Abstract
A typical Wireless Sensor Network (WSN) defines the usage of static sensors; however, the growing focus on smart cities has led to a rise in the adoption of mobile sensors to meet the varied demands of Internet of Things (IoT) applications. This results in significantly increasing dependencies towards secure storage and effective resource management. One way to address this issue is to harness the immutability property of the Ethereum blockchain. However, the existing challenges in IoT communication using blockchain are noted to eventually lead to symmetry issues in the network dynamics of Ethereum. The key issues related to this symmetry are scalability, resource disparities, and centralization risk, which offer sub-optimal opportunities for nodes to gain benefits, influence, or participate in the processes in the blockchain network. Therefore, this paper presents a novel blockchain-based computation model for optimizing resource utilization and offering secure data exchange during active communication among mobile sensors. An empirical method of trust computation was carried out to identify the degree of legitimacy of mobile sensor participation in the network. Finally, a novel cost model has been presented for cost estimation and to enhance the users’ quality of experience. With the aid of a simulation study, the benchmarked outcome of the study exhibited that the proposed scheme achieved a 40% reduced validation time, 28% reduced latency, 23% improved throughput, 38% minimized overhead, 27% reduced cost, and 38% reduced processing time, in contrast to the existing blockchain-based solutions reported in the literature. This outcome prominently exhibits fairer symmetry in the network dynamics of Ethereum presented in the proposed system.
1. Introduction
The Internet of Things (IoT) has emerged as a transformative force across various sectors, enabling the seamless integration of physical devices with digital networks to enhance connectivity and data-driven decision-making. The integration of mobile sensors into IoT applications represents a significant advancement in digital ecosystems, particularly in sectors such as smart cities, healthcare, and environmental monitoring. The sensors contribute to a data-rich environment demanding robust frameworks for efficient resource management and secure data communication. Conventional IoT architectures, primarily based on static sensor networks, need to be revised owing to the dynamic nature of mobile sensors, which necessitates more flexible and scalable solutions. At the heart of this revolution lies blockchain technology, which offers robust solutions to the inherent challenges of security and trust in decentralized environments [1]. Blockchain attributes, such as decentralization, immutability, and transparency, are particularly advantageous for managing the complexities of IoT ecosystems, where data integrity and system reliability are paramount [2]. Blockchain technology, particularly Ethereum, offers promising solutions with decentralization, immutability, and transparency. Such attributes are crucial for managing complex IoT ecosystems, ensuring data integrity, and enhancing system reliability. However, the adoption of blockchain technology in this context may be challenging. The resource constraints of mobile sensors, including their limited computational power, storage capacity, and energy, pose significant barriers. These limitations restrict the practicality of implementing complex blockchain operations such as mining and smart contracts directly on mobile sensors. In addition, the continuous interaction between mobile sensors and blockchain networks can exacerbate bandwidth constraints, leading to increased transaction costs and latency.
As IoT devices, including mobile sensors, proliferate, they generate large amounts of data that must be efficiently managed and protected. This convergence of IoT and blockchain promises enhanced security protocols and introduces new complexities in resource management [3]. Conventional Wireless Sensor Networks (WSNs) typically utilize static sensors. However, the dynamic nature of mobile sensors demands innovative approaches to resource allocation and data security, where blockchain can play a crucial role. As WSNs are characterized by resource-constrained wireless nodes, the primary challenges in WSNs are pivotal to issues related to resource management [4,5]. The prominent challenges within WSNs are the intelligent allocation of resources such as energy, bandwidth, processing power, and resource management techniques. The core ideology is to maximize the overall lifetime of a WSN using proper resource management to ensure that the network remains operational for as long as possible without frequent battery replacement or node reconfiguration [6,7,8,9,10,11].
The adoption of blockchain offers greater scope to bridge this gap in security and resource consumption [12,13]. Integrating sensor nodes with the Ethereum blockchain presents several challenges related to resource management. However, some key issues exist: (i) Sensor nodes typically require more computational capabilities, including processing power, memory, and storage. Due to these limitations, running a full Ethereum node or executing smart contracts on resource-constrained sensor nodes is impractical. (ii) Ethereum blockchain operations, such as mining, transaction validation, and smart contract execution, require significant energy resources. Running these operations on sensor nodes can quickly deplete the battery, reducing network lifetime and operational efficiency. (iii) Transmitting data between the sensor nodes and the Ethereum blockchain introduces additional bandwidth requirements. Sending and receiving blockchain transactions, maintaining synchronization with the blockchain, and propagating blocks across the network consume valuable bandwidth that may be scarce in WSNs. (iv) Storing and managing the entire Ethereum blockchain ledger on resource-constrained sensor nodes is not feasible owing to limited storage capacity. As the Ethereum blockchain size increases, maintaining a synchronized copy of the ledger becomes challenging for the sensor nodes with constrained storage resources. (v) Integrating sensor nodes with the Ethereum blockchain raises security concerns, including vulnerabilities in smart contracts, potential attacks on sensor node communication, and risks associated with private key management. Therefore, ensuring the security and integrity of data and transactions transmitted between sensor nodes and the blockchain is essential; however, this is challenging in resource-constrained environments.
Addressing these issues requires innovative solutions that balance blockchain technology’s benefits with the sensor nodes’ resource limitations. This may involve offloading blockchain-related tasks to more powerful edge devices or cloud servers, optimizing blockchain protocols for resource-constrained environments, and implementing lightweight consensus mechanisms tailored to the requirements of WSNs. Although different variants of studies associated with improving blockchain operations exist, it is noted that they are either more inclined towards larger-scale operations such as IoT or are more concerned with security. Therefore, the current state of blockchain in sensors requires greater emphasis on resource management.
Therefore, the issues mentioned earlier are addressed in the proposed study by introducing a simplified and novel computational model for efficient resource management and seamless communication among mobile sensors. The highlighted contributions of the proposed research that differentiate itself from existing systems are as follows:
- A simplified and novel computational framework has been presented for efficient resource management while facilitating seamless communication among mobile sensors.
- This paper presents a novel validation mechanism supported by the unique enrollment of the identity of nodes with a distinct generation process of secret keys for securing internal communications among the nodes.
- An Ethereum blockchain has been used to further strengthen the validation process by presenting a distributed consensus method, whereas hashing and incognito coefficients have been used for privacy preservation.
- A novel trust computation mechanism has been presented that enables nodes to estimate trust under all dynamic scenarios of sensor nodes.
- The proposed system has introduced a novel cost modeling that estimates cost and enhances user experience.
The structure of this paper is as follows: Section 2 presents an elaborate discussion of the existing literature, and a discussion of the identified research problem is given in Section 3. A discussion of the adopted research methodologies for addressing the issues identified is presented in Section 4, while Section 5 presents a vivid debate on the accomplished result. Finally, Section 6 presents a conclusive summary of the study’s contributions.
2. Related Work
Alam et al. [14] presented an elaborate discussion of blockchain applications in IoT, highlighting the essential operations. This study discussed the five-layer architecture of blockchain, emphasizing the fundamental interaction between the blockchain framework and IoT nodes to support numerous blockchain applications. Other studies have reported blockchain applications for supply chain management [15], energy trading [16], water management [17], waste management [18], forestry and agriculture [19], mineral traceability [20], and fishery management [21]. Based on these studies, almost every work revolves around applications that are more inclined towards its usage with the Ethereum blockchain.
In addition, various studies have adopted the Ethereum blockchain application in smart cities, secure sensor communication, and resource management. Existing studies in this direction have been carried out to develop smart contracts for governance and transactions [22], where such contracts can automate various governance processes, such as permits, licenses, and property transactions, thereby reducing bureaucracy and increasing transparency. Ethereum-based decentralized identity solutions can enhance security and privacy in smart cities by providing secure and verifiable digital identities for residents, workers, and devices. These identities can be used for access control in sensitive areas, services, and data [23]. Furthermore, Ethereum’s blockchain provides a tamper-resistant and immutable ledger for recording sensor data in smart cities to prevent unauthorized tampering or manipulation [24]. Subsequently, smart contracts can automate data validation, aggregation, and analysis, enabling real-time decision-making and optimization of city operations [25]. Ethereum’s blockchain enables the tokenizing of physical and digital assets and services in smart cities to create new business models for sharing economy initiatives [26]. Ethereum-based decentralized data marketplaces can allow the exchange of valuable urban data among stakeholders, such as government agencies, businesses, researchers, and citizens [27]. Marketplaces can catalyze innovation in urban analytics, urban planning, and smart city development by incentivizing data sharing through token incentives and smart contracts.
The usage of blockchain in IoT varies; however, it is more harnessed for accomplishing security objectives towards resisting various lethal threats. In this regard, trust management-based approaches have evolved more in IoT utilizing Ethereum. The work presented by Alam et al. [28] has multiple trust management schemes for the service provider that contribute towards yielding a list of permissible and non-permissible operations by the nodes. The model can resist potential trust-based attacks. A trust-based approach using blockchain was also reported by Awan et al. [29], which facilitates secure data transmission using asymmetric encryption keys in sensor networks. The attacker is identified using the delayed transmission, response time, and forwarding rate. Another unique trust assessment scheme was presented by Liang et al. [30], where the framework for spectrum management using a blockchain was presented with a target to achieve higher privacy conservation. This study presents a trust-based evaluation in which the outcome resists the most trust-based attacks. Latif et al. [31] presented a trust evaluation model using blockchain for smart marketplaces. The study outcome was observed to have a significantly reduced latency. Other reviewed studies on trust-based blockchain design have also been conducted by Al-Rakhami [32], Arshad et al. [33], Bellaj et al. [34], Masmoudi et al. [35], and Javaid et al. [36].
Ding et al. [37] presented an energy minimization approach for mobile edge computing in which blockchain was used to design a unique multiple access approach. This study addresses energy resource issues while securing applications for dynamic edge devices. Existing studies have also considered strengthening storage resources with unique authentication schemes using blockchain, and one such study was carried out by Feng et al. [38]. The authors provided a unique authentication scheme in which a storage system is designed using a Merkle tree and blockchain to achieve authentication efficiency. The scheme resists internal and external attacks using two-way validation performed with the servers hosted in the cloud ecosystem. Hwaitat et al. [39] also presented a study on authentication in which a permission-based blockchain was used to simplify the authentication method and optimize the data storage system in a large-scale network. Data encryption was performed using homomorphic encryption, and the outcome exhibited practical privacy preservation. Various authentication schemes using blockchain were also presented by Amjad et al. [40], Dwivedi et al. [41], and Chen et al. [42].
Existing blockchain schemes also alleviate various internal IoT operations, indirectly contributing to security. Lee et al. [43] presented a unique architectural design for a gateway node to resist malicious activities in data using the Ethereum blockchain. Li et al. [44] presented a task-offloading scheme using blockchain and bio-inspired algorithms that targeted optimal resource allocation in edge networks. Namane and Dhaou [45] discussed an access control scheme in a blockchain free from any dependencies of trusted third parties. Distributed and open-source software frameworks have been adopted for data provenance in extensive-scale networks, as noted by Pajooh et al. [46]. This study contributes to distributed data storage using Hyperledger fabric to retain extensive metadata and verification tags. Thangaraj and Sree [47] presented a computation offloading mechanism in which a search optimization algorithm was integrated with a bio-inspired algorithm implemented on fog computing characterized by blockchain properties.
The existing system also adopts a machine learning approach to improvise blockchain-based operations on a large scale. Dong et al. [48] used attention-based gated recurrent units to predict the inbound tasks. Federated learning was used by Fu et al. [49] to strengthen trust in IoT. In addition to predictive resource management, this model performs attacker detection using a Support Vector Machine. Further use of machine learning approaches in blockchain has been reported by Rathod et al. [50], Charles et al. [51], Farooq et al. [52], and Ismail et al. [53]. Faheem et al. [54] presented a secure blockchain model for controlling and monitoring events in smart grids.
Table 1 summarizes the existing studies discussed in this section.

Table 1.
Comparative summary of existing studies.
Hence, various approaches exist in the existing literature where blockchain has been considered for simultaneously addressing smart resource management and data security. The summary of the review findings are as follows: (i) Ethereum blockchain has been increasingly used for catering to the operational demands of various blockchain operations apart from its inherent security characteristic. (ii) Existing studies are more focused on accomplishing application targets and less towards resource optimization, with (iii) less inclusion of dynamicity of nodes and flexible architecture to support extensive network communication at low cost. Hence, a significant gap is observed between (i) increasing blockchain operations focusing on less flexible communication and low-focus cost efficiency and (ii) a need for more balance between security and resource management in IoT applications.
3. Problem Description
Integrating mobile sensors into IoT applications represents a significant advancement in digital ecosystems, particularly in smart cities, healthcare, and environmental monitoring. These sensors contribute to a data-rich environment that demands robust frameworks for efficient resource management and secure data communication. Conventional IoT architectures, predominantly based on static sensor networks, need to be revised due to the dynamic nature of mobile sensors, necessitating more flexible and scalable solutions.
Blockchain technology, particularly Ethereum, offers promising features such as decentralization, immutability, and transparency, which are crucial for managing complex IoT ecosystems and ensuring data integrity. However, the adoption of blockchain in this context faces several challenges:
- Sub-Optimal Scalability: Existing blockchain networks often struggle with scalability as the number of nodes and transactions increases [28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53]. In sensor networks, where thousands or even millions of devices generate data and transactions, scalability becomes a significant concern. Each node’s computational and storage requirements grow with the blockchain, potentially leading to performance degradation and decreased efficiency.
- Extensive Energy Consumption: Traditional blockchain consensus mechanisms, such as Proof-of-Work (PoW), require significant computational power and energy consumption [42]. This is particularly problematic for resource-constrained sensor networks with limited battery life. Energy-efficient consensus mechanisms like Proof-of-Stake (PoS) or delegated consensus are more suitable but still need careful consideration [46,48].
- Storage Requirements: Storing a full copy of the blockchain ledger on each node consumes considerable storage space, which may be limited in sensor devices [46,48]. As the blockchain grows over time, storage requirements increase, potentially exceeding the capacity of sensor devices. Managing and pruning historical data while maintaining blockchain integrity remains a challenge.
- Bandwidth Constraints: Blockchain transactions and communication with other nodes consume network bandwidth. Blockchain-related traffic can compete with sensor data transmission in sensor networks with constrained or intermittent communication channels, leading to congestion and delays [38].
- Latency: The validation and consensus processes required for blockchain transactions introduce latency, which can be problematic for time-sensitive applications [39]. Balancing transaction validation with the need for low latency is essential in sensor networks.
- Transaction Cost: Blockchain transactions often incentivize miners or validators [29,38]. In sensor networks where microtransactions are typical, these fees can become a significant overhead due to their disproportionate nature compared to the value of the transactions.
- Security and Privacy Concerns: Blockchain’s immutability and transparency can raise security and privacy issues, particularly in sensor networks dealing with sensitive data [52,53,55]. Ensuring data privacy and confidentiality while maintaining blockchain integrity is crucial.
To address these challenges, our research proposes several innovative solutions:
- Communication Modes: We introduce two distinct modes of communication—node-to-node (N2N) and node-to-structure (N2S)—to enhance data exchange capabilities and improve scalability. This approach provides more alternatives for data transmission, even under peak traffic conditions, thereby addressing scalability issues.
- Unique Network Model: A novel network model is proposed that optimizes performance by considering multiple attributes of network and signal quality, such as transmittance power, channel gain, and noise. This model aims to reduce latency and energy consumption while addressing scalability challenges.
- Simplified Consensus Mechanism: The proposed scheme includes a simplified finite field and robust key generation approach to enhance security without compromising performance. This covers a novel validation scheme and an innovative trust computation method.
These innovations collectively address the limitations of existing blockchain-based approaches by improving scalability, reducing energy consumption, optimizing storage and bandwidth usage, minimizing latency, and managing transaction costs effectively. The proposed scheme aims to provide a scalable, efficient, and secure model that bridges the gap between blockchain technologies and mobile sensor networks, thereby enhancing IoT applications.
