4. Results
4.1. Respondents’ Social Demography Characteristics
From
Table 1, the respondents’ gender, age, marital status, and level of education were analyzed.
4.1.3. Benefits of Using Mobile Money Services
Table 3 shows the responses of the participants according to a 5-point Likert scale concerning the benefits of using mobile money services. Percentages, means (M), standard deviations (Std Dev), and Chi-square tests (χ
2) were computed to assist the research conclusion.
The significant majority (70.4%) of the respondents strongly agreed that mobile money provides a convenient way to send and receive money to anyone who owns a mobile phone or has access to a mobile money agent. The mean (M) is 4.64 (4.64 ≥ 4.5), which strongly agrees that mobile money provides a convenient way to send and receive money to anyone who owns a mobile phone or has access to a mobile money agent while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money provides a convenient way to send and receive money to anyone who owns a mobile phone or has access to a mobile money agent, χ2 (df = 4, N = 1240) = 2229.177, p = 0.000.
It was reported that 61.9% of the respondents strongly agreed that mobile money is more reliable than physically transporting money. The mean (M) is 4.45 (4.45 ≥ 4.0), which agrees with the notion that mobile money is more reliable than physically transporting money while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money is more reliable than physically transporting money, χ2 (df = 4, N = 1240) = 1522.274, p = 0.000.
The consensus of 56.9% of the respondents strongly agreed that mobile money services save time. The mean (M) is 4.33 (4.33 ≥ 4.0), which agrees that mobile money services save time while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services save time, χ2 (df = 4, N = 1240) = 1214.411, p = 0.000.
It was reported that 52.1% of the respondents strongly agreed that mobile money services are trustworthy. The mean (M) is 4.09 (4.09 ≥ 4.0), which agrees that mobile money services are trustworthy while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services are trustworthy, χ2 (df = 4, N = 1240) = 761.935, p = 0.000.
Besides, 47.7% of the respondents strongly agreed that mobile money services are faster and easier market transactions. The mean (M) is 4.27 (4.27 ≥ 4.0), which agrees that mobile money services are faster and easier market transactions while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services are faster and easier market transactions, χ2 (df = 4, N = 1240) = 1050.355, p = 0.000.
It was reported that 48.1% of the respondents strongly agreed that mobile money services improve access to financial services for a large number of people. The mean (M) is 4.30 (4.30 ≥ 4.0), which agrees that mobile money services improve access to financial services for a large number of people while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services improve access to financial services for a large number of people, χ2 (df = 4, N = 1240) = 1154.847, p = 0.000.
A similar majority (44.4%) of the respondents strongly agreed that mobile money services reduce the expenses and delays associated with opening, operating, and maintaining bank accounts. The mean (M) is 4.13 (4.13 ≥ 4.0), which agrees with the notion that mobile money services reduce the expenses and delays associated with opening, operating, and maintaining bank accounts while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services reduce the expenses and delays associated with opening, operating, and maintaining bank accounts, χ2 (df = 4, N = 1240) = 806.944, p = 0.000.
It was reported that 41.7% of the respondents strongly agreed that mobile money services lead to economic growth and development through increased savings and investments. The mean (M) is 3.90 (3.90 ≥ 3.5), which agrees with the notion that mobile money services lead to economic growth and development through increased savings and investments while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services lead to economic growth and development through increased savings and investments, χ2 (df = 4, N = 1240) = 518.798, p = 0.000.
Still, 38.4% of the respondents strongly agreed that mobile money services offer many services such as money transfers, mobile payment, mobile banking, and mobile financial services. The mean (M) is 4.53 (4.53 ≥ 4.5), which strongly agrees with the notion that mobile money services offer many services such as money transfers, mobile payment, mobile banking, and mobile financial services while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services offer many services such as money transfers, mobile payment, mobile banking, and mobile financial services, χ2 (df = 4, N = 1240) = 1737.234, p = 0.000.
It was reported that 36.5% of the respondents strongly agreed that mobile money services enhance the standard of living for the unbanked population. The mean (M) is 3.96 (3.96 ≥ 3.5), which agrees with the notion that mobile money services enhance the standard of living for the unbanked population while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that mobile money services enhance the standard of living for the unbanked population, χ2 (df = 4, N = 1240) = 593.250, p = 0.000.
