Strategic Management of IT Practices in Tourism for Operation and Service Enhancement
Abstract
:1. Introduction
- The first idea managed by different authors (Orlandi et al. 2020; Masarat et al. 2009) is the definition of a general and unique sequence of ITIL processes. This sequence is meant to be the same for all companies. Even if the sequences proposed for the adoption of ITIL are different among authors, this approach is suggested in recent studies (Orlandi et al. 2020; Lema 2015) and older papers (Masarat et al. 2009; Cater-Steel et al. 2009). Obviously, these sequences of IT procedures and tasks present advantages and inconveniences: (a) the main advantage is its uniqueness and simplicity (as a fixed sequence of processes for IT departments is proposed, no more calculations are needed); (b) conversely, the disadvantage of this approach is that, independently of the companies’ characteristics, all authors suggest a static, general, and universal sequence of ITIL procedures and tasks that should be used by the companies: the main inconvenience hereby is the fact that the proposed set of IT procedures are not specifically adapted to the needs of each company neither to its specific characteristics.
- Another approach is the definition of an adaptive sequence, where the characteristics of the company are taken into account and a specific sequence of the ITIL procedures can be proposed specifically for that company (Schaefer et al. 2020). Some examples of this dynamic approach can be seen in the previous literature (Rubio Sánchez 2021; Miller 2017; Shojafar and Zarrazvand 2012) where specific sequences of the ITIL procedures and tasks are proposed for each company. This method allows the generation of specific sets of IT procedures and tasks for each company. The authors define methods to obtain the sequences in several ways, such as an example (Schaefer et al. 2020), and (Rubio Sánchez 2021): they refer to mathematical optimization techniques, where the objective function is fixed to some requisites defined by the company. Another example can be found in (Miller 2017). This author obtains the sequence from the company’s priorities and business objectives. On the other hand, (Shojafar and Zarrazvand 2012) consider this fuzzy logic. So, the conclusion is that even if the dynamic sets of procedures for IT fit better for each company, there are different ways to obtain this dynamic set of IT procedures.
- Alternatively, the ‘critical implementation factors’ methodology focuses on determining the factors that might help in the IT procedures adoption (Cater-Steel and Pollard 2008). This choice does not clearly set a process order for the adoption of IT procedures, however, it simply defines its conditions to succeed. This type of approach has already been used in different relevant studies (Iden and Eikebrokk 2015).
- It is possible to find another strategy (Case 2007) that is focused on general steps for the implementation of ITI. In this case, the implementation is based on different periods or phases, as suggested by (Case 2007). There is no specific intention to define the order of procedures and tasks for the IT department. It is preferable to lead the implementation as an overall project with the definition of the phases that are necessary to succeed. This approach was definitively abandoned as the adoption and implementation of ITIL is, however, treated from a project management perspective. So, the conclusion is that no clear sequences specifically adapted for small tourism and hospitality organizations can be found.
Tourism and Hospitality Companies
- Revenue management: Yield Revenue Management (YRM) (Jones 2000; CERIUM 2022) systems, help in yield management in hotels.
- Customer Relationship Management (CRM): (Jones 2000; Kimes 1997): client communications to achieve overall client relationship management.
- Room and visit management: including check-in and check-out processes, room management, as well as visitor management, and selling terminals through a PMS (Property Management System) (Jones 2000; Jafari and Medina 2000).
- Reservation management: Central Reservation System (CRS) (Arellano Díaz 2017), principally for room booking management.
