Comprehensive Analysis of Maritime Cybersecurity Landscape Based on the NIST CSF v2.0
Abstract
1. Introduction
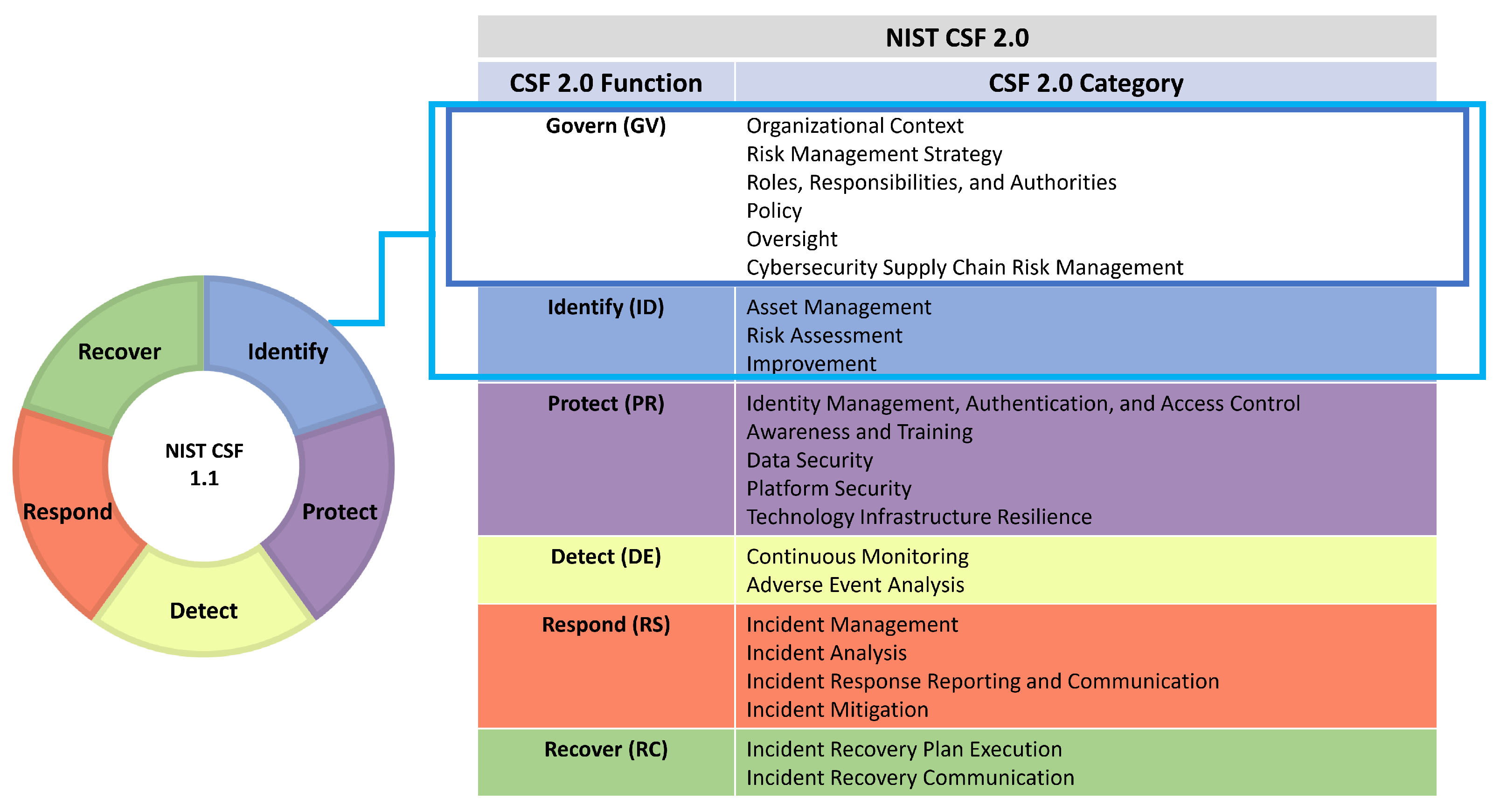
2. Background: NIST CSF in the Maritime Context
3. Research Methodology
3.1. Research Scope, Aim, and Research Questions
- RQ1.
- What are the most recent advancements in the literature on maritime cybersecurity with reference to the NIST CSF functions and their related cybersecurity categories?
- RQ2.
- How mature are the respective cybersecurity functions in the maritime domain?
- RQ3.
- Are there any identified gaps in maritime cybersecurity that necessitate attention from the scientific community?
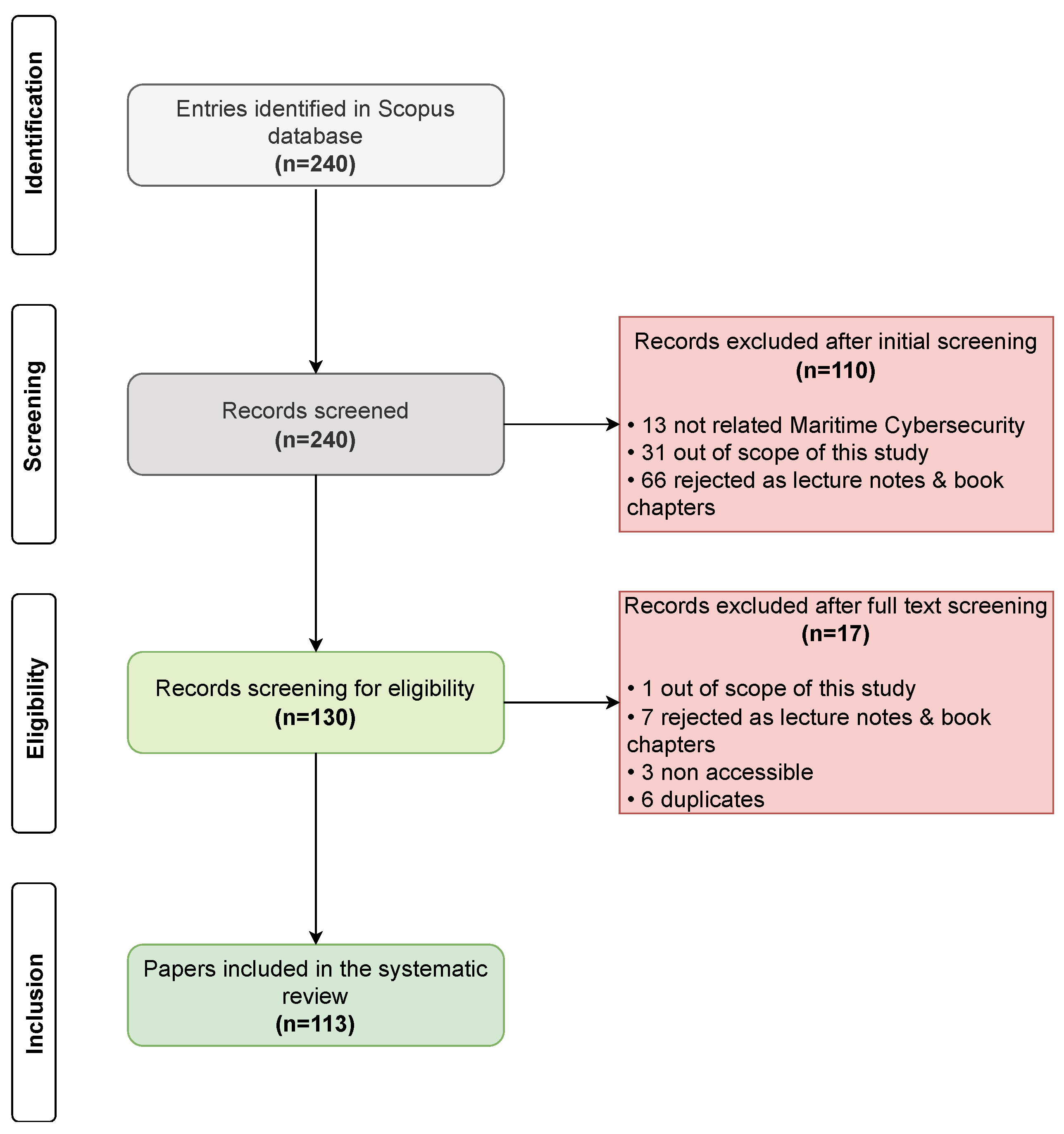
3.2. SLR Methodology
3.3. Research Strategy and Eligibility Criteria
- TITLE-ABS-KEY ((Cybersecurity OR Information security) AND (Maritime OR Shipping))
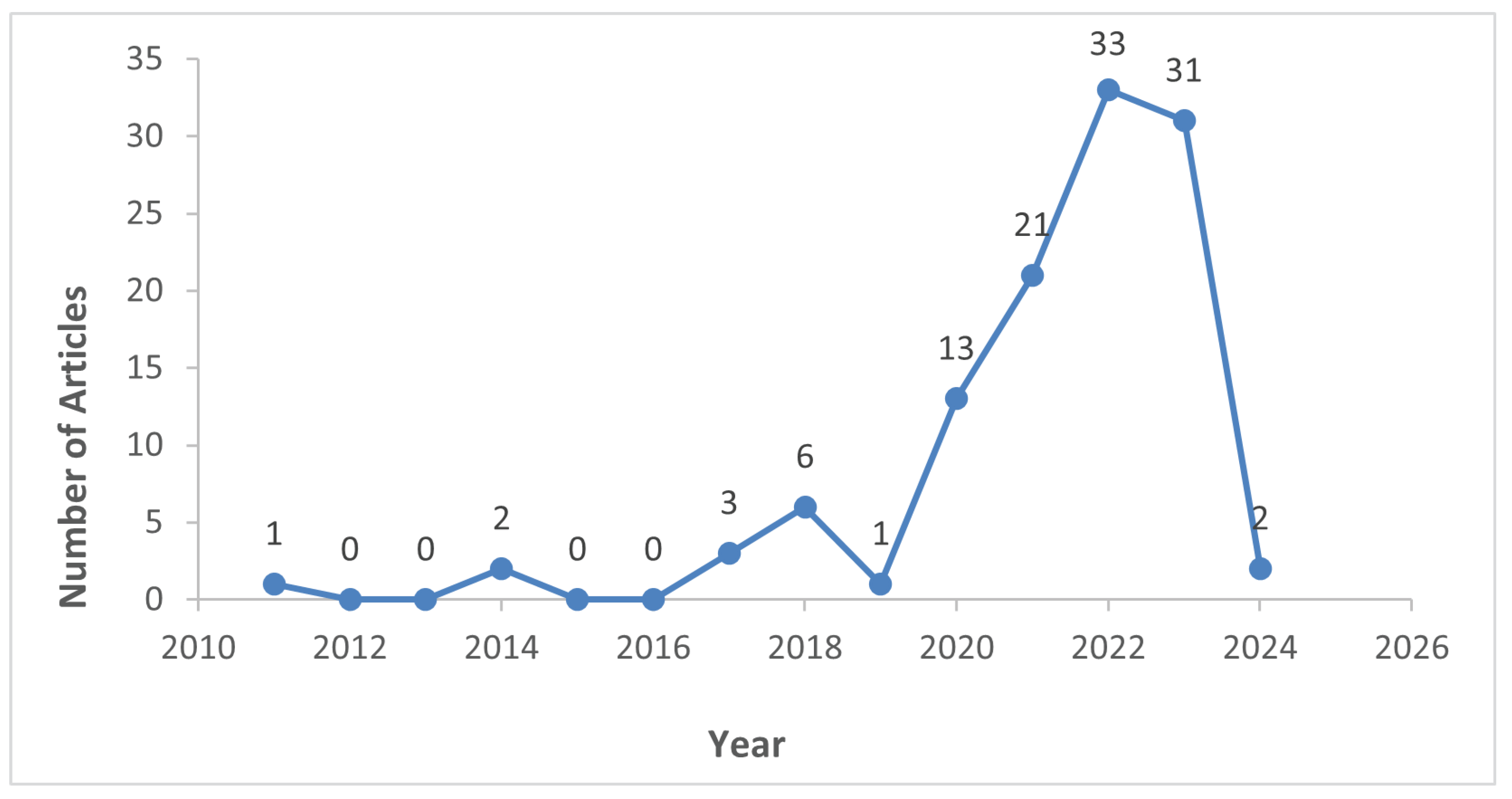
3.4. Methodology Results
4. Related Work
5. NIST CSF-Based Analysis of Maritime Cybersecurity
5.1. Govern
5.1.1. Organizational Context
5.1.2. Risk Management Strategy
5.1.3. Cybersecurity Supply Chain Risk Management
5.2. Identify
5.2.1. Asset Management
5.2.2. Risk Assessment
5.2.3. Improvement
5.3. Protect
5.3.1. Identity Management, Authentication, and Access Control
5.3.2. Awareness and Training
5.3.3. Data Security
5.3.4. Platform Security
5.3.5. Technology Infrastructure Resilience
5.4. Detect
5.4.1. Continuous Monitoring
5.4.2. Adverse Event Analysis
5.5. Respond
5.5.1. Incident Management
5.5.2. Incident Analysis
5.6. Recover
Incident Recovery Plan Execution
6. Discussion
- RQ1.
- What are the most recent advancements in the literature on maritime cybersecurity with reference to the NIST CSF functions and their related cybersecurity categories?Recent advancements in maritime cybersecurity literature, as aligned with the NIST CSF Functions, include:
- Govern Function: There has been a focus on ‘Organizational Context’ [24,25,26,27,28] and ‘Risk Management Strategy’ [14,29,30,31,32,33], with several articles addressing these areas. This indicates progress in the understanding and implementation of cybersecurity within the organizational frameworks and risk management processes of maritime operations.
- Cybersecurity Supply Chain Risk Management: Although there are gaps, the literature has begun to address the importance of cybersecurity in the maritime supply chain [34,35,36]. Considering the interconnected nature of global supply chains, advancements in this area are critical for mitigating the potential widespread impact of cybersecurity breaches.
