Abstract
The preliminary credibility assessment screening system (PCASS) is a US-based program, which is currently being implemented by intelligence units of the North Atlantic Treaty Organization (NATO) to make the initial screening of individuals suspected of infiltrating the Afghan National Defense and Security Forces (ANDSF). Sensors have been instrumental in the PCASS, leading to organizational change. The aim of this research is to describe how the ANDSF adapted to the implementation of PCASS, as well as implemented changes since the beginning of the program. To do so, we have conducted a qualitative, exploratory, and descriptive case study that allows one to understand, through the use of a series of data collection sources, a real-life phenomenon of which little is known. The results suggest that the sensors used in PCASS empower security forces with reliable technologies to identify and neutralize internal threats. It then becomes evident that the technological leadership that PCASS provides allows the developing of a relatively stable and consistent organizational change, fulfilling the objectives of the NATO and the ANDSF.
1. Introduction
In the past two decades, scholars [1,2], professionals [3], and governments [4] have started to develop technological systems that work through sensors and that are playing a significant role in the course of wars. An example is reported by Walters and Traugutt [3], who stated that the preliminary credibility assessment screening system (PCASS) program had a positive impact on the North Atlantic Treaty Organization (NATO) forces in Afghanistan. As of the end of 2012, due to the high rate of incidents arising from internal threats (green-on-blue), the PCASS was able to prevent insurgent cells from infiltrating Afghan police and military forces, allowing the US and coalition advisers to continue their noncombat mission. The relevance of PCASS is not limited to removing insurgents from close contact with coalition forces. Together with the polygraph program, it also ensures that the Afghan National Defense and Security Forces (ANDSF) are adequately capable of developing self-reliance and long-term institutional viability. Generally speaking, the PCASS is a “handheld computer or personal digital assistant that attempts to measure stress to decide whether a subject is telling the truth” [5] (p. 210). The PCASS test is typically used to describe diagnostic procedures using instruments to assess credibility [6]. Those PCASS instruments are essentially based on external physiological information, such as galvanic skin response (GSR) (collects electrodermal activity) and photoplethysmograph (PPG) (collects vasomotor information), which are collected during an interview process, showing photos to the person interviewed or taking questions to stimulate emotional responses that could then be reliably measured physiologically [7].
Even if the scarcity of scientific research on PCASS is not questionable, the limited existing research shows relevant quality and promising results. Some notable examples are presented by Fuller et al. [1], who conducted a research using text-mining methods for detecting deception in the real world, or MacNeill and Bradley [8], who studied the thermoregulatory influences on electrodermal and cardiovascular activity, which can interfere with the detection of hidden information using a polygraph. However, to the best of our knowledge, no article to date examines how sensors and technological leadership drive organizational change. Recognizing the existence of this gap in the literature, we started a phenomenological approach by posing two research questions (RQ) that allowed us to understand and describe the phenomenon in a real-life setting. Based on a case study research, which uses different data collection sources, it is possible to understand, explore and describe the PCASS phenomenon in its real-life setting and, consequently, to appropriately answer the research questions.
The RQ1 focuses on the description of the event: How have Afghan National Defense and Security Forces adapted to the implementation of the preliminary credibility assessment screening system?
The RQ2 describes how the phenomenon under analysis develops or changes: How have the Afghan National Defense and Security Forces developed changes since the beginning of the program?
The main results of this article showed that ANDSF organizationally adapted to the implementation of the PCASS from the perspective of Kotter’s eight-step model of change [9], except for the consolidation of improvements and the production of changes, as well as the institutionalization of new approaches (the last two steps of the model). It will be a challenge for ANDSF to reach the last stages, given that there has been limited technological research and development capacity of the PCASS. Moreover, as ANDSF implements new counterintelligence technologies, those forces are shifting from a closed perspective, where borders are minimal, to a more open organization with greater inter-institutional and supranational cooperation.
This article is organized into five sections. The first section introduces the research by providing a brief contextualization, as well as identifying the gap in the literature and the research questions. Section 2 presents the literature review, which aims to develop the most relevant concepts, focusing on the description of sensors and PCASS technology. Section 3 presents the research methodology, including the research design, sources of data collection, and data analysis. This is followed by the results, where the answers to the research questions are given, along with a discussion of the organizational changes that the sensors and technological leadership have made. The article ends with the conclusions section, which includes the article’s contributions to theory and practice, as well as suggestions for future research.
2. Literature Review
2.1. Brief Contextualization
From the moment the operation entitled “Enduring Freedom” took place, in October 2001, the US forces and their NATO allies initiated an ambitious plan to build Afghanistan by helping the Islamic Republic of Afghanistan to exercise its authority in the country [10]. This effort was particularly significant since Afghanistan is still a major worldwide focus of nation-building efforts and US-led counterinsurgency programs. However, the success of rebuilding Afghanistan is both far-fetched and far-off [11]. With that purpose on the horizon, NATO took the lead with the International Security Assistance Force (ISAF) in August 2003. Its primary objective was to enable the Afghan government to provide effective security across the country and develop new Afghan security forces [12]. Some years later, in November 2010, at the Lisbon summit, NATO agreed gradually to hand over security responsibility to the Afghan National Defense and Security Forces (ANDSF) [10]. By the end of 2014, the transition process was completed, and ISAF finished its mission, while the Afghan forces assumed all the security and defence responsibilities [13].
