In this section, general properties of cyclic matrices and circulant matrices are introduced first. Then, we discuss the construction of the isotropic subgroup from the proposed modified circulant matrix, and then the calculation for an entanglement group is given. As a consequence, the parameters for EAQECC are obtained.
3.3. Construction of Parity Check Matrices of EAQECC Based on Modified Circulant Matrices
From the combination of circulant matrices and the left-circulant matrices, the parity check matrix that corresponds to isotropic subgroup have been formed in Theorem 2, then the anti-commuting subgroup are determined as logical operators of the parity check matrix as Theorem 3. Finally, the EAQECCs [[n, k, dmin; 1]] are found as the Corollary 1.
Theorem 2. For any two binary vectors u, v of size n, two circulant matrices are P1(u, n) and P2(v, n). Then, the parity-check matrix H = [HX | HZ], where HX and HZ correspond to P1(u, n) and P2(v, n), respectively, satisfies the SIP condition in (2).
Proof. From Definitions 3 and 4,
P1(
u,
n) and
P2(
v,
n) can be written as
where {
u1,
u2, …,
uk} and {
v1,
v2, …,
vk} are the positions of 1 at vectors
u and
v, respectively.
From the properties of circulant matrices, we get following equation for any 0 <
m,
l ≪ n:
In addition, any left-cyclic matrix is a symmetric matrix. So, the following equation is always true:
From (4), we get:
Therefore, the matrix
H = [
HX |
HZ] satisfies the SIP condition in (2), and Theorem 2 is proven. ☐
Since the parity-check matrices constructed from Theorem 2 satisfy the SIP condition in (2), we can choose the independent vectors from H to create corresponding isotropic subgroup SI. To have the entanglement subgroup, the following theorem can be considered to satisfy the conditions.