4. Methodology
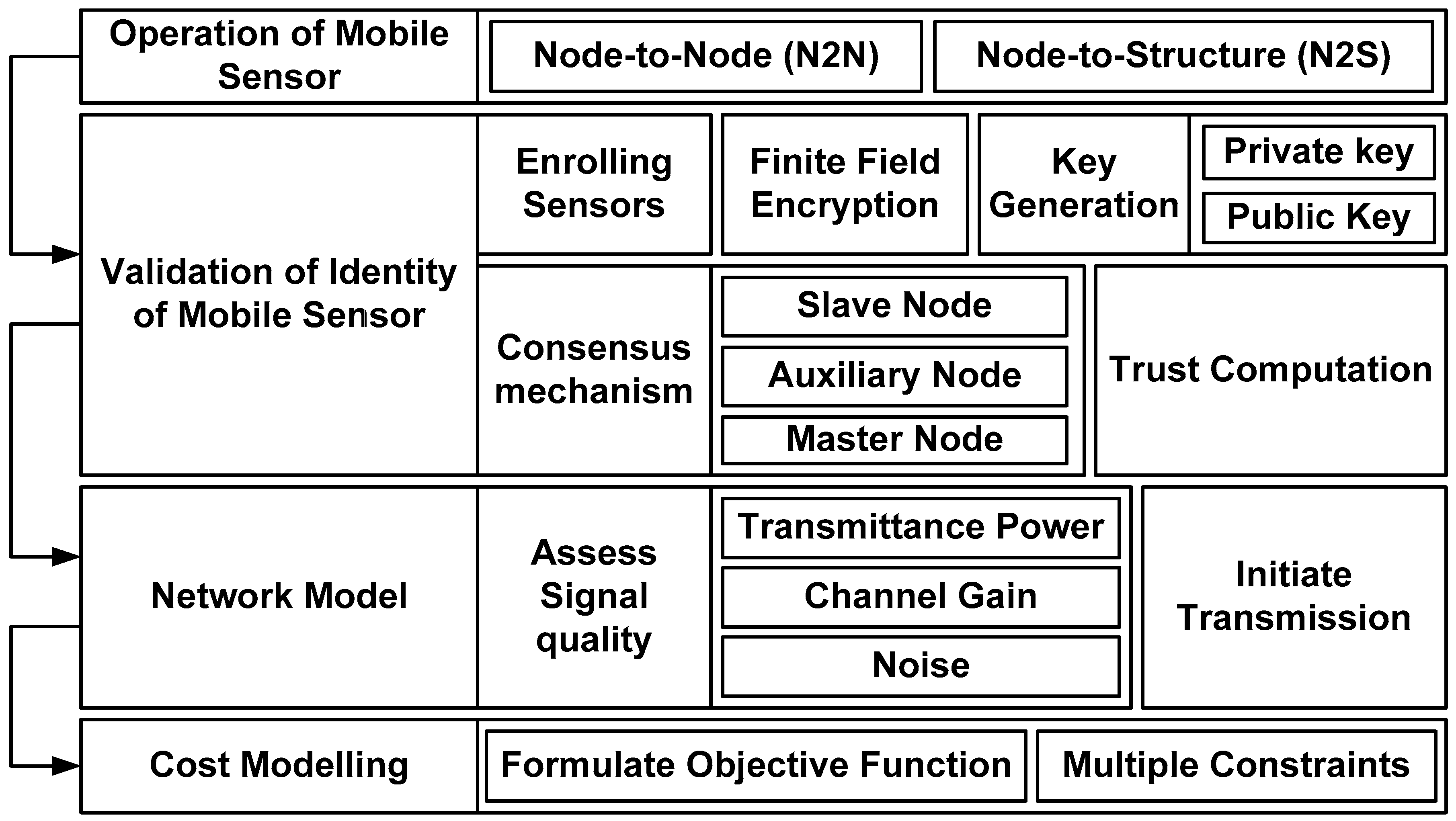
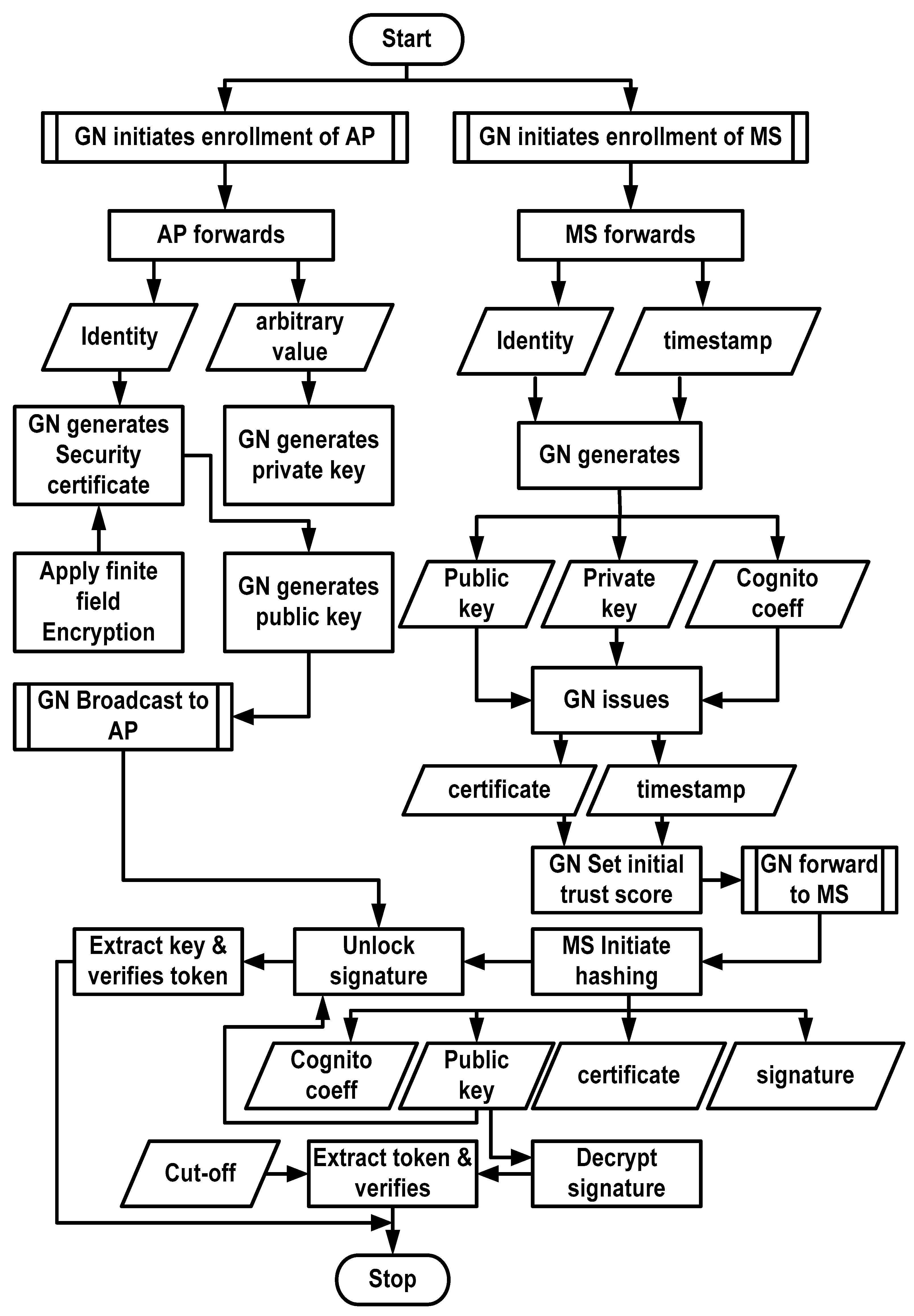
The proposed system introduces a novel computational model for cost-effective resource management to support secure communication among mobile sensors in the Ethereum blockchain. The core idea of this model is to resist various illegitimate accesses to sensitive data in large-scale sensory applications. The proposed model also aims to achieve a higher degree of symmetry from the perspective of network dynamics to retain sufficient equilibrium of fairness, equality, and balance in sensory applications. Owing to the inclusion of an innovative scheme for securing mobile sensors and their associated operations within the network model, the proposed system also encourages an efficient decentralized environment resilient against undue actions adopted by a small group or single entity. The concept of the proposed scheme is illustrated in Figure 1.
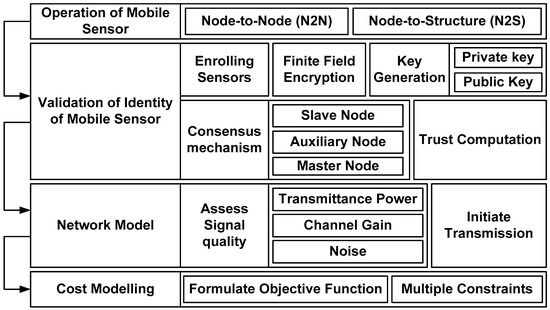
Figure 1.
Proposed conceptual model of securing communication in sensory applications.
As shown in Figure 1, the proposed system involves four discrete operational blocks related to modeling the operations of mobile sensors, performing validation, a discrete network model, and a cost model. All four operational tasks are jointly aligned for secure communication using the Ethereum blockchain. The modeling of the proposed scheme considers direct communication within mobile sensors and communication between the mobile sensor and network structures in the form of access points and gateway nodes. The scheme authenticates the data based on resource-based constraints and trust scores by utilizing the optimal resources of the communication channels. The first module of the mobile sensor operation introduces density-based computation, and the second module validates the operation. Validation involves the sensors’ identity enrollment process, where public and private keys are used to safeguard the secure exchange of keys. The gateway node enrolls mobile sensors and access points and provides communication authorization. The validation model also introduces a simplified consensus method in which an access point is set with multiple roles. Additional validation was performed on the identity of the sensors where digital signatures were used, followed by a computation of the trust score. The proposed model introduces a novel trust score computation for node-to-node and node-to-structure communications, considering the possibilities of failed and successful communication. Finally, a network model was introduced to facilitate communication on the computed path with higher signal quality. The proposed scheme also presents a cost model incorporating sustainable resource management.
The contributions of the proposed conceptual model are discussed as follows: (i) unlike the existing usage of blockchain-based communication systems between two nodes, the architecture presents a dual mode of communication of nodes, i.e., N2N and N2S, to facilitate broader communication in an extensive distributed system in IoT; (ii) the architecture also introduces a dual validation scheme for mobile sensors using less-complex and yet innovative public key encryption, as well as a novel consensus method; (iii) a newly introduced role of nodes is introduced in the proposed consensus method that not only offers better node selection but also contributes towards reliable trust computation; and (iv) the proposed architecture presents a novel cost modeling scheme with the inclusion of multiple practical schemes, which is seemingly not witnessed in existing methods of blockchain-based resource management in IoT.
A closer look at the proposed methodology shown in Figure 1 shows the inclusion of some novel traits associated with the operational framing of mobile sensors, the confirmation process of sensor identity, simplified modeling of communication, and novel cost modeling. It should also be noted that this model includes computational power or stake in the network structure of Ethereum, which acts as a criterion for node participation in the network in the form of a miner or validator. This means the proposed scheme incorporates symmetry in its design architecture, offering fair and equal opportunities for all nodes to perform consensus and block validation.
Considering the adoption of Ethereum 2.0, this scheme offers a fair deal of symmetry in its consensus operations. In a real-world scenario, the selection of validators in Ethereum 2.0 to perform block validation is carried out based on their stake (i.e., the amount of cryptocurrency). From the perspective of novelty, it can be seen that the proposed study model introduces three types of nodes in the consensus block (i.e., slave, auxiliary, and master) that contribute to effective trust computation. The security design involved in the proposed system is also controlled by cost modeling, which includes multiple constraints on the specific design states of the network model. In this process, a better form of symmetry is maintained to ensure their impact is directly proportional to their proposed stake. At the same time, this scheme prevents the participation of any single node from gaining uneven control of the network.
Apart from this, the triple role of nodes in the consensus mechanism presented in the proposed system with mobile sensors also ensures that there is always a functional network for supporting seamless communication with mobile sensors. The prime notion of this phenomenon is to offer a sustainable network that can withstand significant failures and attacks. In short, a better form of data integrity and consensus is maintained by the combined efforts of multiple nodes. Hence, better symmetry towards resiliency and network stability is presented in the proposed methodology.