Established in 2015, the Resolute Support Mission (RSM), a new and small non-combat NATO-led mission to train, advise, and assist (TAA) the ANDSF [14], assumed nationwide responsibility for Afghanistan’s security [15]. The purpose of the RSM was to help the Afghan security forces and institutions to develop the capability to defend Afghanistan and protect its citizens in a sustainable manner [16]. While the allies continue to train and finance Afghan security forces, the Afghan government and the Taliban have started intra-Afghan peace negotiations, announced at a ceremony in Doha on September 12, 2020 [15]. In addition to the contributions that the PCASS has made so far and the need to consolidate short-term gains, the ANDSF should move toward institutionalizing new technological developments, even when the alliance forces withdraw from Afghanistan.
2.2. Sensors and the Preliminary Credibility Assessment Screening System
The PCASS was developed by Lafayette Instrument Company, an American manufacturer of polygraphs [17]. The device collects physiological data from an examinee’s hand during structured interviews carried out by trained operators/examiners. Thus, the psychophysiological detection (PDD) serves a critical complementary function within the forensic sciences, mostly when little physical evidence exists [18]. To do so, the PCASS uses two sensors (Figure 1a) as it collects: (1) electrodermal data from silver/silver/chloride (Ag/Ag/Cl) sensors, for measuring perspiration through changes in the galvanic resistance of the skin [4,19]; and (2) vasomotor information by measuring cardiovascular changes from a photoplethysmograph [4,19,20]. The questions made by the operator are communicated to a personal digital assistant (Figure 1b) that algorithmically evaluates the physiological data. Figure 1 is an adaptation of photos collected from the United States Department of Defense (DoD) [21] and used in Reis’ research [22], having been displayed separately for a better description of the system (i.e., Sensors and PDA).

Figure 1.
Preliminary credibility assessment screening system (PCASS) (Adapted from CSFP [21] and Reis [22]): (a) PCASS aensors; and (b) personal digital assistant (PDA).
The two sensors that can be identified in Figure 1a must be placed in the same examinee’s hand, i.e., Ag/Ag/Cl sensors must be placed on the second and fourth fingers of the participant using Velcro®, and the photoplethysmograph must be connected to the tip of the third finger with a spring clip [20]. Widacki [5] explains that the use of a galvanometer for lie detection has been the golden standard of all polygraph devices, while galvanic skin response (GSR) is among the principal means to identify physiological changes in instrumental deception detection. In addition, the photoplethysmograph (PPG) can noinvasively identify many physiological parameters, such as heart function, blood vessel elasticity, and so on, with the advantage of convenience and accuracy [23]. In that regard, the PPG detects plethysmographic reactions, meaning an increase in the finger’s in blood volume is reflected by an increase in the plethysmography curve [24]. As far as we know, many other technologies have been used by the military, law enforcement, and the intelligence community. Examples are the technologies of voice stress [25], recognition of facial expressions and emotions [26,27] or cellular exploitation (CELLEX), which can enhance the PCASS results, if used as a complement. For instance, CELLEX is a technology that captures and retrieves data from electronic devices, such as contacts, phone numbers, call logs, text messages, SMS messages, app data, pictures, location data, voice messages, and social networking information [28]. Since early on, CELLEX operators have worked in support of the PCASS operations (i.e., tracking suspects), as the information collected by the PCASS is usually not valid as evidence in court [22].
2.3. Technological Leadership
Innovative and disruptive technological advances have led to creating new products, services, and mechanisms, precipitating a revolution in all aspects of personal and professional life [29]. Blair [29] also argues that using systematic thinking to develop new knowledge through artificial intelligence, big data analysis, and the development of more technological teams has implications for leadership, in that it can stimulate necessary changes and inspire others to embark on a new vision. Indeed, the acceleration in the growth of innovations and technological capacity has increased uncertainty regarding the ability of organizations to adapt to these new disruptive contexts, and, in that regard, studies on leadership have brought relevant contributions. However, the literature has also identified resistance to technological change. For instance, Bao [30] distinguishes a series of resistance determinants associated with organizational innovation and technological adaptation, such as psychological, economic, and political, just to name a few. Therefore, to mitigate that effect, transformational leaders typically use various tactics to stimulate beneficial behaviors in followers through their involvement in work [31,32]. Regarding the technological leadership, we identified situations in which companies in different technological and market share positions use foreign research and development to increase their technological capabilities [33]. The issue of technological transfer and absorption capacity is very relevant to developing the ANDSF counterintelligence technological capabilities. Studies from the business world suggest that the most technology-backward organizations may try to reduce the gap (i.e., technology transference) with the help from abroad [34], which was precisely the case of the ANDSF. In that context, NATO continues its mission to enhance the ANDSF’s long-term autonomy and viability, at least in the field of counterintelligence technology, which is the scope of this article.
