A Methodology for Creating a Macro Action Plan to Improve IT Use and Its Governance in Organizations
Abstract
:1. Introduction
2. Literature Review
3. Materials and Methods
3.1. Institution Studied and Sample
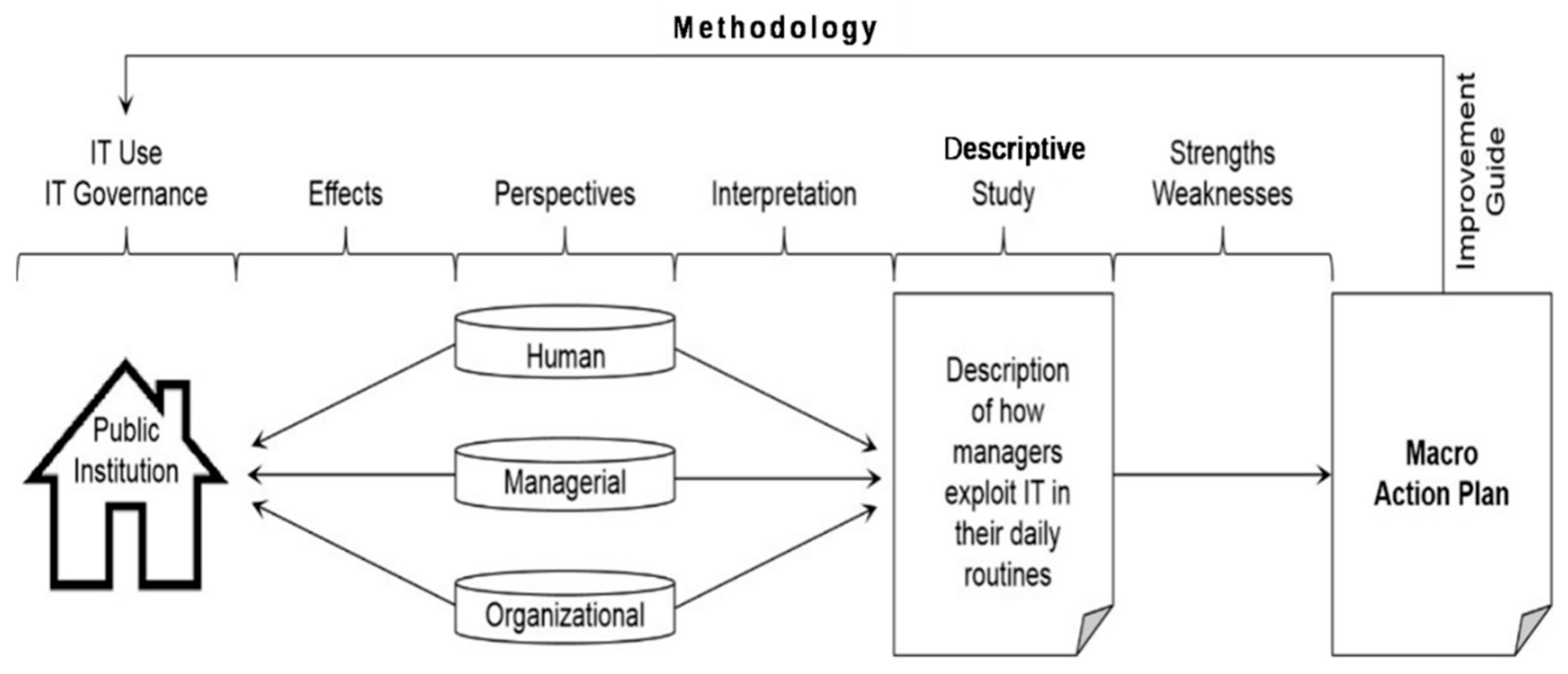
3.2. Method and Design of the Research
3.3. Collection Instrument and Data Collection
3.4. Analysis of Collected Data
- Inclusion of the eight documents (one document per interviewee) with the transcriptions; the notes helped in understanding the interviewees’ thoughts on the use of IT item
- Code generation for each interview according to the subjects or themes associated with the use of IT and the manager (the left-hand side of Figure 3 shows the system captured by the MAXQDA12 tool)
- The eight documents are then compiled into a single report (right-hand side of Figure 3), using the codes as an aggregation key