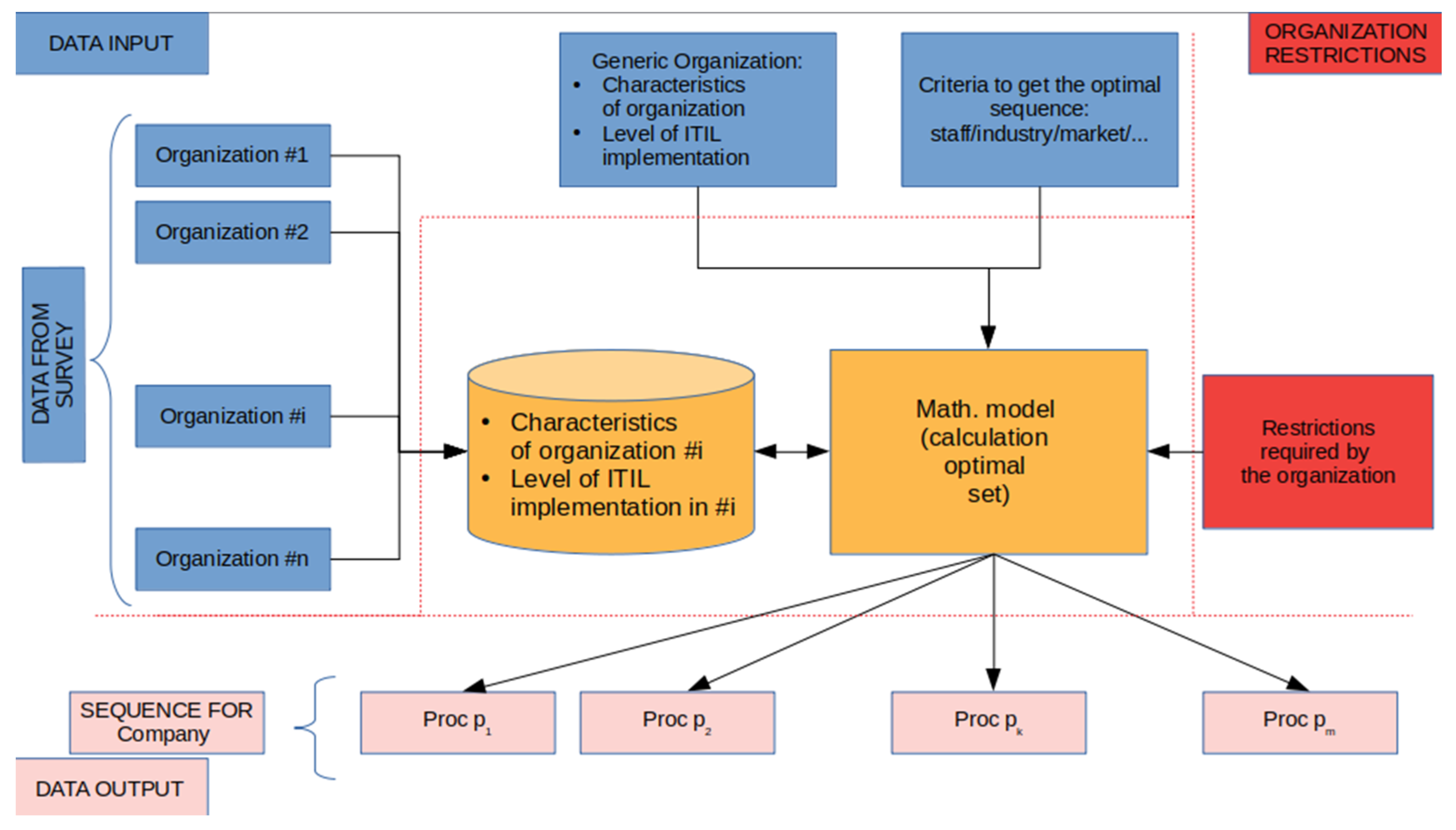
- From the theoretical perspective, it offers a mathematical model to achieve an optimal sequence of processes and procedures that should be implemented in the IT departments of tourism companies. This mathematical model overcomes the disadvantages of previously known models since it does not consider implementing nonuseful or nondesired processes and procedures. This mathematical model is translated into an algorithm and finally into pseudocode to ease its implementation.
- From the methodological point of view, the contribution is an implementation of the model previously addressed, which can be entirely used, as it is public domain, as pointed out in the Supplementary Material section. The database with the data gathered in the survey, the algorithm, and the implementation itself are available.
- Finally, from the practical point of view, we have fully developed an application of the methodology to sequence IT processes to a generic tourism company, which clearly will help the organizations to improve their IT services.
2. Results
2.1. An Example in the Tourism and Hospitality Industry
2.1.1. Characteristics of the Sample
2.1.2. Calculus of the Best Restricted Set of the IT Procedures
3. Discussion
3.1. Sequence Analysis
3.2. Comparison to Other Methodologies
3.2.1. Comparison to Methodology with No Restrictions
3.2.2. Comparing to the Standard List of Tasks and Procedures
3.2.3. About Using the Method in Other Companies
4. Materials and Methods
- Principal activity in the tourism and hospitality sector.
- No more than fifty employees.
- No more than 5 workers in the technological department.
- Offering national and local destines and operating in international markets.
- Not high or low level of IT procedures adoption, as concluded from the study of the responses to the questionnaire.
- The collected data of the survey, which are saved in a database, show the tourism companies’ characteristics and their level of implementation of ITIL procedures.
- After the data are saved, a generic company in the tourism industry was defined and entered into the software application that supports the enhanced method.
