What Message Characteristics Make Social Engineering Successful on Facebook: The Role of Central Route, Peripheral Route, and Perceived Risk
Abstract
:1. Introduction
2. Context and Motivation
2.1. Social Engineering in SNSs
2.2. Choosing Facebook as a Context
3. Theoretical Framing and Pre-Study
3.1. Theoretical Base
3.2. Central Route of Persuasion (Argument Quality)
3.3. Perceived Risk
3.4. Peripheral Route of Persuasion
3.5. Interaction between Central Route Dimentions, Perceived Risk, and Peripheral Cues
4. Method
4.1. Experimental Design
4.2. Using Fractional Factorial Design
4.3. Measurement
4.4. Sample and Procedures
5. Results
5.1. Factor Analysis and Data Screening
5.2. Hypotheses Testing
5.2.1. Testing Hypotheses H1–H3
5.2.2. Testing Hypotheses H4–H12
5.3. Demographics Analysis
5.4. Testing Mediation Effects
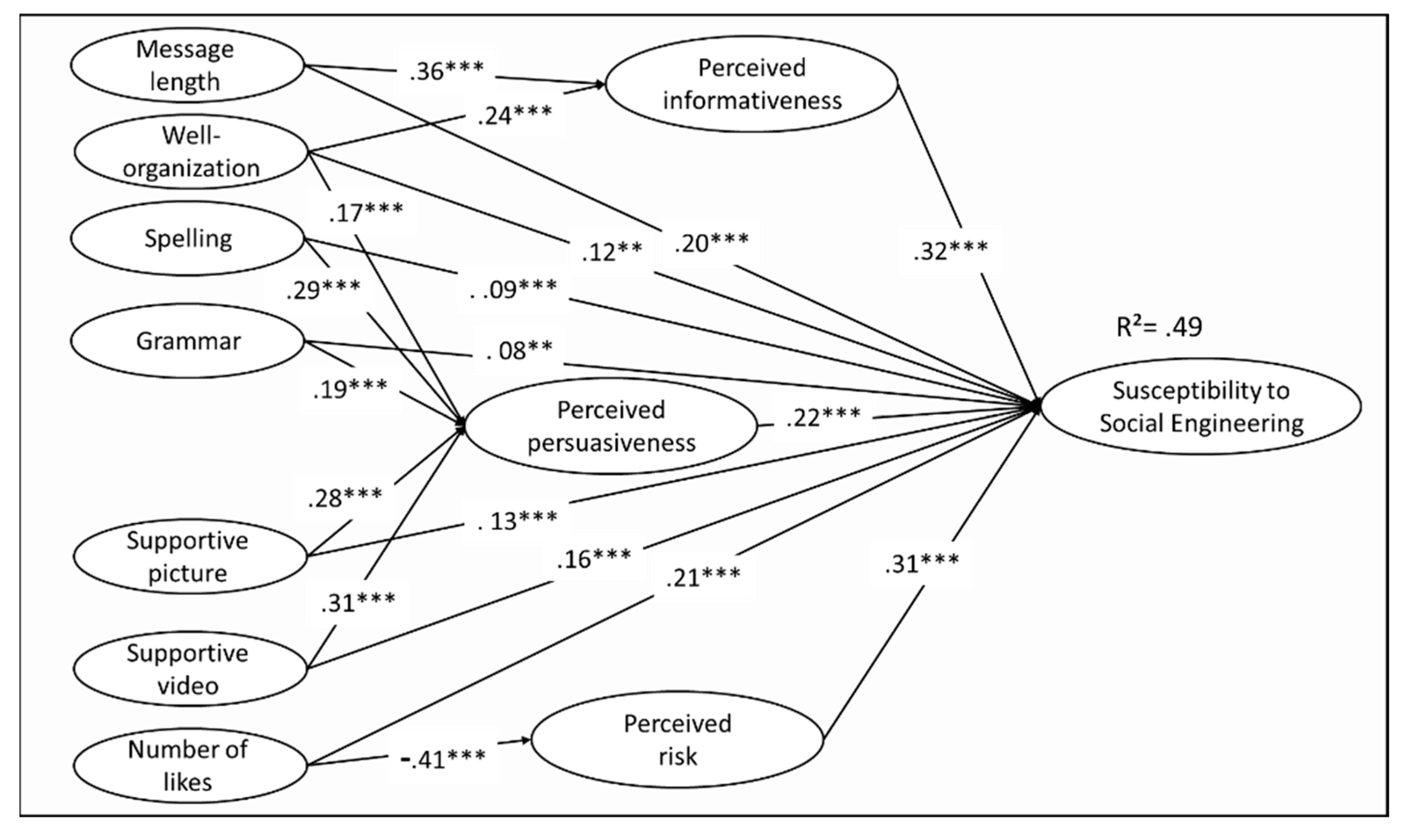
5.5. Structural Model and Fitting Assessment
6. Discussion and Conclusion
6.1. Implication for Research and Practice
6.2. Limitations and Future Work
Funding
Conflicts of Interest
Appendix
- ◻
- Definitely yes
- ◻
- Very probably yes
- ◻
- Probably yes
- ◻
- Very probably no
- ◻
- Definitely no

References
- Hadnagy, C. Social Engineering: The Art of Human Hacking; Wiley: Hoboken, NJ, USA, 2010. [Google Scholar]
- Thornburgh, T. Social Engineering: The Dark Art. In Proceedings of the 1st Annual Conference on Information Security Curriculum Development, Kennesaw, GA, USA, 8 October 2004; ACM: New York, NY, USA; pp. 133–135. [Google Scholar]
- Workman, M. Gaining Access with Social Engineering: An Empirical Study of the Threat. Inf. Syst. Secur. 2007, 16, 315–331. [Google Scholar] [CrossRef]
- Grazioli, S. Where Did They Go Wrong? An Analysis of the Failure of Knowledgeable Internet Consumers to Detect Deception over the Internet. In Group Decision and Negotiation; Springer: Berlin/Heidelberg, Germany, 2004; Volume 13, pp. 149–172. [Google Scholar]
- Qi, T. An Investigation of Heuristics of Human Judgment in Detecting Deception and Potential Implications in Countering Social Engineering. In Proceedings of the 2007 IEEE Intelligence and Security Informatics, New Brunswick, NJ, USA, 23–24 May 2007; pp. 152–159. [Google Scholar]
- Kvedar, D.; Nettis, M.; Fulton, S.P. The use of formal social engineering techniques to identify weaknesses during a computer vulnerability competition. J. Comput. Sci. Coll. 2010, 26, 80–87. [Google Scholar]
- Algarni, A.; Xu, Y.; Chan, T.; Tian, Y.-C. Social Engineering in Social Networking Sites: Affect-Based Model. In Proceedings of the 8th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 9–12 December 2013; pp. 508–515. [Google Scholar]
- Algarni, A.; Xu, Y.; Chan, T.; Tian, Y.-C. Toward Understanding Social Engineering. In Law & Practice: Critical Analysis and Legal Reasoning; Sylvia, K., Ed.; International Association of IT Lawyers: Copenhagen, Denmark, 2013; pp. 279–300. [Google Scholar]
- Braun, R.; Esswein, W. Towards a Conceptualization of Corporate Risks in Online Social Networks: A Literature Based Overview of Risks. In Proceedings of the 17th IEEE International Enterprise Distributed Object Computing Conference (EDOC), Vancouver, BC, Canada, 9–13 September 2013; pp. 267–274. [Google Scholar]
- Chitrey, A.; Singh, D.; Singh, V. A Comprehensive Study of Social Engineering Based Attacks in India to Develop a Conceptual Model. Int. J. Inf. Netw. Secur. 2012, 1, 45–53. [Google Scholar] [CrossRef]
- Dimensional-Research. The Risk of Social Engineering on Information Security: A Survey of It Professionals; Technical Report; Dimensional-Research: Long Beach, CA, USA, 2011. [Google Scholar]
- Jagatic, T.N.; Johnson, N.A.; Jakobsson, M.; Menczer, F. Social phishing. Commun. ACM 2007, 50, 94–100. [Google Scholar] [CrossRef]
- Nagy, J.; Pecho, P. Social Networks Security. In Proceedings of the Third International Conference on Emerging Security Information, Systems and Technologies, Athens/Glyfada, Greece, 18–23 June 2009; pp. 321–325. [Google Scholar]
- Mazzuca, T. 7 Scary Findings from the 2014 Symantec Internet Security Threat Report; Property & Casualty 360; Red Rock Casino Resort & Spa: Las Vegas, NV, USA, 2014. [Google Scholar]
- Chaiken, S.; Eagly, A.H. Heuristic and Systematic Information Processing within and Beyond the Persuasion Context; In Unintended Thought; Wiley: Hoboken, NJ, USA, 1989; pp. 212–252. [Google Scholar]
- Chen, S.; Chaiken, S. The Heuristic-Systematic Model in Its Broader Context. In Dual-Process Theories in Social Psychology; Guilford Press: New York, NY, USA, 1999; pp. 73–96. [Google Scholar]
- Darke, P.R.; Freedman, J.L.; Chaiken, S. Percentage discounts, initial price, and bargain hunting: A heuristic-systematic approach to price search behavior. J. Appl. Psychol. 1995, 80, 580–586. [Google Scholar] [CrossRef]
- Petty, R.E.; Cacioppo, J. Elaboration Likelihood Model. In Handbook of Theories of Social Psychology; Sage: London, UK, 1986. [Google Scholar]
- Petty, R.E.; Cacioppo, J.T. The elaboration likelihood model of persuasion. Adv. Exp. Soc. Psychol. 1986, 19, 123–205. [Google Scholar]
- Petty, R.E.; Cacioppo, J.T. The Elaboration Likelihood Model of Persuasion. In Communication and Persuasion; Springer: Berlin/Heidelberg, Germany, 1986; pp. 1–24. [Google Scholar]