- Identity Management, Authentication, and Access Control: Advancements in identity management, authentication, and access control have been highlighted as essential for effective cybersecurity in the maritime sector [74,75]. The research suggests that implementing secure management systems and multi-factor authentication mechanisms can enhance security while maintaining usability.
- Education and Training: The literature significantly underscores the role of education and training in enhancing maritime cybersecurity [16,20,68,76,77,78,79,80]. There is a consensus on the need for comprehensive education and training programs to build sufficient cybersecurity knowledge across all levels of the industry.
- Data Security: Data security has been identified as a critical area of advancement, with the research proposing various strategies to protect data within the maritime sector [60,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95]. This includes the development of technologies and processes to ensure the integrity and confidentiality of maritime data.
- Strategic and Proactive Research: The research aims to develop a proactive approach to cybersecurity in the maritime industry, anticipating future developments and challenges. This strategic focus is expected to contribute to the maturity of maritime cybersecurity and lead to the development of advanced measures to protect against cyber threats.
These advancements reflect a growing alignment with the NIST CSF and a concerted effort to address the dynamic cybersecurity challenges within the maritime industry. The literature suggests that while there are areas of progress, there is also a need for ongoing research and development to further enhance the cybersecurity posture of maritime operations. - RQ2.
- How mature are the respective cybersecurity functions in the maritime domain? The maturity of the NIST CSF v2.0 in maritime operations has yet to fully evolve. While areas involving the Govern, Identify, and Protect functions have received considerable coverage in the literature, there are significant gaps, particularly with respect to the Respond and Recover functions, particularly the incident response reporting and communication, incident mitigation, and incident recovery communication processes. Furthermore, only three articles were found on cybersecurity for maritime supply chains [34,35,36], a particularly critical area; this lack of comprehensive coverage implies a need for further research to reinforce maritime cybersecurity, especially in the context of response and recovery strategies. Overall, while the maritime sector has made strides in aligning with NIST CSF v2.0, as shown in the study, there remains room for maturity and advancement.
- RQ3.