- It has also drawn up the criteria to obtain the optimal sequence of IT management procedures to obtain the optimal set of processes that best fit the needs of the company. The mathematical model offers different alternatives: a universal optimization, a single-parameter configuration, and a multiple-parameter calculation. In order to get a more general solution, we suggest a universal optimization.
- The limitations required by the generic tourism and hospitality organization are modeled and introduced into the system. The enhanced method designed in this study allows the exclusion of several IT procedures from the list of possible candidates to be implemented.
- Once executed, the mathematical model is an optimal sequence with the set of ordered ITIL processes that best fit the formerly established criteria obtained (fulfilling the imposed restrictions).
4.1. Survey Description
4.2. Data Storage
4.3. Survey: Technical Elements
4.4. Methodology
4.5. Steps to Determine the Ordered List of Processes
- Fill the database with data (level of implementation and characteristics of organizations) gathered through the survey. These data are required by the next steps
- Get data about the level of IT tasks and procedures adopted, and also about its characteristics for the company that wants to adopt ITIL.
- Build the list of tasks S_IT, excluding those ones already implemented
- Create an empty set SCHOSEN = {}
- Eliminate the excluded tasks and procedures S_IT-S_Excluded
- Define the criteria used to calculate the optimal result by fixing αj, γj. Typical values are: αj = 1, γj = 0
- Calculate the parameter NP for each element in S_IT
- Select procCHOSEN and add it to SCHOSEN
- Delete procCHOSEN from S_IT
- If S_IT still has elements go to 7
- The solution is contained in SCHOSEN.
5. Conclusions
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Number.Process |
|---|
| 1.Handling of incidences |
| 2.Administration of continuous enhancements |
| 3.Handling of validation and approval tests |
| 4.Requesting government |
| 5.Transition-on-production scheduling |
| 6.Supply administration |
| 7.Deployment and version control |
| 8.Phisical and logical security management |
| 9.Capacities handling |
| 10.Infrastructure-access control |
| 11.Asset and config. government |
| 12.Service level agreement control |
| 13.Administration of continuous enhancements |
| 14.Demand control |
| 15.Availability handling |
| 16.Change management |
| 17.Service portfolio control in ICT |
| 18.Service catalogue control |
| Task Information Question (Assign 1 to 3 for …) |
|---|
| Strategic administration of Information and Communication Technologies (ICT) |
| Service portfolio control in ICT |
| Finance administration |
| Demand control |
| Administration of business relations |
| Coordination for design service |
| Service catalogue control |
| Availability handling |
| Service level agreement control |
| Business-continuity administration |
| Physical and logical security management |
| Supply administration |
| Capacities handling |
| Transition-on-production scheduling |
| Change management |
| Deployment and version control |
| Handling of validation and approval tests |
| Asset and config. government |
| Change evaluation |
| Knowledge storing |
| Control of problems flow |
| Handling of incidences |
| Infrastructure-access control |
| Handling/Tracking of events |
| Requesting government |
| Administration of continuous enhancements |
Appendix B
References
- Arellano Díaz, Hernán O. 2017. La calidad en el servicio como ventaja competitiva. Revista Científica Domiio De Las Ciencias 3: 72–83. [Google Scholar]
- Benavides, Giovanny Fernando. 2019. Cadenas de valor y tendencias en innovación en actividades turísticas. Value chains and innovation trends in tourism activities. Cuadernos de Administración 29: 24–37. Available online: https://www.researchgate.net/publication/348348818_Cadenas_de_valor_y_tendencias_en_innovacion_en_actividades_turisticas (accessed on 3 November 2022). [CrossRef]
- Caixabank Research. 2022. Informe Sectorial de Turismo. Available online: https://www.caixabankresearch.com/sites/default/files/content/file/2022/01/17/91185/is_turismo1_2022_esp.pdf (accessed on 3 November 2022).
- Calvo-Manzano, Jose A., Lohana Lema, Magdalena Arcilla, and Juan Luis Rubio. 2015. How small and medium enterprises can begin their implementation of ITIL? Revista Facultad de Ingeniería 77: 127–36. [Google Scholar] [CrossRef] [Green Version]
- Case, Gary. 2007. ITIL V3. Where to Start and How to Achieve Quick Wins. Available online: https://www3.pinkelephant.com/articles/itilv3wheretostarthowtoachievequickwins.pdf (accessed on 4 May 2022).
