79,
80], certificate validation time [
58] or key generation time [
41], real-time complexity of the algorithmic processes [
33], delay time between transactions [
16], or time required in executing tasks [
28,
34,
72].
Store costs were also considered by several studies, which included considerations such as storing credentials that facilitate the authentication process [
7], device information and device-user binding information [
69], the space required to store the necessary data and cryptographic keys for the protocol’s operation [
10,
26,
27,
28,
31,
36,
76], storing associated authentication key parameters [
27,
28,
29,
40,
42,
65], and the size of compiled programs and memory areas of certificates [
9,
29,
58].
Accuracy and energy requirements were among the emerging performance metrics identified in the reviewed papers. The accuracy measures were performance measures associated with using artificial intelligence techniques to evaluate prediction models [
68]: accuracy, F-score, precision, and recall. Accuracy compares the number of correct predictions to the total number of predictions. The F-score combines precision and recall, considering feature differentiation. Precision measures correctly predicted positive samples out of all predicted positives, and recall measures correctly predicted positive samples out of all positives. Prediction performance in authentication was evaluated based on such accuracy measures [
14,
16,
46,
59,
60,
68,
74], as well as the quality of the encryption technique [
34]. Other studies focus on converging the prediction model incorporated in the overall authentication processes [
71].
Meanwhile, energy requirements are considered one of the performance metrics for evaluating the proposed protocol based on an energy model (measured in millijoules or mJ), which is calculated based on the operations performed during the protocol execution and cryptographic operations [
10,
42,
51,
52], the energy required to run the source code (communication cost, sensed data, and implementation cost for each time unit) [
9,
26], the energy consumption of IoT devices during the authentication process using different types of certificates [
9,
58], or multiplying power (in milliwatt or mW) with time required to send a data packet to the destination node through either centralized edge-level or blockchain authentication [
79].
One performance measure was focused on usability, which is associated with the IoT system’s consideration of integrating readily available infrastructure without the need for new hardware to be installed. Some studies focused on such metrics due to proximity-related restrictions [
46], avoiding misdetection or false positive outcomes [
48,
66,
74], mitigating rogue or shadow devices [
50], features associated with access control (context-awareness, granularity, scalability, and interoperability) [
76], and a feature-rich approach [
51].
Some studies considered performance metrics such as throughput, variable sizes, and falseness rate. Throughout, the measure is used either to reflect the ratio of data delivery rates sent by network nodes [
29,
32,
52] or the number of transactions processed per unit of time typically associated with industrial IoT systems [
16,
32]. Meanwhile, variable size refers to the size of the entity measured as a comparison between different authentication techniques, such as the sizes of different types of certificates [
58] or signatures [
33], the key and block size of encryption algorithms [
15], and the total packet size between communicating network nodes. Finally, falseness rate involves determining the possibility or probabilities of attacks or additional detection mechanisms to enhance security features, such as the measure of resistance to guessing attacks via statistical analysis [
65], utility of detection (probability of false alarm rate and miss detection rate) [
57,
74], and fingerprint utility mechanism (false acceptance rate and false rejection rate) [
66].
4.8. RQ8: How Can Advancements in IoT Authentication Address the Collective Challenges in the IoT Authentication Environment?
Clearly defining future directions is critical in the field of IoT authentication research. These directions capture the goals that researchers have in mind for moving the field forward, tackling new problems, and expanding the use of authentication protocols. Future directions act as markers that point researchers in the direction of important objectives, such as improving security and efficiency, encouraging practical applications, and embracing emerging technology. In addition to advancing scholarly conversation, researchers’ articulation of these trajectories opens the door for useful innovations that maintain the resilience, scalability, and adaptability of the IoT authentication domain in the face of changing technical environments. The consolidation of future research trends and directions, structured around common themes, establishes a comprehensive roadmap to stimulate advancements and foster creativity in the secure integration of IoT authentication within interconnected ecosystems.
Security Enhancement and Efficiency Optimization: Researchers in multiple studies [
11,
13,
27,
31,
39,
53,
54,
72,
75,
76,
80] underscore the crucial significance of enhancing security measures while optimizing computational efficiency. This direction aims to achieve a delicate balance between robust security protocols and minimal computational overhead, acknowledging the inherent trade-off between security and performance.