- Are there any identified gaps in maritime cybersecurity that necessitate attention from the scientific community? In light of the data presented in Table 7 below, further research is required to address a number of observed gaps, particularly within the Govern, Respond, and Recover functions of the NIST CSF v2.0. Notably, within the Govern function, there is a lack of research on the categories of roles, responsibilities, and authorities, policy, and oversight, all of which are essential for establishing a clear governance structure for cybersecurity in maritime operations. Moreover, the category of cybersecurity supply chain risk management is particularly crucial in the maritime industry in light of the interconnected nature of global supply chains. Cybersecurity breaches could potentially disrupt not only a single ship or company, but ripple through the entire network, causing widespread damage. A gap in the literature on this area suggests an urgent need for research into strategies, protocols, and frameworks that specifically address cybersecurity risks in maritime supply chains. Furthermore, the Respond function reveals gaps in incident response reporting and communication as well as incident mitigation, both of which are critical areas for effectively managing the impact of cybersecurity incidents. The research indicates another significant shortfall in the Recover function, particularly in incident recovery communication, which is vital for coordinating cohesive post-incident recovery efforts. This gap points to the need for research into communication protocols and strategies that can aid in swift and efficient recovery from cybersecurity breaches in the maritime context. By addressing these research gaps, the maritime sector could potentially achieve a more robust and comprehensive approach to cybersecurity.
| NIST CSF v2.0 Functions | Answers per Function RQ1 | Answers per Function RQ2 | Answers per Function RQ3 |
|---|---|---|---|
| Govern: | Function’s Categories:
| In the “Govern” function, 2 out of 6 categories were identified. | Within the “Govern” function, only 2 out of the 6 categories were recognized. As per the NIST CSF v2.0, this is significant as it sets the stage for how an organization carries out the remaining five functions. The research community definitely needs to focus on the 4 categories that have not been identified. |
| Identify: | Function’s Categories:
| In the “Identify” function, comprehensively, all 3 categories were recognized. | The research community has demonstrated maturity in this function, with all categories having been identified. However, more research is required, with a particular focus needed on the “Asset Management” category, as only 3 articles have been identified. |
| Protect: | Function’s Categories:
| Under the “Protect” function, every single one of the 5 categories was successfully determined. | The research community has demonstrated maturity in this function, with all categories having been identified. However, there is a definite need to focus more on the “Identity Management, Authentication, and Access Control” category, as only 2 articles have been identified. |
| Detect: | Function’s Categories:
| In the “Detect” function, all 2 categories were pinpointed without exception. | The research community has demonstrated maturity in this function, with all categories having been identified. |
| Respond: | Function’s Categories:
| Within the “Respond” function, half of the categories, precisely 2 out of 4, were decisively identified. | In light of our research, 2 crucial aspects of the “Respond” function ‘Incident Response Reporting and Communication’ and ‘Incident Mitigation’ have not been identified. This presents a significant gap as these elements play key roles in handling cybersecurity incidents effectively. |
| Recover: | Function’s Categories:
| In the “Recover” function, 1 out of 2 categories was detected. | Our research, which accounts for only 2 articles under the “Recover” function, particularly in the ‘Incident Recovery Plan Execution’ category, reveals a distinct void in the area of ‘Incident Recovery Communication’. The research community definitely needs to focus on this function. |
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bannister, A. When the Screens Went Black: How NotPetya Taught Maersk to Rely on Resilience—Not Luck—to Mitigate Future Cyber-Attacks. Available online: https://portswigger.net/daily-swig/when-the-screens-went-black-how-notpetya-taught-maersk-to-rely-on-resilience-not-luck-to-mitigate-future-cyber-attacks (accessed on 9 December 2019).
- Customs & International Trade Law Blog. Maritime Industry Rocked by Cyber Attacks. Available online: https://customsandinternationaltradelaw.com/2020/10/20/maritime-industry-rocked-by-cyber-attacks/ (accessed on 1 October 2020).
- National Institute of Standards and Technology (NIST). Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1; Cybersecurity Framework NIST.CSWP.04162018; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- National Institute of Standards and Technology (NIST). Framework for Improving Critical Infrastructure Cybersecurity, Version 2.0; Public Draft NIST.CSWP.29.ipd; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. [Google Scholar]
- National Institute of Standards and Technology (NIST). New Cybersecurity Framework Profile to Help Ensure Safe Transfer of Hazardous Liquids at Ports. Available online: https://www.nccoe.nist.gov/news-insights/new-cybersecurity-framework-profile-help-ensure-safe-transfer-hazardous-liquids-ports (accessed on 10 November 2016).
- IMO. Guidelines on Maritime Cyber Risk Management. MSC-FAL.1/Circ.3/Rev.2. Available online: https://www.imo.org/en/OurWork/Security/Pages/Cyber-security.aspx (accessed on 7 June 2022).
- International Maritime Organization. Maritime Cyber Risk Management in Safety Management Systems—Resolution MSC.428(98). Available online: https://www.imo.org/en/OurWork/Security/Pages/Cyber-security.aspx (accessed on 16 June 2017).
- International Association of Classification Societies. IACS Adopts New Requirements on Cyber Safety. Available online: https://iacs.org.uk/news/iacs-adopts-new-requirements-on-cyber-safety/ (accessed on 1 January 2024).
- ABS Advanced Solutions Answers US Coast Guard Call for Implementing Cyber Security in US Ports. Available online: https://www.abs-group.com/News-and-Events/Press-Releases/ABS-Advanced-Solutions-Answers-US-Coast-Guard-Call-for-Implementing-Cyber-Security-in-US-Ports/ (accessed on 25 February 2019).
- Boland, A.; Dickson, R.; Cherry, G. Doing a Systematic Review: A Student’s Guide; SAGE Publications Ltd.: London, UK, 2017. [Google Scholar]
- Fink, A. Conducting Research Literature Reviews: From the Internet to Paper, 2nd ed.; Sage Publications: Thousand Oaks, CA, USA, 2005. [Google Scholar]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. BMJ 2009, 339, b2535. [Google Scholar] [CrossRef]
- Androjna, A.; Perkovič, M.; Pavic, I.; Mišković, J. Ais data vulnerability indicated by a spoofing case-study. Appl. Sci. 2021, 11, 5015. [Google Scholar] [CrossRef]
- Jia, X.; Zhang, D. Prediction of maritime logistics service risks applying soft set based association rule: An early warning model. Reliab. Eng. Syst. Saf. 2021, 207, 107339. [Google Scholar] [CrossRef]
- de la Peña Zarzuelo, I. Cybersecurity in ports and maritime industry: Reasons for raising awareness on this issue. Transp. Policy 2021, 100, 1–4. [Google Scholar] [CrossRef]
- Alcaide, J.I.; Llave, R.G. Critical infrastructures cybersecurity and the maritime sector. Transp. Res. Procedia 2020, 45, 547–554. [Google Scholar] [CrossRef]