- Cater-Steel, Aileen, and Carol E. Pollard. 2008. Conflicting views on ITIL implementation: Managed as a project–or business as usual. Paper presented at the 2008 International Conference on Information Resources Management, Niagara Falls, ON, Canada, May 18–20. [Google Scholar]
- Cater-Steel, Aileen, and Wui-Gee Tan. 2005. Implementation of IT Infrastructure Library (ITIL) in Australia: Progress and Success Factors. Paper presented at the IT Governance International Conference, Auckland, New Zealand, November 14–16. [Google Scholar]
- Cater-Steel, Aileen, Mark Toleman, and Wui-Gee Tan. 2009. Implementing IT service management: A case study focusing on critical success factors. Journal of Computer Information Systems 50: 1–12. [Google Scholar]
- CERIUM. 2022. Hotel Revenue Management: Nuevas Tendencias e Innovaciones. Available online: https://cerium.es/hotel-revenue-management-tendencias/ (accessed on 3 November 2022).
- Chourabi, Hafedh, Taewoo Nam, Shawn Walker, J. Ramon Gil-Garcia, Sehl Mellouli, Karine Nahon, Theresa A. Pardo, and Hans Jochen Scholl. 2012. Understanding Smart City Initiatives: An Integrative and Comprehensive Theoretical Framework. Paper presented at the 45th Hawaii International Conference on System Sciences, Maui, HI, USA, January 4–7; pp. 2289–97. [Google Scholar]
- CIGREF. 2009. Les Référentiels De La DSI—Usages Et Bonnes Pratiques. Available online: https://www.cigref.fr/cigref_publications/RapportsContainer/Parus2009/Referentiels_de_la_DSI_CIGREF_2009.pdf (accessed on 1 December 2021).
- Dirks, Susanne, and Mark Keeling. 2009. A Vision of Smarter Cities. Somers: IBM Institute for Business Value. [Google Scholar]
- Figueroa Domecq, Cristina, and P. Talón Ballestero. 2007. La gestión de la información en el sector hotelero madrileño la inversión en TICS, la importancia de la conectividad y las características del hotel. Paper presented at the XXI Congreso Anual AEDEM, Universidad Rey Juan Carlos Base de datos, Madrid, Spain, June 6–8; vol. 1, p. 26. [Google Scholar]
- Fundación Orange España. 2016. La Transformación Digital en el Sector Turístico. Available online: https://www.fundacionorange.es/wp-content/uploads/2016/05/eE_La_transformacion_digital_del_sector_turistico.pdf (accessed on 3 November 2022).
- Garayar, Ramón. 2021. Los seis pilares de la tecnología en gestión hotelera. June 2022 de Instituto Tecnológico Hotelero Sitio web. Available online: https://www.ithotelero.com/blog/los-6-pilares-de-la-tecnologia-en-gestion-hotelera/ (accessed on 4 May 2022).
- Gervalla, Muhamet, Naim Preniqi, and Peter Kopacek. 2018. IT infrastructure library (ITIL) framework approach to IT governance. IFAC PapersOnLine 51: 181–85. [Google Scholar] [CrossRef]
- Hotelogix. 2014. 4 Claves Que Todo Equipo De IT De Grupos De Múltiples Hoteles Debe Considerar. Available online: https://www.hotelogix.com/es/blog/2014/04/17/4-claves-que-todo-equipo-de-it-de-grupos-de-multiples-hoteles-debe-considerar/5/ (accessed on 3 November 2022).
- Iden, Jon, and Tom Roar Eikebrokk. 2015. The impact of senior management involvement, organisational commitment and group efficacy on ITIL implementation benefits. Information Systems and e-Business Management 13: 527–52. [Google Scholar] [CrossRef] [Green Version]
- Jafari, Jafar, and Víctor Manuel Pina Medina. 2000. Enciclopedia Del Turismo. Madrid: Síntesis. [Google Scholar]
- Jones, Peter. 2000. Defining YM and measuring its impact on hotel performance. In YM: Strategies for the Service Industries. Edited by A. Ingold, U. McMahon-Beattie and I. Yeoman. London: Continuum. [Google Scholar]
- Kimes, Sheryl. 1997. The principles of YM: An overview. In YM: Strategies for the Service Industries. Edited by I. Yeoman and A. Ingold. London: Cassell. [Google Scholar]
- Komninos, Nicos. 2002. Intelligent Cities. London: Spon Press. [Google Scholar]
- Lema, Lohana. 2015. ITIL in Small to Medium-Sized Enterprises: Toward a Proposal Based on an IT procedures Implementation Sequence and a Profile Scheme Strategy for Implementing the First Process in the Sequence. Master’s thesis, Universidad Politécnica deMadrid, Lenguajes y Sistemas Informáticos e Ingeniería del Software, Madrid, Spain. Available online: http://oa.upm.es/36237/ (accessed on 1 April 2022).