The significant majority (35.1%) of the respondents strongly agreed that mobile money services increase banking penetration/untapped market at a low acquisition cost. The mean (M) is 4.06 (4.06 ≥ 4.0), which agrees that mobile money services increase banking penetration/untapped market at a low acquisition cost while the chi-square test was performed with the sig. value of 0.000 which is less than 0.05. This means that it was statistically significant to say that mobile money services increase banking penetration/untapped market at a low acquisition cost, χ2 (df = 4, N = 1240) = 749.960, p = 0.000.
4.2. Security Issues Associated with Mobile Money Systems
This study mainly focuses on the evaluation of key security issues associated with mobile money systems.
Table 4 depicts the opinion of respondents regarding the security issues associated with mobile money systems. Percentages, means (M), standard deviations (Std Dev), and Chi-square tests (χ
2) were computed to assist the research conclusion.
It was reported that 34.7% of the respondents strongly agreed that identity theft is one of the security challenges of mobile money systems. The mean (M) is 3.63 (3.63 ≥ 3.5), which agrees that identity theft is a key security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that identity theft is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 334.508, p = 0.000.
34.5% of the respondents strongly agreed that an authentication attack is a security challenge to mobile money systems. The mean (M) is 3.69 (3.69 ≥ 3.5), which agrees that the authentication attack is a key security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that the authentication attack is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 387.661, p = 0.000.
A similar majority (30.4%) of the respondents strongly agreed that a phishing attack is a security challenge to mobile money systems. The mean (M) is 3.27 (3.27 ≥ 3.0), which agrees with the notion that a phishing attack is a key security challenge while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that a phishing attack is a security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 145.145, p = 0.000.
It was reported that 49.8% of the respondents strongly agreed that a vishing attack is a common security challenge to mobile money systems. The mean (M) is 3.96 (3.96 ≥ 3.5), which agrees with the notion that a vishing attack is a security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that a vishing attack is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 771.298, p = 0.000.
The consensus of 32.1% of the respondents strongly agreed that a smishing attack is a security challenge to mobile money systems. The mean (M) is 3.30 (3.30 ≥ 3.0), which agrees that a smishing attack is a key security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that a smishing attack is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 143.927, p = 0.000.
Besides, 33.4% of the respondents strongly agreed that PIN sharing is one of the security challenges of mobile money systems. The mean (M) is 3.68 (3.68 ≥ 3.5), which agrees with the notion that PIN sharing is a key security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that PIN sharing is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 368.379, p = 0.000.
Lastly, 22.3% of the respondents agreed that agent-driven fraud is a common security challenge to mobile money systems. The mean (M) is 3.05 (3.05 ≥ 3.0), which agrees with the notion that agent-driven fraud is a key security challenge experienced by the users while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that agent-driven fraud is a key security challenge to mobile money systems, χ2 (df = 4, N = 1240) = 54.524, p = 0.000.
4.3. The Relationship between Demographic Variables (Like Gender, Age, Education Level, Duration of Mobile Money Usage, Mobile Money Transactions in a Month) and Mobile Money Systems’ Security Challenges
Hypothesis 1 (H1). There is no significant relationship between gender and mobile money systems’ security challenges.
From
Table 5, a Pearson chi-square test suggests that there is no statistically significant relationship between gender and identity theft (
χ2 (4) = 0.625,
p = 0.804), authentication attack (
χ2 (4) = 6.312,
p = 0.177), phishing attack (
χ2 (4) = 1.109,
p = 0.893), vishing attack (
χ2 (4) = 8.405,
p = 0.078), smishing attack (
χ2 (4) = 4.626,
p = 0.328), PIN sharing (
χ2 (4) = 1.214,
p = 0.876), and agent-driven fraud (
χ2 (4) = 4.383,
p = 0.357) because the
p-values are greater than 0.05, then we accept the null hypothesis.
Hypothesis 2 (H2). There is no significant relationship between age and mobile money systems’ security challenges.