- Algarni, A.; Xu, Y.; Chan, T. Susceptibility to Social Engineering in Social Networking Sites: The Case of Facebook. In Proceedings of the 36th International Conference on Information Systems (ICIS 2015), Fort Worth, TX, USA, 13–16 December 2015. [Google Scholar]
- Algarni, A.; Xu, Y.; Chan, T. Measuring Source Credibility of Social Engineering Attackers on Facebook. In Proceedings of the 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 3686–3695. [Google Scholar]
- Algarni, A.; Xu, Y.; Chan, T. An empirical study on the susceptibility to social engineering in social networking sites: The case of Facebook. Eur. J. Inf. Syst. 2017, 1–27. [Google Scholar] [CrossRef]
- Gu, J.; Xu, Y.C.; Xu, H.; Zhang, C.; Ling, H. Privacy concerns for mobile app download: An elaboration likelihood model perspective. Decis. Support Syst. 2017, 94, 19–28. [Google Scholar] [CrossRef]
- Li, C.-Y. The effects of source credibility and argument quality on employees’ responses toward information system usage. Asia Pac. Manag. Rev. 2015, 20, 56–64. [Google Scholar] [CrossRef]
- Mun, Y.Y.; Yoon, J.J.; Davis, J.M.; Lee, T. Untangling the antecedents of initial trust in Web-based health information: The roles of argument quality, source expertise, and user perceptions of information quality and risk. Decis. Support Syst. 2013, 55, 284–295. [Google Scholar]
- Petty, R.E.; Cacioppo, J.T. Issue involvement can increase or decrease persuasion by enhancing message-relevant cognitive responses. J. Personal. Soc. Psychol. 1979, 37, 1915–1926. [Google Scholar] [CrossRef]
- Petty, R.E.; Cacioppo, J.T. The effects of involvement on responses to argument quantity and quality: Central and peripheral routes to persuasion. J. Personal. Soc. Psychol. 1984, 46, 69–81. [Google Scholar] [CrossRef]
- Petty, R.E.; Cacioppo, J.T.; Schumann, D. Central and peripheral routes to advertising effectiveness: The moderating role of involvement. J. Consum. Res. 1983, 10, 135–146. [Google Scholar] [CrossRef]
- Shin, S.Y.; Van Der Heide, B.; Beyea, D.; Dai, Y.N.; Prchal, B. Investigating moderating roles of goals, reviewer similarity, and self-disclosure on the effect of argument quality of online consumer reviews on attitude formation. Comput. Hum. Behav. 2017, 76, 218–226. [Google Scholar] [CrossRef]
- Maconachy, W.V.; Schou, C.D.; Ragsdale, D.; Welch, D. A Model for Information Assurance: An Integrated Approach. In Proceedings of the 2001 IEEE Workshop on Information Assurance and Security, West Point, NY, USA, 5–6 June 2001. [Google Scholar]
- Kumaraguru, P.; Cranshaw, J.; Acquisti, A.; Cranor, L.F.; Hong, J.; Blair, M.A.; Pham, T. School of Phish: A Real-Word Evaluation of Anti-Phishing Training (Cmu-Cylab-09-002); Carnegie Mellon University: Pittsburgh, PA, USA, 2009. [Google Scholar]
- Parrish, J.L., Jr.; Bailey, J.L.; Courtney, J.F. A Personality Based Model for Determining Susceptibility to Phishing Attacks; University of Arkansas: Little Rock, AR, USA, 2009. [Google Scholar]
- Pattinson, M.; Jerram, C.; Parsons, K.; McCormac, A.; Butavicius, M. Why do some people manage phishing e-mails better than others? Inf. Manag. Comput. Secur. 2012, 20, 18–28. [Google Scholar] [CrossRef]
- Sheng, S.; Holbrook, M.; Kumaraguru, P.; Cranor, L.F.; Downs, J. Who Falls for Phish? A Demographic Analysis of Phishing Susceptibility and Effectiveness of Interventions. In Proceedings of the 2010 SIGCHI Conference on Human Factors in Computing Systems, New York, NY, USA, 10–15 April 2010; pp. 373–382. [Google Scholar]
- Workman, M. Wisecrackers: A theory–grounded investigation of phishing and pretext social engineering threats to information security. J. Am. Soc. Inf. Sci. Technol. 2008, 59, 662–674. [Google Scholar] [CrossRef]
- Wright, R.T.; Jensen, M.L.; Thatcher, J.B.; Dinger, M.; Marett, K. Research Note-Influence Techniques in Phishing Attacks: An Examination of Vulnerability and Resistance. Inf. Syst. Res. 2014, 25, 385–400. [Google Scholar] [CrossRef]
- Algarni, A. Inattentional Blindness Factors that Make People Vulnerable to Security Threats in Social Networking Sites. J. Comput. 2019, 14, 184–194. [Google Scholar]
- Castillo, C.; Mendoza, M.; Poblete, B. Information Credibility on Twitter. In Proceedings of the 20th International Conference on the World Wide Web, Hyderabad, India, 28 March–1 April 2011; ACM: New York, NY, USA, 2011; pp. 675–684. [Google Scholar]
- Chu, Z.; Gianvecchio, S.; Wang, H.; Jajodia, S. Detecting automation of twitter accounts: Are you a human, bot, or cyborg? IEEE Trans. Depend. Secur. Comput. 2012, 9, 811–824. [Google Scholar] [CrossRef]
- Huber, M.; Kowalski, S.; Nohlberg, M.; Tjoa, S. Towards Automating Social Engineering Using Social Networking Sites. In Proceedings of the CSE’09 International Conference on Computational Science and Engineering, Vancouver, BC, Canada, 29–31 August 2009; pp. 117–124. [Google Scholar]
- McCord, M.; Chuah, M. Spam Detection on Twitter Using Traditional Classifiers. In Autonomic and Trusted Computing; Springer: Berlin/Heidelberg, Germany, 2011; pp. 175–186. [Google Scholar] [Green Version]