2.4. Organizational Change
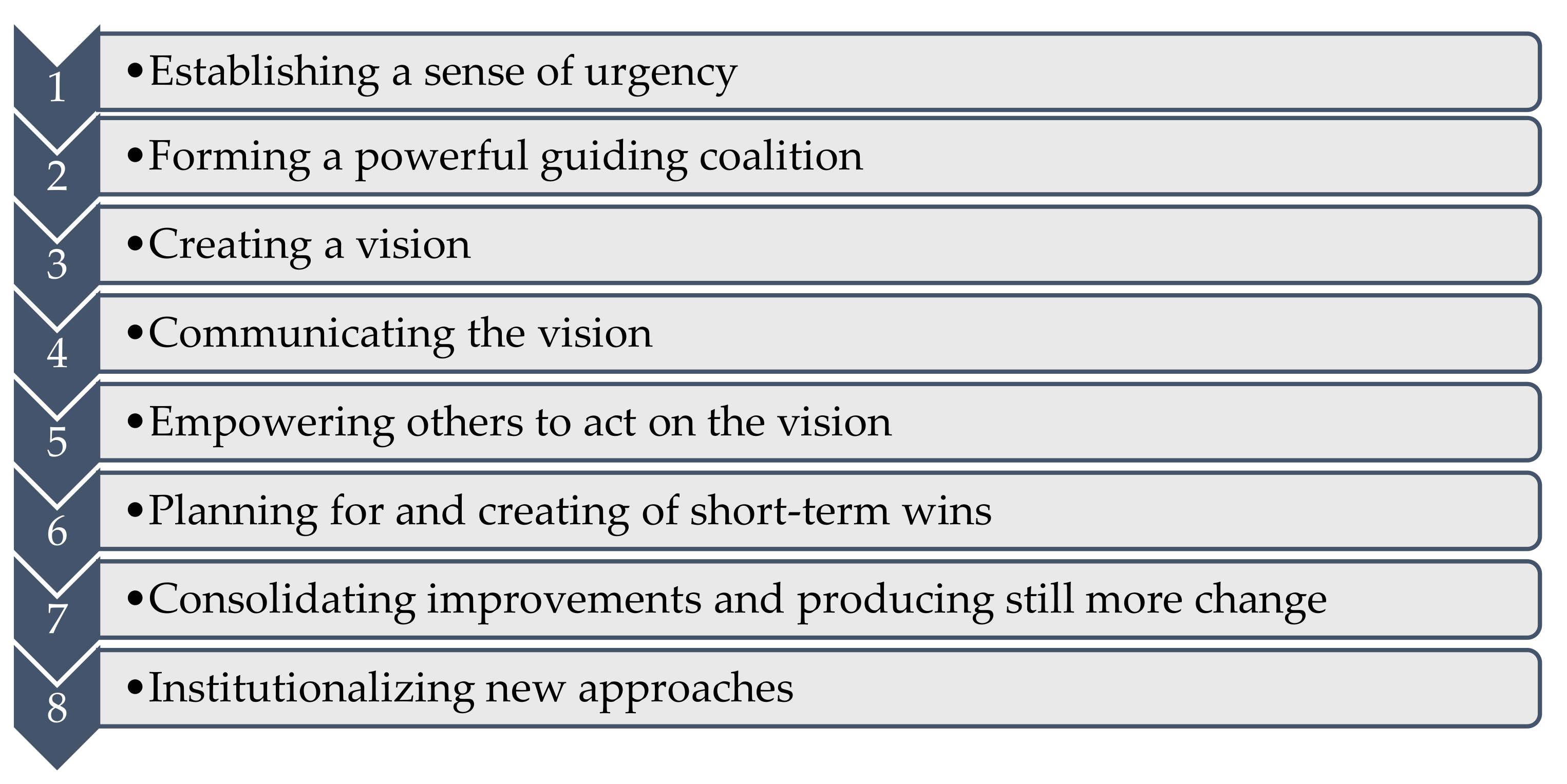
Organizational change is an essential element to all organizations. In that regard, Kotter [9] brought a significant advancement by dividing organizational change into eight essential steps that we now describe (Figure 2).

Figure 2.
Steps of organizational change (Adapted from Kotter [9]).
The first step focuses on establishing a sense of urgency because change is successful when an organization realizes that it has to change to become more competitive or because it needs to survive. However, it is at this stage that most organizations fail because it is usually difficult to convince employees to leave their comfort zone, demanding a proactive and agile leadership. In the second stage, organizations tend to fail when they generally underestimate the importance of alliances. It is important to include elements that are not part of senior management so that there is improved critical thinking and that cross-cutting efforts across the organization are effective. The next step is to develop a vision that helps to establish the direction that the organization needs to follow. Without a strategy to achieve that vision, organizational members may feel lost, and their efforts are ineffective. The communication must be comprehensive and clear, encouraging employees to change and have a perspective for growth. The most successful transformation efforts have included executives using communication across all existing channels, but above all, setting an example.
The fifth step aims to enable others to act according to the vision and to involve as many people as possible in this effort. To that end, it is necessary to encourage new approaches, ideas, and stimulate leadership within the organization. The sixth step concerns obtaining short-term gains, as a real transformation takes time, and in order not to lose momentum, it is important to have short deadlines to meet and celebrate each gain. The seventh step is associated with consolidating improvements and promoting more changes. Instead of declaring victory, successful leaders continue to work to solve bigger problems. The last step is related to the institutionalization of new approaches, and the development of means to guarantee the succession of leadership behaviors are not subject to degradation as soon as the pressure of change is removed, and, for this reason, it is necessary to change norms, behaviors, and values.
Although Kotter’s [9] model is popular in military schools in the USA, Galvin et al. [35] have a slightly more critical view. Kotter’s articles involve a wide range of organizations; however, his concepts need to be refined if we are to implement them in a military context. According to Galvin et al. [35], there are three aspects to consider. First, Kotter’s perspective is that the organization must operate as a unified whole as it moves from the current state to the future state. However, the US armed forces are widely distributed geographically and functionally diverse; therefore, a change at this level would be difficult to operationalize. Second, a sense of urgency can be difficult to establish for an extremely large and complex organization, as is the case with the US armed forces. Finally, the US armed forces have several change efforts taking place simultaneously, and despite the organization’s desire for harmonization, this aspect is difficult to achieve. A more moderate view is presented in Sandler and Galvin [36], who analyze and apply Kotter’s [9] model to the context of military organizations. Thus, we will follow the same guidelines as Sandler and Galvin [36].