As shown in
Table 6, a Pearson chi-square test suggests that there is no statistically significant relationship between age and identity theft (
χ2 (12) = 8.956,
p = 0.707), authentication attack (
χ2 (12) = 20.086,
p = 0.065), smishing attack (
χ2 (12) = 20.359,
p = 0.061), PIN sharing (
χ2 (12) = 17.476,
p = 0.133), agent-driven fraud (
χ2 (12) = 18.766,
p = 0.094) because the
p-values are greater than 0.05, then we accept the null hypothesis. However, there is a statistically significant relationship between age and phishing attack (
χ2 (12) = 31.544,
p < 0.05), vishing attack (
χ2 (12) = 41.697,
p < 0.05) because the
p-values are less than 0.05, then we reject the null hypothesis for the two security challenges.
Hypothesis 3 (H3). There is no significant relationship between education level and mobile money systems’ security challenges.
From
Table 7, a Pearson chi-square test suggests that there is statistically significant relationship between education level and identity theft (
χ2 (28) = 62.972,
p < 0.05), phishing attack (
χ2 (28) = 61.796,
p < 0.05), vishing attack (
χ2 (28) = 56.076,
p < 0.05), smishing attack (
χ2 (28) = 52.370,
p < 0.05), PIN sharing (
χ2 (28) = 49.025,
p < 0.05), agent-driven fraud (
χ2 (28) = 42.564,
p < 0.05) because the
p-values are less than 0.05, then we reject the null hypothesis. However, there is no statistically significant relationship between education level and authentication attack (
χ2 (28) = 40.446,
p = 0.060) because the
p-values are greater than 0.05, then we accept the null hypothesis for this security challenge.
Hypothesis 4 (H4). There is no significant relationship between the duration of mobile money usage and mobile money systems’ security challenges.
As shown in
Table 8, a Pearson chi-square test suggests that there is statistically significant relationship between duration of mobile money usage and identity theft (
χ2 (12) = 26.785,
p < 0.05), phishing attack (
χ2 (12) = 24.192,
p < 0.05), vishing attack (
χ2 (12) = 25.792,
p < 0.05), smishing attack (
χ2 (12) = 40.608,
p < 0.05), PIN sharing (
χ2 (12) = 21.734,
p < 0.05), agent-driven fraud (
χ2 (12) = 38.095,
p < 0.05) because the
p-values are less than 0.05, then we reject the null hypothesis. However, there is no statistically significant relationship between duration of mobile money usage and authentication attack (
χ2 (12) = 12.757,
p = 0.387) because the
p-values are greater than 0.05, then we accept the null hypothesis for this security challenge.
Hypothesis 5 (H5). There is no significant relationship between the number of mobile money transactions in a month and mobile money systems’ security challenges.
From
Table 9, a Pearson chi-square test suggests that there is no statistically significant relationship between number of mobile money transactions in a month and authentication attack (
χ2 (20) = 21.641,
p = 0.360), vishing attack (
χ2 (20) = 21.209,
p = 0.385), smishing attack (
χ2 (20) = 15.540,
p = 0.745), PIN sharing (
χ2 (20) = 29.827,
p = 0.073), agent-driven fraud (
χ2 (20) = 25.778,
p = 0.173) because the
p-values are greater than 0.05, then we accept the null hypothesis. However, there is a statistically significant relationship between the number of mobile money transactions in a month and identity theft (
χ2 (20) = 42.570,
p < 0.05), phishing attack (
χ2 (20) = 33.884,
p < 0.05) because the
p-values are less than 0.05, then we reject the null hypothesis for these security challenges.
4.4. The Different Ways or Measures to Mitigate the Mobile Money Systems Security Challenges
From
Table 10, the responses of the participants regarding the different measures to mitigate the security challenges associated with mobile money systems are presented in the form of percentages, means (M), standard deviations (Std Dev), and Chi-square tests (χ
2) to assist in research conclusion.
There was a significant majority (64.7%) of the respondents who strongly agreed that the use of better access controls like, PIN, one-time password, and Biometric fingerprint altogether is a high priority. The mean (M) is 4.41 (4.41 ≥ 4.0), which agrees with the notion that the use of better access controls can mitigate mobile money systems’ security challenges while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that the use of better access controls is a priority in mitigating mobile money systems’ security challenges, χ2 (df = 4, N = 1240) = 1698.427, p = 0.000.