- Stringhini, G.; Kruegel, C.; Vigna, G. Detecting Spammers on Social Networks. In Proceedings of the 26th Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2010; pp. 1–9. [Google Scholar]
- Thomas, K.; McCoy, D.; Grier, C.; Kolcz, A.; Paxson, V. Trafficking Fraudulent Accounts: The Role of the Underground Market in Twitter Spam and Abuse. In Proceedings of the 22nd Annual USENIX Security Symposium (Usenix Sec 2013), Washington, DC, USA, 14–16 August 2013; pp. 195–210. [Google Scholar]
- Wang, A.H. Don’t Follow Me: Spam Detection in Twitter. In Proceedings of the 2010 International Conference on Security and Cryptography (SECRYPT), Athens, Greece, 26–28 July 2010; pp. 1–10. [Google Scholar]
- Algarni, A.; AlMakrami, H.; Alarifi, A. Toward Evaluating Trustworthiness of Social Networking Site Users: Reputation-Based Method. Arch. Bus. Res. 2019, 7. [Google Scholar] [CrossRef] [Green Version]
- Al Zamal, F.; Liu, W.; Ruths, D. Homophily and Latent Attribute Inference: Inferring Latent Attributes of Twitter Users from Neighbors. In Proceedings of the Sixth International AAAI Conference on Weblogs and Social Media (ICWSM), Dublin, Ireland, 4–8 June 2012; Association for the Advancement of Artificial Intelligence: Menlo Park, CA, USA, 2012; pp. 387–390. [Google Scholar]
- Burger, J.D.; Henderson, J.; Kim, G.; Zarrella, G. Discriminating Gender on Twitter. In Proceedings of the Conference on Empirical Methods in Natural Language Processing, Edinburgh, UK, 27–31 July 2011; pp. 1301–1309. [Google Scholar]
- Liu, W.; Ruths, D. What’s in a Name? Using First Names as Features for Gender Inference in Twitter; AAAI Spring Symposium: Analyzing Microtext; AAAI: Menlo Park, CA, USA, 2013. [Google Scholar]
- Mislove, A.; Lehmann, S.; Ahn, Y.-Y.; Onnela, J.-P.; Rosenquist, J.N. Understanding the Demographics of Twitter Users. In Proceedings of the Fifth International AAAI Conference on Weblogs and Social Media, Barcelona, Spain, 17–21 July 2011; Association for the Advancement of Artificial Intelligence: Menlo Park, CA, USA, 2011; pp. 1–4. [Google Scholar]
- Rao, D.; Paul, M.J.; Fink, C.; Yarowsky, D.; Oates, T.; Coppersmith, G. Hierarchical Bayesian Models for Latent Attribute Detection in Social Media. In Proceedings of the Fifth International AAAI Conference on Weblogs and Social Media, Barcelona, Spain, 17–21 July 2011; pp. 598–601. [Google Scholar]
- Cheung, C.M.; Chiu, P.Y.; Lee, M.K. Online social networks: Why do students use Facebook? Comput. Hum. Behav. 2011, 27, 1337–1343. [Google Scholar] [CrossRef]
- Papacharissi, Z. The virtual geographies of social networks: A comparative analysis of Facebook, LinkedIn and ASmallWorld. New Med. Soc. 2009, 11, 199–220. [Google Scholar] [CrossRef]
- Trumbo, C.W. Heuristic-systematic information processing and risk judgment. Risk Anal. 1999, 19, 391–400. [Google Scholar] [CrossRef] [PubMed]
- Trumbo, C.W. Information processing and risk perception: An adaptation of the Heuristic-Systematic model. J. Commun. 2002, 52, 367–382. [Google Scholar] [CrossRef]
- Lee, J.K.; Rao, H.R. Perceived risks, counter-beliefs, and intentions to use anti-/counter-terrorism websites: An exploratory study of government-citizens online interactions in a turbulent environment. Decis. Support Syst. 2007, 43, 1431–1449. [Google Scholar] [CrossRef]
- Cheung, C.M.; Thadani, D.R. The impact of electronic word-of-mouth communication: A literature analysis and integrative model. Decis. Support Syst. 2012, 54, 461–470. [Google Scholar] [CrossRef]
- Li, M.; Kankanhalli, A.; Kim, S.H. Which ideas are more likely to be implemented in online user innovation communities? An empirical analysis. Decis. Support Syst. 2016, 84, 28–40. [Google Scholar] [CrossRef]
- Cheung, M.Y.; Luo, C.; Sia, C.L.; Chen, H. Credibility of electronic word-of-mouth: Informational and normative determinants of on-line consumer recommendations. Int. J. Electron. Commer. 2009, 13, 9–38. [Google Scholar] [CrossRef]
- Zhang, K.Z.; Zhao, S.J.; Cheung, C.M.; Lee, M.K. Examining the influence of online reviews on consumers’ decision-making: A heuristic–systematic model. Decis. Support Syst. 2014, 67, 78–89. [Google Scholar] [CrossRef]
- Zhang, Y. Responses to humorous advertising: The moderating effect of need for cognition. J. Advert. 1996, 25, 15–32. [Google Scholar] [CrossRef]
- Burke, K. Language as Symbolic Action: Essays on Life, Literature, and Method; University of California Press: Oakland, CA, USA, 1966. [Google Scholar]
- Cheung, C.M.; Lee, M.K.; Rabjohn, N. The impact of electronic word-of-mouth: The adoption of online opinions in online customer communities. Internet Res. 2008, 18, 229–247. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J.-N. Understanding the product information inference process in electronic word-of-mouth: An objectivity–subjectivity dichotomy perspective. Inf. Manag. 2009, 46, 302–311. [Google Scholar] [CrossRef]
- Sussman, S.W.; Siegal, W.S. Informational influence in organizations: An integrated approach to knowledge adoption. Inf. Syst. Res. 2003, 14, 47–65. [Google Scholar] [CrossRef]
- Zhang, W.; Watts, S.A. Capitalizing on content: Information adoption in two online communities. J. Assoc. Inf. Syst. 2008, 9, 3. [Google Scholar]