3. Methodology
This article follows a qualitative case study research strategy [37], as it aims to understand, explore, and describe a real-life phenomenon [38] rather than exploring and testing hypotheses. It is also exploratory [39] and descriptive [40], as it investigates, describes, and documents a reality for which little is known. Although the study of sensors usually involves a structured and formal research design focused on natural sciences, the objective of this article is to follow an approach focused on social and human sciences due to the need to describe and understand the PCASS phenomenon by conducting an empirical research in a naturalistic setting. Thus, the research approach is based on the constructivist (interpretive) paradigm [41] and inductive thinking [42], in which it seeks to determine the meaning of the PCASS phenomenon from descriptions and development of concepts that help in understanding that reality.
To carry out the research, we used several sources of data collection [43], such as participant observation [44], the review of official documents [40], and semistructured interviews [45]; the latter source was used until theoretical saturation was reached [46]. In this regard, the theoretical saturation was achieved when the inclusion of new respondents led to the repetition and redundancy of results [37], and, therefore, it was not relevant to persist in collecting data from that moment on. Regarding the technical aspects, it was sometimes challenging to achieve theoretical saturation due to the limited number of respondents (i.e., PCASS operators) [22]. Neverthless, we were able to address the research questions satisfactorily with the information collected. The selection of interviewees was performed through convenience sampling, based on their accessibility and availability to participate during the data collection period (6 months). Moreover, similar to other investigations [37,47], we only interviewed highly knowledgeable informants, who were able to describe the phenomenon from different perspectives. Thus, we also chose participants according to different functional areas (i.e., operators, team leaders, and trainers) and different levels of responsibility (i.e., general officers, senior officers, sergeants, and soldiers). The semistructured interviews followed a well-defined protocol, based on the theoretical framework that supported the research questions. This allowed us to understand the process in a structured way, while, at the same time, giving enough freedom to respondents to answer and clarify each question. For credibility reasons, we choose official documents produced by the intervening organizations, mainly by NATO and the US Department of Defense. The documentation was a key piece, and it was collected from open sources (i.e., the Internet), being relevant for the purposes of corroboration and triangulation. Participant observation is sometimes identified as one of the main sources of data collection in qualitative research [40] since it offers a first-hand account of the phenomenon, and when combined with other sources of data collection, it can become a powerful tool. This technique was used because our intention was to assess human behaviors, involving daily trips to the place of study. Therefore, this research’s strength lies in the participant observation, given that the difficulty of most researchers who study this phenomenon is in accessing the data, especially in places of conflict and war, as is the case of Afghanistan. To avoid being influenced by the external environment, we made a personnel record in a research diary [48] in as much detail as possible. This record took the form of field notes that included our observations (comments), direct quotes, and behaviors [49]. For ethical, deontological, and, mainly, confidentiality reasons, all records were destroyed after the research was completed, presenting itself as a significant limitation of the research.
After the data was collected, it was analyzed according to a qualitative data analysis technique, known as “content analysis” [50]. After reading the entire text (i.e., transcripts, field notes, and official documents), we started by identifying the most relevant phrases and ideas, followed by a coding process [51]. After the categories were identified, we had to found patterns in the codes to identify the most relevant topics, and, finally, we generated a map that provided an overview of the data [52]. After completing the aforementioned process, we met the necessary conditions to write the results that can be found in the next section.
This research also has methodological limitations, such as the lack of generalization [53] and greater subjectivity [54] when compared with quantitative research. Thus, although the results are not statistically representative, they capture various perspectives and analyze a complex reality with full descriptive detail, providing a thorough knowledge. To that end, we gathered as much information and detail as possible, collecting data from several sources of information to cover the whole phenomenon.
To ensure reliability (replicability), we made use of data triangulation [55], as in situations where the findings were contradictory, and data collection continued until these inconsistencies were eliminated. In addition, we also made use of university peers to carry out an audit of the methodological process, thus ensuring that the results could be replicated. The validity of the research was challenging to measure. However, one of the most relevant premises was to find out if the results of this research resemble the experiences lived by those we have studied. In that regard, we tried to find out with the respondents if the preliminary results of the interviews really meant what they wanted to tell us. As for external validity (generalization), it is too early to give any assurance.
4. Results and Discussion
4.1. Technological Leadership
Since the beginning of its development (20th century), polygraphs have promised to be a reliable security technology. However, the most critical studies state that the use of lie detector throughout history proved that it was not a fully reliable technology and that it exacerbated mistrust and conflicts regarding its intrusive use, as well as unfounded assumptions that govern its use [56]. Nevertheless, the concern with security reinforced the need to maintain a dissuasive posture, stimulating the need to collect more evidence about its use in an operational environment and also to develop a better understanding of its impact on the organizational environment.
During the study, the reduction in green-on-blue incidents due to the use of the PCASS was evident, resulting in fewer victims among RSM members (NATO data). The NATO internal data also suggests that the reduction of incidents in the coalition forces was mainly due to two factors: first, the ANDSF equipped with the PCASS made it possible to prevent insurgent cells from infiltrating Afghan police forces; second, the PCASS allowed the identification and removal of suspicious Afghan police officers of working closely with the coalition forces. Therefore, it seems clear that the RSM’s objectives have been partially achieved, motivating the reinforcement of programs of this nature as a complementary form to the counterintelligence activities. While the PCASS has been implemented at the ANDSF, we have found that the introduction of this technology has encouraged greater inter-institutional cooperation, particularly amongst the Afghan Armed Forces, the Afghan National Police, and the National Security Directorate (NDS). This inter-institutional relationship is very relevant with regard to information sharing, given that this has been one of the most significant difficulties in the context of the ANDSF.