It was reported that 60.9% of the respondents strongly agreed that customer awareness campaigns to increase customer education and protection is a high priority. The mean (M) is 4.47 (4.47 ≥ 4.5), which strongly agrees with the notion that customer awareness campaigns to increase customer education and protection is a high priority while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that customer awareness campaigns to increase customer education and protection is a high priority in mitigating mobile money systems’ security challenges, χ2 (df = 4, N = 1240) = 1603.621, p = 0.000.
Besides, 60.4% of the respondents strongly agreed that agent training on acceptable practices is a higher priority. The mean (M) is 4.41 (4.41 ≥ 4.0), which agrees with notion that agent training on acceptable practices is necessary while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that agent training on acceptable practices is a priority in mitigating the security challenges, χ2 (df = 4, N = 1240) = 1486.452, p = 0.000.
It was reported that 51.0% of the respondents strongly agreed that a comprehensive legal document to guide mobile money service is a high priority. The mean (M) is 4.22 (4.22 ≥ 4.0), which agrees with the notion that comprehensive legal document to guide mobile money service is necessary for mobile money service providers and the government while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that a comprehensive legal document to guide mobile money service is necessary for successful implementation of mobile money services, χ2 (df = 4, N = 1240) = 1015.024, p = 0.000.
The consensus of 68.5% of the respondents strongly agreed that strict measures against fraudsters are a high priority. The mean (M) is 4.48 (4.48 ≥ 4.0), which agrees with the notion that strict measures against fraudsters are a priority while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that strict measures against fraudsters are a high priority in mitigating mobile money systems’ security challenges, χ2 (df = 4, N = 1240) = 1918.411, p = 0.000.
It was reported that 49.4% of the respondents strongly agreed that knowing your customer controls during registration is necessary. The mean (M) is 4.19 (4.19 ≥ 4.0), which agrees that knowing and verifying customer credentials during registration is a priority while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that know your customer controls during registration is necessary for mitigating the security challenges, χ2 (df = 4, N = 1240) = 951.669, p = 0.000.
Furthermore, 64.4% of the respondents strongly agreed that mobile users should report any security incidence/fraud to the regulators and security agencies. The mean (M) is 4.48 (4.48 ≥ 4.0), which agrees with the notion that mobile users reporting any security incidence/fraud to the regulators and security agencies is a priority while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that reporting any security incidence/fraud to the regulators and security agencies by mobile users is necessary for mitigating mobile money systems’ security challenges, χ2 (df = 4, N = 1240) = 1727.944, p = 0.000.
It was reported that 56.5% of the respondents strongly agreed that high-value transaction monitoring from the service providers is a high priority. The mean (M) is 4.32 (4.32 ≥ 4.0), which agrees with the notion that high-value transaction monitoring from the service providers is a must while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that high-value transaction monitoring from the service providers is a priority in mitigating the security challenges, χ2 (df = 4, N = 1240) = 1278.927, p = 0.000.
A similar majority (54.9%) of the respondents strongly agreed that the government and mobile money service providers should publish any reported incidences. The mean (M) is 4.28 (4.28 ≥ 4.0), which agrees with the notion that the government and mobile money service providers should publish any reported incidences while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that the government and mobile money service providers should publish any reported incidences to mitigate the security challenges, χ2 (df = 4, N = 1240) = 1190.427, p = 0.000.
Lastly, 50.5% of the respondents strongly agreed that the government and mobile money service providers should come up with a portal where victims can share their incidences anonymously. The mean (M) is 4.16 (4.16 ≥ 4.0) which strongly agrees with the notion that it is a priority for the government and mobile money service providers to come up with a portal where victims can share their incidences anonymously while the chi-square test was performed with the sig. value of 0.000, which is less than 0.05. This means that it was statistically significant to say that the government and mobile money service providers should come up with a portal where victims can share their incidences anonymously to mitigate the security challenges associated with mobile money systems, χ2 (df = 4, N = 1240) = 950.935, p = 0.000.
5. Discussion
The opinion of MM users, MM agents, and MNO IT officers remain paramount in the implementation of secured mobile money systems. Therefore, the main aim of this study was to evaluate the key security issues associated with mobile money systems in Uganda. The crucial objective of the survey was for MM users, MM agents, and MNO IT officers to identify and evaluate the key security challenges associated with mobile money systems, assess the relationship between demographic variables and mobile money systems’ security challenges in Uganda, and suggest mitigation measures for the security challenges to improve the mobile money technology. Before evaluating the key security challenges, there is a need to establish the services and benefits offered by mobile money.