- Codes are maintained and combined into categories according to the analysis and meaning of results (Code System). In MAXQDA12, categories are called codes
4. Results
4.1. Perspectives
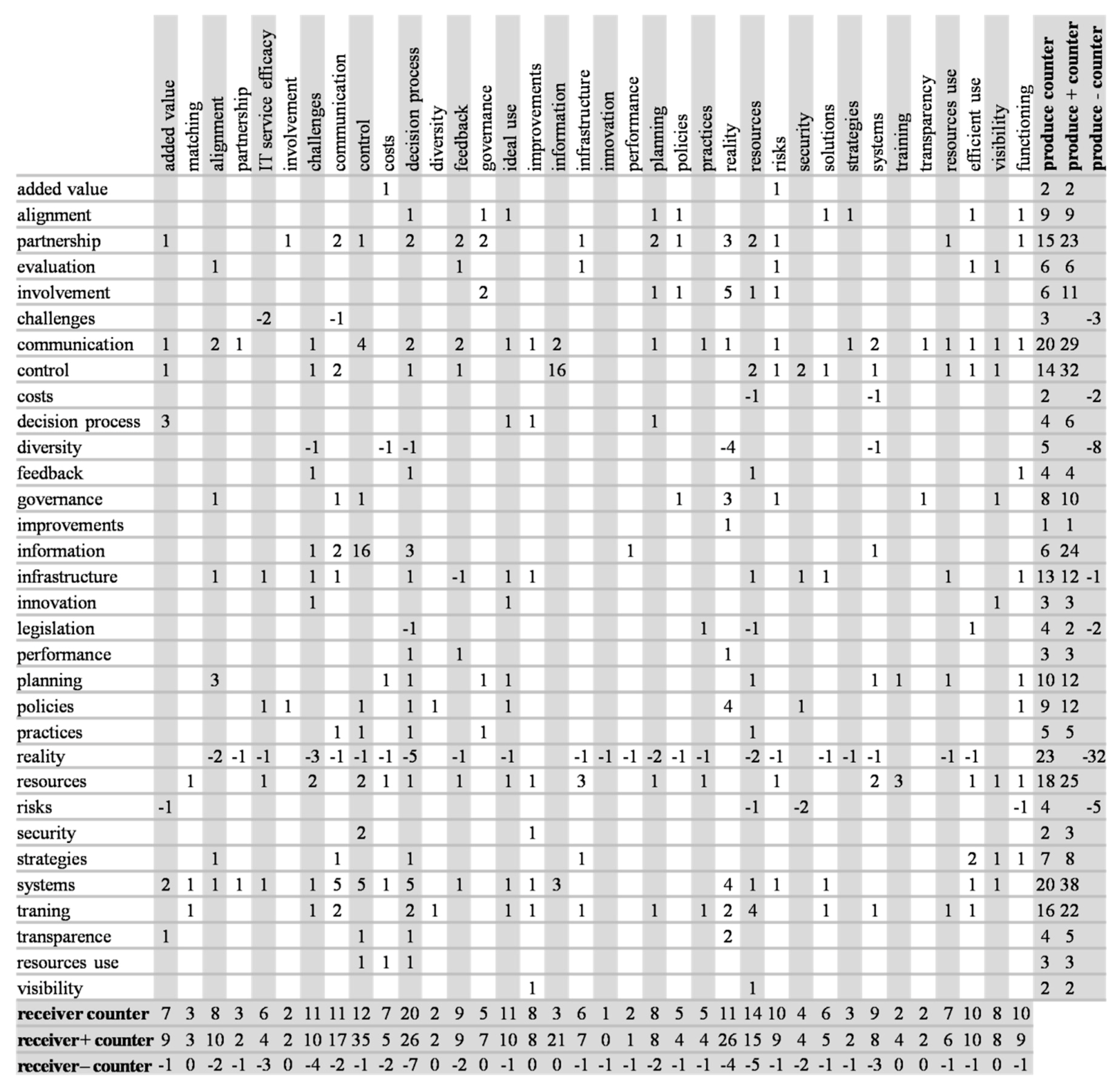
4.2. Interference Matrix
4.3. Avaliação das Perspectives
4.4. Seleção das Perspectives
4.5. Base Scenario to Construct the Macro Action Plan
4.6. The Macro Action Plan
- When: when it will be executed?
- Where: where to execute the action?
- Who: who will execute it?
- What: what action will take place?
- Why: why perform the action?
- How: how to conduct the execution of each action?
4.7. The Methodology
5. Discussion
6. Conclusions
6.1. Actions Recommended
6.2. Limitations
7. Further Works
Author Contributions
Funding
Conflicts of Interest
Appendix A
- (A)
- Initial preparations
- Introduce yourself;
- Thank for the availability to participate in the interview;
- Ask for permission to record. If the interviewee does not allow recording, transcribe the entire conversation manually.
