Coverage and Rate Analysis for Location-Aware Cross-Tier Cooperation in Two-Tier HetNets
Abstract
:1. Introduction
1.1. Related Work
1.2. Approach and Contributions
2. System Model
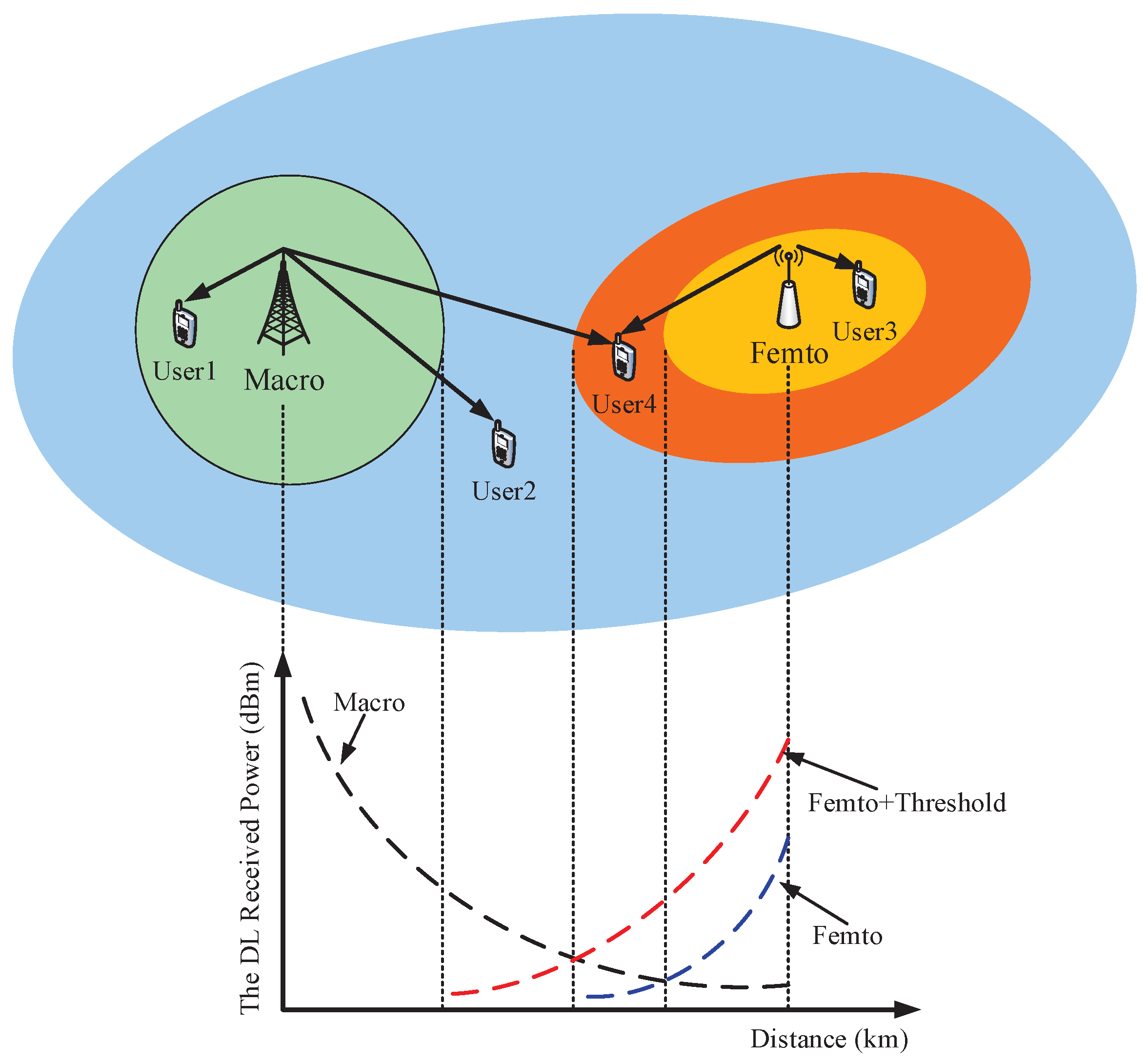
2.1. Two-Tier Heterogeneous Network Model
2.2. Location-Aware Cross-Tier Cooperation Scheme
2.3. The Signal-To-Interference-Plus-Noise Ratio for a Typical User
3. Analysis of the Coverage Probability and Average Rate
3.1. Statistical Distance to Serving Base Station
3.2. Coverage Probability
3.3. Average Rate
3.4. The Extension to the Multi-Tier Network
4. Numerical Results
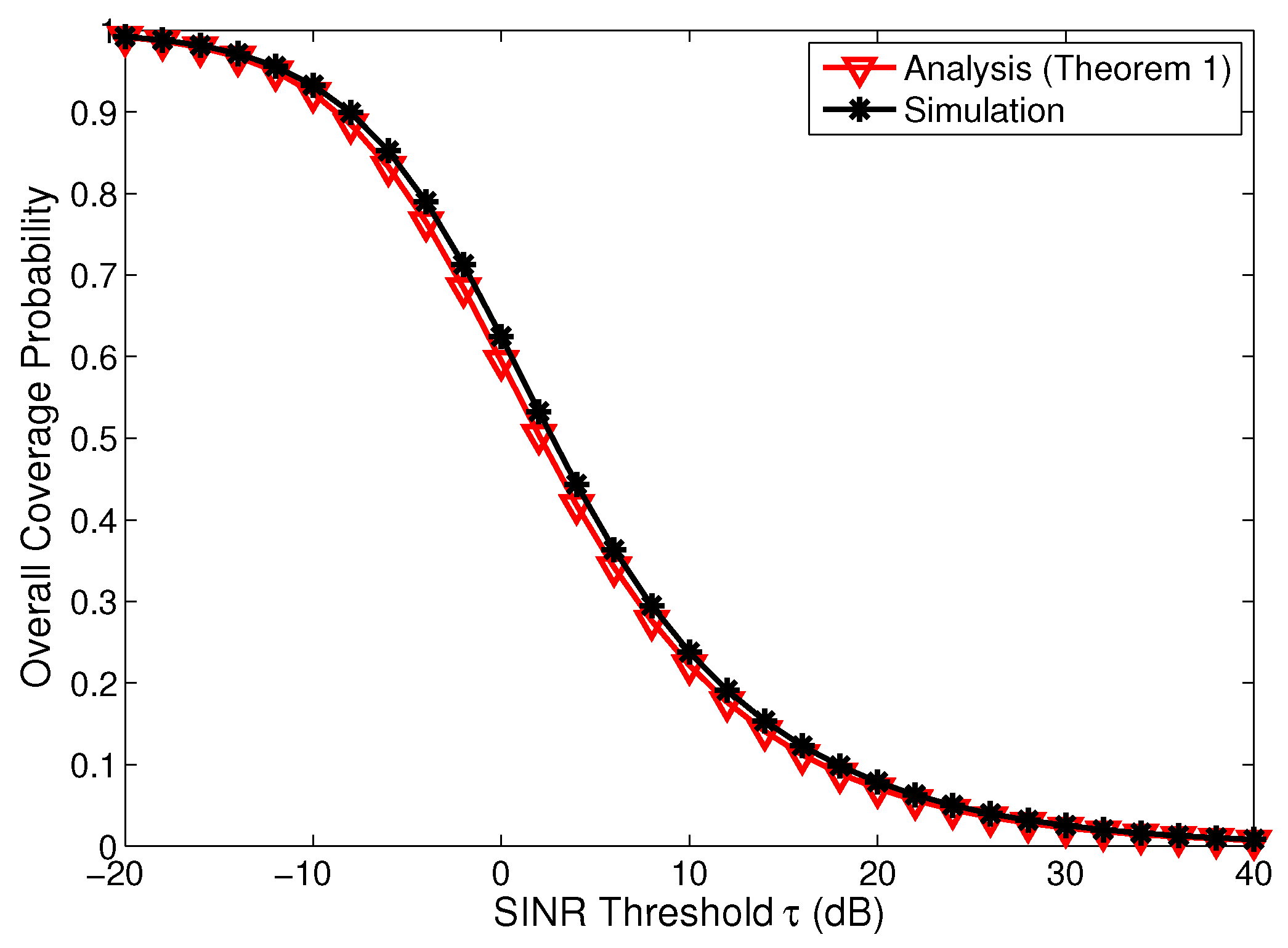
4.1. Validation of Analysis
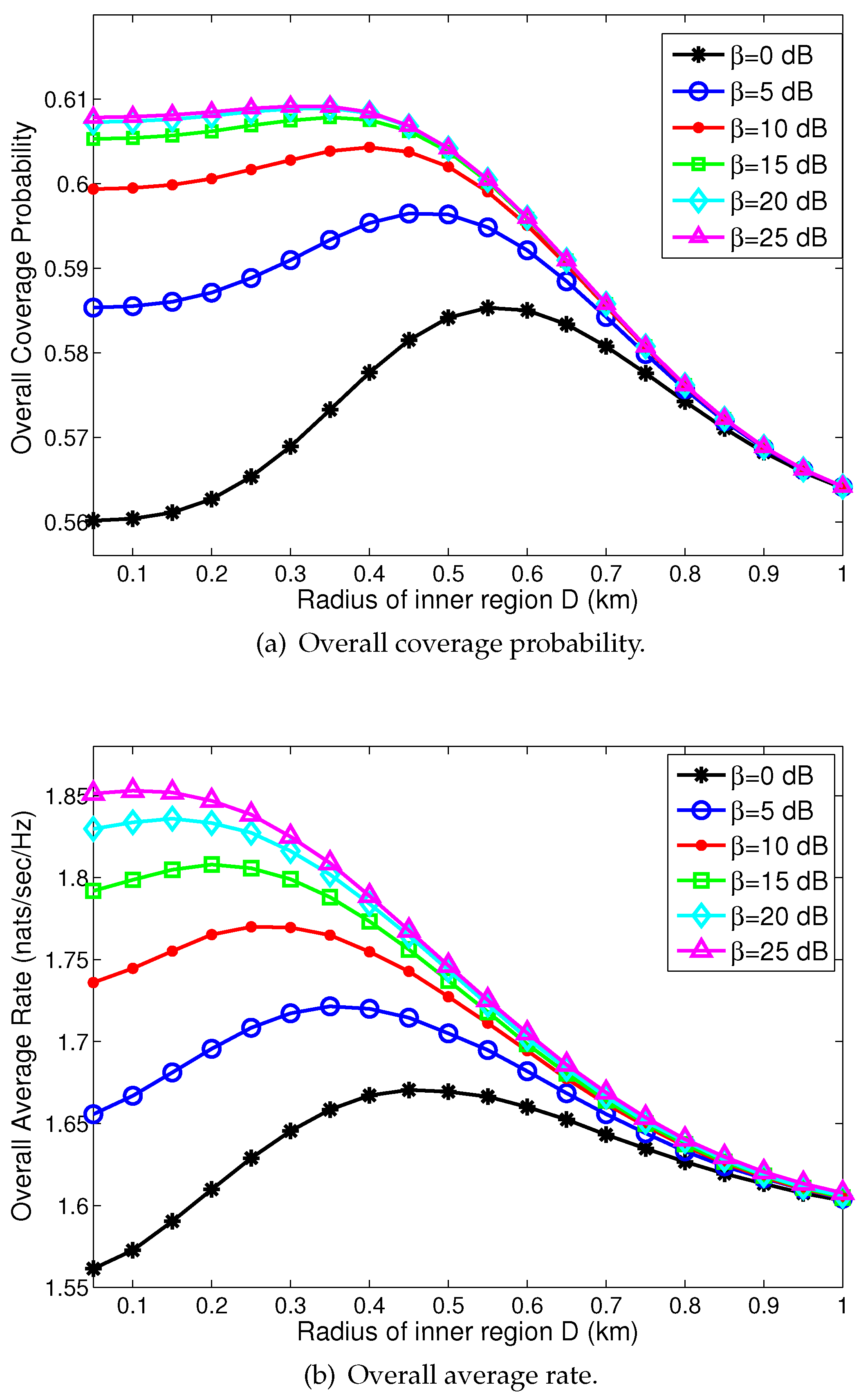
4.2. Performance Evaluation: Trends and Discussion
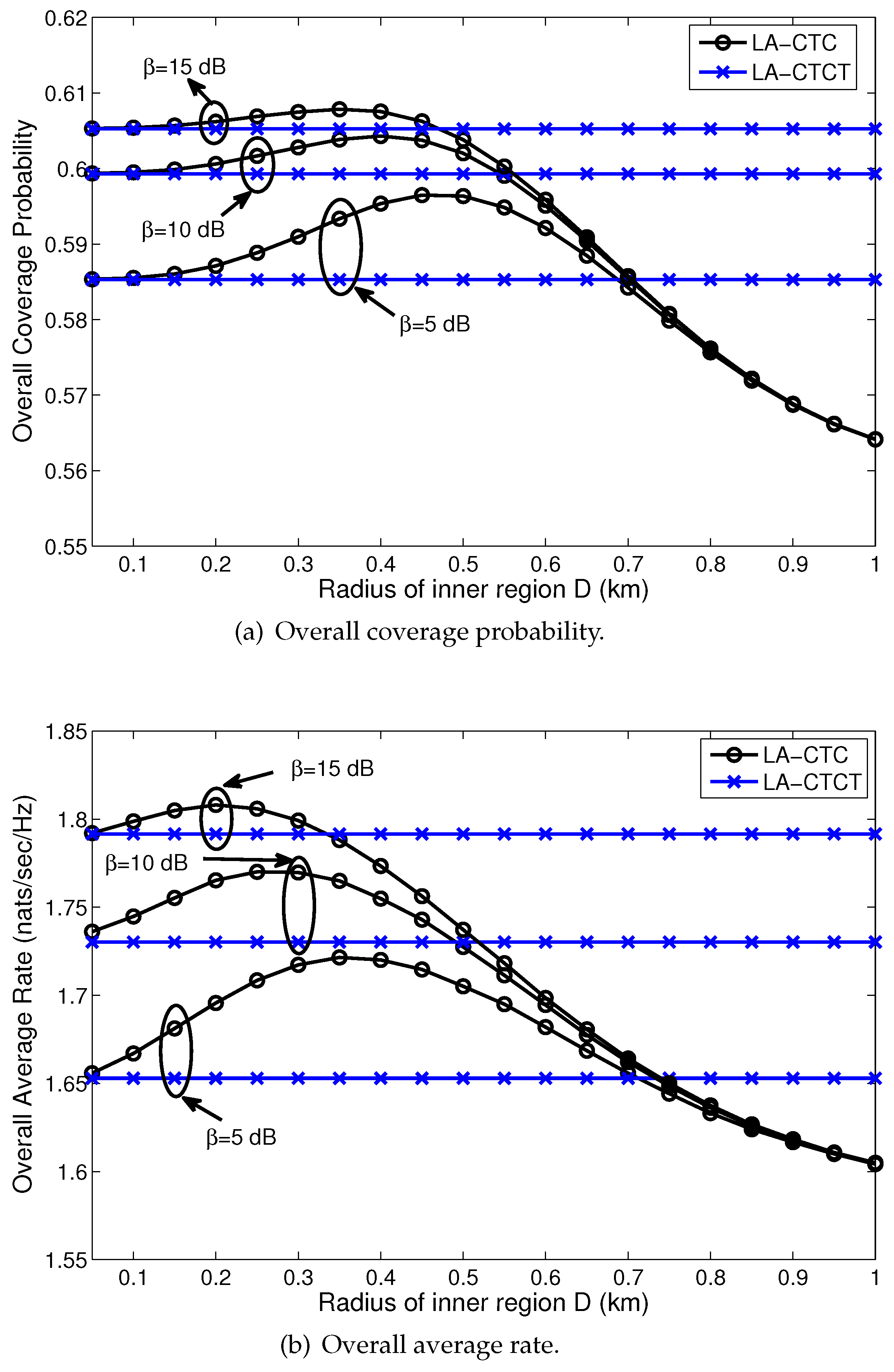
4.3. Performance Comparison with Other User Association Schemes
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A
Appendix B
Appendix C
Appendix D
Appendix E
References
- Andrews, J.G.; Buzzi, S.; Choi, W.; Stephen, V.H.; Lozano, A.; Soong Anthony, C.K.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Hossain, E.; Hasan, M. 5G cellular: Key enabling technologies and research challenges. IEEE Instrum. Meas. Mag. 2015, 18, 11–21. [Google Scholar] [CrossRef]
- Damnjanovic, A.; Montojo, J.; Wei, Y.; Ji, T.; Luo, T.; Vajapeyam, M.; Yoo, T.; Song, O.; Malladi, D. A survey on 3GPP heterogeneous networks. IEEE Wirel. Commun. 2011, 18, 11–21. [Google Scholar] [CrossRef]