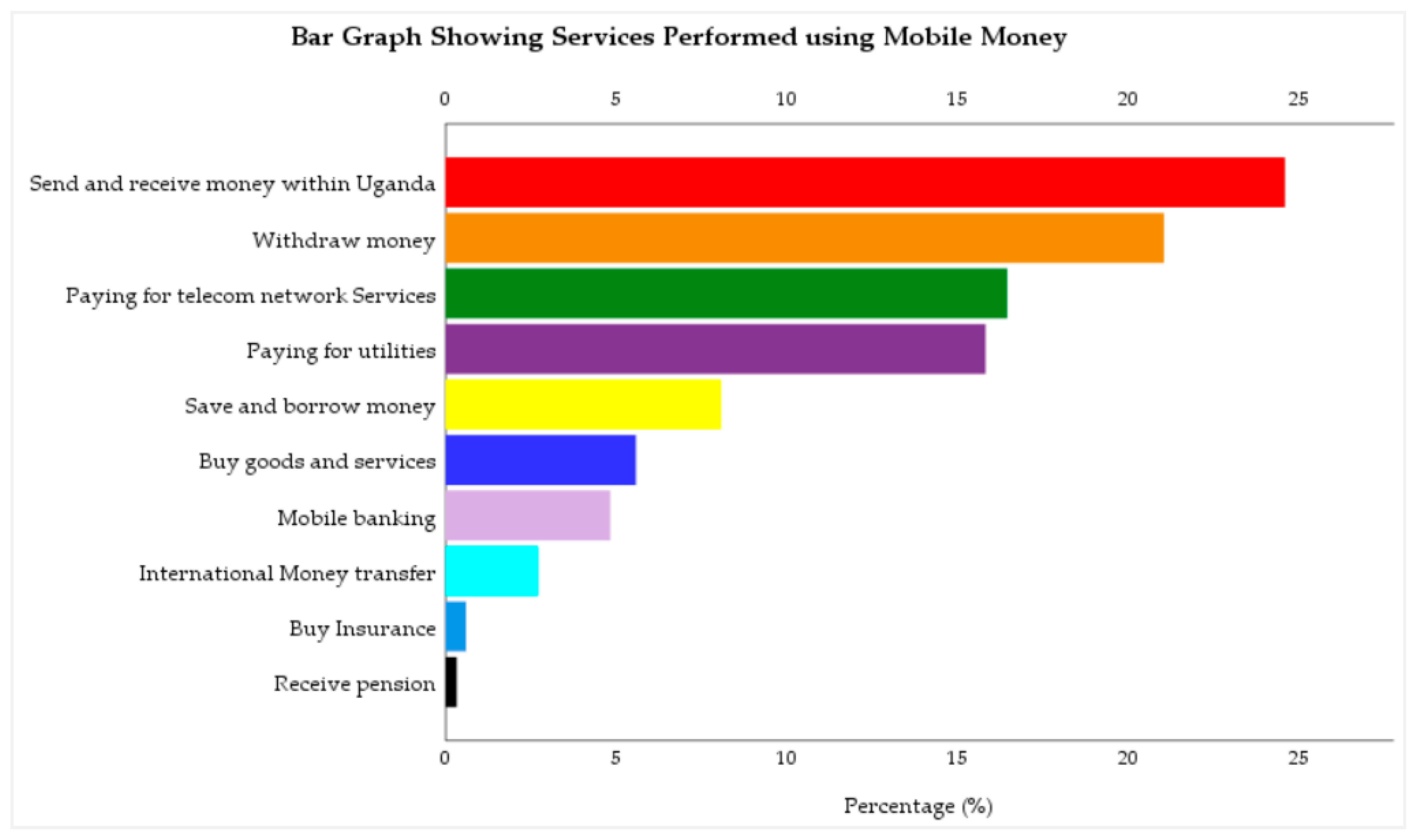
The results in
Figure 1 shows some of the services performed using mobile money. They include sending and receiving money within Uganda, withdrawing money; paying for telecom network services (like data bundles, airtime, etc.); paying for utilities (like NWSC, UMEME, DStv); saving and borrowing money; buying goods and services; mobile banking; international money transfer; buying insurance, and receiving a pension. This outcome is consistent with the studies conducted by Lwanga and Adong [
17], BoU [
1], Afi [
18], who identified depositing and withdrawing of money, transfer of money to other users, paying utility bills, paying for goods in a store, saving money for future purchases or payment, receiving a salary, taking a loan, receiving state aid or pension, buying insurance, purchasing airtime and data bundle, and making bank transactions as the services performed using mobile money.