- Androjna, A.; Perkovič, M. Impact of Spoofing of Navigation Systems on Maritime Situational Awareness. Trans. Marit. Sci. 2021, 10, 361–373. [Google Scholar] [CrossRef]
- McGillivary, P. Why maritime cybersecurity is an ocean policy priority and how it can be addressed. Mar. Technol. Soc. J. 2018, 52, 44–57. [Google Scholar] [CrossRef]
- Meyer-Larsen, N.; Müller, R. Enhancing the Cybersecurity of Port Community Systems. In Dynamics in Logistics; Springer: Cham, Switzerland, 2018; pp. 318–323. [Google Scholar] [CrossRef]
- Hopcraft, R. Developing Maritime Digital Competencies. IEEE Commun. Stand. Mag. 2021, 5, 12–18. [Google Scholar] [CrossRef]
- Oruc, A.; Amro, A.; Gkioulos, V. Assessing Cyber Risks of an INS Using the MITRE ATT&CK Framework. Sensors 2022, 22, 8745. [Google Scholar] [CrossRef]
- Kapalidis, C.; Karamperidis, S.; Watson, T.; Koligiannis, G. A Vulnerability Centric System of Systems Analysis on the Maritime Transportation Sector Most Valuable Assets: Recommendations for Port Facilities and Ships. J. Mar. Sci. Eng. 2022, 10, 1486. [Google Scholar] [CrossRef]
- Søner, Ø.; Kayisoglu, G.; Bolat, P.; Tam, K. Risk sensitivity analysis of AIS cyber security through maritime cyber regulatory frameworks. Appl. Ocean Res. 2024, 142, 103855. [Google Scholar] [CrossRef]
- Jo, Y.; Choi, O.; You, J.; Cha, Y.; Lee, D.H. Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework. Sensors 2022, 22, 1860. [Google Scholar] [CrossRef] [PubMed]
- Karim, M.S. Maritime cybersecurity and the IMO legal instruments: Sluggish response to an escalating threat? Mar. Policy 2022, 143, 105138. [Google Scholar] [CrossRef]
- Kaczerska, D.; Kizielewicz, J.; Skrzeszewska, K. Digital Transformation in Ferry Shipping—Case Study in the Baltic Sea Region. TransNav 2023, 17, 553–560. [Google Scholar] [CrossRef]
- Smith, M. Transatlantic security relations since the European security strategy: What role for the EU in its pursuit of strategic autonomy? J. Eur. Integr. 2018, 40, 605–620. [Google Scholar] [CrossRef]
- Sheng, L.; Dai, Z. Research on the maritime communication cryptographic chip’s compiler optimization. Pol. Marit. Res. 2017, 24, 60–65. [Google Scholar] [CrossRef]
- Ahmed, A.M.; Hussaini, A.; Abdulhamid, A. Cyber Warfare And National Security: Imperative For Naval Operations. In Proceedings of the 2022 International Conference on Computational Science and Computational Intelligence, CSCI 2022, Las Vegas, NV, USA, 14–16 December 2022; pp. 990–996. [Google Scholar] [CrossRef]
- Abkowitz, M.; Camp, J. An application of enterprise risk management in the marine transportation industry. WIT Trans. Built Environ. 2011, 119, 221–232. [Google Scholar] [CrossRef]
- Melnyk, O.; Onyshchenko, S.; Onishchenko, O.; Shumylo, O.; Voloshyn, A.; Koskina, Y.; Volianska, Y. Review of Ship Information Security Risks and Safety of Maritime Transportation Issues. TransNav 2022, 16, 717–722. [Google Scholar] [CrossRef]
- Amro, A.; Gkioulos, V. Cyber risk management for autonomous passenger ships using threat-informed defense-in-depth. Int. J. Inf. Secur. 2023, 22, 249–288. [Google Scholar] [CrossRef]
- Rajaram, P.; Goh, M.; Zhou, J. Guidelines for cyber risk management in shipboard operational technology systems. J. Phys. Conf. Ser. 2022, 2311, 012002. [Google Scholar] [CrossRef]
- Kusrini, E.; Hanim, K. Analysis of compliance and supply chain security risks based on ISO 28001 in a logistic service provider in Indonesia. Int. J. Saf. Secur. Eng. 2021, 11, 135–142. [Google Scholar] [CrossRef]
- Meland, P.; Nesheim, D.; Bernsmed, K.; Sindre, G. Assessing cyber threats for storyless systems. J. Inf. Secur. Appl. 2022, 64, 103050. [Google Scholar] [CrossRef]
- Longo, G.; Russo, E.; Armando, A.; Merlo, A. Attacking (and Defending) the Maritime Radar System. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3575–3589. [Google Scholar] [CrossRef]
- ISO 28001:2007; Security Management Systems for the Supply Chain—Best Practices for Implementing Supply Chain Security, Assessments and Plans—Requirements and Guidance International Standard. International Organization for Standardization (ISO): Geneva, Switzerland, 2007. Available online: https://www.iso.org/standard/45654.html (accessed on 1 January 2024).
- Oruc, A.; Gkioulos, V.; Katsikas, S. Towards a Cyber-Physical Range for the Integrated Navigation System (INS). J. Mar. Sci. Eng. 2022, 10, 107. [Google Scholar] [CrossRef]
- Ashraf, I.; Park, Y.; Hur, S.; Kim, S.W.; Alroobaea, R.; Zikria, Y.B.; Nosheen, S. A Survey on Cyber Security Threats in IoT-Enabled Maritime Industry. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2677–2690. [Google Scholar] [CrossRef]
- Charitos, E.D.; Kounalakis, N.A.; Kantzavelou, I. Cybersecurity at Merchant Shipping. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 27–29 July 2022; pp. 394–399. [Google Scholar] [CrossRef]
- Lee, C.; Lee, S. Evaluating the Vulnerability of YOLOv5 to Adversarial Attacks for Enhanced Cybersecurity in MASS. J. Mar. Sci. Eng. 2023, 11, 947. [Google Scholar] [CrossRef]
- Bolbot, V.; Theotokatos, G.; Boulougouris, E.; Vassalos, D. A novel cyber-risk assessment method for ship systems. Saf. Sci. 2020, 131, 104908. [Google Scholar] [CrossRef]
- Martinie, C.; Grigoriadis, C.; Kalogeraki, E.M.; Kotzanikolaou, P. Modelling Human Tasks to Enhance Threat Identification in Critical Maritime Systems. In Proceedings of the 25th Pan-Hellenic Conference on Informatics, Volos, Greece, 26–28 November 2021; pp. 375–380. [Google Scholar] [CrossRef]
- Yoo, Y.; Park, H.S. Qualitative risk assessment of cybersecurity and development of vulnerability enhancement plans in consideration of digitalized ship. J. Mar. Sci. Eng. 2021, 9, 565. [Google Scholar] [CrossRef]
- Androjna, A.; Brcko, T.; Pavic, I.; Greidanus, H. Assessing cyber challenges of maritime navigation. J. Mar. Sci. Eng. 2020, 8, 776. [Google Scholar] [CrossRef]
- Bolbot, V.; Theotokatos, G.; Wennersberg, L.; Faivre, J.; Vassalos, D.; Boulougouris, E.; Jan Rødseth, Ø.; Andersen, P.; Pauwelyn, A.S.; Van Coillie, A. A novel risk assessment process: Application to an autonomous inland waterways ship. Proc. Inst. Mech. Eng. Part O J. Risk Reliab. 2023, 237, 436–458. [Google Scholar] [CrossRef]
- Melnyk, O.; Onyshchenko, S.; Onishchenko, O.; Lohinov, O.; Ocheretna, V. Integral Approach to Vulnerability Assessment of Ship’s Critical Equipment and Systems. Trans. Marit. Sci. 2023, 12. [Google Scholar] [CrossRef]
- Park, C.; Kontovas, C.; Yang, Z.; Chang, C.H. A BN driven FMEA approach to assess maritime cybersecurity risks. Ocean Coast. Manag. 2023, 235, 106480. [Google Scholar] [CrossRef]
- Eichenhofer, J.; Heymann, E.; Miller, B.; Kang, A. An In-Depth Security Assessment of Maritime Container Terminal Software Systems. IEEE Access 2020, 8, 128050–128067. [Google Scholar] [CrossRef]
- Trimble, D.; Monken, J.; Sand, A.F.L. A framework for cybersecurity assessments of critical port infrastructure. In Proceedings of the 2017 International Conference on Cyber Conflict (CyCon U.S.), Washington, DC, USA, 7–8 November 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Poyhonen, J.; Simola, J.; Khan, I.; Lehto, M.; Wali, S. Assessment of cyber security risks: A smart terminal process. In Proceedings of the European Conference on Information Warfare and Security, ECCWS, Piraeus, Greece, 22–23 June 2023; pp. 366–373. [Google Scholar] [CrossRef]
- Progoulakis, I.; Nikitakos, N.; Dalaklis, D.; Yaacob, R. Cyber-Physical Security For Ports Infrastructure. In Proceedings of the International Maritime Transport and Logistics Conference, Alexandria, Egypt, 20–22 March 2022; Volume 11. [Google Scholar] [CrossRef]
- Weaver, G.A.; Feddersen, B.; Marla, L.; Wei, D.; Rose, A.; Van Moer, M. Estimating economic losses from cyber-attacks on shipping ports: An optimization-based approach. Transp. Res. Part C Emerg. Technol. 2022, 137, 103423. [Google Scholar] [CrossRef]