- Liu, D.; Wang, L.; Chen, Y.; Elkashlan, M.; Wong, K.; Schober, R.; Hanzo, L. User association in 5G networks: A survey and an outlook. IEEE Commun. Surv. Tutor. 2016, 18, 1018–1044. [Google Scholar] [CrossRef]
- Kyocera. Potential performance of range expansion in macro-pico deployment (R1-104355). In Proceedings of the 3GPP TSG RAN WG1 Meeting-62, Madrid, Spain, 23–27 August 2010. [Google Scholar]
- Li, Q.; Hu, R.Q.; Qian, Y.; Wu, G. Cooperative communications for wireless networks: techniques and applications in LTE-advanced systems. IEEE Wirel. Commun. 2012, 19, 22–29. [Google Scholar]
- Gesbert, D.; Hanly, S.; Huang, H.; Shitz, S.S.; Simeone, O.; Yu, W. Multi-cell MIMO cooperative networks: A new look at interference. IEEE J. Sel. Areas Commun. 2010, 28, 1380–1408. [Google Scholar] [CrossRef]
- Irmer, R.; Droste, H.; Marsch, P.; Grieger, M.; Fettweis, G.; Brueck, S.; Mayer, H.P.; Thiele, L.; Jungnickel, V. Coordinated multipoint: Concepts, performance, and field trial results. IEEE Commun. Mag. 2011, 49, 102–111. [Google Scholar] [CrossRef]
- Lee, D.; Seo, H.; Clerckx, B.; Hardouin, E.; Mazzarese, D.; Nagata, S.; Sayana, K. Coordinated multipoint transmission and reception in LTE-advanced: Deployment scenarios and operational challenges. IEEE Commun. Mag. 2012, 50, 148–155. [Google Scholar] [CrossRef]
- Andrews, J.G.; Baccelli, F.; Ganti, R.K. A tractable approach to coverage and rate in cellular networks. IEEE Trans. Commun. 2011, 59, 3122–3134. [Google Scholar] [CrossRef]