In light of the above, the PCASS had implications at the level of senior Afghan officials, who tended to shift from a liberal leadership style to a transformational style due to the need to adapt in a volatile, uncertain, complex, and ambiguous (VUCA) environment. In such environments, as is the case in war zones or nation-state building countries [57], ANDSF leaders must embrace the opportunities and challenges of the PCASS technologies [58]. As new counterintelligence technologies are changing the way the ANDSF operates and organizes its work, this organization is shifting from a closed perspective, where boundaries are very well-defined, to a more open organization with NATO allies and their Afghan counterparts in order to capitalize on results. This shift naturally means that assumptions about leadership tend to change. That change should move toward maintaining relations with NATO and the US so as to convince these stakeholders to increase technology transfer to Afghanistan, thus allowing ANDSF to develop its own R&D capabilities. While NATO’s organizational vision involves empowering Afghan, the underlying difficulty may be related to the US’s willingness to hand over its know-how in ANDSF-critical technologies.
4.2. Organizational Change
Following Kotter [9], the US and coalition forces established a sense of urgency (no. 1, Figure 2) from the events that happened between January 2011 and December 2012. During that time, there were more than 60 attacks by the ANDSF members against the US and coalition forces, with more attacks in the last six months of 2012 than in the previous year [59]. The Roggio and Lundquist’s [60] and Shortland et al.’s [61] articles provide statistics that confirm the above argument. Following, the Resolute Support Mission (RSM) developed the projects (e.g., PCASS) and the means to face the green-on-blue threat, forming a powerful guiding coalition (no. 2, Figure 2) supported by the NATO military, who had the responsibility to carry out the mission of training, advising, and assisting (TAA) their Afghan counterparts (in the specific case of the PCASS, the ANDSF counterintelligence units). TAA missions included organization, training, and equipment of the Afghan Ministry of Interior Affairs (MoI) and the Ministry of Defences (MoD) intelligence system. The counterintelligence advisors included missions such as mentoring and counseling; assisting the implementation of an intelligence and counterintelligence model; synchronizing intelligence activities between agencies; supporting the development of plans, policies, and doctrines; supervising technical innovations and development; and institutionalizing an intelligence record management system, just to mention a few [22]. On several occasions, the first researcher of the article had the opportunity to participate and assist in developing the milestones to be achieved over the next years, making the PCASS program part of RSM’s new organizational vision (no. 3, Figure 2). Within NATO intelligence staff and, in particular, within the TAA advisors, every effort was made to communicate the RSM’s vision and strategies (no. 4, Figure 2), aligning the new behaviors with the established milestones. The TAA advisors made an additional contribution to communicating NATO’s organizational vision by passing on the (adapted) strategy to their Afghan counterparts, aiming for a joint effort on the path of the ANDSF long-term autonomy. Concerning empowering others to act according to the vision (no. 5, Figure 2), in addition to enabling the Afghan counterintelligence units with the necessary PCASS technologies, NATO also invested in training programs to renew the ANDSF human resources [22].
In steps 6 and 7 (Figure 2), it is not expected that, in the coming years, the ANDSF will move from technological laggards to innovators or technology developers. For now, their success is limited to the imitation and development of standards that make it possible to carry out the PCASS procedures in a credible manner, as well as to ensure their operations with the existing material and human resources. The reality is that Afghanistan will remain dependent on the international community for years to come, both to finance its forces and to have independent projects, even in a post-reconciliation environment [14]. As one of the US Department of Defense reports to the Senate mentions [14], the Afghan government’s funding for the MoD and MoI together is about $500 million a year, about a 1/4 of the government’s total revenue. Thus, it is expected to take some time before Afghanistan is able to finance its own PCASS technological development programs. As far as the institutionalization of new approaches (no. 8, Figure 2) is concerned, there are still no answers. Although the means to ensure leadership development and succession are being developed (e.g., train-the-trainers program), there are still some doubts from NATO and the ANDSF side about the ability of Afghan counterintelligence units to guarantee their full autonomy.
Overall, despite the existing criticism of the application of Kotter’s model in the armed forces (e.g., Galvin et al. [35]), we recognize that, in the scope of this research, the model is adequate to understand and describe the PCASS phenomenon in organizational change. It is worth noting that the information contained in this section is somewhat limited because of the difficulty of acquiring data in environments of war and conflict, as well as the impossibility of disclosing confidential data. Nevertheless, an exploratory discussion is still worthwhile, as the results are innovative, original, and help understand a phenomenon that has not yet been explored.
5. Conclusions
The findings indicate that the implementation of PCASS, which has been instrumental to the US-based program and resulted in a series of organizational changes in Afghanistan, has led mainly to short-term organizational achievements. However, the challenge is quite evident in a long-term consolidation. ANDSF has difficulties not only in guaranteeing its operations with the existing materials and human resources but also in guaranteeing the autonomy of counterintelligence of ANDSF leaders. It is also worth mentioning that the US is the leader in R&D of the PCASS and holds know-how that is not fully shared with ANDSF. Thus, the latter are still dependent on US technologies to develop their own operations.