4.1. System Design
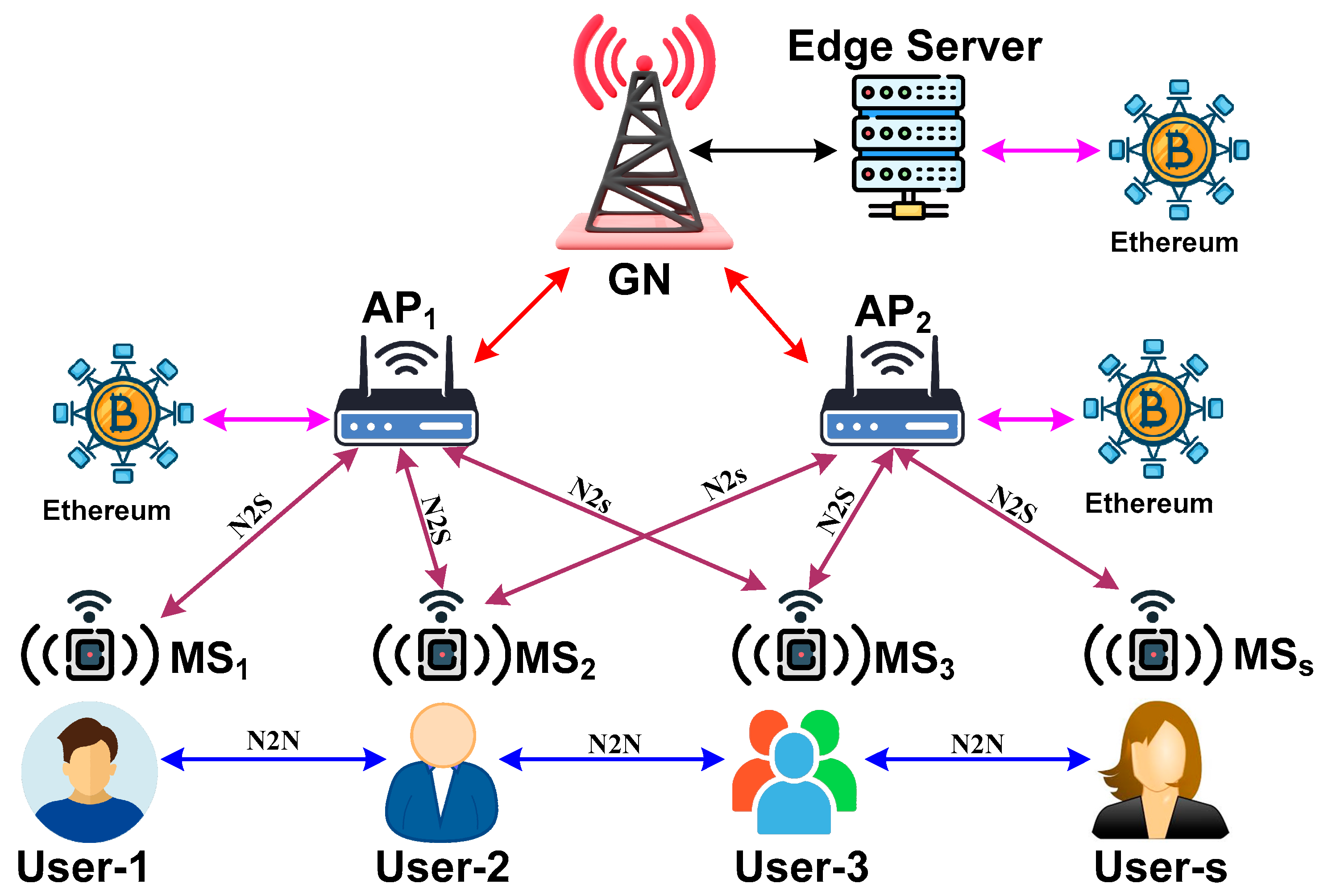
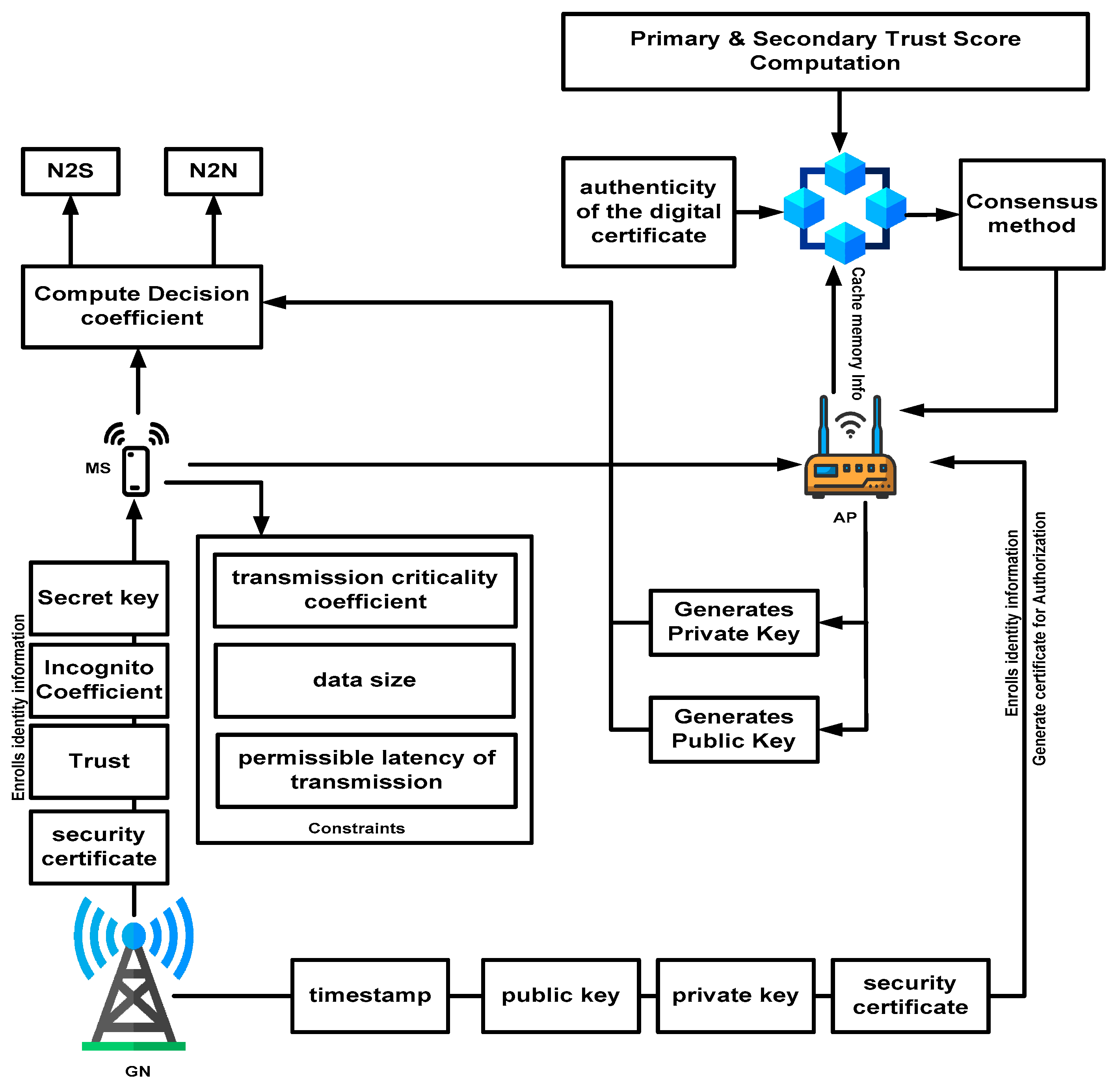
The proposed model considers multiple mobile sensor devices within an IoT environment, where communication is facilitated between the sensors or network structure. The proposed scheme comprises two prominent actors, mobile sensors and access points, as well as node-to-node communication systems, node-to-structure communication systems, and gateway nodes. The various forms of communication among the actors presented in the proposed model are exhibited in Figure 2.
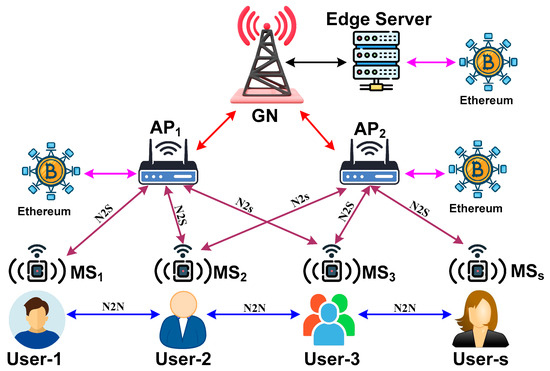
Figure 2.
Communication system among the actors.
Figure 2 shows the implementation scenario of the proposed study model with the aid of multiple actors: (i) The first actor of this model is the mobile sensor (MS), which is considered to be possessed by the user within a definitive IoT environment. The proposed scheme assumes that a specific application related to the smart city runs on the user’s handheld device, which is also equipped with a sensor. The purpose of this mobile sensing device is to facilitate communication by acting as a source, destination, or relay node during the transmission process. (ii) The second actor in this model is the access point (AP), which collects essential data from various mobile sensors and other hotspots situated within a smart city environment. The primary purpose of the AP is to enable the MSs to communicate with each other and the surrounding network structure. (iii) The third actor of this model is a node-to-node (N2N) communication system, where one MS can exchange data with one of multiple MSs within an IoT environment. (iv) The fourth actor is node-to-structure (N2S) communication, in which one MS can communicate with the current network structure. It should be noted that both N2N and N2S are facilitated by AP, which initially identifies a specific MS and then authenticates its genuine identity and privileges to participate in data exchange within an IoT environment. (v) The fifth actor is the gateway node (GN), which connects all the APs residing in one smart city to communicate with APs residing in different smart cities. This significantly assists in increasing the transmission coverage. The proposed scheme introduces the Ethereum blockchain to validate the identity of the MS for both the communication processes (N2N and N2S) when a specific mechanism of enrolling the identity of the MS is followed by a validation framework to safeguard the transmission process among MSs. Table 2 highlights the notations used in the manuscript.

Table 2.
Table of notations.
The scheme also considers the rate of data transmission as well as the temporal attribute association, which is computed based on the current location of the MS. Furthermore, the model introduces cost modeling for its resources based on the saturation state of the server. All of these operational modules are integrated to perform user cost management securely. The essential operations are discussed as follows:
4.2. MS Operation Module
The module considers the GN residing in uniform proximity to the AP in a defined deployment within a smart city region. The AP and GN are powered by an edge server, where the resources are provisioned for various operations, e.g., generating updates associated with the real-time condition of the road to the MS, the dissemination of emergency events, and congestion-related information analysis. Considering , the number of N2N mobile users assumed to possess time slots is represented by a discrete probability function once number of MSs enter the coverage of specific regions within the smart city. Therefore, the mathematical representation of the density number of MSs is expressed by Equation (1).
Equation (1) shows the formation of the density of sensors , which depends on two variables: and . The first variable, , represents , and the second variable, , represents , where the attribute represents the mean onset score of MS in a specific smart city zone. It should be noted that is also influenced by various sets of information that the MS demands during the mobility process to enable seamless communication with another MS or network structure. In addition, the computational burden of GN is controlled by the MS, which occasionally switches between N2N and N2S modes of communication. This switching mechanism is used to access the information stored within the cache from the neighboring MS or the nearest AP. The proposed module considers the dual mode of sensory communication in transmitting Tr(N2N) and receiving Re(N2N) while adopting the N2N mode of data transmission. The model executes communication strategies mainly within an IoT environment and with less network traffic based on cellular systems. Different numbers of connected N2N modes of communication within the MS are not permitted to exchange their data within the same communication channel. In contrast, only one MS (i.e., ) is allowed to pair with another MS in N2N. Simultaneously, the connection (in the form of request and response) of the MS is permitted to be paired with only one AP. This simplified strategy allows each sensor to be free of any possibility of interference.
As the MS within the users is free to move at any variable speed within the defined region of a smart city, it is necessary to characterize this topology and connection among the MSs as highly dynamic and intermittent. This situation could introduce security vulnerabilities in the IoT environment. In such circumstances, it is computationally challenging for every individual peer sensor within the N2N mode of communication to be protected from being traced or vulnerable to attackers in IoT. Also, it directly contributes to introducing security loopholes into the N2S mode of communication. This means attackers can leverage a victim MS and traverse the entire network structure. Hence, verifying each MS’s legitimate identity is essential before authorizing the node to permit caching or allow data exchange operations.
To render an effective transmission, an MS must have access to the resource-level information stored within the cache of another MS or AP while performing its mobility. The proposed scheme introduces controlled constraints to realize the complexity associated with the data transmission process. The first constraint attribute chosen is the transmission criticality coefficient , which the user with MS defines. The second constraint attribute is the data size , and the third constraint is the permissible latency of transmission . The constraint attributes differ from each other. It is based on the computational effort required to process varied forms of data transmission with various content to be exchanged. For this purpose, the GN provides resources (especially channel capacity), and different costs are assigned according to the demands of the data transmitted and exchanged by the MS.
4.3. Validation of MS Identity
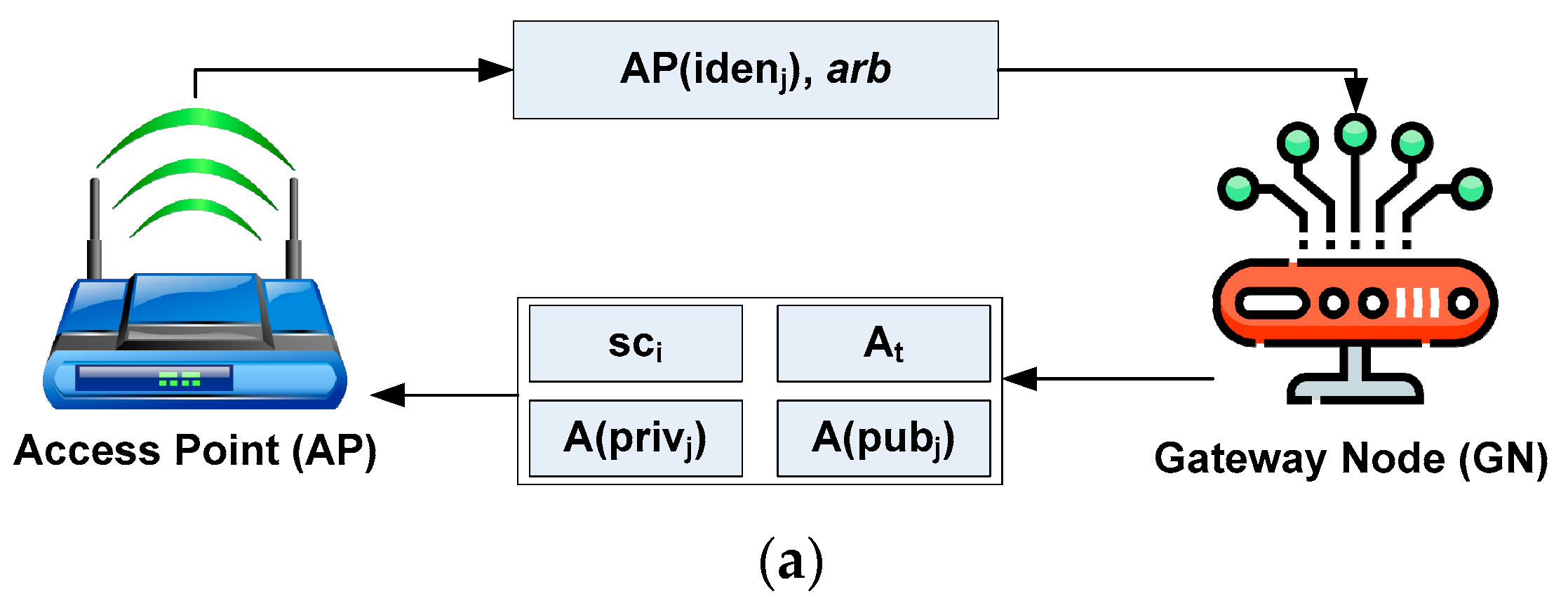
The prominent actors involved in the validation process are the MS, AP, and GN. The GN enrolls the original and legitimate identity-based information of each MS once it enters its specific coverage. The secret key (both private and public) is generated, followed by the GN dispatching the security certificates to the MS. The AP facilitates the caching operation for each MS while all the information within the cache memory is forwarded to the Ethereum blockchain. Each MS can perform the data exchange process while updating its information for the AP. The complete communication via the Ethereum blockchain facilitated in the proposed scheme is carried out in multiple operational modules.
The first operation module in this process is associated with enrolling the identity of the MS. Under this enrollment process, the system considers that there are ith APs, i.e., , that are responsible for performing the enrollment task to the GN, followed by forwarding the identity of AP, i.e., , along with an arbitrary number , which is mathematically expressed by Equation (2).
In Equation (2), each available AP forwards the identity information and arbitrary score to the GN. In addition, the size of an arbitrary score can range between 128 and 512 bits, depending on the scale of data being exchanged. After the information related to enrollment is obtained from each by the GN, the proposed system generates a security certificate for the authorization . Adopting the finite field encryption strategy, the GN generates a security method expressed by Equation (3).
In Equation (3), the generation of security method concerning two non-negative numbers of integer type is achieved considering three attributes of finite field encryption, where , , and , where variable pr represents a prime number. The arbitrary variable is a private key for access point and is acquired by the GN. On the other hand, the generation of the public key is computed for an arbitrary value from the reference point in a finite field. The mathematical expression for generating private and public keys from the access point obtained by GN is shown by Equation (4).
Equation (4) exhibits two essential tasks: the generation of a private key by the access point, i.e., A that is equivalent to an arbitrary number , and the generation of a public key by the access point, i.e., which is equivalent to the product of a recently generated private key, i.e., and the location of the reference point of a finite field, i.e., , where represents in elliptical curves. The suffix represents the number of access points, AP. After generating keys, the information associated with the public key, i.e., and timestamp , are disseminated using broadcasting to the entire network by the GN. The timestamp represents the instantaneous time when GN completes the enrollment process for AP. Furthermore, the essential information is forwarded to the AP by the GN, which is mathematically expressed by Equation (5).
Equation (5) shows that a secured and dedicated communication channel is utilized for forwarding essential information , which consists of a timestamp during enrollment , the public key of access point , the private key of access point , and the security certificate for authorization . The proposed scheme uses a consensus mechanism to retain the sequence of operations within a network with the Ethereum blockchain in a decentralized manner. Adopting the consensus method assists in confirming the appropriate accounting of blocks to mitigate trust-related issues. The proposed scheme adopts a fault-tolerant consensus method to incorporate adaptiveness in blockchain operations, especially in the case of the N2S mode of communication [56]. According to the consensus mechanism, more entities are involved, known as slaves, auxiliaries, and masters. The following discussion details the entities engaged in the implemented consensus methods:
- Slave Node: This node is set to silently monitor the system’s actual states, followed by responding to the request from either the master node or the auxiliary node. Slave nodes refrain from participating in the election process of the master node directly; however, they can become auxiliary nodes if acknowledgment is not received from the master node after a certain period of timeout. The primary task of the slave node is to maintain sync with the master node by replicating its actions.
- Auxiliary Node: This node actively participates in transactions as a master node. The adopted consensus method [56] permits the selection of the master node based on arbitrary timeout instances. If the slave node does not hear from the master node within a specific cut-off time, the slave node changes to the auxiliary node state and initiates the election process. During the election process, the auxiliary node forwards requests from other nodes present within the system. If an auxiliary node receives votes in prominent numbers, it acts as a new master node.