- Progoulakis, I.; Rohmeyer, P.; Nikitakos, N. Cyber Physical Systems Security for Maritime Assets. J. Mar. Sci. Eng. 2021, 9, 1384. [Google Scholar] [CrossRef]
- Gurren, J.; Harish, A.V.; Tam, K.; Jones, K. Security Implications of a Satellite Communication Device on Wireless Networks Using Pentesting. In Proceedings of the 2023 19th International Conference on Wireless and Mobile Computing, Networking and Communications, Montreal, QC, Canada, 21–23 June 2023. [Google Scholar] [CrossRef]
- Oruc, A.; Kavallieratos, G.; Gkioulos, V.; Katsikas, S. Cyber Risk Assessment for SHips (CRASH). TransNav 2024, 18, 115–124. [Google Scholar] [CrossRef]
- Kechagias, E.P.; Chatzistelios, G.; Papadopoulos, G.A.; Apostolou, P. Digital transformation of the maritime industry: A cybersecurity systemic approach. Int. J. Crit. Infrastruct. Prot. 2022, 37, 100526. [Google Scholar] [CrossRef]
- Putra, I.; Octavian, A.; Susilo, A.; Prabowo, A. A hybrid AHP-TOPSIS for risk analysis in maritime cybersecurity based on 3D models. Decis. Sci. Lett. 2023, 12, 759–772. [Google Scholar] [CrossRef]
- Illiashenko, O.; Kharchenko, V.; Babeshko, I.; Fesenko, H.; Di Giandomenico, F. Security-Informed Safety Analysis of Autonomous Transport Systems Considering AI-Powered Cyberattacks and Protection. Entropy 2023, 25, 1123. [Google Scholar] [CrossRef]
- Lee, C.; Lee, S. Overcoming the DDoS Attack Vulnerability of an ISO 19847 Shipboard Data Server. J. Mar. Sci. Eng. 2023, 11, 1000. [Google Scholar] [CrossRef]
- Amro, A.; Gkioulos, V. Evaluation of a Cyber Risk Assessment Approach for Cyber–Physical Systems: Maritime- and Energy-Use Cases. J. Mar. Sci. Eng. 2023, 11, 744. [Google Scholar] [CrossRef]
- Chae, C.J.; Kim, M.; Kim, H.J. A study on identification of development status of MASS technologies and directions of improvement. Appl. Sci. 2020, 10, 4564. [Google Scholar] [CrossRef]
- Dghaym, D.; Hoang, T.; Turnock, S.; Butler, M.; Downes, J.; Pritchard, B. An STPA-based formal composition framework for trustworthy autonomous maritime systems. Saf. Sci. 2021, 136, 105139. [Google Scholar] [CrossRef]
- Shipunov, I.S.; Nyrkov, A.P.; Ryabenkov, M.U.; Morozova, E.V.; Goloskokov, K.P. Investigation of Computer Incidents as an Important Component in the Security of Maritime Transportation. In Proceedings of the 2021 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), St. Petersburg/Moscow, Russia, 26–29 January 2021; pp. 657–660. [Google Scholar] [CrossRef]
- De Faria, D. The impact of cybersecurity on the regulatory legal framework for maritime security. Janus.net 2020, 11, 163–184. [Google Scholar] [CrossRef]
- Hopcraft, R.; Martin, K. Effective maritime cybersecurity regulation—The case for a cyber code. J. Indian Ocean Reg. 2018, 14, 354–366. [Google Scholar] [CrossRef]
- Belev, B.C. Purdue Model Implementation in the Shipping Control Systems. In Proceedings of the 2022 10th International Scientific Conference on Computer Science (COMSCI), Sofia, Bulgaria, 30 May–2 June 2022. [Google Scholar] [CrossRef]
- Longo, G.; Orlich, A.; Musante, S.; Merlo, A.; Russo, E. MaCySTe: A virtual testbed for maritime cybersecurity. SoftwareX 2023, 23, 101426. [Google Scholar] [CrossRef]
- Caprolu, M.; Pietro, R.; Raponi, S.; Sciancalepore, S.; Tedeschi, P. Vessels Cybersecurity: Issues, Challenges, and the Road Ahead. IEEE Commun. Mag. 2020, 58, 90–96. [Google Scholar] [CrossRef]
- Ben Farah, M.A.; Ukwandu, E.; Hindy, H.; Brosset, D.; Bures, M.; Andonovic, I.; Bellekens, X. Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends. Information 2022, 13, 22. [Google Scholar] [CrossRef]
- Avanesova, T.P.; Gruzdeva, L.K.; Iuskaev, R.A.; Yu Gruzdev, D.; Somko, M.L. Analysis of cyber-security aspects both ashore and at sea. IOP Conf. Ser. Earth Environ. Sci. 2021, 872, 012024. [Google Scholar] [CrossRef]
- ISO 27001:2013; Information Technology—Security Techniques—Information Security Management Systems—Requirements, 2nd ed. International for Standardization and International Electrotechnical Commission (ISO/IEC): Geneva, Switzerland,, 2013. Available online: https://www.iso.org/contents/data/standard/05/45/54534.html (accessed on 1 January 2024).
- ISO 19847:2018; Ships and Marine Technology—Shipboard Data Servers to Share Field Data at Sea, 1st ed. ISO: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/66405.html (accessed on 1 January 2024).
- Aksentijevic, S.; Tijan, E.; Čišić, D. Modeling of economically sustainable information security management systems in seaport clusters. Pomorstvo 2014, 28, 56–64. [Google Scholar]
- Edwards, J.; Aparicio-Navarro, F.J.; Maglaras, L.; Douligeris, C. FFDA: A novel Four-Factor Distributed Authentication mechanism. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience, CSR 2022, Rhodes, Greece, 27–29 July 2022; pp. 376–381. [Google Scholar] [CrossRef]
- Senarak, C. Port cybersecurity and threat: A structural model for prevention and policy development. Asian J. Shipp. Logist. 2021, 37, 20–36. [Google Scholar] [CrossRef]
- Koola, P. Cybersecurity: A deep dive into the abyss. Mar. Technol. Soc. J. 2018, 52, 31–43. [Google Scholar] [CrossRef]
- Kayisoglu, G.; Bolat, P.; Tam, K. Evaluating SLIM-based human error probability for ECDIS cybersecurity in maritime. J. Navig. 2022, 75, 1364–1388. [Google Scholar] [CrossRef]
- Bacasdoon, J.; Bolmsten, J. A Multiple Case Study of METI Cybersecurity Education and Training: A Basis for the Development of a Guiding Framework for Educational Approaches. TransNav 2022, 16, 319–334. [Google Scholar] [CrossRef]
- Raimondi, M.; Longo, G.; Merlo, A.; Armando, A.; Russo, E. Training the Maritime Security Operations Centre Teams. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience, CSR 2022, Rhodes, Greece, 27–29 July 2022; pp. 388–393. [Google Scholar] [CrossRef]
- Yoo, J.; Jo, Y. Formulating Cybersecurity Requirements for Autonomous Ships Using the SQUARE Methodology. Sensors 2023, 23, 5033. [Google Scholar] [CrossRef] [PubMed]
- Søner, Ø.; Kayisoglu, G.; Bolat, P.; Tam, K. Cybersecurity risk assessment of VDR. J. Navig. 2023, 76, 20–37. [Google Scholar] [CrossRef]
- Oruc, A. Ethical Considerations in Maritime Cybersecurity Research. TransNav 2022, 16, 309–318. [Google Scholar] [CrossRef]
- Wang, D.; He, T.; Lou, Y.; Pang, L.; He, Y.; Chen, H.H. Double-Edge Computation Offloading for Secure Integrated Space-Air-Aqua Networks. IEEE Internet Things J. 2023, 10, 15581–15593. [Google Scholar] [CrossRef]
- Ilcev, D. Software Solutions for GMDSS Network and Equipment. TransNav 2022, 16, 463–472. [Google Scholar] [CrossRef]
- Freire, W.P.; Melo, W.S.; Do Nascimento, V.D.; Nascimento, P.R.M.; de Sá, A.O. Towards a Secure and Scalable Maritime Monitoring System Using Blockchain and Low-Cost IoT Technology. Sensors 2022, 22, 4895. [Google Scholar] [CrossRef]
- Min, L.; Li, J.; He, Y.; Wang, W. Secure Rate-Splitting Multiple Access for Maritime Cognitive Radio Network: Power Allocation and UAV’s Location Optimization. J. Mar. Sci. Eng. 2023, 11, 1012. [Google Scholar] [CrossRef]
- Khandker, S.; Turtiainen, H.; Costin, A.; Hamalainen, T. Cybersecurity Attacks on Software Logic and Error Handling within AIS Implementations: A Systematic Testing of Resilience. IEEE Access 2022, 10, 29493–29505. [Google Scholar] [CrossRef]
- Shyshkin, O. Cybersecurity Providing for Maritime Automatic Identification System. In Proceedings of the 2022 IEEE 41st International Conference on Electronics and Nanotechnology, ELNANO 2022—Proceedings, Kyiv, Ukraine, 10–14 October 2022; pp. 736–740. [Google Scholar] [CrossRef]
- Arumugam, M.; Parasuraman, K. Optimized Routing and Security in Maritime Safety Applications. In Proceedings of the International Conference on Circuit Power and Computing Technologies (ICCPCT), Kollam, India, 10–11 August 2023; pp. 1636–1641. [Google Scholar] [CrossRef]