Theorem 3. Given that parity-check matrix H of size (n − k) × 2n and its vectors are an independent relationship, we can transform H into the standard form Hst in the following form: Then, the pairs of anti-commuting can be determined as
where the rank of matrix
XE and
ZE are
k.
Proof. - (1)
To transform the parity-check matrix to standard form, we use the Gauss-Jordan elimination, swap the qubits, and add one row to another. The codewords and stabilizer are invariant to these changes. So, step by step, the standard form can be obtained with (5).
- (2)
From the standard form,
Hst, we calculate the encoded Pauli operators
and
that satisfy the following conditions:
Consequently, encoded Pauli operators
and
can be used as
XE and
ZE. Theorem 3 is proven. ☐
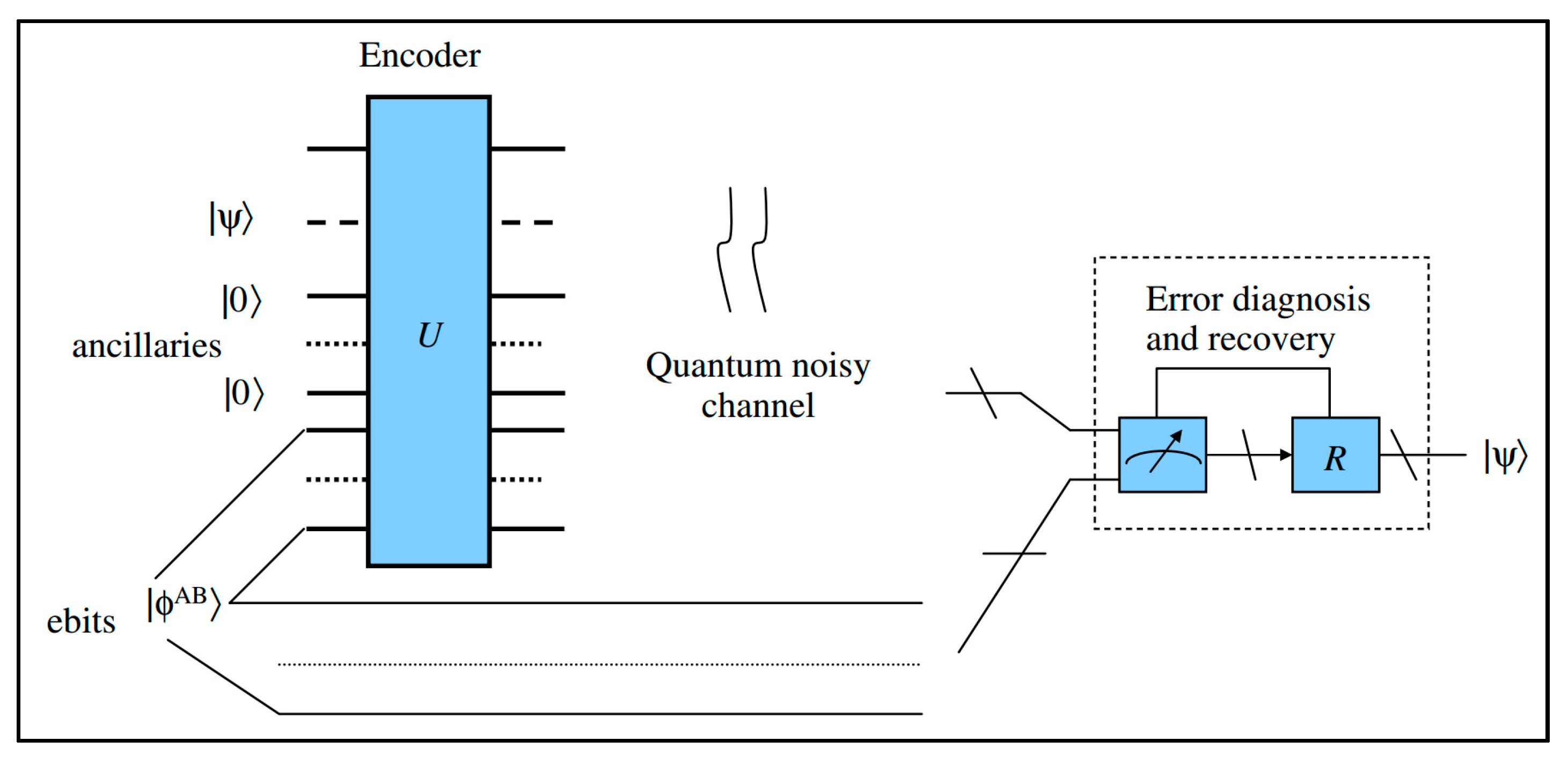
EAQECCs use pre-existing entanglement between transmitter and receiver to improve the reliability of transmission. Hence, before transmission we must manufacture the entanglement state between transmitter and receiver. It will be difficult to set up if the number of ebits becomes larger. So, an EAQECC design to minimize the numbers of ebits is an important constraint. In following Corollary, we will consider the result of the Theorem 2 when the number of ebits is 1.
Corollary 1. From the Theorem 3, firstly we choose one pair of anti-commuting from SE, it denotes as {X1, Z1}. Then, we choose n − k − 1 generators {Z2, Z3, …, Zn-k} from parity check matrix that satisfy the commutation property of isotropic sub-group SI. The minimum distance dmin is calculated from the generators of SE and SI. The EAQECCs with parameter [[n, k, dmin;1]] is constructed.
Proof.
As the definition of EAQECC in
Section 2.3, the non-Abelian group can be partitioned into:
a commuting subgroup, the isotropic group SI = {Zc+1, Zc+2, …, Zc+s}.
entanglement subgroup pairs SE = {Z1, Z2, …, Zc, X1, X2, …, Xc} with anti-commuting pairs; the anti-commuting pairs (Zi, Xi) being shared between source and receiver.