- Ducoffe, R.H. Advertising value and advertising on the web. J. Advert. Res. 1996, 36, 21. [Google Scholar]
- Rosenstock, I.M. Historical origins of the health belief model. Health Educ. Behav. 1974, 2, 328–335. [Google Scholar] [CrossRef]
- Posey, C.; Roberts, T.L.; Lowry, P.B.; Hightower, R.T. Bridging the divide: A qualitative comparison of information security thought patterns between information security professionals and ordinary organizational insiders. Inf. Manag. 2014, 51, 551–567. [Google Scholar] [CrossRef]
- Aldoory, L.; Van Dyke, M.A. The roles of perceived “shared” involvement and information overload in understanding how audiences make meaning of news about bioterrorism. J. Mass Commun. Q. 2006, 83, 346–361. [Google Scholar] [CrossRef]
- Grunig, J.E.; Moss, D.; MacMANUS, T. A Situational Theory of Publics: Conceptual History, Recent Challenges and New Research; In Public Relations Research: An International Perspective; International Thomson Business Press: Stamford, CT, USA, 1997; p. 48. [Google Scholar]
- Brafman, O.; Brafman, R. Click: The Forces Behind How We Fully Engage with People, Work, and Everything We Do; Crown Pub.: New York, NY, USA, 2011. [Google Scholar]
- Zimbardo, P. The Lucifer Effect: Understanding How Good People Turn Evil; Blackwell Publishing Ltd.: New York, NY, USA, 2007. [Google Scholar]
- Orgill, G.L.; Romney, G.W.; Bailey, M.G.; Orgill, P.M. The Urgency for Effective User Privacy-Education to Counter Social Engineering Attacks on Secure Computer Systems. In Proceedings of the 5th Conference on Information Technology Education, Salt Lake City, UT, USA, 28–30 October 2004; pp. 177–181. [Google Scholar]
- Pyszczynski, T.; Greenberg, J.; Solomon, S. Why Do We Need What We Need? A Terror Management Perspective on the Roots of Human Social Motivation. Psychol. Inq. 1997, 8, 1–20. [Google Scholar] [CrossRef]
- Cheung, C.M.; Lee, M.K. Trust in internet shopping: Instrumental development and validation through classical and modern approaches. Adv. Top. Glob. Inf. Manag. 2001, 1, 25–41. [Google Scholar] [CrossRef]
- Taking, R. Information Handling in Consumer Behaviour; Cox, D.F., Ed.; Boston Graduate School of Business Administration, Harvard University: Boston, MA, USA, 1967. [Google Scholar]
- Nicolaou, A.I.; McKnight, D.H. Perceived information quality in data exchanges: Effects on risk, trust, and intention to use. Inf. Syst. Res. 2006, 17, 332–351. [Google Scholar] [CrossRef]
- Cheung, C.M.; Chan, G.W.; Limayem, M. A critical review of online consumer behavior: Empirical research. J. Electron. Commer. Org. 2005, 3, 1–19. [Google Scholar] [CrossRef]
- Metzger, M.J.; Flanagin, A.J.; Eyal, K.; Lemus, D.R.; McCann, R.M. Credibility for the 21st century: Integrating perspectives on source, message, and media credibility in the contemporary media environment. Commun. Yearb. 2003, 27, 293–336. [Google Scholar] [CrossRef]
- Kane, G.C.; Alavi, M.; Labianca, G.J.; Borgatti, S.P. What’s Different About Social Media Networks? A Framework and Research Agenda. Mis Q. 2014, 38, 274–304. [Google Scholar] [CrossRef]
- Creswell, J.W. Qualitative Inquiry and Research Design: Choosing among Five Approaches; Sage Publications: Thousand Oaks, CA, USA, 2012. [Google Scholar]
- Sutton, S.G.; Arnold, V. Focus group methods: Using interactive and nominal groups to explore emerging technology-driven phenomena in accounting and information systems. Int. J. Account. Inf. Syst. 2013, 14, 81–88. [Google Scholar] [CrossRef]
- Hausman, A.V.; Siekpe, J.S. The effect of web interface features on consumer online purchase intentions. J. Bus. Res. 2009, 62, 5–13. [Google Scholar] [CrossRef]
- Metzger, M.J.; Flanagin, A.J. Credibility and trust of information in online environments: The use of cognitive heuristics. J. Pragmat. 2013, 59, 210–220. [Google Scholar] [CrossRef]
- Castillo, C.; Mendoza, M.; Poblete, B. Predicting information credibility in time-sensitive social media. Internet Res. 2013, 23, 560–588. [Google Scholar] [CrossRef] [Green Version]
- Yardley-Matwiejczuk, K.M. Role Play: Theory and Practice; Sage Publications: London, UK, 1997. [Google Scholar]
- Dhamija, R.; Tygar, J.D.; Hearst, M. Why Phishing Works. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Montréal, QC, Canada, 22–27 April 2006; pp. 581–590. [Google Scholar]
- Downs, J.S.; Holbrook, M.; Cranor, L.F. Behavioral Response to Phishing Risk. In Proceedings of the Anti-Phishing Working Groups 2nd Annual eCrime Researchers Summit, Pittsburgh, PA, USA, 4–5 October 2007; pp. 37–44. [Google Scholar]
- Furnell, S. Phishing: Can We Spot the Signs? Comput. Fraud Secur. 2007, 2007, 10–15. [Google Scholar] [CrossRef]
- Baltazar, J.; Costoya, J.; Flores, R. The real face of koobface: The largest web 2.0 botnet explained. Trend Micro Res. 2009, 5, 10. [Google Scholar]
- Baumhof, V.; Shipp, A. Zeus P2p Advancements and Mitb Attack Vectors; ThreatMetrix™ Labs Public Report; ThreatMetrix Inc.: San Jose, CA, USA, 2012; 2p. [Google Scholar]
- Clark, K. Five Notorious Facebook Attacks (Learn How to Protect Yourself). Soc. Med. 2013. Available online: http://www.hongkiat.com/blog/five-facebook-attacks/ (accessed on 2 March 2015).