- Yang, T.; Cui, Z.; Alshehri, A.H.; Wang, M.; Gao, K.; Yu, K. Distributed Maritime Transport Communication System with Reliability and Safety Based on Blockchain and Edge Computing. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2296–2306. [Google Scholar] [CrossRef]
- Rath, S.; Intriago, A.; Sengupta, S.; Konstantinou, C. Lost at Sea: Assessment and Evaluation of Rootkit Attacks on Shipboard Microgrids. In Proceedings of the 2023 IEEE Electric Ship Technologies Symposium, ESTS 2023, Alexandria, VA, USA, 1–4 August 2023; pp. 534–541. [Google Scholar] [CrossRef]
- Ravi, R.V.; Goyal, S.; Aggarwal, A.; Bhala, T. Secure Image Transmission Using 2D ECT and Latin Square Algorithm for IoUT Systems. Procedia Comput. Sci. 2022, 215, 299–308. [Google Scholar] [CrossRef]
- Wolsing, K.; Saillard, A.; Bauer, J.; Wagner, E.; Van Sloun, C.; Fink, I.B.; Schmidt, M.; Wehrle, K.; Henze, M. Network Attacks Against Marine Radar Systems: A Taxonomy, Simulation Environment, and Dataset. In Proceedings of the 2022 IEEE 47th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 26–29 September 2022; pp. 114–122. [Google Scholar] [CrossRef]
- Onishchenko, O.; Shumilova, K.; Volyanskyy, S.; Volyanskaya, Y.; Volianskyi, Y. Ensuring Cyber Resilience of Ship Information Systems. TransNav 2022, 16, 43–50. [Google Scholar] [CrossRef]
- Leite Junior, W.; de Moraes, C.; de Albuquerque, C.; Machado, R.; de Sá, A. A Triggering Mechanism for Cyber-Attacks in Naval Sensors and Systems. Sensors 2021, 21, 3195. [Google Scholar] [CrossRef]
- Aziz, A.; Tedeschi, P.; Sciancalepore, S.; Pietro, R. SecureAIS—Securing Pairwise Vessels Communications. In Proceedings of the 2020 IEEE Conference on Communications and Network Security, CNS 2020, Avignon, France, 29 June–1 July 2020. [Google Scholar] [CrossRef]
- Shipunov, I.; Nyrkov, A.; Korotkov, V.; Alimov, O.; Knysh, T. Principles of using modern IT trends in maritime shipping. E3S Web Conf. 2020, 203, 05005. [Google Scholar] [CrossRef]
- Akdağ, M.; Solnør, P.; Johansen, T.A. Collaborative collision avoidance for Maritime Autonomous Surface Ships: A review. Ocean Eng. 2022, 250, 110920. [Google Scholar] [CrossRef]
- Canepa, M.; Ballini, F.; Dalaklis, D.; Vakili, S.; Hernandez, L. CR CyberMar as a solution path towards cybersecurity soundness in maritime logistics domain. Trans. Marit. Sci. 2021, 10, 147–153. [Google Scholar] [CrossRef]
- Wiseman, Y. Protecting seaport communication system by steganography based procedures. Int. J. Secur. Its Appl. 2014, 8, 25–36. [Google Scholar] [CrossRef]
- Lin, T.; Zhao, Y.; Zhang, H.; Li, G.; Zhang, J. Research on Information Security System of Ship Platform Based on Cloud Computing. J. Phys. Conf. Ser. 2021, 1802, 042032. [Google Scholar] [CrossRef]
- Carter, J.; Narman, H.; Cosgun, O.; Liu, J. Trade-off model of fog-cloud computing for space information networks. In Proceedings of the 2020 IEEE Cloud Summit, Cloud Summit 2020, Harrisburg, PA, USA, 21–22 October 2020; pp. 91–96. [Google Scholar] [CrossRef]
- Vangala, A.; Maheshwari, R.; Das, A.K.; Pal, S. Cloud-Assisted Security Framework for Drone-Enabled Offshore Communications. In Proceedings of the IEEE INFOCOM 2023—Conference on Computer Communications Workshops, INFOCOM WKSHPS 2023, Hoboken, NJ, USA, 20 May 2023. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, P.; Wu, B.; Wan, C.; Yang, Z. A trustable architecture over blockchain to facilitate maritime administration for MASS systems. Reliab. Eng. Syst. Saf. 2022, 219, 108246. [Google Scholar] [CrossRef]
- Li, C. Electronic countermeasure technology of supporting ship intelligent navigation. In Proceedings of the ICISCAE 2021: 2021 4th International Conference on Information Systems and Computer Aided Education, Dalian, China, 24–26 September 2021; pp. 2504–2508. [Google Scholar] [CrossRef]
- Solnør, P.; Volden, Ø.; Gryte, K.; Petrovic, S.; Fossen, T.I. Hijacking of unmanned surface vehicles: A demonstration of attacks and countermeasures in the field. J. Field Robot. 2022, 39, 631–649. [Google Scholar] [CrossRef]
- Antonopoulos, M.; Drainakis, G.; Ouzounoglou, E.; Papavassiliou, G.; Amditis, A. Design and proof of concept of a prediction engine for decision support during cyber range attack simulations in the maritime domain. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience, CSR 2022, Rhodes, Greece, 27–29 July 2022; pp. 305–310. [Google Scholar] [CrossRef]
- Maeder, C.; Sohr, K.; Nguempnang, R.; Meyer-Larsen, N.; Müller, R. Modeling and Validating Role-Based Authorization Policies for a Port Communication System with UML and OCL. J. Object Technol. 2020, 19, 1–14. [Google Scholar] [CrossRef]
- Ruhland, L.; Schmidt, M.; Bauer, J.; Padilla, E. Keeping the Baddies Out and the Bridge Calm: Embedded Authentication for Maritime Networks. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications, ISNCC 2022, Shenzhen, China, 19–22 July 2022. [Google Scholar] [CrossRef]
- Le, W.; Moros-Daza, A.; Jubiz-Diaz, M.; Voß, S. A Blockchain Prototype for Improving Electronic Seals on Container Shipping Operations. Sustainability 2023, 15, 11341. [Google Scholar] [CrossRef]
- Cichocki, R. State-Sponsored and Organized Crime Threats to Maritime Transportation Systems in the Context of the Attack on Ukraine. TransNav 2023, 17, 717–721. [Google Scholar] [CrossRef]
- Yigit, Y.; Kinaci, O.K.; Duong, T.Q.; Canberk, B. TwinPot: Digital Twin-assisted Honeypot for Cyber-Secure Smart Seaports. In Proceedings of the 2023 IEEE International Conference on Communications Workshops: Sustainable Communications for Renaissance, ICC Workshops 2023, Rome, Italy, 28 May–1 June 2023; pp. 740–745. [Google Scholar] [CrossRef]
- Gyamfi, E.; Ansere, J.A.; Kamal, M.; Tariq, M.; Jurcut, A. An Adaptive Network Security System for IoT-Enabled Maritime Transportation. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2538–2547. [Google Scholar] [CrossRef]
- Guo, J.; Guo, H. Real-Time Risk Detection Method and Protection Strategy for Intelligent Ship Network Security Based on Cloud Computing. Symmetry 2023, 15, 988. [Google Scholar] [CrossRef]
- Harris, D.A. Cyberwarfare Readiness in the Maritime Environment. In Proceedings of the International Conference on Enterprise Information Systems, ICEIS—Proceedings, Virtual, 25–27 April 2022; Volume 2, pp. 119–125. [Google Scholar] [CrossRef]
- Heering, D. Ensuring cybersecurity in shipping: Reference to Estonian shipowners. TransNav 2020, 14, 271–278. [Google Scholar] [CrossRef]
- Billard, D. Investigation of an alleged PLC hacking on sea vessels. J. Phys. Conf. Ser. 2019, 1297, 012035. [Google Scholar] [CrossRef]
- Mileski, J.; Clott, C.; Galvao, C. Cyberattacks on ships: A wicked problem approach. Marit. Bus. Rev. 2018, 3, 414–430. [Google Scholar] [CrossRef]
- Hadjidimitriou, N.S.; Renzi, G.; Apruzzese, M.; Perboli, G.; Musso, S. Identifying 5G technology enablers in the maritime sector using survey and Twitter data. In Proceedings of the International Computer Software and Applications Conference, Torino, Italy, 26–30 June 2023; pp. 1897–1902. [Google Scholar] [CrossRef]
- Amro, A.; Oruc, A.; Gkioulos, V.; Katsikas, S. Navigation Data Anomaly Analysis and Detection. Information 2022, 13, 104. [Google Scholar] [CrossRef]
- Lofu, D.; Gennaro, P.D.; Tedeschi, P.; Noia, T.D.; Sciascio, E.D. URANUS: Radio Frequency Tracking, Classification and Identification of Unmanned Aircraft Vehicles. IEEE Open J. Veh. Technol. 2023, 4, 921–935. [Google Scholar] [CrossRef]
- Le, H.V.; Nguyen, T.N.; Nguyen, H.N.; Le, L. An Efficient Hybrid Webshell Detection Method for Webserver of Marine Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2630–2642. [Google Scholar] [CrossRef]