Real-World Implementation and Assessment: Studies [
6,
9,
13,
31,
48,
55,
66,
68,
73] highlight the need to transition from theoretical proposals to practical implementations. Real-world assessments guarantee the effectiveness, scalability, and resilience of proposed authentication solutions, ensuring their capability to withstand the complexities of diverse environments. Researchers aspire to bridge the gap between theoretical advancements and practical usability.
Scalability and Reliability: As evident in various studies [
12,
13,
34,
51,
55,
73,
74], scalability and reliability emerge as central concerns for researchers. As IoT networks expand, the necessity to ensure authentication solutions can seamlessly scale and maintain reliability becomes imperative. This future direction aims to tackle challenges associated with the growing size and complexity of IoT ecosystems.
Blockchain Integration and Security Issues: Recognizing the potential of blockchain in enhancing security in IoT authentication, studies [
14,
17,
31,
65,
72,
73,
75] highlight its importance. Integration with blockchain effectively addresses challenges such as decentralization, immutability, and transparency. Researchers envision blockchain as a viable solution to secure data transactions and user identities within IoT networks.
AI Integration and Advanced Computing Technologies: Unearthed in studies [
15,
51,
77,
80], the integration of AI and advanced computing technologies emerges as a promising avenue for future exploration. AI holds the potential to elevate authentication mechanisms by learning and adapting to evolving threats. Researchers anticipate AI as a tool to enhance the adaptability and intelligence of IoT authentication systems.
Privacy and Access Control: Emphasized in studies [
12,
17,
32,
61], privacy and access control stand out as critical concerns. Given that IoT devices accumulate vast amounts of sensitive data, ensuring robust privacy measures and granular access control becomes imperative. Researchers strive to design authentication systems that prioritize user privacy and offer effective access management.
Communication Efficiency and IoT Optimization: As acknowledged in studies [
10,
15,
44,
55,
56], optimizing communication efficiency emerges as crucial for IoT networks. Researchers endeavor to minimize latency, improve data transmission, and optimize resource usage. This direction tackles challenges associated with communication bottlenecks, particularly in scenarios where real-time data exchange is paramount.
Multifactor Authentication and Standardization: Investigated in studies [
54,
59,
70] multifactor authentication and standardization emerge as essential components for robust security. Researchers advocate for the widespread adoption of standardized protocols to ensure interoperability and emphasize the incorporation of multifactor authentication to strengthen the overall security posture of IoT environments.
Cross-Domain Authentication and Interoperability: Investigated in studies [
13,
75], cross-domain authentication and interoperability emerge as crucial elements for seamless integration across diverse IoT domains. Researchers aspire to devise authentication solutions that can function cohesively in heterogeneous environments, facilitating interoperability between various IoT applications and industries.
Decentralization and Edge Computing: Explored in studies [
10,
73,
77], decentralization and edge computing respond to the demand for distributed authentication mechanisms. Researchers anticipate integrating edge computing to enhance processing at the network’s edge, thereby reducing latency and improving response times for authentication requests.
Efficiency in Authentication Protocols: Studies [
28,
36,
44,
60,
75] focus on optimizing authentication protocols for efficiency. This direction aims to streamline the authentication process, reduce computational overhead, and enhance the overall efficiency of authentication mechanisms while maintaining a delicate balance between security and performance.
Diverse Domain Application: Explored in studies [
32,
55,
59,
66,
69], the examination of diverse domain applications underscores the adaptability of authentication solutions. Researchers seek to design authentication protocols that are applicable across various domains, addressing challenges unique to each application area.
This research question offers insights into the motivations behind each future direction theme, reflecting the considerations of researchers and the challenges they seek to overcome in the evolving landscape of IoT authentication.
Table 11 compiles the studies, grouping them based on shared areas of future work within the realm of authentication in the Internet of Things (IoT).
Figure 11 visually organizes future directions based on common themes, offering a structured overview of the emerging trends in research.
In
Figure 11, the choice to present the data in a linear format is justified by the need to visually represent the common future directions identified in numerous existing research works. The figure, depicting a linear line, serves as a graphical representation of the insights gained from exploring the motivations behind each future direction theme based on the thorough analysis offered by
Table 1.
Figure 11 provides a systematic and easily interpreted summary of the developing trends in IoT authentication research by grouping these future approaches according to common themes. This linear representation enhances clarity and facilitates a deeper understanding of the considerations and challenges that researchers aim to address within the dynamic landscape of IoT authentication.