- (B)
- General clarifications (the researchers inform the interviewees)
- “The purpose of this research is to describe the use of IT by public bodies in their daily work”;
- “We will adopt the concept of IT to indicate the entire infrastructure for the storage, control and security of information circulating in the institution”;
- “We will take all measures to prevent third parties from identifying the interviewees’ statements”;
- “Your participation is voluntary. You can stop participating in the survey at any time. Do you agree to participate?”
- (C)
- General stages of the interview process
- First phase: the interviewee will answer the questions and the questionnaire;
- Second phase (scheduling a new meeting-optional): opportunity for the interviewee to remember something important that was not mentioned in the initial conversation.
- (D)
- Questions about the interviewees’ background, experiences and behavior (allow the researcher to understand how the interviewees’ experiences can interfere with the interviewee’s current choices and behavior)
- What is your formal education?
- How long have you worked at this institution?
- How long have you worked in this department?
- What is your current position at the institution?
- How many members participate in the team that works directly with IT in your department?
- What other departments at the institution collaborate with your department to promote the proper use of IT?
- How does your department collaborate with the institution’s central administration to promote the proper use of IT?
- Who makes IT-related decisions in your department?
- How do employees in your department report their views on IT decisions?
- If employees in your department do not report their views on IT decisions, how could you encourage such behavior?
- How often would you like to receive feedback from employees about IT decisions?
- When the institution makes IT-related decisions, how do you present your opinion on those decisions?
- Suppose you want to give your feedback to the institution. How would you do that?
- What are the difficulties related to the use of IT faced by your department?
- How would you address problems related to the use of IT in your department?
- What do you do when IT is unavailable in your department?
- How does your department manage IT performance?
- How does your department plan the development of IT?
- How would you control the cost of IT in your department?
- How to use IT resources more effectively?
- How does your department ensure the proper use of IT?
- What IT products and services are available for your department?
- Analyze if the IT resources used in your department are adequate for the users’ profile?
- Do you explore new technologies to generate new strategic opportunities?
- What are the information control requirements in your department?
- Daily, how do you address IT-related risks?
- Do you perform periodic assessments of the IT resources employed in your department?
- How would you assess the IT resources employed in your department?
- (E)
- Questions about the interviewee’s beliefs and opinions
- What would you do to make the use of IT more effective in your department?
- What would you do to make the use of IT more effective at the institution?
- Regarding the IT demands of your department, how do you evaluate the service provided by the institution?
- How do you think your department takes strategic decisions about using IT?
- What do you think of these strategies?
- There are some methodologies and practices related to the use of IT in the literature. How do you think the institution should adopt them?
- Name the difficulties in making IT-related decisions in your department.
- Cite the current challenges in working with IT at the institution.
- Cite the current challenges of working with IT in your department.
- What are the advantages of implementing proper IT management and control (governance) practices within the institution?
- What would you suggest to the institution to improve the use of IT in your department?
- Describe the ideal use for IT today within the institution.
- Describe the ideal use for IT today within your department.
- How do you feel about the use of IT within the institution?
- How would you rate the evolution of institution departments concerning IT decision making?
- How is IT aligned with your department’s needs?
- How do you think using IT can bring value to your department?