- Lucio-Nieto, Teresa, and Dora Luz González-Bañales. 2019. Exploring ITIL® Implementation Challenges in Latin American Companies. International Journal of Information Technologies and Systems Approach 12: 73–86. [Google Scholar] [CrossRef]
- Marrone, Mauricio, Francis Gacenga, Aileen Cater-Steel, and Lutz Kolbe. 2014. IT Service Management: A Cross-national Study of ITIL Adoption. Communications of the Association for Information Systems 34: 49. [Google Scholar] [CrossRef] [Green Version]
- Masarat, Ayat, Mohammad Sharifi, Shamsul Sahibudin, and Sulaimi Ibrahim. 2009. Adoption Factors and Implementation Steps of ITSM in the Target. Paper presented at the 2009 Third Asia International Conference on Modelling & Simulation, Bali, Indonesia, May 25–29; pp. 369–74. [Google Scholar]
- Miller, Alma C. H. 2017. Implementation Priority of the ITIL Framework Based on a Process Sequencing Model. Ph.D. thesis, The George Washington University, Washington, DC. [Google Scholar]
- Ministerio de Industria, Comercio y Turismo. 2020. Cifras Pyme. Madrid: Gobierno de España. Available online: http://www.ipyme.org/es-ES/publicaciones/Paginas/estadisticaspyme.aspx (accessed on 31 January 2022).
- Orlandi, Tomas Roberto, Fernando Santos Dantas, and João Souza Neto. 2020. The use of portfolio management for strategic alignment—A survey with Brazilian Companies. Journal of Information Systems and Technology Management 17: e202017004. [Google Scholar] [CrossRef]
- Pastuszak, Jarosław, Adam Czarnecki, and Cezary Orłowski. 2012. Ontologically Aided Rule Model for the Implementation of IT procedures. In Advances in Knowledge-Based and Intelligent Information and Engineering Systems. Edited by M. Graña, C. Toro, J. Posada, R. J. Howlett and L. C. Jain. Amsterdam: IOS Press, pp. 1428–38. [Google Scholar]
- Polard, Carol, and Aileen Cater-Steel. 2009. Justifications, Strategies, and Critical Success Factors in Successful ITIL Implementations in U.S. and Australian Companies: An Exploratory Study. Information Systems Management 26: 164–75. [Google Scholar] [CrossRef] [Green Version]
- Roach, Stephen. 1991. Services under Siege—The Restructuring Imperative. Harvard Business Review 5: 82–92. [Google Scholar]
- Romero, Rocio. 2020. El Sector Hotelero En La Era Covid: Cae La Demanda Pero Crece La Inversión. Available online: https://www.elconfidencial.com/mercados/2020-12-18/estrategias-inversion-sector-hotelero-bra_2875863/ (accessed on 3 November 2022).
- Rubio Sánchez, Juan Luis. 2021. Model to Optimize the Decision Making on Processes in IT Departments. Mathematics 9: 983. [Google Scholar] [CrossRef]
- Sayles, C. I. 1963. New York Hilton data-processing system. Cornell Hotel and Restaurant Administration Quarterly 4: 20–41. [Google Scholar]
- Schaefer, Jones Luís, Ismael Cristofer Baierle, Elpidio Oscar Benitez Nara, Guilherme Brittes Benitez, and Claus Haetinger. 2020. Corporate Governance and Information Technology: A Hybrid Vision Based on COBIT and ITIL for Small Companies. Paper presented at the XL Encontro Nacional de Engenharia de producao, Foz do Iguaçu, Brazil, October 20–23. [Google Scholar]
- Shojafar, Mohammad, and Hamid Zarrazvand. 2012. The Use of Fuzzy Cognitive Maps in Analyzing and Implementation of IT procedures. arXiv arXiv:1206.2297. [Google Scholar]
- Tan, Wui-Gee, Aileen Cater-Steel, Mark Toleman, and Rachel Seaniger. 2007. Implementing centralized IT service management: Drawing lessons from the public sector. IFAC PapersOnLine 51: 181–85. [Google Scholar]
- Tawar, Tawar. 2013. Applying ITIL Based Software Inside University’s ICT Centre toward Continual Service Improvement. Paper presented at the Information Systems International Conference (ISICO), Bali, Indonesia, December 2–4; vol. 2. [Google Scholar]
- Urueña, Alberto, María Pilar Ballestero, Raquel Castro, Santiago Cadenas, Eva Prieto, and Menchu Maira. 2019. Análisis Sectorial de la Implantación de las TIC en las Empresas Españolas. Informe ePYME; Madrid: Ministerio de Asuntos Económicos y Transformación Digital.