Concerning the research questions, this article highlights that, with the PCASS technology deployment, ANDSF has successfully implemented six out of the eight phases of Kotter’s [9] organizational change model. In light of the above, as ANDSF implements new counterintelligence technologies, the organization is becoming more open as it enables to establish cooperation opportunities between similar Afghan (e.g., National Security Directorate, Afghan Armed Forces, Afghan National Police, etc.) and international forces (e.g., NATO). In sum, the theoretical contributions of this article are related to the analysis and discussion of the implementation of PCASS technologies according to Kotter’s [9] model in the context of the NATO–ANDSF organizational change. This contribution is particularly relevant when there is a shortage of scientific research about organizational change on defense and security forces, making it possible to shed some light on the existing literature [32]. In addition, most articles published in this field focus on technical analysis of the PCASS [62], leaving a void on the dynamics of organizational change.
This research has interesting managerial or practical contributions. It reveals that ANDSF senior officials tend to shift from a liberal leadership style to a transformational one due to the need to adapt to a VUCA counterintelligence environment. On the other hand, the article reminds ANDSF leaders that they should be aware of the opportunities to establish technological cooperation and information-sharing relationships between national and international defense and security forces. Moreover, this research and others [3] suggest that the PCASS has enabled Afghan defense and security forces to identify and neutralize internal threats. It seems that the objectives of RSM have been partially achieved, motivating the reinforcement of programs of this nature for counterintelligence activities. Moreover, it is somewhat clear that the technological leadership that the PCASS provides to Afghan forces has enabled them to develop a necessary, stable, and consistent organizational change, fulfilling the objectives of NATO and the ANDSF. Despite the gains achieved to date, there is still some way to go, namely concerning the consolidation of improvements, producing even more change, and institutionalizing new approaches.
As for suggestions for future research, it may be relevant to conduct similar research in Iraq, where the PCASS projects have also been successfully implemented so as to validate the results of this case study. An alternative may be related to the reinforcement of intelligence systems that use a combination of technologies; specifically, it is expected that facial expressions and emotional recognition technologies will assume greater relevance in the sphere of counterintelligence, extrapolating the domains of psychology and medicine. Besides the investigation of advanced sensors applied to the military, law enforcement, and intelligence community, it is also essential to study their impact on organizational change.
Author Contributions
Conceptualization, J.R.; methodology, J.R.; software, J.R.; validation, M.A., J.C., N.M., and Y.C.; formal analysis, J.R.; investigation, J.R.; resources, J.R.; data curation, J.R.; writing—original draft preparation, J.R.; writing—review and editing, J.R. and N.M.; supervision, J.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Funds through the FCT (Foundation for Science and Technology), I.P., within the scope of the project Ref. UIDB/05583/2020.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
We would like to thank the Research Centre in Digital Services (CISeD) and the Polytechnic of Viseu for their support.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Fuller, C.; Biros, D.; Delen, D. An Investigation of Data and Text Mining Methods for Real World Deception Detection. Expert Syst. Appl. 2011, 38, 8392–8398. [Google Scholar] [CrossRef]
- Shamoo, A. Ethical and Regulatory Challenges in Psychophysiology and Neuroscience-based Technology for Determining Behavior. Account. Res. 2010, 17, 8–29. [Google Scholar] [CrossRef] [PubMed]
- Walters, R., Jr.; Traugutt, L. The State of Afghanistan´s Intelligence Enterprise. Mil. Rev. 2017, 97, 64–71. [Google Scholar]
- Senter, S.; Waller, J.; Krapohl, D. Validation Studies for the Preliminary Credibility Assessment Screening System (PCASS); Department of Defense Polygraph Institute: Fort Jackson, SC, USA, 2006. [Google Scholar]
- Widacki, J. Discoverers of the Galvanic Skin Response. Eur. Polygr. 2015, 9, 209–220. [Google Scholar] [CrossRef][Green Version]
- Palmatier, J.; Rovner, L. Credibility assessment: Preliminary Process Theory, the polygraph process, and construct validity. Int. J. Psychophysiol. 2015, 95, 3–13. [Google Scholar] [CrossRef]
- Gordon, N.; Fleisher, W. Effective Interviewing and Interrogation Techniques, 3rd ed.; Academic Press, Elsevier: Burlington, MA, USA, 2010. [Google Scholar]
- MacNeill, A.; Brandley, M. Temperature Effects on Polygraph Detection of Concealed Information. Psychophysiology 2016, 53, 143–150. [Google Scholar] [CrossRef] [PubMed]
- Kotter, J. Leading Change: Why Transformation Efforts Fail. Harv. Bus. Rev. 1995, 73, 59–67. [Google Scholar]
- Taylor, C. Afghanistan: The Timetable for Security Transition; House of Commons Library: London, UK, 2011. [Google Scholar]
- Berger, M.; Reese, J. From Nation-States in Conflict to Conflict in Nation-States: The United States of America and Nation Building from South Vietnam to Afghanistan. Int. Polit. 2010, 47, 451–471. [Google Scholar] [CrossRef]
- NATO. ISAF´s Mission in Afghanistan (2001–2014) (Archived). 2015. Available online: https://www.nato.int/cps/en/natohq/topics_69366.htm (accessed on 20 August 2020).
- NATO. Inteqal: Transition to Afghan Lead. 2015. Available online: https://www.nato.int/cps/en/natohq/topics_87183.htm (accessed on 23 August 2020).