- Sadeghian, A.; Zamani, M.; Shanmugam, B. Security Threats in Online Social Networks. In Proceedings of the 2013 International Conference on Informatics and Creative Multimedia (ICICM), Kuala Lumpur, Malaysia, 4–6 September 2013; pp. 254–258. [Google Scholar]
- Thomas, K.; Nicol, D.M. The Koobface Botnet and the Rise of Social Malware. In Proceedings of the 5th International Conference on Malicious and Unwanted Software (MALWARE), Nancy Lorraine, France, 19–20 October 2010; pp. 63–70. [Google Scholar]
- Albaum, G. The Likert Scale Revisited, J. Mark. Res. Soc. 1997, 39, 331–348. [Google Scholar] [CrossRef]
- Gunst, R.F.; Mason, R.L. Fractional factorial design. Wiley Interdiscip. Rev. Comput. Stat. 2009, 1, 234–244. [Google Scholar] [CrossRef]
- Dey, A. Orthogonal Fractional Factorial Designs; Wiley: New York, NY, USA, 1985. [Google Scholar]
- DeVellis, R.F. Scale Development: Theory and Applications; Sage Publications: Thousand Oaks, CA, USA, 2012. [Google Scholar]
- Ducoffe, R.H. How consumers assess the value of advertising. J. Curr. Issues Res. Advert. 1995, 17, 1–18. [Google Scholar] [CrossRef]
- Dowling, G.R.; Staelin, R. A model of perceived risk and intended risk-handling activity. J. Consum. Res. 1994, 21, 119–134. [Google Scholar] [CrossRef]
- Coates, J.F. In defense of Delphi. A review of Delphi assessment, expert opinion, forecasting, and group process by H. Sackman. Technol. Forecast. Soc. Chang. 1975, 7, 193–194. [Google Scholar] [CrossRef]
- Dalkey, N.; Helmer, O. An experimental application of the Delphi method to the use of experts. Manag. Sci. 1963, 9, 458–467. [Google Scholar] [CrossRef]
- Sivo, S.A.; Saunders, C.; Chang, Q.; Jiang, J.J. How low should you go? Low response rates and the validity of inference in IS questionnaire research. J. Assoc. Inf. Syst. 2006, 7, 351–414. [Google Scholar] [CrossRef]
- Tabachnick, B.G.; Fidell, L.S. Using Multivariate Statistics, 4th ed.; Allyn and Bacon: Boston, MA, USA, 2001. [Google Scholar]
- Osborne, J.; Waters, E. Four assumptions of multiple regression that researchers should always test, Practical assessment. Res. Eval. 2002, 8, 1–9. [Google Scholar]
- Klockars, A.J.; Sax, G. Multiple Comparisons; No. 61; Sage: London, UK, 1986. [Google Scholar]
- Cohen, J. Statistical Power Analysis for the Behavioral Sciences; Academic Press: New York, NY, USA, 1977. [Google Scholar]
- Recker, J. Scientific Research in Information Systems: A Beginner’s Guide; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Baron, R.M.; Kenny, D.A. The moderator–mediator variable distinction in social psychological research: Conceptual, strategic, and statistical considerations. J. Personal. Soc. Psychol. 1986, 51, 1173–1182. [Google Scholar] [CrossRef]
- Conger, A.J. A revised definition for suppressor variables: A guide to their identification and interpretation. Educ. Psychol. Meas. 1974, 34, 35–46. [Google Scholar] [CrossRef]
- MacKinnon, D.P.; Krull, J.L.; Lockwood, C.M. Equivalence of the mediation, confounding and suppression effect. Prev. Sci. 2000, 1, 173–181. [Google Scholar] [CrossRef] [PubMed]
- Rucker, D.D.; Preacher, K.J.; Tormala, Z.L.; Petty, R.E. Mediation analysis in social psychology: Current practices and new recommendations. Soc. Personal. Psychol. Compass 2011, 5, 359–371. [Google Scholar] [CrossRef]
- Anderson, J.C.; Gerbing, D.W. Structural equation modeling in practice: A review and recommended two-step approach. Psychol. Bull. 1988, 103, 411–423. [Google Scholar] [CrossRef]
- Hair, J.F.; Black, W.C.; Babin, B.J.; Anderson, R.E.; Tatham, R.L. Multivariate Data Analysis; Pearson Prentice Hall: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Hooper, D.; Coughlan, J.; Mullen, M. Structural Equation Modelling: Guidelines for Determining Model Fit. Electron. J. Bus. Res. Methods 2008, 6, 53–60. [Google Scholar]
- Darwish, A.; Zarka, A.E.; Aloul, F. Towards Understanding Phishing Victims’ Profile. In Proceedings of the International Conference on Computer Systems and Industrial Informatics (ICCSII), Sharjah, UAE, 18–20 December 2012; pp. 1–5. [Google Scholar]
- Vishwanath, A. Habitual Facebook Use and its Impact on Getting Deceived on Social Media. J. Comput. Med. Commun. 2015, 20, 83–98. [Google Scholar] [CrossRef]
- Hong, C.; Chen, Z.; Li, C. “Liking” and being “liked”: How are personality traits and demographics associated with giving and receiving “likes” on Facebook? Comput. Hum. Behav. 2017, 68, 292–299. [Google Scholar] [CrossRef]
- Lee, E.; Kim, Y.J.; Ahn, J. How do people use Facebook features to manage social capital? Comput. Hum. Behav. 2014, 36, 440–445. [Google Scholar] [CrossRef]
- Burrow, A.L.; Rainone, N. How many likes did I get? Purpose moderates links between positive social media feedback and self-esteem. J. Exp. Soc. Psychol. 2017, 69, 232–236. [Google Scholar] [CrossRef]
- Scissors, L.; Burke, M.; Wengrovitz, S. What’s in a Like? Attitudes and Behaviors Around Receiving Likes on Facebook. In Proceedings of the 19th ACM Conference on Computer-Supported Cooperative Work & Social Computing, San Francisco, CA, USA, 27 February–2 March 2016; pp. 1501–1510. [Google Scholar] [CrossRef]
- Meshi, D.; Morawetz, C.; Heekeren, H.R. Nucleus accumbens response to gains in reputation for the self relative to gains for others predicts social media use. Front. Hum. Neurosci. 2013, 7, 1–11. [Google Scholar] [CrossRef]
- Cao, J.; Basoglu, K.A.; Sheng, H.; Lowry, P.B. A Systematic Review of Social Networking Research in Information Systems. Commun. Assoc. Inf. Syst. 2014, 36, 1–41. [Google Scholar]
- Twitchell, D.P. Social Engineering in Information Assurance Curricula. In Proceedings of the 3rd Annual Conference on Information Security Curriculum Development, Kennesaw, GA, USA, 22–23 September 2006; pp. 191–193. [Google Scholar]
- Hogben, G. Security Issues and Recommendations for Online Social Networks; ENISA Position Paper; European Union Agency for Network and Information Security: Heraklion, Greece, 2007; Volume 1.