- Liu, W.; Xu, X.; Wu, L.; Qi, L.; Jolfaei, A.; Ding, W.; Khosravi, M.R. Intrusion Detection for Maritime Transportation Systems with Batch Federated Aggregation. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2503–2514. [Google Scholar] [CrossRef]
- Bernal, A.; Monterrubio, S.; Fuente, J.; Crespo, R.; Verdu, E. Methodology for computer security incident response teams into IoT strategy. KSII Trans. Internet Inf. Syst. 2021, 15, 1909–1928. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Gkioulos, V.; Katsikas, S. A Systematic Literature Review on RAMS analysis for critical infrastructures protection. Int. J. Crit. Infrastruct. Prot. 2021, 33, 100427. [Google Scholar] [CrossRef]
- Wang, H.W.; Kuo, S.Y.; Chen, L.B. Exploring the relationship between internal information security, response cost, and security intention in container shipping. Appl. Sci. 2021, 11, 2609. [Google Scholar] [CrossRef]
- Carreras Guzman, N.; Wied, M.; Kozine, I.; Lundteigen, M. Conceptualizing the key features of cyber-physical systems in a multi-layered representation for safety and security analysis. Syst. Eng. 2020, 23, 189–210. [Google Scholar] [CrossRef]
| Category | References | Conclusions |
|---|---|---|
| Organizational Context | Jo (2022) [24], Karim et al. (2022) [25], Kaczerska et al. (2023) [26], Smith et al. (2018) [27], Sheng et al. (2017) [28] | The Organizational Context is key to cybersecurity risk management, considering unique aspects of an organization that influence decision-making. The reviewed papers highlight this through various perspectives. They underscore the need for comprehensive governance, importance of international legal reform, vital role of secure transactions, impact of evolving international laws and significance of technological dependencies all within each organization’s context. These emphasize the importance of the Organizational Context in formulating effective cybersecurity risk management strategies. |
| Risk Management Strategy | Jia et al. (2021) [14], Ahmed et al. (2022) [29], Abkowitz et al. (2011) [30], Melnyk et al. (2022) [31], Amro et al. (2023) [32], Rajaram et al. (2022) [33] | The role of strategic risk management is indispensable in establishing an effective cybersecurity posture. The studies explored highlight the holistic technical and human-centric approach needed in this rapidly evolving digital landscape. It becomes clear that understanding, assessing, and implementing tailored mitigation techniques across industries such as maritime and defense are imperative. Ultimately, robust risk management strategy fosters awareness, preparedness, and resilience, paving the way for secure digital operations. |
| Cybersecurity Supply Chain Risk Management | Kusrini et al. (2021) [34], Meland et al. (2022) [35], Longo et al. (2023) [36] | The studies collectively advocate for an integrated risk management strategy in the supply chain, utilizing both ISO 28001 standards [37] and innovative tools for threat assessment and anomaly detection, to bolster security and resilience in the face of evolving digital threats in industries such as maritime and defense. |
| Category | References | Conclusions |
|---|---|---|
| Asset Management | Oruc et al. (2022) [21], Oruc et al. (2022) [38], Kapalidis et al. (2022) [22] | Asset management serves as a vital cornerstone in ensuring cybersecurity within the maritime sector. The studies underline the significant role of industry-led initiatives and international guidelines, coupled with the adoption of advanced technologies, in managing assets effectively. Given the evolving threat landscape, the two studies advocate for a holistic approach to asset management, emphasizing the need for comprehensive strategies that interweave technology, people, and business processes, thereby fortifying the resilience of marine navigation systems against cyber threats. |
| Risk Assessment | Ashraf et al. (2023) [39], Charitos et al. (2022) [40], Lee et al. (2023) [41], Bolbot et al. (2020) [42], Martinie(2021)[43], Yoo et al. (2021) [44], Androjna et al. (2020) [45], Bolbot et al. (2023) [46], Melnyk et al. (2023) [47], Soner et al. (2024) [23], Park et al. (2023) [48], Eichenhofer et al. (2020) [49], Trimble et al. (2017) [50], Poyhonen et al. (2023) [51], Progoulakis et al. (2022) [52], Weaver et al. (2022) [53], Progoulakis et al. (2021) [54], Gurren et al. (2023) [55], Oruc et al. (2024) [56], Kechagias et al. (2022) [57], Putra et al. (2023) [58], Illiashenko et al. (2023) [59], Lee (2023) [60], Amro et al. (2023) [61] | The increasing integration of technology in maritime operations has amplified cybersecurity threats, highlighting the exigency for specialized and continuous risk assessment. Studies encompassing ship operations, software systems, smart ports and maritime security emphasize persistent evaluation and regulatory compliance to ensure maritime safety and security. As the technological landscape evolves, continuous refinement of risk assessment methodologies remains crucial to foresee and counter potential cyber threats, thereby reinforcing maritime cybersecurity. |
| Improvement | Chae et al. (2020) [62], Dghaym et al. (2021) [63], Shipunov et al. (2021) [64], Karim et al. (2022) [25], De la Peña Zarzuelo, I. et al. (2021) [15], Defaria et al. (2020) [65], Hopcraft et al. (2018) [66], Belev et al. (2022) [67], Longo et al. (2023) [68], McGillivary (2018) [18], Caprolu et al. (2020) [69], Hopcraft et al. (2018) [20], Ben Farah et al. (2022) [70], Avanesova et al. (2021) [71], Ashraf et al. (2023) [39] | The Improvement category, stresses the continual enhancement of cybersecurity practices. Research highlights include the exploration of Maritime Autonomous Surface Ship technologies, underscoring the need for improved decision-making systems. Importance is also placed on the regulation of autonomous systems and evolving technologies for enhanced security. Further studies focus on the defense against and mitigation of cybersecurity threats within the maritime industry, advocating for effective risk analysis and controls to bolster information protection. Collectively, these studies underline the need for continuous improvements, implementation of effective security policies and regulations, nurturing resilience, and adaptability in maritime cybersecurity in the face of emerging threats. |
| Category | References | Conclusions |
|---|---|---|
| Identity Management, Authentication and Access Control | Aksentijevic et al. (2014) [74], Edwards et al. (2022) [75] | The NIST CSF emphasizes the need for Identity Management, Authentication, and Access Control in maritime cybersecurity. Research shows that secure management systems and multi-factor authentication improve security without sacrificing usability. It’s crucial to balance these aspects in the digital maritime industry, with ongoing advancements needed to keep systems resilient in a interconnected world. |
| Awareness and Training | Senarak et al. (2022) [76], Hopcraft et al. (2018) [20], Alcaide et al. (2020) [16], Koola et al. (2018) [77], Kayisoglu et al. (2022) [78], Bacasdoon et al. (2022) [79], Longo et al. (2023) [68], Raimondi et al. (2022) [80] | The literature highlights the vital importance of education and training in enhancing maritime cybersecurity. It stresses the need for widespread cybersecurity knowledge throughout the industry, including ports, supply chains, and interfaces. The consensus is clear on the need for specialized and practical training solutions to improve maritime cyber defenses. These initiatives aim to increase awareness and establish a robust cyber-secure culture within the maritime sector. |