The findings presented in
Table 3, mentioned convenient means to transport and receive money to anyone who has a mobile phone or has access to a mobile money agent, improved access to financial services for a large number of people, more reliability than physically transporting money, and that it saves time as some of the benefits of mobile money services. This is in line with the submissions of Kikulwe, Fischer, and Qaim [
23], Mugambi, Njunge, and Yang [
24], Saxena et al. [
27], Marumbwa and Mutsikiwa [
30], Kanobe et al. [
33], Cisco [
35], who identified a convenient way to send money to anyone who owns a mobile phone, enhance access to financial services for a large number of people who are effectively excluded from banks, transfer money through mobile phones without physically visiting the bank, and cut down time lags associated with opening, operating, and maintaining a traditional bank account as some of the benefits. Furthermore, faster and easier market transactions, increased banking penetration, enhanced standard of living for the unbanked population, and economic growth and development are some of the mentioned benefits. These findings conform with the studies of Lonergan et al. [
31], Hu et al. [
34], who stated that mobile money provides the quickest mechanism for clearing unplanned domestic financial payments, enhances the standard of living for the unbanked population, and stimulates economic development.
From
Table 4, respondents identified the following as the security issues associated with mobile money systems:
Identity theft: This is a form of mobile money crime committed by a friend, relative, or a fraudster who steals the owners’ financial information such as PIN for performing transactions. According to Bosamia [
9], when a customer’s mobile phone is stolen, attackers make use of any sensitive data stored in it, including the PIN, and have control over the device. The mobile money PIN stored on the mobile phone will provide them with access to the mobile money account enabling them to carry out fraudulent transactions [
45,
46]. This is in line with the work of Trulioo [
40], Mtaho [
7], who noted that identity theft is usually an inside job activity through unscrupulous employees gaining unauthorized access to mobile money data that belongs to the users and then irregularly misappropriating their funds. This is affirmed by Gwahula [
37], Buku and Mazer [
41], who observed that identity theft results from fraudulent or offline SIM swaps by fraudsters that transfer the mobile wallet account from the customer’s SIM to the fraudster’s SIM, enabling them to have full access to the user’s mobile wallet to carry out fraudulent transactions [
42,
43].
Authentication attack: This is a mobile money crime where attackers target and try to exploit the mobile money authentication process by an applying brutal-force attack or weak PIN attack. This is in line with the findings of Mtaho [
7], Castle et al. [
8], Mtaho and Mselle [
13], Gwahula [
37], Reaves et al. [
38], who found out that attackers use many ways to gain access to users’ account and take advantage of weak PIN reset procedures, making it easy to guess, smudge, or snoop. This outcome is consistent with the study conducted by Bosamia [
9], Akomea-Frimpong et al. [
39], who reported that most of the mobile money systems are not properly protected, giving IT fraudsters the ability to apply reverse engineering to attack hardcoded passwords or PINs, encryption keys, and steal customer money.
Phishing attack: This is a form of mobile money crime where fraudsters masquerade as employees of the mobile money service provider by calling or sending SMS messages to mobile money users and agents to reveal their data including a PIN for an update. This is in line with the submissions of Bosamia [
9], who also found out that fraudsters carry out sophisticated attacks by sending either email messages, SMSs, or calls to mobile money users to disclose their personal and financial information.
Vishing attack: This is a form of mobile money fraud where fraudsters use voice calls to trick mobile money users and agents into revealing their critical financial information like a PIN. This reaffirms the findings of earlier studies by Saxena et al. [
27], Maseno, Ogao, and Matende [
48] who observed that attackers use anonymous phone calls or false promotions to trick users into disclosing their PINs or other sensitive personal information that is then used to steal from their mobile money accounts. It was further supported by Kigen et al. [
49], who added that vishing is a widely used method of launching attacks on mobile money platforms in Kenya, where individuals have been tricked to provide sensitive information such as mobile money PINs, which have led to fraudulent transactions.