- Baird, C.; Parasnis, G. From social media to social customer relationship management. IEEE Eng. Manag. Rev. 2013, 41, 48–55. [Google Scholar] [CrossRef]
- Dam, J.-W.V.; Michel van de, V. Online profiling and clustering of Facebook users. Decis. Support Syst. 2015, 70, 60–72. [Google Scholar] [Green Version]
- Ngai, E.W.T.; Xiu, L.; Chau, D.C.K. Application of data mining techniques in customer relationship management: A literature review and classification. Expert Syst. Appl. 2009, 36, 2592–2602. [Google Scholar] [CrossRef]
- Park, N.; Lee, S.; Kim, J.H. Individuals’ personal network characteristics and patterns of Facebook use: A social network approach. Comput. Hum. Behav. 2012, 28, 1700–1707. [Google Scholar] [CrossRef]
- Erlandsson, F.; Boldt, M.; Johnson, H. Privacy Threats Related to User Profiling in Online Social Networks, Privacy, Security, Risk and Trust (PASSAT). In Proceedings of the 2012 International Conference on Social Computing (SocialCom), Amsterdam, The Netherlands, 3–5 September 2012; pp. 838–842. [Google Scholar]
- Wisniewski, P.; Knijnenburg, B.P.; Richter Lipford, H. Profiling Facebook Users’ Privacy Behavior. In Proceedings of the SOUPS 2014 Workshop on Privacy Personas and Segmentation, Menlo Park, CA, USA, 9–11 July 2014. [Google Scholar]
- Terrana, D.; Augello, A.; Pilato, G. Facebook Users Relationships Analysis Based on Sentiment Classification. In Proceedings of the 2014 IEEE International Conference on Semantic Computing (ICSC), Newport Beach, CA, USA, 16–18 June 2014; pp. 290–296. [Google Scholar]
- Terrana, D.; Augello, A.; Pilato, G. A System for Analysis and Comparison of Social Network Profiles. In Proceedings of the 2015 IEEE International Conference on Semantic Computing (ICSC), Anaheim, CA, USA, 7–9 February 2015; pp. 109–115. [Google Scholar]
- Nohlberg, M. Why humans are the weakest link. Social and Human Elements in Information Security: Emerging Trends and Countermeasures; Gupta, M., Sharman, R., Eds.; IGI Global: Hershey, PA, USA, 2008. [Google Scholar]
- D’Arcy, J.; Hovav, A.; Galletta, D. User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach. Inf. Syst. Res. 2009, 20, 79–98. [Google Scholar] [CrossRef]
- Haney, C.; Banks, C.; Zimbardo, P. Interpersonal Dynamics in a Simulated Prison; Defense Technical Information Center: Fort Belvoir, VA, USA, 1972. [Google Scholar]
- Mixon, D. Instead of Deception. J. Theory Soc. Behav. 1972, 2, 145–178. [Google Scholar] [CrossRef]
- O’Leary, C.J.; Willis, F.N.; Tomich, E. Conformity under Deceptive and Non-Deceptive Techniques. Sociol. Q. 1970, 11, 87–93. [Google Scholar] [CrossRef]
- Olson, T.; Christiansen, G. Thirty-One Hours: The Grindstone Experiment; Canadian Friends Service Committee: Toronto, ON, Canada, 1966. [Google Scholar]
- Gibbins, M. Deception: A Tricky Issue for Behavioral Research in Accounting and Auditing. Auditing 1992, 11, 113. [Google Scholar]
- Kimmel, A.J. Deception in Marketing Research and Practice: An Introduction. Psychol. Market. 2000, 18, 657–661. [Google Scholar] [CrossRef]
- Cheung, C.M.; Lee, M.K. What drives consumers to spread electronic word of mouth in online consumer-opinion platforms. Decis. Support Syst. 2012, 53, 218–225. [Google Scholar] [CrossRef]
- Lee, M.K.; Shi, N.; Cheung, C.M.; Lim, K.H.; Sia, C.L. Consumer’s decision to shop online: The moderating role of positive informational social influence. Inf. Manag. 2011, 48, 185–191. [Google Scholar] [CrossRef]
- Luo, C.; Luo, X.R.; Schatzberg, L.; Sia, C.L. Impact of informational factors on online recommendation credibility: The moderating role of source credibility. Decis. Support Syst. 2013, 56, 92–102. [Google Scholar] [CrossRef]
| Social Engineering Tricks | |
|---|---|
| 1 | Clickjacking with executable file. The message offers a file that contains leaked government documents, while the actual extension is (.exe). The actual URL displayed in the status bar is: http://128.2.72.235/documents.jpg.exe |
| 2 | Phishing through a post offering free cell phone minutes. |
| 3 | Downloading Who-Viewed-Your-Profile application/software. |
| 4 | Spam or malware, by giving permission/access to the site before it allows the user to see a video. |
| 5 | Phishing through a message from Facebook that threatens account suspension. The link in the message is written as: https://www.facebook.com/ while the actual URL displayed in the status bar is: http://www.facebooc.com/login/ |
| Treatments | Spelling | Grammar | Message Length | Supportive Picture | Supportive Video | Number of Likes | Number of Comments | Emoji | Well-Organization |
|---|---|---|---|---|---|---|---|---|---|
| Message/Experiment 1 | − | − | − | − | − | − | − | − | + |
| Message/Experiment 2 | + | − | − | − | + | − | + | + | − |
| Message/Experiment 3 | − | + | − | − | + | + | − | + | − |
| Message/Experiment 4 | + | + | − | − | − | + | + | − | + |