- Master Node: The master node is primarily responsible for replica management associated with the log entries in the blockchain network. The master node processes requests generated from the client coordinates the complete consensus method, and transmits the updates to the slave nodes to retain the status of the master node. Notably, the master node is the pivotal contact point for the write operations in the Ethereum blockchain.
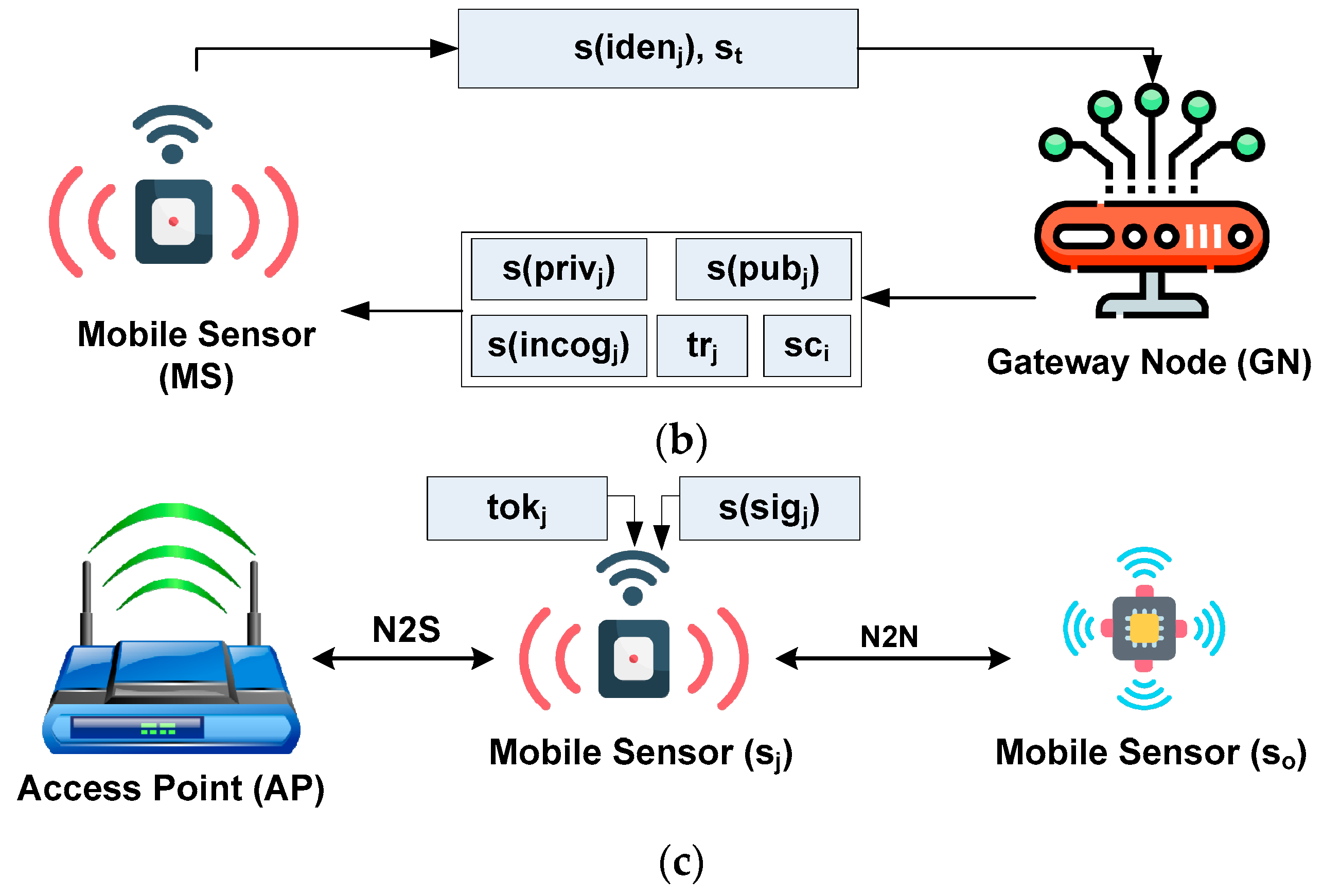
Based on implementing this consensus mechanism, the proposed model considers the AP to be initially represented by a slave node. However, the AP changes to an auxiliary node if it does not hear from the master or auxiliary nodes. The Ethereum blockchain is managed by the master node elected by the auxiliary node in each operational cycle. The acquired set of information is transformed into blocks by the master node, and this information is disseminated to every remaining node. The system approves the generated block, and the timestamp is subjected to verification. Therefore, according to the proposed scheme, the access point APj plays the role of a slave, auxiliary, and master in the preliminary point of operation if there is no response and if it receives a majority of the consensus. Each user device equipped with sensor must furnish the identity information to the gateway node, GN, where the identity information consists of a unique index of the user sensor, i.e., and timestamp . An arbitrary number is generated by GN, which plays the role of the sensor’s private key, . This means that once the system obtains the request message, a private key is generated, i.e., , where the suffix represents all mobile sensors. Based on Equation (3), the proposed scheme incorporates the reference variable to include a finite field while generating a public key. The generation of an incognito coefficient is obtained using Equation (6).
Equation (6) shows that the generation of the updated public key of the mobile sensor, i.e., s(), is carried out by considering attribute , which represents the product of the private key of the mobile sensor and the reference variable of the finite field . Furthermore, it is shown that the generation of the incognito coefficient s() of the mobile sensor is performed using attribute , which represents a hashing method applied to the value obtained from the concatenation of the identity of sensor and an arbitrary number of sensors . The incognito coefficient is a substitute or alternative name adopted in the proposed system to hide an entity’s true identity and susceptible information using mobile sensors. Its purpose is to provide anonymity and privacy in digital transactions and communications. The incognito coefficient can be useful when individuals want to interact with others while keeping their real identities concealed. Furthermore, incognito coefficients can be generated using cryptographic techniques to prevent traceability, which can be linked to the original identity. This allows individuals to participate in transactions or communications without revealing personal information. The incognito coefficient can also be crucial in various cryptographic systems, including anonymous cryptocurrencies, privacy-preserving communication protocols, and secure authentication schemes. Figure 3 shows the complete process of enrolling and validating the mobile sensors, which mainly exhibits the process of enrolling AP (Figure 3a), the process of enrolling mobile sensors (Figure 3b), and the validation process of each mobile sensor (Figure 3c).
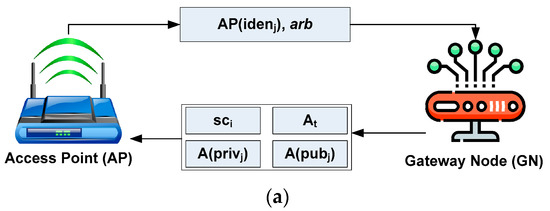
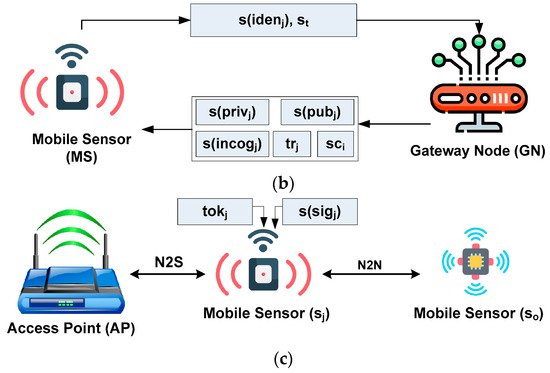
Figure 3.
Enrollment and validation of sensor.
A digital certificate is generated by GN, followed by configuring the preliminary trust score . This means that there are various ranges of security information embedded in the form of the trust score , digital certificate , incognito coefficient s(incogj), public key s(pubj), and private key s(privj). GN disseminates the embedded information to each mobile sensor. The content of the information can be acquired by the mobile sensor either using the N2N or the N2S mode of communication. The mobile sensors perform validation checks for other nodes before communicating concerning their identities. When the mobile sensor sj is interested in communicating with another node, a request must be made for this intended communication to the APj and the target mobile sensor. In such cases, the source mobile sensor encrypts its incognito coefficient s() using a one-way hash function. A similar hashing operation is performed for a digital certificate sci and public key s() that forms a security token followed by the application of a digital signature to generate a security token to generate a user signature s(). The digital signature s() can be opened by the access point with the aid of the extracted public key s(). Using this procedure, the security token is obtained, followed by authentication of the equivalency of the security token with .
However, the authenticity of the digital certificate sci is determined by the access point in Ethereum. Concurrently, it responds with either successful or failed authentication flags to the user, i.e., mobile sensor . Similarly, the other sensor node decrypts the digital signature s() using its public key to acquire the security token . The system further checks the equivalency of to be the same as . In contrast, this further verifies that the trust score is higher than the cut-off, followed by successfully generating a response message to validate the sensor .
However, there remains a likelihood of intrusive activity despite completing the enrollment procedure for the mobile sensors. To alleviate this issue, communicating mobile sensors must possess individual trust scores before disseminating the contents among the users. The flowchart of the implemented validation is shown in Figure 4.
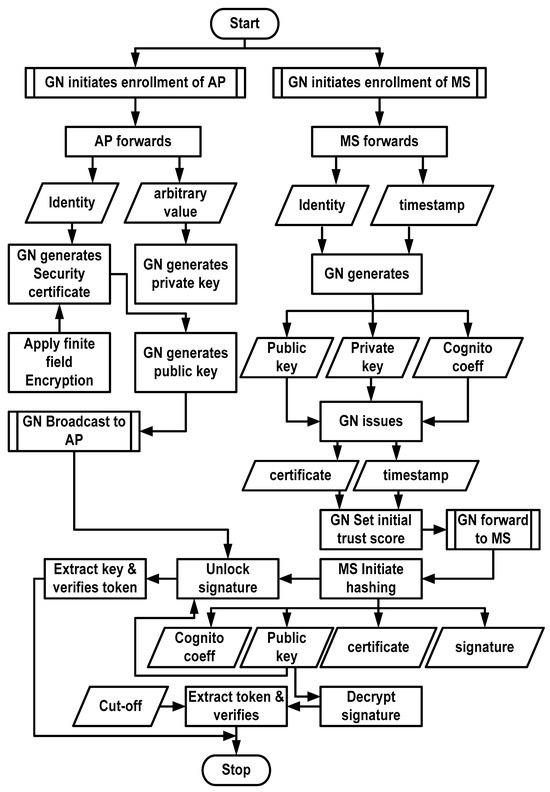
Figure 4.
Flowchart of adopted validation.
The computed trust score must be forwarded to the AP residing near the mobile sensors. By adopting the proposed consensus mechanism, an Ethereum blockchain was formed by considering the trust score for storage. The computation of the trust score Tr is mathematically expressed by Equation (7).
In Equation (7), the evaluation of the primary trust score is performed using two sets of attributes, and . The attributes , , and represent the state of the communication channel, the current state of the mobile sensor, and the penalty for outlier data, respectively. The attribute represents an accomplished number of communications divided by the summation of accomplished and failed data transmissions. Attribute represents original sourced data divided by an accomplished number of communications, while attribute represents outlier data divided by an accomplished number of communications. However, as mentioned earlier, the computation of the trust score is for two mobile sensors in the direct communication range with each other. Otherwise, the mobile sensor is required to compute the trust score values obtained by any other mobile sensor directly communicating with the target mobile sensor. The computation of the secondary trust score is mathematically expressed by Equation (8).
In Equation (8), the secondary trust score is calculated by dividing attribute by variable representing the number of mobile sensors. The attribute represents the summed-up values of all the mobile sensors (1, 2, … ). Hence, the final trust score is computed by considering both primary trust and secondary trust , as shown by Equation (9).
Equation (9) computes the primary trust score. The primary trust is calculated when two mobile sensors are in direct communication. In contrast, the nodes must depend on the secondary trust calculation if they are not in direct communication.
4.4. Network Model
Mobile sensors initiate data transmission after validating the identity, as discussed in the previous section. The source mobile sensor communicates with the target sensor, which is characterized by a higher trust score, by forwarding a request for initiating data dissemination by . After the validation, the system initially chooses the N2N mode of communication between the two mobile sensors. This operation is followed by disseminating data to the source sensor obtained from the target sensor . The system records the positional information for the transmitting sensor and receiving sensor , followed by evaluating an adequate distance between them. To obtain quality data, it is necessary to consider the possibility of interference when mobile sensors attempt to communicate concurrently with the AP and different mobile sensors. Potential interference will negatively affect the outcome of the experiment. Hence, it is necessary to determine the proportion of information that can be extracted from a given set of traffic-flow information. The signal quality is expressed by Equation (10).
Equation (10) shows that the signal quality is computed using three dependable attributes: , , and . The attribute represents the product of the transmittance power and channel gain, whereas the second attribute, , represents the Gaussian noise power. The third attribute, , is the product of the decision coefficient and channel gain. The decision coefficient represents whether the mobile sensor chooses to use the N2N mode of communication or the N2S mode of communication. The proposed scheme considers the decision coefficient to be one in the case of N2N, or else it is zero in the case of N2S. Finally, the model computes the cumulative duration required for data transmission using Equation (11).
In Equation (11), the cumulative duration is computed by exploring the maximum score, where and represent the durations required for the N2N and N2S communication modes, respectively. Both and are computed using the respective parameters of the side of the data and transmission rate.
4.5. Cost Modeling
The proposed scheme introduces a simplified form of cost modeling to ensure the effective deployment and utilization of all network and computational resources. The field data obtained by the validated mobile sensors are legitimate users, and the respective costs are paid to the sensory service provider. The empirical formulation of the cost model for the proposed system is shown by Equation (12).
In Equation (12), the scheme computes the cost using two dependable attributes, and . The attribute represents the product of the channel capacity size χ assigned to the mobile sensors and where the variables and represent a change in the unit price and instantaneous channel capacity identified at specific timeslots. The last attribute, , represents the minimum unit price for channel capacity usage. Based on the cost modeling, the higher the usage of channel capacity by the user, the higher the cost required to be paid by the user. Therefore, the user may opt for a different access point or use a different user (or mobile sensor) to explore alternative solutions to lower resource costs. Increasing the resource cost can significantly contribute towards minimizing the bottleneck condition and assist the system in offering a better quality of experience.
Equation (12) is related to the cost model for the overall system. Hence, the system also introduces a cost model for individual mobile sensors based on the occupied duration of resource usage, mathematically expressed by Equation (13).
Equation (13) indicates that the user cost is computed using two cost attributes, and . The first attribute, , is the product of the system cost (obtained from Equation (12)) and the time stamp for the transmitting sensor, and represents the same for the receiving sensor. Furthermore, an objective function is designed for this purpose with a target to minimize the cost.
The prime conditions used for Equation (14) for the objective function Ofun are multiple viz. (i) there is a limited channel capacity assigned for all APs to a single mobile service; (ii) there is a limited cumulative channel capacity for facilitating the N2N mode of communication; (iii) limited channel capacity is assigned for APs to a single mobile sensor; (iv) only one AP can be used to connect with one mobile sensor (that can also be connected with another mobile sensor at maximum); (v) the trust score of communicating mobile sensors should be greater than the cut-off trust score; (vi) the formation of complete data using data extracted from the access point, AP and N2N itself; and (vii) cumulative latency should not be more than its tolerable latency for accomplishing data transmission. A high-level diagram of the proposed scheme is exhibited in Figure 5.
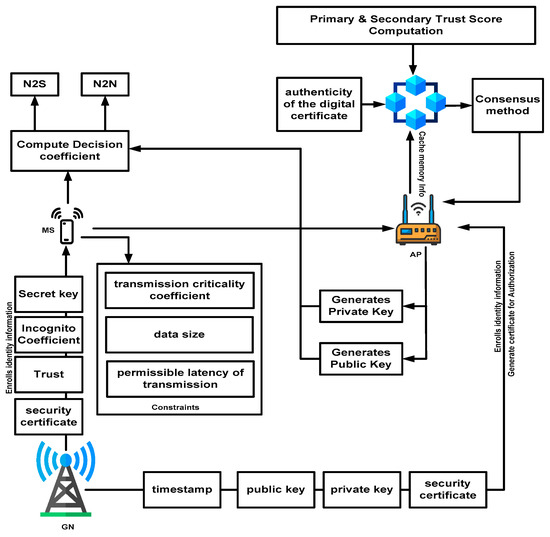
Figure 5.