Appendix B
- SMART objective: define the actions of the IT’s annual strategic plans, checking the actions scheduled every six months; the head of each IT’s sector is responsible for monitoring the objective
- KPI: number of open problems in the checklist
- Metric: Number of open problems = 0
- Specific: yes
- Measurable: yes (counting the number of open problems)
- Attainable: yes (by controlling the execution of the strategic plan)
- Relevant: yes (to ensure the execution of the IT´s annual strategic plan)
- Time-related: yes (one year)
- SMART objective: train 50 people (departments A, B, C and D) per month in the use of digital platforms for one year; the head of each department is responsible for monitoring the objective
- KPI: people trained in the use of digital platforms
- Metric: number of people × number of months × number of years = 50 × 12 × 1 = 600
- Specific: yes
- Measurable: yes (counting the number of training)
- Attainable: yes (by offering high-quality training)
- Relevant: yes (to promote visibility to the products and services provided by the IT sectors)
- Time-related: yes (one year)
- SMART objective: promote campaigns to publicize the importance of respecting IT policies for one year; the head of each department is responsible for monitoring the objective
- KPI: respected politics
- Metric: number of violations of IT politics = 0
- Specific: yes
- Measurable: yes (counting the number of violations of IT policies)
- Attainable: partially (the campaigns can reduce the number of violations of IT policies but it is unlikely that no employee neglects an IT policy)
- Relevant: yes (to promote ethical practices in the use of IT)
- Time-related: yes (one year)
- SMART objective: design a risk management plan for remote work for the pandemic period through a task force with 10 IT people, within ten days; the leader of the task force is responsible for monitoring the objective
- KPI: risk management plan completed
- Metric: time to elaborate the plan ≤ ten days
- Specific: yes
- Measurable: yes (counting the number of days to deliver the plan)
- Attainable: yes (the organization created a task force with ten experts)
- Relevant: yes (to maintain the organizations working during the Coronavirus pandemic)
- Time-related: yes (the plan must be ready within ten days)
- SMART objective: make 100% of the information required for decision-making within 2 h; decision-makers are responsible for monitoring the objective
- KPI:100% of the information available within 2 h
- Metric: percentage of information available within 2 h = 100%
- Specific: yes
- Measurable: yes (counting the percentage of the information available within 2 h)
- Attainable: yes (by investing in data science-related technologies)
- Relevant: yes (to take right decisions)
- Time-related: yes (the information must be available within two hours)
- SMART objective: eliminating conflicts between IT staff and IT users, clarifying roles and responsibilities of each one through monthly group dynamics with ten people (representatives of sectors A, B, C and D), mediated by two professionals with the necessary competence, for one year; a member of the IT staff is responsible for monitoring the objective
- KPI: number of participants in the dynamic groups
- Metric: number of participants necessary competence, for number of months necessary competence, for number of years = 10 × 12 × 1 = 120 participants and number of conflict = 0
- Specific: yes
- Measurable: yes (counting the number of conflicts)
- Attainable: partially (there are many variables involved and some depend on aspects not fully controlled by the action)
- Relevant: yes (to promote the well-being of IT staff and IT users)
- Time-related: yes (one year)
Appendix C
- From the point of view of development professionals and even IT support, there is a need to be more prepared for remote work, since there is unpredictability in relation to live working conditions. It is necessary that they have more access to mobile equipment (notebooks) that can be used at work and at home and/or that conditions are given so that they have equipment and adequate connectivity in their homes. The opportunity to work remotely is also an important factor for the quality of life of professionals, so one should explore hybrid work mechanisms (face-to-face/remote) at least for part of the team, depending on the activity and considering the preference of the professional, when possible
- From an infrastructure point of view, the use of more virtual servers, in the cloud, should be evaluated.
- From the point of view of infrastructure for teachers and other professionals, equipment and mobile infrastructure should also be prioritized whenever possible, with the purchase of devices such as notebooks or ensuring remote secure access to equipment installed at the university.
- From the students’ point of view, especially in relation to those in a vulnerable situation, there is a need for loan and management mechanisms for more equipment under some level of responsibility of the university. Or support the acquisition of equipment and communication infrastructure by these students.
- More investment is needed in VPN (Virtual Private Network) and security solutions, given the increase in remote access. In addition, it is necessary to invest in backup solutions and guarantee that university data is protected and safe, even with the expansion of remote access. Avoid risk that the data is not only on mobile devices, external or that have no control/management of the university
- In general, there is an increase in responsibilities for the university’s IT, because in addition to supporting the existing infrastructure within its physical facilities, there is a significant increase in the need for infrastructure and support for remote access for servers and students, which will increase the workload. IT managers must plan the acquisition and use of new software or remote support procedures. Including to help maintain physical distance, in the most critical moment.”