| Message/Experiment 5 | − | − | + | − | + | + | + | − | − |
| Message/Experiment 6 | + | − | + | − | − | + | − | + | + |
| Message/Experiment 7 | − | + | + | − | − | − | + | + | + |
| Message/Experiment 8 | + | + | + | − | + | − | − | − | − |
| Message/Experiment 9 | − | − | − | + | − | + | + | + | − |
| Message/Experiment 10 | + | − | − | + | + | + | − | − | + |
| Message/Experiment 11 | − | + | − | + | + | − | + | − | + |
| Message/Experiment 12 | + | + | − | + | − | − | − | + | − |
| Message/Experiment 13 | − | − | + | + | + | − | − | + | + |
| Message/Experiment 14 | + | − | + | + | − | − | + | − | − |
| Message/Experiment 15 | − | + | + | + | − | + | − | − | − |
| Message/Experiment 16 | + | + | + | + | + | + | + | + | + |
| Variable | N (=267) | Percentage | |
|---|---|---|---|
| Organization | |||
| First organization | 142 | 54% | |
| Second Organization | 125 | 46% | |
| Gender | |||
| Male | 166 | 62% | |
| Female | 101 | 38% | |
| Age | |||
| From 18–25 | 80 | 30% | |
| From 26–35 | 53 | 20% | |
| From 36–45 | 72 | 27% | |
| Over 45 years old | 62 | 23% | |
| Education Level | |||
| Lower than a Bachelor’s degree | 66 | 25% | |
| Bachelor’s | 96 | 36% | |
| Master’s | 64 | 24% | |
| PhD | 41 | 15% | |
| Security Knowledge Levels | |||
| Level 1 (lowest) | 53 | 20% | |
| Level 2 | 99 | 37% | |
| Level 3 | 67 | 25% | |
| Level 4 | 48 | 18% | |
| Round of Recruitment | |||
| First round | 174 | 65% | |
| Second round | 95 | 35% | |
| Factor | Items | Number of Observations | Loading | Mean | Standard Deviation | Standard Error |
|---|---|---|---|---|---|---|
| Name: Perceived informativeness Cronbach’s alpha: 0.91 Eigenvalue: 3.38 Variance Explained: 0.18 | This message provided relevant information about the (document, application, offer, …) | 4272 | 0.778 | 4.36 | 1.79 | 0.019 |
| This message provided complete information about the … | 4272 | 0.881 | 4.46 | 1.98 | 0.020 | |
| This message provided accurate information about the … | 4272 | 0.837 | 4.62 | 1.97 | 0.021 | |
| This message provided adequate information about the … | 4272 | 0.846 | 4.67 | 2.1 | 0.021 | |
| Name: Perceived persuasiveness Cronbach’s alpha: 0.93 Eigenvalue: 5.41 Variance Explained: 0.19 | The argument of this message was convincing | 4272 | 0.872 | 4.45 | 2.12 | 0.024 |
| The arguments of this message were persuasive | 4272 | 0.853 | 4.50 | 2.1 | 0.023 | |
| The arguments of this message were strong | 4272 | 0.871 | 4.44 | 2.12 | 0.025 | |
| The arguments of this message were good | 4272 | 0.862 | 4.54 | 2.0 | 0.023 | |
| Name: Perceived risk Cronbach’s alpha: 0.89 Eigenvalue: 4.86 Variance Explained: 0.15 | How risky do you feel it would be to make a decision based on the message provided? | 4272 | 0.847 | 4.45 | 1.89 | 0.025 |
| How risky do you feel it would be to accept and [download the document, download the application, etc.] based on the provided message? | 4272 | 0.816 | 4.58 | 1.98 | 0.024 | |
| How safe do you feel it would be to consent and [download the document, download the application, etc.] based on the provided message? [reversed] | 4272 | 0.704 | 4.71 | 1.83 | 0.022 |
| Model | Standardized Coefficients | t | Sig. | R Square | Adjusted R Square | F Change | Sig. of F Change | |
|---|---|---|---|---|---|---|---|---|
| Beta | ||||||||
| 1 | (Constant) | 111.1 | <0.0001 | 0.31 | 0.31 | 641.9 | <0.0001 | |
| Perceived informativeness | 0.59 | 61.12 | <0.0001 | |||||
| 2 | (Constant) | 97.73 | <0.0001 | 0.42 | 0.42 | 469.2 | <0.0001 | |
| Perceived informativeness | 0.41 | 46.32 | <0.0001 | |||||
| Perceived persuasiveness | 0.37 | 44.44 | <0.0001 | |||||
| 3 | (Constant) | 73.19 | <0.0001 | 0.46 | 0.46 | 212.8 | <0.0001 | |
| Perceived informativeness | 0.36 | 41.2 | <0.0001 | |||||
| Perceived persuasiveness | 0.27 | 29.08 | <0.0001 | |||||
| Perceived risk | 0.29 | 33.73 | <0.0001 | |||||
| Constructs | Treatment Group | Cases (N) | Standard Deviation | Mean | F Value | Sig. | Eta Squared | Result |
|---|---|---|---|---|---|---|---|---|
| Spelling (Hypothesis: H4) | Low Level | 2136 | 0.36584 | 2.6159 | 614.934 | <0.0001 | 0.169 | Supported |
| High Level | 2136 | 0.46664 | 2.9946 | |||||
| Grammar (Hypothesis: H5) | Low Level | 2136 | 0.43868 | 2.5228 | 317.325 | <0.0001 | 0.174 | Supported |
| High Level | 2136 | 0.75236 | 3.0878 | |||||
| Message length (Hypothesis: H6) | Low Level | 2136 | 0.34177 | 2.4019 | 828.797 | <0.0001 | 0.355 | Supported |
| High Level | 2136 | 0.68958 | 3.2088 | |||||
| Supportive picture (Hypothesis: H7) | Low Level | 2136 | 0.39824 | 2.7443 | 53.865 | <0.0001 | 0.018 | Supported |
| High Level | 2136 | 0.50725 | 2.8662 | |||||
| Supportive video (Hypothesis: H8) | Low Level | 2136 | 0.42963 | 2.6915 | 196.296 | <0.0001 | 0.061 | Supported |
| High Level | 2136 | 0.46137 | 2.9190 | |||||
| Number of likes (Hypothesis: H9) | Low Level | 2136 | 0.32367 | 2.2493 | 4342.588 | <0.0001 | 0.743 | Supported |