Then, from the isotropic and entanglement subgroup, EAQECC code
CEA are defined as [[
n,
k;
c]] that encodes
k =
n −
s −
c qubits into
n physical qubits with the help of
s =
n −
k −
c ancillas qubits and
c ebits shared between the sender and receiver. As the expectation to get the minimum distance, one entanglement pair is chosen, hence
c = 1, the operators are chosen above, the minimum distance is determined by the minimum weights of operators in the error set
N:
Finally, the parameter of EAQECC [[n, k, dmin;1]] are determined and the Corollary is proven. ☐
Following examples show the outputs of Corollary 1 where the minimum distance dmin ≥ 3, we search vectors which make codes with various minimum distance. Then, among many candidates of the vectors, to achieve largest minimum distance that has the error correctable ability the number of error t = ⎿(dmin − 1)/2⏌ ≥ 1 when the length of code up to 12.
Example 3. For n = 7, let us consider the EAQECC when u = [1 1 0 0 1 0 1] and v = [1 0 0 1 0 1 1]. We have a code with the minimum number of ebits and good minimum distance, as in the following explanations.
Per
Theorem 2, we have the corresponding parity-check matrix:
The six generators are chosen from the first six rows of matrix
H, which satisfy the independent condition to generate all elements of an inotropic subgroup. By using Gaussian elimination and interchanges of columns, matrix
H in (7) takes the standard form:
And the corresponding entanglement subgroup pair is calculated as:
Then, from vectors in (8) and (9) we have the generators for EAQECC as follows:
SE = {
X1,
Z1} and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6} where
The generators S = <SI, SE > correspond to EAQECC [[7,1,3;1]] that encodes one information qubit into seven physical qubits with the help of s = 6 ancilla qubits and only one pair entanglement -assisted ebit, and they can correct one error.
Example 4. For n = 9, let us consider the EAQECC where u = [0 1 1 0 0 1 0 0 1] and v = [1 1 0 0 1 0 0 1 0]. We have a code with the minimum number of ebits and good minimum distance, as in the following explanations.
From Theorem 2, we have the corresponding parity-check matrix:
The eight generators are chosen from the first eight rows of matrix
H, which satisfies the independent condition to generate all elements of an inotropic subgroup. By using Gaussian elimination and interchange of columns, matrix
H in (10) takes the standard form:
And the corresponding entanglement subgroup pair is calculated as:
Then, from vectors in (11) and (12), we have the generators for EAQECC as follows:
SE = {
X1,
Z1} and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8}, where
The generators S = < SI, SE > correspond to EAQECC [[9,1,3;1]] that encodes one information qubit into nine physical qubits with the help of s = 7 ancilla qubits and one pair entanglement -assisted ebit, and they can also correct one error.
Example 5. For n = 10, let us consider the EAQECC when u = [0 1 1 1 0 1 1 0 1 0] and v = [1 1 1 0 1 1 0 1 0 0]. We have a code with the minimum number of ebits and good minimum distance as in the following explanations.
Per Theorem 2, we have the corresponding parity-check matrix:
The nine rows of matrix
H satisfy the independent condition to generate all elements of an inotropic subgroup. By using Gaussian elimination and interchange of columns, matrix
H in (13) takes the standard form:
And the corresponding entanglement subgroup pair is calculated as:
a/ Then, from vectors in (14) and (15) we have the generators for EAQECC as follows:
SE = {
X1,
Z1} and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8,
Z9} where
The generators S = < SI, SE > correspond to EAQECC [[10,1,3;1]] that encodes one information qubit into 10 physical qubits with the help of s = 8 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
b/ When we calculate with
SE = {
X1,
Z1} where
and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8} where
The generator S = < SI, SE > correspond to EAQECC [[10,2,3;1]] that encodes two information qubits into 10 physical qubits with the help of s = 7 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
Example 6. For n = 11, let us consider the EAQECC when u = [1 1 1 0 0 1 1 0 0 0 1], v = [1 1 0 0 1 1 0 0 0 1 1]. We have a code with the minimum number of ebits and good minimum distance as in the following explanations.