Smishing attack: This is a form of mobile money fraud where fraudsters send emotional delusional SMS messages to lure mobile money users and agents into revealing their mobile money account information, including the PIN. This finding is described in other earlier studies conducted by Mudiri [
42], Maseno, Ogao, and Matende [
48], where fraudsters send fake SMS using their mobile phones to mobile money users and mobile money agents, and then take them through various steps, which later result in the transfer of money from their account to the fraudsters’ account. It is also consistent with the studies of Akomea-Frimpong et al. [
39], Buku and Mazer [
41], Gilman and Joyce [
44], Lonie [
45] who reported that fraudsters impersonating as employees of mobile money service providers send fake SMS messages to customers that they have won a promotion prize, and for them to claim the price they should send money to the fraudster’s number.
PIN sharing: Many mobile money users and agents tend to share their mobile money PIN(s) among relatives, friends, which makes their account vulnerable to identity theft, brute-force attack, and authentication attacks. This finding is reported in other earlier studies conducted by Mtaho [
7], who observed that most people tend to share their mobile money PIN among friends and families, which has also added more security risks to the platform.
Agent-driven fraud: mobile money agents also experience fraud from both mobile money attackers/fraudsters, employees of the MNO, and users, thus threatening the security of the platform. This result is logical with the work conducted by Buku and Mazer [
41], Lonie [
45], in which they found that the common acts of fraud that agents experience include float loss in the agent’s account resulting from unauthorized use, misuse of PINs, and fraudster impersonating MNO staff to gain unauthorized access to the agent’s float account. Buku and Mazer [
41] reported that the 2015 surveys of the Helix Institute indicate that fraud was the primary concern of many agents, and found that 53% of mobile money agents in Uganda and 42% in Tanzania had experienced fraud. Uganda recorded the highest rate of fraud and crime rates in the region. Castle et al. [
8], Gilman, and Joyce [
44] added that customers also commit fraud against agents by giving wrong mobile phone numbers repeatedly to get the agent’s PIN.
Table 5,
Table 6,
Table 7,
Table 8 and
Table 9 analyzed the relationships between demographic variables (like gender, age, education level, duration of mobile money usage, mobile money transactions in a month) and mobile money systems’ security challenges. Respondents observed that:
There is no statistically significant relationship between gender and identity theft, authentication attack, phishing attack, vishing attack, smishing attack, PIN sharing, and agent-driven fraud. There is a statistically significant relationship between age and phishing attack or vishing attack. Furthermore, there is a statistically significant relationship between education level and identity theft, phishing attack, vishing attack, smishing attack, PIN sharing, agent-driven fraud. Besides, there is a statistically significant relationship between duration of mobile money usage and identity theft, phishing attack, vishing attack, smishing attack, PIN sharing, agent-driven fraud. Finally, there is a statistically significant relationship between the number of mobile money transactions in a month and identity theft, phishing attacks.
The findings presented in
Table 10 are regarding the different ways and measures to mitigate the security challenges associated with mobile money systems, respondents agreed that:
Use of better access controls such as multi-factor authentication (i.e., PIN, one-time password, and biometric fingerprint). These findings are similar to the studies of Bosamia [
9], Gilman and Joyce [
44], Lonie [
45], who found out that there is a need for control access rights to protect customer information, and that all interactions between servers must be logged, secured, and strongly authenticated using two-factor authentication. Lonie [
45] further pointed out that there is a need to enforce high-security standard measures for payment processing systems and encryption should occur at the earliest possible point in the messaging flow where all external messages between customer and partner activities are encrypted.
Customer awareness campaigns to increase customer education and protection. This finding is reported in other earlier studies conducted by Bosamia [
9], Gwahula [
37], Akomea-Frimpong et al. [
39], Mudiri [
42], Gilman and Joyce [
44], who added that financial education, customer awareness campaigns, security awareness, and risk awareness need to be carried out to increase customer education, protection and encourage their participation in this industry.
Agent training on acceptable practices. It is also consistent with the study of Gilman and Joyce [
44], who argued that agent training is needed on acceptable practices, terms, and conditions.