| Data Security | Lee et al. (2023) [60], Yoo et al. (2021) [81], Soner et al. (2023) [82], Oruc et al. (2022) [83], Wang et al. (2023) [84], Ilcev et al. (2022) [85], Freire et al. (2022) [86], Lingtong Min et al. (2023) [87], Khandker et al. (2022) [88], Shyshkin et al. (2022) [89], Arumugam et al. (2023) [90], Yang et al. (2023) [91], Rath et al. (2023) [92], Ravi et al. (2022) [93], Wolsing et al. (2022) [94], Onishchenko et al. (2022) [95] | The reviewed literature highlights the crucial role of robust data security measures in the increasingly digital and interconnected maritime domain. Key findings include the importance of applying technologies like AI and blockchain, using secure protocols, and maintaining ethical standards in cybersecurity research to protect shipboard data, secure communication systems, and ensure the integrity of navigation data. This underscores the urgent need to safeguard maritime systems and data from cyber threats, focusing on comprehensive and proactive approaches to bolster the resilience and security of maritime operations. |
| Platform Security | Leite Junior et al. (2021) [96], Khandker et al. (2022) [88], Aziz et al. (2020) [97], Shipunov et al. (2020) [98], Shipunov et al. (2021) [64], Koola et al. (2018) [77], Akdag et al. (2022) [99] | The Platform Security category focuses on aligning the management of an organization’s hardware, software, and services with its risk strategy. It highlights the importance of proper configuration management and secure software development to protect the integrity, availability, and confidentiality of platforms. This is crucial for enhancing maritime cybersecurity, including the protection of AIS systems and maritime operations. By adopting advanced algorithms and preventive measures for better decision-making and collision avoidance, organizations can boost their cybersecurity resilience and create a safer digital space. |
| Technology Infrastructure Resilience | Canepa et al. (2021) [100], Meyer-Larsen et al. (2018) [19], Wiseman et al. (2014) [101], Lin et al. (2021) [102], Carter et al. (2020) [103], Longo et al. (2023) [68], Freire et al. (2022) [86], Vangala et al. (2023) [104], Wang et al. (2022) [105], Li et al. (2021) [106], Sölnör et al. (2022) [107], Antonopoulos et al. (2022) [108], Gürren et al. (2023) [55], Maeder et al. (2020) [109], Kechagias et al. (2022) [57], Ruhland et al. (2022) [110], Le et al. (2023) [111], Yang et al. (2023) [91] | Our research underscores the critical role of Technology Infrastructure Resilience in safeguarding an organization’s tech assets. This includes cybersecurity for ports and autonomous maritime vehicles, utilizing tools like blockchain, cyber-attack simulations, and image encryption for protection. Advancements in cloud computing, 5G, and open-source contribute to data security and service excellence. To counter cyber threats, risk management, updating legacy systems, and reliable communication are essential for continuous operations. Effective technology infrastructure management is key to bolstering maritime defenses and resilience in a dynamic digital landscape. |
| Category | References | Conclusions |
|---|---|---|
| Continuous Monitoring | Cichocki et al. (2023) [112], Androjna, A. et al. (2021) [13], Androjna et al. (2021) [17], Yigit et al. (2023) [113], Longo et al. (2023) [36], Gyamfi et al. (2023) [114], Guo et al. (2023) [115], Harris et al. (2022) [116] | Continuous Monitoring is crucial for detecting anomalies in the maritime sector’s physical and digital realms. It requires constant oversight of networks, user activities, and technology, including third-party services and system components. Highlighted vulnerabilities in critical technologies like AIS and GNSS underscore the need for persistent surveillance. Advanced tools like Digital Twin technology and real-time risk detection enhance system defense. Ongoing enhancements in monitoring are essential to counter evolving cybersecurity threats. |
| Adverse Event Analysis | Heering, D. et al. (2020) [117], Billard, D. et al. (2019) [118], Mileski et al. (2018) [119], Caprolu, M. et al. (2020) [69], Hadjidimitriou et al. (2023) [120], Amro navigation, (2022) [121], Arumugam et al. (2023) [90], Rath et al., (2023) [92], Wolsing et al. (2022) [94], Lofu et al., (2023) [122], Le et al. (2023) [123], Liu et al. (2023) [124] | The Adverse Event Analysis category is key to managing cybersecurity risks in the maritime sector, focusing on detecting and responding to unusual activities indicative of threats. Research explores system vulnerabilities, including shipboard power, maritime radar, autonomous ships, and IoT. Findings highlight the need for cybersecurity training, securing communication systems, and leveraging technologies like 5G. Innovations such as genetic algorithm-based ANN classifiers and CNN-MLP intrusion detection systems, along with machine learning, are critical for improving threat detection. With the maritime industry’s growing complexity, continuous research and vigilance in anomaly detection are essential for strong cybersecurity. |
| Category | References | Conclusions |
|---|---|---|
| Incident Management | Bernal, A. et al. (2021) [125], Onishchenko et al. (2022) [95], Rath et al. (2023) [92] | Incident Management is crucial in cybersecurity, as outlined by NIST CSF v2.0. It’s a methodical approach to manage cyber incidents from detection to recovery, involving third-party coordination. Researchers worldwide apply these principles to sectors like government and maritime. Unified guidelines, detailed response plans, and regular updates are key. This method enhances data security and cyber resilience. |
| Incident Analysis | Pirbhulal, S. et al. (2021) [126], Wang et al. (2021) [127], Carreras Guzman, N. et al. (2020) [128] | Incident analysis is key for cybersecurity. It shapes response tactics, aids recovery, and improves security practices. Deep analysis clarifies complexities, underscores the need for robust information security, and highlights cyber-physical system safety. Across various domains, detailed analysis is vital for managing and reducing cyber incidents. |
| Category | References | Conclusions |
|---|---|---|
| Incident Recovery Plan Execution | Weaver et al. (2022) [53], Koola et al. (2018) [77] | Integrating NIST v2.0 Incident Recovery Plan Execution into company strategies is vital for cybersecurity resilience. Recovery plans aim for quick, effective incident handling to minimize disruption and damage. Research highlights unique strategies, like optimization algorithms, to combat issues like data loss. These findings stress the importance of adept recovery planning in boosting cybersecurity robustness. With rapid tech progress, recovery strategies must evolve to protect systems and assets effectively. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dimakopoulou, A.; Rantos, K. Comprehensive Analysis of Maritime Cybersecurity Landscape Based on the NIST CSF v2.0. J. Mar. Sci. Eng. 2024, 12, 919. https://doi.org/10.3390/jmse12060919
Dimakopoulou A, Rantos K. Comprehensive Analysis of Maritime Cybersecurity Landscape Based on the NIST CSF v2.0. Journal of Marine Science and Engineering. 2024; 12(6):919. https://doi.org/10.3390/jmse12060919
Chicago/Turabian StyleDimakopoulou, Anastasia, and Konstantinos Rantos. 2024. "Comprehensive Analysis of Maritime Cybersecurity Landscape Based on the NIST CSF v2.0" Journal of Marine Science and Engineering 12, no. 6: 919. https://doi.org/10.3390/jmse12060919
APA StyleDimakopoulou, A., & Rantos, K. (2024). Comprehensive Analysis of Maritime Cybersecurity Landscape Based on the NIST CSF v2.0. Journal of Marine Science and Engineering, 12(6), 919. https://doi.org/10.3390/jmse12060919