Per Theorem 2, we have the corresponding parity-check matrix:
The ten rows of matrix
H satisfy the independent condition to generate all elements of an inotropic subgroup. By using Gaussian elimination and interchange of columns, matrix
H in (16) takes the standard form:
And the corresponding entanglement subgroup pair is calculated as:
a/ Then, from vectors in (14) and (15), we have the generators for EAQECC as follows:
SE = {
X1,
Z1} and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8,
Z9,
Z10} where
The generators S = < SI, SE > correspond to EAQECC [[11,1,4;1]] that encodes one information qubit into 11 physical qubits with the help of s = 9 ancilla qubits and only one entanglement-assisted ebit, and the minimum distance is four.
b/ When we calculate with
SE = {
X1,
Z1} where
and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8,
Z9} where
The generator S = < SI, SE > correspond to EAQECC [[11,2,3;1]] that encodes two information qubits into 11 physical qubits with the help of s = 8 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
c/ When we calculate with
SE = {
X1,
Z1} where
and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8} where
The generator S = <SI, SE > correspond to EAQECC [[11,3,3;1]] that encodes three information qubits into 11 physical qubits with the help of s = 7 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
d/ When we calculate with
SE = {
X1,
Z1} where
and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7} where
The generator S = <SI, SE > correspond to EAQECC [[11,4,3;1]] that encodes four information qubits into 11 physical qubits with the help of s = 6 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
Example 7. For n = 12, let us consider the EAQECC where u = [1 1 1 0 0 1 0 1 0 1 0 1], v = [1 1 0 0 1 0 1 0 1 0 1 1]. We have a code with the minimum number of ebits and good minimum distance, as in the following explanations.
Per Theorem 2, we have the corresponding parity-check matrix:
The eleven rows of matrix
H satisfy the independent condition to generate all elements of an inotropic subgroup. By using Gaussian elimination and interchange of columns, matrix
H in (19) takes the standard form:
And the corresponding entanglement subgroup pair is calculated as:
a/ Then, from vectors in (14) and (15) we have the generators for EAQECC as follows:
SE = {
X1,
Z1} and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8,
Z9,
Z10,
Z11} where
The generators S = <SI, SE > correspond to EAQECC [[12,1,4;1]] that encodes one information qubit into 12 physical qubits with the help of s = 10 ancilla qubits and only one pair entanglement -assisted ebit and the minimum distance is four.
b/ When we calculate with
SE = {
X1,
Z1} where
and
SI = {
Z2,
Z3,
Z4,
Z5,
Z6,
Z7,
Z8,
Z9,
Z10} where
The generator S = <SI, SE > correspond to EAQECC [[12,2,4;1]] that encodes two information qubits into 12 physical qubits with the help of s = 9 ancilla qubits and only one pair entanglement-assisted ebit, and they can correct one error.
The results of the proposed EAQECC with lengths up to 12 are listed in
Table 1. The detailed values of the operators are calculated in Examples 3–7.
In comparison with the results of referenced studies [
12,
13,
14,
15], the proposed EAQECC shows outperform as a smaller number of ebits and larger minimum distance. As the construction of EAQECC by generalized quadrangles in [
13] and circulant matrix in [
14], the two main things are clearly to conclude the advances of proposed methods that are code lengths and the classification of generators. Firstly, in [
13,
14], the code lengths are limited as the conditions to construct the parity check matrix, in contrast the proposed method can find the corresponding EAQECCs for any length. In addition, proposed codes are expressed as the standard form transformation to classify subgroups
SI and
SE; hence, the operators of subgroups are clearly determined, instead of knowing the numbers and operators not being determined, as seen in elsewhere, hence the minimum distance of outputs are not calculated in [
13,
14], furthermore the determined generators also open the effective way to implement the quantum system in future works. For more details, the comparisons are listed in
Table 2.