References
- Wilkin, C.; Campbell, J. Corporate governance of IT: A case study in an Australian government department. In Proceedings of the 14th Pacific Asia Conference on Information Systems, Taipei, Taiwan, 9–12 July 2010. [Google Scholar]
- Qassimi, N.A.; Rusu, L. IT governance in a public organization in a developing country: A case study of a governmental organization. Procedia Comput. Sci. 2015, 64, 450–456. [Google Scholar] [CrossRef] [Green Version]
- Turel, O.; Liu, P.; Bart, C. Board-level information technology governance effects on organizational performance: The roles of strategic alignment and authoritarian governance style. Inf. Syst. Manag. 2017, 34, 117–136. [Google Scholar] [CrossRef]
- Nunes, D.; Rosa, I.; Silva, M.M. Improving IT strategic plan for the Portuguese public administration. In Proceedings of the 15th International Conference on Business Informatics, Vienna, Austria, 15–18 July 2013. [Google Scholar]
- De Haes, S.; Huygh, T.; Joshi, A.; Caluwe, L. National corporate governance codes and IT governance transparency in annual reports. J. Glob. Inf. Manag. 2019, 27, 91–118. [Google Scholar] [CrossRef]
- Safari, M.R.; Jiang, Q. The theory and practice of IT governance maturity and strategies alignment: Evidence from banking industry. J. Glob. Inf. Manag. 2018, 26, 127–146. [Google Scholar] [CrossRef]
- Levstek, A.; Hovelja, T.; Pucihar, A. IT governance mechanisms and contingency factors: Towards an adaptive IT governance model. J. Manag. Inf. Hum. Resour. 2018, 51, 286–310. [Google Scholar] [CrossRef] [Green Version]
- Vugec, D.S.; Spremić, M.; Bach, M.P. IT governance adoption in banking and insurance sector: Longitudinal case study of COBIT use. Int. J. Qual. Res. 2017, 11, 691–716. [Google Scholar] [CrossRef]
- Weill, P.; Ross, J.W. IT Governance: How Top Performers Manage IT Decision Rights for Superior Results. Book Review. Int. J. Electron. Gov. Res. 2005, 1, 63–67. Available online: https://www.researchgate.net/publication/236973378_IT_Governance_How_Top_Performers_Manage_IT_Decision_Rights_for_Superior_Results (accessed on 18 August 2019).
- Willson, P.; Pollard, C. Exploring IT governance in theory and practice in a large multi-national organisation in Australia. Inf. Syst. Manag. 2009, 26, 98–109. [Google Scholar] [CrossRef]
- Pereira, R.; da Silva, M.M. A literature review: IT governance guidelines and areas. In Proceedings of the 6th International Conference on Theory and Practice of Electronic Governance, Albany, NY, USA, 22–25 October 2012. [Google Scholar]
- Bouayad, H.; Benabbou, L.; Berrado, A. An analytic hierarchy process-based approach for information technology governance framework selection. In Proceedings of the 12th International Conference on Intelligent Systems: Theories and Applications, EMI Rabat, Marocco, 24–25 October 2018. [Google Scholar]
- Nielsen, M.M. Governance lessons from Denmark’s digital transformation. In Proceedings of the 20th Annual International Conference on Digital Government Research, Dubai, UAE, 18–20 June 2019. [Google Scholar]
- Maes, K.; De Haes, S.; Van Grembergen, W. How IT enabled investments bring value to the business: A literature review. In Proceedings of the 44th Hawaii International Conference on System Sciences, Kauai, HI, USA, 4–7 January 2011. [Google Scholar]
- Larsen, M.H.; Pedersen, M.K.; Viborg Andersen, K. IT Governance: Reviewing 17 IT governance tools and analysing the case of novozymes A/S. In Proceedings of the 39th Hawaii International Conference on System Sciences, Kauai, HI, USA, 4–7 January 2006. [Google Scholar] [CrossRef]
- Janahi, L.; Griffiths, M.; Al-Ammal, H. A conceptual model for IT governance in public sectors. In Proceedings of the 4th International Conference on Future Generation Communication Technologies, Bedfordshire Luton, UK, 29–31 July 2015. [Google Scholar]
- Othman, M.F.I.; Chan, T. Barriers to formal IT governance practice—Insights from a qualitative study. In Proceedings of the 46th Hawaii International Conference on System Sciences, Maui, Wailea, HI, USA, 7–10 January 2013. [Google Scholar]
- Bartens, Y.; De Haes, S.; Lamoen, Y.; Schulte, F.; Voss, S. On the way to a minimum baseline in IT governance: Using expert views for selective implementation of COBIT 5. In Proceedings of the 48th Hawaii International Conference on System Sciences, Kauai, HI, USA, 5–8 January 2015. [Google Scholar]