- US DoD. Enhancing Security and Stability in Afghanistan. Available online: https://media.defense.gov/2020/Jul/01/2002348001/-1/-1/1/enhancing_security_and_stability_in_afghanistan.pdf (accessed on 27 February 2021).
- NATO. NATO and Afghanistan. 2020. Available online: https://www.nato.int/cps/en/natohq/topics_8189.htm (accessed on 19 December 2020).
- NATO. Newsroom. Afghan National Police Learn New System for Intelligence Sharing and Records Archiving. 2018. Available online: https://rs.nato.int/news-center/feature-stories/2018-feature-stories/afghan-national-police-learn-new-system-for-intelligence-sharing-and-records-archiving.aspx (accessed on 20 August 2020).
- Krapohl, D.; Handler, M.; Sturm, S.; Ansley, N.; Backster, C.; Barland, G.; Brown, T.; Cestaro, V.; Dollins, A.; Dutton, D.; et al. Terminology Reference for the Science of Psychophysiological Detection of Deception; 3rd Edition. 2012. Available online: https://www.polygraph.org (accessed on 19 December 2020).
- Senter, S.; Dollins, A.; Krapohl, D. A Comparison of Polygraph Data Evaluation Conventions Used at the University of Utah and the Department of Defense Polygraph Institute. Polygraph 2004, 33, 214–222. [Google Scholar]
- Harris, M.; McQuarrie, A. The Preliminary Credibility Assessment System Embedded Algorithm Description and Validation Results; Johns Hopkins University Applied Physics Laboratory Report Number GED-R-06-7571; Johns Hopkins University: Baltimore, MD, USA, 2009. [Google Scholar]
- Battelle Memorial Institute. Efficacy of Prototype Credibility Assessment Technologies: PCASS Final Report; Battelle Memorial Institute: Columbus, OH, USA, 2007. [Google Scholar]
- CSFP. Counterintelligence Support to Force Protection. Number 5240.22. 2019. Available online: https://fas.org/irp/doddir/dod/ (accessed on 2 July 2019).
- Reis, J. Counterintelligence in Afghanistan: Preliminary Credibility Assessment Screening System. Adv. Mil. Technol. 2020, 15, 43–53. [Google Scholar] [CrossRef]
- Wei, C.; Sheng, L.; Lihua, G.; Yuquan, C.; Min, P. Study on conditioning and feature extraction algorithm of photoplethysmography signal for physiological parameters detection. In Proceedings of the 2011 4th International Congress on Image and Signal Processing, Shanghai, China, 15–17 October 2011; IEEE: Piscatway, NJ, USA, 2011; Volume 4, pp. 2194–2197. [Google Scholar]
- Kubis, J. Analysis of Polygraphic Data (Part 2). Polygraph. J. Am. Polygr. Assoc. 1973, 2, 89–107. Available online: https://www.polygraph.org/assets/docs/APA-Journal.Articles/Vol.2.1973/polygraph%201973%20022.pdf (accessed on 26 August 2020).
- Pool, R. Field Evaluation in Intelligence and Counterintelligence Context: Workshop Summary; National Academies Press: Washington, DC, USA, 2010. [Google Scholar]
- Bartlett, M.; Littlewort, G.; Frank, M.; Lainscsek, C.; Fasel, I.; Movellan, J. Automatic Recognition of Facial Actions in Spontaneous Expressions. J. Multimed. 2006, 1, 22–35. [Google Scholar] [CrossRef]
- Sajjad, M.; Nasir, M.; Ullah, F.; Muhammad, K.; Sangaiah, A.; Baik, S. Raspberry Pi assisted facial expression recognition framework for smart security in law-enforcement services. Inf. Sci. 2019, 479, 416–431. [Google Scholar] [CrossRef]
- Hugdahl, K. Perspectives in Cognitive Neuroscience. Psychophysiology: The Mind-Body Perspective; Harvard University Press: Cambridge, MA, USA, 1995. [Google Scholar]
- Blair, G. Leadership and Context to Create the New Technological Society. J. Innov. Res. Educ. Manag. 2020, 4, 6–9. [Google Scholar]
- Bao, Y. Organizational Resistance to Performance-enhancing Technological Innovations: A Motivation-threat-ability Framework. J. Bus. Ind. Mark. 2009, 24, 119–130. [Google Scholar] [CrossRef]
- Farahnak, L.; Ehrhart, M.; Torres, E.; Aarons, G. The influence of transformational leadership and leader attitudes on subordinate attitudes and implementation success. J. Leadersh. Organ. Stud. 2020, 27, 98–111. [Google Scholar] [CrossRef]
- Lai, F.; Tang, H.; Lu, S.; Lee, Y.; Lin, C. Transformational Leadership and Job Performance. The Mediating Role of Work Engagement. SAGE Open 2020, 10, 2158244019899085. [Google Scholar] [CrossRef]
- Berry, H. Leaders, Laggards, and the Pursuit of Foreign Knoledge. Strateg. Manag. J. 2006, 27, 151–168. [Google Scholar] [CrossRef]
- Smeets, R.; Bosker, E. Leaders, Laggards and Technology Seeking Strategies. J. Econ. Behav. Organ. 2011, 80, 481–497. [Google Scholar] [CrossRef]
- Galvin, T.; Clark, L. Beyond Kotters Leading Change: A Broad Perspective on Organizational Change for Senior US Military Leaders; Army War College Carlisle United Stage: Carlisle, PA, USA, 2015; pp. 1–59. [Google Scholar]