High-level diagram of the proposed framework.
5. Results
The previous section discussed the methodology adopted for implementing the proposed study agenda. The proposed method targets cost-effective resource optimization for sensory devices operating in a mobility-based environment. Furthermore, the Ethereum blockchain was introduced to secure the participation of sensors and safeguard the transacted information among mobile sensors. Unlike existing blockchain approaches, the proposed model retains an equilibrium between the security and communication of the sensor devices in a mobile environment. Hence, a well-planned assessment strategy is required to test the effectiveness of the proposed model. This section comprehensively discusses the assessment environment adopted and the results.
5.1. Assessment Environment
The proposed scheme was implemented in Python using a standard 64-bit Windows machine. The numerical data obtained from the analysis were subjected to MATLAB enriched with a data analytical toolbox for an extensive and dedicated study. As the proposed scheme must be benchmarked with the existing system, it is necessary to consider specific standard simulation parameters universally adopted in most existing approaches. The values of the simulation area, the quantity of mobile sensors, and its velocity, transmittance power, initialized energy, and energy to transmit data are chosen considering the frequently adopted research work discussed in Section 2. The channel capacities of MS, AP, and GN are selected based on conventional applications in WSNs. All the assigned values of the simulation parameters are highly flexible and can be easily amended based on particulars of applications. The details of the assessment environment concerning the simulation parameters are presented in Table 3.

Table 3.
Simulation parameters.
A specific dimension was considered for the simulation environment, which could be upscaled to fit any size of sensory application. The simulation area consisted of 500 users (or mobile sensors) with ten APs uniformly assigned within the simulation area, while two gateway nodes were appropriately positioned. The mobile sensors are randomly deployed within the simulation area, while the AP’s coverage and service extensibility are optimal for all the sensors near the AP. Every AP was further connected to two GNs, where the coverage was sufficient to encapsulate the APs within the simulation area. The transmission range of each AP was uniform at 200 m, whereas the transmission range of each GN was maintained at 600 m. Although the values are lower than the original values of commercially available APs and GNs, they provide a scope for understanding the communication performance in the model. Various permutations and combinations of the location of the AP and GN have been explored to find that there is only a 0.76–1.87% fluctuation in the overall outcome. The simulation can be executed until all 500 mobile sensors deplete the energy while 5000 bytes of the test data packet is used to evaluate the communication performance. The experiment was also extended to evaluate peak traffic conditions by randomly varying the number of mobile sensors. The outcomes accomplished under varied assessment environments showed a satisfactory level of consistency.
5.2. Accomplished Result
As discussed in the previous subsection, the final result is obtained after the complete saturation point of energy of all the sensors. The outcome of the proposed model is compared with some of the recently established works conducted by Alam et al. [28], Awan et al. [29], Ding et al. [37], Dong et al. [48], Feng et al. [38], Fu et al. [49], Hwaitat et al. [39], Lee et al. [43], Li et al. [44], Namane et al. [45], Pajooh et al. [46], and Thangaraj et al. [47]. The main reasons for comparing the existing approaches with the proposed study are as follows: (i) the stated approaches use blockchain for both resource management and accomplishing primary objectives of applications; (ii) the stated approaches also present some of the unique implementations towards lightweight security and efficient data transmission for all sensor-supported network environments; (iii) the stated approaches also present distinguished consensus methods of blockchain for secure storage of data in various large-scale and distributed environments; and (iv) the stated approaches have also been tested using varied ranges of attacks. The features stated show that the existing approaches are more suitable for a comparative analysis with the proposed scheme, thereby yielding a fair opportunity for assessment. However, the existing approaches have different implementation environments and environment use cases, posing a challenge in comparative analysis. Hence, a uniform testbed was constructed, where the core methods of blockchain, security features, and resource management of the existing approaches were compared with the proposed study model. Table 4 shows the numerical outcomes obtained when the proposed and existing studies were assessed using a common testbed and a standard performance metric. Although various studies have been implemented and discussed in Section 2 regarding IoT security and blockchains, they are yet to be tested in a dynamic environment. Hence, the prime novelty of the result accomplishment is associated with better performance towards data delivery services in IoT, along with minimal complexity involvement in the proposed scheme. Furthermore, benchmarking has been carried out extensively, considering multiple performance metrics concerning all major existing methods in IoT security.

Table 4.
Numerical outcomes of assessment.
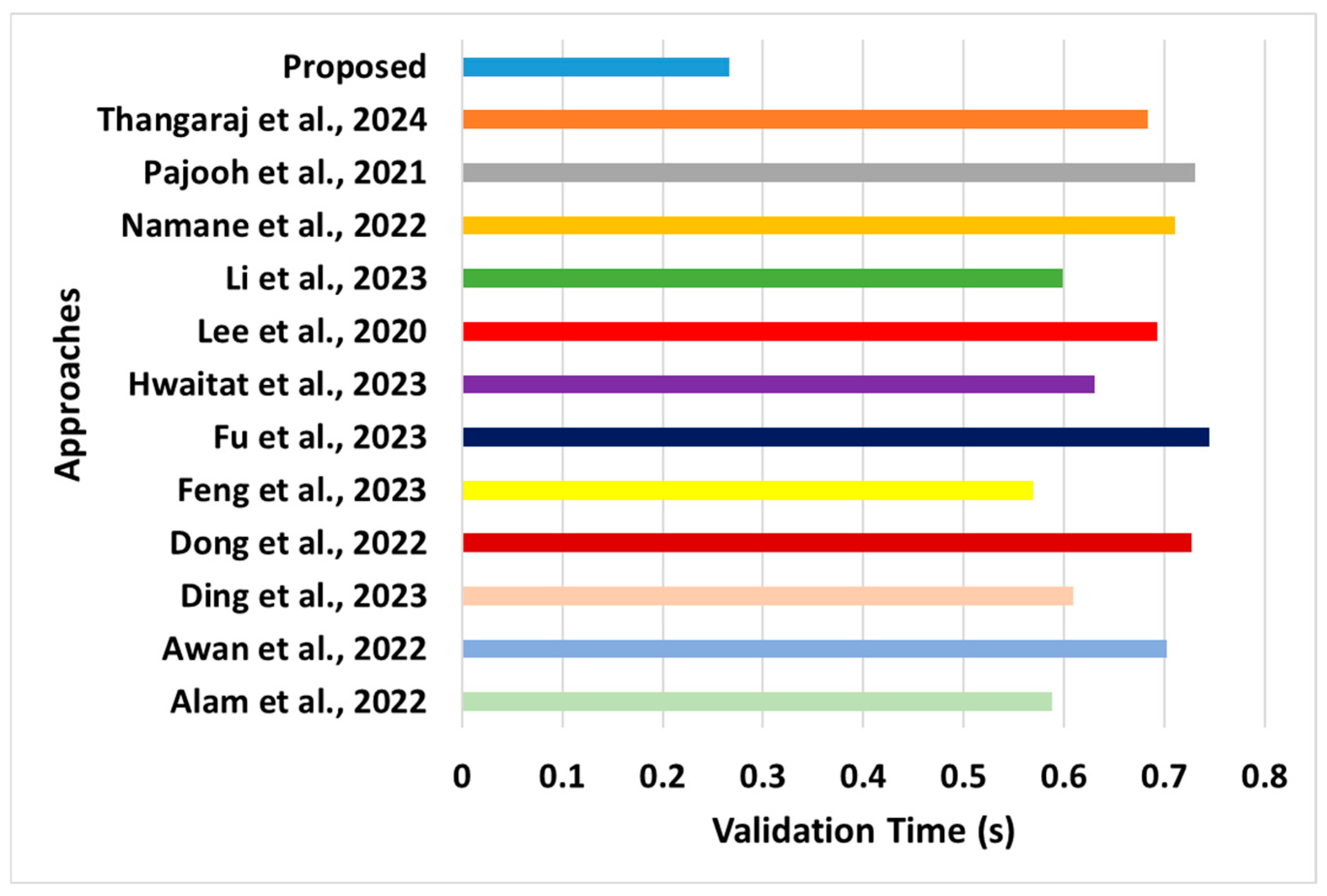
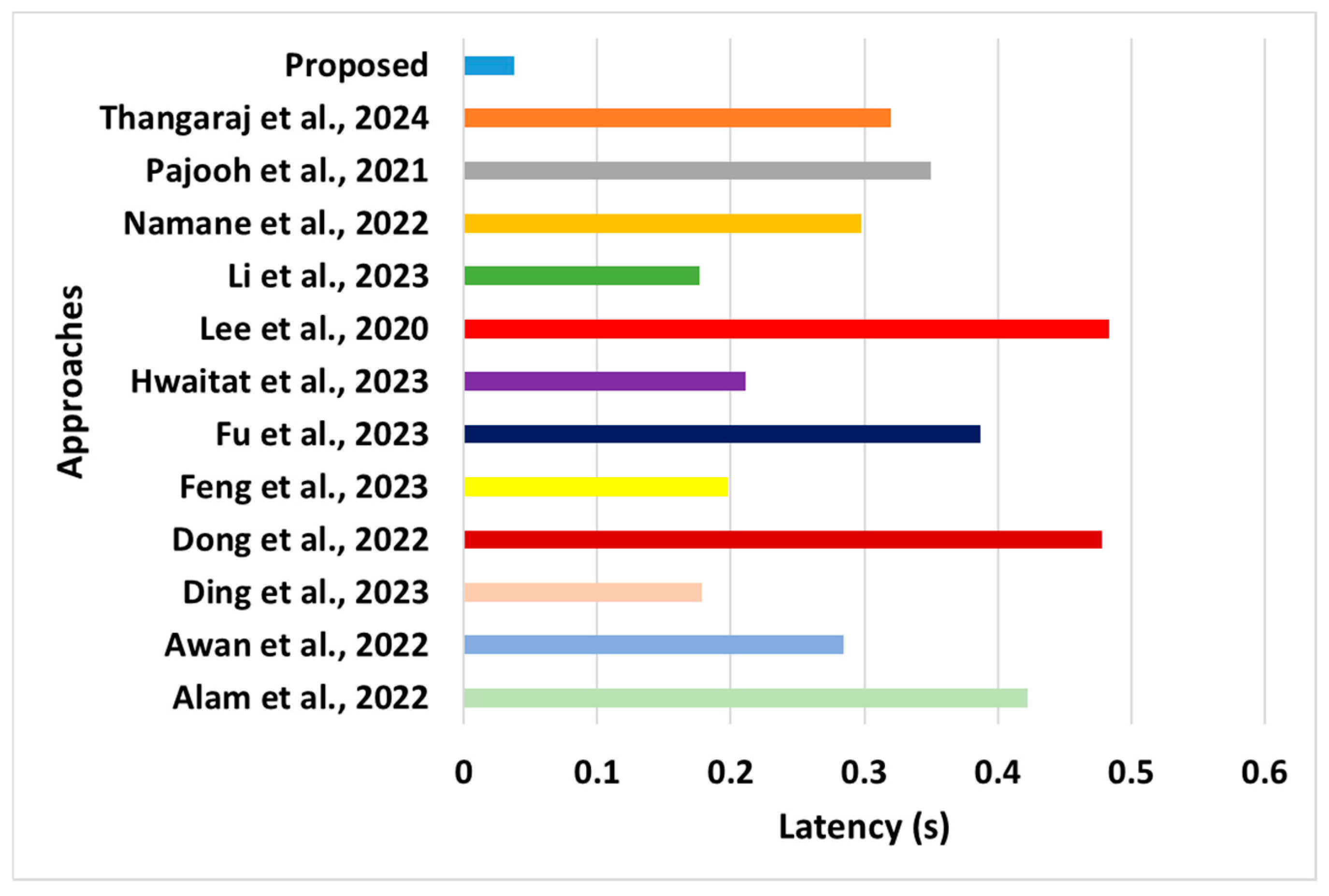
A simulation environment was subjected to various traffic loads and attack scenarios to assess the robustness and seamless communication capability of the proposed system. The proposed scheme considers the standard performance metrics of validation time, latency, throughput, overhead, cost, and processing time, as listed in Table 4. To simplify the learning outcome of the simulation study, the intermediate numerical values were averaged, and the final mean score was presented. The numerical and graphical outcomes (Figure 6, Figure 7, Figure 8, Figure 9, Figure 10 and Figure 11) exhibit better performance of the proposed model than the existing models.
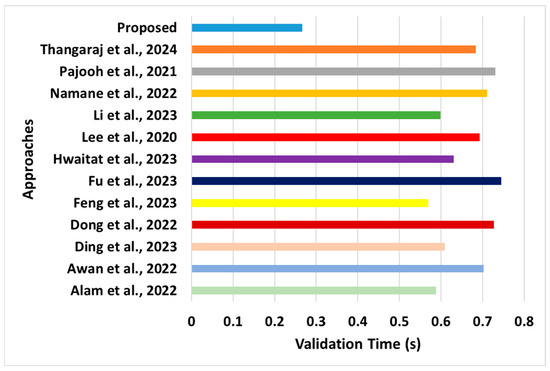
Figure 6.
Comparative assessment of validation time [28,29,37,38,39,43,44,45,46,47,48,49].
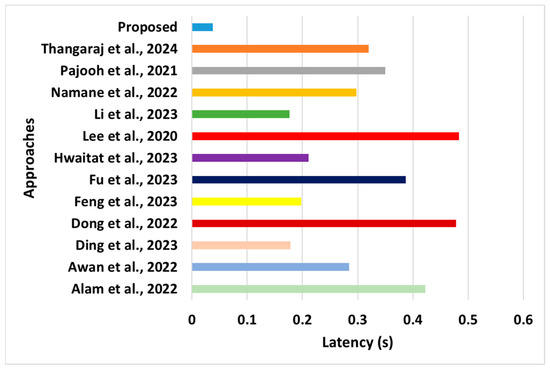
Figure 7.
Comparative assessment of latency [28,29,37,38,39,43,44,45,46,47,48,49].
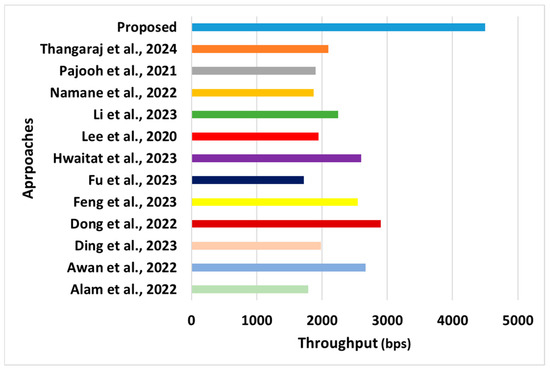
Figure 8.