Need for a comprehensive legal document to guide mobile money service. This is in line with the work of Akomea-Frimpong et al. [
39], Lonie [
45], Alhassan et al. [
54], who stated that detailed legal code, internal fraud policy, and an efficient and robust user and security policy should be developed and used by mobile money merchants and partner banks.
Mobile money service providers should monitor high-value transactions. This outcome is consistent with the study conducted by Gilman and Joyce [
44], who argued that there is a need for threshold limits to reduce the risk associated with anti-money laundering/combating the financing of terrorism (AML/CFT). Mudiri [
42], Gilman, and Joyce [
44], further added that monitoring and supervision of mobile money agents are imperative.
Some other measures to mitigate the security challenges of mobile money systems include: taking strict measures against fraudsters; reporting any security incidences or fraud to the regulators and security agencies; publishing any reported incidences by the government and mobile money service providers; the government and mobile money service providers should come up with a portal where victims can share their incidences anonymously.
6. Conclusions
Mobile money systems have come out as the primary payment platform for the digital economy, thus bettering the standard of living of many people who have limited access to the banking infrastructure in developing nations like Uganda. By enabling access to cashless payment infrastructure, these systems allow citizens of developing nations to decrease the physical security risks associated with hard currency transactions. However, the security of most of the mobile money systems remains a big challenge. In this article, the researchers evaluated the security challenges of mobile money systems. They found significant security challenges with the current mobile money systems such as identity theft, authentication attack, phishing attack, vishing attack, SMiShing attack, PIN sharing, and agent-driven fraud. The study also found significant relationships between constructs and mobile money systems’ security challenges in Uganda. Several mitigation measures were recommended for successful implementation of secure mobile money systems such as the use of better access controls, customer awareness campaigns, agent training on acceptable practices, developing a comprehensive legal document to run mobile money service, KYC controls, high-value transaction monitoring by the service providers, but to mention a few.
The findings of this study contribute to the theoretical literature in the following ways. First, this paper extends the theoretical knowledge of security challenges in mobile money systems. To our best knowledge, no empirical study has been conducted to evaluate the key security issues associated with mobile money systems in Uganda. Second, our study contributes to the literature by empirically testing the relationship between constructs (gender, age, education level, duration of mobile money usage, and mobile money transactions in a month) and mobile money systems’ security challenges. Most of these constructs have never been used in studies focusing on mobile money systems’ security challenges. The study also offers useful managerial contributions. Firstly, the study suggests that identifying and improving the security issues and challenges of mobile money systems are an important factor in the implementation of secure mobile money services. Thus, to encourage the successful implementation of secure mobile money systems, MMSPs need to evaluate the current system so that proper mitigation measures can be proposed and implemented to increase service delivery. Secondly, mobile money systems’ security challenges are a threat to the implementation of mobile money services. By assessing the relationship between constructs and mobile money systems’ security challenges in Uganda, MNOs can emphasize measures to counter those challenges. Lastly, the study can be useful to the Bank of Uganda concerning financial inclusion, which is important to achieve a sustainable development goal.
This study encountered some limitations that create an opportunity for future research on mobile money systems’ security challenges. Firstly, the survey was restricted to only Uganda and the survey data were mainly used for descriptive analysis regarding the key security issues associated with mobile money systems. The study did not investigate the views of other stakeholders, such as banks or other financial institutions and regulatory institutions. Thus, the findings from this study may not fully represent the opinions of all the stakeholders in Uganda. Secondly, the respondents’ involvement in answering the questionnaires were primarily voluntary, which might make some bias towards the sample. Thus, future research involving an online survey is encouraged to embrace the views of all the mobile money stakeholders who did not take part in the study. Thirdly, the research is limited to statistical data gathered from the few participants since mobile money security is a complicated issue, and data can only be availed on request and approval. Finally, the data used for empirical analysis were gathered from respondents in Uganda who have characteristics differing from respondents in other parts of the world. Future research could focus on repeating a similar topic in other regions of the world like Kenya, Tanzania, Rwanda, Burundi, Somalia, Nigeria, Ghana, South Africa, Haiti, India, Pakistan, Colombia, Philippines, Mexico, Brazil, and so on. This would help in the evaluation of the validity of the proposed measures across different countries. This study, therefore, provides a baseline survey to help MNO and the government that would wish to implement secure mobile money systems.