- Dhillon, H.S.; Ganti, R.K.; Baccelli, F.; Andrews, J.G. Modeling and analysis of K-tier downlink heterogeneous cellular networks. IEEE J. Sel. Areas Commun. 2012, 30, 550–560. [Google Scholar] [CrossRef]
- Korrai, P.; Sen, D. Downlink SINR coverage and rate analysis with dual slope pathloss model in mmWave networks. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Vien, Q.-T.; Akinbote, T.; Nguyen, H.X.; Trestian, R.; Gemikonakli, O. On the coverage and power allocation for downlink in heterogeneous wireless cellular networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015. [Google Scholar]
- Jo, H.-S.; Sang, Y.J.; Xia, P.; Andrews, J.G. Heterogeneous cellular networks with flexible cell association: A comprehensive downlink SINR analysis. IEEE Trans. Wirel. Commun. 2012, 11, 3484–3495. [Google Scholar] [CrossRef]
- Singh, S.; Dhillon, H.S.; Andrews, J.G. Offloading in heterogeneous networks: Modeling, analysis, and design insights. IEEE Trans. Wirel. Commun. 2013, 12, 2484–2497. [Google Scholar] [CrossRef]
- Singh, S.; Zhang, X.; Andrews, J.G. Joint rate and SINR coverage analysis for decoupled uplink-downlink biased cell associations in hetNets. IEEE Trans. Wirel. Commun. 2015, 14, 5360–5373. [Google Scholar] [CrossRef]
- Novlan, T.D.; Ganti, R.k.; Ghosh, A.; Andrews, J.G. Analytical evaluation of fractional frequency reuse for OFDMA cellular networks. IEEE Trans. Wirel. Commun. 2011, 10, 4294–4305. [Google Scholar] [CrossRef]
- Novlan, T.D.; Ganti, R.K.; Ghosh, A.; Andrews, J.G. Analytical evaluation of fractional frequency reuse for heterogeneous cellular networks. IEEE Trans. Commun. 2012, 60, 2029–2039. [Google Scholar] [CrossRef]