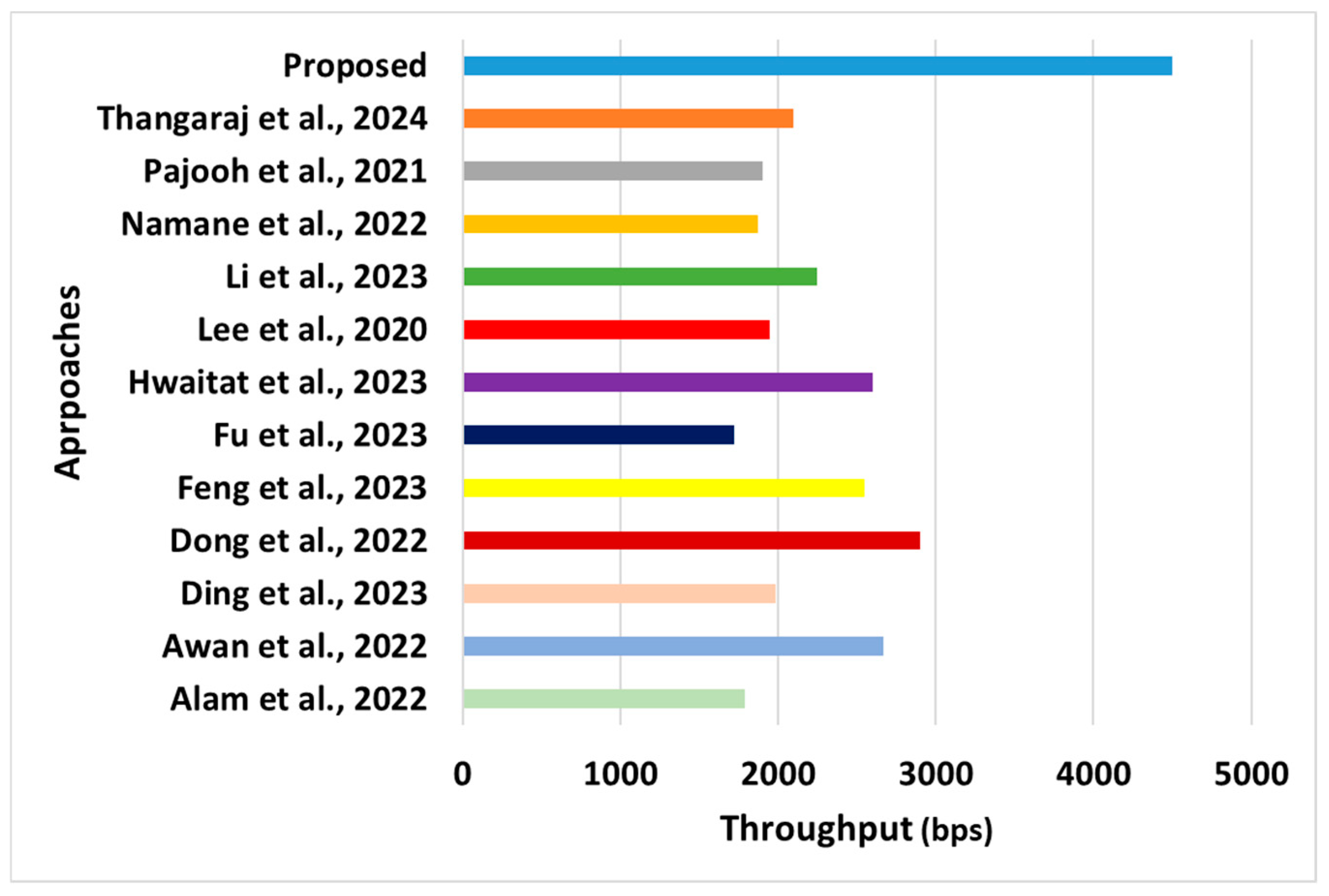
Comparative assessment of throughput [28,29,37,38,39,43,44,45,46,47,48,49].
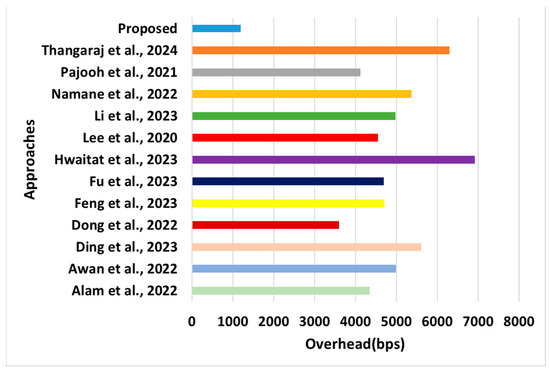
Figure 9.
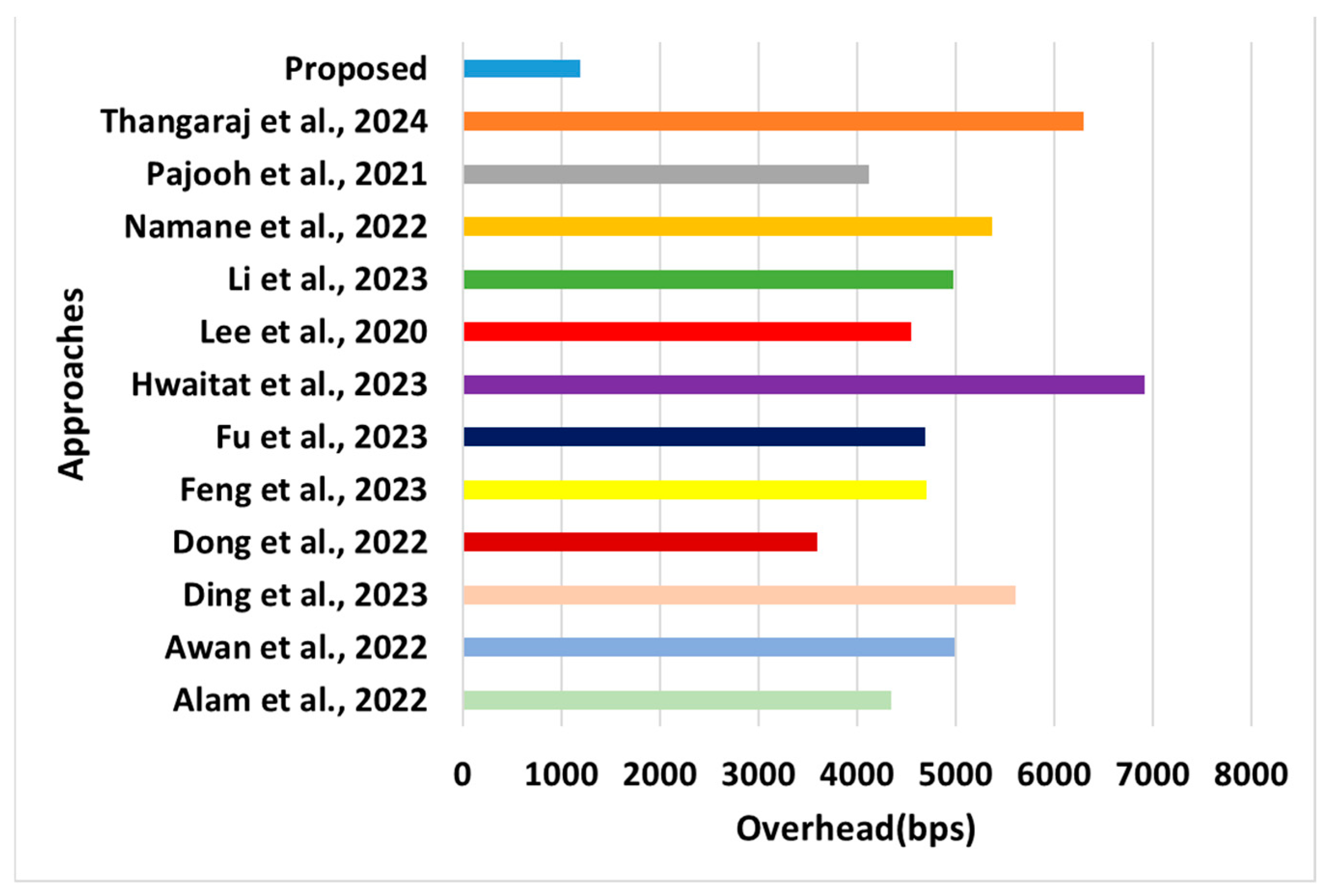
Comparative assessment of overhead [28,29,37,38,39,43,44,45,46,47,48,49].
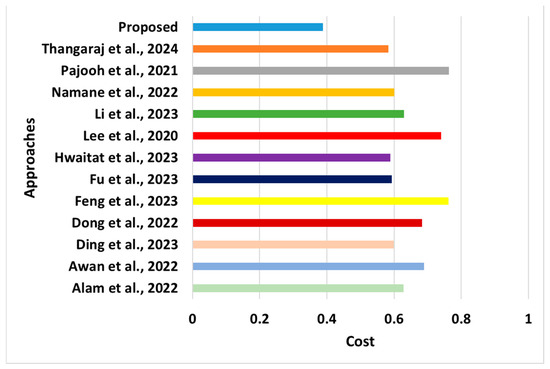
Figure 10.
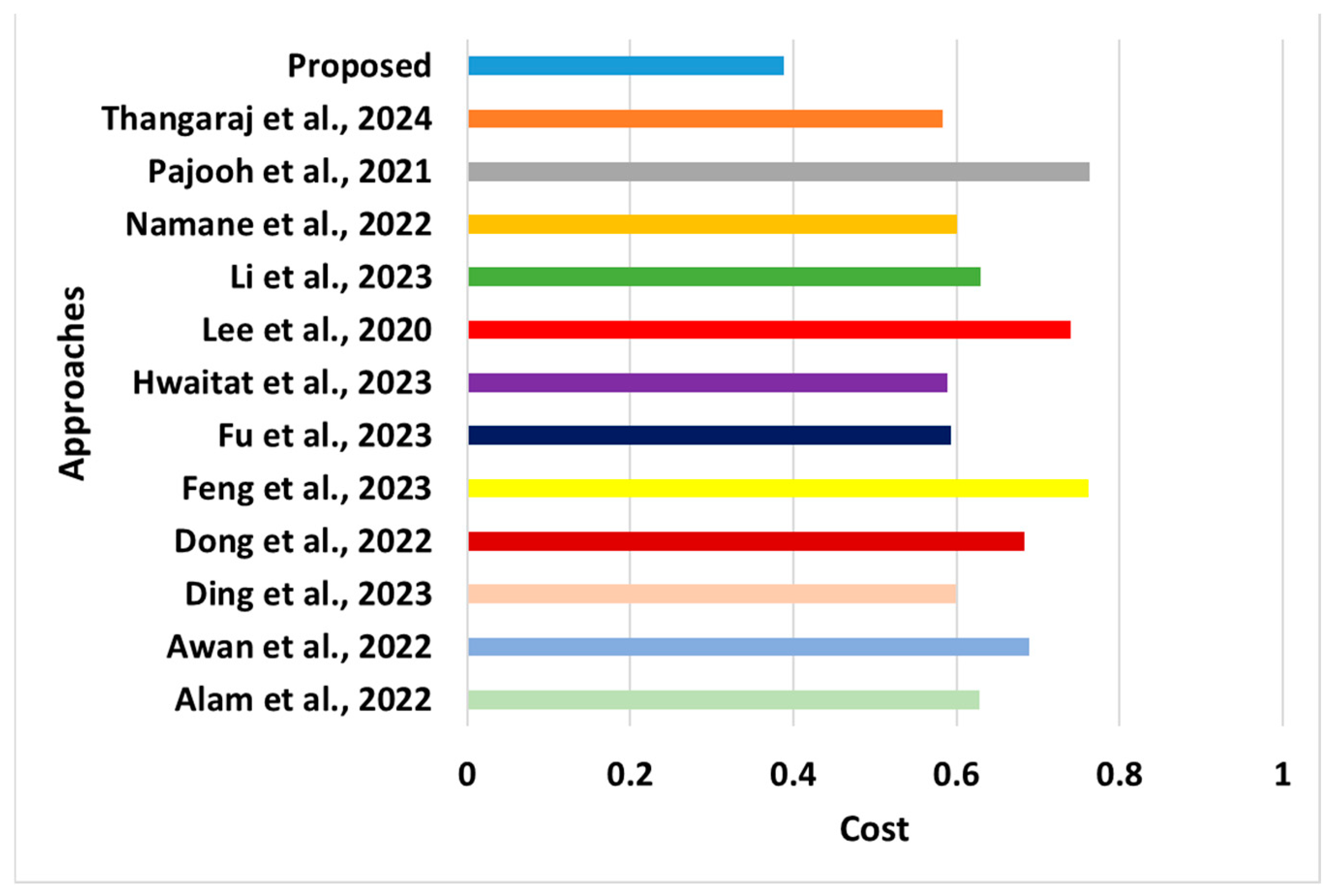
Comparative assessment of cost [28,29,37,38,39,43,44,45,46,47,48,49].
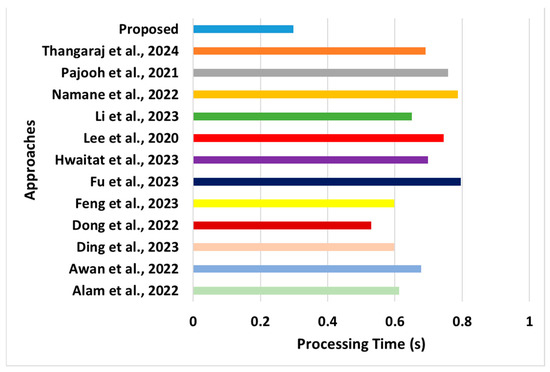
Figure 11.
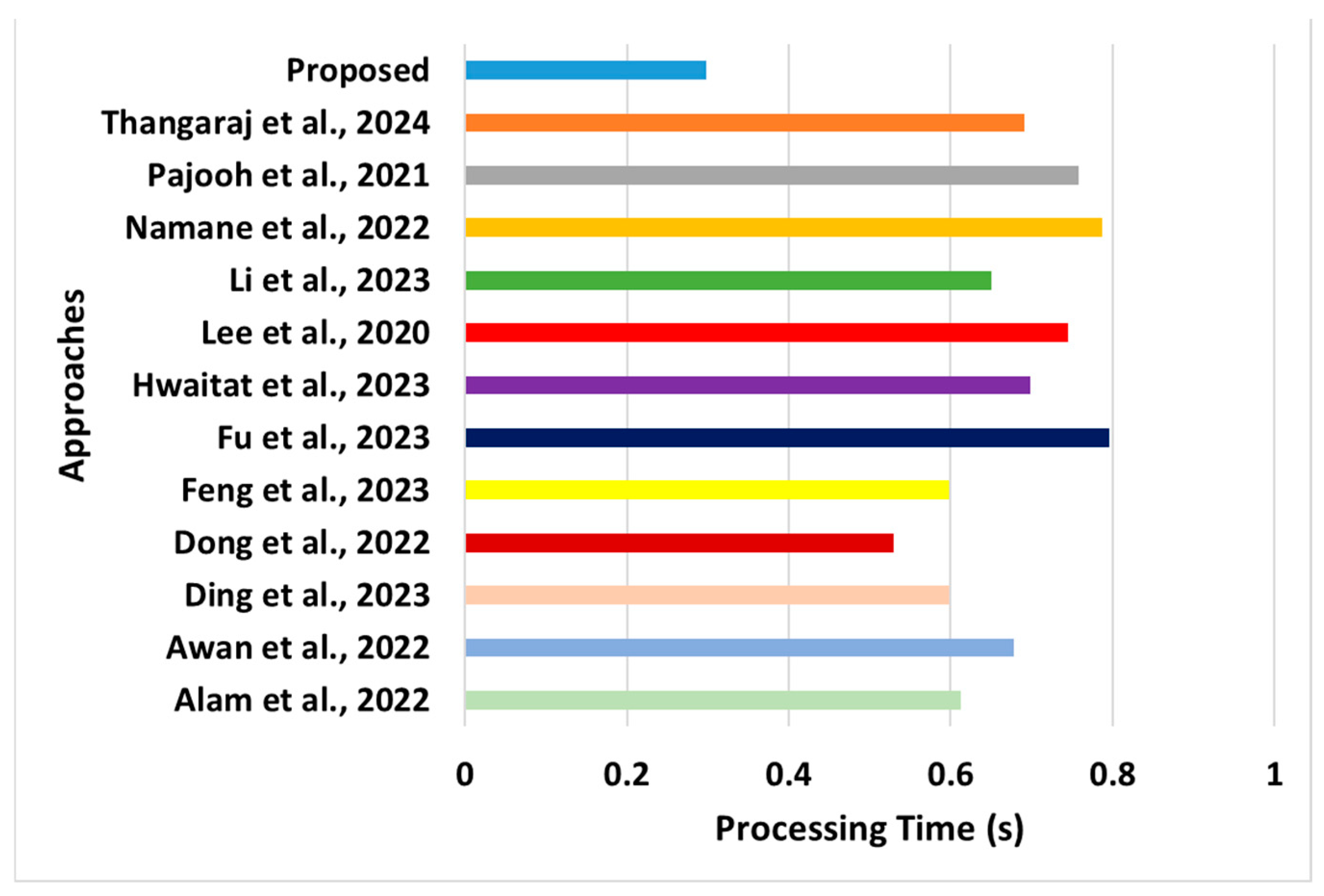
Comparative assessment of processing time [28,29,37,38,39,43,44,45,46,47,48,49].