| High Level | 2136 | 0.34938 | 3.3923 | |||||
| Number of comments (Hypothesis: H10) | Low Level | 2136 | 0.53982 | 2.7871 | 4.677 | 0.051 | 0.001 | Not Supported |
| High Level | 2136 | 0.36231 | 2.8233 | |||||
| Emoji (Hypothesis: H11) | Low Level | 2136 | 0.38874 | 2.7963 | 1.142 | 0.285 | 0.0003 | Not Supported |
| High Level | 2136 | 0.52158 | 2.8142 | |||||
| Well-organization (Hypothesis: H12) | Low Level | 2136 | 0.45186 | 2.1069 | 443.154 | <0.0001 | 0.227 | Supported |
| High Level | 2136 | 0.36344 | 2.5515 |
| Interaction Specifications | Effect of the Treatment (Mean Difference) for These Demographic Group | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Interaction | F | Sig | Observed Power | P. Eta Square | |||||
| Number of likes with User’s Gender | 151.7 | <0.0001 | 0.9 | 0.041 | Female | Male | |||
| 2.811 | 0.94 | ||||||||
| Well-organization with User’s Educational Level | 3.75 | <0.0001 | 0.77 | 0.005 | Lower than Bachelor | Bachelor | Masters | PhD or Doctorate | |
| 0.87 | 1.25 | 1.82 | 2.05 | ||||||
| Grammar with User’s Educational Level | 2.98 | 0.002 | 0.74 | 0.002 | Lower than Bachelor | Bachelor | Masters | PhD or Doctorate | |
| 0.99 | 1.17 | 1.51 | 1.75 | ||||||
| Number of likes with User’s Security Knowledge | 6.15 | <0.0001 | 0.98 | 0.018 | Lowest Level | Level 2 | Level 3 | Highest Level | |
| 0.39 | 1.11 | 1.52 | 1.74 | ||||||
| Message length with User’s Age | 2.54 | 0.031 | 0.64 | 0.008 | 18–25 Years | 26–35 | 36–45 | 46-55 | 56 and Over |
| 1.07 | 1.04 | 1.39 | 1.58 | 1.81 | |||||
| Supporting picture with User’s Age | 3.45 | <0.0001 | 0.86 | 0.01 | 18–25 Years | 26–35 | 36–45 | 46–55 | 56 and Over |
| 2.5 | 1.97 | 1.92 | 1.53 | 1.38 | |||||
| Supportive video with User’s Age | 2.8 | <0.0001 | 0.71 | 0.008 | 18–25 Years | 26–35 | 36–45 | 46–55 | 56 and Over |
| 2.1 | 1.81 | 1.92 | 1.49 | 1.27 | |||||
| Number of likes with User’s Age | 3.53 | 0.001 | 0.86 | 0.01 | 18–25 Years | 26–35 | 36–45 | 46–55 | 56 and Over |
| 3.1 | 2.21 | 1.91 | 1.59 | 1.22 | |||||
| Message length with User’s Educational Level | 3.56 | 0.003 | 0.81 | 0.009 | Lower than Bachelor | Bachelor | Masters | PhD or Doctorate | |
| 2.71 | 3.11 | 3.37 | 3.76 | ||||||
| Regression Analysis | Variance Tests | Means | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Demographic | Standardized Coefficient | Sig | T or F Values | Sig | |||||||
| Security knowledge | −0.18 | <0.0001 | F = 241.27 | <0.0001 | Lowest Level | Level 2 | Level 3 | Highest Level | |||
| 3.09 | 2.91 | 2.77 | 2.73 | ||||||||
| Gender | −0.04 | 0.001 | T = 17.03 | <0.0001 | Female | Male | |||||
| 2.57 | 2.41 | ||||||||||
| Time elapsed since joining Facebook | −0.12 | <0.0001 | F = 10.59 | <0.0001 | 6 Months or Less | 6 Months to 1 Year | 1 to 2 Years | 2 to 3 Years | More than 3 Years | ||
| 2.91 | 2.73 | 2.61 | 2.64 | 2.51 | |||||||
| Relationship | Direct Effect (with mediation) | Type of Mediation | |||
|---|---|---|---|---|---|
| IV | Mediated by | DV | Estimate | p | |
| Spelling | Perceived persuasiveness | Susceptibility to SE | 0.09 | <0.0001 | Partial Mediation |
| Grammar | Perceived persuasiveness | Susceptibility to SE | 0.08 | 0.008 | Partial Mediation |
| Message length | Perceived informativeness | Susceptibility to SE | 0.20 | <0.0001 | Partial Mediation |
| Supportive picture | Perceived persuasiveness | Susceptibility to SE | 0.13 | <0.0001 | Partial Mediation |
| Supportive video | Perceived persuasiveness | Susceptibility to SE | 0.16 | <0.0001 | Partial Mediation |
| Number of likes | Perceived risk | Susceptibility to SE | 0.21 | <0.0001 | Suppression Mediation |
| Well-organization | Perceived persuasiveness | Susceptibility to SE | 0.12 | 0.001 | Partial Mediation |
| Well-organization | Perceived informativeness | Susceptibility to SE | 0.12 | 0.003 | Partial Mediation |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Algarni, A. What Message Characteristics Make Social Engineering Successful on Facebook: The Role of Central Route, Peripheral Route, and Perceived Risk. Information 2019, 10, 211. https://doi.org/10.3390/info10060211
Algarni A. What Message Characteristics Make Social Engineering Successful on Facebook: The Role of Central Route, Peripheral Route, and Perceived Risk. Information. 2019; 10(6):211. https://doi.org/10.3390/info10060211
Chicago/Turabian StyleAlgarni, Abdullah. 2019. "What Message Characteristics Make Social Engineering Successful on Facebook: The Role of Central Route, Peripheral Route, and Perceived Risk" Information 10, no. 6: 211. https://doi.org/10.3390/info10060211
APA StyleAlgarni, A. (2019). What Message Characteristics Make Social Engineering Successful on Facebook: The Role of Central Route, Peripheral Route, and Perceived Risk. Information, 10(6), 211. https://doi.org/10.3390/info10060211