- Nigam, G.; Minero, P.; Haenggi, M. Coordinated multipoint joint transmission in heterogeneous networks. IEEE Trans. Commun. 2014, 62, 4134–4146. [Google Scholar] [CrossRef]
- Xia, P.; Liu, C.-H.; Andrews, J.G. Downlink coordinated multipoint with overhead modeling in heterogeneous cellular networks. IEEE Trans. Wirel. Commun. 2013, 12, 4025–4037. [Google Scholar] [CrossRef]
- Baccelli, F.; Giovanidis, A. A stochastic geometry framework for analyzing pairwise-cooperative cellular networks. IEEE Trans. Wirel. Commun. 2015, 14, 794–808. [Google Scholar] [CrossRef]
- Tanbourgi, R.; Singh, S.; Andrews, J.G.; Jondral, F.K. A tractable model for non-coherent joint-transmission base station cooperation. IEEE Trans. Wirel. Commun. 2014, 13, 4959–4973. [Google Scholar] [CrossRef]
- Sakr, A.H.; Hossain, E. Location-aware cross-tier coordinated multipoint transmission in two-tier cellular networks. IEEE Trans. Wirel. Commun. 2014, 13, 6311–6325. [Google Scholar] [CrossRef]
- Lopez-Perez, D.; Guvenc, I.; De La Roche, G.; Kountouris, M.; Quek, T.Q.; Zhang, J. Enhanced intercell interference coordination challenges in heterogeneous networks. IEEE Wirel. Commun. 2011, 18, 22–31. [Google Scholar] [CrossRef]
- Singh, S.; Andrews, J.G. Joint resource partitioning and offloading in heterogeneous cellular networks. IEEE Trans. Wirel. Commun. 2014, 13, 888–901. [Google Scholar] [CrossRef]