- Barrera, S.M.B.; Kim, K.; Yoon, H.; Hwang, J. IT governance effectiveness and its influence on innovation product and process. In Proceedings of the Portland International Conference for Management of Engineering and Technology, Honolulu, HI, USA, 3–6 January 2018. [Google Scholar]
- Da Silva, C.J.N.; Ribeiro, Q.A.D.S.; Soares, M.S.; Nascimento, R.P.C. ICT governance: A view of adoption of best practices in enterprises of Sergipe state. In Proceedings of the XV Brazilian Symposium on Information Systems, Aracaju, Brazil, 20–24 May 2019. [Google Scholar]
- Alonso, I.A.; Verdún, J.C.; Caro, E.T. Description of the structure of the IT demand management process framework. Int. J. Inf. Manag. 2017, 37, 1461–1473. [Google Scholar] [CrossRef]
- Kizito, M. Transdisciplinarity and information systems: IT governance in the digitalisation of healthcare. Proceedings 2017, 1, 175. [Google Scholar] [CrossRef] [Green Version]
- Veerankutty, F.; Ramayah, T.; Ali, N.A. Information technology governance on audit technology performance among malaysian public sector auditors. Soc. Sci. 2018, 7, 124. [Google Scholar] [CrossRef] [Green Version]
- Ajayi, B.A.; Hussin, H. IT governance from practitioners’ perspective: Sharing the experience of a Malaysian university. J. Theor. Appl. Inf. Technol. 2016, 88, 219–230. [Google Scholar]
- Borges, G.C.; Simao, J.B.; Miani, R.S. Exploratory analysis of ICT best practices for Brazilian federal universities. In Proceedings of the 35th Conference of the Chilean Computer Science Society, Valparaíso, Chile, 10–14 October 2016. [Google Scholar]
- Delport, P.M.J.; Von Solms, R.; Gerber, M. Towards corporate governance of ICT in local government. In Proceedings of the 11th International School of Tanganyika-Africa Week Conference, Durban, South Africa, 11–13 May 2016. [Google Scholar]
- Ngoma, M.; Erasmus, W. Maturity of IT governance in the South African public sector. In Proceedings of the 25th International Association for Management of Technology Conference Technology—Future Thinking, Orlando, FL, USA, 15–19 May 2016. [Google Scholar]
- Mamboko, P.; Zhou, M.; Tsokota, T.; Mhaka, C. IT governance: Status and level of implementation in Zimbabwean urban local authorities. Eur. J. Bus. Manag. 2015, 7, 173–179. Available online: https://iiste.org/Journals/index.php/EJBM/article/viewFile/18891/19361 (accessed on 18 August 2019).
- Ahlan, A.R.; Arshad, Y.; Ajayi, B.A. IT governance in a Malaysian public institute of higher learning and intelligent decision-making support system solution. Intell. Syst. Ref. Libr. 2014, 55, 19–33. [Google Scholar] [CrossRef]
- Arshad, Y.; Ahlan, A.R.; Ajayi, B.A. Intelligent IT governance decision-making support framework for a developing country’s public university. Intell. Decis. Technol. 2014, 8, 131–146. [Google Scholar] [CrossRef]
- Merriam, S.B. Qualitative Research: A Guide to Design and Implementation; Revised and expanded from Qualitative research and case study applications in education; Jossey-Bass: San Francisco, CA, USA, 2009. [Google Scholar]
- Charmaz, K. A Construção da Teoria Fundamentada: Guia Prático Para Análise Qualitativa; Tradução de Joice Elias Costa.Artmed: Porto Alegre, Brasil, 2009. [Google Scholar]
- Patton, M.Q. Qualitative Research and Evaluation Method; Sage: Thousand Oaks, CA, USA, 2002. [Google Scholar]
- Stray, V.; Sjøberg, D.I.K.; Dybå, T. The daily stand-up meeting: A grounded theory study. J. Syst. Softw. 2016, 114, 101–124. [Google Scholar] [CrossRef] [Green Version]
- Information Technology Secretariat of the Ministry of Planning, Budget and Management. Guia de Governança de Tecnologia da Informação e Comunicação do Sistema de Administração dos Recursos de Tecnologia da Informação, 1st ed.; STI/MPOG: Brasilia, Brazil, 2015. Available online: http://sisp.gov.br/govtic/wiki/download/file/GuiaGovTIC (accessed on 18 August 2019).
- Information Systems Audit and Control Association. Cobit 5: A Business Framework for the Governance and Management of Enterprise IT, 1st ed.; ISACA: Rolling Meadows, IL, USA, 2012; Available online: http://www.isaca.org/COBIT/Documents/COBIT-5-Introduction.pdf (accessed on 18 August 2019).