- Sandler, K.; Galvin, T. Leading Change in Military Organizations: Primer for Senior Leaders. Nav. War Coll. Rev. 2020, 73, 13. [Google Scholar]
- Kraus, S.; Clauss, T.; Breier, M.; Gast, J.; Zardini, A.; Tiberius, V. The economics of COVID-19: Initial empirical evidence on how family firms in five European countries cope with the corona crisis. Int. J. Entrep. Behav. Res. 2020, 26, 1067–1092. [Google Scholar] [CrossRef]
- Yin, R. Case Study Research and Applications: Design and Methods; SAGE Publications: Thousand Oaks, CA, USA, 2018. [Google Scholar]
- Hancock, D.; Algozzine, B. Doing Case Study Research: A Practical Guide for Beginning Researchers; Teachers College Press: New York, NY, USA, 2016. [Google Scholar]
- Mills, A.; Durepos, G.; Wiebe, E. Encyclopedia of Case Study Research; SAGE Publications: London, UK, 2010. [Google Scholar]
- Mackenzie, N.; Knipe, S. Research Dilemmas: Paradigms, Methods and Methodology. Issues Educ. Res. 2006, 16, 193–205. [Google Scholar]
- Yin, R. Qualitative Research from Start to Finish; The Guilford Press: New York, NY, USA, 2016. [Google Scholar]
- Given, L. The Sage Encyclopedia of Qualitative Research Methods; SAGE Publications: Thousand Oaks, CA, USA, 2008. [Google Scholar]
- Merriam, S.; Tisdell, E. Qualitative Research: A Guide to Design and Implementation; John Wiley & Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Galletta, A. Mastering the Semi-Structured Interview and Beyond: From Research Design to Analysis and Publication; New York University Press: New York, NY, USA, 2013. [Google Scholar]
- Saunders, M.; Townsend, K. Reporting and Justifying the number of Interview Participants in Organizational and Workplace Research. Br. J. Manag. 2016, 27, 836–852. [Google Scholar] [CrossRef]
- Reis, J.; Amorim, M.; Melão, N. Multichannel Service Failure and Recovery in a O2O Era: A Qualitative Multi-Method Research in the Banking Services Industry. Int. J. Prod. Econ. 2019, 215, 24–33. [Google Scholar] [CrossRef]
- Thorpe, R.; Holt, R. The Sage Dictionary of Qualitative Management Research; SAGE Publications: Thousand Oaks, CA, USA, 2008. [Google Scholar]
- Bloor, M.; Wood, F. Keywords in Qualitative Methods: A Vocabulary of Research Concepts; SAGE Publications: London, UK, 2006. [Google Scholar]
- Elo, S.; Kyngäs, H. The Qualitative Content Analysis Process. J. Adv. Nurs. 2008, 62, 107–115. [Google Scholar] [CrossRef] [PubMed]
- Neuendorf, K.; Kumar, A. Content Analysis. Int. Encycl. Polit. Commun. 2015, 1–10. [Google Scholar] [CrossRef]
- Reis, J.; Santo, P.; Melão, N. Impact of Artificial Intelligence Research on Politics of the European Union Member States: The Case Study of Portugal. Sustainability 2020, 12, 6708. [Google Scholar] [CrossRef]
- Stake, R. The Art of Case Study Research; SAGE Publications: Thousand Oaks, CA, USA, 1995. [Google Scholar]
- Ciesielska, M. Qualitative Methodologies in Organization Studies Volume II: Methods and Possibilities; Springer: Cham, Switzerland, 2018. [Google Scholar]
- Golafshani, N. Understanding Reliability and Validity in Qualitative Research. Qual. Rep. 2003, 8, 597–607. [Google Scholar]
- Baesler, J. From Detection to Surveillance: US Lie Detection Regimes from the Cold War to the War on Terror. BEHEMOTH-A J. Civilis. 2015, 8, 46–66. [Google Scholar]
- Beten, D.; Palestini, C.; Marchesoni, E.; Brouillon, M. Advanced Technologies at NATO: An Overview. In Advanced Technologies for Security Applications; Palestini, C., Ed.; NATO Science for Peace and Security Series B: Physics and Biophysics; Springer: Dordrecht, The Netherlands, 2020. [Google Scholar] [CrossRef]
- Cockburn, T.; Smith, P. Reflecting Emerging Digital Technologies in Leadership Models. In Global Business Leadership Development for the Fourth Industrial Revolution; IGI Global: Hershey PA, USA, 2021; pp. 26–64. [Google Scholar]
- Long, A. “Green on Blue”: Insider attacks in Afghanistan. Survival 2013, 55, 167–182. [Google Scholar] [CrossRef]
- Roggio, B.; Lundquist, L. Green-on-Blue Attacks in Afghanistan: The Data. Available online: http://www.longwarjournal.org/archives/2012/08/Green-on-blue_attack.php (accessed on 23 August 2020).
- Shortland, N.; Nader, E.; Sari, H.; Palasinski, M.; Hilland, C. Murder on Maneuver: Exploring Green-on-blue Attacks in Afghanistan. Armed Forces Soc. 2019, 45, 368–388. [Google Scholar] [CrossRef]
- Kircher, J.C.; Packard, T.; Bell, B.G.; Bernhardt, P. Effects of Prior Demonstrations of Polygraph Accuracy on Outcomes of Probable-Lie and Directed-Lie Polygraph Tests; Utah University: Salt Lake City, UT, USA, 2001; Available online: https://apps.dtic.mil/sti/citations/ADA404128 (accessed on 27 February 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).