- Dhungana, Y.; Tellambura, C. Multichannel analysis of cell range expansion and resource partitioning in two-tier heterogeneous cellular networks. IEEE Trans. Wirel. Commun. 2016, 15, 2394–2406. [Google Scholar] [CrossRef]
- Xie, B.; Zhang, Z.; Hu, R.Q.; Qian, Y. Spectral efficiency analysis in wireless heterogeneous networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016. [Google Scholar]
- Merwaday, A.; Mukherjee, S.; Guvenc, I. Capacity analysis of LTE-advanced HetNets with reduced power subframes and range expansion. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 189. [Google Scholar] [CrossRef]
- Khoriaty, J.; Artail, H. Coordinated multipoint in heterogeneous networks with overlapping microcell expanded regions. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, UAE, 19–21 Octomber 2015. [Google Scholar]
- Yang, K.; Zhang, J.; Zhang, X.; Wang, W. Edge aware cross-tier base station cooperation in heterogeneous wireless networks with non-uniformly-distributed nodes. IET Commun. 2016, 10, 1896–1903. [Google Scholar] [CrossRef]
- Wu, H.; Tao, X.; Xu, J.; Li, N. Coverage analysis for CoMP in two-tier HetNets with non-uniformly deployed femtocells. IEEE Commun. Lett. 2015, 19, 1600–1603. [Google Scholar] [CrossRef]
- Wang, H.; Zhou, X.; Reed, M.C. Coverage and throughput analysis with a non-uniform small cell deployment. IEEE Trans. Wirel. Commun. 2014, 13, 2047–2059. [Google Scholar] [CrossRef]
- Muhammad, F.; Abbas, Z.H.; Li, F.Y. Cell association with load balancing in non-uniform heterogeneous cellular networks: coverage probability and rate analysis. IEEE Trans. Veh. Technol. 2016, 99, 1–15. [Google Scholar]