This section illustrates the learning outcomes obtained from the numerical outcome in Table 4 and the respective graphical outcomes in Figure 6, Figure 7, Figure 8, Figure 9, Figure 10 and Figure 11. The discussion of each performance metric is as follows:
- Validation Time: This performance parameter represents the time required to validate the user’s request. This involves enrolling users, validating their identities, and computing the trust score. The aim is to determine the capability of the proposed system in terms of its responsiveness to process multiple requests from concurrent users in peak traffic situations. The outcome presented in Figure 6 eventually showed a faster validation time. The learning outcomes of this performance metric are as follows:
- °
- Novelty: The main novelty of this analysis is that the proposed system does not use any form of complex encryption (apart from hashing during validation of the sensor’s identity) to offer a faster validation time. This is not witnessed in existing approaches (Namane et al. [45], Li et al. [44], Lee et al. [43], and Hwaitat et al. [39]), where a complex form of encryption method was applied. This is unlikely in the majority of the existing approaches to blockchain. The secondary novelty of the analysis is associated with a simplified consensus method that allows the AP to interchange roles based on three entities (follower, auxiliary, and leader). The consensus methods in existing approaches perform quite a more extensive set of operations without defining the precise role of sensors, leading to increased validation times. Hence, the processing of such a consensus is faster and can accurately map the dynamic state of the network to facilitate an appropriate security action. Therefore, the proposed system is anticipated to exhibit faster responsiveness when exposed to real-time scenarios based on an extensive analysis of various traffic loads.
- °
- Evidential Justification: The existing approaches show that the implementation strategy is more inclined toward blockchain design than normalizing the communication model or enrollment process. For example, the validation times for Dong et al. [48] and Fu et al. [49] are expected to increase because of their dependency on the iterative training operation. Although these schemes can offer better security results, their validation times increase with an increase in the number of sensors and traffic. Similarly, approaches presented by Pajooh et al. [46] use big data approaches that can effectively offer better data quality towards effective resource management; however, the complex structure could easily offer sub-optimal scalability performance in the presence of a complex form of request or a higher amount of concurrent request processing. The approaches of Namane et al. [45], Li et al. [44], Lee et al. [43], and Hwaitat et al. [39] offer extensive encryption usage, which eventually increases the validation time. However, in contrast to existing schemes, the proposed model provides a novel synchronized design between the enrollment process and trust score calculation in the presence of both direct and indirect communication. This implies that the proposed scheme is capable of faster trust calculation without much dependency on the complexities of traffic or topological changes. Furthermore, the inclusion of state-based attributes in trust estimation assists in further considering all optimal possibilities of resource usage while performing data transmission between communicating mobile sensors. The lack of such inclusion in the design aspect of existing approaches proves the novel outcome generated by the proposed scheme.
- °
- Quantified Outcome: The proposed system offers an approximately 40% reduced validation time compared to the average validation time of existing blockchain-based approaches.
- Latency: This performance parameter is responsible for computing the latency between the transmitting and receiving nodes and involves processing the AP and GN during either the N2N or N2S mode of communication. The outcome shown in the previous section (Figure 7) exhibited a reduced latency in the proposed model. The learning outcomes of this part of the analysis are as follows:
- °
- Novelty: The primary novelty of this outcome is that the proposed scheme assigns channel capacity in the sequential form of mobile user demands. Such progressive allocation of resources has yet to be witnessed in the existing approaches discussed in the literature (Alam et al. [28], Feng et al. [38], Hwaitat et al. [39], and Thangaraj [47]). Simultaneously, the latency attribute is used to determine the cardinality of the allocated resources. This contributes to a progressive reduction in latency, even under peak traffic conditions. The secondary novelty of this outcome is that the proposed scheme can minimize the latency by adhering to the constraints considered while formulating the objective functions. This will eventually mean that the proposed modeling approach complies with the constraints to be satisfied by the objective function, leading to a greater likelihood of being functional over the real-time traffic of the sensor network. Hence, the reduced latency does not degrade the proposed system’s data quality or transmission rate, which must be addressed in existing related studies.
- °
- Evidential Justification: The proposed system completes the task related to data transmission within permissible latency, pl, by adopting optimal resources. Furthermore, the proposed model can perform both N2N and N2S concurrently, thereby contributing towards minimizing the latency, while the objective function constructed is compliant with the latency reduction phenomenon. However, this is different from the existing approaches. For example, the work of Alam et al. [28] has an extensive trust computation overlooking the latency demands of various tasks to resist varied forms of attack. Such a discrete form of task requirement was not considered. Other studies, such as Feng et al. [38], Hwaitat et al. [39], and Thangaraj [47], are characterized by various forms of internal operations related to the computation of security attributes. Although this complements blockchain security, it introduces significant latency when exposed to a highly distributed sensing environment. Similar trends have been reported in other studies.
- °
- Quantified Outcome: The proposed system offers approximately 28% reduced latency compared to the average latency of existing blockchain approaches.
- Throughput: This performance metric refers to the rate at which data are successfully transmitted from the source to the destination mobile sensor within the network (Figure 8). It measures the data transmitted over a network within a specified period. Throughput is influenced by various factors such as network topology, routing protocols, transmission power, interference, and data traffic patterns.
- °
- Novelty: The primary novelty of the proposed system is that it offers an unbiased balance between communication and optimal security performance. The choice of consensus method, as well as block size, has a potential influence on the throughput of WSNs. A closer look at the proposed scheme shows that the adopted consensus method used in the proposed scheme retains information about the computed trust scores from mobile sensors, where the consensus consists of reviewing requests from mobile sensors, forwarding of leader nodes, the response of mobile sensors, and replies made by the leader node. This offers a clear and precise voting process in adverse conditions (traffic or attack), leading to optimal throughput gains. This is a novel approach, whereas existing schemes use a stale consensus mechanism that could be more challenging to fine-tune when exposed to dynamic environments (especially in mobility). Hence, the proposed scheme will perform optimally towards resource management and data transmission when exposed to any form of adverse and challenging real-time environment with hardware constraints.
- °
- Evidential Justification: In the dynamic use case of a sensory application with mobility, where nodes typically have limited resources, such as battery power and processing capability, achieving high throughput while conserving energy is a crucial challenge. Efficient routing algorithms and protocols are often employed to optimize throughput and prolong the network’s lifetime. The proposed scheme contributes towards adjusting the transmission power of sensor nodes to help maximize the communication range and reduce interference, leading to better throughput. The mobile sensors can dynamically change their transmission power based on the distance to the destination and signal strength. The proposed scheme uses multiple channels to mitigate interference and improve the network throughput. Finally, implementing QoS mechanisms allows the network to prioritize certain types of traffic based on their importance and urgency. By allocating resources efficiently and ensuring the timely delivery of critical data, QoS mechanisms can enhance the throughput in WSNs. However, none of the existing approaches [38,39,40,41,42,43,44,45,46,47] use sophisticated operations that are mainly witnessed to adopt any such process and hence witnessed with reduced throughput.
- °
- Quantified Outcome: The proposed system achieved an enhanced throughput of approximately 23% compared with existing approaches.
- Overhead: This performance metric refers to any additional data or control information transmitted or required beyond the actual payload data (Figure 9). This information is necessary for network management, communication protocols, error detection and correction, and other administrative purposes. Overhead can significantly impact the network’s performance and efficiency, as it consumes bandwidth, energy, and computational resources. The proposed system computes the control overhead among the various types of overhead. Control messages are used for synchronization, neighbor discovery, channel allocation, and other management functions within the network. These messages help maintain the integrity and reliability of the communication process but add overhead to the data transmission.
- °
- Novelty: A closer look at the overhead outcome shows that it is much better, even in contrast to the other previously assessed performance metrics in the proposed analysis. This is because of the novel features introduced in the proposed system associated with the redistribution and reassignment of resources. When any mobile sensor is assigned a surplus resource, the surplus resources are autonomously assigned to other needy mobile users, which is not observed in the existing approaches [38,39,40,41,42,43,44,45,46,47]. This phenomenon leads to a fair redistribution of resources, reducing the possibilities of fluctuating network size, network density, and a higher degree of topology changes.
- °
- Evidential Justification: In densely populated simulation areas, the control overhead increases because of the significant number of neighboring nodes and the frequency of route discovery and maintenance messages. Sparse networks may have lower control overhead but may suffer from longer route establishment times. This problem is addressed in the proposed system by adopting a network model based on a novel cost modeling that controls the network’s density. This characteristic is not observed in existing approaches [38,39,40,41,42,43,44,45,46,47], which have the least control over overhead increments. In addition, dynamic network conditions, such as node mobility or failures, can trigger frequent topology changes, leading to an increased control overhead. The proposed system is a network model that can adapt to these changes by updating the data dissemination information and recalculating paths, thereby contributing to reduced control message transmission. Furthermore, in the existing system, the transmission range of the sensor nodes affects the frequency of neighbor discovery and synchronization messages. Nodes within range of each other must exchange control messages to establish and maintain links, leading to a higher control overhead in networks with more extensive transmission ranges. It is also deemed that the existing approaches [38,39,40,41,42,43,44,45,46,47] use stringent QoS requirements and may require more frequent control message exchanges to maintain the desired performance levels, leading to a higher control overhead.
- °
- Quantified Outcome: The proposed system contributes to an overhead reduction of approximately 38% compared with existing approaches.
- Cost: This is another significant performance metric for establishing a cost-effective model. The computation of this metric is carried out by considering all possible networks and computation-based resources used to transmit data successfully. The network resources include channel capacity, whereas computational resources include the assigned energy/power resources. The learning outcomes of this performance metric, as shown in Figure 10, are as follows:
- °
- Novelty: The core novelty of the proposed outcome is that it computes the cost following the user’s payment of the cost of using the services, unlike any reported schemes in the literature (e.g., Hwaitat et al. [39], Dong et al. [48], Awan et al. [29]). The novelty of this scheme is that when the saturation rate of the server resources is higher, the resource unit price will also be higher. This optimal cost prompts the user to select resources using N2N or N2S modes of communication. Hence, if the utilization of resources is higher, it can contribute towards minimizing the possibilities of bottleneck conditions in the network. Therefore, the proposed system contributes to both QoS and experience.
- °
- Evidential Justification: A closer look at existing approaches shows various dedicated efforts to comply with cost-effective outcomes. The cost-effectiveness of Hwaitat et al. [39] is associated with the optimal execution time of the blocks and multiparty signatures. Dong et al. [48] used machine learning to minimize costs, whereas Awan et al. [29] used blockchain to minimize operational costs. However, there is still a loophole in these cost computation processes, as these models can perform cost computations but cannot contribute to proactive cost reduction. This loophole is potentially addressed in the proposed system, where novel and distinct cost modeling is carried out that computes the cost over multiple scenarios and significantly reduces the cost.
- °
- Quantified Outcome: The proposed scheme offers an approximately 27% reduction in cost compared to existing approaches.
- Processing Time: The proposed system’s final performance parameter focuses on analyzing the models’ computational efficiency performance. This performance metric was computed by recording the overall time required by the model to start and finish its operations. The learning outcomes of the model, shown in Figure 11, are as follows:
- °
- Novelty: The proposed scheme offers a unique cost model in which one objective function complies with seven constraints to ensure optimal resource utilization. The compliance standard toward satisfying constraints is much higher than that of any existing approach (Alam et al. [28], Awan et al. [29], Ding et al. [37], Feng et al. [38]). The existing system must assess its adherence to a broader consideration of constraints. This scheme reduces operational costs and potential resistance to illegitimate activities within the network. Hence, the proposed scheme presents a proper equilibrium between secure blockchain operations and data transmission with optimal resource management. This phenomenon is suitable for supporting secure data transmission in WSNs or any large-scale distributed networks in the presence of mobility, considering emergencies and standard applications hosted on it.
- °
- Evidential Justification: Reducing the computational complexity of blockchains in sensor networks is crucial for ensuring scalability and efficiency. The proposed scheme uses a simplified consensus mechanism that minimizes the computational overhead. The proposed scheme also aggregates the sensor data at the edge before sending them to the blockchain at the AP. This reduces the volume of data transmitted and processed on the blockchain, lowering computational complexity. Finally, the proposed system uses a cache that frequently accesses the data or computation results to reduce redundant calculations. The scheme stores the previously computed results, avoiding recomputation when the same inputs occur again, thus decreasing the overall computational complexity and reducing the processing time. However, the processing time for existing systems (Alam et al. [28], Awan et al. [29], Ding et al. [37], Feng et al. [38]) uses complex forms of blockchain operations. Simultaneously, some existing approaches (e.g., Dong et al. [48], Fu et al. [49]) tend to use highly iterative internal operations towards accomplishing their security targets.
- °
- Quantified Outcome: The processing time of the proposed system was found to offer approximately 38% of the reduced score, in contrast to existing approaches.
Therefore, the novel and original results can be summarized as follows:
- Without adopting any complex cryptographic approach, unlike the frequently used methods in existing studies, the proposed scheme offers a significant reduction in validation time by 40% in dynamic scenarios. Hence, the supportability for scalable performance in the proposed blockchain is highly ensured for near-world services in IoT, unlike existing approaches.
- The latency performance is improved by 28% in the proposed system, which can be attributed to its mechanism to handle optimal resources right from the consensus mechanism until the final stage of assessing the constraint adherence of the model. This is an unconventionally novel outcome, as existing systems are mainly reported to undertake extensive internal security operations without any latency compensation schemes in dynamic environments.
- The data transmission performance was improved by a 23% increase in throughput and a 38% reduction in overhead. The prime novelty of this outcome is associated with the symmetric network dynamics of the proposed consensus methods that balance both resource demands and security demands, unlike methods reported in the literature with unfair resource distribution during the consensus mechanism.
- The presented scheme also offers a 27% reduction in cost along with a 38% faster responsiveness, proving this score as a high accomplishment to date in contrast to existing methods of blockchain operations.
6. Conclusions and Outlook
This paper presents a novel solution to address the challenges of adopting the Ethereum blockchain for resource management while strengthening security. Irrespective of including N2N and N2S communication modes, a novel consensus mechanism, and a cost model, the proposed scheme managed a streamlined balance among all the considered performance evaluation metrics. It maintains an optimal resource management performance with better consistency when increasing traffic load. The implemented scheme not only improves the security strength of the Ethereum blockchain but also successfully maintains optimal performance in data transmission and responsiveness. A resource-efficient mechanism using N2N and N2S communication modes with mobile sensors was presented in the proposed scheme to validate sensory devices in mobile sensors for network structures using the Ethereum blockchain, with computed trust scores further ascertaining the node authenticity. A cost model with a multi-objective function was proposed to reduce the cost of mobile sensors in data transmission tasks. Unlike existing blockchain approaches that use sophisticated encryption schemes, the proposed method employs a simplified finite field and hashing during sensor enrollment, thereby introducing a novel consensus mechanism in which an access point acts as a follower, auxiliary, and leader for better blockchain adaptability in dynamic sensor networks. Performance benchmarking shows that the proposed scheme reduces the validation time by 40%, latency by 28%, overhead by 38%, processing time by 38%, and cost by 27%, and improves throughput by 23%.