- Glaser, B.G. Basics of Grounded Theory Analysis: Emergence vs. Forcing; Sociology Press: Mill Valley, CA, USA, 1992. [Google Scholar]
- Goulding, C. Grounded theory: The missing methodology on the interpretive agenda. Qual. Mark. Res. 1998, 1, 50–57. [Google Scholar] [CrossRef] [Green Version]
- Santos, R.E.S.; Silva, F.Q.B.; Magalhães, C.V.C.; Monteiro, C.V.F. Building a theory of job rotation in software engineering from an instrumental case study. In Proceedings of the 38th International Conference on Software Engineering, Austin, TX, USA, 14–22 May 2016. [Google Scholar]
- Peterson, R.R. Integration Strategies and Tactics for Information Technology Governance.; Idea Group Publishing: Hershey, PA, USA, 2003; pp. 37–80. [Google Scholar]
- Janssen, M.; Helbig, N. Innovating and changing the policy-cycle: Policy-makers be prepared! Gov. Inf. Q. 2018, 35, 99–105. [Google Scholar] [CrossRef]
- Sanchez, X.; Bayona-Oré, S. Strategic alignment between business and information technology in companies. In Proceedings of the 15th Iberian Conference on Information Systems and Technologies, Sevilla, Spain, 24–27 June 2020. [Google Scholar] [CrossRef]
- Marchão, J.; Reis, L.; Martins, P.V. Business areas and processes alignment in ICT framework. In Proceedings of the 15th Iberian Conference on Information Systems and Technologies, Sevilla, Spain, 24–27 June 2020. [Google Scholar] [CrossRef]
- Wautelet, Y. Using the RUP/UML business use case model for service development governance: A business and IT alignment based approach. In Proceedings of the 22nd Conference on Business Informatics, Antwerp, Belgium, 22–24 June 2020. [Google Scholar] [CrossRef]
- Chang, S.-l.; Chang, L.-M.; Liao, J.-C. Risk factors of enterprise internal control under the internet of things governance: A qualitative research approach. Inf. Manag. 2020, 57, 1–18. [Google Scholar] [CrossRef]
- Koltay, T. Quality of Open Research Data: Values, Convergences and Governance. Information 2020, 11, 175. [Google Scholar] [CrossRef] [Green Version]
- Guo, G.; Zhu, Y.; Yu, R.; Chu, W.C.-C.; Ma, D. A Privacy-preserving Framework with Self-governanceand Permission Delegation in Online Social Networks. IEEE Access 2020. [Google Scholar] [CrossRef]
- Solana-González, P.; Vanti, A.A.; Fontana, K.H.S. Multicriteria analysis of the compliance for the improvement of information security. J. Inf. Syst. Technol. Manag. 2019, 16. [Google Scholar] [CrossRef]








| Perspective | Percentage of Articles that Cite the Perspective in the Systematic Mapping |
|---|---|
| Alignment | 100% |
| Performance and evaluation | 67% |
| Adoption of international norms/practices for IT governance | 53% |
| Value-added to IT | 53% |
| IT resources management | 40% |
| IT risk management | 40% |
| Knowledge management | 33% |
| Management of service level | 27% |
| Transparency | 20% |
| Ethics | 13% |
| Compliance culture | 13% |
| Position | Total Number | IT-Related | ||
|---|---|---|---|---|
| Managers | Interviewees | Managers | Interviewees | |
| Dean | 1 | 1/100% | 1 | 1/100% |
| Dean’s Assistant | 9 | 3/33% | 1 | 1/100% |
| Head of Administration Unit | 8 | 1/38% | 1 | 1/100% |
| Head | 10 | 3/30% | 2 | 1/50% |
| Perspectives Codes | Types of Interferences: | |||
|---|---|---|---|---|
| Strength+ | Weakness- | |||
| Number of Direct Interferences: | ||||
| Affect | Is Affected | Affect | Is Affected | |
| Reality and organizational culture: Reality | 10 | 23 | 1 | |
| Alignment of IT and the institution needs: Alignment * | 9 | 7 | 1 | |
| Partnership between institutions’ units: Partnership * | 15 | 2 | 1 | |
| Matching between resources and users’ needs: Matching * | 3 | |||
| Adoption of international norms/practices for ITG: Practices * | 5 | 4 | 1 | |
| Continuous evaluation of IT resources: Evaluation * | 6 | |||
| Continuous training of IT professionals: Training | 16 | 2 | ||
| Communication | 20 | 9 | 2 | |