- Muhammad, M.P.; Abbas, Z.H.; Muhammad, F.; Jiao, L. Location-based coverage and capacity analysis of a two tier HetNet. IET Commun. 2017, 11, 1067–1073. [Google Scholar]
- Dahlman, E.; Parkvall, S.; Skold, J.; Beming, P. 3G Evolution: HSPA and LTE for Mobile Broadband, 2nd ed.; Elsevier: Amsterdam, The Netherlands, 2008. [Google Scholar]
- Pantisano, P.; Bennis, M.; Saad, W.; Debbah, M.; Latva-aho, M. On the impact of heterogeneous backhauls on coordinated multipoint transmission in femtocell networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012. [Google Scholar]
- Arshad, R.; Elsawy, H.; Sorour, S.; Y.Al-Naffouri, T.; Alouini, M.-S. Handover management in 5G and beyond: A topology aware skipping approach. IEEE Access. 2016, 4, 9073–9081. [Google Scholar] [CrossRef]
- Milocco, H.R.; Boumerdassi, S. Estimation and prediction for tracking trajectories in cellular networks using the recursive prediction error method. In Proceedings of the 2010 IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks (WoWMoM), Montrreal, QC, Canada, 14–17 June 2010. [Google Scholar]
- Leontiadis, I.; Lima, A.; Kwak, H.; Stanojevic, R.; Wetherall, D.; Papagiannaki, K. From cells to streets: Estimating mobile paths with cellular-side data. In Proceedings of the The 10th ACM International on Conference on emerging Networking Experiments and Technologies, Sydney, Australia, 2–5 December 2014. [Google Scholar]