Future work will optimize this model by considering it as a baseline and incorporating preemptive measures to mitigate bottleneck conditions at variable resource saturation points for mobile nodes. Integrating the Ethereum blockchain with IoT platforms can provide a standardized framework for managing mobile sensor networks, enabling seamless interoperability between different sensor devices and facilitating data exchange and coordination to prevent congestion. Ethereum smart contracts can be programmed to manage mobile sensor resources efficiently, allocate bandwidth and processing power based on demand, and prioritize critical data transmissions to reduce bottleneck conditions. Additionally, using Ethereum’s native cryptocurrency, Ether, for micropayments and incentives can encourage mobile sensors to cooperate in lowering bottleneck conditions by rewarding them for relaying data, providing computational resources, or adopting energy-saving behaviors.
Author Contributions
Conceptualization, methodology, and validation: B.U.I.K., K.W.G., A.R.K. and M.F.Z.; formal analysis and investigation: K.W.G., M.F.Z. and M.C.; writing—original draft preparation: B.U.I.K., K.W.G., M.C. and A.R.K.; writing—review and editing: B.U.I.K., M.C. and M.F.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Deanship of Scientific Research, Vice Presidency for Graduate Studies and Scientific Research, King Faisal University, Saudi Arabia, under Project Grant KFU241720.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
The authors express their appreciation for Bisma Rasool’s effort in proofreading and editing the paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Suyatna, I.P.; Mohamed, Y.H.; Abbas, M.S.; Ismail, A.F.; Magiman, M.M.; Yunus, Y. The Emergence and Challenges of Blockchain Technology in Business and IoT Applications. In Proceedings of the 2023 3rd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 12–13 May 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- Anwar, F.; Khan, B.U.I.; Kiah, L.B.M.; Abdullah, N.A.; Goh, K.W. A Comprehensive Insight into Blockchain Technology: Past Development, Present Impact and Future Considerations. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 878–890. [Google Scholar] [CrossRef]
- Khan, B.U.I.; Goh, K.W.; Mir, M.S.; Mohd Rosely, N.F.L.; Mir, A.A.; Chaimanee, M. Blockchain-Enhanced Sensor-as-a-Service (SEaaS) in IoT: Leveraging Blockchain for Efficient and Secure Sensing Data Transactions. Information 2024, 15, 212. [Google Scholar] [CrossRef]
- Xu, D.; Gao, Y.; Xiao, X. Precision Poverty Alleviation Methods in the Agricultural Field Based Upon Wireless Communication Networks and Blockchain. Wirel. Commun. Mob. Comput. 2022, 2022, 2687445. [Google Scholar] [CrossRef]
- Leelakrishnan, S.; Chakrapani, A. Power Optimization in Wireless Sensor Network Using VLSI Technique on FPGA Platform. Neural Process. Lett. 2024, 56, 125. [Google Scholar] [CrossRef]
- Abidoye, A.P.; Kabaso, B. Energy-Efficient Hierarchical Routing in Wireless Sensor Networks Based on Fog Computing. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 8. [Google Scholar] [CrossRef]
- Liang, D.; Shen, H.; Chen, L. Maximum Target Coverage Problem in Mobile Wireless Sensor Networks. Sensors 2020, 21, 184. [Google Scholar] [CrossRef]
- Ullah, A.; Khan, F.S.; Mohy-ud-din, Z.; Hassany, N.; Gul, J.Z.; Khan, M.; Kim, W.Y.; Park, Y.C.; Rehman, M.M. A Hybrid Approach for Energy Consumption and Improvement in Sensor Network Lifespan in Wireless Sensor Networks. Sensors 2024, 24, 1353. [Google Scholar] [CrossRef]
- Haq, M.Z.U.; Khan, M.Z.; Rehman, H.U.; Mehmood, G.; Binmahfoudh, A.; Krichen, M.; Alroobaea, R. An Adaptive Topology Management Scheme to Maintain Network Connectivity in Wireless Sensor Networks. Sensors 2022, 22, 2855. [Google Scholar] [CrossRef]
- Vellaichamy, J.; Basheer, S.; Bai, P.S.M.; Khan, M.; Kumar Mathivanan, S.; Jayagopal, P.; Babu, J.C. Wireless Sensor Networks Based on Multi-Criteria Clustering and Optimal Bio-Inspired Algorithm for Energy-Efficient Routing. Appl. Sci. 2023, 13, 2801. [Google Scholar] [CrossRef]
- Erskine, S.K. Secure Data Aggregation Using Authentication and Authorization for Privacy Preservation in Wireless Sensor Networks. Sensors 2024, 24, 2090. [Google Scholar] [CrossRef]
- Biswas, K.; Chowdhury, M.J.M.; Usman, M. Blockchain of Things: Benefits, Challenges and Future Directions. Sensors 2024, 24, 934. [Google Scholar] [CrossRef]
- Nazir, H.; Fan, J. Revolutionizing Retail: Examining the Influence of Blockchain-Enabled IoT Capabilities on Sustainable Firm Performance. Sustainability 2024, 16, 3534. [Google Scholar] [CrossRef]
- Alam, T. Blockchain-Based Internet of Things: Review, Current Trends, Applications, and Future Challenges. Computers 2022, 12, 6. [Google Scholar] [CrossRef]
- Manzoor, R.; Sahay, B.S.; Singh, S.K. Blockchain Technology in Supply Chain Management: An Organizational Theoretic Overview and Research Agenda. Ann. Oper. Res. 2022. [Google Scholar] [CrossRef]
- Singh, K.; Singha, N. Credit-Based Energy Trading System Using Blockchain and Machine Learning. J. Supercomput. 2024, 80, 15386–15407. [Google Scholar] [CrossRef]
- Kumar, B.C.G.; Harsha, K.G.; Mahesh, G.; Shukla, V.; Talari, S. BBIWMS: A Secure Blockchain-Based Framework for Integrated Water Management System for Smart City. In Cryptology and Network Security with Machine Learning; Springer Nature Singapore: Singapore, 2024; pp. 157–168. ISBN 9789819922284. [Google Scholar]
- Sambare, S.S.; Khandait, K.; Kolage, K.; Kolambe, K.; Nimbalkar, T. Literature Review on Waste Management Using Blockchain. In Proceedings of International Conference on Data Science and Applications; Springer Nature Singapore: Singapore, 2023; pp. 495–510. ISBN 9789811966309. [Google Scholar]
- Chiaraluce, G.; Bentivoglio, D.; Finco, A.; Fiore, M.; Contò, F.; Galati, A. Exploring the Role of Blockchain Technology in Modern High-Value Food Supply Chains: Global Trends and Future Research Directions. Agric. Food Econ. 2024, 12, 6. [Google Scholar] [CrossRef]
- Calvão, F.; Archer, M. Digital Extraction: Blockchain Traceability in Mineral Supply Chains. Polit. Geogr. 2021, 87, 102381. [Google Scholar] [CrossRef]
- Petracci, R.; Culmone, R.; Mostarda, L. Blockchain Application for Fish Origin Certification. In Advances on Broad-Band and Wireless Computing, Communication and Applications; Springer Nature Switzerland: Cham, Switzerland, 2024; pp. 149–158. ISBN 9783031467837. [Google Scholar]
- Zhu, G.; He, D.; An, H.; Luo, M.; Peng, C. The Governance Technology for Blockchain Systems: A Survey. Front. Comput. Sci. 2024, 18, 182813. [Google Scholar] [CrossRef]
- Buttar, A.M.; Shahid, M.A.; Arshad, M.N.; Akbar, M.A. Decentralized Identity Management Using Blockchain Technology: Challenges and Solutions. In Blockchain Transformations; Springer Nature Switzerland: Cham, Switzerland, 2024; pp. 131–166. ISBN 9783031495922. [Google Scholar]
- Upadrista, V.; Nazir, S.; Tianfield, H. Secure Data Sharing with Blockchain for Remote Health Monitoring Applications: A Review. J. Reliab. Intell. Environ. 2023, 9, 349–368. [Google Scholar] [CrossRef]
- Altulyan, M.; Yao, L.; Kanhere, S.; Huang, C. A Blockchain Framework Data Integrity Enhanced Recommender System. Comput. Intell. 2023, 39, 104–120. [Google Scholar] [CrossRef]
- Tian, Y.; Lu, Z.; Adriaens, P.; Minchin, R.E.; Caithness, A.; Woo, J. Finance Infrastructure through Blockchain-Based Tokenization. Front. Eng. Manag. 2020, 7, 485–499. [Google Scholar] [CrossRef]
- Sober, M.; Scaffino, G.; Schulte, S.; Kanhere, S.S. A Blockchain-Based IoT Data Marketplace. Clust. Comput. 2023, 26, 3523–3545. [Google Scholar] [CrossRef]
- Alam, S.; Zardari, S.; Shamsi, J.A. Blockchain-Based Trust and Reputation Management in SIoT. Electronics 2022, 11, 3871. [Google Scholar] [CrossRef]
- Awan, S.; Javaid, N.; Ullah, S.; Khan, A.U.; Qamar, A.M.; Choi, J.-G. Blockchain Based Secure Routing and Trust Management in Wireless Sensor Networks. Sensors 2022, 22, 411. [Google Scholar] [CrossRef] [PubMed]
- Liang, Y.-C. Blockchain for Dynamic Spectrum Management. In Dynamic Spectrum Management; Springer Singapore: Singapore, 2020; pp. 121–146. ISBN 9789811507755. [Google Scholar]
- Latif, R.; Yakubu, B.M.; Saba, T. MarketTrust: Blockchain-Based Trust Evaluation Model for SIoT-Based Smart Marketplaces. Sci. Rep. 2023, 13, 11571. [Google Scholar] [CrossRef]
- Al-Rakhami, M.S.; Al-Mashari, M. A Blockchain-Based Trust Model for the Internet of Things Supply Chain Management. Sensors 2021, 21, 1759. [Google Scholar] [CrossRef]
- Arshad, Q.-U.-A.; Khan, W.Z.; Azam, F.; Khan, M.K.; Yu, H.; Zikria, Y.B. Blockchain-Based Decentralized Trust Management in IoT: Systems, Requirements and Challenges. Complex Intell. Syst. 2023, 9, 6155–6176. [Google Scholar] [CrossRef]
- Bellaj, B.; Ouaddah, A.; Bertin, E.; Crespi, N.; Mezrioui, A.; Bellaj, K. BTrust: A New Blockchain-Based Trust Management Protocol for Resource Sharing. J. Netw. Syst. Manag. 2022, 30, 64. [Google Scholar] [CrossRef]
- Masmoudi, M.; Zayani, C.A.; Amous, I.; Sèdes, F. A New Blockchain-Based Trust Management Model. Procedia Comput. Sci. 2021, 192, 1081–1091. [Google Scholar] [CrossRef]
- Javaid, N. A Secure and Efficient Trust Model for Wireless Sensor IoTs Using Blockchain. IEEE Access 2022, 10, 4568–4579. [Google Scholar] [CrossRef]
- Ding, J.; Han, L.; Li, J.; Zhang, D. Resource Allocation Strategy for Blockchain-Enabled NOMA-Based MEC Networks. J. Cloud Comput. Adv. Syst. Appl. 2023, 12, 142. [Google Scholar] [CrossRef]
- Feng, Y.; Zhong, Z.; Sun, X.; Wang, L.; Lu, Y.; Zhu, Y. Blockchain Enabled Zero Trust Based Authentication Scheme for Railway Communication Networks. J. Cloud Comput. Adv. Syst. Appl. 2023, 12, 62. [Google Scholar] [CrossRef]
- Al Hwaitat, A.K.; Almaiah, M.A.; Ali, A.; Al-Otaibi, S.; Shishakly, R.; Lutfi, A.; Alrawad, M. A New Blockchain-Based Authentication Framework for Secure IoT Networks. Electronics 2023, 12, 3618. [Google Scholar] [CrossRef]
- Amjad, S.; Abbas, S.; Abubaker, Z.; Alsharif, M.H.; Jahid, A.; Javaid, N. Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things. Sensors 2022, 22, 1972. [Google Scholar] [CrossRef] [PubMed]
- Dwivedi, S.K.; Amin, R.; Vollala, S. Design of Secured Blockchain Based Decentralized Authentication Protocol for Sensor Networks with Auditing and Accountability. Comput. Commun. 2023, 197, 124–140. [Google Scholar] [CrossRef]
- Chen, Y.; Yang, X.; Li, T.; Ren, Y.; Long, Y. A Blockchain-Empowered Authentication Scheme for Worm Detection in Wireless Sensor Network. Digit. Commun. Netw. 2022, 10, 265–272. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A Blockchain-Based Smart Home Gateway Architecture for Preventing Data Forgery. Hum.-centric Comput. Inf. Sci. 2020, 10, 9. [Google Scholar] [CrossRef]
- Li, C.; Chen, Q.; Chen, M.; Su, Z.; Ding, Y.; Lan, D.; Taherkordi, A. Blockchain Enabled Task Offloading Based on Edge Cooperation in the Digital Twin Vehicular Edge Network. J. Cloud Comput. Adv. Syst. Appl. 2023, 12, 120. [Google Scholar] [CrossRef]
- Namane, S.; Ben Dhaou, I. Blockchain-Based Access Control Techniques for IoT Applications. Electronics 2022, 11, 2225. [Google Scholar] [CrossRef]
- Honar Pajooh, H.; Rashid, M.A.; Alam, F.; Demidenko, S. IoT Big Data Provenance Scheme Using Blockchain on Hadoop Ecosystem. J. Big Data 2021, 8, 114. [Google Scholar] [CrossRef]
- Thangaraj, V.; Raja Sree, T. MSCO: Mobility-Aware Secure Computation Offloading in Blockchain-Enabled Fog Computing Environments. J. Cloud Comput. Adv. Syst. Appl. 2024, 13, 88. [Google Scholar] [CrossRef]
- Dong, Z.; Liang, W.; Liang, Y.; Gao, W.; Lu, Y. Blockchained Supply Chain Management Based on IoT Tracking and Machine Learning. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 127. [Google Scholar] [CrossRef] [PubMed]
- Fu, X.; Peng, R.; Yuan, W.; Ding, T.; Zhang, Z.; Yu, P.; Kadoch, M. Federated Learning-Based Resource Management with Blockchain Trust Assurance in Smart IoT. Electronics 2023, 12, 1034. [Google Scholar] [CrossRef]
- Rathod, T.; Jadav, N.K.; Tanwar, S.; Polkowski, Z.; Yamsani, N.; Sharma, R.; Alqahtani, F.; Gafar, A. AI and Blockchain-Based Secure Data Dissemination Architecture for IoT-Enabled Critical Infrastructure. Sensors 2023, 23, 8928. [Google Scholar] [CrossRef] [PubMed]
- Charles, V.; Emrouznejad, A.; Gherman, T. A Critical Analysis of the Integration of Blockchain and Artificial Intelligence for Supply Chain. Ann. Oper. Res. 2023, 327, 7–47. [Google Scholar] [CrossRef]
- Farooq, M.S.; Khan, S.; Rehman, A.; Abbas, S.; Khan, M.A.; Hwang, S.O. Blockchain-Based Smart Home Networks Security Empowered with Fused Machine Learning. Sensors 2022, 22, 4522. [Google Scholar] [CrossRef]
- Ismail, S.; Nouman, M.; Dawoud, D.W.; Reza, H. Towards a Lightweight Security Framework Using Blockchain and Machine Learning. Blockchain Res. Appl. 2024, 5, 100174. [Google Scholar] [CrossRef]
- Faheem, M.; Raza, B.; Bhutta, M.S.; Madni, S.H.H. A blockchain-based resilient and secure framework for events monitoring and control in distributed renewable energy systems. IET Blockchainpage 2024, 1–15. [Google Scholar] [CrossRef]
- Gaur, A.K.; Valan, J.A. Impact of Security in Blockchain Based Real Time Applications. In Computational Intelligence in Pattern Recognition; Springer Nature Singapore: Singapore, 2022; pp. 193–200. ISBN 9789811930881. [Google Scholar]
- Fu, W.; Wei, X.; Tong, S. An Improved Blockchain Consensus Algorithm Based on Raft. Arab. J. Sci. Eng. 2021, 46, 8137–8149. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).