| Information control: Control * | 14 | 11 | 1 | |
| IT costs: Costs * | 5 | 2 | 2 | |
| Challenges to working with IT: Challenges * | 9 | 3 | 2 | |
| Diversity (institution, sectors, people): Diversity | 2 | 5 | ||
| Efficacy to provide IT services: IT Service Efficacy * | 4 | 3 | ||
| Strategies to use the IT: Strategies * | 7 | 2 | 1 | |
| Ensure the proper functioning of IT: Functioning * | 9 | 1 | ||
| Performance analysis: Performance * | 3 | 1 | 1 | |
| IT governance and processes: Governance | 8 | 5 | ||
| Information availability: Information | 6 | 3 | ||
| Infrastructure (network, physical installations, …): Infrastructure | 12 | 6 | 1 | 1 |
| Innovation | 3 | 1 | ||
| Federal legislation: Legislation | 2 | 2 | ||
| Improvements in the use of IT: Improvements * | 1 | 8 | ||
| IT Planning: Planning * | 10 | 7 | 1 | |
| Definition of IT policies: Policies | 9 | 4 | 1 | |
| IT resources management: Resources | 18 | 10 | 4 | |
| Risks management of IT: Risks * | 9 | 4 | 1 | |
| Information security: Security | 2 | 3 | 1 | |
| Personal involvement: Involvement | 6 | 2 | ||
| Information systems: Systems | 20 | 6 | 3 | |
| Solution for problems in the use of IT: Solutions * | 5 | 1 | ||
| Feedback * | 4 | 7 | 2 | |
| Decision process * | 4 | 17 | 3 | |
| Transparency | 4 | 1 | ||
| More efficient use of IT resources: Resources Use * | 3 | 6 | 1 | |
| Ideal use of IT: Ideal Use * | 10 | 1 | ||
| Efficient use of IT: Efficient Use * | 9 | 1 | ||
| Value added to IT: Added Value * | 2 | 6 | 1 | |
| Visibility | 2 | 8 | ||
| c1 | c2 | c3 |
|---|---|---|
| = 252 | = 312 | = −21 |
| #c = 32 | #+c = 27 | #-c = 6 |
| Round [252/32] = 8 | Round [312/27] = 11 | Round [−21/6] = −3 |
| Perspectives | Produce Counteri | Counteri | Produce- Counteri | Satisfies the Criterion? |
|---|---|---|---|---|
| Added value | 2 | 2 | 0 | No |
| Alignment | 9 | 9 | 0 | Yes |
| Partnership | 15 | 23 | 0 | Yes |
| Evaluation | 6 | 6 | 0 | No |
| Involvement | 6 | 11 | 0 | Yes |
| Challenges | 3 | 0 | −3 | Yes |
| Communication | 21 | 29 | 0 | Yes |
| Control | 14 | 32 | 0 | Yes |
| Cost | 2 | 0 | −2 | No |
| Decision process | 4 | 6 | 0 | No |
| Diversity | 5 | 0 | −8 | Yes |
| Feedback | 4 | 4 | 0 | No |
| Governance | 8 | 10 | 0 | Yes |
| Improvements | 1 | 1 | 0 | No |
| Information | 6 | 24 | 0 | Yes |
| Infrastructure | 13 | 12 | −1 | Yes |
| Innovation | 3 | 3 | 0 | No |
| Legislation | 4 | 2 | −2 | No |
| Performance | 3 | 3 | 0 | No |
| Planning | 10 | 12 | 0 | Yes |
| Policies | 9 | 12 | 0 | Yes |
| Practices | 5 | 5 | 0 | No |
| Reality | 23 | 0 | −32 | Yes |
| Resources | 18 | 25 | 0 | Yes |
| Risks | 4 | 0 | −5 | Yes |
| Security | 2 | 3 | 0 | No |
| Strategies | 7 | 8 | 0 | No |
| Systems | 20 | 18 | 0 | Yes |
| Training | 16 | 22 | 0 | Yes |
| Transparence | 4 | 5 | 0 | No |
| Resources use | 3 | 3 | 0 | No |
| Visibility | 2 | 2 | 0 | No |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Telino, V.; Massa, R.; Mota, I.; Gomes, A.; Moreira, F. A Methodology for Creating a Macro Action Plan to Improve IT Use and Its Governance in Organizations. Information 2020, 11, 427. https://doi.org/10.3390/info11090427
Telino V, Massa R, Mota I, Gomes A, Moreira F. A Methodology for Creating a Macro Action Plan to Improve IT Use and Its Governance in Organizations. Information. 2020; 11(9):427. https://doi.org/10.3390/info11090427
Chicago/Turabian StyleTelino, Veronica, Ricardo Massa, Ioná Mota, Alexsandro Gomes, and Fernando Moreira. 2020. "A Methodology for Creating a Macro Action Plan to Improve IT Use and Its Governance in Organizations" Information 11, no. 9: 427. https://doi.org/10.3390/info11090427
APA StyleTelino, V., Massa, R., Mota, I., Gomes, A., & Moreira, F. (2020). A Methodology for Creating a Macro Action Plan to Improve IT Use and Its Governance in Organizations. Information, 11(9), 427. https://doi.org/10.3390/info11090427