- Arshad, R.; Elsawy, H.; Sorour, S.; Y.Al-Naffouri, T.; Alouini, M.-S. Velocity-aware handover management in two-tier cellular networks. IEEE Trans. Wirel. Commun. 2017, 16, 1851–1867. [Google Scholar] [CrossRef]
- Mukherjee, S. Distribution of downlink SINR in heterogeneous cellular networks. IEEE J. Sel. Areas Commun. 2012, 30, 54–64. [Google Scholar] [CrossRef]
- Merwaday, A.; Mukherjee, S.; Guvenc, I. On the capacity analysis of HetNets with range expansion and eICIC. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013. [Google Scholar]
- Haenggi, M. Stochastic Geometry for Wireless Networks; Cambridge University Press: New York, NY, USA, 2012. [Google Scholar]
- Lee, C.-H.; Haenggi, M. Interference and outage in Poisson cognitive networks. IEEE Trans. Wirel. Commun. 2012, 11, 1392–1401. [Google Scholar] [CrossRef]


© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guo, L.; Cong, S. Coverage and Rate Analysis for Location-Aware Cross-Tier Cooperation in Two-Tier HetNets. Symmetry 2017, 9, 157. https://doi.org/10.3390/sym9080157
Guo L, Cong S. Coverage and Rate Analysis for Location-Aware Cross-Tier Cooperation in Two-Tier HetNets. Symmetry. 2017; 9(8):157. https://doi.org/10.3390/sym9080157
Chicago/Turabian StyleGuo, Lili, and Shanya Cong. 2017. "Coverage and Rate Analysis for Location-Aware Cross-Tier Cooperation in Two-Tier HetNets" Symmetry 9, no. 8: 157. https://doi.org/10.3390/sym9080157
APA StyleGuo, L., & Cong, S. (2017). Coverage and Rate Analysis for Location-Aware Cross-Tier Cooperation in Two-Tier HetNets. Symmetry, 9(8), 157. https://doi.org/10.3390/sym9080157