- Zareravasan, Ahad, Taha Mansouri, Mohammad Mehrabioun Mohammadi, and Saeed Rouhani. 2014. Supporting the module sequencing decision in ITIL solution implementation: An application of the fuzzy TOPSIS approach. International Journal of Information Technologies and Systems Approach 7: 41–60. [Google Scholar] [CrossRef]
- Zhang, Lingyue, Dawei Lu, and Xiaoguang Wang. 2020. Measuring and testing interdependence among random vectors based on Spearman’s ρ and Kendall’s τ. Computational Statistics 35: 1685–713. [Google Scholar] [CrossRef]
| Procedure |
|---|
| Strategic administration of Information and Communication Technologies (ICT) |
| Finance administration |
| Coordination for design service |
| Change management |
| Knowledge storing |
| Handling/Tracking of events |
| Administration of business relations (1) |
| Control of problems flow (1) |
| Procedure |
|---|
| Handling of incidences |
| Administration of continuous enhancements |
| Handling of validation and approval tests |
| Requesting government |
| Transition-on-production scheduling |
| Supply administration |
| Deployment and version control |
| Physical and logical security management |
| Capacities handling |
| Infrastructure-access control |
| Identification of Sequenced Procedures |
|---|
| Handling of incidences |
| Administration of continuous enhancements |
| Handling of validation and approval tests |
| Requesting government |
| Transition-on-production scheduling |
| Handling/Tracking of events |
| Supply administration |
| Deployment and version control |
| Change evaluation |
| Knowledge storing |
| List of IT Tasks (Author) | Test 1 * Results (Null Hypothesis Limits) | Test 2 * Results (Null Hypothesis Limits) | Conclusion |
|---|---|---|---|
| (Miller 2017) | −0.023 (−0.47; 0.47) | 0.509 (−0.34; 0.34) | Could be dependent |
| (Pastuszak et al. 2012) | 0.516 (−0.70; 0.70) | 0.444 (−0.55; 0.55) | Dependency not found |
| (Caixabank Research 2022) | −0.417 (0.50; −0.50) | −0.101 (0.38; −0.38) | Dependency not found |
| (Marrone et al. 2014) | −0.111 (−0.47; 0.47) | −0.046 (−0.34; 0.34) | Dependency not found |
| (Zareravasan et al. 2014) | −0.50 (−1.00; 1.00) | 0 (−1.00; 1.00) | Dependency not found |
| (Lucio-Nieto and González-Bañales 2019) | 0.14 (−0.73; 0.73) | −0.071 (−0.64; 0.64) | Dependency not found |
| Technical Element | Value |
|---|---|
| Geographic area | Spain |
| Polling method | On lines/Phoning/Present |
| Tries | 201 |
| Responses | 110 |
| Required to be significative | 95 |
| Confidence degree | 95% |
| Discrepancy | 8.5% |
| Interest organizations | Tourism companies |
| Company selection | Random |
| Survey mode | One step |
| Channel communication | |
| Questionnaire | See Table A2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Juan Luis, R.S.; Mercedes Raquel, G.R.; Moure Olga, M. Strategic Management of IT Practices in Tourism for Operation and Service Enhancement. Adm. Sci. 2023, 13, 2. https://doi.org/10.3390/admsci13010002
Juan Luis RS, Mercedes Raquel GR, Moure Olga M. Strategic Management of IT Practices in Tourism for Operation and Service Enhancement. Administrative Sciences. 2023; 13(1):2. https://doi.org/10.3390/admsci13010002
Chicago/Turabian StyleJuan Luis, Rubio Sánchez, García Revilla Mercedes Raquel, and Martínez Moure Olga. 2023. "Strategic Management of IT Practices in Tourism for Operation and Service Enhancement" Administrative Sciences 13, no. 1: 2. https://doi.org/10.3390/admsci13010002
APA StyleJuan Luis, R. S., Mercedes Raquel, G. R., & Moure Olga, M. (2023). Strategic Management of IT Practices in Tourism for Operation and Service Enhancement. Administrative Sciences, 13(1), 2. https://doi.org/10.3390/admsci13010002





